HACKING Dont Learn to Hack Hack to Learn













- Slides: 22

HACKING Don’t Learn to Hack – Hack to Learn

Outline • • Brief History What do hackers do? Hacker’s techniques System Hacking

Who is a “hacker”? • There at least two common interpretations: – Someone who bypasses the system’s access controls by taking advantage of security weaknesses left in the system by developers – Someone who is both knowledgeable and skilled at computer programming, and who is a member of the hacker subculture, one with it’s own philosophy and code of ethics

A Brief History of Hacking • 1960 s – MIT AI Lab – Ken Thompson invented UNIX – Positive Meaning • 1970 s – Dennis Ritchie invented C – Phreaking : John Draper – Phreaking : YIPL/TAP – Phreaking : Blue boxes

A Brief History of Hacking • 1980 s – Cyberspace coined – 414 s arrested – Two hacker groups formed – 2600 published • 1990 s – National Crackdown on hackers – Kevin Mitnick arrested – Microsoft’s NT operating system pierced – National infrastructure protection center unveiled

A Brief History of Hacking • 2000 – In one of the biggest denial-of-service attacks , hackers launch attacks against e. Bay, Yahoo!, CNN. com. , Amazon and others.

What Do Hackers Do? • System – Access confidential information – Threaten someone from YOUR computer – Broadcast your confidential letters or materials – Store illegal or espionage material

What Do Hackers Do? • Network – Eavesdrop and replay – Imposer: server / client – Modify data / stream – Denial-of-Service

Hacker’s techniques • System hacking • Network hacking • Software hacking

System Hacking • • Footprinting Scanning Enumeration Gaining access Escalating privilege Covering tracks Creating backdoors Denial of service

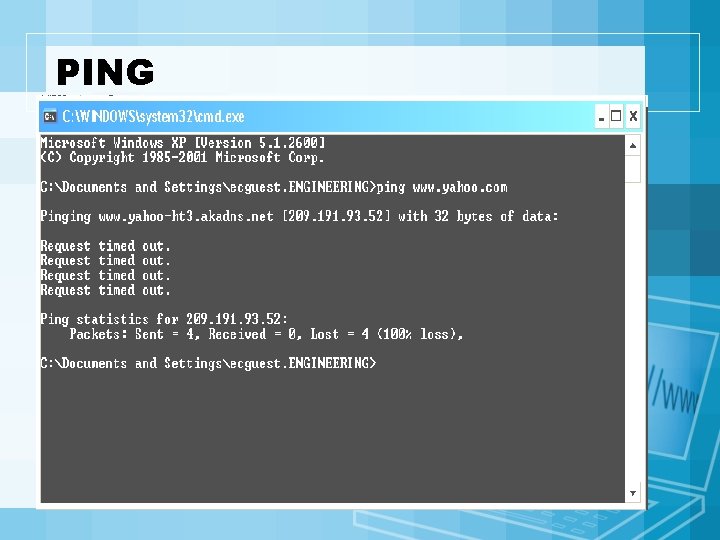
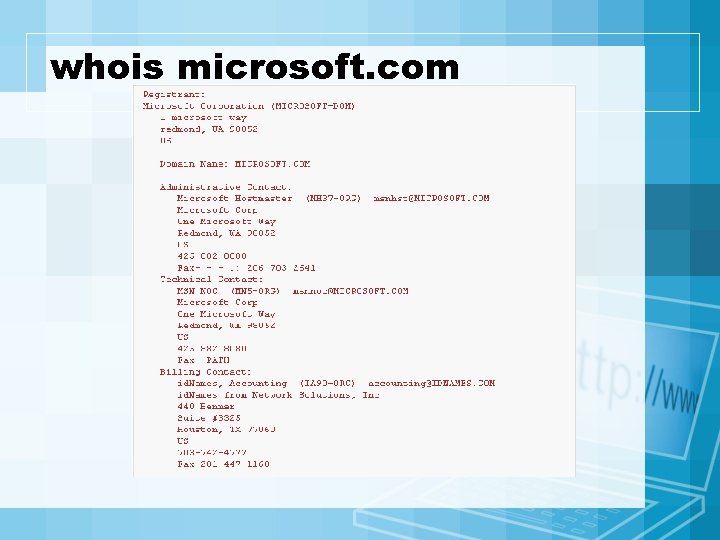
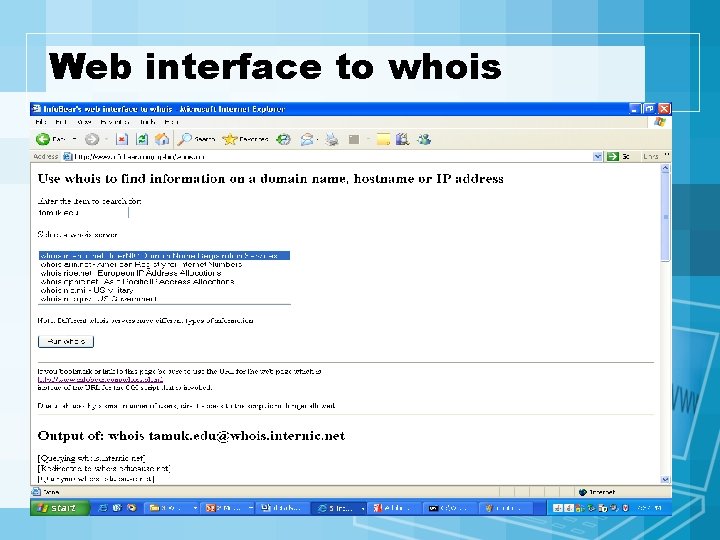
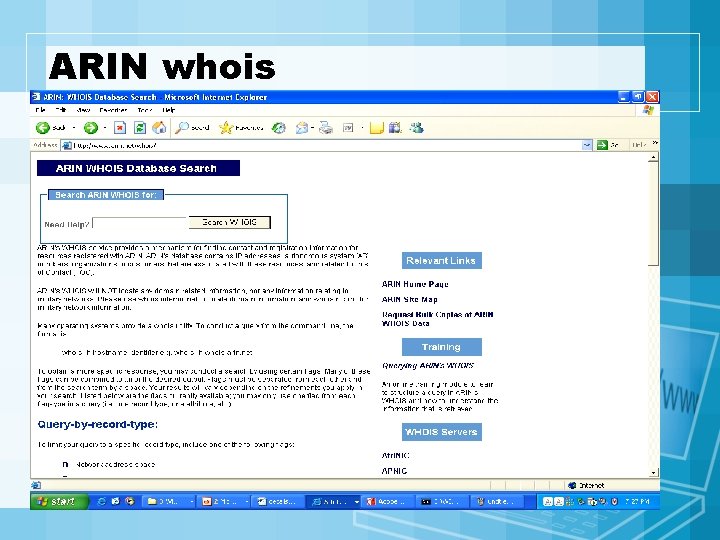
Footprinting • Objective – To learn as much as you can about target system, it's remote access capabilities, its ports and services, and the aspects of its security. • Techniques – Open source search – Whois – Web interface to whois – ARIN whois

PING

whois microsoft. com

Web interface to whois

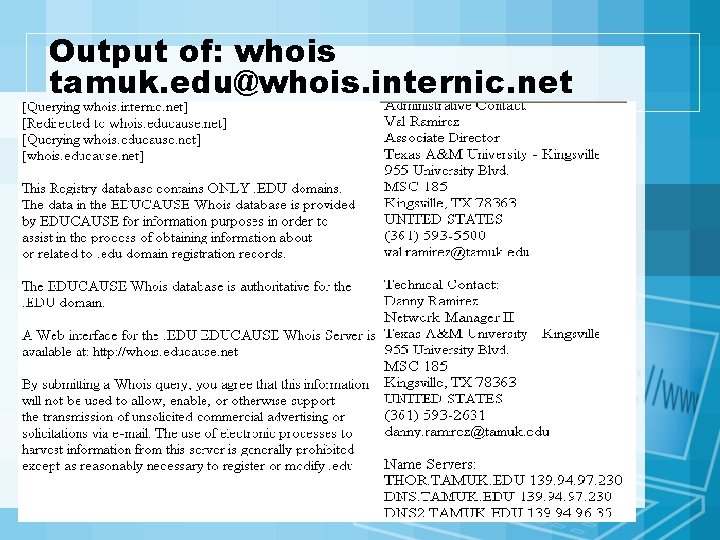
Output of: whois tamuk. edu@whois. internic. net

ARIN whois

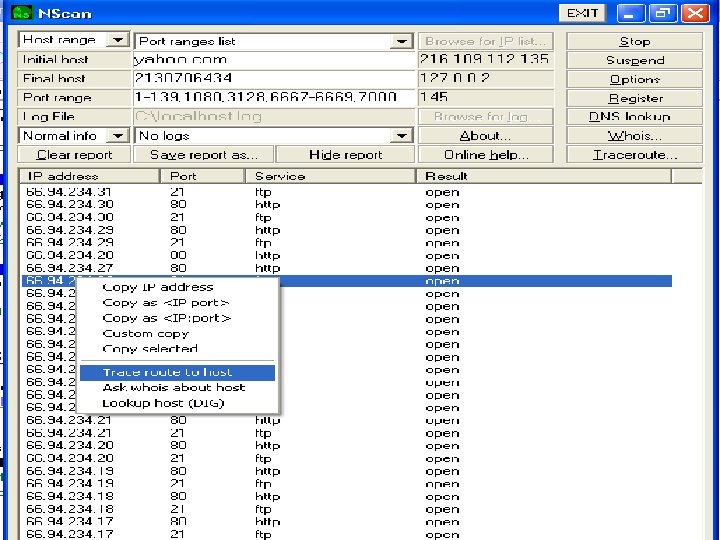
Scanning • Objective – Bulk target assessment and identification of listing services focuses the attention on the most promising avenues of entry • Techniques – Ping sweep – TCP/UDP port scan – OS Detection


Port numbers and description

Enumeration • Objective – More intrusive probing now begins as attackers begin identifying valid user accounts or poorly protected resource shares • Techniques – List user accounts – List file shares – Identify applications

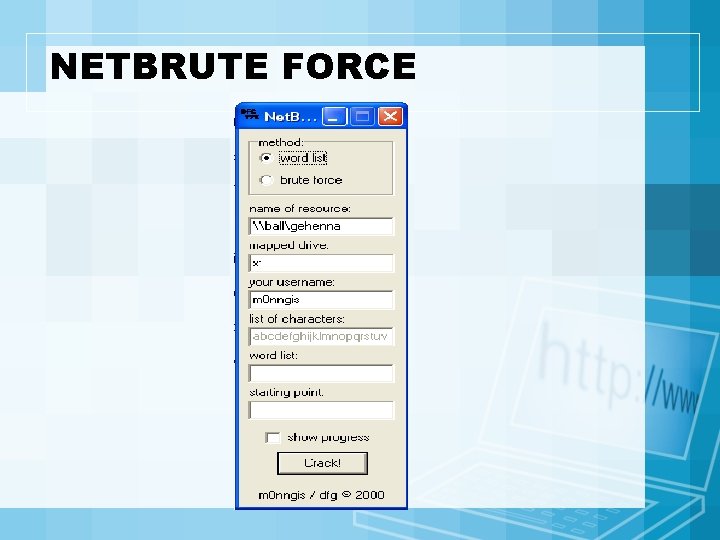
NETBRUTE FORCE

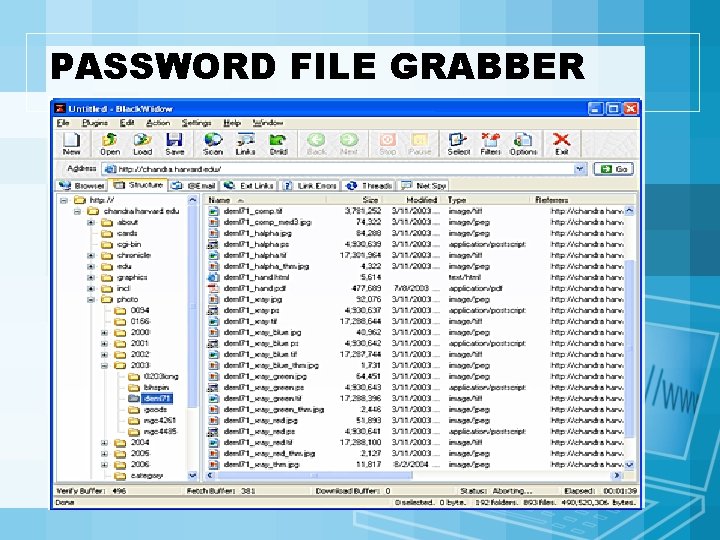
PASSWORD FILE GRABBER