Intro to Kali Linux Tools What makes Kali








- Slides: 19

Intro to Kali Linux & Tools What makes Kali Linux different? Stuart Hoxie

Basics ❖ Debian distro for the use of industry grade penetration testing ❖ Completely customizable, any user can tweak the experience to their liking ❖ ARMEL and ARMHF, compatible with ARM based devices Stuart Hoxie

Legal Remember: anything you do while inside an environment such as many of the tools Kali linux offers, they can be viewed as malicious activity. Any form of testing should be done in a safe environment, VM, or done with the strict permission and supervision of the organization. -in short, be smart about what you do. Stuart Hoxie

Ethical Phases ❖ ❖ ❖ Information Gathering Reconnaissance Access/Exploitation Post Exploitation Reporting Finishing/wrap up Stuart Hoxie

Installations ❖ Nothing inherently special about installing Kali linux ➢ Single, dual, etc boot ➢ https: //www. kali. org/downloads/ ❖ Prefered if, as a student, use a virtual box ❖ After installation and boot, open console and enter: ➢ apt-get update && apt-get upgrade && apt-get dist-upgrade Stuart Hoxie

Tools 3 phases will be covered: resource gathering/Reconnaissance Exploitation Zenmap/Nmap Wireshark Armitage Metasploit Stuart Hoxie (GUI of Metasploit) Meta. Sploit Framework

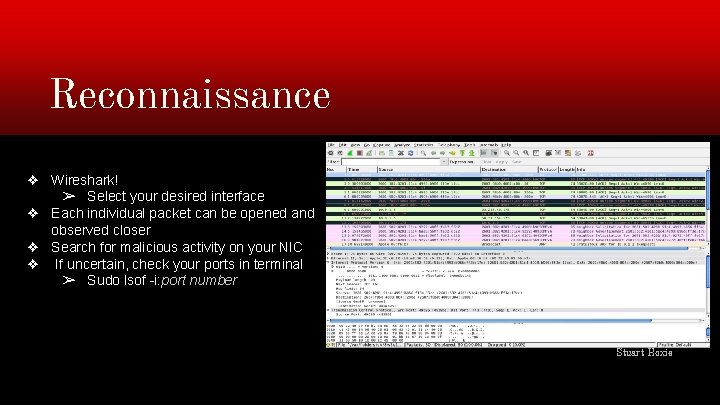
Reconnaissance ❖ Wireshark! ➢ Select your desired interface ❖ Each individual packet can be opened and observed closer ❖ Search for malicious activity on your NIC ❖ If uncertain, check your ports in terminal ➢ Sudo lsof -i: port number Stuart Hoxie

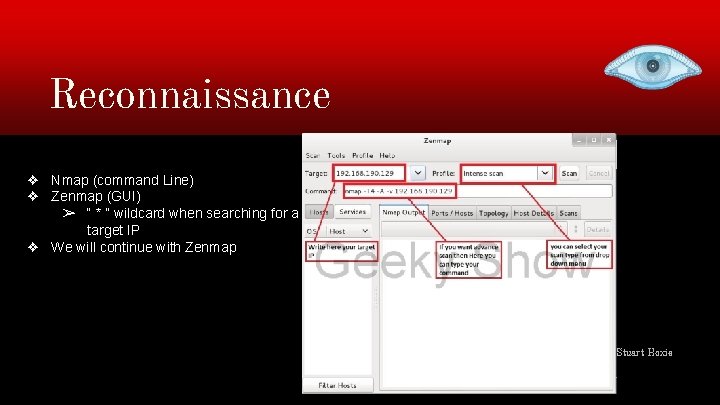
Reconnaissance ❖ Nmap (command Line) ❖ Zenmap (GUI) ➢ “ * ” wildcard when searching for a target IP ❖ We will continue with Zenmap Stuart Hoxie

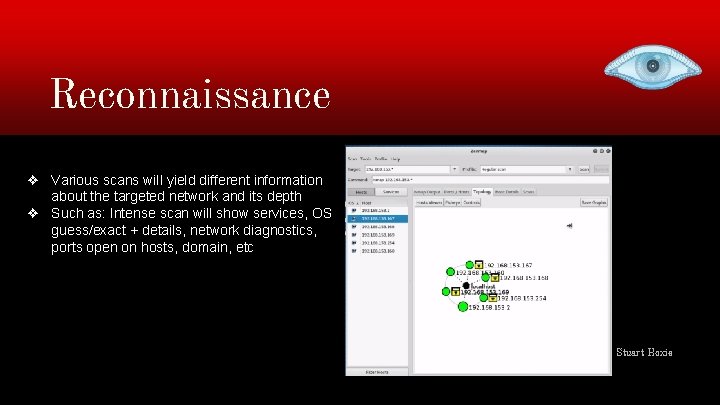
Reconnaissance ❖ Various scans will yield different information about the targeted network and its depth ❖ Such as: Intense scan will show services, OS guess/exact + details, network diagnostics, ports open on hosts, domain, etc Stuart Hoxie

Exploitation ❖ ❖ ❖ Remote Attack Client Side Attack Blind Side Attack/ Hail Mary Social Engineering Attack Fuzzing/ Dos Man In The Middle Stuart Hoxie

Access: Exploit ❖ ❖ ❖ Metasploit + Armitage Scripting (public + nonpublic) SE-Toolkit Dos Google Stuart Hoxie

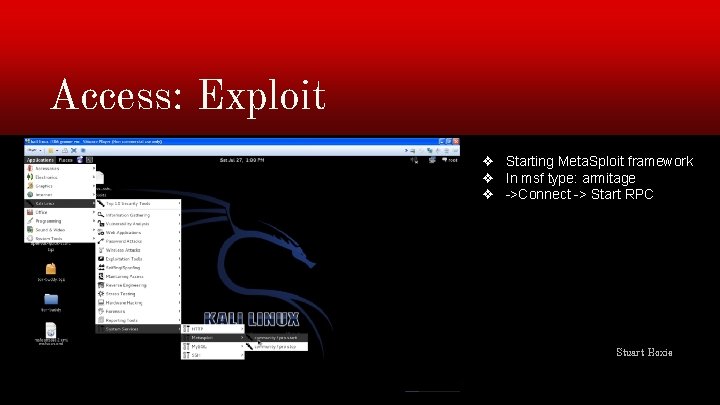
Access: Exploit ❖ Starting Meta. Sploit framework ❖ In msf type: armitage ❖ ->Connect -> Start RPC Stuart Hoxie

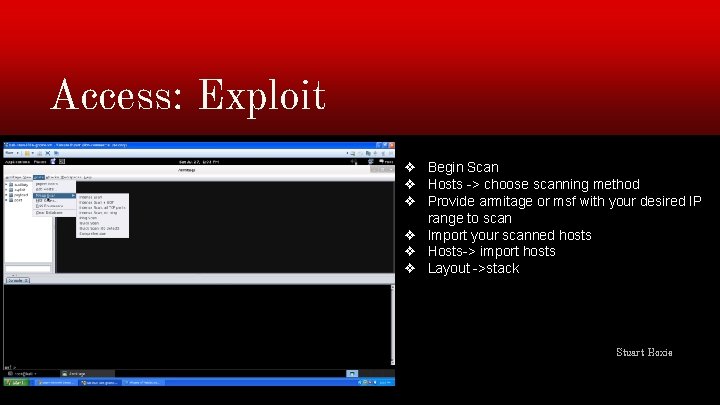
Access: Exploit ❖ Begin Scan ❖ Hosts -> choose scanning method ❖ Provide armitage or msf with your desired IP range to scan ❖ Import your scanned hosts ❖ Hosts-> import hosts ❖ Layout ->stack Stuart Hoxie

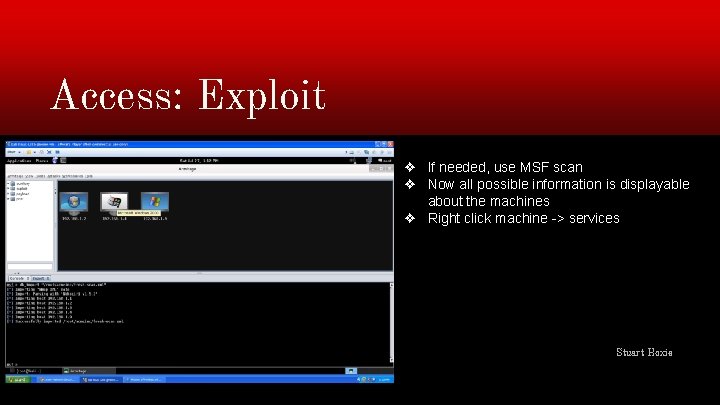
Access: Exploit ❖ If needed, use MSF scan ❖ Now all possible information is displayable about the machines ❖ Right click machine -> services Stuart Hoxie

Footnote: security ❖ These scans can a fantastic source for finding open ports, useless programs, and vulnerabilities to your system. Stuart Hoxie

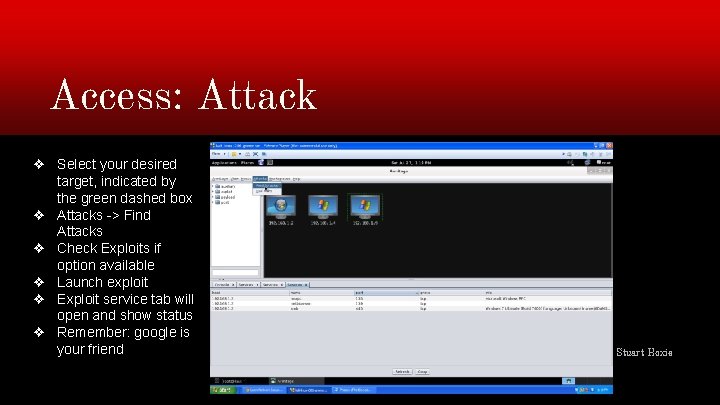
Access: Attack ❖ Select your desired target, indicated by the green dashed box ❖ Attacks -> Find Attacks ❖ Check Exploits if option available ❖ Launch exploit ❖ Exploit service tab will open and show status ❖ Remember: google is your friend Stuart Hoxie

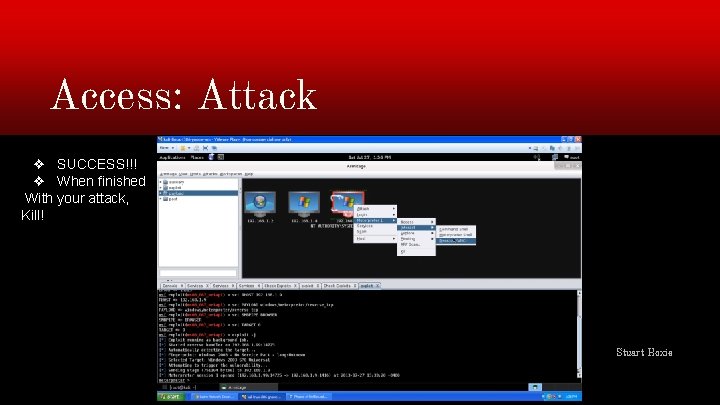
Access: Attack ❖ SUCCESS!!! ❖ When finished With your attack, Kill! Stuart Hoxie


Sources: https: //www. youtube. com/watch? v=l. Zlqr 2 PFJIo https: //www. youtube. com/watch? v=8 l. R 27 r 8 Y_ik https: //www. youtube. com/watch? v=dlcx-fmzrnc http: //knoxd 3. blogspot. com/2013/07/how-to-use-zenmap-in-kali-linux. html https: //www. youtube. com/watch? v=Tk. CSr 30 Uoj. M