Malware Analysis With Volatility Module 3 1 Dlllist

- Slides: 10

Malware Analysis With Volatility Module 3. 1

Dlllist plugin ● ● Considering that a malware can unlink, change the name, or substitute libraries of a system (Windows, for example), we are interested in investigating a malware infection in the libraries (dll). The initial task is the analysis of suspicious dlls because malware can be a hidden process. We can use the command vol. exe dlllist --profile=Win. XPSP 3 x 86 -f stuxnet. vmem Malware Analysis With Volatility Module 3. 2

Dlllist plugin -p flag ● The output shows us all dlls loaded by the process in the machine. Since this is difficult, our task is to investigate a specific process. We will use this command: ● vol. exe dlllist --profile=Win. XPSP 3 x 86 -p 1928 -f stuxnet. vmem ● And we can see the output for this specific process. We can obtain the same output using the command ● vol. exe dlllist --profile=Win. XPSP 3 x 86 -offset=0 x 01 e 47 c 00 -f stuxnet. vmem Malware Analysis With Volatility Module 3. 3

Malfind plugin ● ● Another Volatility plugin that we can use when we are searching for MZ signature is malfind. If you want to analyze each process, type this command: vol. exe malfind --profile=Win. XPSP 3 x 86 -f stuxnet. vmem | more Or, since we suspect a particular process, we can use this plugin with -p flag. vol. exe malfind --profile=Win. XPSP 3 x 86 -p 1928 -f stuxnet. vmem Malware Analysis With Volatility Module 3. 4

Handles plugin ● ● To see an object that is not signaled by a thread, we use the handles plugin that gives us the mutant/mutex (or mutual exclusion) object of a process. According to Microsoft: “to prevent two threads from writing to shared memory at the same time, each thread waits for ownership of a mutex object before executing the code that accesses the memory. After writing to the shared memory, the thread releases the mutex object. " vol. exe handles --profile=Win. XPSP 3 x 86 -t Mutant -p 1928 -s -f stuxnet. vmem Malware Analysis With Volatility Module 3. 5

Vaddump plugin (be careful!) ● ● To obtain VAD segments of process we use vaddump plugin (please take care). vol. exe vaddump --profile=Win. XPSP 3 x 86 -p 868 -D vad -f stuxnet. vmem In this example “vad” is my directory Malware Analysis With Volatility Module 3. 6

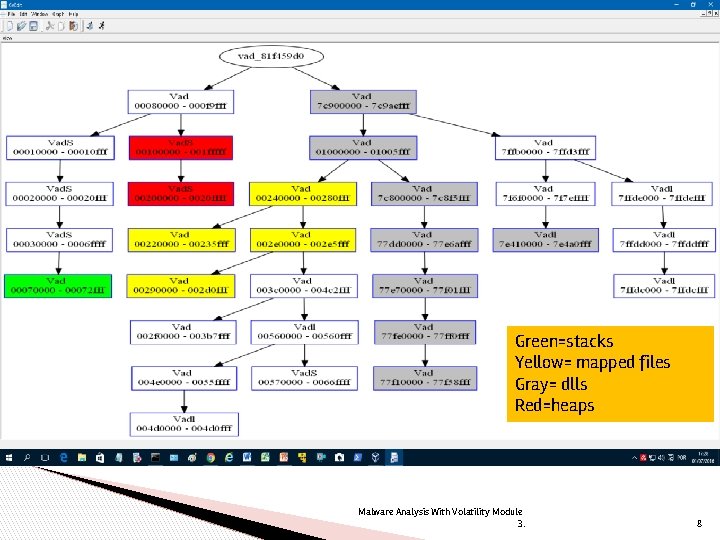
Vadtree plugin ● ● ● We can also extract in a graphic output: vol. exe vadtree --profile=Win. XPSP 3 x 86 --output=dot --outputfile=grapha. dot -p 868 -f stuxnet. vmem In the next slide, we see vadtree process 868 stuxnet malware. Malware Analysis With Volatility Module 3. 7

Green=stacks Yellow= mapped files Gray= dlls Red=heaps Malware Analysis With Volatility Module 3. 8

Vaddump (I recommend: use Linux!) ● ● In Kali Linux, vaddump can be used (if you set up an environment variable): volatility vaddump -p 1928 -D Malware Analysis With Volatility Module 3. 9

Procdump plugin (be careful!) ● ● I am working in Linux! First you should create a folder (that will receive the extract. exe files. In my example, I use my folder “forensics” to download these files). In Kali Linux, the command is: volatility procdump -p 680, 868, 1928 -D forensics Malware Analysis With Volatility Module 3. 10