Malware Spam Viruses Spyware Phishing Pharming Trojans Worms
























- Slides: 43

Malware: Spam, Viruses, Spyware, Phishing, Pharming, Trojans, Worms, Backdoors, and Zombie Computers © 2006 Consumer Jungle

Estimating the Threat of Malware • 1 -in-3 chance of suffering: – computer damage – financial loss • Viruses & Spyware © 2006 Consumer Jungle – $2. 6 Billion to Protect yet $9 Billion to Replace

Spam © 2006 Consumer Jungle

What is Spam? • An e-mail that is: – Unsolicited – Advertising something • Similar to: – Junk mail delivered in the mail – Telemarketing calls on the phone © 2006 Consumer Jungle

CAN SPAM Act of 2003 • Acronym stands for: – Controlling the Assault of Non. Solicited Pornography And Marketing • Allows spam as long as it contains: – an opt-out mechanism – a valid subject line and header (routing) information – the legitimate physical address of the mailer – a label if the content is for adults only • Regulated by the FTC, but has made little impact to curb Spam. © 2006 Consumer Jungle

Virus © 2006 Consumer Jungle

What is a Virus? • A program that can replicate itself and spreads itself by means of a transferable host. • How a virus spreads: – Removable Medium – Network Connection © 2006 Consumer Jungle

Why is it Called a Virus? • Similar to a biological virus that spreads itself into living cells. – Insertion of a virus is called an infection – Infected file is called a host. © 2006 Consumer Jungle

Virus Tricks: What to Look For © 2006 Consumer Jungle

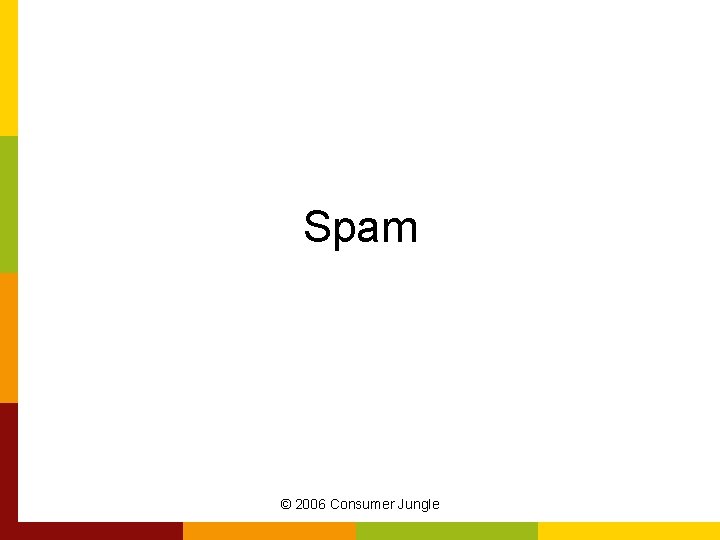
The Infected Document • Subject line includes the name of the sender – Probably someone you know • Message tempts you to open attachment • Attachment is a legitimate Word file that is infected with a macro © 2006 Consumer Jungle

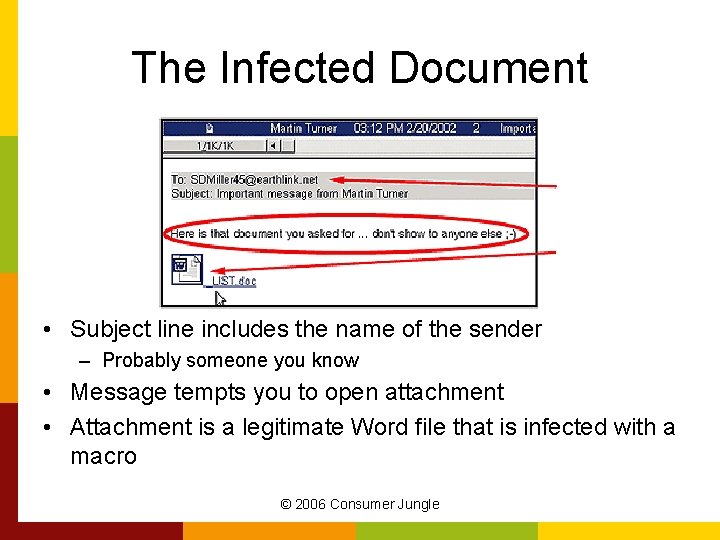
The Misleading File Name • Look at the attachment's name "LOVE-LETTER-FOR-YOU. TXT. vbs – Looks like a harmless text (TXT) file, but it is a vbs file with a windows script – The suffix (. vbs) might be completely hidden – appearing to be a type of file you’d willingly open i. e. JPEG, MP 3, or PDF. © 2006 Consumer Jungle

The Offer You Can’t Refuse • Gives a compelling message – get rid of a computer virus • Doesn’t disguise that the attachment is a program • The program is a worm that sends itself to e-mail addresses it finds on your computer © 2006 Consumer Jungle

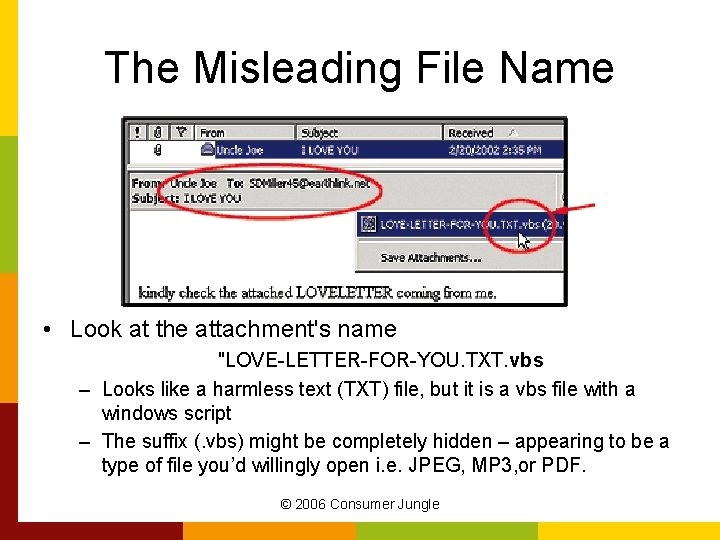
The Fake Web Link • Subject and message suggest that opening attachment will take you to a web page containing party photos. • Attachments name resembles a web address – Actually a program that sends itself to people in your address book • Designed to tie up your e-mail; can also be designed to destroy data © 2006 Consumer Jungle

Spyware © 2006 Consumer Jungle

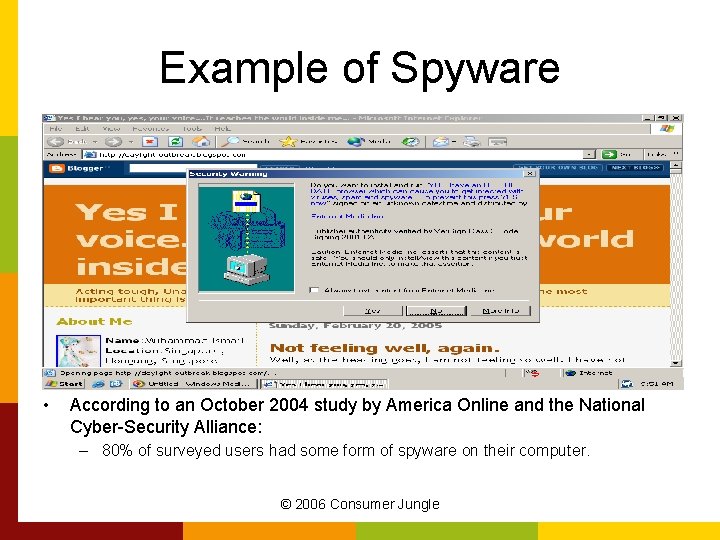
What is Spyware? • Malicious software that – Subverts the computer’s operation for the benefit of a third party • Designed to exploit infected computers for commercial gain via: – Unsolicited pop-up advertisements – Theft of personal information – Monitoring of web-browsing for marketing purposes – Re-routing of http requests to advertising sites © 2006 Consumer Jungle

Example of Spyware • According to an October 2004 study by America Online and the National Cyber-Security Alliance: – 80% of surveyed users had some form of spyware on their computer. © 2006 Consumer Jungle

Phishing © 2006 Consumer Jungle

What is Phishing? • An attempt to fraudulently acquire confidential information, such as: – passwords – credit card details • By masquerading as a trustworthy: – – – • Business Financial Institution Government Agency Internet Service Provider Online Payment Service Person In an apparently official electronic communication, such as: – an email – an instant message. © 2006 Consumer Jungle

Why is it called Phishing? • Hackers coined the phrase – “Fish” for accounts – Ph is a common hacker replacement for the letter “f”. © 2006 Consumer Jungle

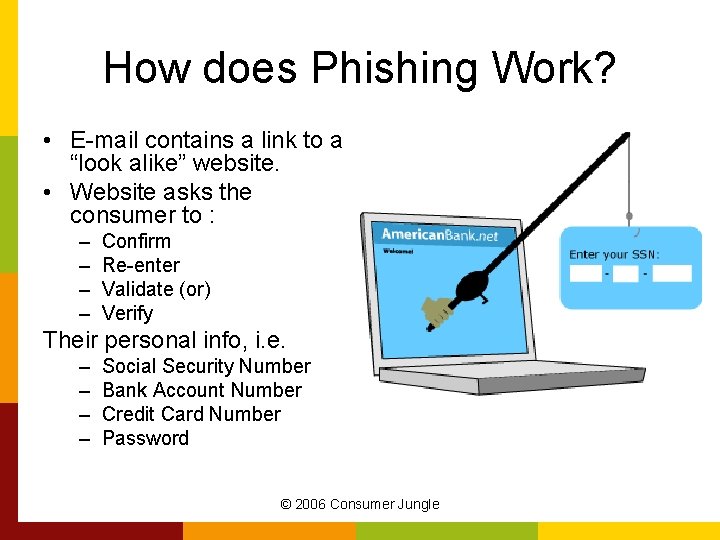
How does Phishing Work? • E-mail contains a link to a “look alike” website. • Website asks the consumer to : – – Confirm Re-enter Validate (or) Verify Their personal info, i. e. – – Social Security Number Bank Account Number Credit Card Number Password © 2006 Consumer Jungle

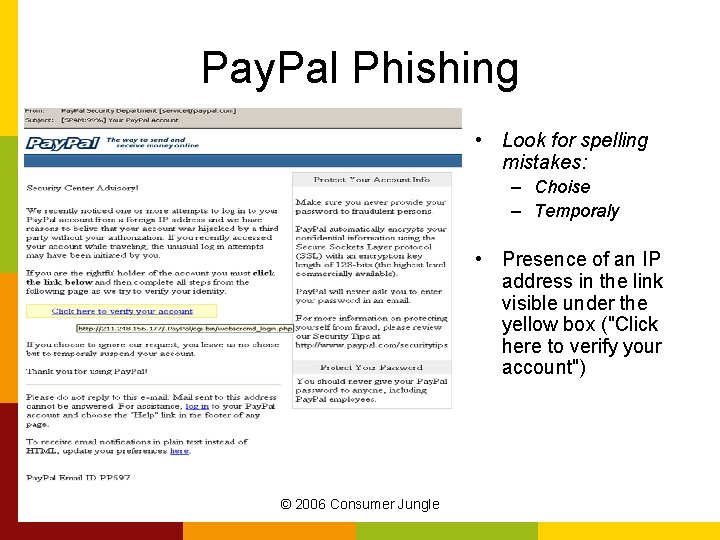
Pay. Pal Phishing • Look for spelling mistakes: – Choise – Temporaly • Presence of an IP address in the link visible under the yellow box ("Click here to verify your account") © 2006 Consumer Jungle

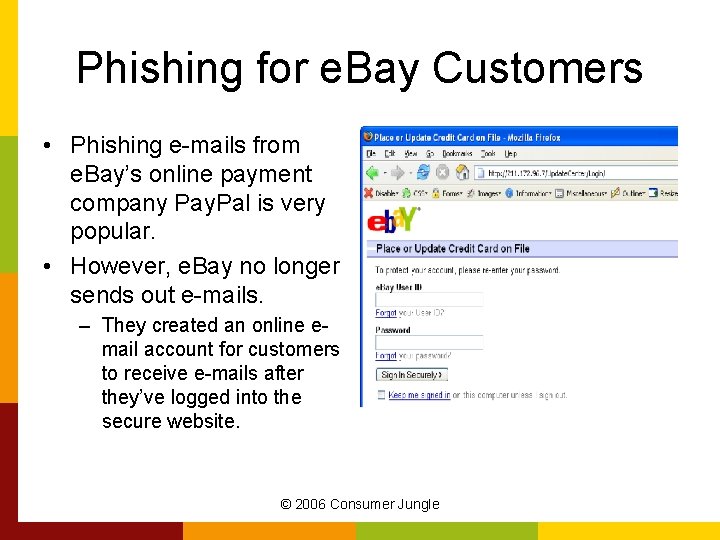
Phishing for e. Bay Customers • Phishing e-mails from e. Bay’s online payment company Pay. Pal is very popular. • However, e. Bay no longer sends out e-mails. – They created an online email account for customers to receive e-mails after they’ve logged into the secure website. © 2006 Consumer Jungle

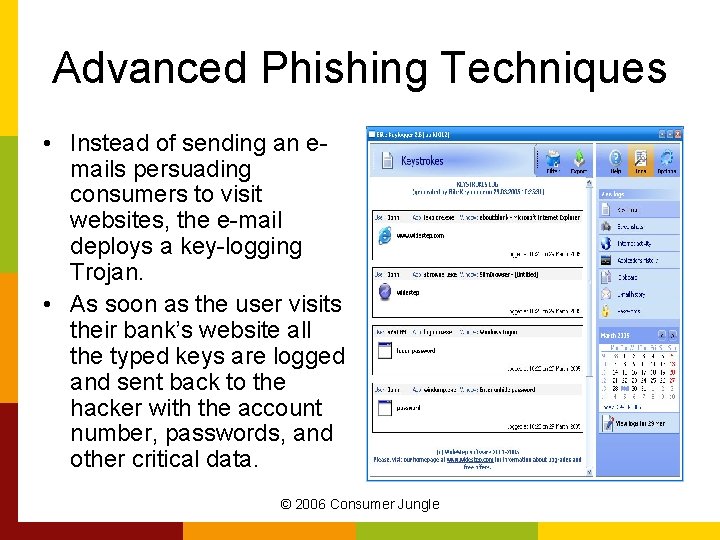
Advanced Phishing Techniques • Instead of sending an emails persuading consumers to visit websites, the e-mail deploys a key-logging Trojan. • As soon as the user visits their bank’s website all the typed keys are logged and sent back to the hacker with the account number, passwords, and other critical data. © 2006 Consumer Jungle

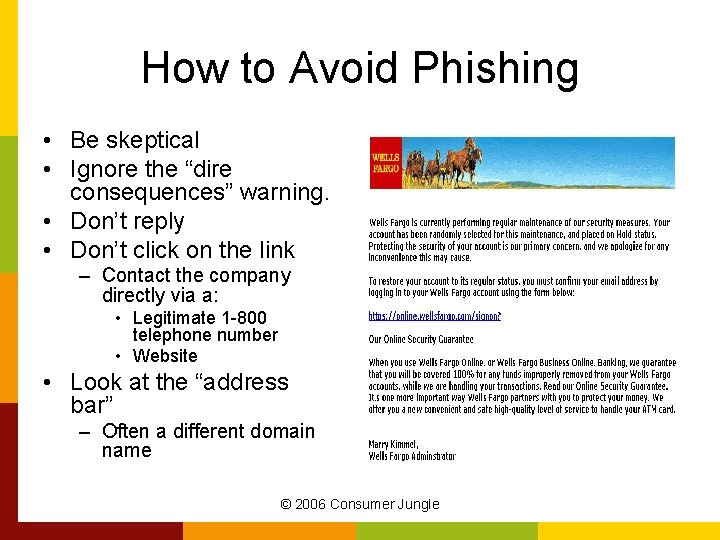
How to Avoid Phishing • Be skeptical • Ignore the “dire consequences” warning. • Don’t reply • Don’t click on the link – Contact the company directly via a: • Legitimate 1 -800 telephone number • Website • Look at the “address bar” – Often a different domain name © 2006 Consumer Jungle

More Tips on Avoiding Phishing • Don’t e-mail personal or financial information. • Open a new browser and look for secure indicators: – Secure lock – https: (s stands for secure) © 2006 Consumer Jungle

What to do with Phishing E-mails • Forward to spam@uce. gov and cc the group that the e-mail impersonates. • Mark as “Junk Mail” in your Spam Software • Delete immediately • File a complaint with the Federal Trade Commission (FTC) – www. ftc. gov – 1 -877 -FTC-HELP (1 -877 -382 -4357) © 2006 Consumer Jungle

Pharming © 2006 Consumer Jungle

What is Pharming? • Exploitation of a vulnerability in the hosts’ file or DNS server software that allows a hacker to: – Acquire the domain name for a site – Redirect that website’s traffic to another website • For gaining access to usernames, passwords, etc. © 2006 Consumer Jungle

Pharming Techniques • The criminal uses a virus or Trojan to modify a user’s ‘Hosts’ file. – OR • The criminal sends out a spam for www. phishsite. com, and the message links to an illegitimate site. – AND • When the user opens the browser and enters the website address, they get sent to the phishing site instead. © 2006 Consumer Jungle

Trojans © 2006 Consumer Jungle

What is a Trojan? • A malicious program that is disguised as a legitimate program. • Usually has a useful function that camouflages undesired functions. • Can not replicate or spread itself. © 2006 Consumer Jungle

Why is it Called a Trojan? • Derived from myth. – Greeks left large wooden horse outside the city of Troy. – Trojans thought it was a gift and moved the horse inside the city wall. – The horse was hollow and filled with Greek soldiers. – Greek soldiers opened the city gates at night for the remaining army to attack. • Application: Greeks gained malicious access to the city of Troy just like a Trojan program gains malicious access to your computer. © 2006 Consumer Jungle

Example of a Trojan • Program posted on a website: – Called FREEMP 3. EXE – Promise “free mp 3 files” • Instead, when run: – Erases all the files on your computer – Displays a taunting message © 2006 Consumer Jungle

What Can a Trojan Do? • • Erase or overwrite data on a computer Corrupt files in a subtle way Spread other malware, such as viruses. In this case the Trojan horse is called a 'dropper'. Set up networks of zombie computers in order to launch “Denial of Service” attacks or send out spam. Spy on the user of a computer and covertly reports data like browsing habits to other people. Log keystrokes to steal information such as passwords and credit card numbers. Phish for bank or other account details. © 2006 Consumer Jungle Install a backdoor on a computer system.

Where Do Trojans Come From? • Infected Programs • Websites • Email • Direct Connection to the Internet © 2006 Consumer Jungle

Worms © 2006 Consumer Jungle

What is a Worm? • Computer program – self-replicating – self-contained • Designed to exploit: the file transmission capabilities on your computer © 2006 Consumer Jungle

Why is it Called a Worm? • Word taken from a 1970’s science fiction novel: – The Shockwave Rider • By John Brunner • Researchers found that their selfreplicating program was similar to the worm program described in the book. © 2006 Consumer Jungle

What Can a Worm Do? • Delete files on a host system • Send documents via e -mail • Create excessive network traffic • Install a backdoor © 2006 Consumer Jungle

What is a Backdoor? • Method of remaining hidden on a computer while: – bypassing normal authentication – Securing remote access to a computer • Can be installed by a worm © 2006 Consumer Jungle

What is a Zombie Computer? • Computer attached to the internet that: – Is under remote direction of an illegitimate user • Check your computer – www. ordb. org © 2006 Consumer Jungle

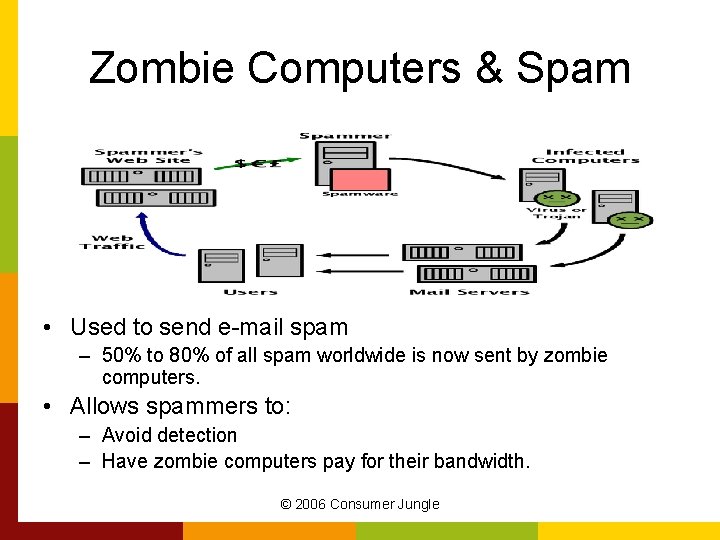
Zombie Computers & Spam • Used to send e-mail spam – 50% to 80% of all spam worldwide is now sent by zombie computers. • Allows spammers to: – Avoid detection – Have zombie computers pay for their bandwidth. © 2006 Consumer Jungle

Suspicion = Prevention • Best prevention is awareness • Be suspicious of everything to avoid: – – – – Spam Viruses Spyware Phishing Pharming Trojans Worms Backdoors © 2006 Consumer Jungle