ICT Crime Data theft phishing pharming Data losstheft
















- Slides: 23

ICT & Crime Data theft, phishing & pharming

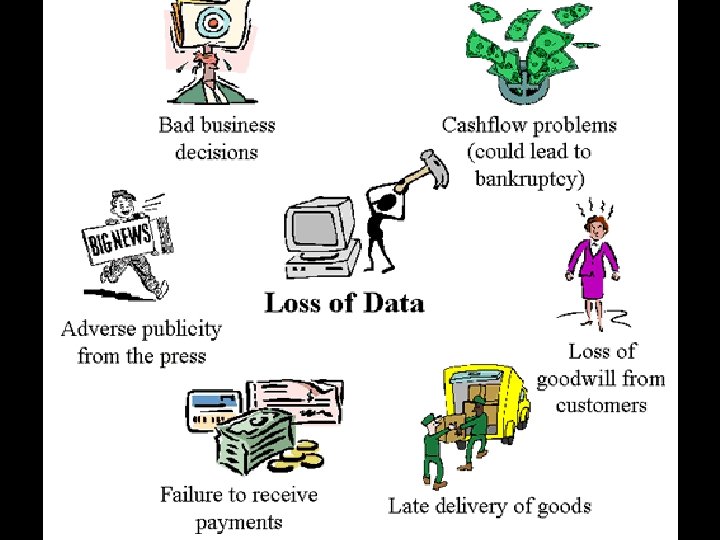
Data loss/theft Data is often the most valuable commodity any business has. The cost of creating data again from scratch can far outweigh the cost of any hardware or programs lost. Loss of data can have serious consequences for a business. Data can be stolen either by: • physical theft of hardware • or through unauthorised access to the system e. g. hacking.

Activity 1 (10 minutes) With your partner, think of as many ways as you can in which this could affect your business. How do you think you could have prevented this from happening?


Introduction Computer crime is defined as 'criminal activity directly related to the use of computers'. Data theft can be even more serious than theft of money. There a number of ways in which data can be stolen, specifically: – – Physical theft of equipment Hacking Phishing Pharming

Physical theft of equipment Businesses can use a range of physical methods to protect their systems and data. Some of these include: • Keeping important computers such as servers or mainframes in locked rooms • Posting security guards • Security locks, smart cards • Keeping sensitive data on stand-alone machines instead of networks • Using alarm systems and video cameras

Hackers & hacking What is a hacker? A hacker is a person who breaks codes and passwords to gain unauthorised entry to computer systems. Who is at risk? Computers which form part of networks or those with external links, such as attached modems, are in danger from hackers. Stand-alone computers are usually safe as there is no connection for the hackers to break into.

Why do hackers hack? • curiosity • challenge - can they get through the system’s defences ? • to access data, usually because the data has value • to steal financial information such as your credit card number, or the password to your bank account, in order to use that information to make purchases.

Protect yourself against hackers • Use strong passwords to protect your user login account • Never reveal your login password to anyone else • Place a firewall between your computer and any network • Disconnect from networks (eg the internet) when you are not using them • Encrypt any sensitive information (just in case they get in(

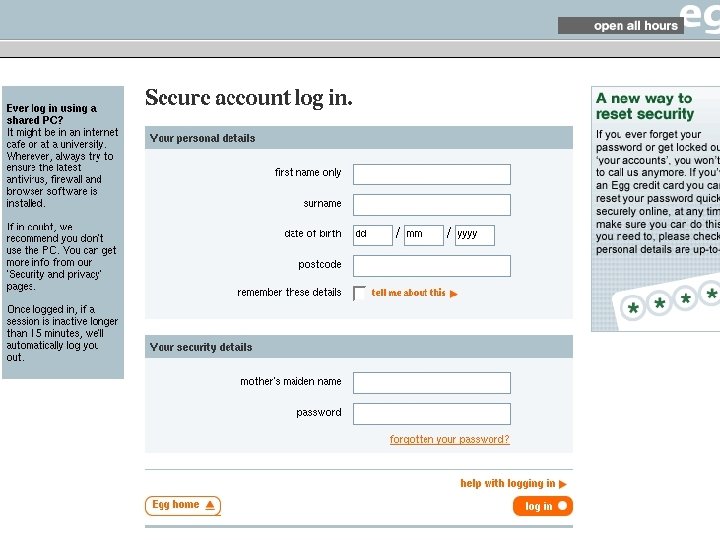
Phishing • This is where a user is tricked into entering their user name & password to a fake website. • The website looks like their bank/ebay/paypal website, but belongs to a hacker. • Watch this movie: Phishing scams in Plain English

What is phishing? • Phishing is a form of identity theft, where fraudsters steal your identity and personal information to gain access to your accounts or commit other crimes using your persona. • In brief, a 'phishing' email is one that pretends to be from a company or bank like e. Bay, Pay. Pal, your bank etc • It usually asks you to enter your account data, such as login details. • These scams are often supported by fake spoof websites, and victims are tricked into thinking they are logging to a real website.



Other scams: • http//: www. aboutpaypal. org/ebay_phishing _email • This uses some quite threatening language to persuade users to follow the link.

Other methods can be less threatening:


Phishing: Protecting yourself • If you receive a suspicious email, check websites such as http//: www. millersmiles. co. uk/ • http//: www. millersmiles. co. uk/articles. php

Pharming What is it? "Pharming "is the term for when criminal hackers redirect Internet traffic from one Web site to a different, identical-looking site in order to trick you into entering your user name and password into the database on their fake site. Why do they do it? Criminals try to acquire your personal information in order to access your bank account, steal your identity, or commit other kinds of fraud in your name, so banking and similar financial sites are often the targets of these attacks.

Pharming vs Phishing Pharming might sound similar to e-mail phishing scams, but pharming is more insidious, because you can be redirected to a false site without any participation or knowledge on your part.

How does pharming work? • A hacker attacks a DNS server • The hacker redirects traffic from the real website to his own fraudulent site • The user types in the web address of the real site • They are instead taken to the fake site – usually a bank or other ecommerce site.


• Pharming is a highly sophisticated extension of phishing that can direct you to fake websites that look identical to the real ones, and then steal your identity, infest your computer with annoying adware, and attack your computer with damaging viruses.

Activity • Make a presentation how anti-Virus and other protection software help to protect the user from security risks.