Live Forensics Investigations Computer Forensics 2013 Live Investigations















- Slides: 65

Live Forensics Investigations Computer Forensics 2013

Live Investigations � Necessary � computer � E. g. : � nature � E. g. : � cost because cannot be shut down important server of evidence is too volatile Malware investigations consideration � remote forensics

Live Investigations � Special challenges: � Interaction with life system changes the status of the life system � Consequence: Need to document carefully what is being done Use scripts Use automated gathering tools � System can be root-kitted � Interaction with system is not usually at the lowest level possible

Live Investigations � Became � Always � If normal only recently seemed better to work directly with hard drive necessary construct a clone of the life system � Tools for capturing volatile evidence have increases

Live Investigation � Need to be preplanned � Bring all the tools, do not interrupt evidence gathering, document every step

Remote gathering of data � Possible � Allows to install forensics module routine investigations via network connection � Installs a trusted agent on each potential target machine � Agent communicates via a secure connection � Once triggered, agent collects data and sends them through a one-way connection to a collector

Remote gathering of data � Forensics Agent � Forensically sound data collection � Fully configurable � Best practice � Cross-platform � Can be used stand-alone or remotely

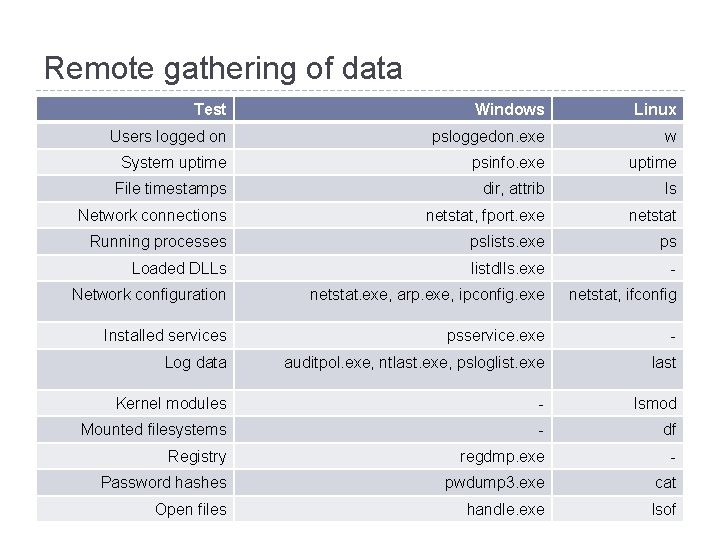
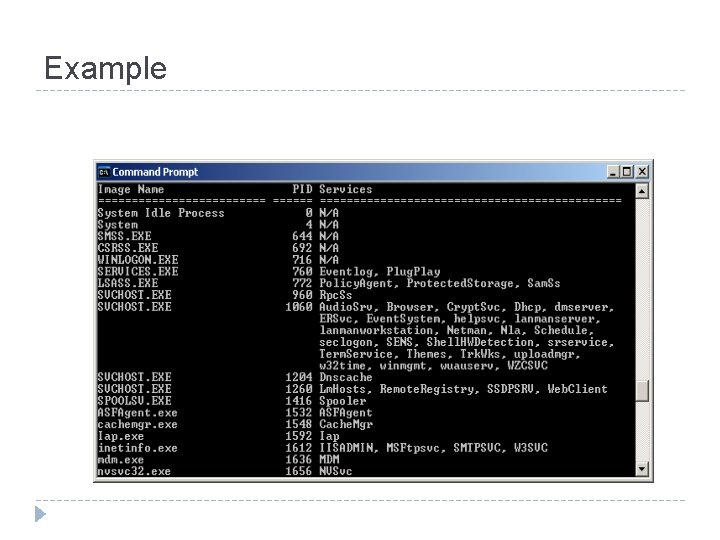
Remote gathering of data Test Windows Linux Users logged on psloggedon. exe w System uptime psinfo. exe uptime File timestamps dir, attrib ls Network connections netstat, fport. exe netstat Running processes pslists. exe ps Loaded DLLs listdlls. exe - Network configuration netstat. exe, arp. exe, ipconfig. exe netstat, ifconfig Installed services psservice. exe - Log data auditpol. exe, ntlast. exe, psloglist. exe last Kernel modules - lsmod Mounted filesystems - df Registry regdmp. exe - Password hashes pwdump 3. exe cat Open files handle. exe lsof

Remote gathering of data � Application � Browser � Memory specific data history, skype chat logs, . . . capture

Remote gathering of data � Various providers � Encase, Access data, F-response, . . .

Live Forensics � Usually use a toolkit � User-level � No rootkits influence since you are using your own tools � System-level rootkits � Norm among rootkits � Do usually not lie consistently: Use several ways / tools to ask the same question Automatically look for inconsistencies � Anti-rootkit-defense � Run various antivirus tools

Preparing the Toolkit

Preparing the Toolkit �Label the toolkit. �Check for dependencies with Filemon or List. DLL. � Lots of dependencies lots of MAC changes. � Lots of dependencies easy to run into a trojaned utility �Create an MD 5 of the toolkit. �Write protect any floppies.

Using the Toolkit

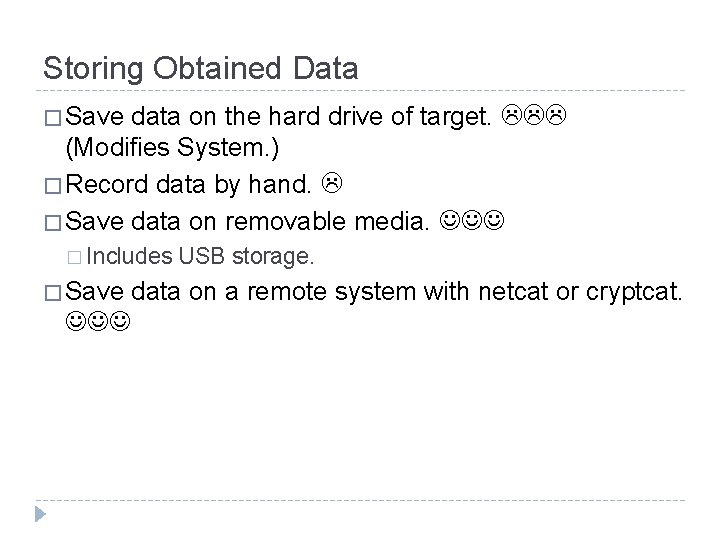
Storing Obtained Data � Save data on the hard drive of target. (Modifies System. ) � Record data by hand. � Save data on removable media. � Includes � Save USB storage. data on a remote system with netcat or cryptcat.

Storing Obtained Data with netcat � Quick on, quick off target system. � Allows offline review. � Establish a netcat listener on the forensic workstation. Redirect into a file. � Establish a netcat funneler on the target system to the forensic workstation. � Cryptcat does the same, but protects against sniffing.

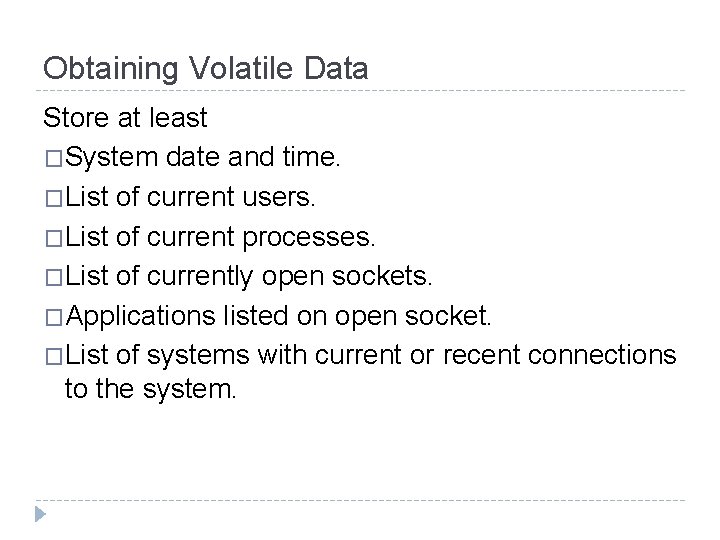
Obtaining Volatile Data Store at least �System date and time. �List of current users. �List of current processes. �List of currently open sockets. �Applications listed on open socket. �List of systems with current or recent connections to the system.

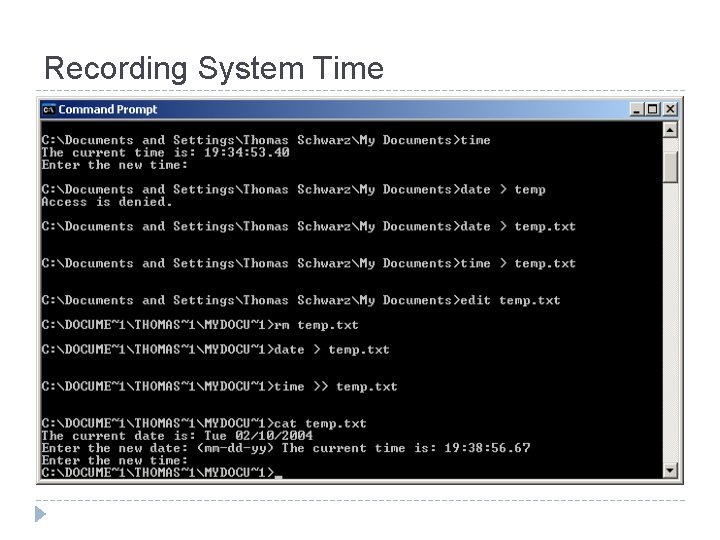
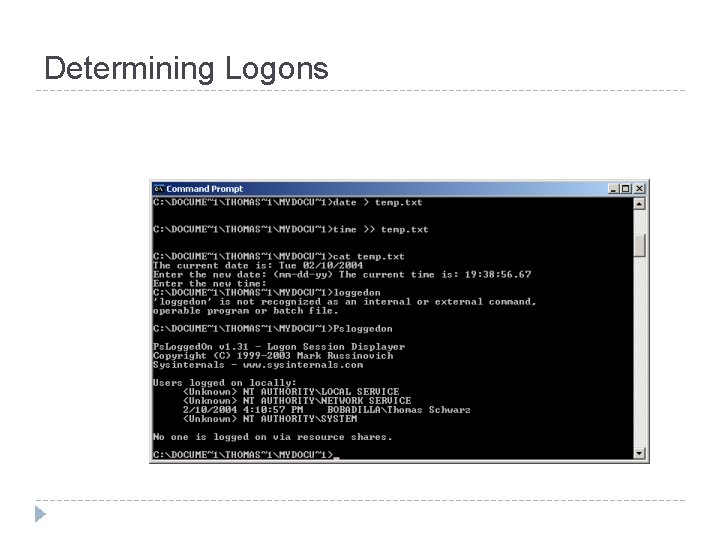
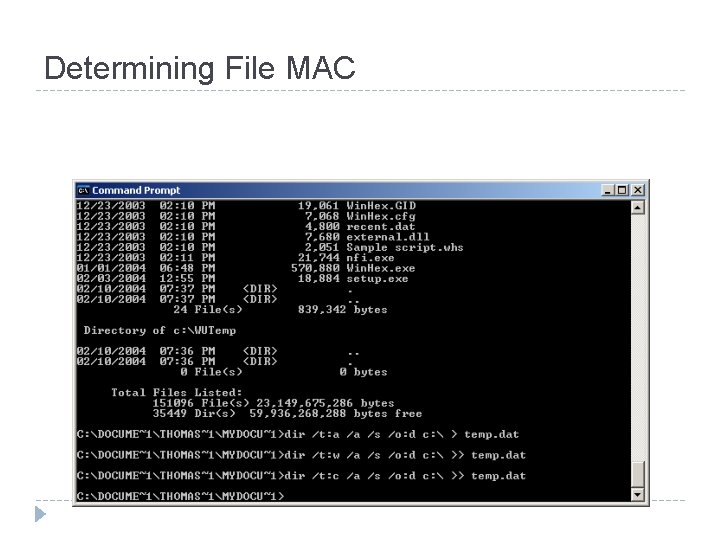
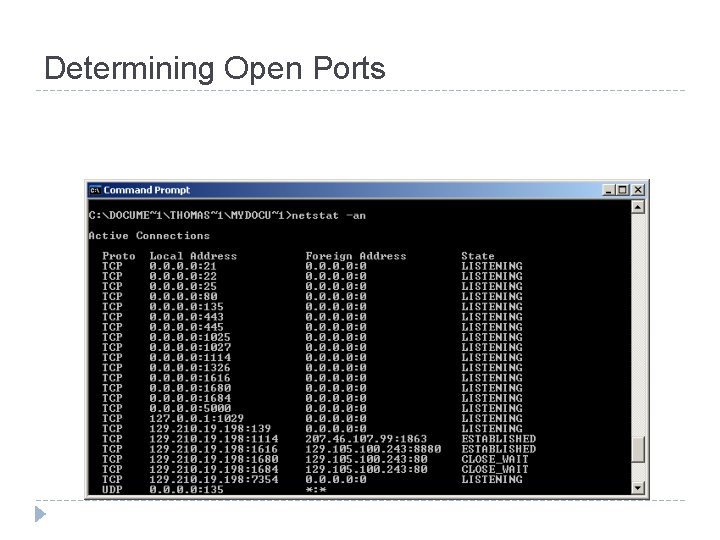
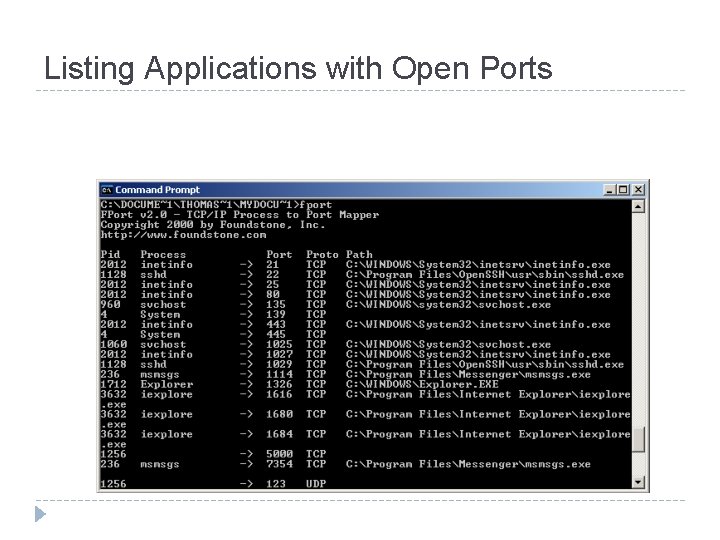
Obtaining Volatile Data: Procedure � � � Execute a trusted cmd. exe Record system time and date. Determine who is logged on. Record file MAC. Determine open ports. List all apps associated with open ports.

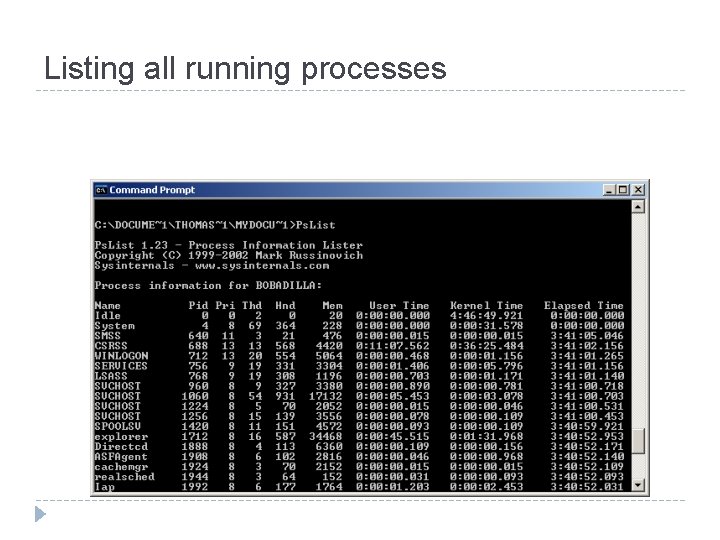
Obtaining Volatile Data: Procedure � � List all running processes. List current and recent connections. Record the system time and date. Document the commands used during initial response.

Recording System Time

Determining Logons

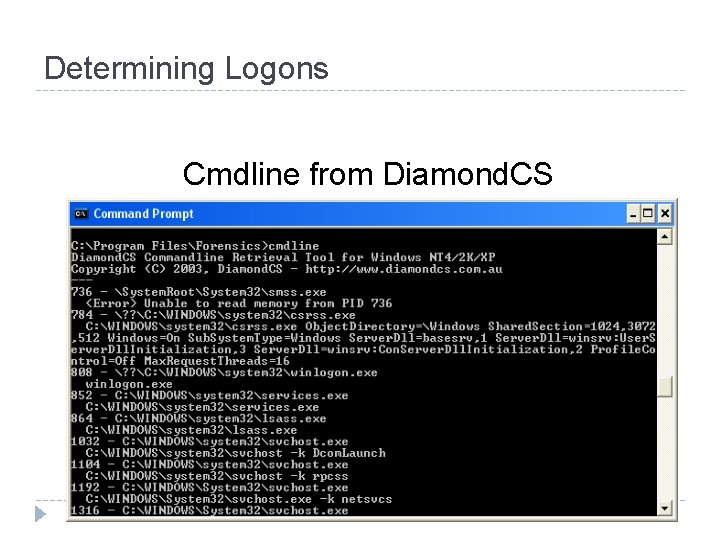
Determining Logons Cmdline from Diamond. CS

Determining File MAC

Determining Open Ports

Listing Applications with Open Ports

Listing all running processes

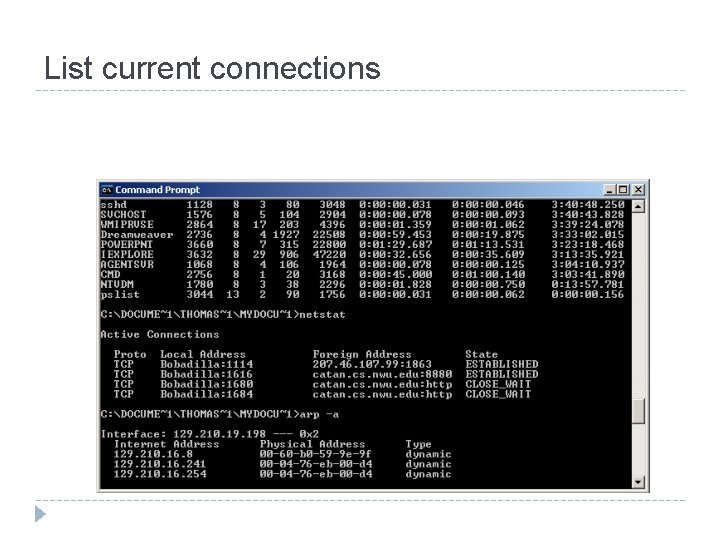
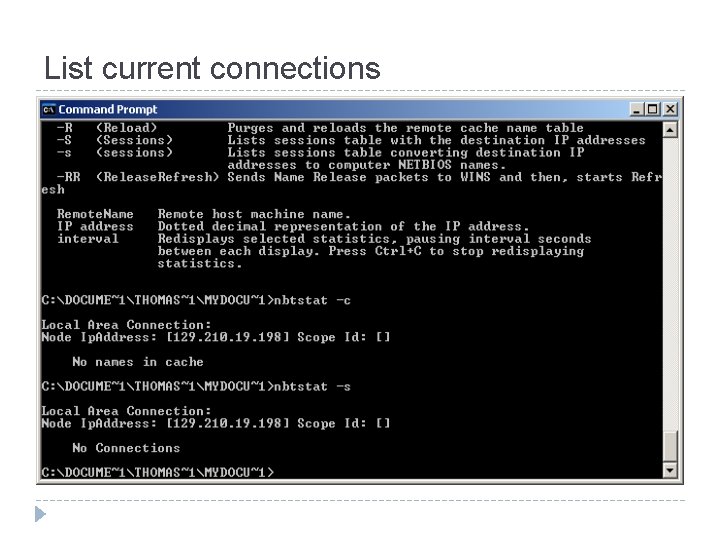
List current connections

List current connections

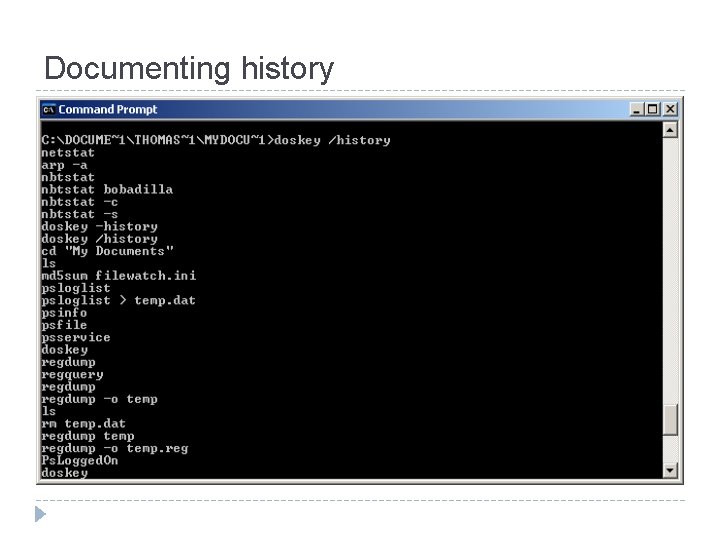
Documenting history

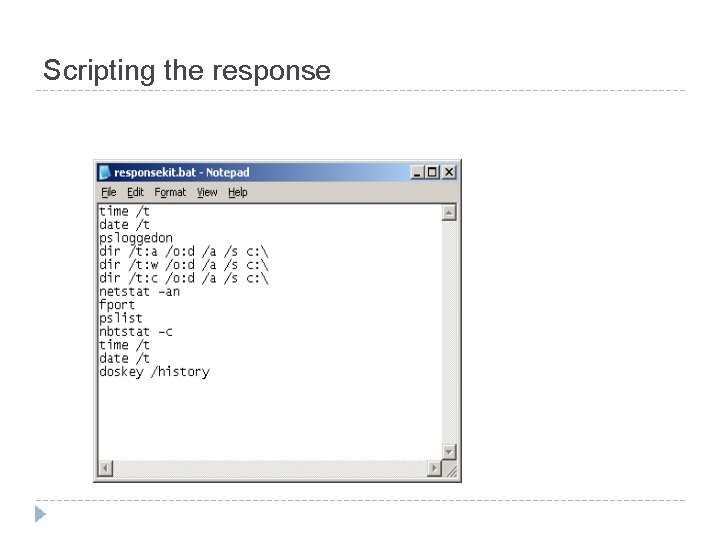
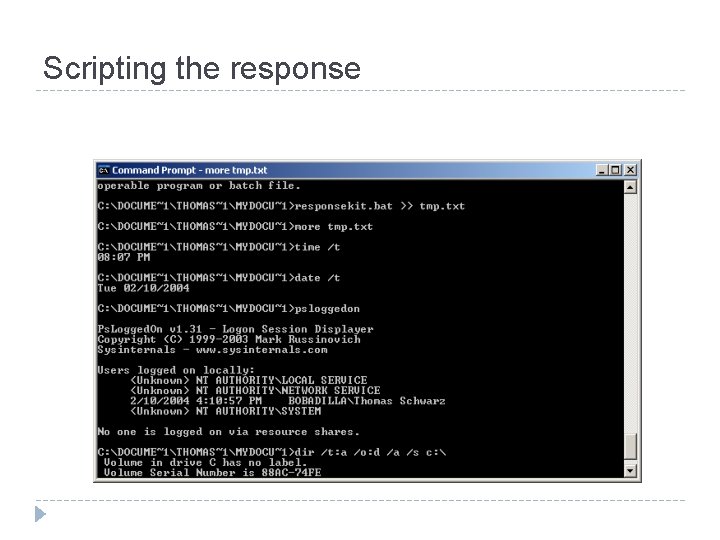
Scripting the response

Scripting the response

Examples �Use Fport to look at open ports. �Use a list of ports to find suspicious ports, i. e. those used by known Trojans, sniffers or spyware. www. doshelp. com/trojanports. htm

Examples �If at your home system, fport shows a suspicious port use and netstat shows a current connection to this port, then kill the process.

Examples � Knowing what processes are running does not do you any good. � You need to know what they are doing. � At least, know the typical processes.

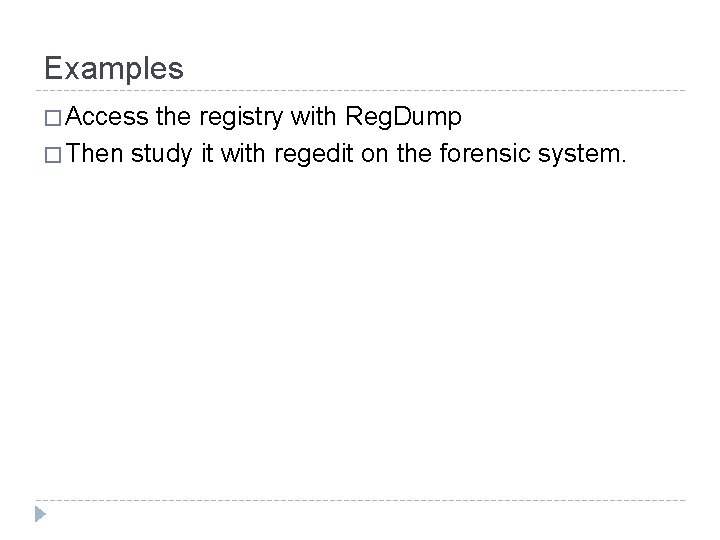
Examples � Access the registry with Reg. Dump � Then study it with regedit on the forensic system.

Examples Assume generic monitoring of systems. Look for � Unusual resource utilization or process behavior. � Missing processes. � Added processes. � Processes with unusual user identification.

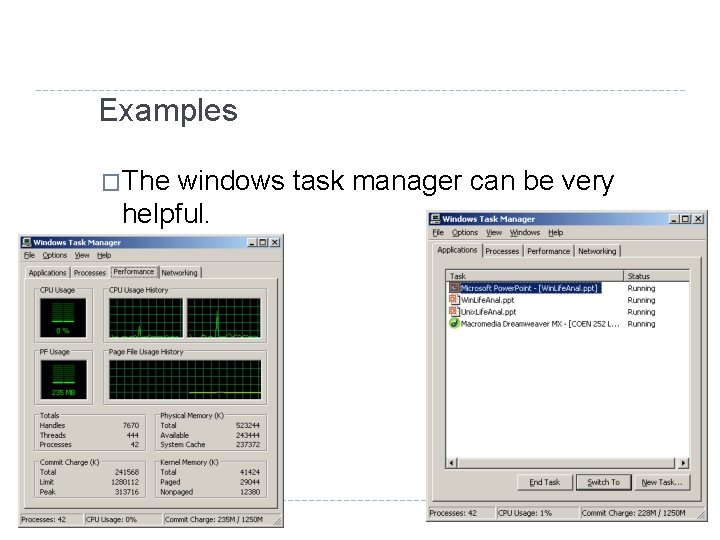
Examples �The windows task manager can be very helpful.

Examples: Detecting and Deleting Trojans � Use port scanning tools, either on host machine or remote machine. � Fport (Windows) � Superscan (Windows) � Nmap � netstat (for open connections)

Examples: Detecting and Deleting Trojans � Identify the Trojan on the disk. � Find out how it is being initiated and prevent the process. � Reboot the machine and delete the Trojan.

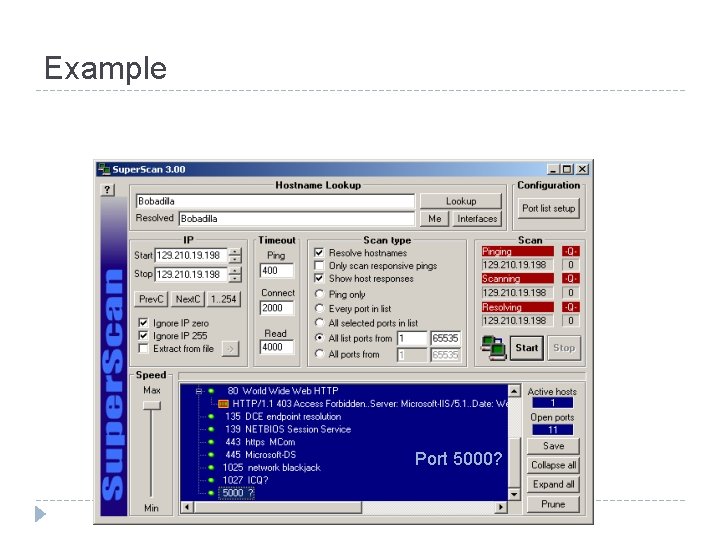
Example � Run superscan on local host to check for open ports. � What is happening at port 5000?

Example Port 5000?

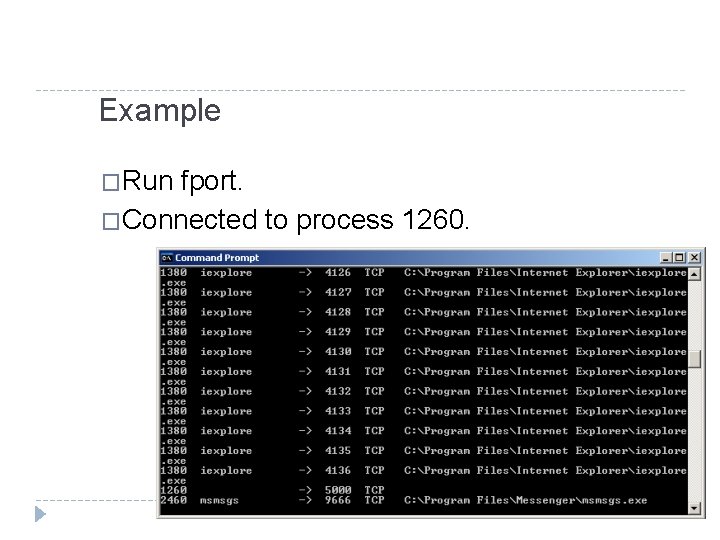
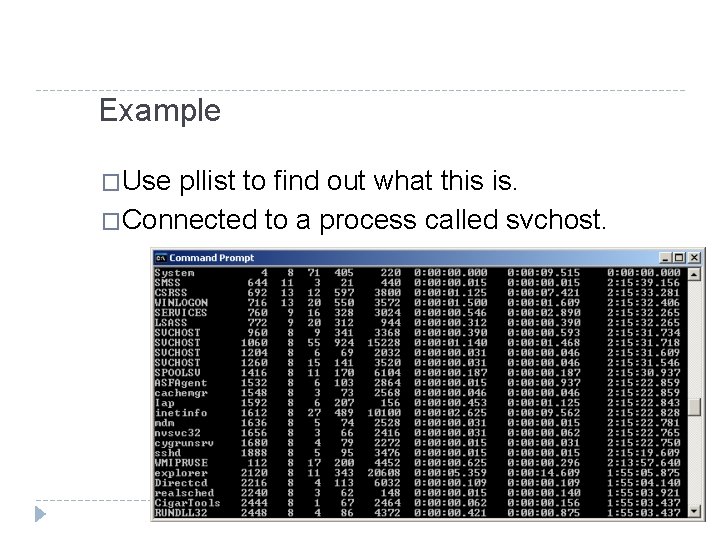
Example �Run fport. �Connected to process 1260.

Example �Use pllist to find out what this is. �Connected to a process called svchost.

Example � Do an internet search on svchost. � Process checks the service portion of the registry to start services that need to run. � Use Tasklist /SVC in a command prompt

Example

Example � Nothing serious here. � At least not on the surface.

Malware investigations � Run malware in a virtual machine � Problem: machine � Run Malware can detect it is running in a virtual malware on a life system � Dangerous � Can � Try for the environment limit network connectivity to observe malware effects � Live system: Need to run monitoring tools � Use � Do E. g. regmon, filemon Can be detected by malware differential analysis system analysis on images taken before and after infection

Malware investigations � Can simulate the internet with inetsim

Malware investigations � Physical � targets Malware runs in native habitat � Without � hypervisors, emulators, . . . Example: TRUMAN – The reusable unknown malware analysis net � Two physical computers Windows machine for malware client Linux machine for supervisor Makes dd-images after executing samples, . . . Simulates internet services such as SMTP, FTP, IRC � Provides Memory analysis with volatility Registry analysis with regdiff. pl, dumphive, Reg. Ripper Packer identification Network traffic analysis NTFS ADS streams Hashes of system files

Malware investigations � Physical � Deep target Freeze: � Prevents permanent changes to computer � FOG � Cloning and imaging software

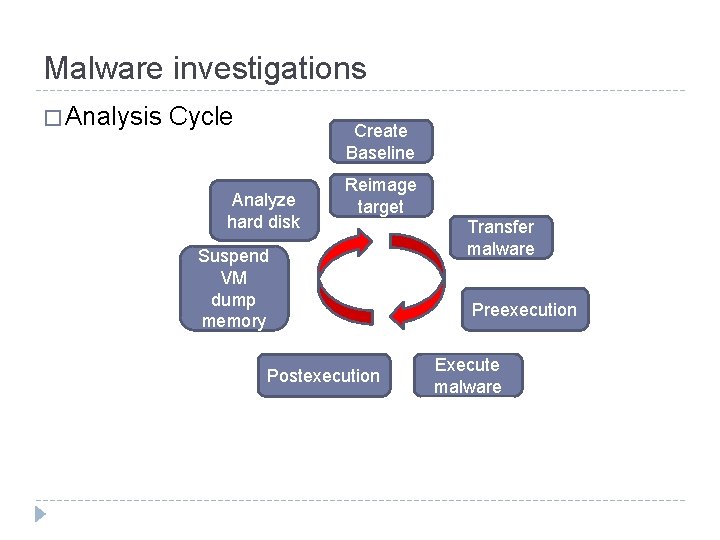
Malware investigations � Analysis Cycle Create Baseline Analyze hard disk Reimage target Suspend VM dump memory Postexecution Transfer malware Preexecution Execute malware

Malware investigations

Malware investigations

Malware investigations

Malware investigations

Malware investigations

Malware investigations

Malware investigations

Malware investigations

Malware investigations

Malware investigations

Malware investigations

Malware investigations

Malware investigations

Malware investigations
 Guide to computer forensics and investigations 6th edition
Guide to computer forensics and investigations 6th edition Guide to computer forensics and investigations 5th edition
Guide to computer forensics and investigations 5th edition Tasks performed by computer forensics tools
Tasks performed by computer forensics tools Digital forensic report template
Digital forensic report template Computer forensics denver
Computer forensics denver Computer forensics workstation
Computer forensics workstation Objectives of computer forensics
Objectives of computer forensics Computer crime
Computer crime Computer forensics tool testing
Computer forensics tool testing Tasks performed by computer forensics tools
Tasks performed by computer forensics tools Dr qaira anum
Dr qaira anum Advanced computer forensics
Advanced computer forensics Fastbloc
Fastbloc Why aren t descriptive investigations repeatable
Why aren t descriptive investigations repeatable Year 6 maths investigations
Year 6 maths investigations Craigslist wayne
Craigslist wayne Unit 3 statistical studies answers
Unit 3 statistical studies answers Statistical investigations examples
Statistical investigations examples Forensic science fundamentals and investigations chapter 6
Forensic science fundamentals and investigations chapter 6 Heatherdowns bmv
Heatherdowns bmv What is the step in scientific method
What is the step in scientific method Child protective investigations pasco county
Child protective investigations pasco county Chs investigations
Chs investigations Right iliac fossa mass investigations
Right iliac fossa mass investigations Verifact investigations
Verifact investigations 3 weeks pregnant ultrasound
3 weeks pregnant ultrasound Investigations
Investigations Chs investigations
Chs investigations Quizlet ,live
Quizlet ,live Live healthy be happy
Live healthy be happy Difference between a computer and computer system
Difference between a computer and computer system Difference between a computer and computer system
Difference between a computer and computer system Keyboard mouse scanner and microphone are blank devices
Keyboard mouse scanner and microphone are blank devices Basic structure of a computer
Basic structure of a computer Computer architecture and computer organization difference
Computer architecture and computer organization difference Basic computer design
Basic computer design Register in computer organization
Register in computer organization Kse 2013 ehdot
Kse 2013 ehdot Contoh cover dokumen 1 kurikulum 2013
Contoh cover dokumen 1 kurikulum 2013 Ms access 2013 tutorial
Ms access 2013 tutorial Quran in word 2013
Quran in word 2013 Brs 2013
Brs 2013 Apes frq 2013
Apes frq 2013 Iso 690:2013
Iso 690:2013 Dpr 80/2013 sintesi
Dpr 80/2013 sintesi Siakad2013
Siakad2013 Rpp bahasa indonesia kelas 1 membaca permulaan
Rpp bahasa indonesia kelas 1 membaca permulaan Fiscal incentives for industrial promotion (revised)-2013
Fiscal incentives for industrial promotion (revised)-2013 Pmi 2013
Pmi 2013 Perdagangan spm
Perdagangan spm Plan nacional del buen vivir 2009 al 2013
Plan nacional del buen vivir 2009 al 2013 Ilc 2013
Ilc 2013 Cakupan penilaian
Cakupan penilaian 7/10/2010
7/10/2010 Owasp top 10 2013
Owasp top 10 2013 Condição de existência dos triângulos
Condição de existência dos triângulos Organigramme du ministère de la santé du mali
Organigramme du ministère de la santé du mali Mendeley literaturverzeichnis erstellen
Mendeley literaturverzeichnis erstellen Lync 2013 features
Lync 2013 features C.m. n. 8 del 6 marzo 2013 sintesi
C.m. n. 8 del 6 marzo 2013 sintesi Ley 1620 de 2013 doc
Ley 1620 de 2013 doc Dpr 80 2013 sintesi
Dpr 80 2013 sintesi Dpr 80 2013 fasi
Dpr 80 2013 fasi Ipk abad 21
Ipk abad 21 Kajian pasaran perolehan
Kajian pasaran perolehan Inpc 2013
Inpc 2013