Forensics An Introduction to Computer Forensics Copyright 2019
























- Slides: 25

Forensics An Introduction to Computer Forensics Copyright © 2019 - Curt Hill

Forensic Definitions • Scientific tests or techniques used in connection with the detection of crime • The process of using scientific knowledge for collecting, analyzing, and presenting evidence to the courts • Pertaining to, connected with, or used in courts of law or public discussion and debate Copyright © 2019 - Curt Hill

What is it? • Forensics deals primarily with the recovery and analysis of latent evidence • In our case it usually is after a breach or the injection of malware • We are looking for several things: – The perpetrator(s) – The means of entry or attack – The items that were damaged, stolen or exposed – Residual malware Copyright © 2019 - Curt Hill

Why do we care? • Will help with the prosecution of the perpetrator • Will help the survivability of the system • Avoid the destruction of evidence • There are liabilities for not protecting data that is regulated – Civil and criminal Copyright © 2019 - Curt Hill

Attention to Detail • In general, forensics deal with gathering and presenting evidence in court – We will consider some of the legal requirements later • The study of computer forensics is valuable even if the evidence will never see a court of law – Preservation of the evidence helps to make the system more secure Copyright © 2019 - Curt Hill

What to look for? • Considerable variance in the crimes that are committed – In a child pornography we are looking for images/videos or evidence of their existence as well as the source – In data loss we are looking for damaged files and the malware that did this • Two basic forms of data – Persistent – Volatile Copyright © 2019 - Curt Hill

Persistent data • This is data that may survive a power loss • Usually located on a disk drive or other storage • We must be careful to not change this data in our investigation • Forensics workers need to know the tools to examine Copyright © 2019 - Curt Hill

Volatile • This is the data in memory, or being transmitted through the network – May be in a registry, a cache, RAM • This can only be accessed while the computer/network has remained powered up since the attack • The forensic technician needs a different set of tools to find items in the running computer Copyright © 2019 - Curt Hill

Process • There are many different processes that have been proposed – Most are specific to a particular environment such as incident response of law enforcement • What they largely have in common is three basic steps: – Acquisition – Analysis – Report Copyright © 2019 - Curt Hill

Acquisition • The concern that must be addressed is that an exact copy is obtained • This must be subject to examination without change that could obscure evidence • For storage devices the first thing is to make a sector by sector copy onto another device that may be write protected – Verify this with hash functions • Original is stored for later comparison Copyright © 2019 - Curt Hill

Drive Duplicators • There a number of such duplicators – En. Case, Forensic Toolkit (FTK) Imager, DCFLdd, IXimager, Guymager, True. Back or FDAS • Imaging software may also be used – For example the software VCSU uses to image laptops Copyright © 2019 - Curt Hill

Volatile data • If the machine is running memory may have valuable data that cannot be preserved if the machine is shut down • Two live analysis tools – Computer Online Forensic Evidence Extractor (COFEE) contains tools for password decryption, internet history display and snapshots of memory – Windows. SCOPE shows processes, DLLs, drivers, open network sockets, file handles and registry key handles Copyright © 2019 - Curt Hill

Analysis • Systematic search of data relevant to the suspected crime • This looks at existent and deleted files that may be relevant – Relevance depends on the crime – Files may include emails, browser histories or images – Recovering deleted files is seen next • There are tools for examining these • The data is then used to attempt to reconstruct what actually happened Copyright © 2019 - Curt Hill

Deletion • File deletion is not quite as secure as one might think • Deletion often puts files in a trash or recycle bin that may be inspected after the deletion • Emptying this bin typically does two things – Marks the directory entry as unused – often by writing a single byte – Moving the data sectors to the list of available sectors Copyright © 2019 - Curt Hill

Recovery • Most of the information still exists for a time • The information in the directory still exists with one or a few bytes overwritten – The missing bytes can usually be guessed – The sector locations will usually still be present, so they may be recovered from the available sectors list • The available sectors list may also be scanned Copyright © 2019 - Curt Hill

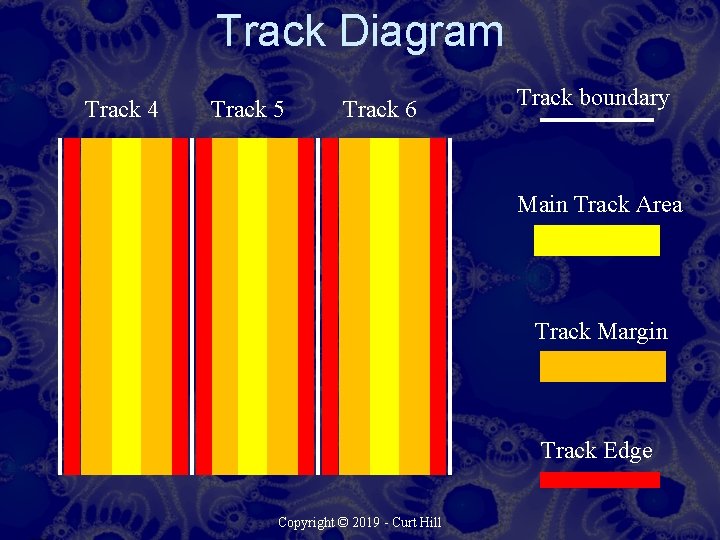
Secure Deletion • Typically a single file contents are modified in place or the entire disk is overwritten – Each sector is updated to obscure the contents – This is usually done multiple times • Even that may not be enough – Sensitive equipment may be able to read the margins of the track and reconstruct original contents – Very hard to do and usually only by security agencies Copyright © 2019 - Curt Hill

Track Diagram Track 4 Track 5 Track 6 Track boundary Main Track Area Track Margin Track Edge Copyright © 2019 - Curt Hill

Secure Deletion • If the data is securely deleted then it is not recoverable – Although backups and logs may provide some information • Similarly, the longer the item was insecurely deleted, the less likely useful information may be found – Reusing the directory entry or the sectors will occur – This reuse will remove the information Copyright © 2019 - Curt Hill

Stochastic Forensics • Most analysis requires the use of artifacts, usually files or information in files • Stochastic forensics is used to reconstruct actions without these – Invented to investigate insider data theft which typically leaves no trail • Involves statistically analyzing the meta data generated by the file system Copyright © 2019 - Curt Hill

Report • This is the report to the courts or prosecutor as to what happened – Should be phrased in non-technical language • This step may be omitted if not used in a legal proceeding – However, in many cases some report will recommend security changes that are needed Copyright © 2019 - Curt Hill

Tools • There a variety of tools • These include Operating Systems specialized towards forensics and packages that are helpful • An Ubuntu based Linux named CAINE – Computer Aided INvestigative Environment – Is a live CD/DVD to prevent changing the system disk • Several others as well Copyright © 2019 - Curt Hill

Several tools • There a few free tools – Autopsy – Digital Forensics Framework – Open Computer Forensics Architecture – The Sleuth Kit • There are more which are proprietary – two common ones: – En. Case – FTK (Forensic Tool Kit) Copyright © 2019 - Curt Hill

Evidentiary Requirements • Like in many cyber areas, legal practice and precedents have lagged • State laws and practices vary • The practitioner should understand the federal laws that are relevant – We have covered these previously • Federal rules on evidence concerning reliability, authentication and hearsay should be understood as well Copyright © 2019 - Curt Hill

Certifications • There are several relevant certifications from groups • International Society of Forensic Computer Examiners (ISFCE) – Certified Computer Examiner • Digital Forensics Investigation Professional (DFIP) • IACRB Certified Computer Forensics Examiner • Notes have some URLs Copyright © 2019 - Curt Hill

Finally • Digital forensics is a series of courses in itself – This has merely hit the high points Copyright © 2019 - Curt Hill