ITEC 502 Chapter 4 1 Deadlock MiJung Choi














- Slides: 27

ITEC 502 컴퓨터 시스템 및 실습 Chapter 4 -1: Deadlock Mi-Jung Choi mjchoi@postech. ac. kr DPNM Lab. Dept. of CSE, POSTECH

Contents 1. 2. 3. 4. 5. Resource Introduction to deadlocks Deadlock modeling The ostrich algorithm Deadlock detection and recovery ITEC 502 컴퓨터 시스템 및 실습 2

Resources (1) § Examples of computer resources – printers – tape drives – tables § Processes need access to resources in reasonable order § Suppose a process holds resource A and requests resource B – at same time another process holds B and requests A – both are blocked and remain so ITEC 502 컴퓨터 시스템 및 실습 3

Resources (2) § Deadlocks occur when … – processes are granted exclusive access to devices – we refer to these devices generally as resources § Preemptable resources – can be taken away from a process with no ill effects § Nonpreemptable resources – will cause the process to fail if taken away ITEC 502 컴퓨터 시스템 및 실습 4

Resources (3) § Sequence of events required to use a resource 1. request the resource 2. use the resource 3. release the resource Must wait if request is denied § – – requesting process may be blocked may fail with error code ITEC 502 컴퓨터 시스템 및 실습 5

Introduction to Deadlocks § Formal definition: – A set of processes is deadlocked if each process in the set is waiting for an event that only another process in the set can cause or – A set of blocked processes each holding a resource and waiting to acquire a resource held by another process in the set § Usually the event is release of a currently held resource § None of the processes can … – run – release resources – be awakened ITEC 502 컴퓨터 시스템 및 실습 6

Deadlock Example § Example – System has 2 tape drives – P 1 and P 2 each hold one tape drive and each needs another one § Example – semaphores A and B, initialized to 1 P 0 wait (A); wait (B); ITEC 502 컴퓨터 시스템 및 실습 P 1 wait (B); wait (A); 7

Four Conditions for Deadlock can arise if four conditions hold simultaneously 1. Mutual exclusion condition - 2. each resource assigned to 1 process or is available Hold and wait condition - 3. process holding resources can request additional No preemption condition - 4. previously granted resources cannot forcibly taken away Circular wait condition - must be a circular chain of 2 or more processes each is waiting for resource held by next member of the chain ITEC 502 컴퓨터 시스템 및 실습 8

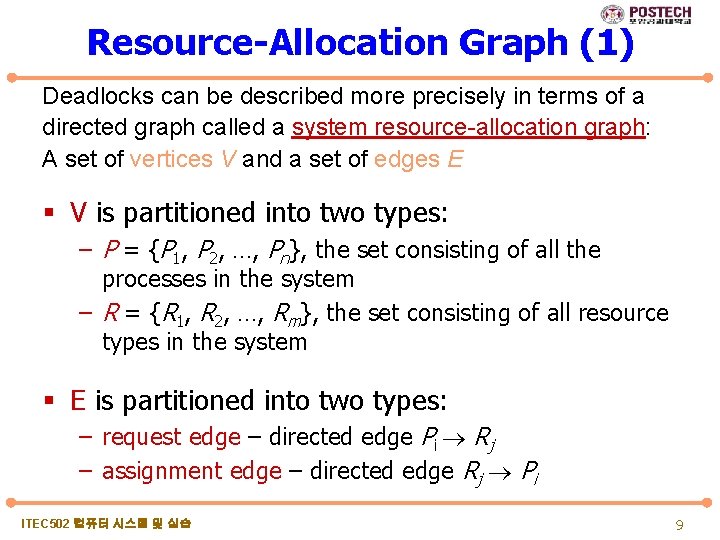
Resource-Allocation Graph (1) Deadlocks can be described more precisely in terms of a directed graph called a system resource-allocation graph: A set of vertices V and a set of edges E § V is partitioned into two types: – P = {P 1, P 2, …, Pn}, the set consisting of all the processes in the system – R = {R 1, R 2, …, Rm}, the set consisting of all resource types in the system § E is partitioned into two types: – request edge – directed edge Pi Rj – assignment edge – directed edge Rj Pi ITEC 502 컴퓨터 시스템 및 실습 9

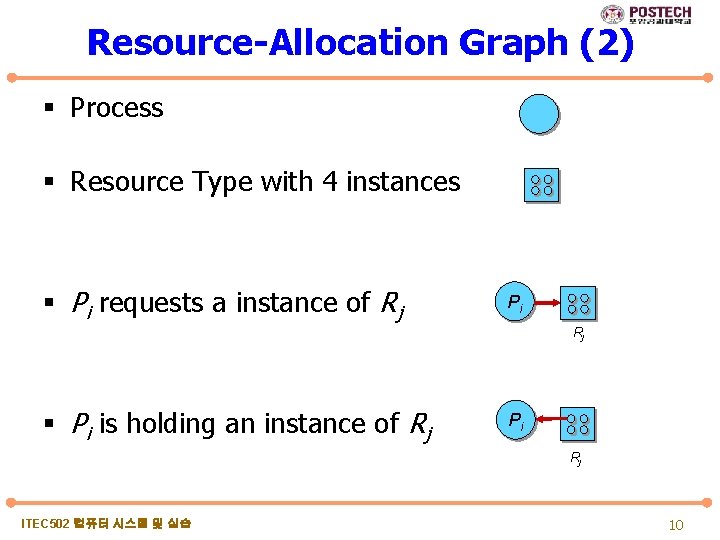
Resource-Allocation Graph (2) § Process § Resource Type with 4 instances § Pi requests a instance of Rj Pi Rj § Pi is holding an instance of Rj Pi Rj ITEC 502 컴퓨터 시스템 및 실습 10

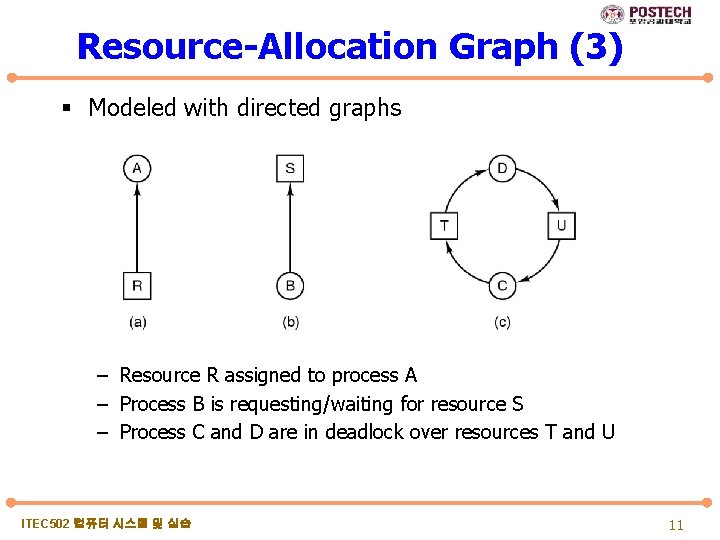
Resource-Allocation Graph (3) § Modeled with directed graphs – Resource R assigned to process A – Process B is requesting/waiting for resource S – Process C and D are in deadlock over resources T and U ITEC 502 컴퓨터 시스템 및 실습 11

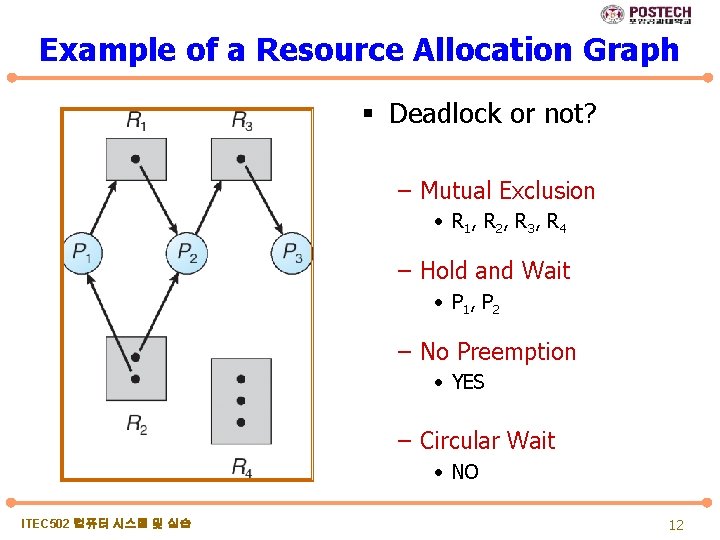
Example of a Resource Allocation Graph § Deadlock or not? – Mutual Exclusion • R 1 , R 2 , R 3 , R 4 – Hold and Wait • P 1 , P 2 – No Preemption • YES – Circular Wait • NO ITEC 502 컴퓨터 시스템 및 실습 12

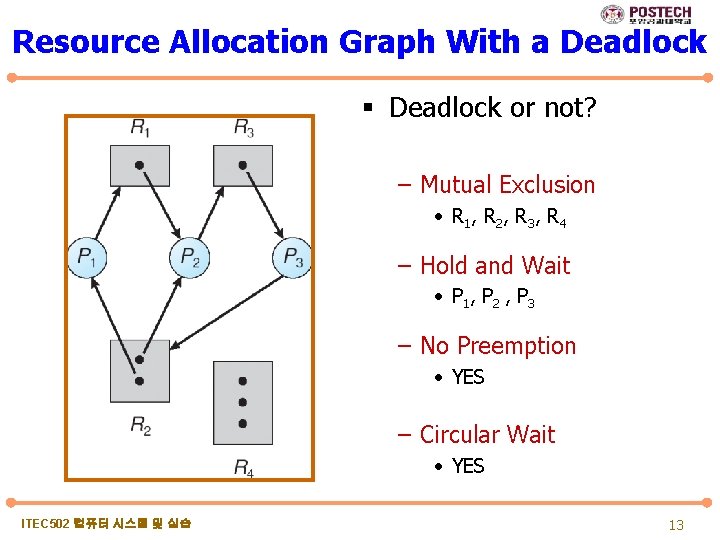
Resource Allocation Graph With a Deadlock § Deadlock or not? – Mutual Exclusion • R 1 , R 2 , R 3 , R 4 – Hold and Wait • P 1 , P 2 , P 3 – No Preemption • YES – Circular Wait • YES ITEC 502 컴퓨터 시스템 및 실습 13

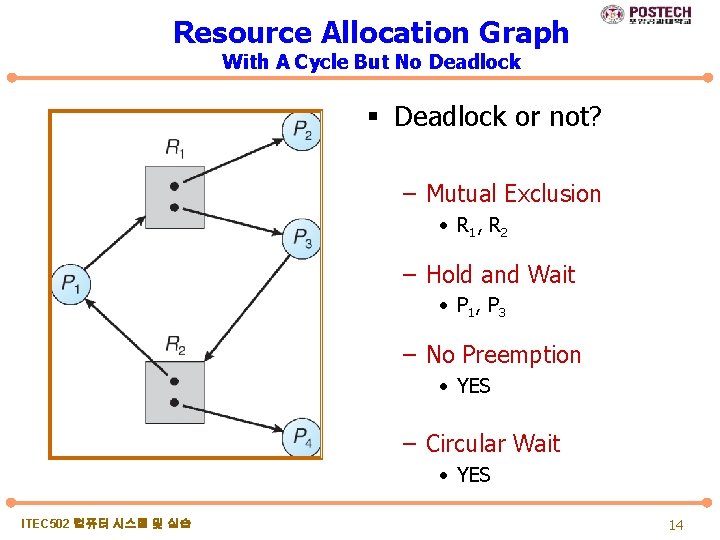
Resource Allocation Graph With A Cycle But No Deadlock § Deadlock or not? – Mutual Exclusion • R 1 , R 2 – Hold and Wait • P 1 , P 3 – No Preemption • YES – Circular Wait • YES ITEC 502 컴퓨터 시스템 및 실습 14

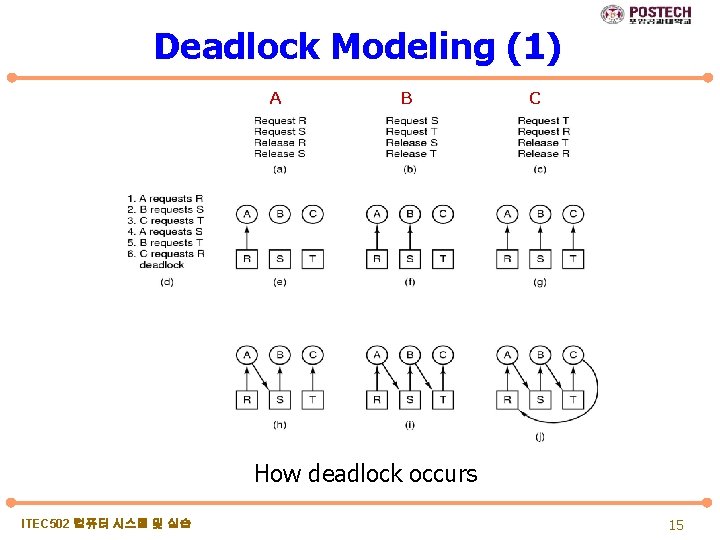
Deadlock Modeling (1) A B C How deadlock occurs ITEC 502 컴퓨터 시스템 및 실습 15

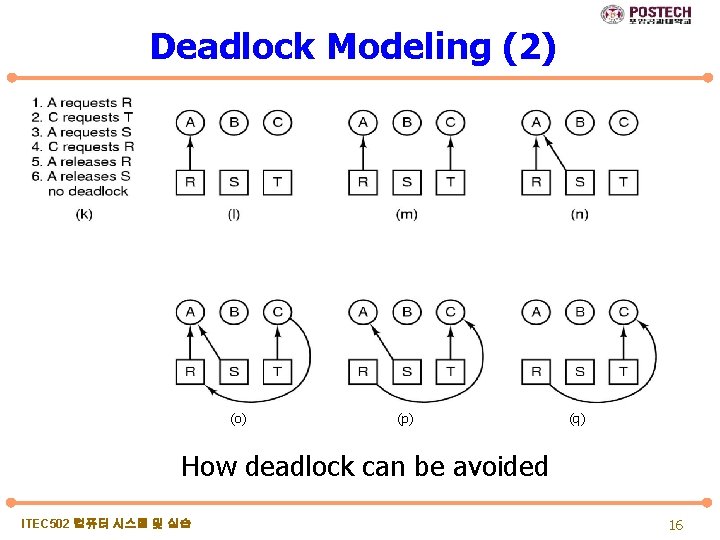
Deadlock Modeling (2) (o) (p) (q) How deadlock can be avoided ITEC 502 컴퓨터 시스템 및 실습 16

Strategies for dealing with Deadlocks 1. just ignore the problem altogether • Ignore the problem and pretend that deadlocks never occur in the system; – – 2. used by most operating systems, including UNIX and Windows It is then up to the application developer to write programs that handle deadlocks detection and recovery • Allow the system to enter a deadlock state and then recover – deadlock detection, deadlock recovery 3. dynamic avoidance • careful resource allocation 4. prevention • negating one of the four necessary conditions • ensure that the system will never enter a deadlock state – Use a protocol to prevent or avoid deadlocks ITEC 502 컴퓨터 시스템 및 실습 17

The Ostrich Algorithm § Pretend there is no problem § Reasonable if – deadlocks occur very rarely – cost of prevention is high § UNIX and Windows takes this approach § It is a trade off between – convenience – correctness ITEC 502 컴퓨터 시스템 및 실습 18

Deadlock Detection § Allow system to enter deadlock state § Detection algorithm § Recovery scheme ITEC 502 컴퓨터 시스템 및 실습 19

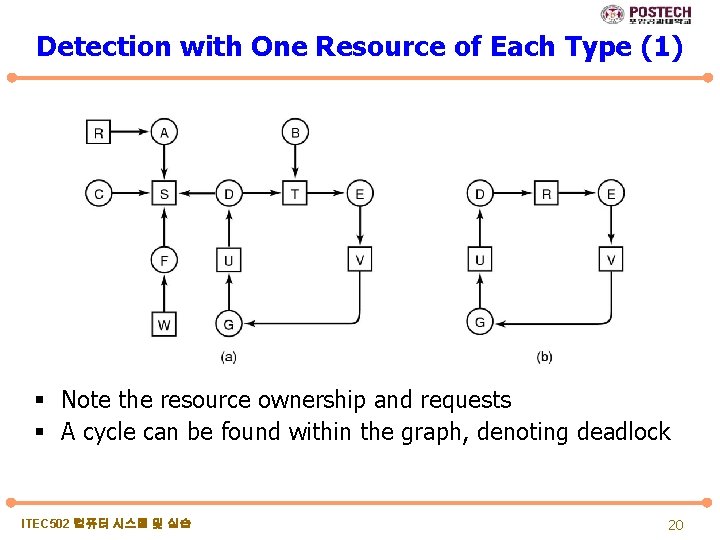
Detection with One Resource of Each Type (1) § Note the resource ownership and requests § A cycle can be found within the graph, denoting deadlock ITEC 502 컴퓨터 시스템 및 실습 20

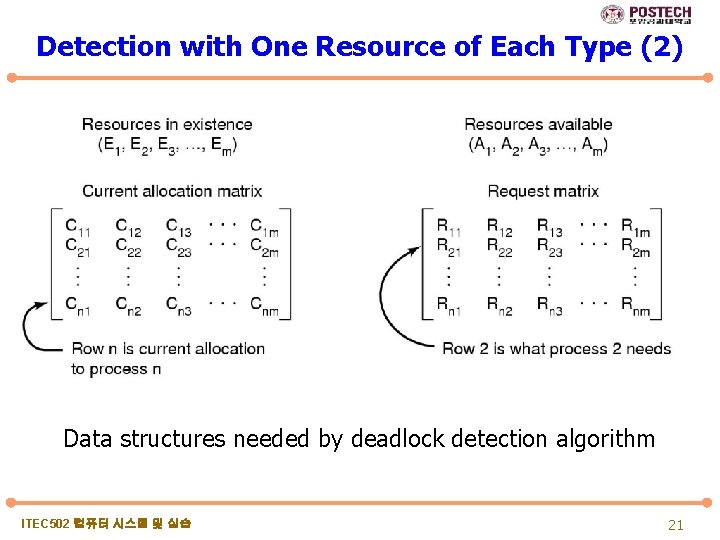
Detection with One Resource of Each Type (2) Data structures needed by deadlock detection algorithm ITEC 502 컴퓨터 시스템 및 실습 21

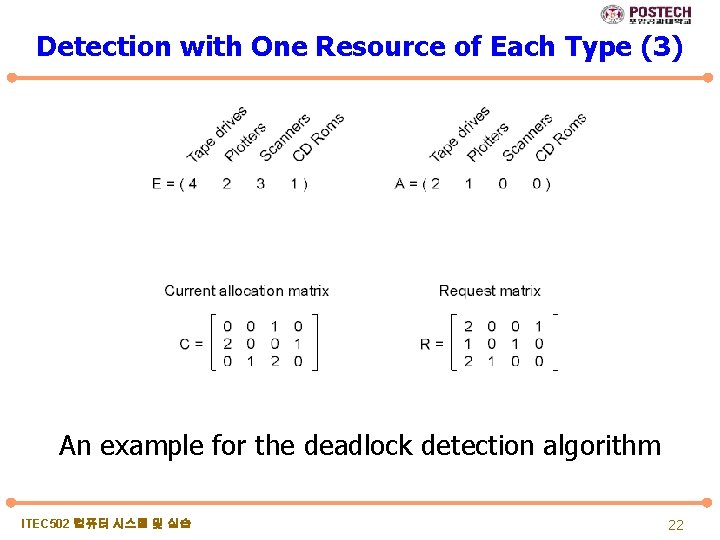
Detection with One Resource of Each Type (3) An example for the deadlock detection algorithm ITEC 502 컴퓨터 시스템 및 실습 22

Recovery from Deadlock (1) § When a detection algorithm determines that a deadlock exists, several alternatives are available: – To inform the operator that a deadlock has occurred and to let the operator deal with the deadlock manually – Recovery through preemption • To preempt some resources from one or more of the deadlocked processes • take a resource from some other process • depends on nature of the resource – Recovery through rollback • checkpoint a process periodically • use this saved state • restart the process if it is found deadlocked ITEC 502 컴퓨터 시스템 및 실습 23

Recovery from Deadlock (2) § Three issues in resource preemption 1. Selecting a victim – minimize cost 2. Rollback – return to some safe state, restart process from that state 3. Starvation – same process may always be picked as victim ITEC 502 컴퓨터 시스템 및 실습 24

Recovery from Deadlock (3) § Recovery through killing processes = process termination – – – to abort one or more processes to break the circular wait crudest but simplest way to break a deadlock kill one of the processes in the deadlock cycle the other processes get its resources choose process that can be rerun from the beginning – In which order should we choose to abort? • • • Priority of the process How long process has computed, and how much longer to completion Resources the process has used Resources process needs to complete How many processes will need to be terminated Is process interactive or batch? ITEC 502 컴퓨터 시스템 및 실습 25

Summary § A deadlock state occurs – when two or more processes are waiting indefinitely for an event that can be caused only by one of the waiting processes § A deadlock requires that four conditions hold simultaneously – Mutual exclusion, hold and wait, no preemption, circular wait § Four principle methods for dealing with deadlocks – – Deadlock prevention Deadlock avoidance Deadlock detection-recovery scheme Ignore the deadlock problem § Deadlock prevention ensures that at least one of the necessary conditions never holds § When deadlock is detected, the system must recover either by terminating some of the deadlocked processes or by preempting resources from some of the deadlocked processes ITEC 502 컴퓨터 시스템 및 실습 26

Review 1. 2. 3. 4. 5. Resource Introduction to deadlocks Deadlock modeling The ostrich algorithm Deadlock detection and recovery ITEC 502 컴퓨터 시스템 및 실습 27