ISQS 6342 Topic Logging Sunil Topics for Discussion































- Slides: 40

ISQS 6342 Topic : Logging : Sunil

Topics for Discussion Ø Introduction Ø System Log Management Ø Syslog-ng Ø Conclusion

INTRODUCTION Logging and System Auditing n n Logging is the recording of per-specified events or actions performed on or by a system. System Auditing is verification of all events and actions recorded in the Logging process to search for system abuse, theft etc

System Log Management n Systems must have a comprehensive , accurate and carefully watched logs. Logs serve several purposes : n n n Helps in troubleshooting virtually all types of application and system problems. Provide valuable early warning signs for system abuse Finally if anything goes wrong it provides crucial forensic data.

System Log Management n Threats : n Scope The type of threats and attacks n Potential unauthorized attacks for n n n Access Information Manipulate Information Render Information systems unreliable/unusable

System Log Management n Risk : n n n Vulnerability : n n Suspect Flaw in the system ( hardware or software) Attack : n n Accidental unpredictable exposure to Information Violation to system integrity due to malfunction A specific execution of a plan to carry out a threat Penetration : n A successful attack

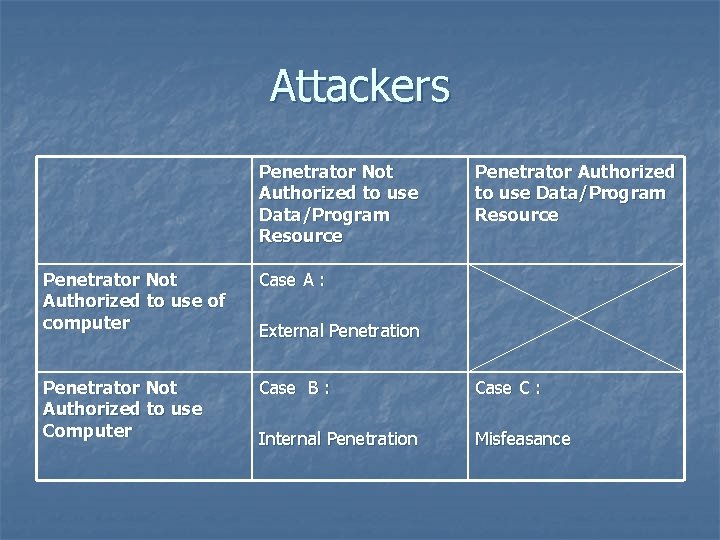
Attackers Penetrator Not Authorized to use Data/Program Resource Penetrator Not Authorized to use of computer Case A : Penetrator Not Authorized to use Computer Case B : Case C : Internal Penetration Misfeasance External Penetration

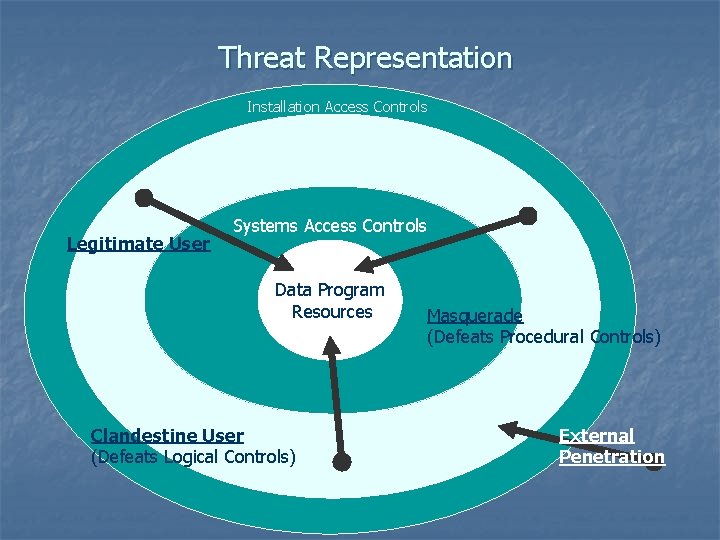
Threat Representation Installation Access Controls Legitimate User Systems Access Controls Data Program Resources Clandestine User (Defeats Logical Controls) Masquerade (Defeats Procedural Controls) External Penetration

Gaining Access to System External Penetration n An Outsider attempting to access information of an organization that he is not a part of. An Employee who has access to the premises but is not an authorized computer user. An individual Taps a communication lines to work on the system. uses trial and error method of logging in

Gaining Access to System Internal Penetration n More Frequent Has Access ( May or may not be Limited) or has over come the barrier to unauthorized access Classified into 3 classes ( shown in increasing order of difficulty of detection ) n n n The Masquerader The Legitimate user The Clandestine user

LEGITIMATE USER A Case of Misfeasance n Traits : User with proper authorization n No extra use of resources n User with proper authorization n Trails do not show abnormal patterns of system usage. n

LEGITIMATE USER n Not easy nor feasible to catch Foul Play n Audit trails : n n Excessive Time spent Excess amount of Data/Program Reference

The Masquerader n Internal user External Penetrator who has succeeded in penetrating the installation n An Employee without full access to the system n An Employee with full access to the system who wishes to exploit another authorized users identity that he might have obtained. He has a legitimate login and password so as far as the system is concerned he is a legitimate user. There is no particular feature to distinguish the masquerader from a legitimate used. n

The Masquerader n Interestingly defined by “ Extra ” use of system resources n Detection Trails : n n Use outside of normal times Abnormal frequency of use Abnormal Volume of data reference Abnormal pattern of reference to programs or data The system focuses on the legitimate users resources as protected all devices and access to the systems. This extra usage is detectable

Clandestine User n Most difficult to detect n Seized supervisory controls of machine n Alters system to evade Audit Trail Data n Operates below the level audit data is taken n Seen as “ The little man who isn’t there ”

Clandestine User n n Check for internal auditing mechanisms n Busy idle states of CPU n Memory usage n Secondary storage etc Counter Measures : n Operating System Code compared to a reference version n Provide audit trail to each major component of machine Tough to detect this pure phantom use

Characterization of Usage n n In characterizing Computer Usage the main issue to be faced is what unit or units should represent system usage. Notions are : n n n Unit of Computer work – Job / Session Time parameters Data Set and Program uses Monitoring Files and Devices Group Statistics

Characterization of Usage n Job or Session Job is for Batch Running n Session is for interactive working n n Both of these terms denotes a continuous and single usage of computer working with well defined starting and ending The parameters that audit trail searches are the user identification, program accessed , Data Set accessed. Case of Principal Parameter :

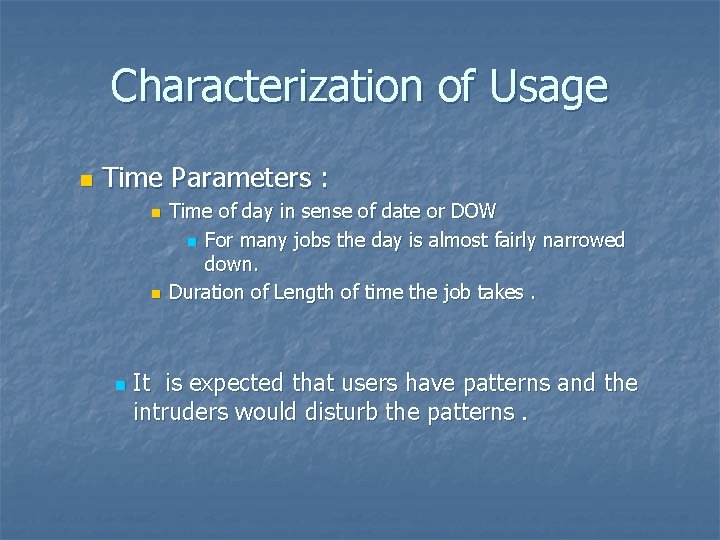
Characterization of Usage n Time Parameters : n n n Time of day in sense of date or DOW n For many jobs the day is almost fairly narrowed down. Duration of Length of time the job takes. It is expected that users have patterns and the intruders would disturb the patterns.

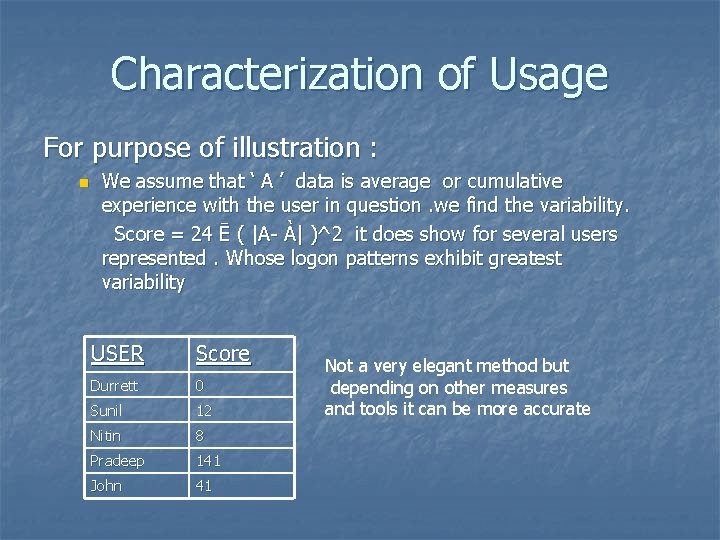
Characterization of Usage For purpose of illustration : n We assume that ‘ A ’ data is average or cumulative experience with the user in question. we find the variability. Score = 24 Ē ( |A- À| )^2 it does show for several users represented. Whose logon patterns exhibit greatest variability USER Score Durrett 0 Sunil 12 Nitin 8 Pradeep 141 John 41 Not a very elegant method but depending on other measures and tools it can be more accurate

Characterization of Usage n Data Set and Program Usage n n This parameter differs significantly from system to system. Program is significant from security point of view as used in reading and writing. Almost a clue of penetration activity.

Characterization of Usage n Monitoring Files and Devices n n Focuses on monitoring of the particular user identifier through a range of actions that he is allowed to access that include submitting jobs and use of system etc Group Statistics n n Grouping records into sets having same properties that refer to same job, session, user , device, files, programs Datasets and other resources. Presumption that a session or job referring to same file sets can exhibit similar properties from run to run.

Linux : Syslog n n n Tired and true work horse of UNIX Logging Utilities Accepts log data from Kernel (by way of Klogd) A Preconfigured syslog is part of base operation systems of Linux and Unix

Configuring Syslog n n Acts on the Message type or facility and its priority The mapping of actions to facilities and priorities are specified in /etc/syslog. conf Each line specifies one or more facilities followed by an action A facility or a facility with one priority constitutes a Selector Sample syslog. conf File mail. notice /var/log/mail

Syslog n Facilities : n Are simply categories they support Some of the facilities are Auth-priv Used for many security events Access control messages Daemon Kern System processes and other daemons Used for Kernel messages Mark User Messages Generated by syslog itself Default facility when none is specified Local 0 -7 * Boot messages etc All Facility None No facility

Syslog n Priorities : n Are priorities assigned to the facilities these are hierarchical in increasing order of urgency n Debug, info, notice, warning, err, crit , alert, emerg The order of urgency is specified by the programmer n * and none can be used like facilities n May be preceded by = or ! n Specify only one priority per facility n

Syslog n Priorities assignment n n Mail. notice mail. =notice mail. !=notice /var/log/mail 1 /var/log/mail 2 Actions n n n Mostly all log message are written into files Full file path must be specified in the lines’s action in syslog. conf file Messages can also be sent to other places. An action can be a file , a named pipe printer, device , remote host or a user screen.

Syslog n Actions n n n n Remote Logging is an important facility in syslog Message that matches that line’s action will be sent though UDP port 514 Ex: *. emerg @mothership. mydomain. org The systems host’s syslog should have started with an –r flag You can specify multiple facilities in one line and one action. The priority assignments is one per selector. Can specify multiple selectors separated by ; Ex: mail, uccp. notice; uucp!=alert /var/log/mail

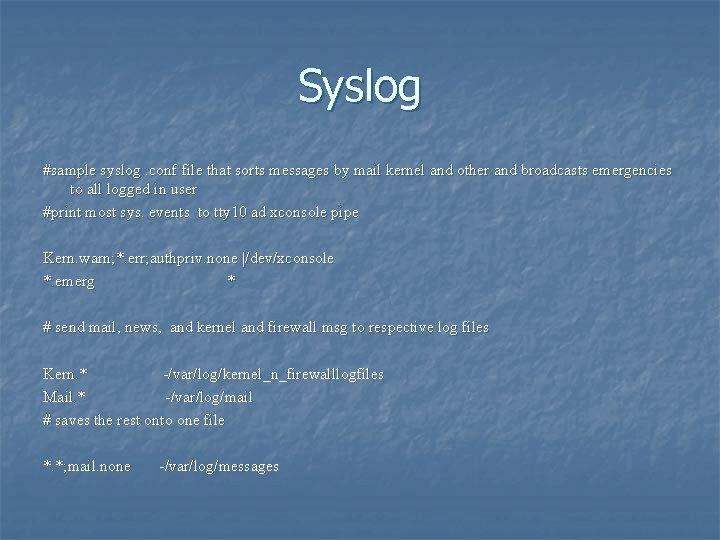
Syslog #sample syslog. conf file that sorts messages by mail kernel and other and broadcasts emergencies to all logged in user #print most sys. events to tty 10 ad xconsole pipe Kern. warn; *. err; authpriv. none |/dev/xconsole *. emerg * # send mail, news, and kernel and firewall msg to respective log files Kern. * -/var/log/kernel_n_firewalllogfiles Mail. * -/var/log/mail # saves the rest onto one file *. *; mail. none -/var/log/messages

Syslog -ng n n n Similar to syslog-ng An attempt to increase syslog flexibility and adding better filtering, forwarding, message integrity and encryption Syslog-ng supports remote logging over TCP and UDP protocols Can be used in conjunction with tunneling tools like stunnel and ssh to authenticate or encrypt log messages sent to remote host Brain child of Balazs Scheidler

Syslog-ng n Bit more involved in configuring syslog-ng n syslog-ng. conf and resides in /etc/syslog-ng/. Defines sections like the Global Options , message Sources, message destinations and message filters and combine them to create logging rules

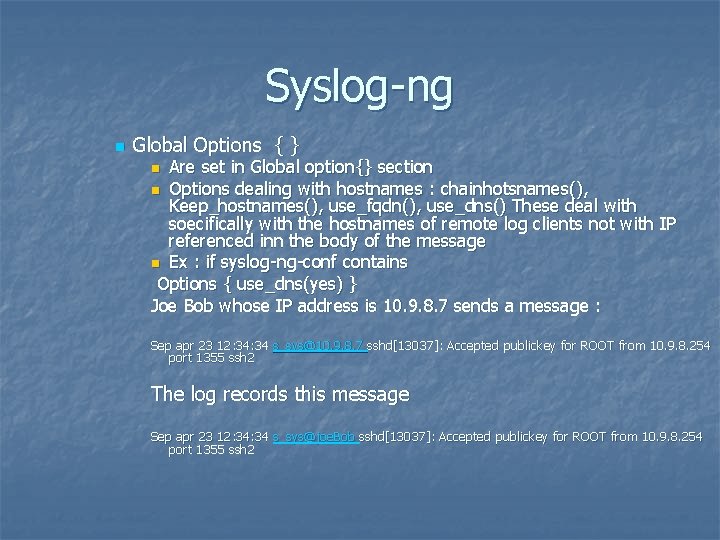
Syslog-ng n Global Options { } Are set in Global option{} section n Options dealing with hostnames : chainhotsnames(), Keep_hostnames(), use_fqdn(), use_dns() These deal with soecifically with the hostnames of remote log clients not with IP referenced inn the body of the message n Ex : if syslog-ng-conf contains Options { use_dns(yes) } Joe Bob whose IP address is 10. 9. 8. 7 sends a message : n Sep apr 23 12: 34 s_sys@10. 9. 8. 7 sshd[13037]: Accepted publickey for ROOT from 10. 9. 8. 254 port 1355 ssh 2 The log records this message Sep apr 23 12: 34 s_sys@joe. Bob sshd[13037]: Accepted publickey for ROOT from 10. 9. 8. 254 port 1355 ssh 2

Syslog-ng n Options{ } : n Keep_hostname() : If set to no the syslog does not take hostname supplied by remote log server at face vaslue. It instead resolves the source of IP packets for itself to decide the hostname n n This is in contrast from syslog who accepts host name at face value. Chain_hostname() : determines wether syslog list all hosts through which each message has been relayed – set to yes

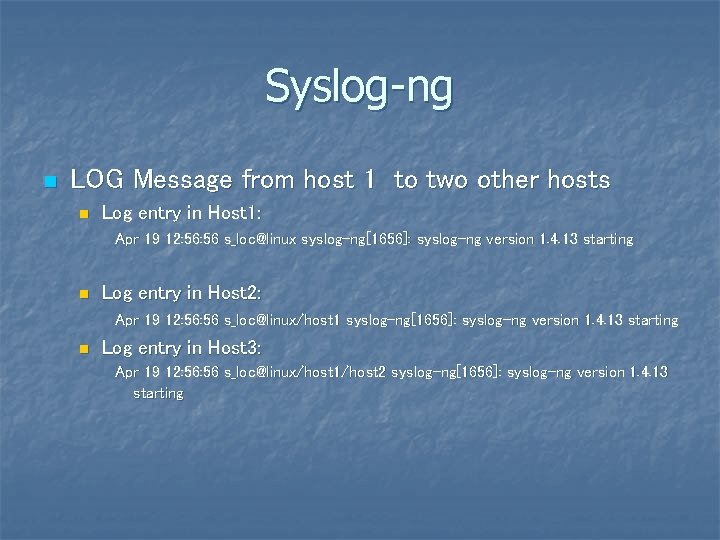
Syslog-ng n LOG Message from host 1 to two other hosts n Log entry in Host 1: Apr 19 12: 56 s_loc@linux syslog-ng[1656]: syslog-ng version 1. 4. 13 starting n Log entry in Host 2: Apr 19 12: 56 s_loc@linux/host 1 syslog-ng[1656]: syslog-ng version 1. 4. 13 starting n Log entry in Host 3: Apr 19 12: 56 s_loc@linux/host 1/host 2 syslog-ng[1656]: syslog- ng version 1. 4. 13 starting

Syslog-ng n Source { }: contains source() definition which contains 2 drivers (message –inputs) , may contain more drivers. Source sourcelable { driver 1([options]) ; driver 2([options ]) } n n Quite flexible and can accept message from various drivers syslog-ng itself , UDP streams from remote hots , names pipes, TCP connections from remote hosts, and special files. Ex : Source s_tcpmessage{ tcp( ip(168. 197. 135. 168) port (10514) ); }; Source s_udpmessage{ udp(); }

Syslog-ng n Destination { }: can send messages at the same places as syslog ASCII files, names pipes, remote hosts via UDP or TCP and to other programs as input. n n n Supports File Macros unlike syslog File ( “filename( [ $MACRO ] “) Filters { }: Optional. Allows you to route messages based on not only facility and priority as syslog does but also on the following n n the name of the program that sent it The Host that forwarded it over the network A regular expression evaluated on the message itself The name of an other filter

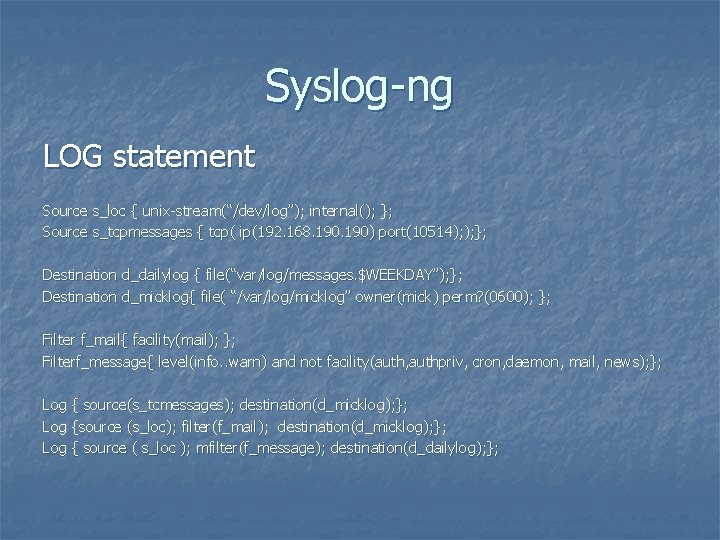
Syslog-ng LOG statement Source s_loc { unix-stream(“/dev/log”); internal(); }; Source s_tcpmessages { tcp( ip(192. 168. 190) port(10514); ); }; Destination d_dailylog { file(“var/log/messages. $WEEKDAY”); }; Destination d_micklog{ file( “/var/log/micklog” owner(mick) perm? (0600); }; Filter f_mail{ facility(mail); }; Filterf_message{ level(info. . warn) and not facility(auth, authpriv, cron, daemon, mail, news); }; Log { source(s_tcmessages); destination(d_micklog); }; Log {source (s_loc); filter(f_mail); destination(d_micklog); }; Log { source ( s_loc ); mfilter(f_message); destination(d_dailylog); };

Automated Log Monitoring n n You have recorded all log data Who read the log messages ? SWATCH Does n A free log-monitoring utility written 100% in perl. n Install from n n http: //www. stanford. edu/~atkins/swatch

References n n James Andersons on Computer Threats and security surveillance Hacking Exposed Stuart Mc. Clure n Building secure Servers with Linux Michael D Bauer

Funny things happen !