IPSec VPN Accton Tech Inc Collected and Prepared










![Relevant RFCs list [RFC 791] Internet Protocol DARPA Internet Program Protocol Specification, Information Sciences Relevant RFCs list [RFC 791] Internet Protocol DARPA Internet Program Protocol Specification, Information Sciences](https://slidetodoc.com/presentation_image_h2/20962525a8364c20987d10029413ab05/image-30.jpg)
- Slides: 30

IPSec VPN Accton Tech. Inc. Collected and Prepared by Tom Ho

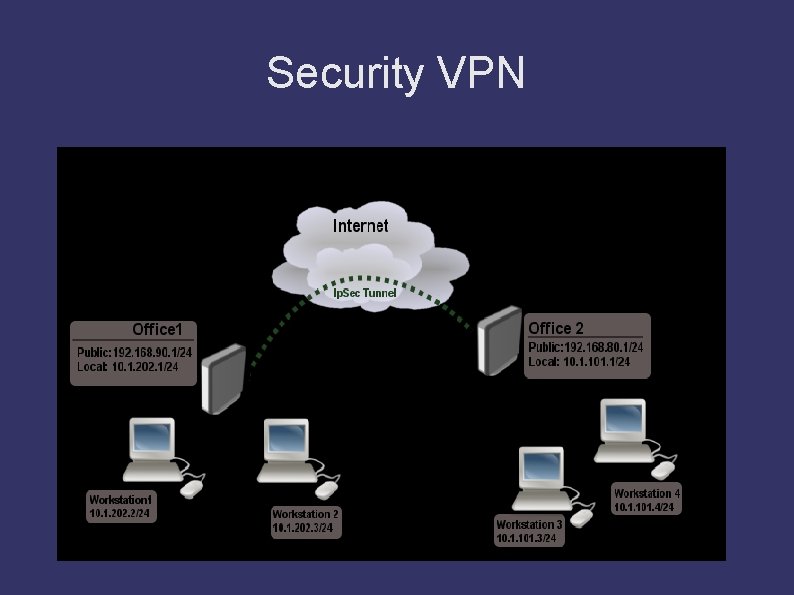
Security VPN

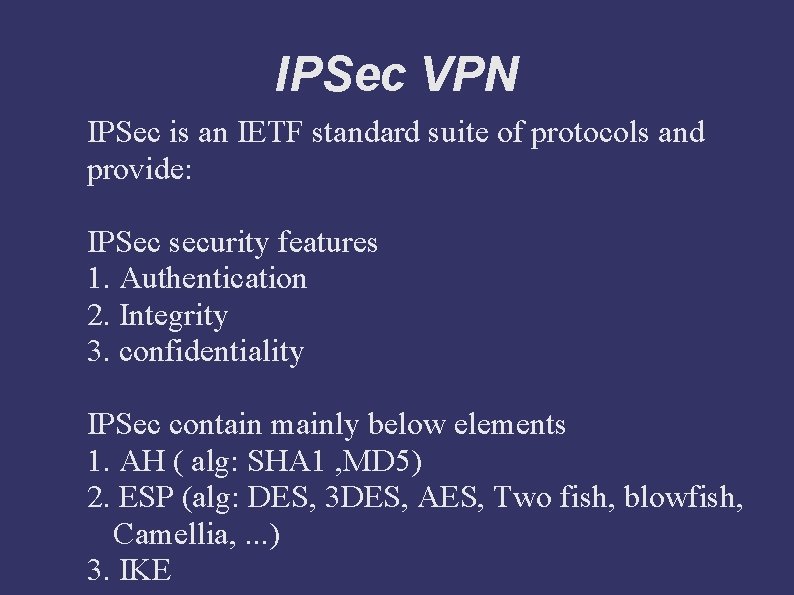
IPSec VPN IPSec is an IETF standard suite of protocols and provide: IPSec security features 1. Authentication 2. Integrity 3. confidentiality IPSec contain mainly below elements 1. AH ( alg: SHA 1 , MD 5) 2. ESP (alg: DES, 3 DES, AES, Two fish, blowfish, Camellia, . . . ) 3. IKE

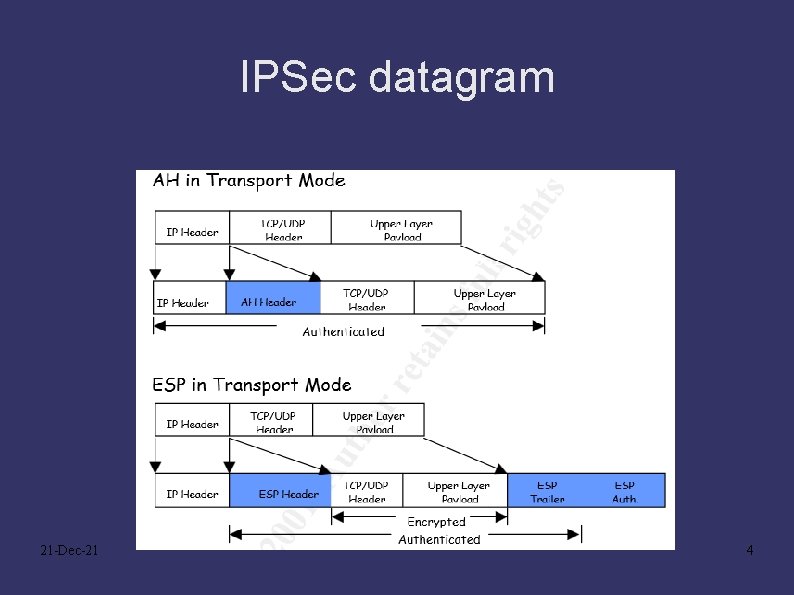
IPSec datagram 21 -Dec-21 4

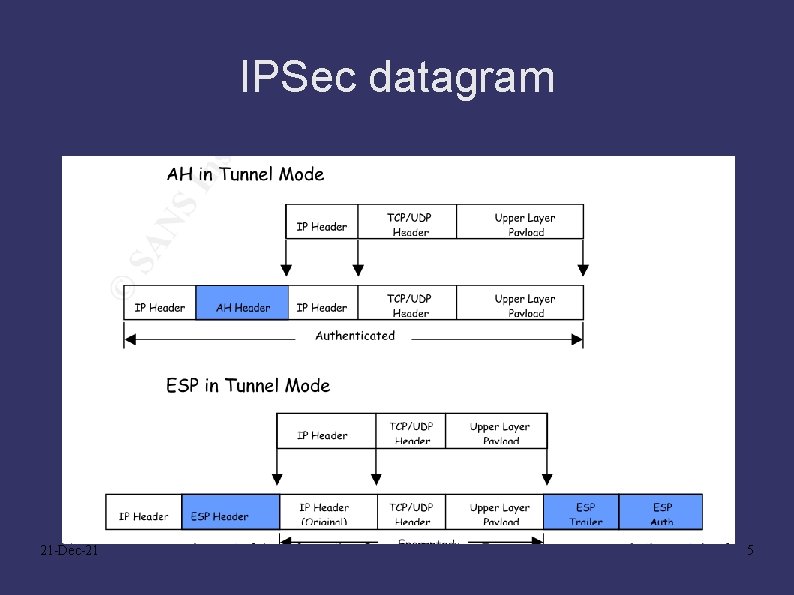
IPSec datagram 21 -Dec-21 5

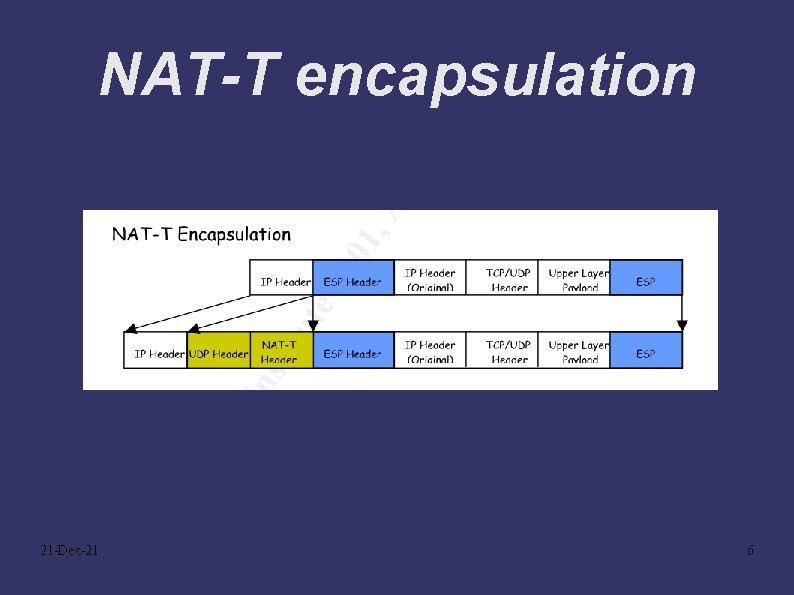
NAT-T encapsulation 21 -Dec-21 6

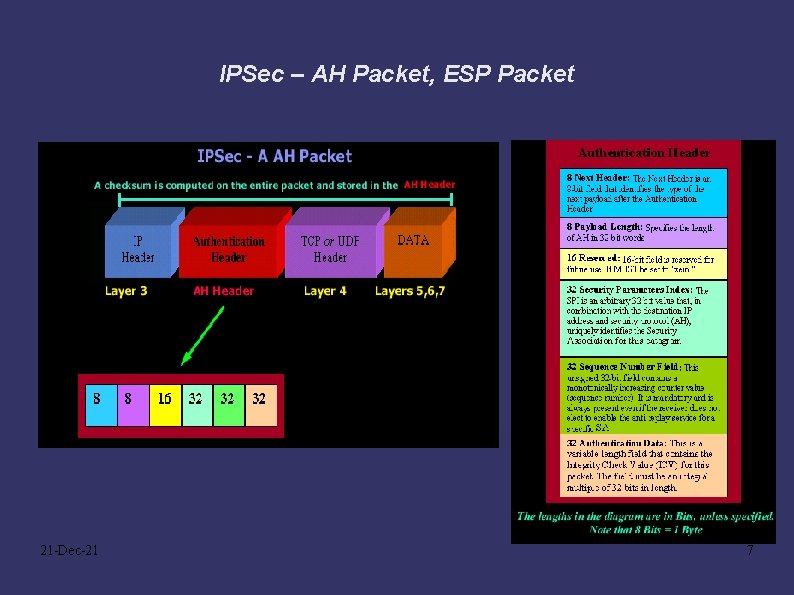
IPSec – AH Packet, ESP Packet 21 -Dec-21 7

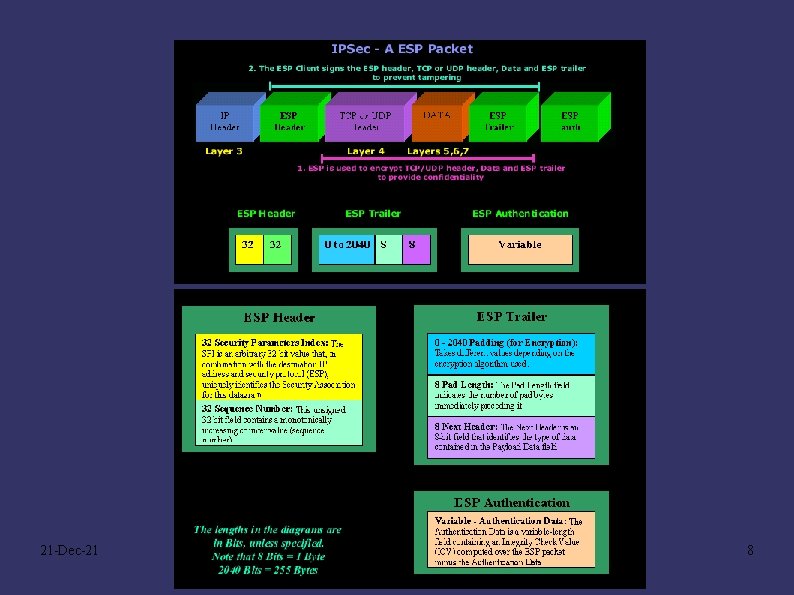
21 -Dec-21 8

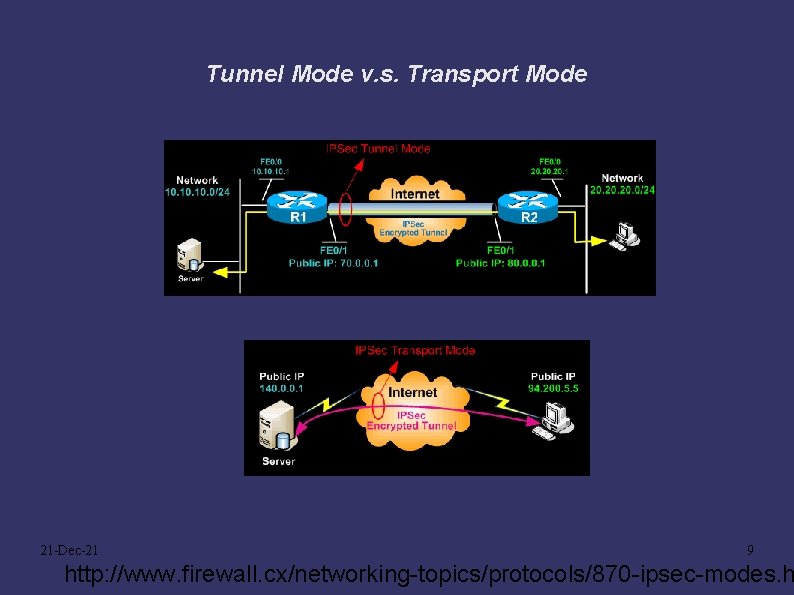
Tunnel Mode v. s. Transport Mode 21 -Dec-21 9 http: //www. firewall. cx/networking-topics/protocols/870 -ipsec-modes. h

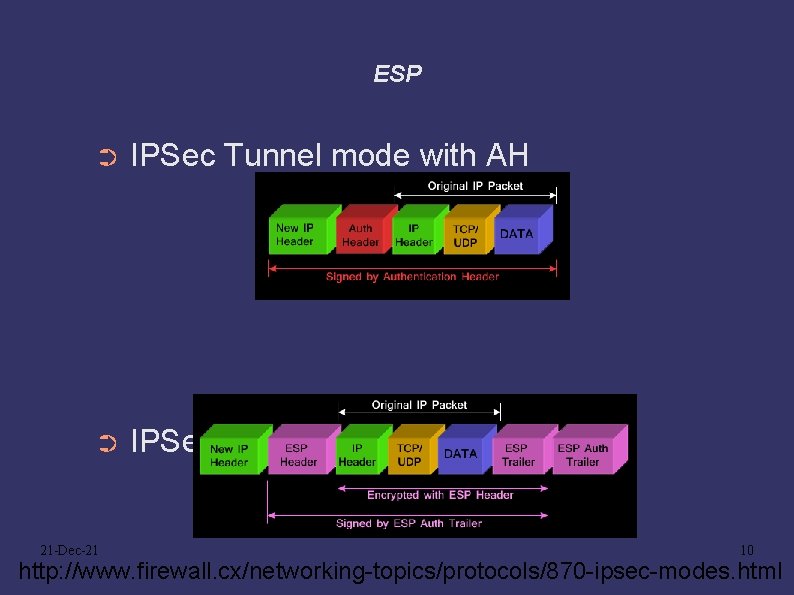
ESP ➲ IPSec Tunnel mode with AH ➲ IPSec Tunnel mode with ESP 21 -Dec-21 10 http: //www. firewall. cx/networking-topics/protocols/870 -ipsec-modes. html

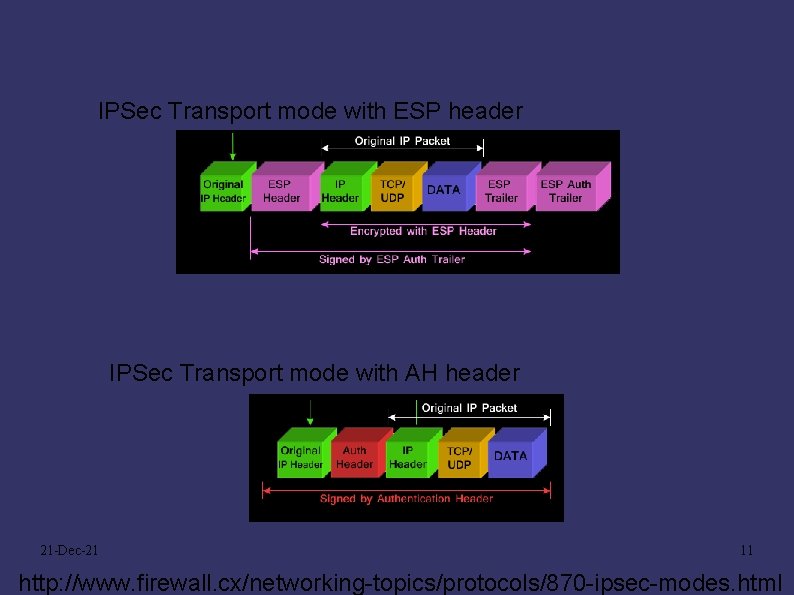
IPSec Transport mode with ESP header IPSec Transport mode with AH header 21 -Dec-21 11 http: //www. firewall. cx/networking-topics/protocols/870 -ipsec-modes. html

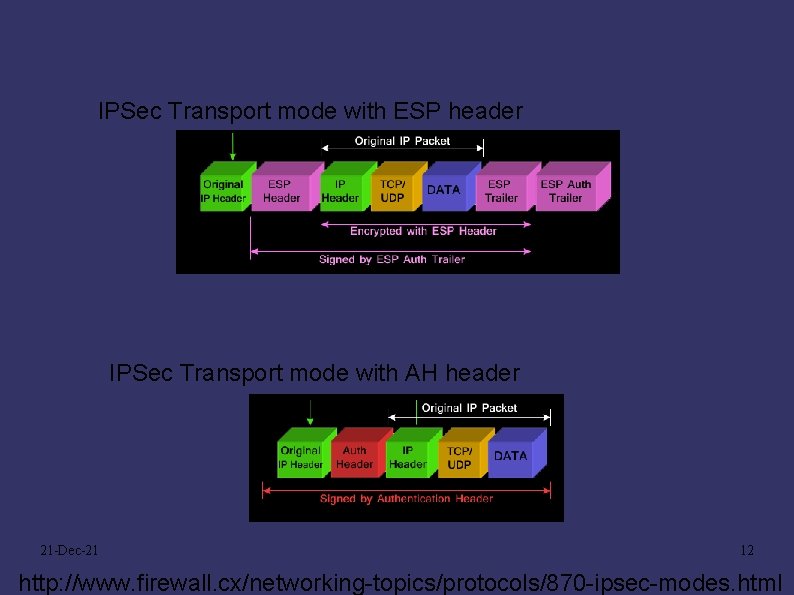
IPSec Transport mode with ESP header IPSec Transport mode with AH header 21 -Dec-21 12 http: //www. firewall. cx/networking-topics/protocols/870 -ipsec-modes. html

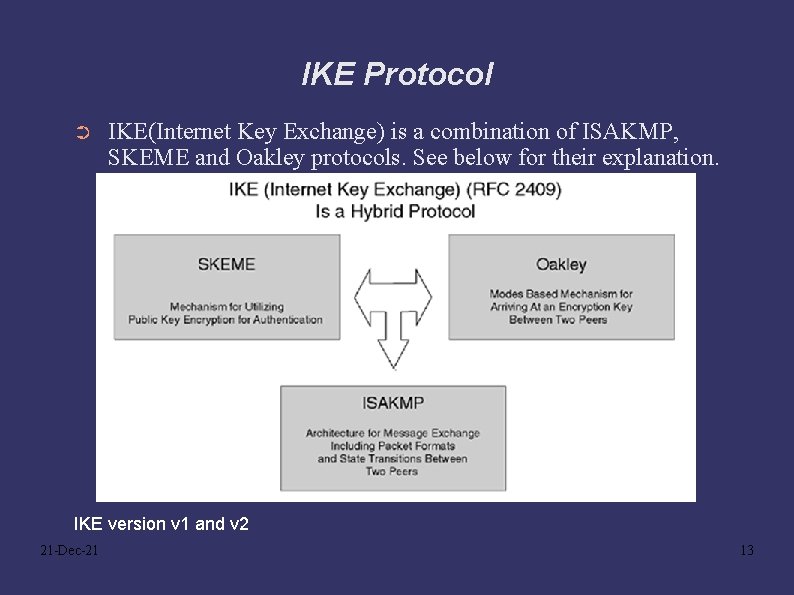
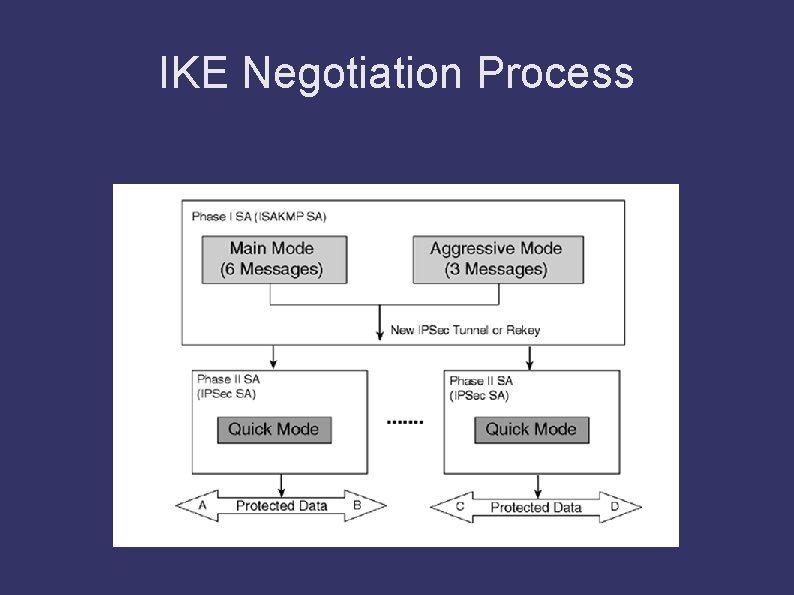
IKE Protocol ➲ IKE(Internet Key Exchange) is a combination of ISAKMP, SKEME and Oakley protocols. See below for their explanation. IKE version v 1 and v 2 21 -Dec-21 13

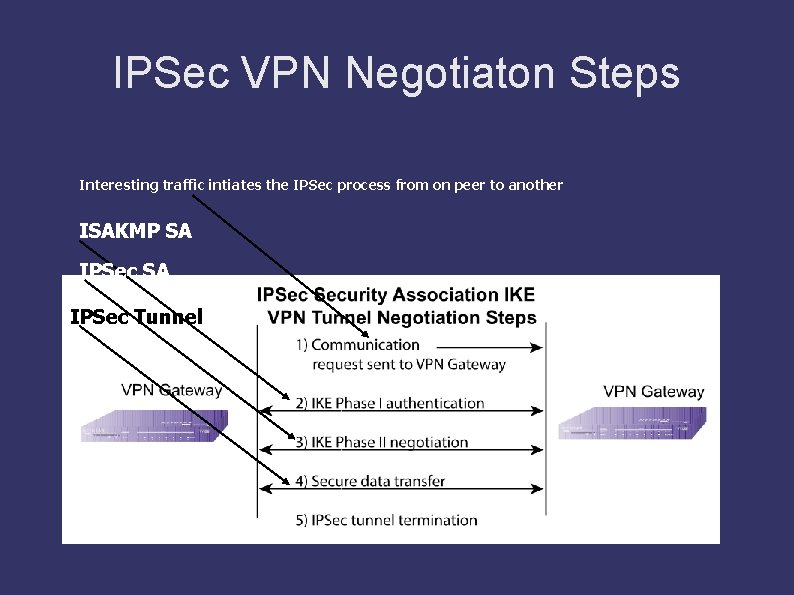
IPSec VPN Negotiaton Steps Interesting traffic intiates the IPSec process from on peer to another ISAKMP SA IPSec Tunnel

IKE Protocol IKE Phase 1 (ISAKMP SA for setup a security channel) ➲ Matching the following settings: ➲ 1. authentication method ➲ 2. DH group ➲ 3. encryption algorithm ➲ 4. exchange mode ➲ 5. hash algorithm ➲ 6. DPD and lifetime ➲ 7. NAT-T ➲ 21 -Dec-21 15

IKE Negotiation Process

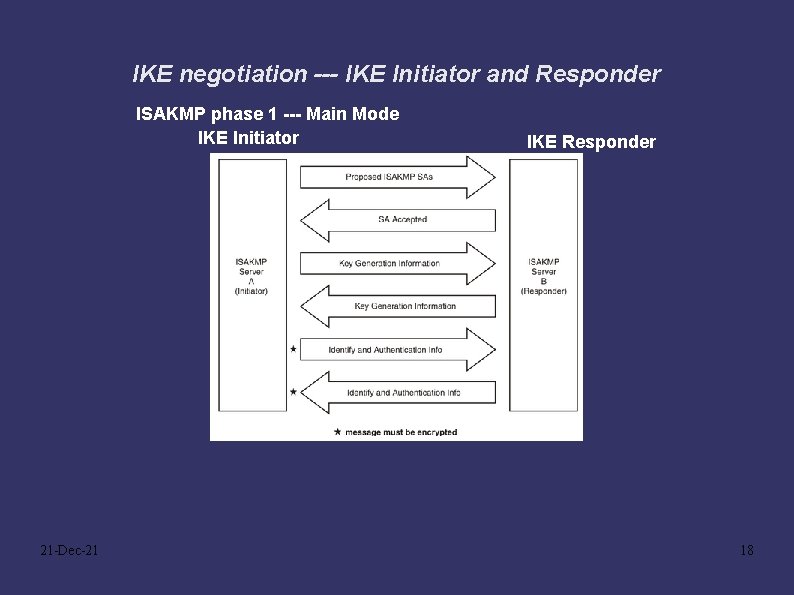
IKE negotiation --- IKE Initiator and Responder ISAKMP phase 1 --- Main Mode IKE Initiator 21 -Dec-21 IKE Responder 18

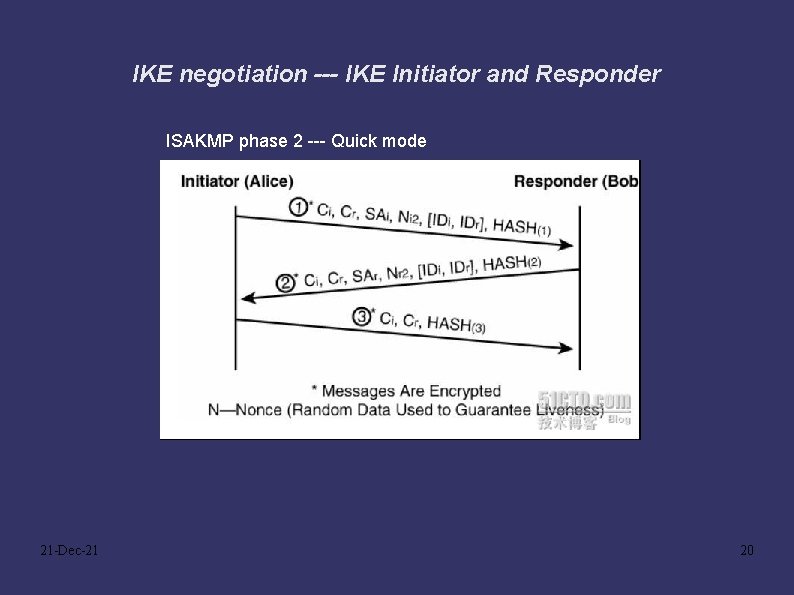
IKE negotiation --- IKE Initiator and Responder ISAKMP phase 2 --- Quick mode 21 -Dec-21 20

Dead Peer Detection is an IPsec IKE Notification message. It uses an ICOOKIE/RCOOKIE mechanism to match an incoming packet to a known Security Association (ISAKMP). ➲ DPD notifications have no phase 2 state association. ➲ DPD is mainly supported by Cisco, Openswan, Strongswan and Mac OS X 10. 5 "Leopard" and higher. ➲ 21 -Dec-21 21

Dead Peer Detection is an IPsec IKE Notification message. It uses an ICOOKIE/RCOOKIE mechanism to match an incoming packet to a known Security Association (ISAKMP). ➲ DPD notifications have no phase 2 state association. ➲ DPD is mainly supported by Cisco, Openswan, Strongswan and Mac OS X 10. 5 "Leopard" and higher. ➲ 21 -Dec-21 22

IPSec VPN IKE automate Key exchange and SA negotiation and setup between parties transferring data ➲ Dynamical Key refreshing ➲ ➲ 21 -Dec-21 23

Diffi-Hellman Key exchange Published by Whitfield Diffie and Martin Hellman in 1976 allows two parties that have no prior knowledge of each other to jointly establish a shared secret key over an insecure communications channel. This key can then be used to encrypt subsequent communications using a symmetric key cipher. 21 -Dec-21 24

Diffie-Hellman Exchange When PFS is enabled, a Diffie-Hellman Exchange will be performed with each quick mdoe for IKE phase 2. 21 -Dec-21 25

VPN uses two IPSec protocols to protect data as it flows through the VPN: Authentication Header (AH) and Encapsulating Security Payload (ESP). The other part of IPSec enablement is the Internet Key Exchange (IKE) protocol, or key management. While IPSec encrypts your data, IKE supports automated negotiation of security associations (SAs), and automated generation and refreshing of cryptographic keys. 21 -Dec-21 26

ISAKMP The ISAKMP protocol is a framework for dynamically establishing security associations and cryptographic keys in an Internet environment. This framework defines a set of message flows (exchanges) and message formats (payloads). ISAKMP defines a generic payload for key exchange information. This enables the ISAKMP protocol to manage cryptographic keys independent of the key exchange protocol that is used to generate them. 21 -Dec-21 27

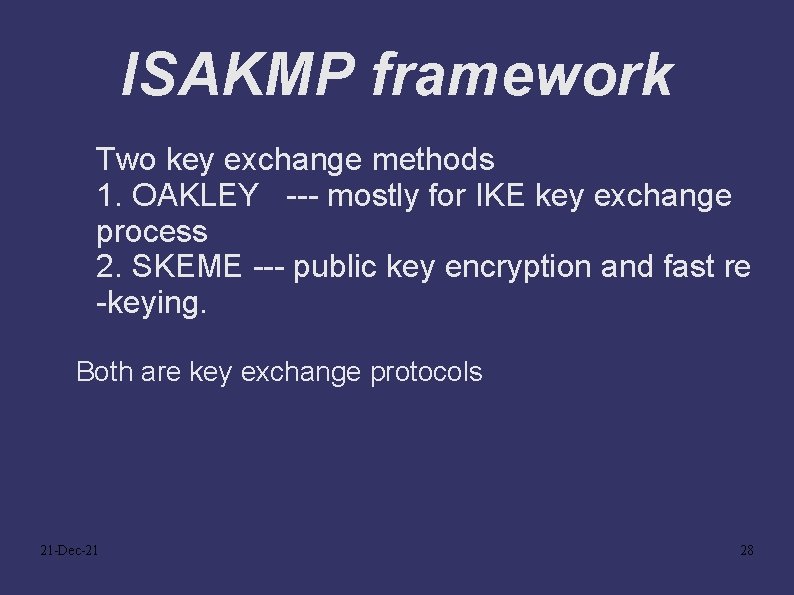
ISAKMP framework Two key exchange methods 1. OAKLEY --- mostly for IKE key exchange process 2. SKEME --- public key encryption and fast re -keying. Both are key exchange protocols 21 -Dec-21 28

Perfect Forwarding Secrecy With PFS disabled, initial keying material is "created" during the key exchange in phase-1 of the IKE negotiation. In phase-2 of the IKE negotiation, encryption and authentication session keys will be extracted from this initial keying material. By using PFS, Perfect Forwarding Secrecy, completely new keying material will always be created upon re-key. Should one key be compromised, no other key can be derived using that information. 21 -Dec-21 29

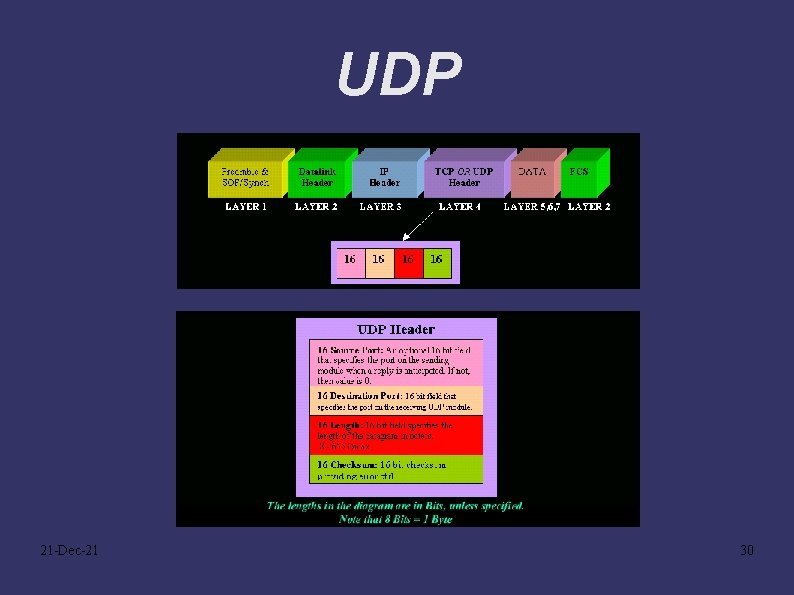
UDP 21 -Dec-21 30

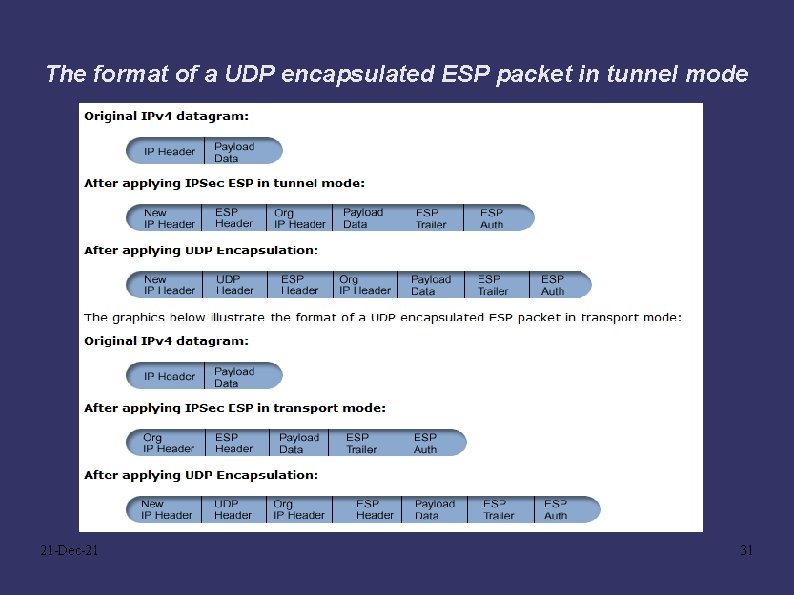
The format of a UDP encapsulated ESP packet in tunnel mode 21 -Dec-21 31
![Relevant RFCs list RFC 791 Internet Protocol DARPA Internet Program Protocol Specification Information Sciences Relevant RFCs list [RFC 791] Internet Protocol DARPA Internet Program Protocol Specification, Information Sciences](https://slidetodoc.com/presentation_image_h2/20962525a8364c20987d10029413ab05/image-30.jpg)
Relevant RFCs list [RFC 791] Internet Protocol DARPA Internet Program Protocol Specification, Information Sciences Institute, USC, September 1981. [RFC 1058] Routing Information Protocol, C Hedrick, Rutgers University, June 1988. [RFC 1483] Multiprotocol Encapsulation over ATM Adaptation Layer 5, Juha Heinanen, Telecom Finland, July 1993. [RFC 2401] S. Kent, R. Atkinson, Security Architecture for the Internet Protocol, RFC 2401, November 1998. [RFC 2407] D. Piper, The Internet IP Security Domain of Interpretation for ISAKMP, November 1998. [RFC 2474] K. Nichols, S. Blake, F. Baker, D. Black, Definition of the Differentiated Services Field (DS Field) in the IPv 4 and IPv 6 Headers, December 1998. [RFC 2475] S. Blake, D. Black, M. Carlson, E. Davies, Z. Wang, and W. Weiss, An Architecture for Differentiated Services, December 1998. [RFC 2481] K. Ramakrishnan, S. Floyd, A Proposal to Add Explicit Congestion Notification (ECN) to IP, January 1999. [RFC 2408] D. Maughan, M. Schertler, M. Schneider, J. Turner, Internet Security Association and Key Management Protocol (ISAKMP). [RFC 2409] D. Harkins, D. Carrel, Internet Key Exchange (IKE) protocol. [RFC 2401] S. Kent, R. Atkinson, Security Architecture for the Internet Protocol. 21 -Dec-21 32