Lecture 15 IPsec AH and ESP IPsec introduction



- Slides: 11

Lecture 15: IPsec AH and ESP • IPsec introduction: uses and modes • IPsec concepts – security association – security policy database • IPsec headers – authentication header (AH) – encapsulating security payload (ESP) 1

IPsec • IETF standard for real-time communication security – designed to work with both IPv 4 and IPv 6 • Cryptographic protection of the IP traffic (level 3), transparent to the user • main components: – Internet Key Exchange (IKE): IPsec key exchange protocol – Authentication Header (AH): Authentication of the IP packet (optional) – Encapsulating Security Payload (ESP): Encryption/authentication of the IP packet (optional) 2

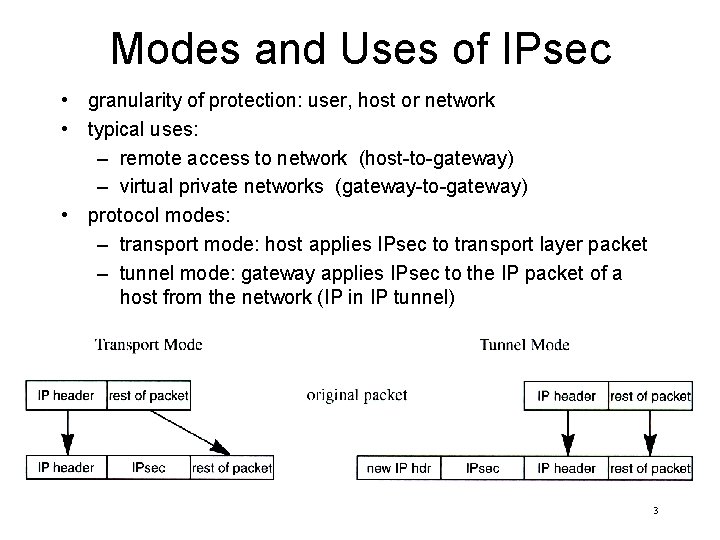
Modes and Uses of IPsec • granularity of protection: user, host or network • typical uses: – remote access to network (host-to-gateway) – virtual private networks (gateway-to-gateway) • protocol modes: – transport mode: host applies IPsec to transport layer packet – tunnel mode: gateway applies IPsec to the IP packet of a host from the network (IP in IP tunnel) 3

Security Association & Policy • Security Association (SA) – IPsec-protected connection (one-way) – specifies the encryption/auth. algorithm, key, etc. – established either “manually” or through IKE – identified by • security parameter index (SPI) • destination IP address • protocol identifier: (AH or ESP – more later) • Security Policy Database – specifies what kind of protection is applied to packets – matches IP packet to SA at source and destination, indexed by SPI – contains • AH information (auth. algorithm, key lifetime, etc. ) • ESP information (auth. /encryption algorithm, key lifetime, etc. ) • sequence number counter • anti-replay window (at the destination SA) • lifetime of the SA • others (protocol mode, path MTU, etc. ) 4

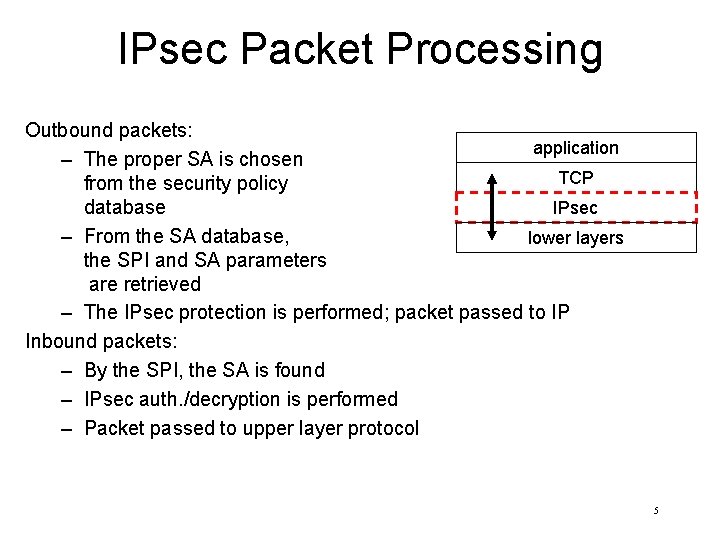
IPsec Packet Processing Outbound packets: application – The proper SA is chosen TCP from the security policy IPsec database – From the SA database, lower layers the SPI and SA parameters are retrieved – The IPsec protection is performed; packet passed to IP Inbound packets: – By the SPI, the SA is found – IPsec auth. /decryption is performed – Packet passed to upper layer protocol 5

Authentication Header (AH) • provides (optional) integrity protection (authentication) – for packet – some of the fields of IP header • the integrity check is provided by a cryptographic hash – MAC is included in the header • some fields of IP header are modified in transit hence cannot be covered by integrity check; these fields differ in IPv 4 and IPv 6 – mutable – modifiable in transit, not protected – immutable – constant, protected – mutable but predictable – changes but in a predictable manner – protected with values at receiver 6

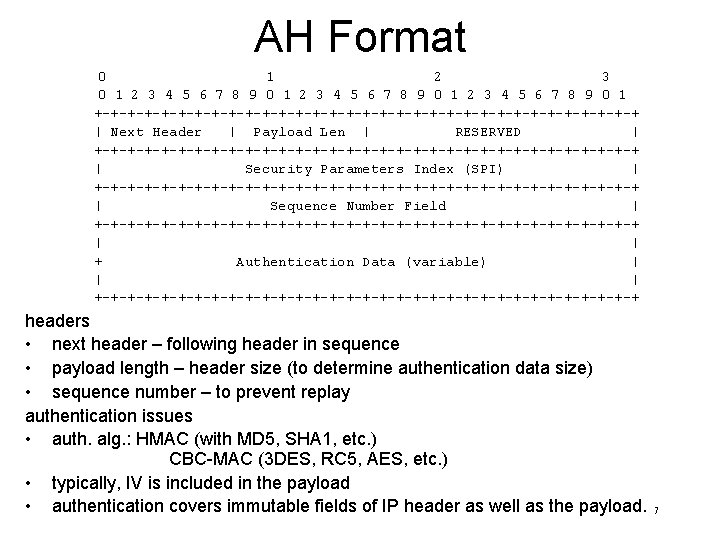
AH Format 0 1 2 3 4 5 6 7 8 9 0 1 +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Next Header | Payload Len | RESERVED | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Security Parameters Index (SPI) | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Sequence Number Field | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | | + Authentication Data (variable) | | | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ headers • next header – following header in sequence • payload length – header size (to determine authentication data size) • sequence number – to prevent replay authentication issues • auth. alg. : HMAC (with MD 5, SHA 1, etc. ) CBC-MAC (3 DES, RC 5, AES, etc. ) • typically, IV is included in the payload • authentication covers immutable fields of IP header as well as the payload. 7

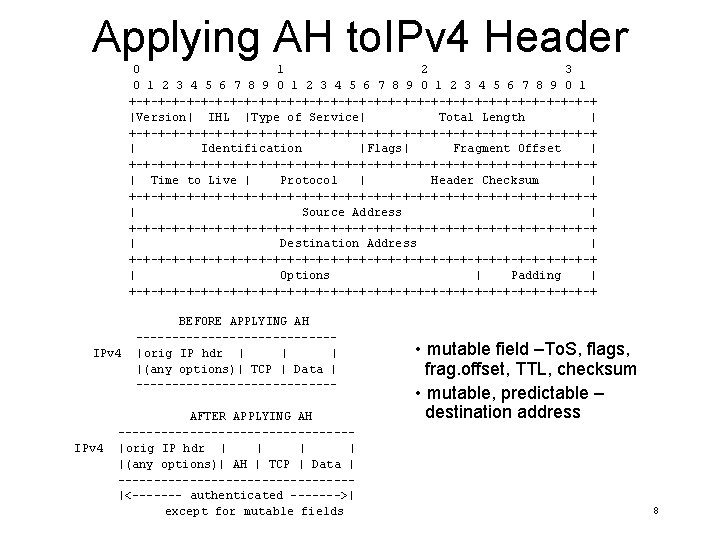
Applying AH to. IPv 4 Header 0 1 2 3 4 5 6 7 8 9 0 1 +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ |Version| IHL |Type of Service| Total Length | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Identification |Flags| Fragment Offset | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Time to Live | Protocol | Header Checksum | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Source Address | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Destination Address | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Options | Padding | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ IPv 4 BEFORE APPLYING AH --------------|orig IP hdr | |(any options)| TCP | Data | -------------- AFTER APPLYING AH ----------------|orig IP hdr | | |(any options)| AH | TCP | Data | ----------------|<------- authenticated ------->| except for mutable fields • mutable field –To. S, flags, frag. offset, TTL, checksum • mutable, predictable – destination address 8

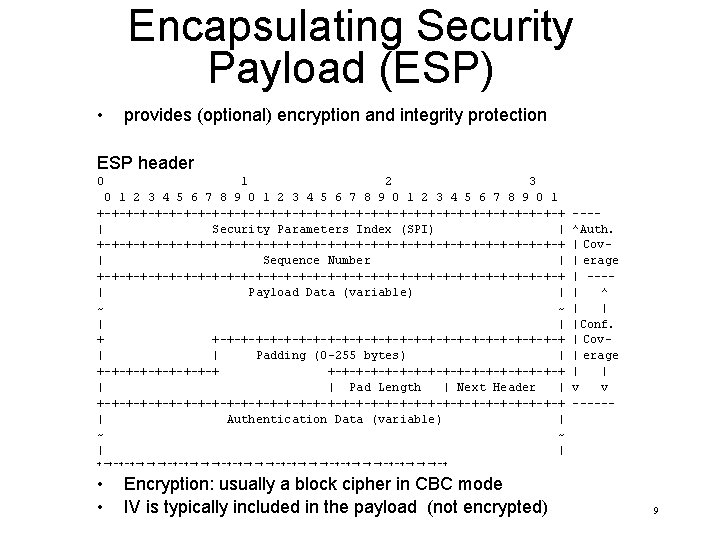
Encapsulating Security Payload (ESP) • provides (optional) encryption and integrity protection ESP header 0 1 2 3 4 5 6 7 8 9 0 1 +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Security Parameters Index (SPI) | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Sequence Number | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Payload Data (variable) | ~ ~ | | + +-+-+-+-+-+-+-+-+-+-+-+-+ | | Padding (0 -255 bytes) | +-+-+-+-+-+-+-+-+-+-+-+-+ | | Pad Length | Next Header | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Authentication Data (variable) | ~ ~ | | ---^Auth. | Cov| erage | ---| ^ | | |Conf. | Cov| erage | | v v ------ +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ • • Encryption: usually a block cipher in CBC mode IV is typically included in the payload (not encrypted) 9

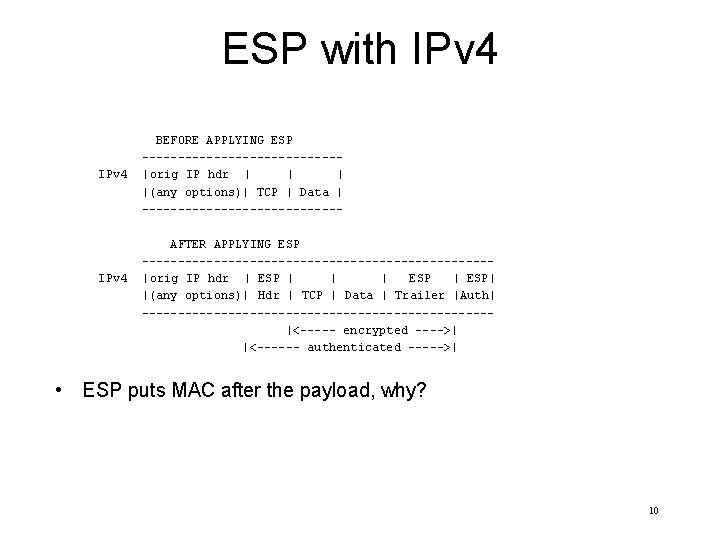
ESP with IPv 4 BEFORE APPLYING ESP --------------|orig IP hdr | |(any options)| TCP | Data | --------------AFTER APPLYING ESP ------------------------|orig IP hdr | ESP | | | ESP| |(any options)| Hdr | TCP | Data | Trailer |Auth| ------------------------|<----- encrypted ---->| |<------ authenticated ----->| • ESP puts MAC after the payload, why? 10

AH vs. ESP issues with AH • usefulness is doubtful (authentication is provided by ESP as well) • not efficient to compute (MAC is at the beginning) • wasted (unused) octets in the header • not compatible with network address translation (NAT) which modifies IP address • the need for immutable fields protections is unclear – ESP in tunneling mode can do it 11