Intrusion Detection System Marmagna Desai 520 Presentation Contents
![Intrusion Detection System Marmagna Desai [ 520 Presentation] Intrusion Detection System Marmagna Desai [ 520 Presentation]](https://slidetodoc.com/presentation_image_h2/71bcb8846867b49c3b415c58c5458812/image-1.jpg)












- Slides: 20
![Intrusion Detection System Marmagna Desai 520 Presentation Intrusion Detection System Marmagna Desai [ 520 Presentation]](https://slidetodoc.com/presentation_image_h2/71bcb8846867b49c3b415c58c5458812/image-1.jpg)
Intrusion Detection System Marmagna Desai [ 520 Presentation]

Contents Computer Security IDS - Introduction Intrusion Detection System Network System Network Based (NIDS) Host Based (HIDS) ID Expert Systems IDS Techniques Misuse Detection Anomaly Detection Immune System Approach Architecture Requirements Conclusion References Thanks

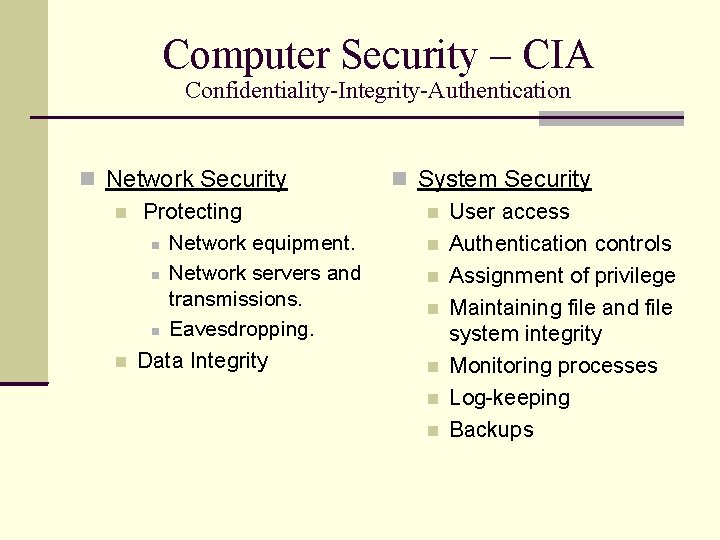
Computer Security – CIA Confidentiality-Integrity-Authentication Network Security Protecting Network equipment. Network servers and transmissions. Eavesdropping. Data Integrity System Security User access Authentication controls Assignment of privilege Maintaining file and file system integrity Monitoring processes Log-keeping Backups

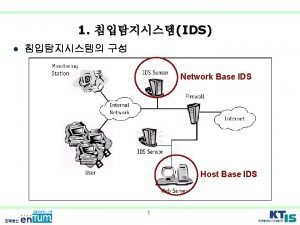
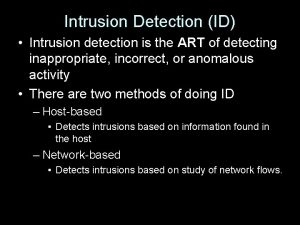
Intrusion Detection System IDS - Definition Monitors either a Network boundary (Network IDS) or a single host (Host IDS) in real-time, looking for patterns that indicate Attacks. Functional Blocks. . Sensor Monitor Resolver Controller

Sensor System Specific Data Gathering Component. Track Network traffic, Log files, System behaviour Monitor Components, Get Events from Sensor. Correlates Events against Behaviour-Model Produce Alerts. Resolver Determine Response against Alerts. E. g. Logging, Changing System Mechanism, Setting Firewall Rule etc. Controller - Coordination and Administration

Network IDS NIDS Sensors collect information from Network Connections. Uses Packet Sniffing on NIC in Promiscuous Mode. No Auditing / Logging required. Agents can introduced without affecting Data Source at NIC level. Detects Network Level Attacks (e. g. SYN Atk) Can NOT scan Protocols or Content of Network Traffic if encrypted.

Host IDS HIDS Sensors collect information reflecting the System Activity. Based on Operating System Audit Trails, Logs and Process Trees. User and Application Level Analysis Process Behaviour Analysis Operate in Encrypted Environments. Platform Specific, Large Overhead for OS and Higher Management/Deployment Costs

ID Expert Systems A set of System Tools Working in Coordination Users Behave in a Consistent Manner Behaviour can be Summarised in a Profile can be generated by Advanced Statistical Analysis. Oracle Database is used for Profiles. Provides Real-Time Response to Intrusion.

IDS Approaches Misuse Detection Models Abnormal behaviour E. G. HTTP request referring to the cmd. exe file Uses Pattern Matching of system setting and user activities against database of known attacks. (Signature Analysis) Highly Efficient – Tightly Defined Signature. Vulnerable to novel attacks.

Anomaly Detection Models Normal Behaviour E. g. Expected System Calls, generated by User Process (Root/Non-root). Statistical profiles for system objects are created by measuring attributes of normal use. Detects Novel and Complex attacks. Low Efficiency False Positive Legitimate action classified as Anomalous.

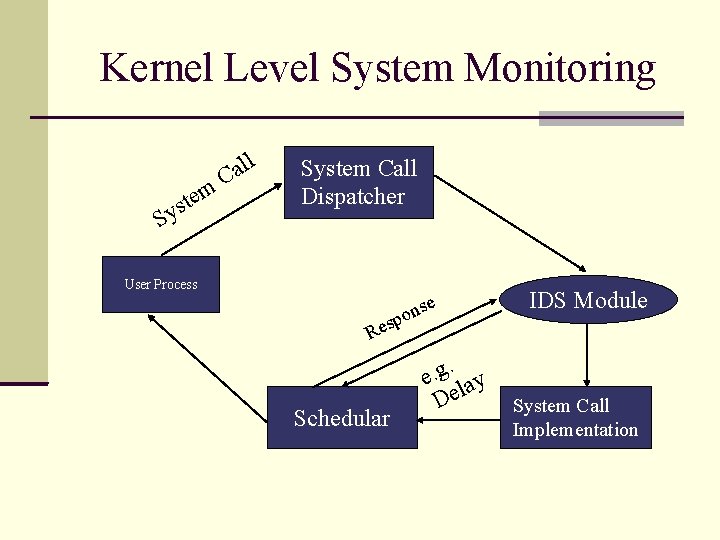
Anomaly Detection - continued Immune System Approach Models in terms of Sequence of System Calls. Sequence for Normal Behaviour Error Condition Anomaly Kernel-Level System-Call Monitoring. E. g. “exec “ System call produces trace in all above situations.

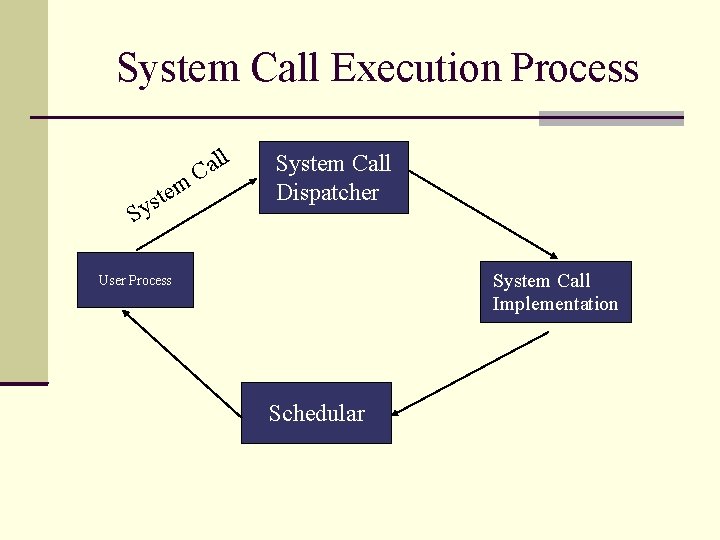
System Call Execution Process m e t ys S ll a C System Call Dispatcher System Call Implementation User Process Schedular

Kernel Level System Monitoring m e t ys S ll a C System Call Dispatcher User Process se n o p s Re Schedular . e. g lay De IDS Module System Call Implementation

Architecture Monolithic Single Application contains sensor, monitor, resolver and controller Most Simplest Architecture, unable to detect attack made by distributed normal events. Hierarchic Resolver and Controller at root of hierarchy. Monitors at sub-system (logical group) level. Sensors at Node-Level Centralised controller correlates information from different Monitors and Resolver take

Architecture – continued Agent Based Distributed Sensors/Monitors/Resolver and Controller. Multi-Hierarchy of Monitors High Scalability Recently used in various IDS.

Requirements Accuracy Prevention, not just detection Broad attack coverage Analyze all relevant traffic Highly granular detection and response Sophisticated forensics and reporting Maximum sensor uptime Wire-speed performance

Requirements. . . Accuracy Reduced False +ve and -ve Thorough Protocol Analysis Prevention Real Time Prevention Reconfiguration and Response Self Learning Profiles Broad Attack Coverage Protects against all Attacks

Requirements. . . Analyze all relevant traffic (NIDS) Deploy IDS to suit varying Networks Topology Granular Detection and Response One size does not fit all. Forensic and Reporting Extensive Historic Analysis and Report Wire-Speed Multi – Giga bit Performance

Conclusion IDS will merge all Network components and tools which exist today, into a complete and cooperative system, dedicated to keeping networks Stable and Secure. Distributed elements performing specific jobs. Hierarchical correlation and analysis. Novel approaches like AI, Data-Mining etc.

Thank You!!
 Open source network intrusion detection system
Open source network intrusion detection system Bro ids hardware requirements
Bro ids hardware requirements Common intrusion detection framework
Common intrusion detection framework Intrusion detection systems (ids)
Intrusion detection systems (ids) Ids sensors
Ids sensors Fiber perimeter intrusion detection systems
Fiber perimeter intrusion detection systems Infrasonic intrusion detection
Infrasonic intrusion detection Wireless intrusion prevention
Wireless intrusion prevention Configure ios intrusion prevention system (ips) using cli
Configure ios intrusion prevention system (ips) using cli Ips intrusion
Ips intrusion Dts expert 500
Dts expert 500 Cidb pps requirement
Cidb pps requirement Csc 520
Csc 520 Kni 520
Kni 520 W= fxd
W= fxd 12vac35-105-160
12vac35-105-160 Bio 520
Bio 520 Aae 520
Aae 520 Aae 520
Aae 520 Aerodynamics
Aerodynamics Arry-520
Arry-520