Information Security or Identity and Access Management Tom




















- Slides: 33

Information Security or Identity and Access Management Tom Barton, University of Chicago Christopher Misra, University of Massachusetts April 2013

Session Abstract Information security shares a complex and interrelated space with identity and access management. IAM forms the basis for many of the other security controls we deploy; however, often there are gaps in understanding or even adversarial relationships between the responsible parties. This session will discuss and explore approaches to solving this problem. April 2013 Security Professionals 2

Introduction § Our discipline has slowly matured from chasing bots to implementing controls as part of a program • ISO 27002, NIST 800 -53, etc… § Identity and Access Management has matured on a parallel path from password changes to complex business systems • Shibboleth, Grouper § The intersection of these spaces does not always harmonize (yet…) April 2013 Security Professionals 3

Common Goals § Security services traditionally focus on preventing badness • protective, defensive and reactive tools and techniques. § Middleware provide infrastructure services that enhance security • identification, authentication, and authorization. § A comprehensive security architecture is necessary to align these services to meet an organization's security needs. § We are trying to solve many of the same problems April 2013 Security Professionals 4

Current Threat Environment § We have not solved all (or even most) of our information security problems • And we should all remain gainfully employed for a long time doing so…. § However, the environment continues to change. • Everyone wants their own application, local or hosted • Those who operate these applications frequently do not have a strong security background • Assignment of privilege is decentralized and often poorly managed • Audit of privilege is limited except in the highest visibility applications April 2013 Security Professionals 5

IAM as an Information Security Control § Who provisions access to your critical applications? • By hand? • How secure are those provisioning applications? • Can you locate and parse the logs and audit trails? § Applications and authentication services generate a lot of logs • Can you find these logs? • Can you correlate across these disparate applications and authentication logs? • Can you further correlate these applications against network-centric data sources? April 2013 Security Professionals 6

Data Release and Cloud-based Applications § Has your campus defined data owners for sensitive data elements or workflows? • Who can approve the release of student data to a cloud based service? § Is there a catalog defining the System of Record for these data? § Does Information Security have any engagement and/or approval authority in the process? April 2013 Security Professionals 7

Opinion time… § Security and Middleware staff need to be engaged with IAM design and implementations • Working with them now may both prevent bad things and even facilitate good things • We are probably trying to solve some of the same problems • IAM is just another control § Educating our community about the drivers is in our collective interest • Preventing data leakage from poorly managed applications and authorizations April 2013 Security Professionals 8

Case Study: University of Massachusetts § Organizational Structure § Operational Practices § Where we are effective § Challenges April 2013 Security Professionals 9

UMass: IAM and Organization Structures § Information Security reports directly to my Associate CIO role • Security program rollout, Incident response, Forensics, Firewalls, etc. § Identity Management is spread across two groups; Enterprise Services (ES) and Administrative Computing (ACSO) • ES also reports to me, but in a different role. § ACSO is responsible for our People. Soft instance which holds all person and account So. R data § ES is responsible for Kerberos, LDAP, RADIUS, Shibboleth deployment and operations April 2013 Security Professionals 10

UMass: Operational Practices § Our accounts and groups provisioning data are written in People. Tools and stored in Peoplesoft (oracle DB) § Provisioning occurs via a RESTful transport from a DB view (along with triggers) § Provisioning code is PERL based and interacts with applications and services using Service Handlers § Service Handlers manage passwords, LDAP objects, account provisioning and deprovisioning • Often run by the service owners directly April 2013 Security Professionals 11

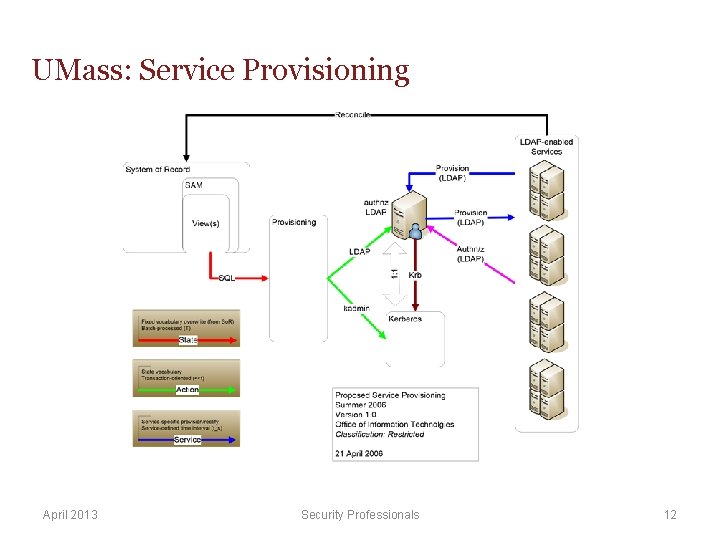
UMass: Service Provisioning April 2013 Security Professionals 12

UMass: Authentication as an Audit artifact § Using this data-driven provisioning approach permits audit artifact creation through log • All provisioning actions have a system of record § All LDAP and RADIUS logs are directed to our SIEM (Qradar) § Shibboleth logs (extensively), but parsing those logs is not for the faint of heart April 2013 Security Professionals 13

UMass: Approaches to bridge the gap… § Given the distributed nature of my organization, I use the following approach to ensure alignment between Info. Sec and IAM • Authentication and authorization system architecture changes require Information Security approval • Data release for cloud-services requires data owner and Information Security approval • Information Technology procurement requires information security approval § The compliance responsibility fall to Info. Sec, the operations fall to Enterprise Services • I am concerned as to how long this approach will scale. April 2013 Security Professionals 14

UMass: Challenges § Web application authentication log analysis is exceptionally challenging (still) • The more complex and multi-tiered the application, the longer it takes. • We still need my ES staff to explain how it all works • Load balancers make the problem worse • Gain some redundancy, lose some fidelity § The compliance burden on Info. Sec has grown exponentially in the last 2 years. • Aside from the issues here, PCI-DSS, ITAR/EAR, TCP approvals, IRB reviews, etc. April 2013 Security Professionals 15

Topics requiring more discussion… § Federations need to be understood in the context of operational security needs • How aware security staff of current federation activities on your campus? • See recent edu. Roam discussions… § IAM is yet another technology in our security toolkits • Integrating business processes with security requirements • Authentication and authorization are a necessary, but insufficient, condition for secure applications April 2013 Security Professionals 16

Topics requiring more discussion § Audit and log correlation will allow us to maintain situational awareness • In our increasingly complex environments • Additional abstraction layers is rendering many traditional detective techniques less effective • Orchestrating logs across systems provides visibility that many of us don’t currently have § Privilege management • Assignment of authorizations places more of our data at risk of disclosure • A next step in incident handling April 2013 Security Professionals 17

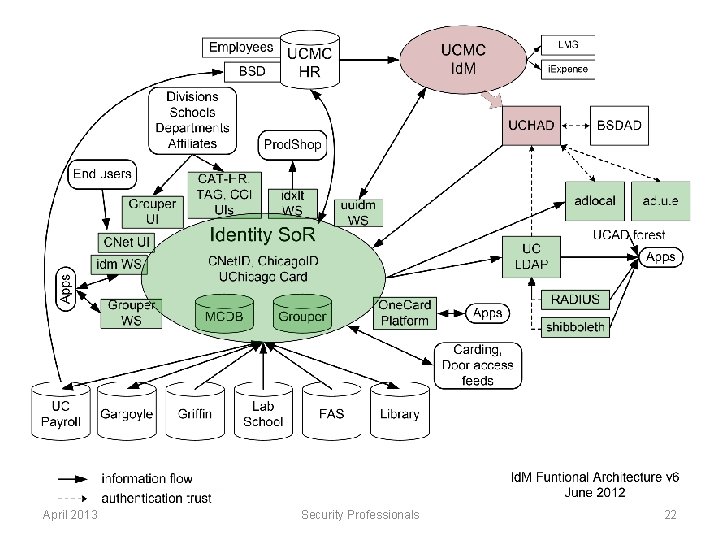
Case Study: University of Chicago § § Organizational strategy IAM picture An access management service is a Good Thing! Why you need Identity Assurance § Me § Senior Director & CISO reporting to CIO § Internet 2 middleware leadership § Grouper § In. Common Federation Technical Advisory Committee § Identity Assurance Framework April 2013 Security Professionals 18

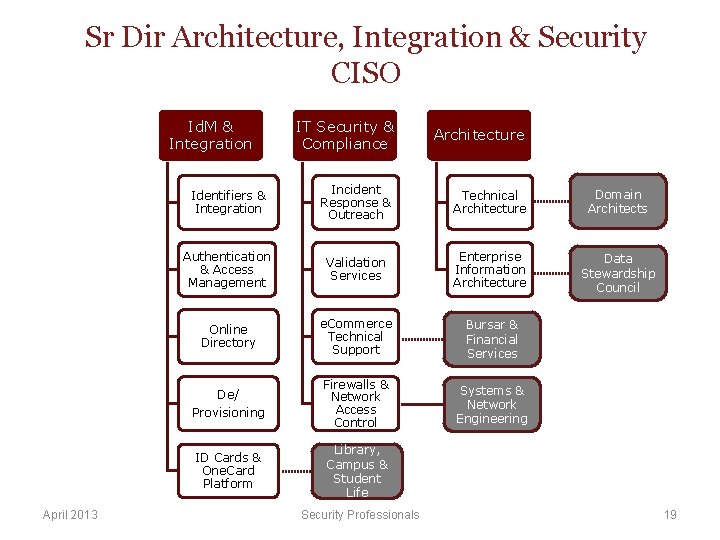
Sr Dir Architecture, Integration & Security CISO Id. M & Integration April 2013 IT Security & Compliance Architecture Identifiers & Integration Incident Response & Outreach Technical Architecture Domain Architects Authentication & Access Management Validation Services Enterprise Information Architecture Data Stewardship Council Online Directory e. Commerce Technical Support Bursar & Financial Services De/ Provisioning Firewalls & Network Access Control Systems & Network Engineering ID Cards & One. Card Platform Library, Campus & Student Life Security Professionals 19

Security strategies need all three pieces § Data Usage Request process • Architecture flywheels Data Stewardship Council (DSC) • IAM Business Analyst supports process • IT Security kicked it off with DSC data classification § Network access • Role-based: IT Security using IAM services § Identity Assurance • In. Common Silver: IAM + IT Security • MFA: IAM + IT Security § Technical Architecture • Participation by Domain Leads in all areas • Run by Architecture • Almost all reviews have IT Security & IAM aspects April 2013 Security Professionals 20

IAM highlights § Real-time integration with Medical Center IAM • Unified authentication across all services § Delegation • Credentials (accounts, ID Cards) • Groups for access management § De/Provisioning • Campus, cloud § Accounts are (almost) never deactivated • We’ve sufficiently mitigated the risk with access management instead April 2013 Security Professionals 21

April 2013 Security Professionals 22

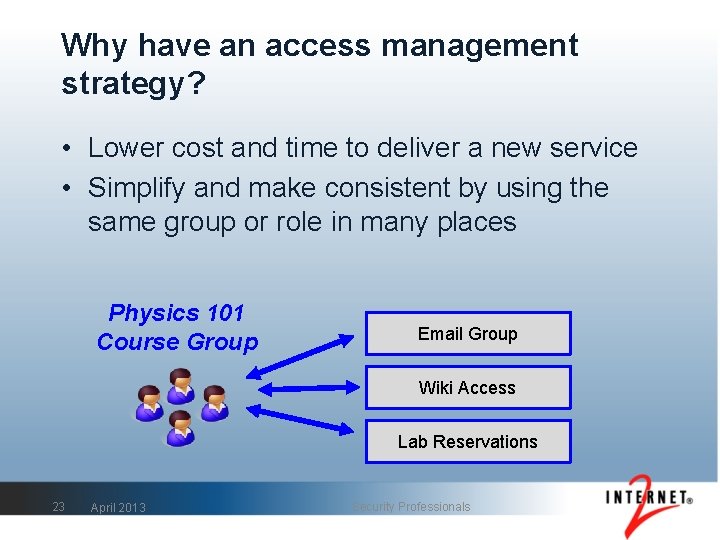
Why have an access management strategy? • Lower cost and time to deliver a new service • Simplify and make consistent by using the same group or role in many places Physics 101 Course Group Email Group Wiki Access Lab Reservations 23 April 2013 Security Professionals

Additional benefits of access management • Empower the right people to manage access. Take central IT out of the loop. • See who can access what, with a report rather than a fire drill 24 April 2013 Security Professionals

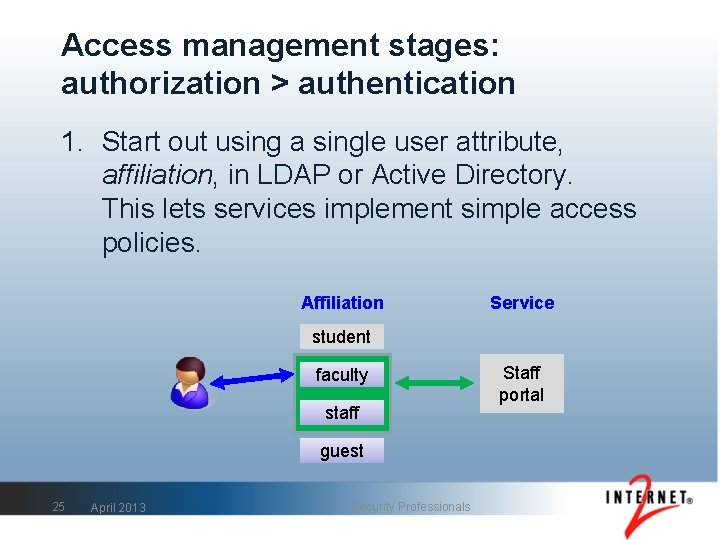
Access management stages: authorization > authentication 1. Start out using a single user attribute, affiliation, in LDAP or Active Directory. This lets services implement simple access policies. Affiliation Service student faculty staff guest 25 April 2013 Security Professionals Staff portal

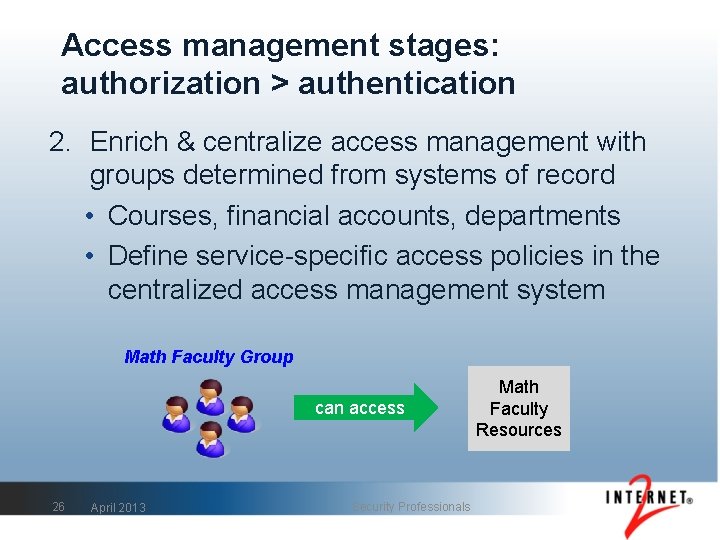
Access management stages: authorization > authentication 2. Enrich & centralize access management with groups determined from systems of record • Courses, financial accounts, departments • Define service-specific access policies in the centralized access management system Math Faculty Group can access 26 April 2013 Security Professionals Math Faculty Resources

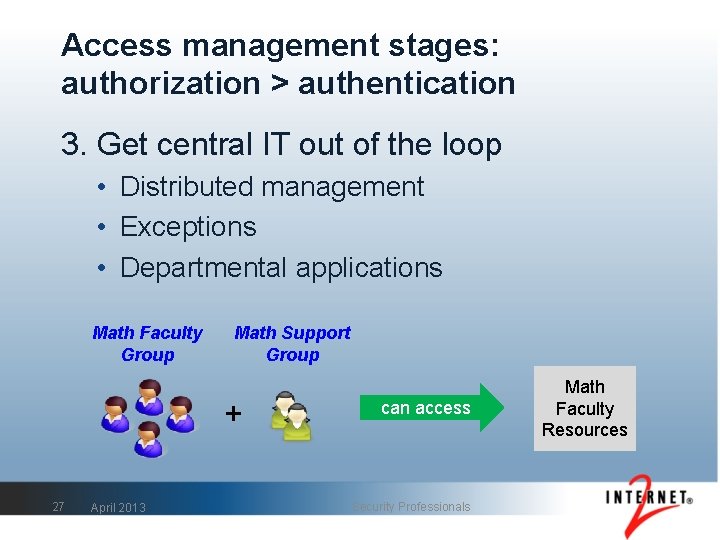
Access management stages: authorization > authentication 3. Get central IT out of the loop • Distributed management • Exceptions • Departmental applications Math Faculty Group Math Support Group + 27 April 2013 can access Security Professionals Math Faculty Resources

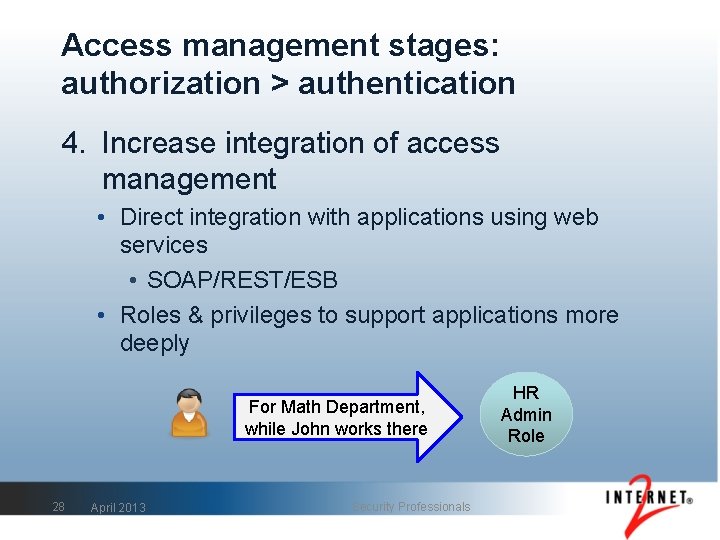
Access management stages: authorization > authentication 4. Increase integration of access management • Direct integration with applications using web services • SOAP/REST/ESB • Roles & privileges to support applications more deeply For Math Department, while John works there 28 April 2013 Security Professionals HR Admin Role

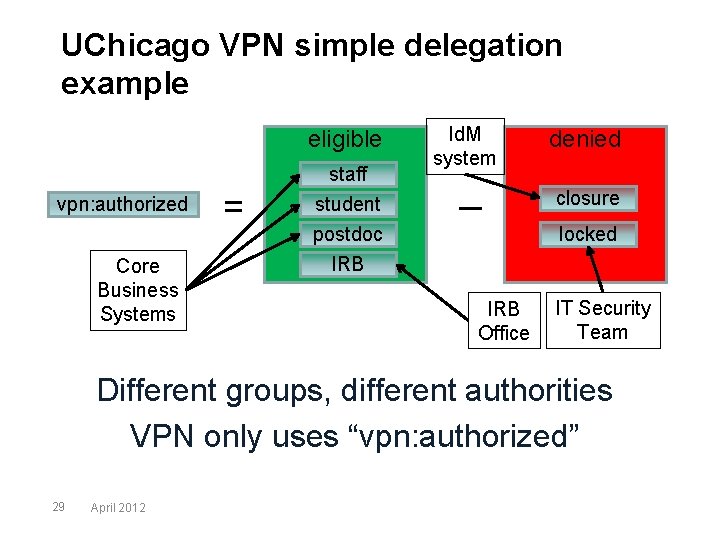
UChicago VPN simple delegation example eligible vpn: authorized Core Business Systems = staff student postdoc IRB Id. M system denied closure locked IRB Office IT Security Team Different groups, different authorities VPN only uses “vpn: authorized” 29 April 2012

Are your credentials good enough to protect access to sensitive data? § What standard do you use to know? § NIST Levels of Assurance 1 – 4 § In. Common Bronze and Silver § Specifications written for US Higher Eds § Approved by US government for access to federal agency services § Approved by International Grid Trust Federation for access to national & international HPC 30

Getting Past Passwords are bad and will get worse. We know! Strategy and choices 1. Use stronger credentials where you can 2. Improve passwords until you no longer need them • Bronze – satisfactory password management • Silver – good password management or stronger creds 31

In. Common Silver at UChicago § Audit of IAM processes & systems underway § Users opt-in • • • Picture ID at ID Card Office Annual password reset Password at least 12 characters (passphrases coming) Register cell phone or external email Password lockout applies § PIs, unit heads may ask their users to opt-in 32

Questions? April 2013 Security Professionals 33