Identity and Access Management Futures and Roadmap Andreas


























- Slides: 41

Identity and Access Management - Futures and Roadmap Andreas Luther Group Program Management Identity and Access - MIIS Microsoft Corporation

Situation Increasingly connected systems Connections span technical, org boundaries Distinctions blur - customer, partner, employee, intranet, Internet Demand for business process integration Clear business drivers around security, cost efficiency, regulatory compliance Issues around policy, compliance, reporting Rapid rise of threats to online safety Phishing, pharming, phraud Concerns over privacy, tracking

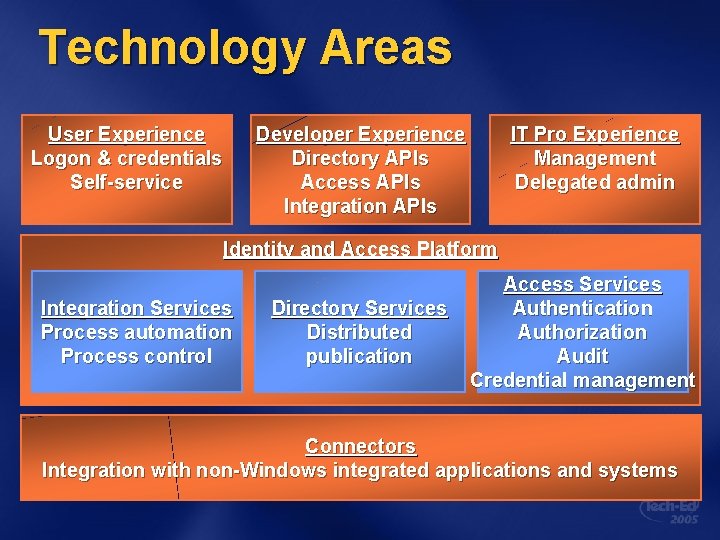
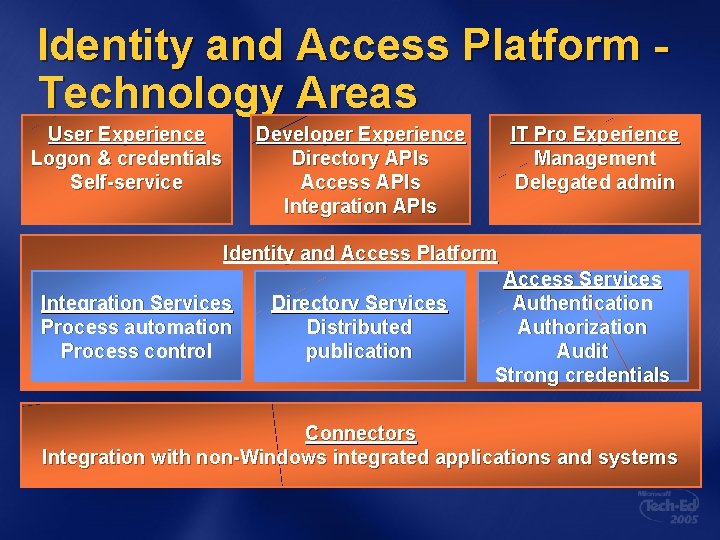
Technology Areas User Experience Logon & credentials Self-service Developer Experience Directory APIs Access APIs Integration APIs IT Pro Experience Management Delegated admin Identity and Access Platform Integration Services Process automation Process control Directory Services Distributed publication Access Services Authentication Authorization Audit Credential management Connectors Integration with non-Windows integrated applications and systems

Microsoft’s Strategy Add native support for interoperable federated identity to Active Directory using web services Build on Microsoft Identity Integration Server as platform for process-driven management of identities and entitlements Evolve and refine Active Directory directory services

What is a Digital Identity? A set of claims one subject makes about another Many identities for many uses Required for transactions in real world and online

Active Directory Federation Services Federated web single sign on WS-Federation Passive Requestor Profile Support SAML token, claims as SAML assertions Integrated with Windows SSO Support Windows Integrated Security and native claims-based identity Transform claims into SIDs for Windows apps Enable web apps to natively consume claims Authorization Manager integration Delivered in Windows Server 2003 R 2

Process-driven management of identities and entitlements

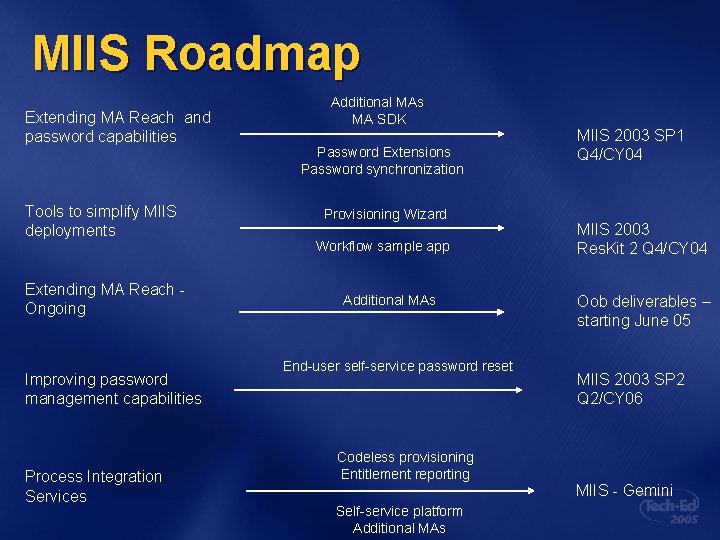
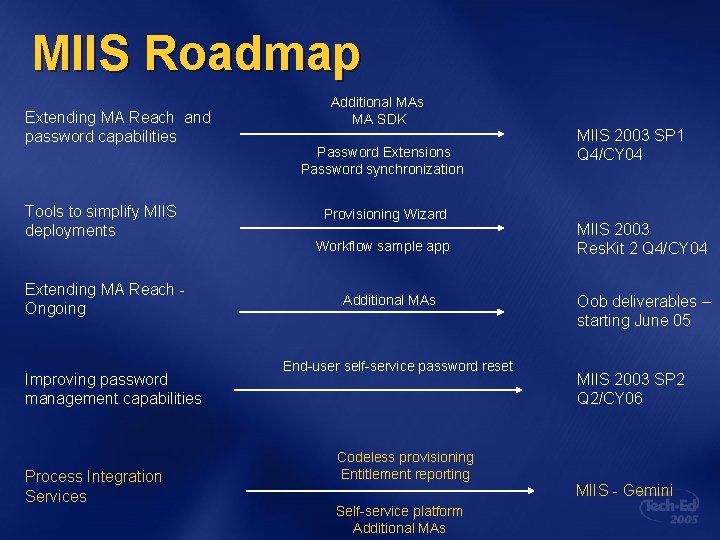
MIIS Roadmap Extending MA Reach and password capabilities Tools to simplify MIIS deployments Extending MA Reach Ongoing Improving password management capabilities Process Integration Services Additional MAs MA SDK Password Extensions Password synchronization Provisioning Wizard Workflow sample app Additional MAs End-user self-service password reset Codeless provisioning Entitlement reporting Self-service platform Additional MAs MIIS 2003 SP 1 Q 4/CY 04 MIIS 2003 Res. Kit 2 Q 4/CY 04 Oob deliverables – starting June 05 MIIS 2003 SP 2 Q 2/CY 06 MIIS - Gemini

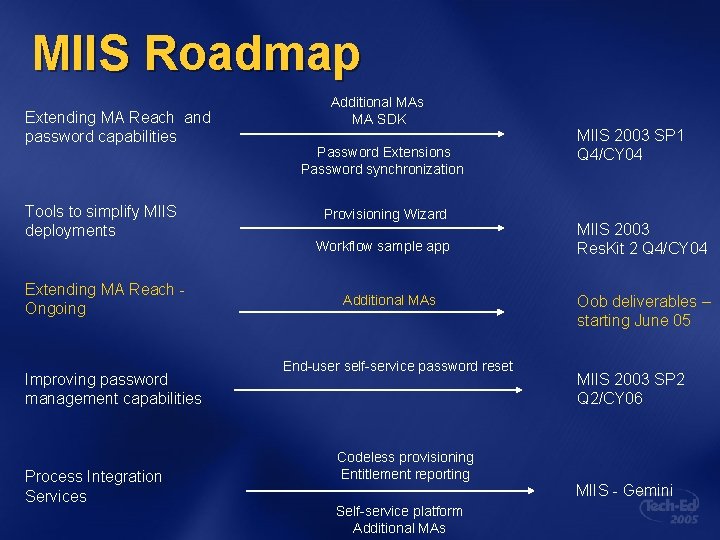
MIIS Roadmap Extending MA Reach and password capabilities Tools to simplify MIIS deployments Extending MA Reach Ongoing Improving password management capabilities Process Integration Services Additional MAs MA SDK Password Extensions Password synchronization Provisioning Wizard Workflow sample app Additional MAs End-user self-service password reset Codeless provisioning Entitlement reporting Self-service platform Additional MAs MIIS 2003 SP 1 Q 4/CY 04 MIIS 2003 Res. Kit 2 Q 4/CY 04 Oob deliverables – starting June 05 MIIS 2003 SP 2 Q 2/CY 06 MIIS - Gemini

MIIS 2003 – Oob MA Deliverables Mainframe MAs RACF: June 05 ACF 2, TS: Fall 05 ERP MAs SAP, People. Soft: Fall 05 Generic LDAP MA Considered for Gemini release

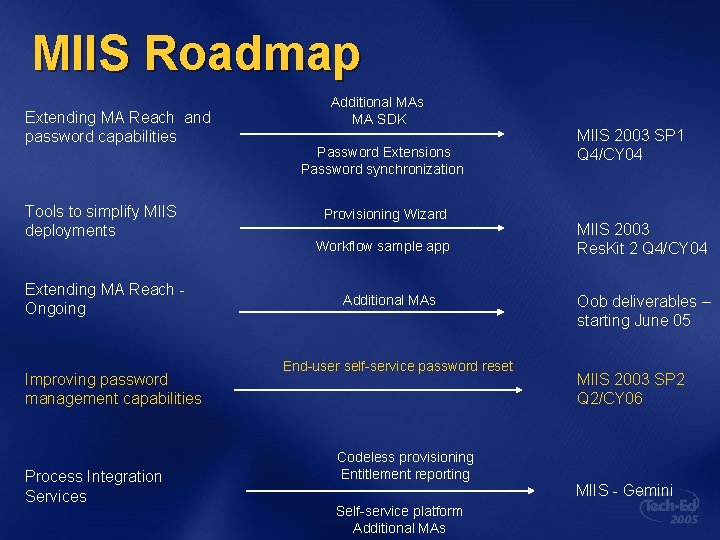
MIIS Roadmap Extending MA Reach and password capabilities Tools to simplify MIIS deployments Extending MA Reach Ongoing Improving password management capabilities Process Integration Services Additional MAs MA SDK Password Extensions Password synchronization Provisioning Wizard Workflow sample app Additional MAs End-user self-service password reset Codeless provisioning Entitlement reporting Self-service platform Additional MAs MIIS 2003 SP 1 Q 4/CY 04 MIIS 2003 Res. Kit 2 Q 4/CY 04 Oob deliverables – starting June 05 MIIS 2003 SP 2 Q 2/CY 06 MIIS - Gemini

MIIS 2003 SP 2 Password Self Service Reset Problem: Users forget passwords Downtime reduces employee productivity High help desk costs associated with reset requests Solution: Password self service reset enables employees to reset forgotten passwords Self Service Password Reset planned for MIIS SP 2 Leverages MIIS System connectivity Account management User Registration Proactive enrollment or help desk can force users to enroll when password is forgotten Q&A authentication configuration is very flexible to accommodate different organizations security requirement Q&A can be exposed to Help Desk to authenticate callers Significant update to web applications shipped with MIIS 2003 Working with Speech Server team to enable phone password reset

MIIS Roadmap Extending MA Reach and password capabilities Tools to simplify MIIS deployments Extending MA Reach Ongoing Improving password management capabilities Process Integration Services Additional MAs MA SDK Password Extensions Password synchronization Provisioning Wizard Workflow sample app Additional MAs End-user self-service password reset Codeless provisioning Entitlement reporting Self-service platform Additional MAs MIIS 2003 SP 1 Q 4/CY 04 MIIS 2003 Res. Kit 2 Q 4/CY 04 Oob deliverables – starting June 05 MIIS 2003 SP 2 Q 2/CY 06 MIIS - Gemini

Process-driven management of identities and entitlements

Identity and Access Platform Technology Areas User Experience Logon & credentials Self-service Developer Experience Directory APIs Access APIs Integration APIs IT Pro Experience Management Delegated admin Identity and Access Platform Integration Services Process automation Process control Directory Services Distributed publication Access Services Authentication Authorization Audit Strong credentials Connectors Integration with non-Windows integrated applications and systems

Integration Services - Business Drivers and Requirements Strengthen security Enforcement of “Least User Access” as required by SOAX, HIPAA etc. Automated de-provisioning of accounts and entitlements Central auditing Increasing operational efficiency Automation: Provisioning and de-provisioning based on business rules Self-service applications to empower business owners to make entitlement decisions Online business enablement Self-service applications for user registration and account management Regulatory requirements Workflow to model controls State based identity management system to enforce use of controls and compliance Central auditing allows tracking of in- and out of compliance situations

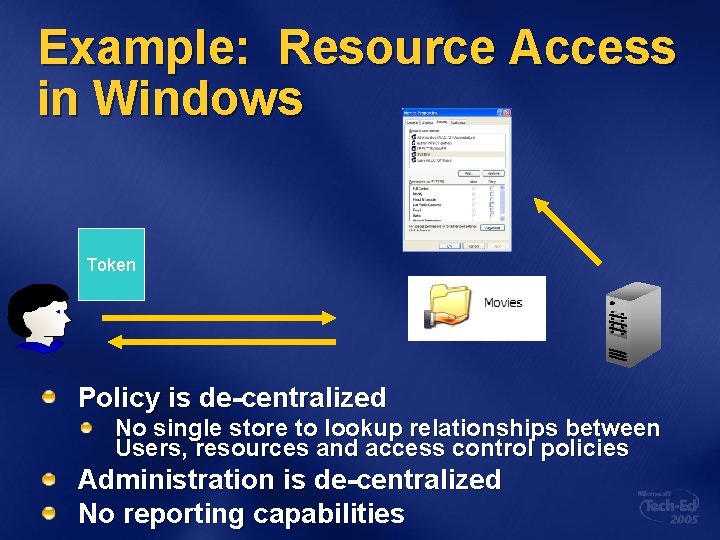
Example: Resource Access in Windows Token Policy is de-centralized No single store to lookup relationships between Users, resources and access control policies Administration is de-centralized No reporting capabilities

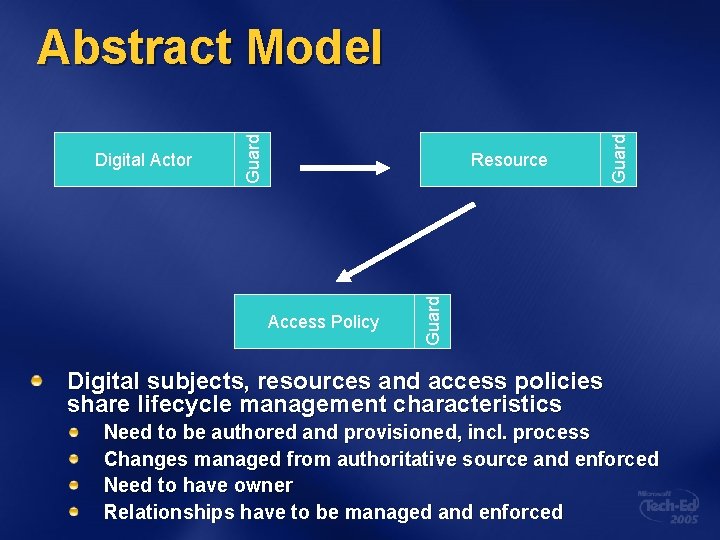
Access Policy Guard Resource Guard Digital Actor Guard Abstract Model Digital subjects, resources and access policies share lifecycle management characteristics Need to be authored and provisioned, incl. process Changes managed from authoritative source and enforced Need to have owner Relationships have to be managed and enforced

Requirements for Process Integration Service Provisioning and lifecycle management of digital subjects Provisioning and lifecycle management of resources File shares, Share. Point sites Provisioning and lifecycle management of access control policies ACLs, Share. Point access rights, web services Workflow to model compliance controls Enforce compliance and flag out-of-compliance situations Central auditing system Audit all aspects of provisioning and lifecycle management (state auditing) Trigger actions (workflows) if out-of-compliance situations are found Integrate with forensic auditing systems (ACS, MOM) Complete set of APIs for any aspects of entitlement provisioning and process integration service configuration

MIIS Evolves into Process Integration Services Digital actors, resources and policies are all identities State-based Metadirectory is the right approach Discovery of identities through Management Agents Aggregation of identity information in central store Use business rules to manage relationships between identities Periodically validate compliance of relationships by comparing existing relationships with model through synchronization Enforce compliance through synchronization Audit all relationship changes MIIS 2003 has the right architecture Future versions will add workflow, business rules authoring, control authoring and auditing

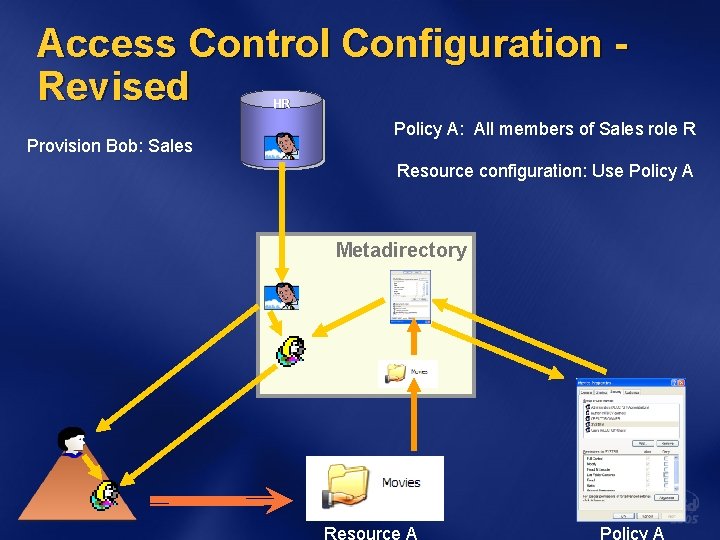
Access Control Configuration Revised HR Provision Bob: Sales Policy A: All members of Sales role R Resource configuration: Use Policy A Metadirectory Resource A Policy A

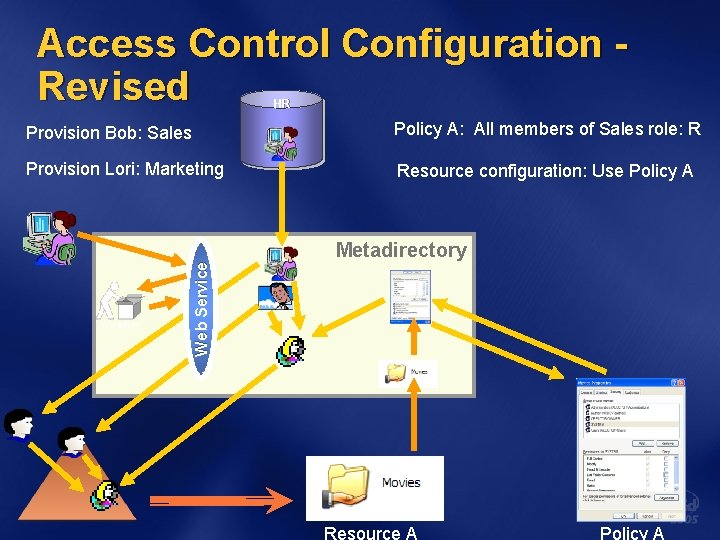
Access Control Configuration Revised HR Policy A: All members of Sales role: R Provision Lori: Marketing Resource configuration: Use Policy A Web Service Provision Bob: Sales Metadirectory Resource A Policy A

Benefits of this Model Centralized management of digital subjects, resources and policies Data driven Application driven (Self-Service or delegated) Heterogeneous environments Workflow allows modeling of controls Compliance validation and enforcement State in Metadirectory is authoritative If administrator adds Sally to ACL on \movies, Metadirectory resets ACL and triggers warning Use of controls Centralized auditing and reporting

Auditing and Reporting All operations create audit entries Including approval steps in workflows Reports answer the following questions: Who had access to \movies on 6/2/05 and why? Bob, member of sales role Who had access to \movies on 6/5/05 and why? Bob, member of sales role Lori, because Bob approved request What resource did Lori have access to on 6/5/05 and why? \movies, because Bob approved request What resources were protected by policy A on 6/5/05? \movies What resources can be accessed by Sales members? \movies

MIIS Gemini Add core functionality required for Process Integration Services Rich workflow Centralized auditing Self-service application platform with integrated workflow and auditing Computed attributes Entitlement management based on organizational roles Expose new functionalities to IT Pros and end users Identity manager console for declarative entitlement management Self-service applications Expose self-service application interfaces for ISVs and corporate developers

Gemini Provisioning Features Integrated Toolset to Manage the Lifecycle of Digital Identities and Entitlements Declarative Provisioning UI to define rules when and where entitlements are created plus templates how they are created No more coding required Self-Service Platform Web service interfaces to build self-service applications E. g. , account requests, entitlement requests, password resets, group membership request Tight integration with VS to develop Self-Service apps Application MV Group Management Improvements Multi-forest, computed groups, Autogroup Unified workflow model Declarative provisioning, self-service apps, existing synchronization framework and group management need workflow Single model to manage workflows

Gemini Provisioning Features Integrated Toolset to Manage the Lifecycle of Digital Identities and Entitlements Ready to use “Out of the Box Self-Service Applications” Only minimal configuration required Entitlement manager, Autouser, Autogroup Auditing / compliance checking All provisioning operations are audited (requests, approvals, changes in CD) Un-authorized changes in CD can be detected and audited; workflow can be kicked off Resource and policy management

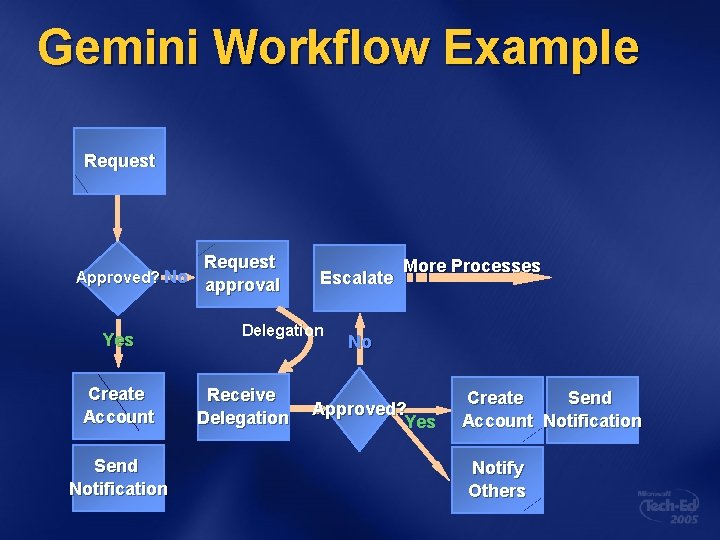
Gemini Workflow Example Request Approved? No Yes Create Account Send Notification Request approval Escalate Delegation Receive Delegation More Processes No Approved? Yes Create Send Account Notification Notify Others

The Evolution of Directory Services

Active Directory Broad usage 86% of US, 57% of enterprises >500 PCs worldwide running Active Directory * Performance at scale Scale out: 1000+ servers Scale up: deployments at 20 M+ users Flexibility: AD and ADAM Centralized or distributed physical deployment Centralized or distributed logical management Shared across applications or dedicated to a specific application Interop: Unix/Linux SSO via Vintela, Centrify * Source: Microsoft internal survey, spring 2005

Domain Mode Windows Server 2003 R 2 Unix compatibility schema ADMT v 3 (web download) Longhorn Server Read-only DC: reduced physical security requirements, simplified manageability Restartable AD: reduce DC reboots DC on Server Core: minimize surface area DC/Domain Admin role separation

Application Mode Windows Server 2003 ADAM download LDAP-only mode of Active Directory with independent configuration Identical performance at scale Windows Server 2003 R 2 ADAM included in OS distribution One-way AD-to-ADAM sync: eliminate need for MIIS (or IIFP) in simple scenarios Longhorn Server: same as R 2

The Next Generation of Digital Identity

Threats to Online Safety The Internet was built without a way to know who and what you are connecting to Everyone offering Internet service has come up with workaround – a patchwork of one-offs Inadvertently taught people to be phished Greater use and greater value attract professional international criminal fringe Understand exploit weaknesses in patchwork Phishing and pharming at 1000% CAGR

From Patchwork to Fabric Little agreement on what identity layer is, or how it should be run Digital identity related to contexts Partial success in specific domains (SSL, Kerberos) Enterprises, governments, verticals prefer one-offs to loss of control Individual is also a key player No simplistic solution is realistic Consider cross cultural, international issues Diverse needs of players means need to integrate multiple constituent technologies

“The Laws of Identity” 1. User control and consent 2. Minimal disclosure for a defined use 3. Justifiable parties 4. Directional identity 5. Pluralism of operators and technologies 6. Human integration 7. Consistent experience across contexts Join the discussion at www. identityblog. com

Identity Metasystem We need a unifying “Identity metasystem” Protect applications from identity complexities Allow digital identity to be loosely coupled: multiple operators, technologies, and implementations Not first time we’ve seen this in computing Abstract display services made possible through device drivers Emergence of TCP/IP unified Ethernet, Token Ring, Frame Relay, X. 25, even the not-yetinvented wireless protocols

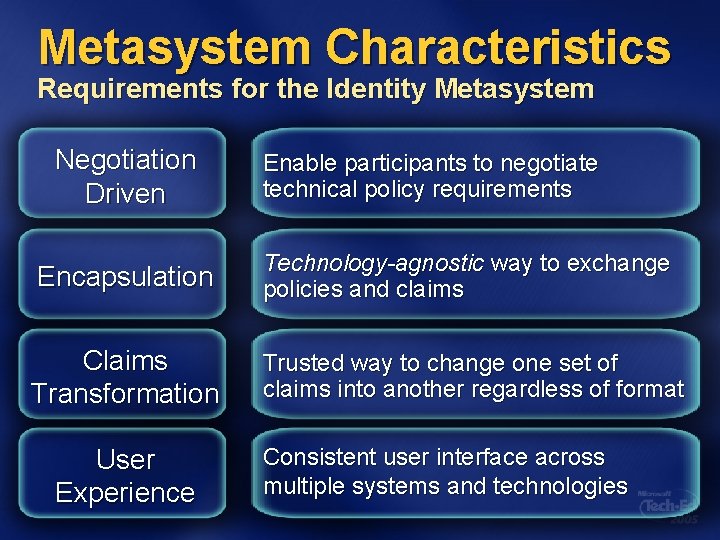
Metasystem Characteristics Requirements for the Identity Metasystem Negotiation Driven Enable participants to negotiate technical policy requirements Encapsulation Technology-agnostic way to exchange policies and claims Claims Transformation Trusted way to change one set of claims into another regardless of format User Experience Consistent user interface across multiple systems and technologies

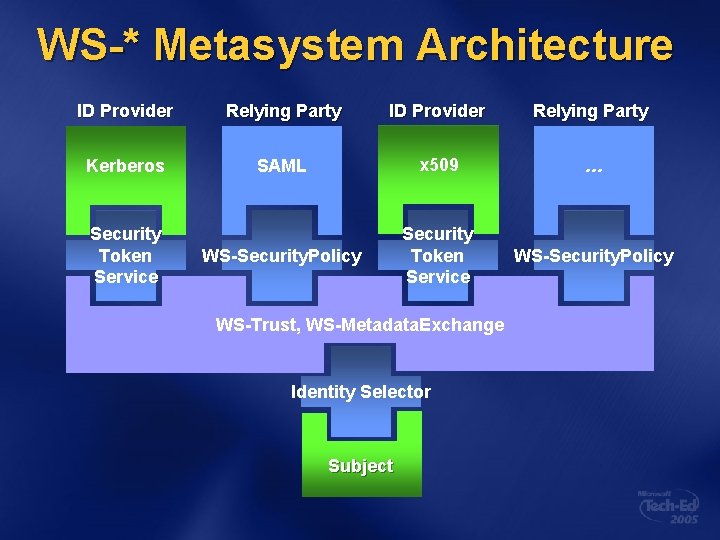
WS-* Metasystem Architecture ID Provider Relying Party Kerberos SAML x 509 … WS-Security. Policy Security Token Service WS-Trust, WS-Metadata. Exchange Identity Selector Subject

Microsoft Support for Identity Metasystem “Indigo” Runtime for building distributed applications supporting identity metasystem “Info. Card” End-Users “Info. Card” Developers “Indigo” WS-* Identity selector for Windows to visualize user’s digital identity Active Directory Infrastructure for identity and access Active Directory IT Organizations

© 2005 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. Microsoft makes no warranties, express or implied, in this summary.