Identity Management Dealing with Disclosure constructing identity management


















![Google: resume ssn site: . edu 1 [DOC]RESUME File Format: Microsoft Word 2000 - Google: resume ssn site: . edu 1 [DOC]RESUME File Format: Microsoft Word 2000 -](https://slidetodoc.com/presentation_image_h2/3d054b540a7c7a427973139e1d19b7d9/image-30.jpg)


![Google: resume ssn site: . edu 1 [DOC]RESUME File Format: Microsoft Word 2000 - Google: resume ssn site: . edu 1 [DOC]RESUME File Format: Microsoft Word 2000 -](https://slidetodoc.com/presentation_image_h2/3d054b540a7c7a427973139e1d19b7d9/image-35.jpg)








![PL 107 -56 SEC. 403 c) S. 1749 [Patriot Act] The Attorney General and PL 107 -56 SEC. 403 c) S. 1749 [Patriot Act] The Attorney General and](https://slidetodoc.com/presentation_image_h2/3d054b540a7c7a427973139e1d19b7d9/image-57.jpg)










- Slides: 87

Identity Management: Dealing with Disclosure “constructing identity management solutions that are provably appropriate for a particular context" privacy. cs. cmu. edu Latanya Sweeney, Ph. D latanya@privacy. cs. cmu. edu

Privacy Technology 1. Privacy is here to stay. 2. Computer scientist must help solve this problem. 3. Selective Revelation 4. Example: video surveillance 5. Example: bio-terrorism surveillance 6. Example: identity theft 7. Example: distributed surveillance 8. Example: privacy-preserving surveillance 9. Example: DNA privacy 10. Example: Identity theft protections 11. Example: k-Anonymity 12. Example: Webcam surveillance 13. Example: Text de-identification 14. Example: Policy specification and enforcement 15. Example: Scam Spam privacy. cs. cmu. edu

Privacy Technology 1. Privacy is here to stay. 2. Computer scientist must help solve this problem. 3. Selective Revelation 4. Example: video surveillance 5. Example: bio-terrorism surveillance identity theft 6. Example: Identity 7. Example: distributed surveillance 8. Example: privacy-preserving surveillance 9. Example: DNA privacy 10. Example: Identity theft protections Example: Identity protections 11. Example: k-Anonymity 12. Example: Webcam surveillance 13. Example: Text de-identification 14. Example: Policy specification and enforcement 15. Example: Scam Spam privacy. cs. cmu. edu

Hand. Shot ID new A Fast 3 -D Imaging System for Capturing Fingerprints, Palm Prints and Hand Geometry Latanya Sweeney, Ph. D School of Computer Science Carnegie Mellon University latanya@cs. cmu. edu Victor Weedn, MD, JD Forensic Science Program Duquesne University weednv@duq. edu Very Grateful to the U. S. Department of Justice for the opportunity to build Hand. Shot and study the science of fingerprint matching. privacy. cs. cmu. edu/dataprivacy/projects/handshot/index. html

new Testimony European Union Commission How should policy makers think about drafting policy for RFID technologies? 1. Cornerstones of privacy protection can be incorporated within many ubiquitous technology applications to provide privacy protection. 2. Focus policy at the general nature of ubiquitous technology and not on specific instances or uses of specific technologies. privacy. cs. cmu. edu

Acknowledgements Special thanks to Mike Gurski Richard Owens Pasha Peroff for inviting me to this outstanding conference. I am always extremely honored to be here.

Addressed in This Talk This talk will examine the nature of identity management problems and examine roles biometrics can play along with accompanying policy or additional technology. An integrated solution (“identity phone”) will be presented as a working example. privacy. cs. cmu. edu/dataprivacy/talks/CACR-05 -11. html

This Talk 1. Identity Management Problems 2. 2. Biometric Technologies 3. 3. Applying Biometrics to Problems 4. 4 Identity Phone Example privacy. cs. cmu. edu

This Talk 1. Identity Management Problems 2. Examine identity theft in terms of the acquisition of fraudulent credit cards and related issues to the U. S. Social Security number. [Identity Angel* & SSNwatch Projects] 3. 2. Biometric Technologies 4. 3. Applying Biometrics to Problems 5. 4. Identity Phone Example * Recently on CBS News

Historical Highlights of the SSN • 1935 Social Security Act SSNs only to be used for the social security program. • 1943 Executive Order 9397 Required federal agencies to use SSNs in new record systems • 1961 IRS began using SSN As taxpayer identification number • 1974 Privacy Act Government agencies use of SSN required authorization and disclosures (exempt agencies already using SSN) • 1976 Tax Reform Act Granted authority to State and local governments to use SSNs: state and local taxes, motor vehicle agencies • Over 400 million different numbers have been issued. Source: Social Security Administration, http: //www. ssa. gov/history/hfaq. html

Non-Government Uses of SSN • Corporate use of the SSN is not bound by the laws. You can request an alternative number. You can refuse to provide, they can refuse service. • Most common non-government use relates to credit bureaus and credit granting companies: Recognition – to locate your credit history for sharing it with you or with others with whom you sought credit. Linkage – to make sure new entries are added to your credit report. • Common uses until recently are for corporate identification Example: medical and school identification cards

Quality of the SSN Assignment Ability to acquire the number and use it falsely grows as more copies of the number are stored for different purposes. A Social Security number is almost always specific to one person and one person typically has a unique SSN. There are exceptions.

Unusual case of SSN 078 -05 -1120 Used by thousands of People! In 1938, a wallet manufacturer provided a sample SSN card, inserted in each new wallet. The company’s Vice President used the actual SSN of his secretary, Mrs. Hilda Schrader Whitcher. The wallet was sold by Woolworth and other stores. It had "specimen" written across the face, but many purchasers of the wallet adopted the SSN as their own. SSA voided the number. (Mrs. Whitcher was given a new number. ) In total, over 40, 000 people reported this as their SSN. As late as 1977, 12 people were still using it. Source: Social Security Administration, http: //www. ssa. gov/history/ssn/misused. html

Social Security Number Summary SSNs are used to represent a person: easy to replicate, easy to provide in-person and remotely easy to store and match BUT not verifiable when presented easily forged encoded, thereby leaking information

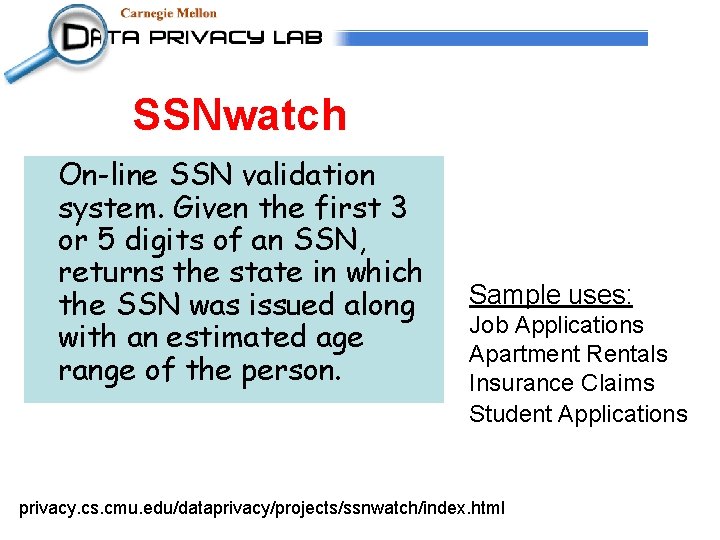
SSNwatch On-line SSN validation system. Given the first 3 or 5 digits of an SSN, returns the state in which the SSN was issued along with an estimated age range of the person. Sample uses: Job Applications Apartment Rentals Insurance Claims Student Applications privacy. cs. cmu. edu/dataprivacy/projects/ssnwatch/index. html

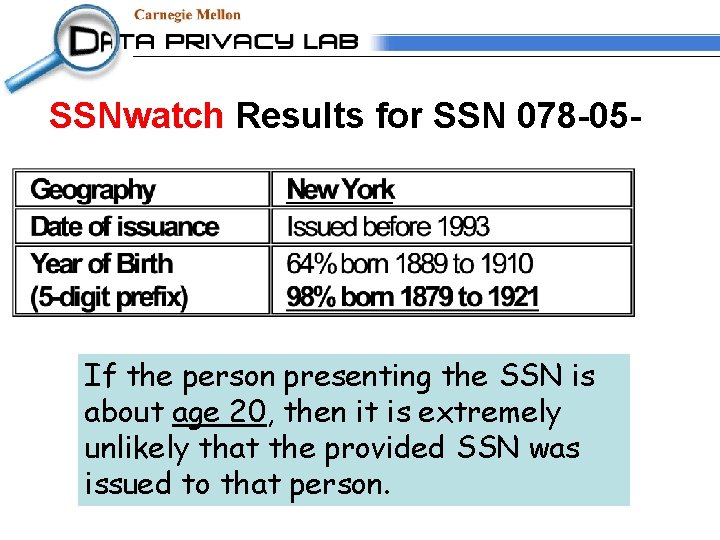
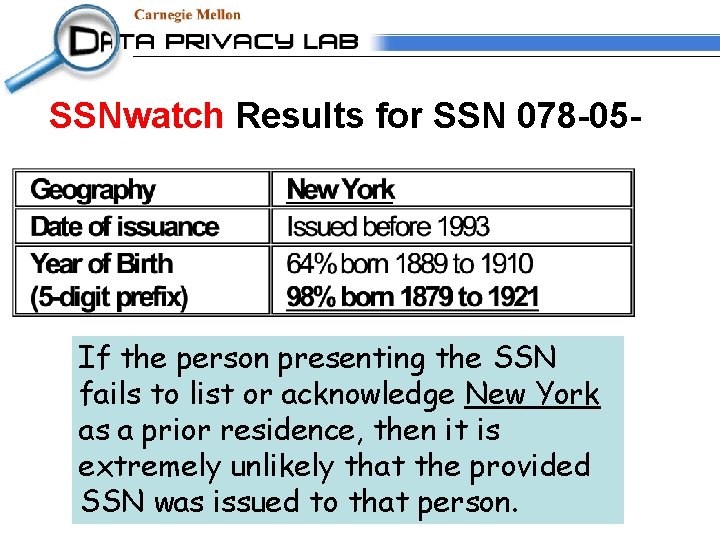
SSNwatch Results for SSN 078 -05 - If the person presenting the SSN is about age 20, then it is extremely unlikely that the provided SSN was issued to that person.

SSNwatch Results for SSN 078 -05 - If the person presenting the SSN fails to list or acknowledge New York as a prior residence, then it is extremely unlikely that the provided SSN was issued to that person.

What is Identity Theft? Identity theft occurs when a person uses another person’s personally-identifying information such as name, Social Security number, credit card number or other explicitly identifying information, without permission to commit fraud or other crimes. Source: Federal Trade Commission, http: //www. consumer. gov/idtheft/

Problems Posed by Identity Theft Identity theft is a serious crime. People whose identities have been stolen can spend months or years - and their hard-earned money - cleaning up the mess thieves have made of their good name and credit record. Victims may lose job opportunities, be refused loans, education, housing or cars, or even get arrested for crimes they didn't commit. Source: Federal Trade Commission, http: //www. consumer. gov/idtheft/

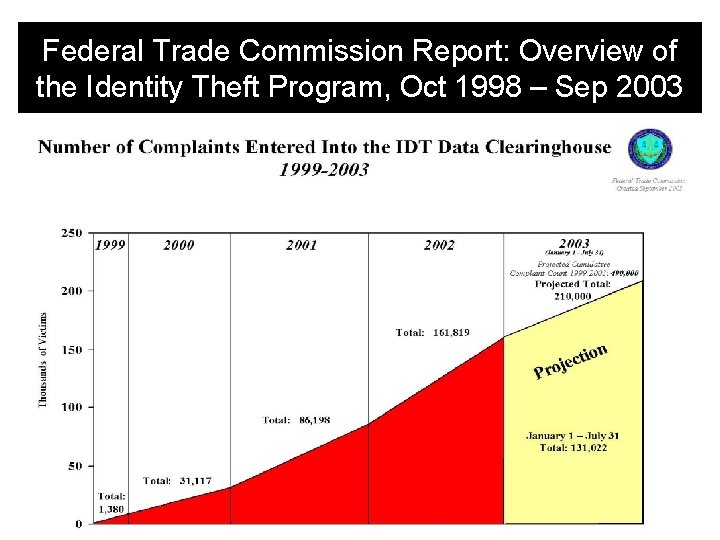
Federal Trade Commission Report: Overview of the Identity Theft Program, Oct 1998 – Sep 2003

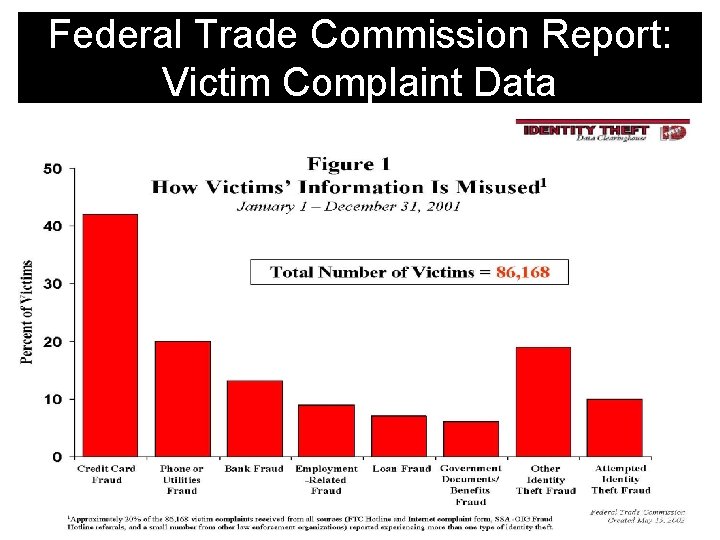
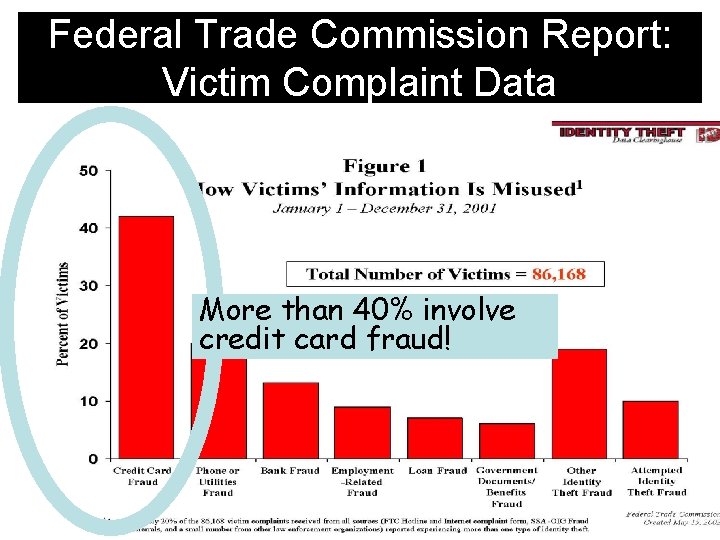
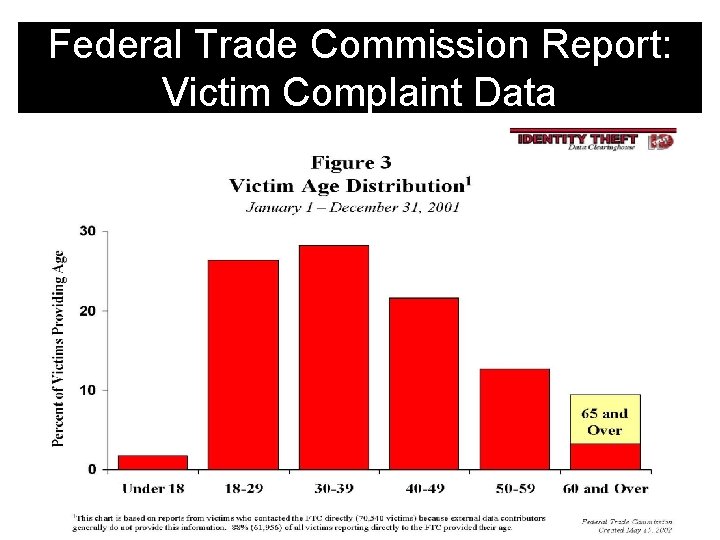
Federal Trade Commission Report: Victim Complaint Data

Federal Trade Commission Report: Victim Complaint Data More than 40% involve credit card fraud!

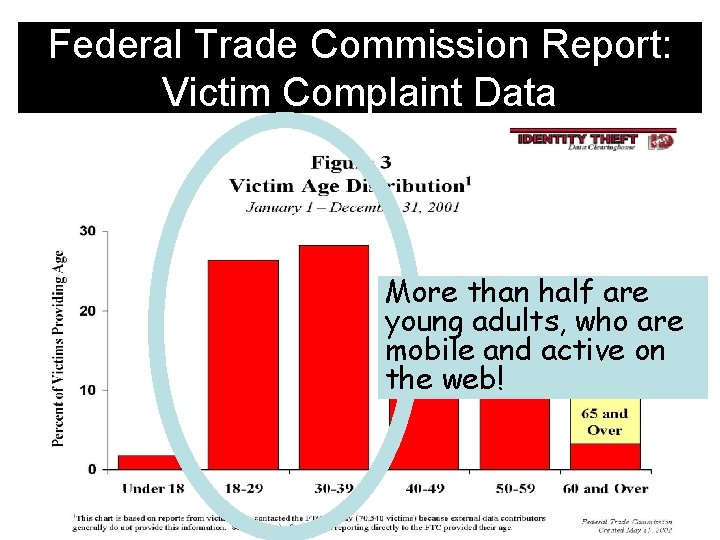
Federal Trade Commission Report: Victim Complaint Data

Federal Trade Commission Report: Victim Complaint Data More than half are young adults, who are mobile and active on the web!

Identity Angel Project Is there sufficient information freely available on-line to obtain fraudulent credit cards? Thousands of Americans are at risk to identity theft immediately! Can be done with little technical knowledge!

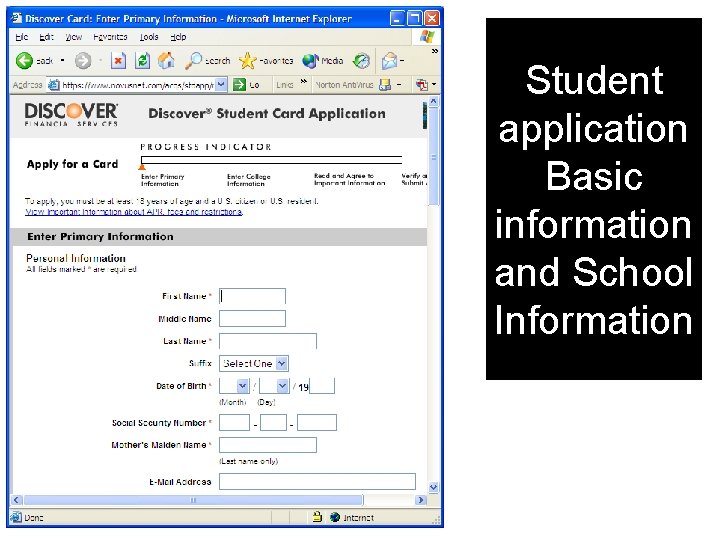
Student application Basic information and School Information

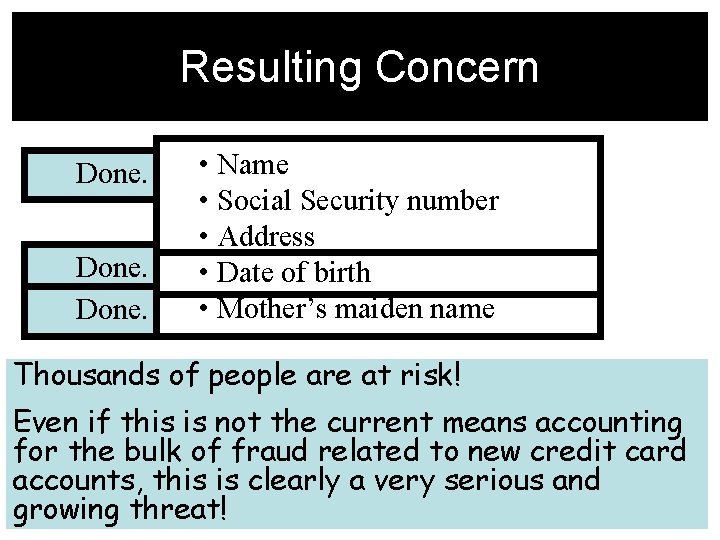
Basic Information Necessary For a Credit Card Application • Name • Social Security number • Address • Date of birth • Mother’s maiden name Strategy: if one can identify these fields for a person, they have the basic information needed to acquire a credit card in that person’s name.

Basic Information Necessary For a Credit Card Application Do these first. • Name • Social Security number • Address • Date of birth • Mother’s maiden name Strategy: if one can identify these fields for a person, they have the basic information needed to acquire a credit card in that person’s name. Therefore, we need only demonstrate how this information can be obtained on-line.

One Approach is to Buy an SSN There are websites that advertise SSNs for sale. The California-based Foundation for Taxpayer and Consumer Rights said for $26 each it was able to purchase the Social Security numbers and home addresses for Tenet, Ashcroft and other top Bush administration officials, including Karl Rove, the president's chief political adviser. [Associated Press, “Social Security numbers sold on Web” 8/28/2003]
![Google resume ssn site edu 1 DOCRESUME File Format Microsoft Word 2000 Google: resume ssn site: . edu 1 [DOC]RESUME File Format: Microsoft Word 2000 -](https://slidetodoc.com/presentation_image_h2/3d054b540a7c7a427973139e1d19b7d9/image-30.jpg)
Google: resume ssn site: . edu 1 [DOC]RESUME File Format: Microsoft Word 2000 - View as HTML RESUME. RICHARD ALLEN BROWN. Richard Allen Brown. PO Box 782. Kayenta, AZ 86033. Home Telephone-520 -697 -3513. NAU Telephone-520 -5234099. DOB: 03 -10 -77. SSN: 527 -71. . . dana. ucc. nau. edu/~rab 39/RAB%20 Resume. doc Many found. One is shown above. But the actual resumes are amidst lots of non-resume pages!

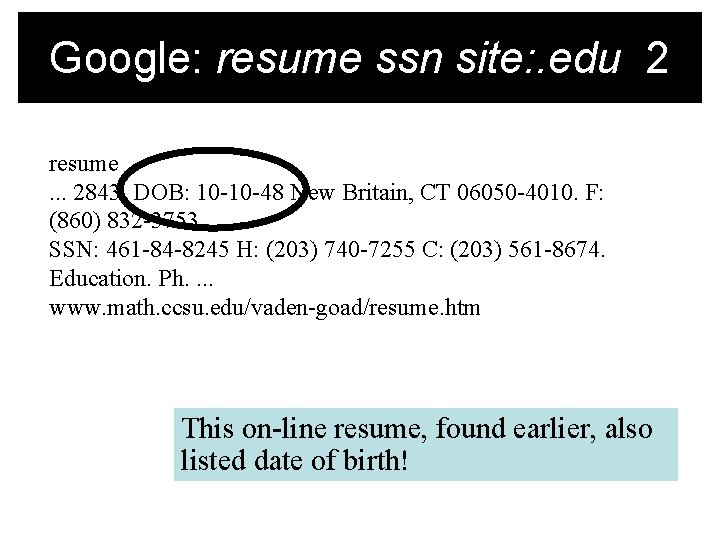
Google: resume ssn site: . edu 2 resume. . . 2843. DOB: 10 -10 -48 New Britain, CT 06050 -4010. F: (860) 832 -3753. SSN: 461 -84 -8245 H: (203) 740 -7255 C: (203) 561 -8674. Education. Ph. . www. math. ccsu. edu/vaden-goad/resume. htm A second example.

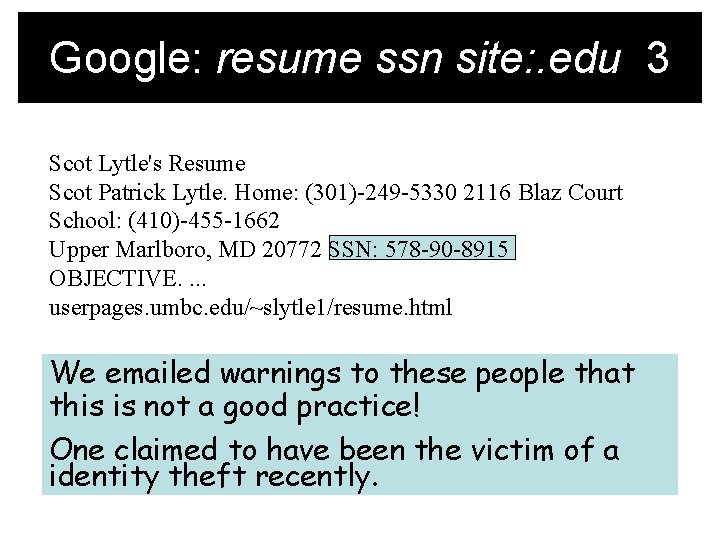
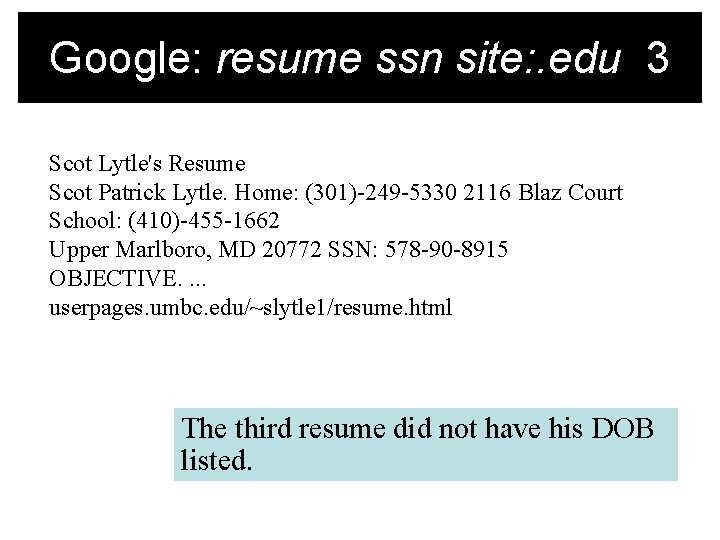
Google: resume ssn site: . edu 3 Scot Lytle's Resume Scot Patrick Lytle. Home: (301)-249 -5330 2116 Blaz Court School: (410)-455 -1662 Upper Marlboro, MD 20772 SSN: 578 -90 -8915 OBJECTIVE. . userpages. umbc. edu/~slytle 1/resume. html We emailed warnings to these people that this is not a good practice! One claimed to have been the victim of a identity theft recently.

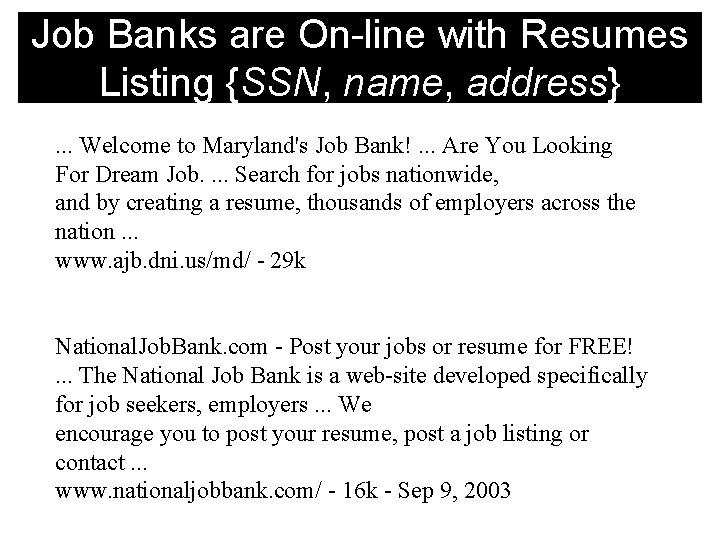
Job Banks are On-line with Resumes Listing {SSN, name, address}. . . Welcome to Maryland's Job Bank!. . . Are You Looking For Dream Job. . Search for jobs nationwide, and by creating a resume, thousands of employers across the nation. . . www. ajb. dni. us/md/ - 29 k National. Job. Bank. com - Post your jobs or resume for FREE!. . . The National Job Bank is a web-site developed specifically for job seekers, employers. . . We encourage you to post your resume, post a job listing or contact. . . www. nationaljobbank. com/ - 16 k - Sep 9, 2003

Basic Information Necessary For a Credit Card Application Done. Next. . . • Name • Social Security number • Address • Date of birth • Mother’s maiden name Strategy: if one can identify these fields for a person, they have the basic information needed to acquire a credit card in that person’s name. Therefore, we need only demonstrate how this information can be obtained on-line.
![Google resume ssn site edu 1 DOCRESUME File Format Microsoft Word 2000 Google: resume ssn site: . edu 1 [DOC]RESUME File Format: Microsoft Word 2000 -](https://slidetodoc.com/presentation_image_h2/3d054b540a7c7a427973139e1d19b7d9/image-35.jpg)
Google: resume ssn site: . edu 1 [DOC]RESUME File Format: Microsoft Word 2000 - View as HTML RESUME. RICHARD ALLEN BROWN. Richard Allen Brown. PO Box 782. Kayenta, AZ 86033. Home Telephone-520 -697 -3513. NAU Telephone-520 -5234099. DOB: 03 -10 -77. SSN: 527 -71. . . dana. ucc. nau. edu/~rab 39/RAB%20 Resume. doc This on-line resume, located earlier, actually listed date of birth too!

Google: resume ssn site: . edu 2 resume. . . 2843. DOB: 10 -10 -48 New Britain, CT 06050 -4010. F: (860) 832 -3753. SSN: 461 -84 -8245 H: (203) 740 -7255 C: (203) 561 -8674. Education. Ph. . www. math. ccsu. edu/vaden-goad/resume. htm This on-line resume, found earlier, also listed date of birth!

Google: resume ssn site: . edu 3 Scot Lytle's Resume Scot Patrick Lytle. Home: (301)-249 -5330 2116 Blaz Court School: (410)-455 -1662 Upper Marlboro, MD 20772 SSN: 578 -90 -8915 OBJECTIVE. . userpages. umbc. edu/~slytle 1/resume. html The third resume did not have his DOB listed.

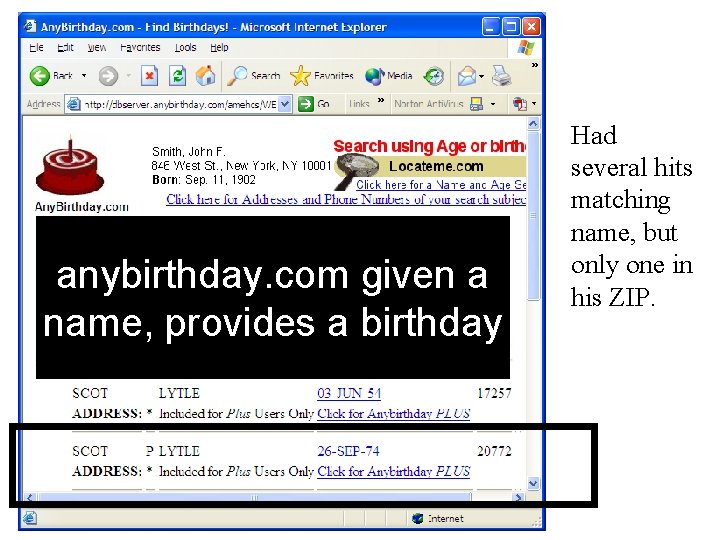
anybirthday. com given a name, provides a birthday Had several hits matching name, but only one in his ZIP.

Finding Dates of Birth Anybirthday. com tends to have information on people over the age of 30. Younger people are often not included. Many other population registers can be used, such as voter lists. Anybirthday. com is not he only source!

Basic Information Necessary For a Credit Card Application Done. Next. . . • Name • Social Security number • Address • Date of birth • Mother’s maiden name Strategy: if one can identify these fields for a person, they have the basic information needed to acquire a credit card in that person’s name. Therefore, we need only demonstrate how this information can be obtained on-line.

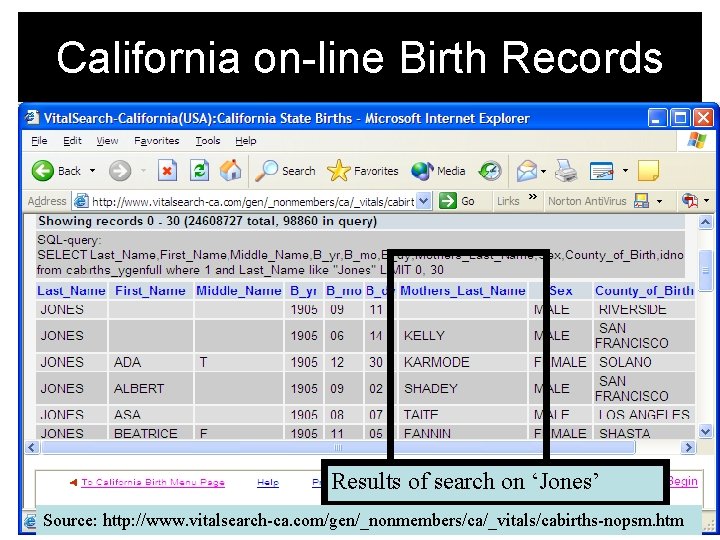
Publicly Available Birth Records Not all states, but many consider birth records, the kind of information included on a person’s birth certificate in the United States, as publicly available information. A few states have gone further to provide this information on-line. In the United States, birth certificate information tends to include the mother’s maiden name!

California on-line Birth Records Results of search on ‘Jones’ Source: http: //www. vitalsearch-ca. com/gen/_nonmembers/ca/_vitals/cabirths-nopsm. htm

Basic Information Necessary For a Credit Card Application Done. • Name • Social Security number • Address • Date of birth • Mother’s maiden name Strategy: if one can identify these fields for a person, they have the basic information needed to acquire a credit card in that person’s name. Therefore, we need only demonstrate how this information can be obtained on-line.

Resulting Concern Done. • Name • Social Security number • Address • Date of birth • Mother’s maiden name Thousands of people are at risk! Even if this is not the current means accounting for the bulk of fraud related to new credit card accounts, this is clearly a very serious and growing threat!

Identity Angel –resumes 1. Locate on-line resumes (using Filtered Searching) 2. Extract sensitive values (using regular expressions) 3. Email subjects about their risks L. Sweeney. AI Technologies to Defeat Identity Theft Vulnerabilities. AAAI Spring Symposium on AI Technologies for Homeland Security, 2005. (Updated version appearing in IEEE journal next month. ) http: //privacy. cs. cmu. edu/dataprivacy/projects/idangel/index. html

Identity Angel –resume findings 1000 resume hits on Google using flitered. Search, revealed 150 resumes, of which 140 (or 93%) had complete 9 digit SSNs. 10 resumes had partial, invalid, or some other country’s SSN. L. Sweeney. AI Technologies to Defeat Identity Theft Vulnerabilities. AAAI Spring Symposium on AI Technologies for Homeland Security, 2005. http: //privacy. cs. cmu. edu/dataprivacy/projects/idangel/index. html

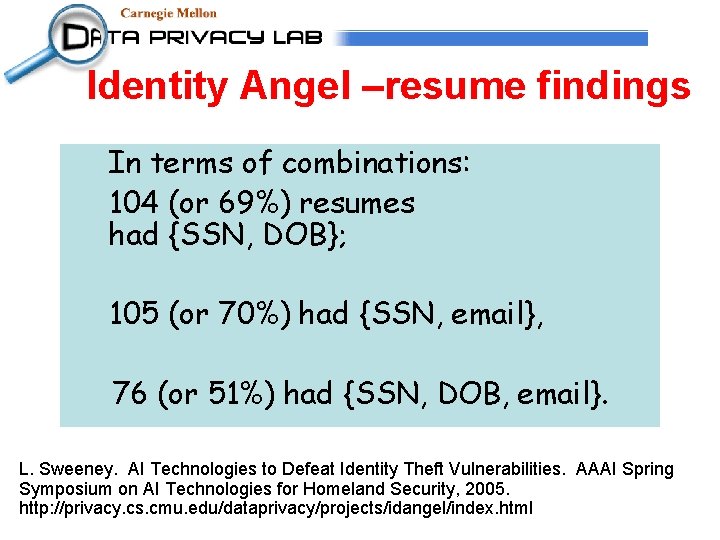
Identity Angel –resume findings In terms of combinations: 104 (or 69%) resumes had {SSN, DOB}; 105 (or 70%) had {SSN, email}, 76 (or 51%) had {SSN, DOB, email}. L. Sweeney. AI Technologies to Defeat Identity Theft Vulnerabilities. AAAI Spring Symposium on AI Technologies for Homeland Security, 2005. http: //privacy. cs. cmu. edu/dataprivacy/projects/idangel/index. html

Identity Angel –resume findings A single email message was sent to each of the 105 people having {SSN, email} alerting them to the risk. Within a month, 42 (or 55% of all of DBB) no longer had the information publicly available. A year later, 102 (or 68% of all of DBA) no longer had the information available. `` L. Sweeney. AI Technologies to Defeat Identity Theft Vulnerabilities. AAAI Spring Symposium on AI Technologies for Homeland Security, 2005. http: //privacy. cs. cmu. edu/dataprivacy/projects/idangel/index. html

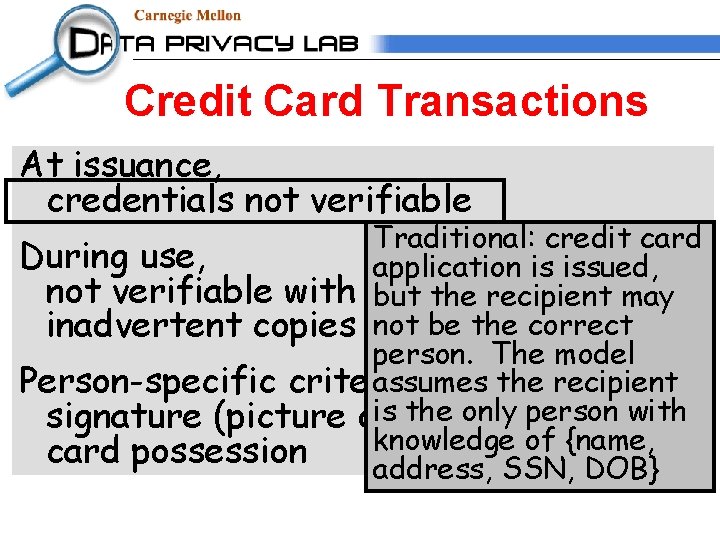
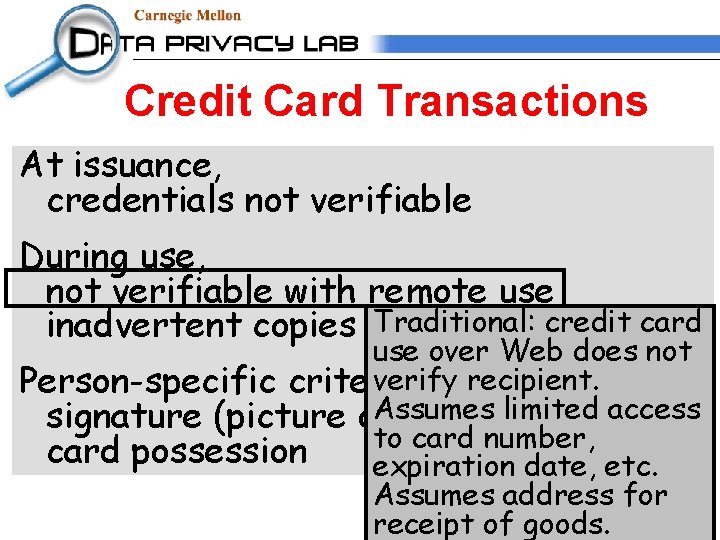
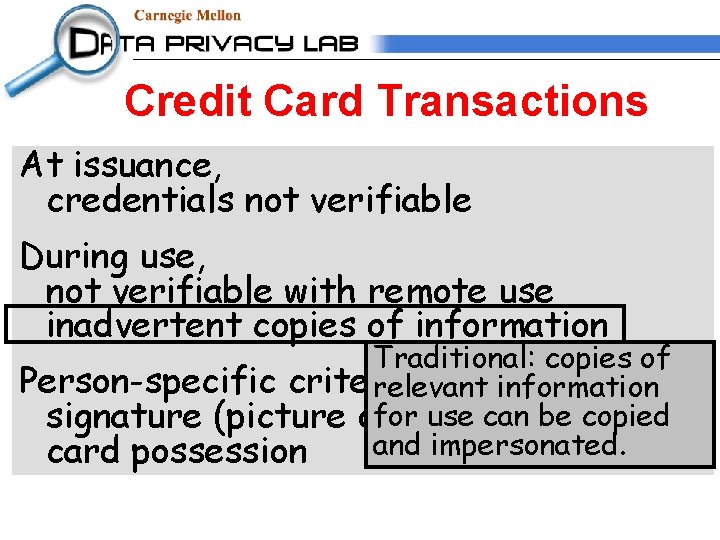
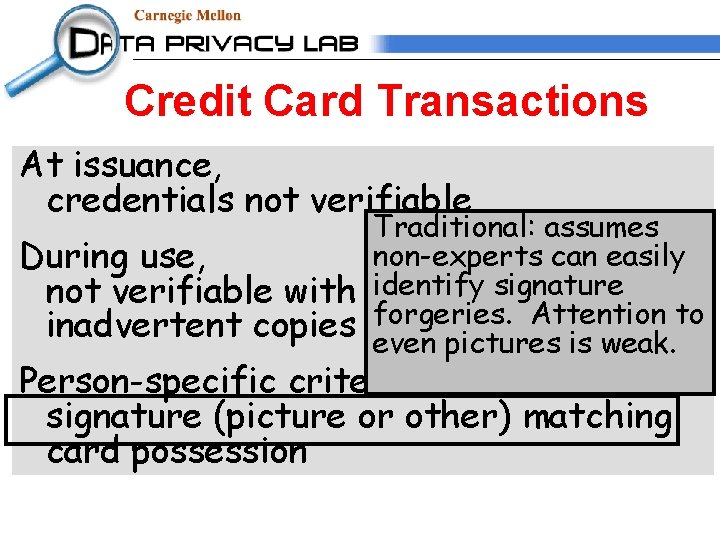
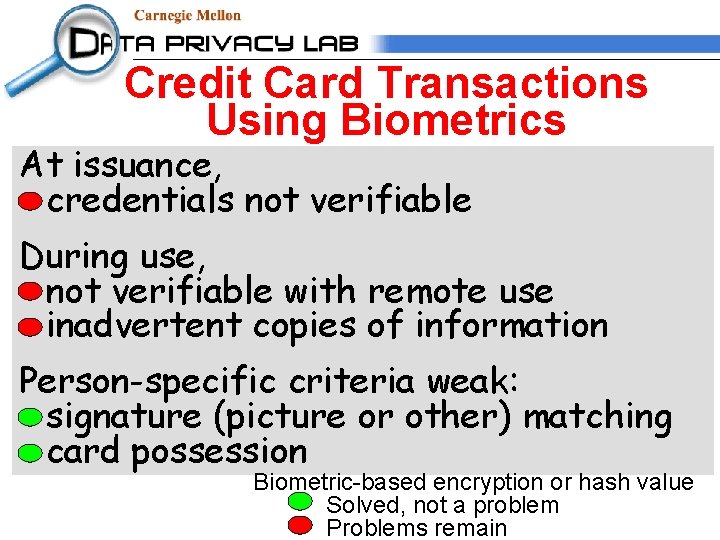
Credit Card Transactions At issuance, credentials not verifiable During use, not verifiable with remote use inadvertent copies of information Person-specific criteria weak: signature (picture or other) matching card possession

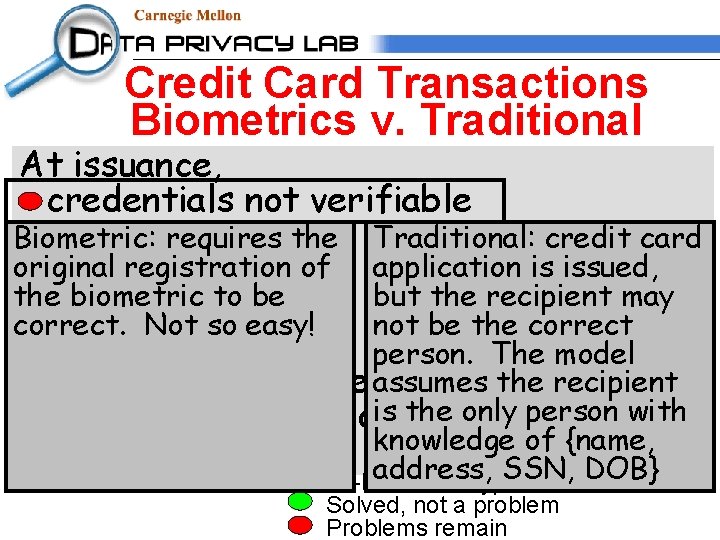
Credit Card Transactions At issuance, credentials not verifiable Traditional: credit card During use, application is issued, not verifiable with remote use but the recipient may notinformation be the correct inadvertent copies of person. The model assumes the recipient Person-specific criteria weak: is other) the only matching person with signature (picture or knowledge of {name, card possession address, SSN, DOB}

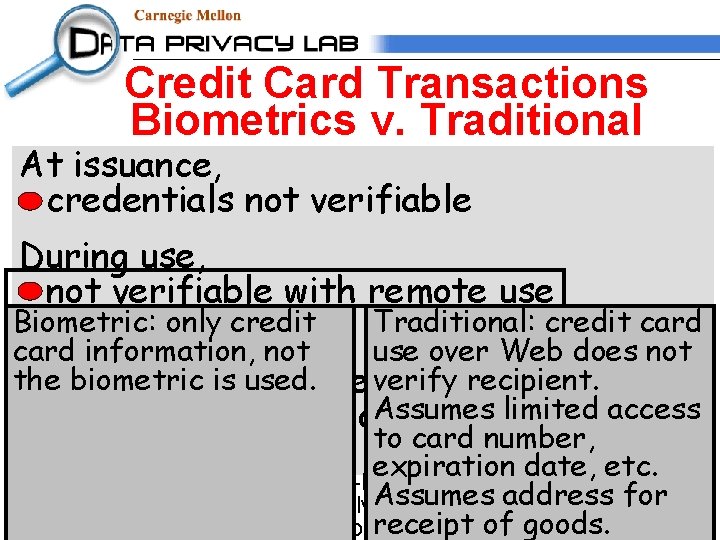
Credit Card Transactions At issuance, credentials not verifiable During use, not verifiable with remote use Traditional: credit card inadvertent copies of information use over Web does not verify recipient. Person-specific criteria weak: Assumes access signature (picture or other)limited matching to card number, card possession expiration date, etc. Assumes address for receipt of goods.

Credit Card Transactions At issuance, credentials not verifiable During use, not verifiable with remote use inadvertent copies of information Traditional: copies of Person-specific criteria weak: relevant information forother) use canmatching be copied signature (picture or and impersonated. card possession

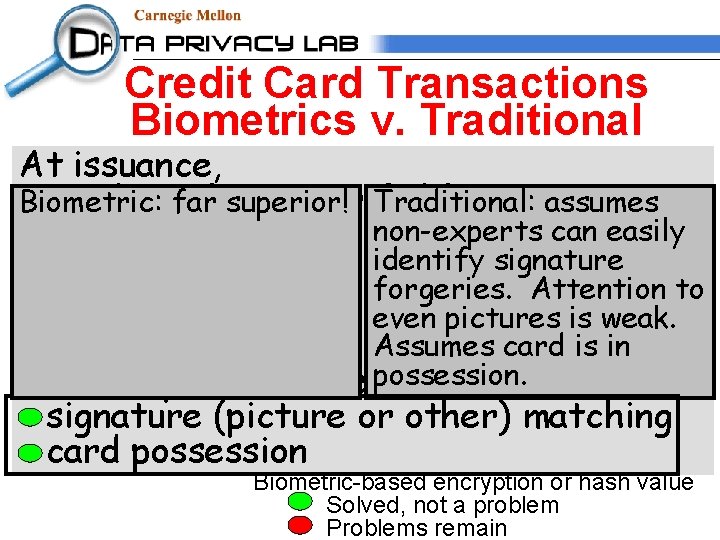
Credit Card Transactions At issuance, credentials not verifiable During use, not verifiable with inadvertent copies Traditional: assumes non-experts can easily identify signature remote use forgeries. Attention to of information even pictures is weak. Person-specific criteria weak: signature (picture or other) matching card possession

Credit Card Transactions At issuance, credentials not verifiable During use, not verifiable with remote useassumes Traditional: card holder is in inadvertent copies of information complete control of the cardweak: and its Person-specific criteria information. signature (picture or other) matching card possession

Travel Documents At issuance, credentials not verifiable During secondary use, inadvertent copies of information Person-specific criteria weak: signature (picture or other) matching card possession

This Talk 1. Identity Management Problems 2. 2. Biometric Technologies 3. 3. Applying Biometrics to Problems 4. 4. Identity Phone Example privacy. cs. cmu. edu
![PL 107 56 SEC 403 c S 1749 Patriot Act The Attorney General and PL 107 -56 SEC. 403 c) S. 1749 [Patriot Act] The Attorney General and](https://slidetodoc.com/presentation_image_h2/3d054b540a7c7a427973139e1d19b7d9/image-57.jpg)
PL 107 -56 SEC. 403 c) S. 1749 [Patriot Act] The Attorney General and the Secretary of State jointly, through the National Institute of Standards and Technology (NIST), …. shall develop and certify a technology standard that can be used to verify the identity of persons applying for a US visa or such persons seeking to enter the US pursuant to a visa for the purposes of conducting background checks, confirming identity, and ensuring that a person has not received a visa under a different name…. .

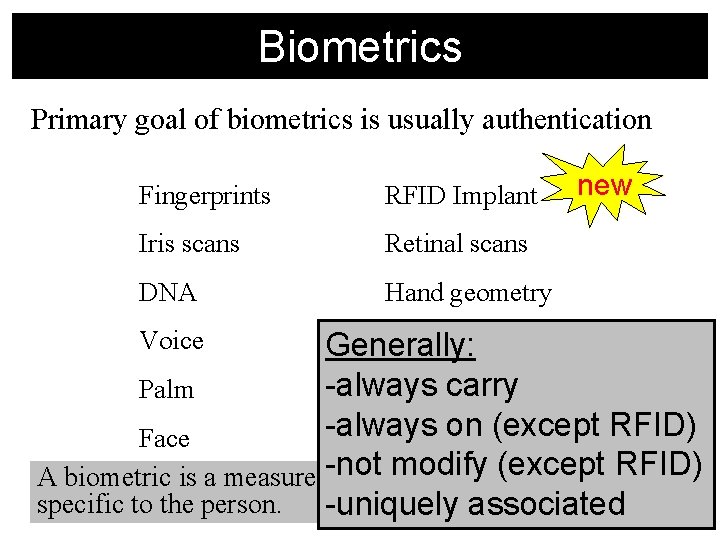
Biometrics Primary goal of biometrics is usually authentication Fingerprints RFID Implant Iris scans Retinal scans DNA Hand geometry Voice Behavioral Palm print Keyboard typing new Face Signature A biometric is a measurement of the person that is specific to the person.

Iris Scanning Iris and retina scans are the most accurate of all biometric techniques and, currently, the most costly. Iris scans analyze the features that exist in the colored tissue surrounding the pupil which has more than 200 points that can be used for comparison, including rings, furrows and freckles. The scans use a regular video camera style and can be done from even 2 feet away.

Retinal Scanning Retinal scanning analyses the blood vessels located at the back of the eye, reading its 400 unique points. A person steps in front of a device, keeping head perfectly still. Takes about 12 seconds. Disadvantage: retina can become diseased (cataracts), be fairly close to the machine

Hand Geometry Source: Arun Ross, Anil Jain and Sharat Pankanti, biometrics. cse. msu. edu/hand_proto. html Hands are not so unique, but one can use finger length, thickness, and curvature for the purposes of verification but not for identification. Lab last term! Measurements from traces.

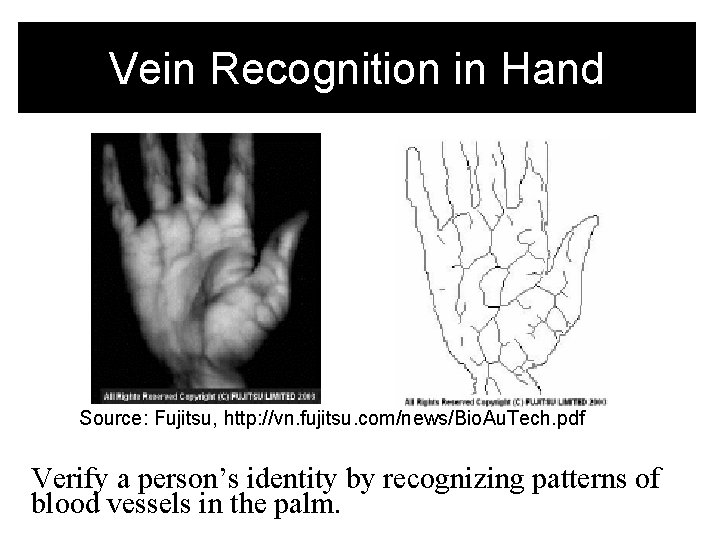
Vein Recognition in Hand Source: Fujitsu, http: //vn. fujitsu. com/news/Bio. Au. Tech. pdf Verify a person’s identity by recognizing patterns of blood vessels in the palm.

RFID • Radio-frequency ID • Passive RFID: device with no battery that draws power from a radio-frequency field • Power drives a processor that can communicate back to a reader • Used for product identification, payment cards, animal tracking • First use: Identification friend or foe (IFF) in WWII Courtesy: Michael Shamos

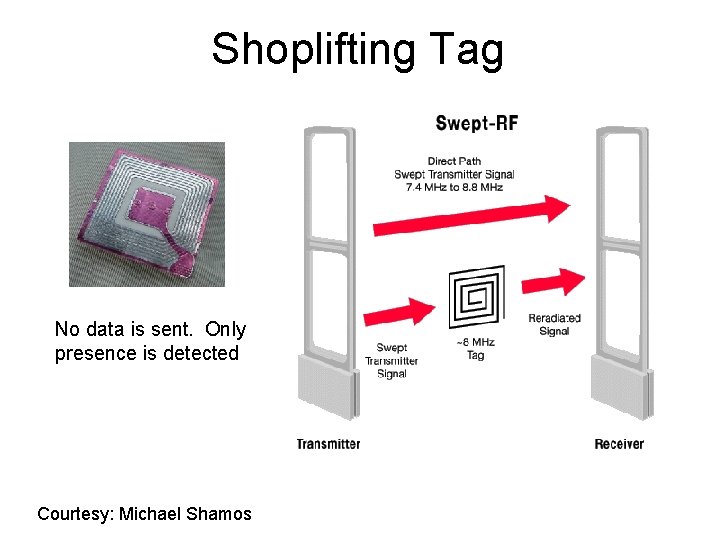
Shoplifting Tag No data is sent. Only presence is detected Courtesy: Michael Shamos

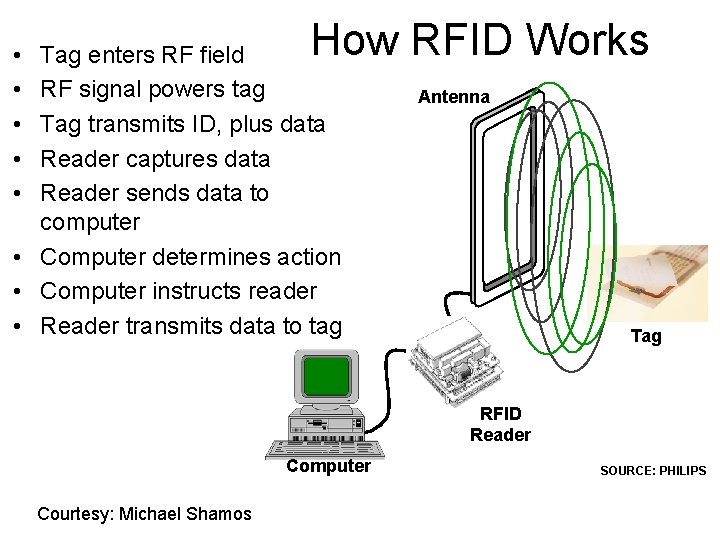
How RFID Works • • • Tag enters RF field RF signal powers tag Tag transmits ID, plus data Reader captures data Reader sends data to computer • Computer determines action • Computer instructs reader • Reader transmits data to tag Antenna Tag RFID Reader Computer Courtesy: Michael Shamos SOURCE: PHILIPS

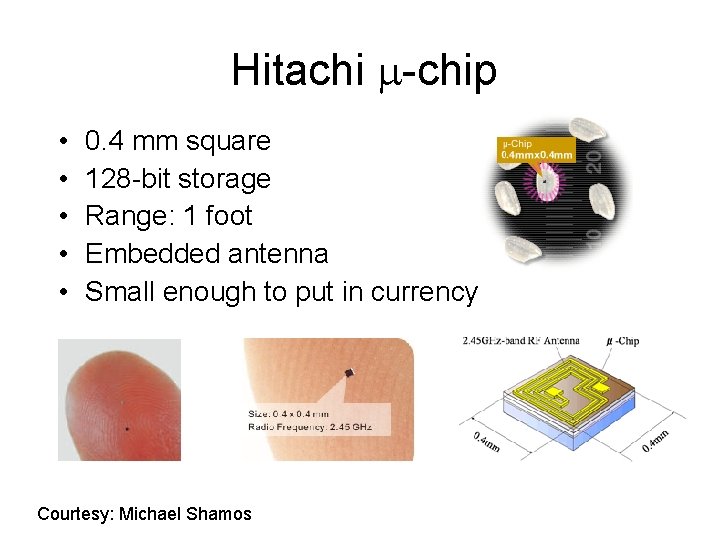
Hitachi -chip • • • 0. 4 mm square 128 -bit storage Range: 1 foot Embedded antenna Small enough to put in currency Courtesy: Michael Shamos

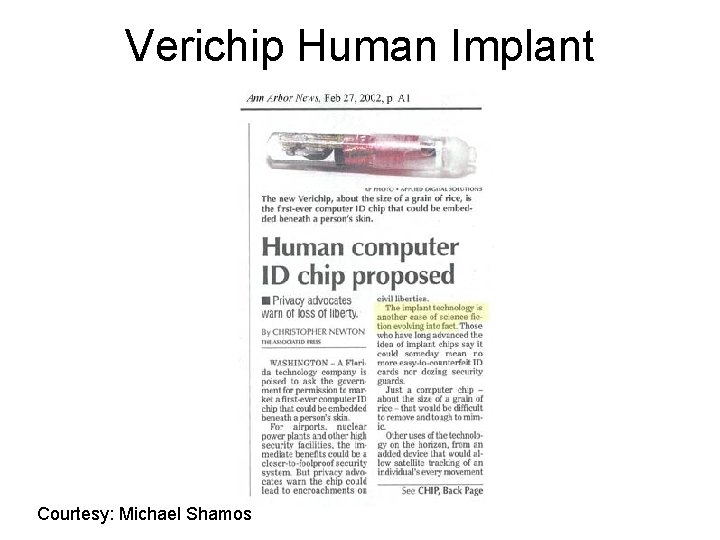
Verichip Human Implant Courtesy: Michael Shamos

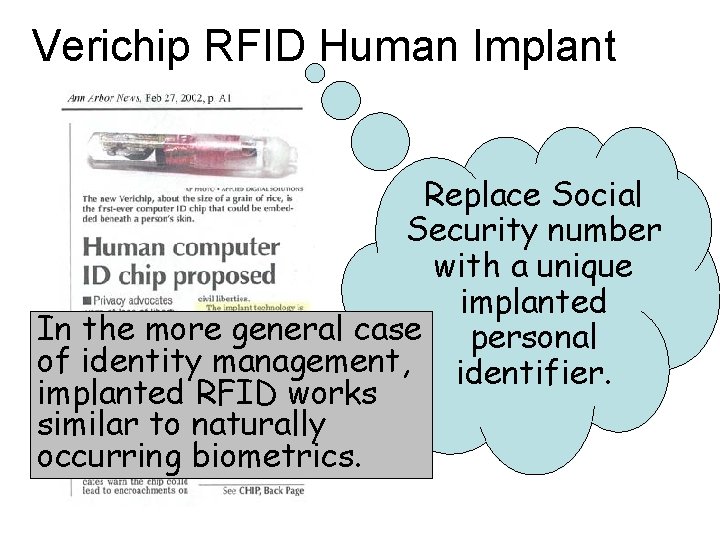
Verichip RFID Human Implant Replace Social Security number with a unique implanted In the more general case personal of identity management, identifier. implanted RFID works similar to naturally occurring biometrics.

Biometrics Primary goal of biometrics is usually authentication Fingerprints RFID Implant Iris scans Retinal scans DNA Hand geometry Voice new Behavioral Generally: -always carry Palm Keyboard typing -always on (except RFID) Face Signature -notofmodify (except A biometric is a measurement the person that is RFID) specific to the person. -uniquely associated

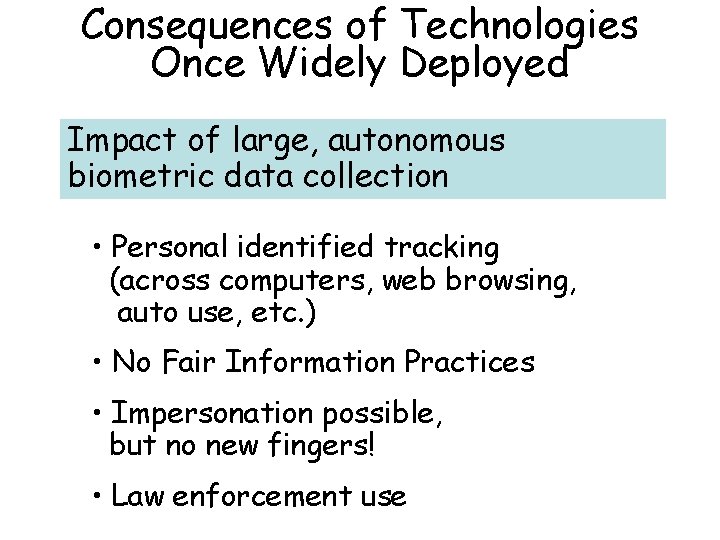
Consequences of Technologies Once Widely Deployed Impact of large, autonomous biometric data collection • Personal identified tracking (across computers, web browsing, auto use, etc. ) • No Fair Information Practices • Impersonation possible, but no new fingers! • Law enforcement use

This Talk 1. Identity Management Problems 2. 2. Biometric Technologies 3. 3. Applying Biometrics to Problems 4. 4. Identity Phone Example privacy. cs. cmu. edu

Credit Card Transactions Using Biometrics At issuance, credentials not verifiable During use, not verifiable with remote use inadvertent copies of information Person-specific criteria weak: signature (picture or other) matching card possession Biometric-based encryption or hash value Solved, not a problem Problems remain

Credit Card Transactions Biometrics v. Traditional At issuance, credentials not verifiable Biometric: requires the Duringregistration use, original of verifiable thenot biometric to bewith correct. Not so easy! inadvertent copies Traditional: credit card application is issued, remote use but the recipient may notinformation be the correct of person. The model assumes the recipient Person-specific criteria weak: is other) the only matching person with signature (picture or knowledge of {name, card possession address, SSN, DOB} Biometric-based encryption or hash value Solved, not a problem Problems remain

Credit Card Transactions Biometrics v. Traditional At issuance, credentials not verifiable During use, not verifiable with remote use Biometric: only credit Traditional: credit card inadvertent copies of information card information, not use over Web does not the biometric is used. verify recipient. Person-specific criteria weak: Assumes access signature (picture or other)limited matching to card number, card possession expiration date, etc. Biometric-based encryption or hash value Assumes address for Solved, not a problem receipt of goods. Problems remain

Credit Card Transactions Biometrics v. Traditional At issuance, credentials not verifiable Biometric: far superior! Traditional: assumes non-experts can easily During use, identify signature forgeries. use Attention to not verifiable with remote even pictures is weak. inadvertent copies of information Assumes card is in possession. Person-specific criteria weak: signature (picture or other) matching card possession Biometric-based encryption or hash value Solved, not a problem Problems remain

Travel Documents At issuance, credentials not verifiable During secondary use, inadvertent copies of information Person-specific criteria weak: signature (picture or other) matching card possession Biometric-based encryption or hash value Solved, not a problem Problems remain

This Talk 1. Identity Management Problems 2. 2. Biometric Technologies 3. 3. Applying Biometrics to Problems 4. 4. Identity Phone Example privacy. cs. cmu. edu

Sweeney Identity Phone new Issued at birth and remains with a person until death. Special set of phone numbers that can be used like Social Security numbers. A special mobile phone that includes: Phone capability to send/receive calls Biometric readers: fingerprint, camera GPS (location) Recognition software: voice, fingerprint, face

Sweeney Identity Phone Sample Sessions • Issue phone number like SSN for matching and storing. • Want to verify a person facing you, phone their # and check GPS location. • Want to authenticate a person facing you, phone their #, check GPS location, and verify using fingerprint reader. • Make a credit card purchase: merchant sends their phone# to credit card company, buyer authenticates and approves using buyer phone.

Credit Card Transactions Identity Phone v. Biometrics At issuance, credentials not verifiable During use, not verifiable with remote use inadvertent copies of information Person-specific criteria weak: signature (picture or other) matching card possession Biometric-based encryption or hash value (right) Sweeney Identity Phone (left) Solved, not a problem Problems remain

Credit Card Transactions Identity Phone v. Biometrics At issuance, credentials not verifiable Identity Phone: Biometric: requires the During use, registration is not at with original registration of not verifiable remote use card issuance but at the biometric to be of information birth. inadvertent copies correct. Not so easy! (Of course, no forgivingcriteria weak: Person-specific or forgetting!) signature (picture or other) matching card possession Biometric-based encryption or hash value (right) Sweeney Identity Phone (left) Solved, not a problem Problems remain

Credit Card Transactions Identity Phone v. Biometrics At issuance, credentials not verifiable During use, not verifiable with remote use copies of information Identityinadvertent Phone: Biometric: only credit authenticates person criteria card information, not Person-specific weak: and vendor! Vendor the biometric is used. signature phones credit card (picture or other) matching possession company, card which in turn Biometric-based encryption or hash value (right) calls customer for Sweeney Identity Phone (left) authorization of charge. Solved, not a problem Problems remain

Credit Card Transactions Identity Phone v. Biometrics At issuance, Identity Phone: same as Biometric: far superior credentials not verifiable biometric alone! over traditional approach! During use, not verifiable with remote use inadvertent copies of information Person-specific criteria weak: signature (picture or other) matching card possession Biometric-based encryption or hash value (right) Sweeney Identity Phone (left) Solved, not a problem Problems remain

Travel Documents Identity Phone v. Biometrics At issuance, credentials not verifiable During secondary use, inadvertent copies of information Person-specific criteria weak: signature (picture or other) matching card possession Biometric-based encryption or hash value (right) Sweeney Identity Phone (left) Solved, not a problem Problems remain

Identity Phone Summary The purpose of the Identity Phone is not to sell phones but to show combinations of biometrics, location information and authoritative issuance can work together to solve some key identity management problems.

Addressed in This Talk This talk will examine the nature of identity management problems and examine roles biometrics can play along with accompanying policy or additional technology. An integrated solution (“identity phone”) will be presented as a working example. privacy. cs. cmu. edu/dataprivacy/talks/CACR-05 -11. html

This Talk 1. Identity Management Problems 2. 2. Biometric Technologies 3. 3. Applying Biometrics to Problems 4. 4. Identity Phone Example privacy. cs. cmu. edu