How to find your way around e s





















- Slides: 37

How to find your way around … e s r You can play the Power. Point and the Test here. u o C e l p m a x E START FINISH

How to find your way around … Always click the ‘home’ icon to save your progress and log off. e s r u o C This is important! e l p m a x E START FINISH

Information Governance For all staff. START FINISH

INTRODUCTION Information Governance Data Protection Act Freedom Of Information Act & Records Management Training START FINISH

Information Governance is the framework structures and processes that ensure the security, confidentiality and integrity of the Trust’s data information about it’s patients and employees, in particular personal sensitive and corporate information. It allows the Trust and individuals to: • Ensure that personal information is dealt with legally, securely, efficiently and effectively • Provides a framework to bring together all requirements, standards and best practices that apply to the handling of all information • Focus on setting standards and giving the Trust tools to achieve them • To be consistent in the way we handle personal/corporate information • Lead improvements in information handling, patient / public confidence in the Trust and employee training and development START FINISH COURSE OBJECTIVES On completion of the Information Governance module, you will understand: • • • Duty of Confidentiality Data Handling & Security Best Practice Guidelines Information Governance Toolkit Confidential/sensitive/corporate Information Sharing & Privacy Impact Assessments Consent Personal information – Date Protection Act Corporate Information – Freedom of Information

Duty of Confidentiality All employees of the Trust who record, handle, store or otherwise come across information, have a common law duty of confidence to patients and staff. We need to remember: • Keep personal information private. • Ensure confidential information is not unlawfully or inappropriately accessed. • Any confidentiality breaches need to be reported to your line manger and Information Governance. • Before disclosing information ensure you know who you are communicating with. • Comply with policies and procedures. • Do not leave manual records unattended. • Dispose of confidential information in the appropriate manner. • Ensure confidential information is held, stored and transported securely. Please note – this guidance applies equally to those such as student, trainees, bank, agency staff. Contract staff on temporary placements (this list is not exhaustive). Information Governance helps all employees to manage person identifiable information so that all patients and staff know their records will not be disclosed inappropriately, which will: • Give individuals greater trust in our working practices. • Encourage individuals to be more open in sharing important personal details. • Ensure they will receive the best quality care. START FINISH

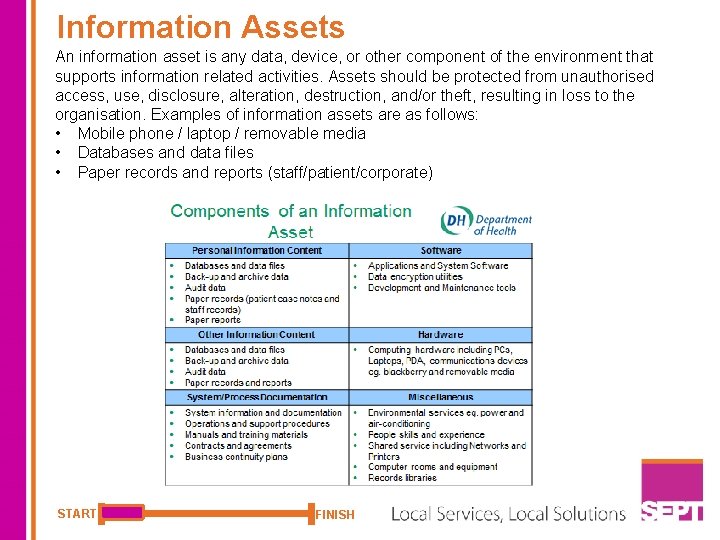
Information Assets An information asset is any data, device, or other component of the environment that supports information related activities. Assets should be protected from unauthorised access, use, disclosure, alteration, destruction, and/or theft, resulting in loss to the organisation. Examples of information assets are as follows: • Mobile phone / laptop / removable media • Databases and data files • Paper records and reports (staff/patient/corporate) START FINISH

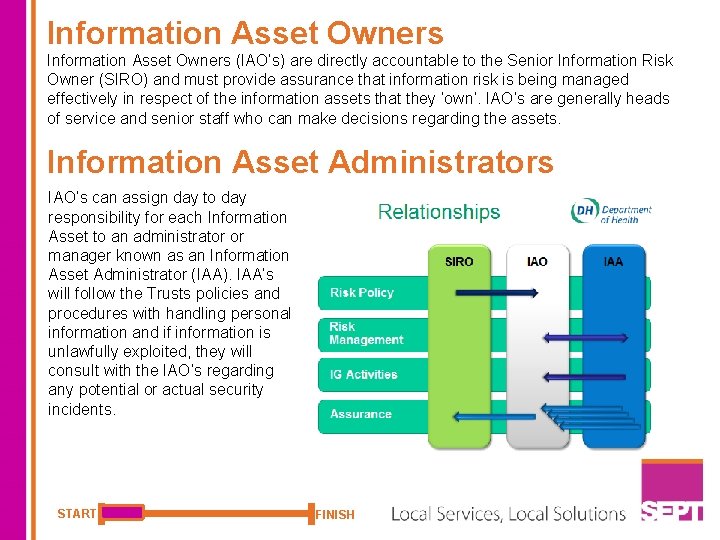
Information Asset Owners (IAO’s) are directly accountable to the Senior Information Risk Owner (SIRO) and must provide assurance that information risk is being managed effectively in respect of the information assets that they ‘own’. IAO’s are generally heads of service and senior staff who can make decisions regarding the assets. Information Asset Administrators IAO’s can assign day to day responsibility for each Information Asset to an administrator or manager known as an Information Asset Administrator (IAA). IAA’s will follow the Trusts policies and procedures with handling personal information and if information is unlawfully exploited, they will consult with the IAO’s regarding any potential or actual security incidents. START FINISH

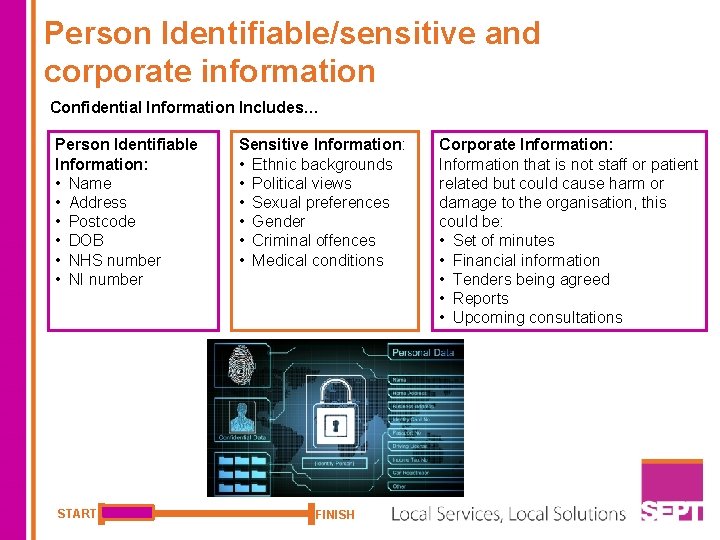
Person Identifiable/sensitive and corporate information Confidential Information Includes… Person Identifiable Information: • Name • Address • Postcode • DOB • NHS number • NI number START Sensitive Information: • Ethnic backgrounds • Political views • Sexual preferences • Gender • Criminal offences • Medical conditions FINISH Corporate Information: Information that is not staff or patient related but could cause harm or damage to the organisation, this could be: • Set of minutes • Financial information • Tenders being agreed • Reports • Upcoming consultations

Transferring Confidential Information Offsite – Paper • Confidential information should only be transferred, if absolutely necessary and with managers authorisation • Where possible, only take enough information with you to enable you to undertake your daily tasks (e. g. if a community nurse needs to visit a patient at home and only needs the postcode to locate the patient. There is no need to take the whole medical record for this purpose. ) • Where possible, data should be anonymised • Lockable carriers must be used when carrying confidential documentation (bus, walking, train, cycling etc. ) • Sealed medical records bags can also be used to transfer confidential information • Throughout transportation all information must be placed in the boot of the car and removed to a place of security at destination For further guidance please refer to the Records Management Procedure – Transportation of Records - Section 6. 3 START FINISH

Transferring Confidential Information Offsite – Electronic • Confidential information should only be transferred, if absolutely necessary • Where possible, only take enough information with you to enable you to undertake your daily tasks (e. g. if a community nurse needs to visit a patient at home and only needs the postcode to locate the patient. There is no need to take the whole medical record for this purpose. ) • All devices must be encrypted and password protected • USBs, CDs, DVDs, mobile phones, laptops, digital Dictaphones etc. should NOT be used to store any confidential information, only to transfer information if necessary and authorised • Once data has been transferred please ensure it is deleted and wiped as, per Trust policy states START FINISH

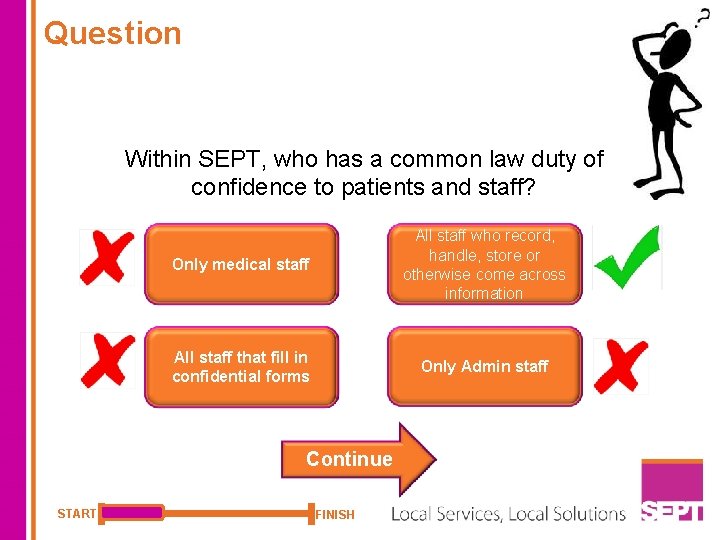
Question Within SEPT, who has a common law duty of confidence to patients and staff? Only medical staff All staff who record, handle, store or otherwise come across information All staff that fill in confidential forms Only Admin staff Continue START FINISH

Data Handling, Security and Best practice Guidelines Best Practice Guidelines – Confidential Waste • All confidential waste should be disposed either using a cross cut shredder (cuts paper both horizontally and vertically) or placing in the blue confidential waste bins • Never put confidential information in black refuse bags/recycling bins • Confidential waste paper should not be used as scrap paper • If you do not have the facility to dispose of confidential information securely at home, please bring back into the office for appropriate disposal. Best Practice Guidelines – Clear Desk Policy Operate a clear desk policy by ensuring all person identifiable/ sensitive/confidential information is locked away as appropriate, especially important when hot desking or working in an open plan office. START FINISH

Data Handling, Security and Best practice Guidelines Best Practice Guidelines – Photocopying • Do not make excessive copies of confidential information; • Do not leave confidential information on the photocopying machine; • Regularly check/update your distribution list to ensure copies are not sent to staff who have left the Trust. Best Practice Guidelines – Post • PO box return labels to be displayed on external post • Ensure marked ‘Private & Confidential’ • Double check full postal address of recipient • Choose secure method of sending confidential information through external post (recorded delivery or private courier) • When necessary ask recipient to confirm receipt • Ensure incoming confidential post is handled appropriately. Best Practice Guidelines – Person Ensure you hold confidential conversations in an appropriate place. Inappropriate areas include: corridors, open plan offices etc Gain patient consent before sharing their personal information with relatives/friends. START FINISH

Data Handling, Security and Best practice Guidelines Best Practice Guidelines – Email • No person identifiable/sensitive/ confidential information is to be detailed in the body or subject heading of the email • Confidential information is to be sent as a password protected attachment or transferred via NHS. net to NHS. net • Passwords to be sent by text or phone (wherever possible) or in a separate email (leave suitable time between emails) Best Practice Guidelines – Faxing Do not fax personal or confidential information unless absolutely necessary and ensure the Safe Haven Fax procedure is followed. • Call individual to make them aware you are sending a fax • Send cover sheet • Confirm this has been received • Continue to fax the information by pressing redial • Ask individual to confirm receipt once received. START FINISH

Data Handling, Security and Best practice Guidelines Best Practice Guidelines – Voicemails for Clients • Only state forename and number • Do not state full name, team, service or organisation unless agreed • Consent needs to be obtained before leaving a voicemail Best Practice Guidelines – Telephone When receiving calls requesting personal information: • Verify the identity of the caller (e. g. make a note of the callers’ name and call back using a switchboard/reception number and ask to speak to the named caller or ask a set of security questions). • Check whether they are entitled to the information they request (e. g. check if there is an information sharing agreement in place or if consent has been gained when a third party is requesting information). • If in doubt, contact the Information Governance Team for further advice. START FINISH

Data Handling, Security and Best practice Guidelines Best Practice Guidelines – Office • Remember to lock and secure the office when left unattended and at the end of the day • Close and lock all windows • Close any blinds/curtains • Set the intruder alarm system (if fitted) • Remember to wear your ID badge • Ensure clear desk policy is followed • Lock computer screens when left unattended (Ctrl, Alt, Delete) • Remove smartcard from keyboard when leaving work station unattended and ensure it is kept secure at all times. START FINISH

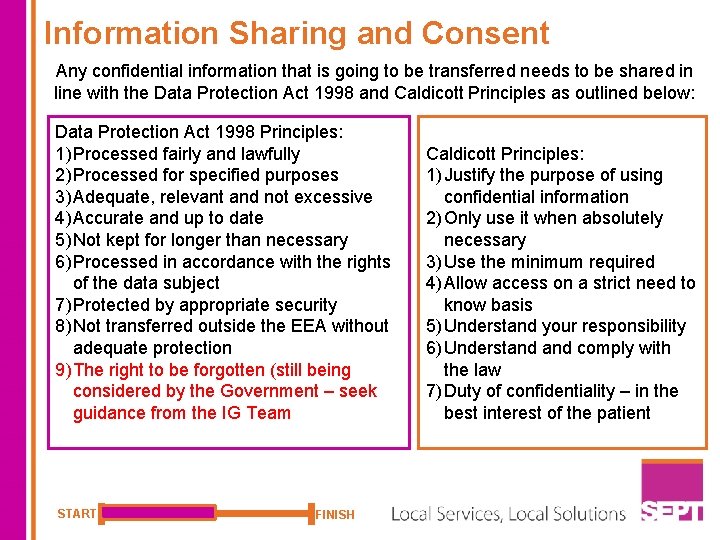
Information Sharing and Consent Any confidential information that is going to be transferred needs to be shared in line with the Data Protection Act 1998 and Caldicott Principles as outlined below: Data Protection Act 1998 Principles: 1) Processed fairly and lawfully 2) Processed for specified purposes 3) Adequate, relevant and not excessive 4) Accurate and up to date 5) Not kept for longer than necessary 6) Processed in accordance with the rights of the data subject 7) Protected by appropriate security 8) Not transferred outside the EEA without adequate protection 9) The right to be forgotten (still being considered by the Government – seek guidance from the IG Team START FINISH Caldicott Principles: 1) Justify the purpose of using confidential information 2) Only use it when absolutely necessary 3) Use the minimum required 4) Allow access on a strict need to know basis 5) Understand your responsibility 6) Understand comply with the law 7) Duty of confidentiality – in the best interest of the patient

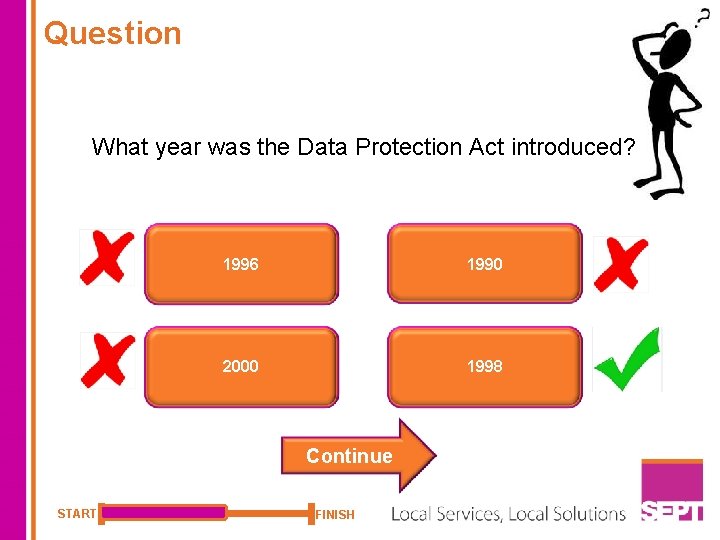
Question What year was the Data Protection Act introduced? 1996 1990 2000 1998 Continue START FINISH

Information Sharing Agreements Where you are considering sharing information or are involved in arranging information sharing agreements you must include the Information Governance Team at the earliest opportunity, and an Information Sharing Agreement (ISA) will be distributed for completion. Privacy Impact Assessments Where a new system/process or change to an existing system/process (paper or electronic) has been identified it is necessary the Information Governance Team are informed to ensure a Privacy Impact Assessment has been completed. This will then allow the Information Governance Team to determine if there any confidentiality, consent, privacy, security or data protection issues related to the new/changed/system/process. For further information on Privacy Impact Assessments, please refer to the ‘Conducting Privacy Impact Assessments Code of Practice’. http: //ico. org. uk/for_organisations/data_protection/topic_guides/~/media/docu ments/library/data_protection/practical_application/pia-code-of-practice-finaldraft. pdf START FINISH

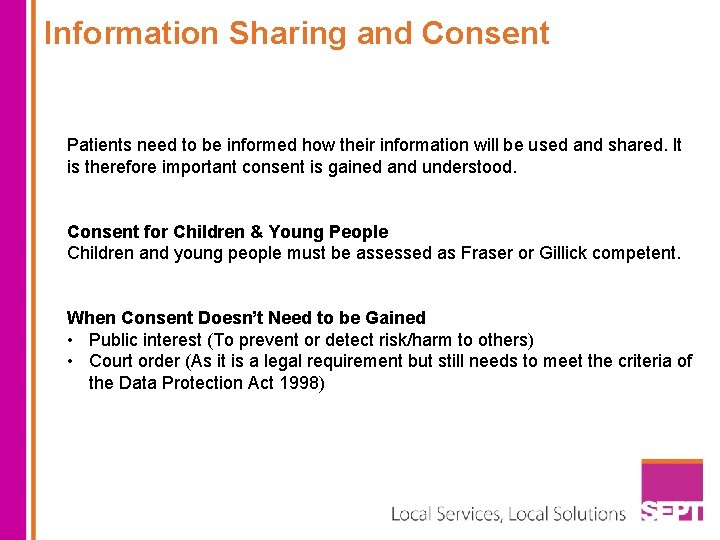
Information Sharing and Consent Patients need to be informed how their information will be used and shared. It is therefore important consent is gained and understood. Consent for Children & Young People Children and young people must be assessed as Fraser or Gillick competent. When Consent Doesn’t Need to be Gained • Public interest (To prevent or detect risk/harm to others) • Court order (As it is a legal requirement but still needs to meet the criteria of the Data Protection Act 1998)

Human Rights Act and Computer Misuse Act Human Rights Act: • Came into force in the UK in October 2000 • All public bodies (police, courts, hospitals, local governments) and others carrying out public functions have to comply with the convention rights. We work with article 8 of the Human Rights Act ‘Respect for your private and family life, home and correspondence’. Computer Misuse Act: Prior to 1990 there were no legislations in place to tackle the problems caused by hacking. Although it was known to be wrong and should be against the law, there was no framework in place to support this. As the problem grew, it became apparent that specific legislation was needed to enable individuals to be prosecuted under the law. So in 1990 the Computer Misuse Act was passed and recognised the following new offences. • • Unauthorised access to computer systems Unauthorised access with intent to commit or facilitate a crime Unauthorised modification of computer material Making, supplying or obtaining anything which can be used in computer misuse offences. START FINISH

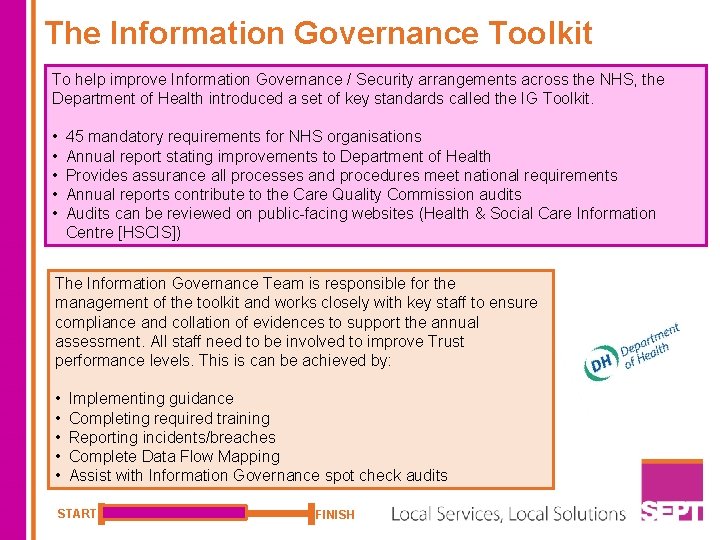
The Information Governance Toolkit To help improve Information Governance / Security arrangements across the NHS, the Department of Health introduced a set of key standards called the IG Toolkit. • • • 45 mandatory requirements for NHS organisations Annual report stating improvements to Department of Health Provides assurance all processes and procedures meet national requirements Annual reports contribute to the Care Quality Commission audits Audits can be reviewed on public-facing websites (Health & Social Care Information Centre [HSCIS]) The Information Governance Team is responsible for the management of the toolkit and works closely with key staff to ensure compliance and collation of evidences to support the annual assessment. All staff need to be involved to improve Trust performance levels. This is can be achieved by: • • • Implementing guidance Completing required training Reporting incidents/breaches Complete Data Flow Mapping Assist with Information Governance spot check audits START FINISH

Legal Services Data Protection Act (Subject Access Requests) & Freedom Of Information START FINISH

Data Subject Access Requests: The Data Protection Act 1998 gives an individual several rights in relation to the information held about them: • The right to seek access to their records held by the Trust • The right to obtain a copy of the record in permanent form or to view a record without obtaining a copy • The right to rectification, blocking, erasure (under very strict regulations) and destruction of information • For all staff related requests, access to records / information is required within 40 calendar days under the DPA Act • For all patient related access to health/medical records the Trust has to respond within 40 calendar days, unless the individual has been seen within 21 days in which case the information must be provided within 21 days of receipt of the application. When a request is made… there are two circumstances in which access can be denied and therefore the requestor may have the right to ask the Information Commissioner to assess: • If the record contains third party information and they have not consented to their information being disclosed • If access to all /part of the record will cause serious harm to the physical or mental wellbeing of the individual, or any other person. START FINISH

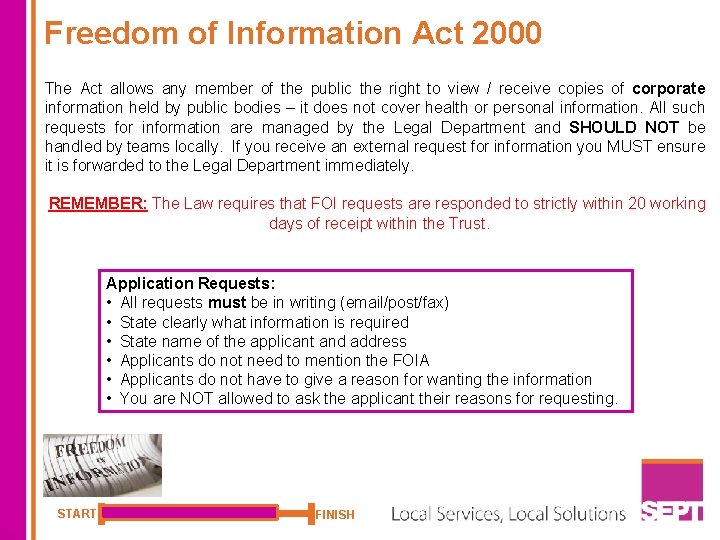
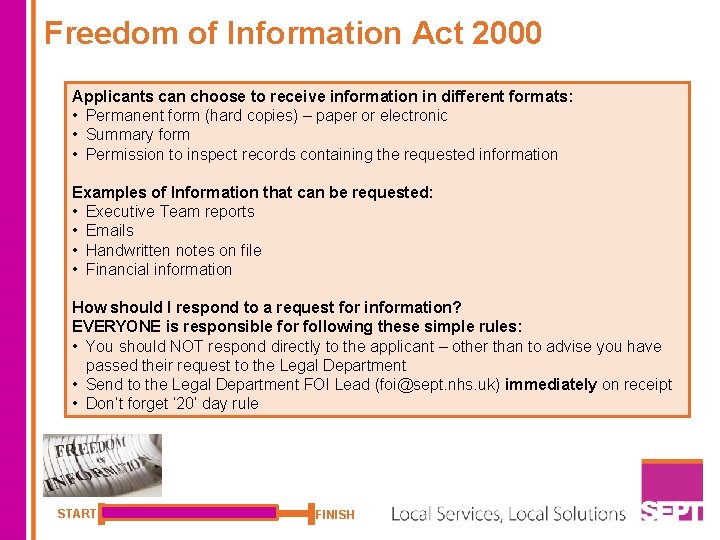
Freedom of Information Act 2000 The Act allows any member of the public the right to view / receive copies of corporate information held by public bodies – it does not cover health or personal information. All such requests for information are managed by the Legal Department and SHOULD NOT be handled by teams locally. If you receive an external request for information you MUST ensure it is forwarded to the Legal Department immediately. REMEMBER: The Law requires that FOI requests are responded to strictly within 20 working days of receipt within the Trust. Application Requests: • All requests must be in writing (email/post/fax) • State clearly what information is required • State name of the applicant and address • Applicants do not need to mention the FOIA • Applicants do not have to give a reason for wanting the information • You are NOT allowed to ask the applicant their reasons for requesting. START FINISH

Freedom of Information Act 2000 Applicants can choose to receive information in different formats: • Permanent form (hard copies) – paper or electronic • Summary form • Permission to inspect records containing the requested information Examples of Information that can be requested: • Executive Team reports • Emails • Handwritten notes on file • Financial information How should I respond to a request for information? EVERYONE is responsible for following these simple rules: • You should NOT respond directly to the applicant – other than to advise you have passed their request to the Legal Department • Send to the Legal Department FOI Lead (foi@sept. nhs. uk) immediately on receipt • Don’t forget ‘ 20’ day rule START FINISH

Data Subject Access Requests Publication Scheme The Publication Scheme is a guide to the information the Trust holds, and must be published on its website. It gives people access to some information without them having to make specific requests. The current publication scheme maybe found on the Trust’s internet site (www. sept. co. uk) START FINISH

Records Management START FINISH

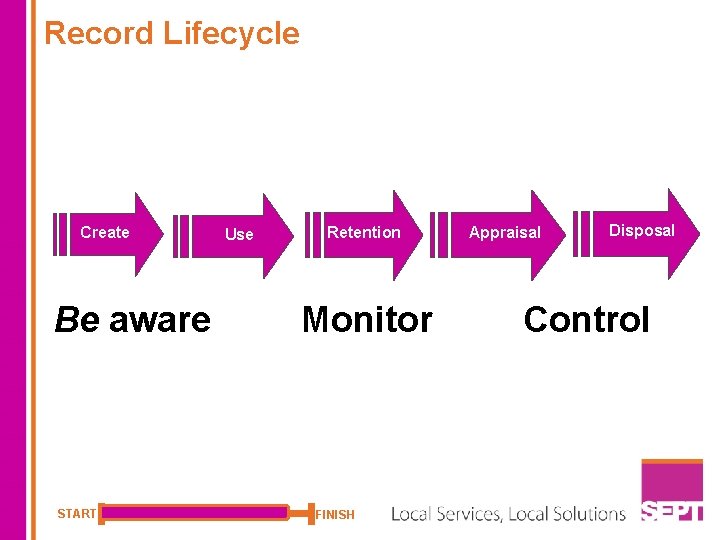
Record Lifecycle All individuals who work for an NHS organisation are responsible for the security of the information they handle or use in the performance of their duties and should keep all types of information: • • • Accurate Up to date Complete – including NHS number Quick and easy to find Free from duplication Free from fragmentation Any record created by an individual, up to its disposal, is a public record and subject to Information requests. Patients have to right to access their health records under the Data Protection Act/Access to Records (deceased) START FINISH

Record Lifecycle Create Be aware START Use Retention Monitor FINISH Appraisal Disposal Control

Record Management and Keeping Records Disposal: The Trusts’ corporate procedural guideline Storage, Retention and Destruction of Records will tell you which records should be kept for how long, prior to disposal. Health and Social Care records must only be destroyed when authorised by the Trusts Head of Records. For Corporate records: • Please ensure records are destroyed in a secure way. Either in blue confidential waste bags or shred using a cross cut shredder. Do not place identifiable information in waste paper bins. • Make note of how, when and where the record(s) were destroyed, together with any reference numbers. • If an applicant wants to see a record that is due to be destroyed, you must not destroy the record until the request has been answered or any complaint and appeals process has finished. • The destruction of all records must be completed in liaison with the Trusts’ Records Management Team. Records Management: Managing records effectively is essential for making access to information possible. Records management covers all aspects of a records life and should be: • • • Factual and correct Relevant and useful Clear and concise Up to date Complete They should not contain: • Unnecessary jargon • Personal opinions • Offensive language

Record Management and Keeping Record Types: Records can be in physical or technical formats, including: • In paper record keeping system • On computer, including emails • On film records, such as CCTV This list is not exhaustive Also covers: • Information located in confidential waste • Information on computers • Information stored on computer internal drives, USB sticks, CD and disks. 1) Create – Use appropriate Trust folders and formats 2) Use – Enter information, use of templates, filing, discharge summaries, clinical coding processes 3) Track – Log the location/pathway 4) Missing – Report to the manager 5) Retain – Look after, manage multiple volumes, hold until not required 6) Disposal Methods – confidentiality using Trust procedures START FINISH

Key Contacts: Overall responsibility for the Information Governance Agenda – Executive Chief Finance Officer & Resources Officer (Senior Information Risk Owner) / Director of ITT Responsibility for public and non-health requests for information – Executive Director Corporate Governance (Freedom of Information/ Data Subject Access Requests) Confidentiality / sharing of patient information – Executive Medical Director (Patient Safety Lead) / Caldicott Guardian Responsibility for the quality/accuracy of information – Assistant Director Systems Implementation & Data Quality (Community) Responsibility for the quality/accuracy of information, managing the IG agenda including the Toolkit and DPA – Assistant Director Systems Implementation & Data Quality (Mental Health) Responsibility for the implementation/security of records management and subject access requests (health) – Head of Records Management Responsibility for legal processes (Data Subject Access Requests (non-health) / Freedom of Information Requests) and general legal advice and guidance – Legal Department START FINISH

Remember, if you want to find more information / evidence about this subject or anything else which is relevant to your work or study, join your local healthcare library. For staff in Essex contact Basildon Healthcare Library. www. btuheks. nhs. uk library@btuh. nhs. uk 01268 524900 EX 3594 It may be that you work in a different area, for example Luton. Details of all the Health Libraries in the East of England can be found at this site… www. eel. nhs. uk You are welcome to join any of these. START FINISH

Review of Objective(s) Before completing the test, please ensure you have acquired the relevant knowledge against the modules objective(s) below: “You will understand: • • • Duty of Confidentiality Data Handling & Security Best Practice Guidelines Information Governance Toolkit Confidential/sensitive/corporate Information Sharing & Privacy Impact Assessments Consent Personal information – Data Protection Act Corporate information – Freedom of Information” If not, please take this opportunity to revisit the presentation content. CONTINUE START FINISH

You now need to take the test! e s r p e l m a x E START FINISH u o C Remember to click the ‘home’ icon when you have finished the test to save your results!