Department of Computer and IT Engineering University of
































- Slides: 63

Department of Computer and IT Engineering University of Kurdistan Computer Networks II Transport Layer (UDP and TCP) By: Dr. Alireza Abdollahpouri 1

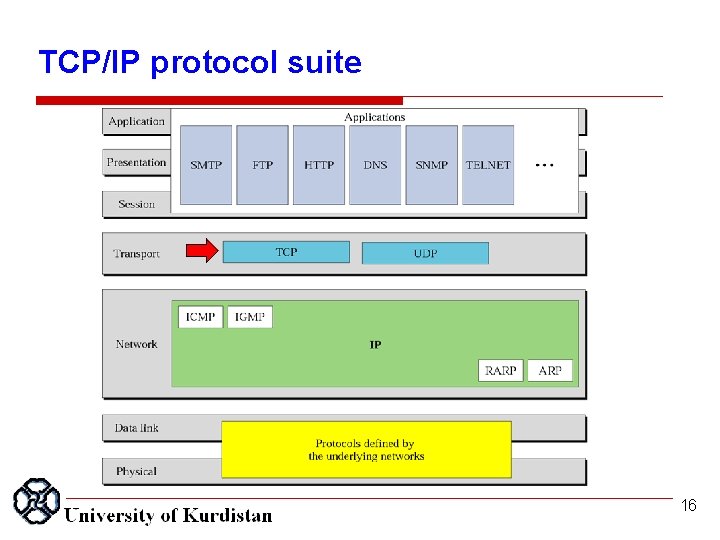
TCP/IP protocol suite 2

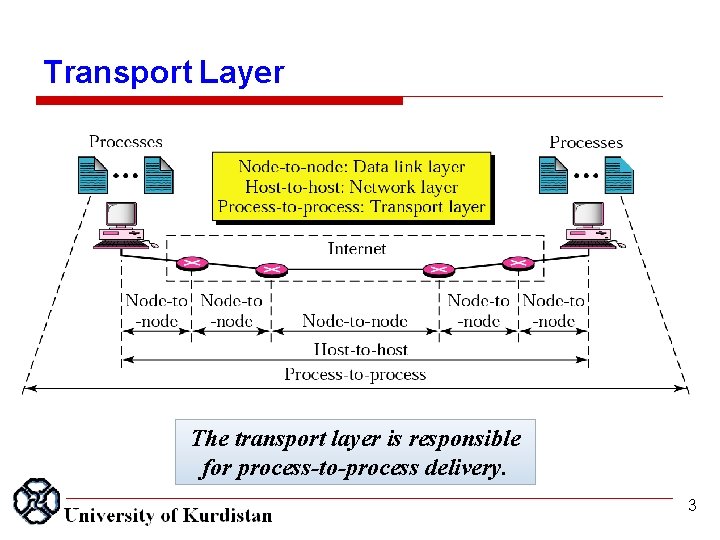
Transport Layer The transport layer is responsible for process-to-process delivery. 3

Transport Layer provide logical communication between application processes running on different hosts transport protocols run in end systems sending side: breaks app messages into segments, passes to network layer receiving side: reassembles segments into messages, messages passes to application layer more than one transport protocol available to applications. Internet: TCP and UDP application transport network data link physical Logical end to end transport network data link physical application transport network data link physical 4

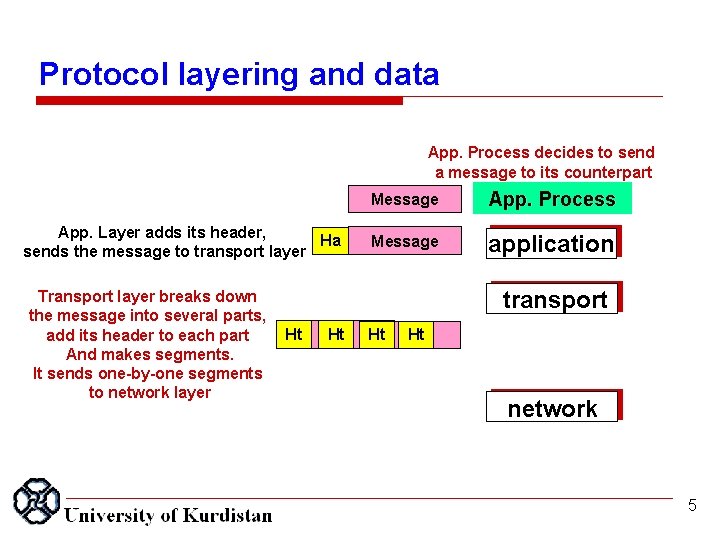
Protocol layering and data App. Process decides to send a message to its counterpart App. Layer adds its header, Ha sends the message to transport layer Transport layer breaks down the message into several parts, add its header to each part And makes segments. It sends one-by-one segments to network layer Message App. Process Message application transport Ht Ht network 5

Port numbers 6

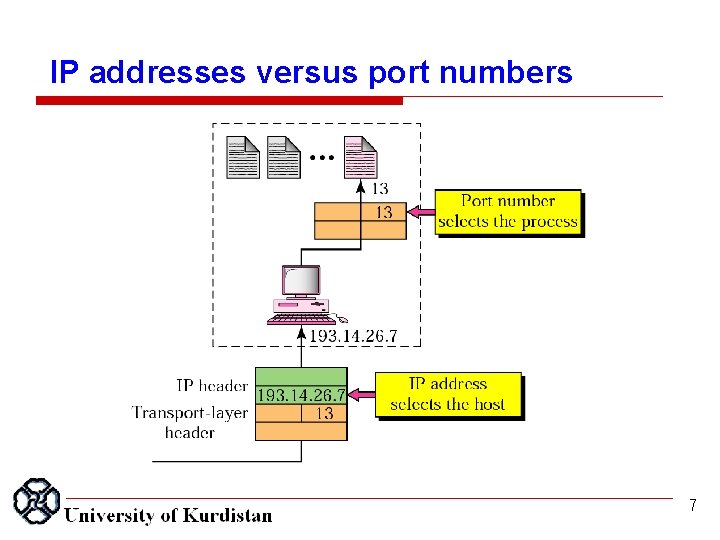
IP addresses versus port numbers 7

IANA ranges for port numbers 8

Socket address 9

Multiplexing and demultiplexing 10

TCP/IP protocol suite 11

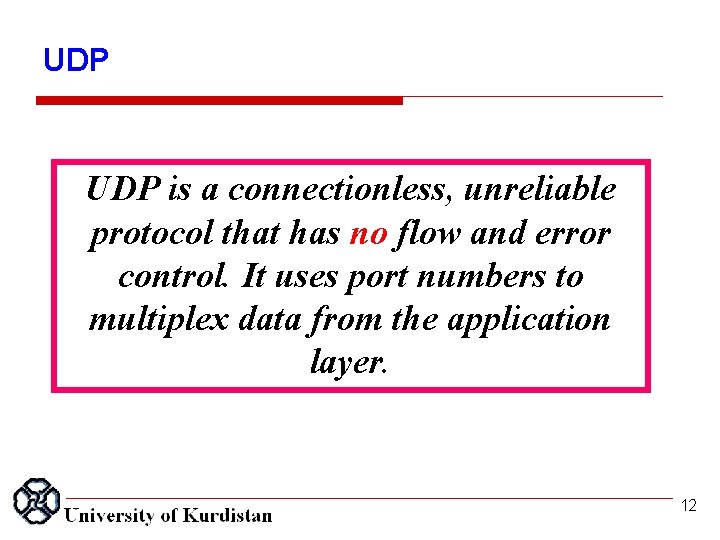
UDP is a connectionless, unreliable protocol that has no flow and error control. It uses port numbers to multiplex data from the application layer. 12

Some Well-known ports used by UDP Port Protocol Description 13 Daytime 17 Quote 53 Nameserver 67 Bootps Server port to download bootstrap information 68 Bootpc Client port to download bootstrap information 69 TFTP Trivial File Transfer Protocol 111 RPC Remote Procedure Call 123 NTP Network Time Protocol 161 SNMP Returns the date and the time Returns a quote of the day Domain Name Service Simple Network Management Protocol 13

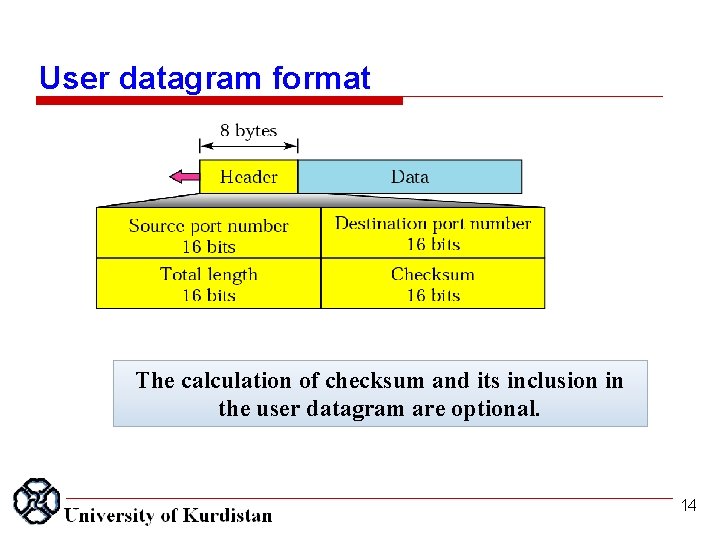
User datagram format The calculation of checksum and its inclusion in the user datagram are optional. 14

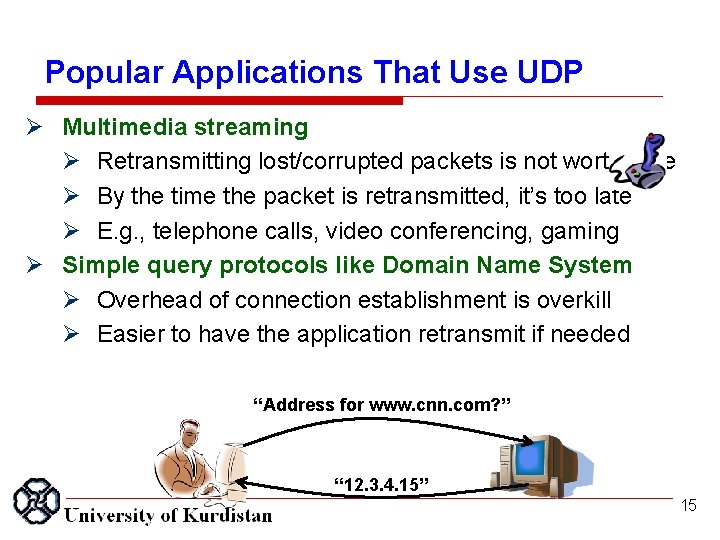
Popular Applications That Use UDP Multimedia streaming Retransmitting lost/corrupted packets is not worthwhile By the time the packet is retransmitted, it’s too late E. g. , telephone calls, video conferencing, gaming Simple query protocols like Domain Name System Overhead of connection establishment is overkill Easier to have the application retransmit if needed “Address for www. cnn. com? ” “ 12. 3. 4. 15” 15

TCP/IP protocol suite 16

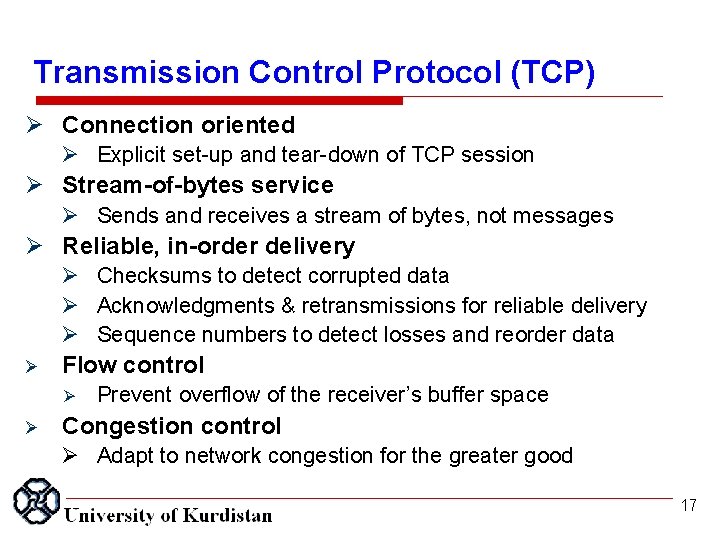
Transmission Control Protocol (TCP) Connection oriented Explicit set-up and tear-down of TCP session Stream-of-bytes service Sends and receives a stream of bytes, not messages Reliable, in-order delivery Checksums to detect corrupted data Acknowledgments & retransmissions for reliable delivery Sequence numbers to detect losses and reorder data Flow control Prevent overflow of the receiver’s buffer space Congestion control Adapt to network congestion for the greater good 17




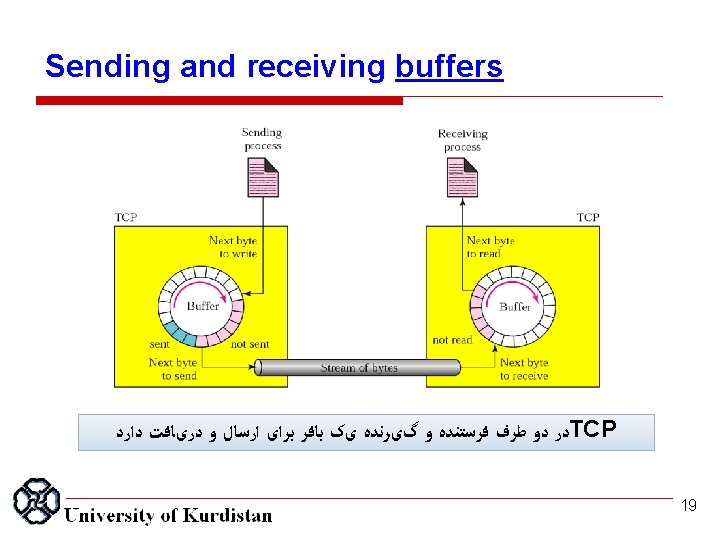
Note: The bytes of data being transferred in each connection are numbered by TCP. The numbering starts with a randomly generated number. 21

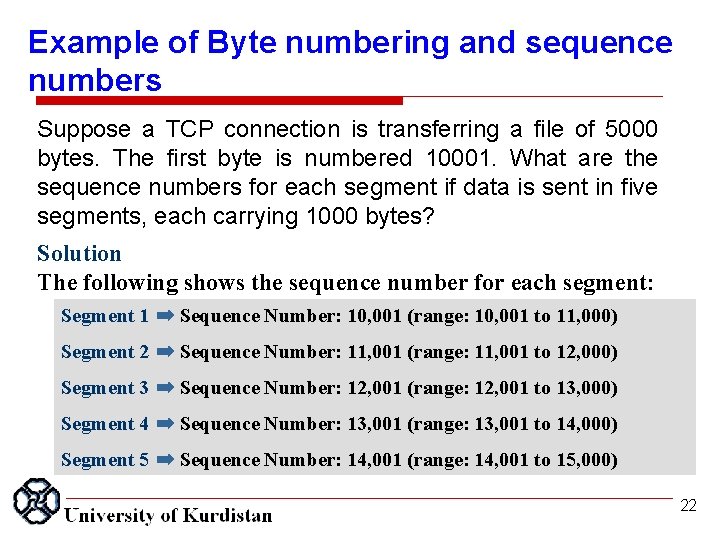
Example of Byte numbering and sequence numbers Suppose a TCP connection is transferring a file of 5000 bytes. The first byte is numbered 10001. What are the sequence numbers for each segment if data is sent in five segments, each carrying 1000 bytes? Solution The following shows the sequence number for each segment: Segment 1 ➡ Sequence Number: 10, 001 (range: 10, 001 to 11, 000) Segment 2 ➡ Sequence Number: 11, 001 (range: 11, 001 to 12, 000) Segment 3 ➡ Sequence Number: 12, 001 (range: 12, 001 to 13, 000) Segment 4 ➡ Sequence Number: 13, 001 (range: 13, 001 to 14, 000) Segment 5 ➡ Sequence Number: 14, 001 (range: 14, 001 to 15, 000) 22

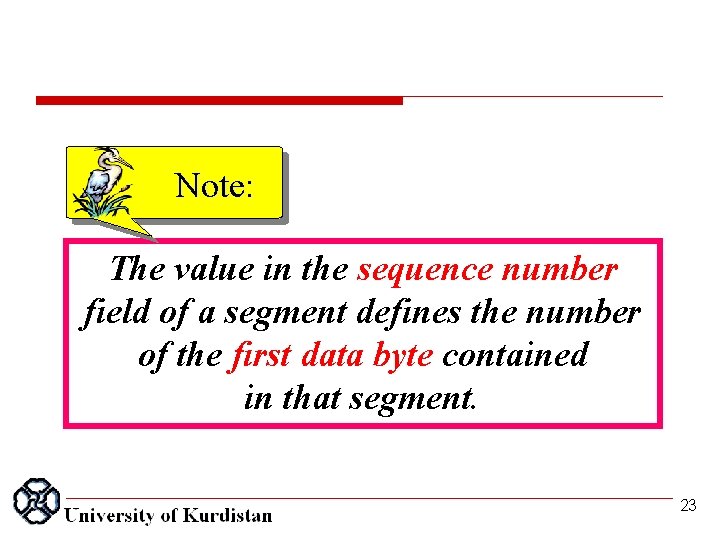
Note: The value in the sequence number field of a segment defines the number of the first data byte contained in that segment. 23

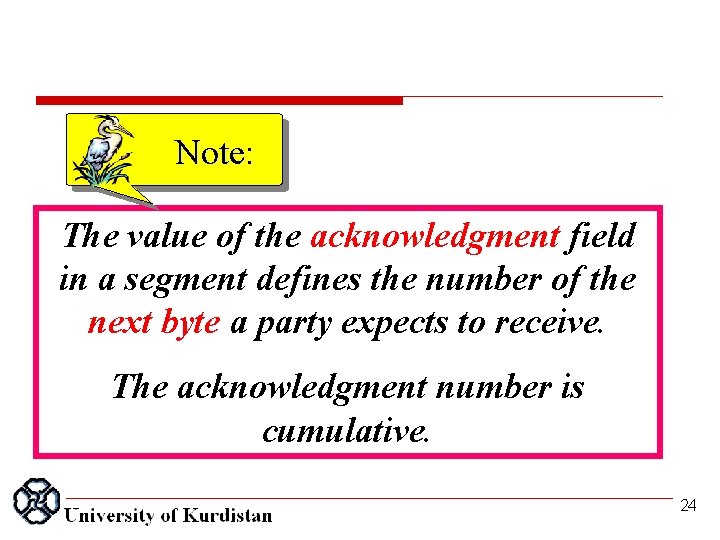
Note: The value of the acknowledgment field in a segment defines the number of the next byte a party expects to receive. The acknowledgment number is cumulative. 24

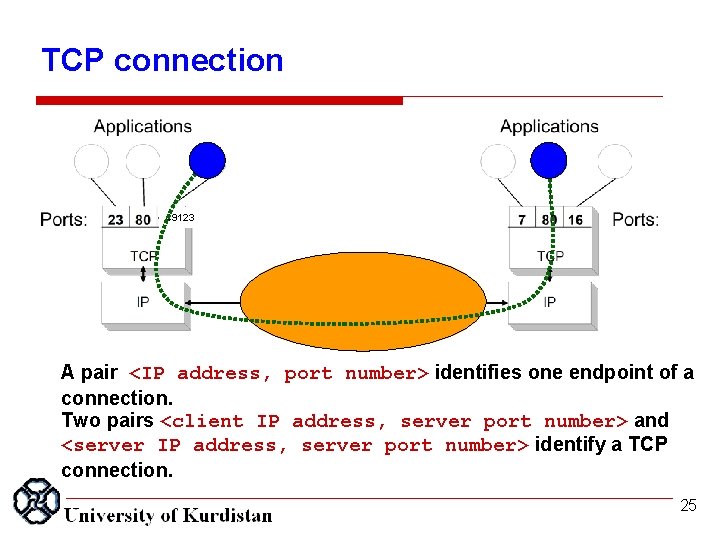
TCP connection 49123 A pair <IP address, port number> identifies one endpoint of a connection. Two pairs <client IP address, server port number> and <server IP address, server port number> identify a TCP connection. 25

data 12… 1001 … 4001 … 5001… Byte Seq=5001 Seq=4001 Seq=3001 Seq=2001 Seq=1001 Seq=001 TCP Header 2001 … 3001 … Data is broken into 6 1000 -Byte-segments. 26





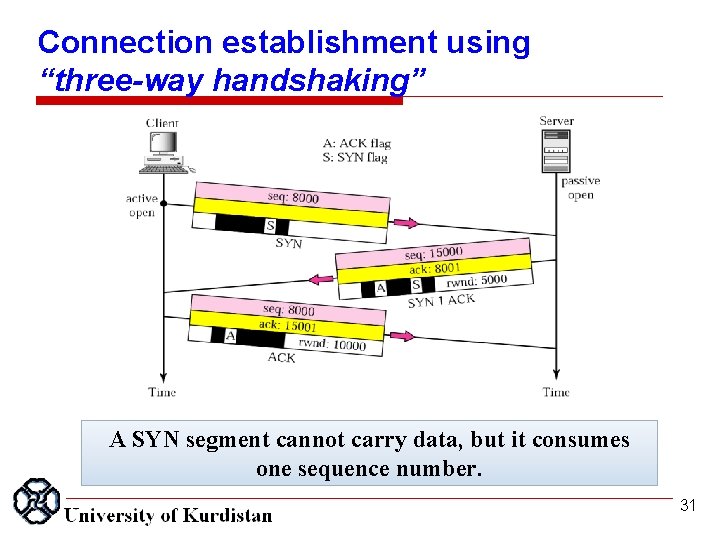
Connection establishment using “three-way handshaking” A SYN segment cannot carry data, but it consumes one sequence number. 31

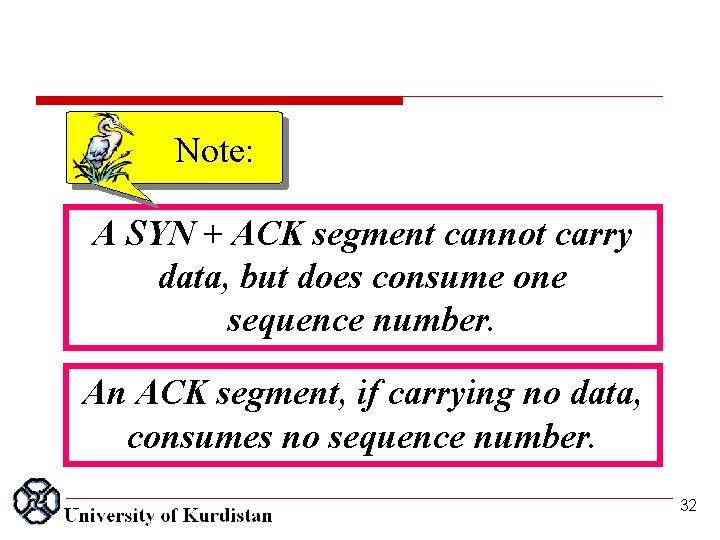
Note: A SYN + ACK segment cannot carry data, but does consume one sequence number. An ACK segment, if carrying no data, consumes no sequence number. 32

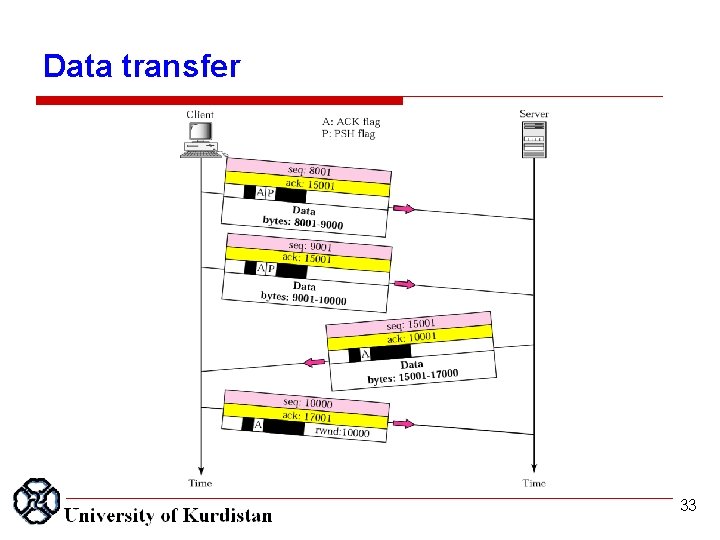
Data transfer 33

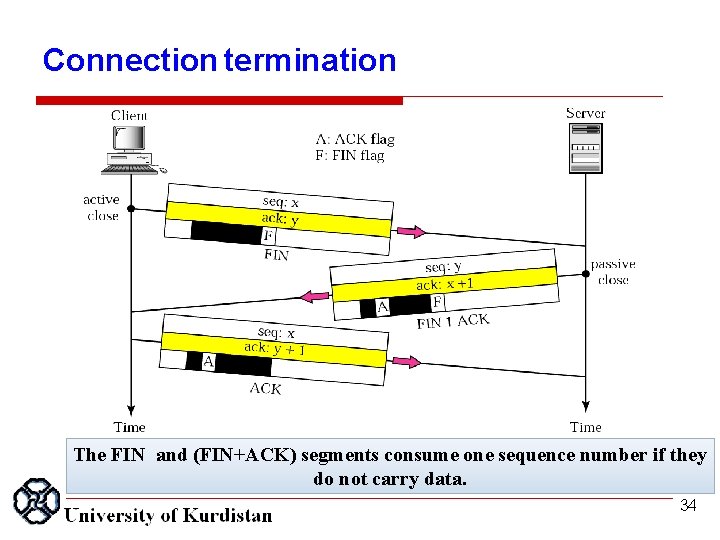
Connection termination The FIN and (FIN+ACK) segments consume one sequence number if they do not carry data. 34

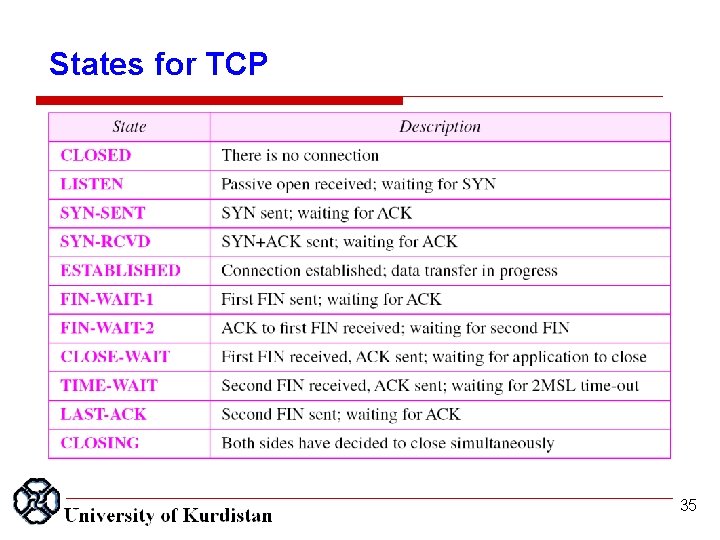
States for TCP 35

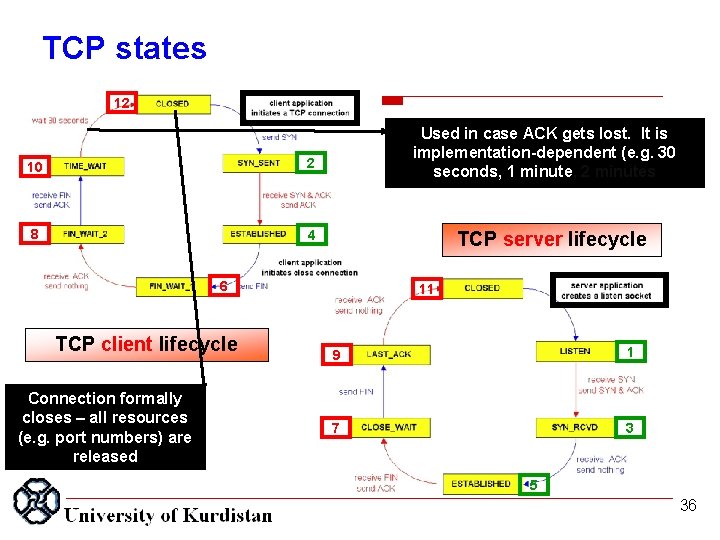
TCP states 12 10 2 8 4 Used in case ACK gets lost. It is implementation-dependent (e. g. 30 seconds, 1 minute, 2 minutes TCP server lifecycle 6 TCP client lifecycle Connection formally closes – all resources (e. g. port numbers) are released 11 9 1 7 3 5 36

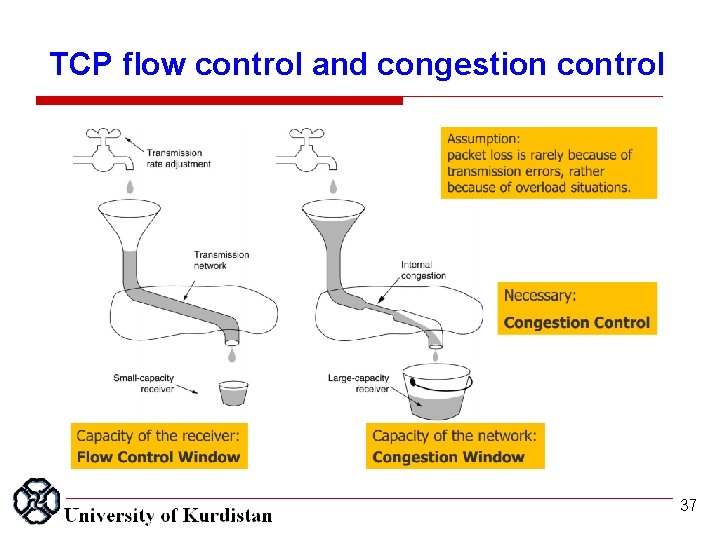
TCP flow control and congestion control 37


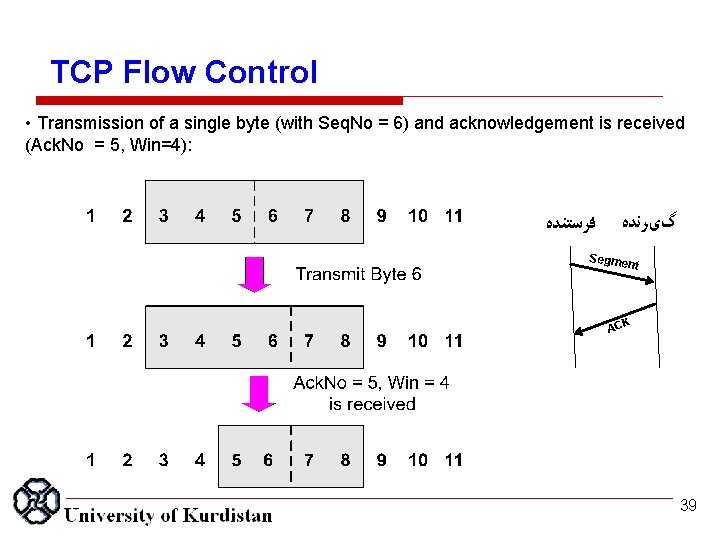
TCP Flow Control • Transmission of a single byte (with Seq. No = 6) and acknowledgement is received (Ack. No = 5, Win=4): ﻓﺮﺳﺘﻨﺪﻩ گیﺮﻧﺪﻩ Segme nt ACK 39

TCP Flow Control • Acknowledgement is received that enlarges the window to the right (Ack. No = 5, Win=6): 40

Sliding Window: Example 41

42

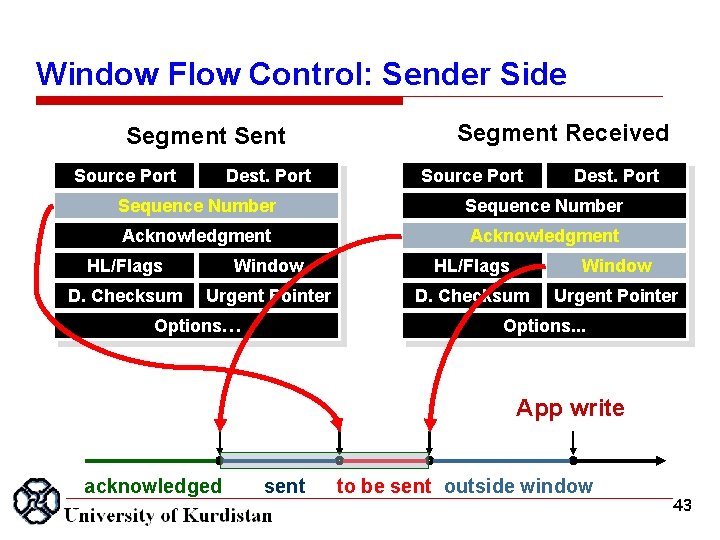
Window Flow Control: Sender Side Segment Source Port Dest. Port Segment Received Source Port Dest. Port Sequence Number Acknowledgment HL/Flags Window D. Checksum Urgent Pointer Options… Options. . . App write acknowledged sent to be sent outside window 43


TCP Congestion Control TCP limit sending rate as a function of perceived network congestion little traffic – increase sending rate much traffic – reduce sending rate Congestion algorithm has three major “components”: additive-increase, multiplicative-decrease (AIMD) slow-start reaction to timeout events 45



TCP in action TCP AQM TCP ACK… Drop!!! ACK… Queue Inbound Link Router Sink Outbound Link ACK… Congestion Notification… Sink 48

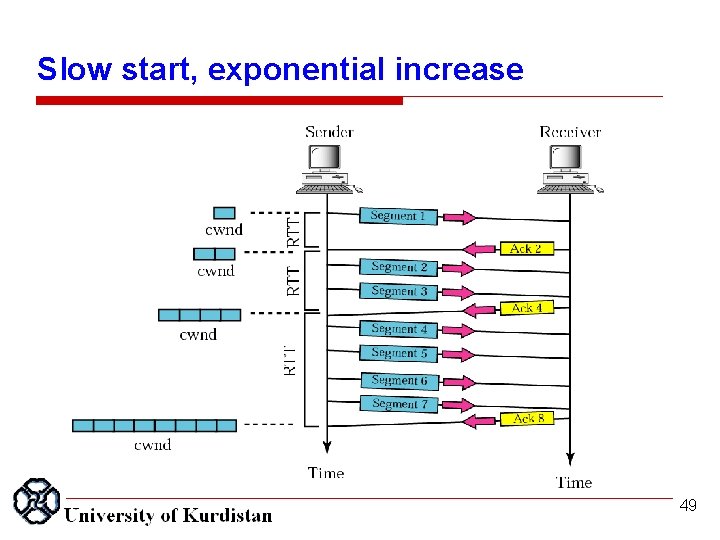
Slow start, exponential increase 49

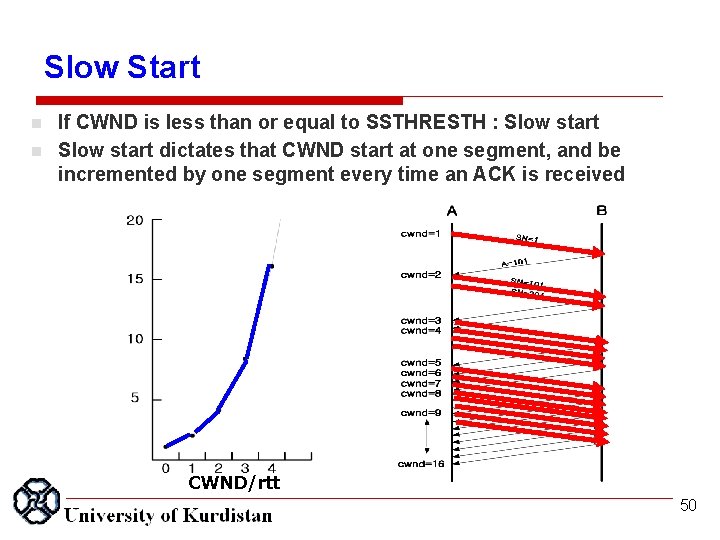
Slow Start n n If CWND is less than or equal to SSTHRESTH : Slow start dictates that CWND start at one segment, and be incremented by one segment every time an ACK is received CWND/rtt 50

Note: In the slow start algorithm, the size of the congestion window increases exponentially until it reaches a threshold. 51

Additive increase 52

Note: In the congestion avoidance algorithm the size of the congestion window increases additively until congestion is detected. 53

Note: Most implementations react differently to congestion detection: ❏ If detection is by time-out, a new slow start phase starts. ❏ If detection is by three ACKs, a new congestion avoidance phase starts. 54

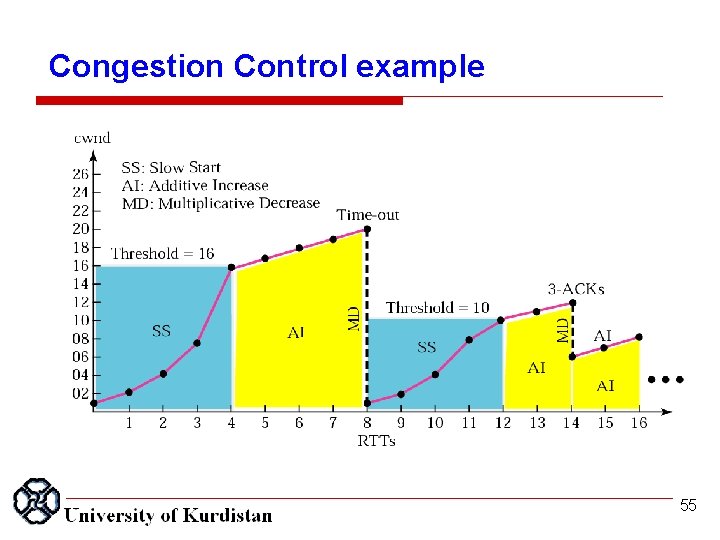
Congestion Control example 55

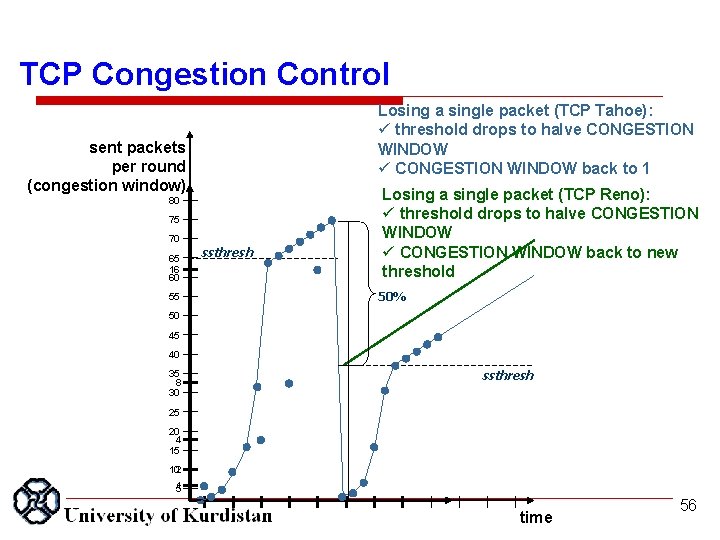
TCP Congestion Control Losing a single packet (TCP Tahoe): ü threshold drops to halve CONGESTION WINDOW ü CONGESTION WINDOW back to 1 sent packets per round (congestion window) 80 75 70 65 16 60 55 ssthresh Losing a single packet (TCP Reno): ü threshold drops to halve CONGESTION WINDOW ü CONGESTION WINDOW back to new threshold 50% 50 45 40 35 8 30 ssthresh 25 20 4 15 102 1 5 time 56

TCP Behavior W 8 Calculate “average packet loss rate” and “average throughput” 7 6 5 4 3 2 1 RTT 57

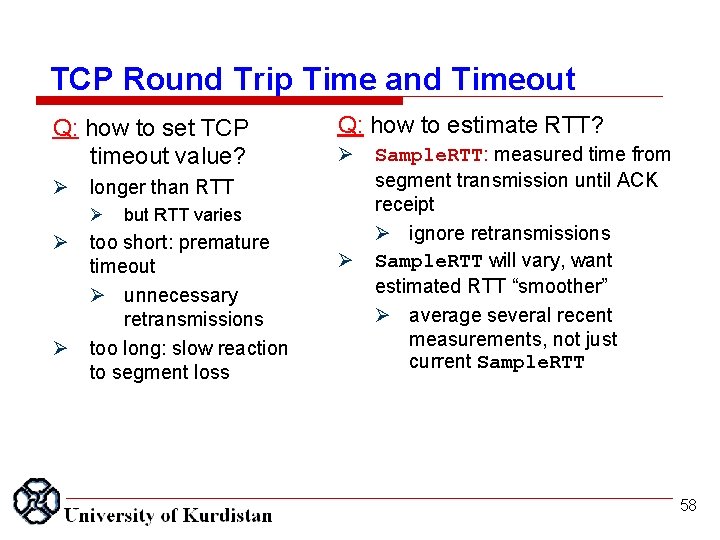
TCP Round Trip Time and Timeout Q: how to set TCP timeout value? longer than RTT Q: how to estimate RTT? but RTT varies too short: premature timeout unnecessary retransmissions too long: slow reaction to segment loss Sample. RTT: measured time from segment transmission until ACK receipt ignore retransmissions Sample. RTT will vary, want estimated RTT “smoother” average several recent measurements, not just current Sample. RTT 58

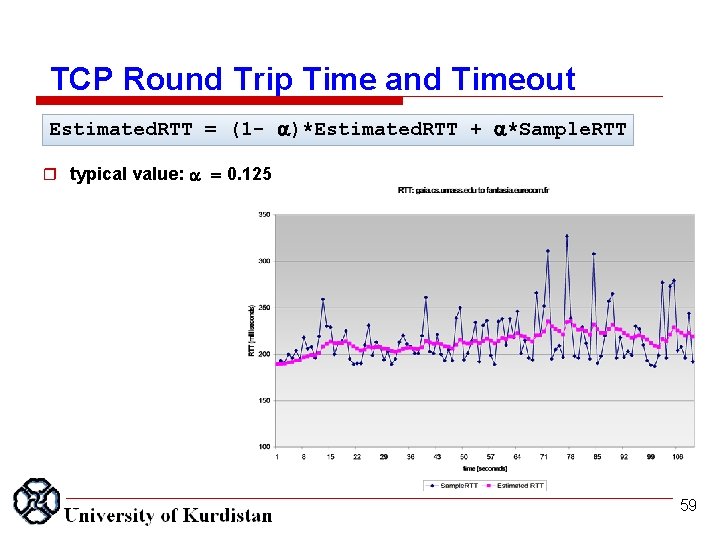
TCP Round Trip Time and Timeout Estimated. RTT = (1 - )*Estimated. RTT + *Sample. RTT r typical value: = 0. 125 59

TCP Round Trip Time and Timeout Setting the timeout Estimated. RTT plus “safety margin” large variation in Estimated. RTT -> larger safety margin first estimate of how much Sample. RTT deviates from Estimated. RTT: Dev. RTT = (1 - )*Dev. RTT + *|Sample. RTT-Estimated. RTT| (typically, = 0. 25) Then set timeout interval: Timeout. Interval = Estimated. RTT + 4*Dev. RTT 60

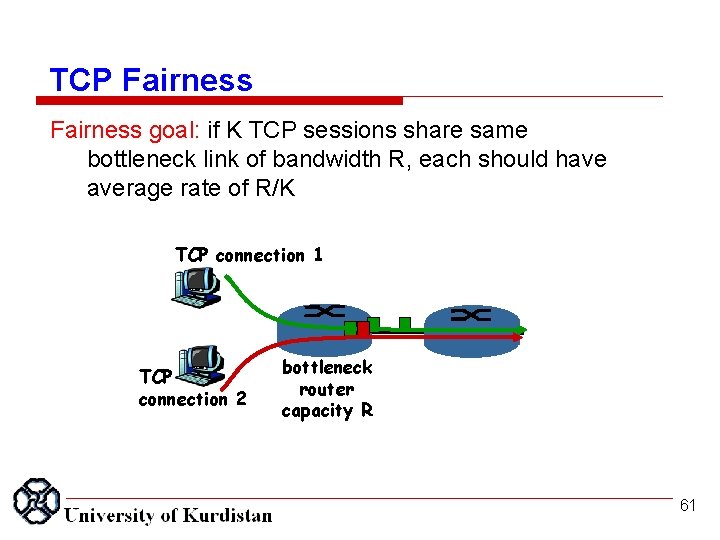
TCP Fairness goal: if K TCP sessions share same bottleneck link of bandwidth R, each should have average rate of R/K TCP connection 1 TCP connection 2 bottleneck router capacity R 61

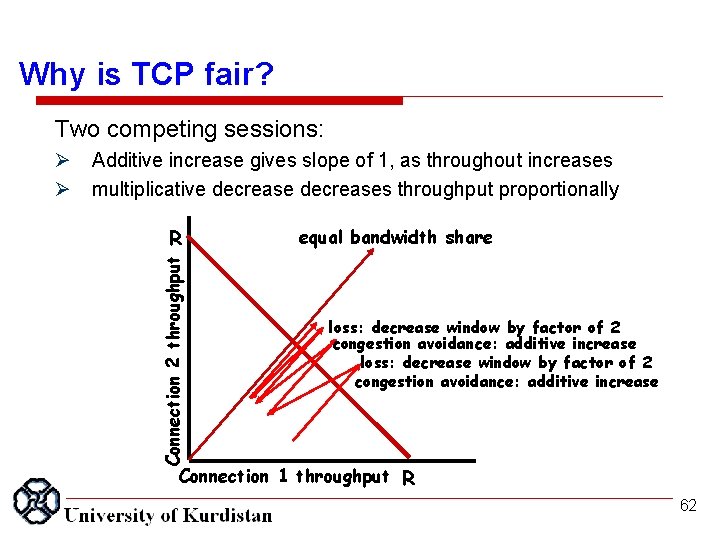
Why is TCP fair? Two competing sessions: Additive increase gives slope of 1, as throughout increases multiplicative decreases throughput proportionally R Connection 2 throughput equal bandwidth share loss: decrease window by factor of 2 congestion avoidance: additive increase Connection 1 throughput R 62

Questions 63
 Tum department of electrical and computer engineering
Tum department of electrical and computer engineering Department of information engineering university of padova
Department of information engineering university of padova Information engineering padova
Information engineering padova University of sargodha engineering department
University of sargodha engineering department Computer engineering department
Computer engineering department Mice.cs.columbia
Mice.cs.columbia Computer based system engineering in software engineering
Computer based system engineering in software engineering Bridgeport engineering department
Bridgeport engineering department Northwestern computer science department
Northwestern computer science department Hacettepe university computer engineering
Hacettepe university computer engineering City of houston department of public works and engineering
City of houston department of public works and engineering Dmse iitd
Dmse iitd Electrical engineering department
Electrical engineering department Hotel engineering department
Hotel engineering department Kpi for engineers
Kpi for engineers University of bridgeport computer science
University of bridgeport computer science Ucla systems engineering
Ucla systems engineering Department of law university of jammu
Department of law university of jammu Department of geology university of dhaka
Department of geology university of dhaka Mechanicistic
Mechanicistic University of bridgeport it department
University of bridgeport it department Iowa state math department
Iowa state math department Sputonik
Sputonik Texas state majors
Texas state majors Manipal university chemistry department
Manipal university chemistry department Syracuse university psychology department
Syracuse university psychology department Jackson state university finance department
Jackson state university finance department Michigan state astronomy
Michigan state astronomy Columbia university cs department
Columbia university cs department Stanford university philosophy department
Stanford university philosophy department Forward engineering in software engineering
Forward engineering in software engineering Brad karp ucl
Brad karp ucl Computer science department rutgers
Computer science department rutgers Vptl tutoring stanford
Vptl tutoring stanford Fsu computer science department
Fsu computer science department Ubc computer science department
Ubc computer science department Department of computer science christ
Department of computer science christ Klipsch school of electrical and computer engineering
Klipsch school of electrical and computer engineering Ucf computer engineering
Ucf computer engineering Erik jonsson school of engineering and computer science
Erik jonsson school of engineering and computer science Computer science and engineering unr
Computer science and engineering unr Ucla
Ucla Erik jonsson school of engineering and computer science
Erik jonsson school of engineering and computer science Erik jonsson school of engineering
Erik jonsson school of engineering General objectives of computer
General objectives of computer What is computer organization
What is computer organization Monitor printer speaker and projector are blank devices
Monitor printer speaker and projector are blank devices Architecture and organization difference
Architecture and organization difference Dicapine
Dicapine Elegant systems
Elegant systems Forward and reverse engineering
Forward and reverse engineering Ytu erasmus ofisi
Ytu erasmus ofisi Aalto university school of engineering
Aalto university school of engineering Tel aviv university electrical engineering
Tel aviv university electrical engineering Louisiana tech university engineering
Louisiana tech university engineering Oakland
Oakland Temple university environmental engineering
Temple university environmental engineering Chemical engineering wisconsin
Chemical engineering wisconsin University of twente biomedical engineering
University of twente biomedical engineering Utah state university engineering
Utah state university engineering University of belgrade school of electrical engineering
University of belgrade school of electrical engineering Gwu electrical engineering
Gwu electrical engineering Sjsu mechanical engineering
Sjsu mechanical engineering Engineering statistics philadelphia university
Engineering statistics philadelphia university