DATA ENCRYPTION STANDARD DES Rajdeep Shaktawat Information Security







- Slides: 23

DATA ENCRYPTION STANDARD (DES) Rajdeep Shaktawat – Information Security

DATA ENCRYPTION STANDARD �The Data Encryption Standard (DES) is a symmetric-key block cipher published by the National Institute of Standards and Technology (NIST). �In 1973, NIST published a request for proposals for a national symmetric-key cryptosystem. A proposal from IBM, a modification of a project called Lucifer, was accepted as DES was published in the Federal Register in March 1975 as a draft of the Federal Information Processing Standard (FIPS).

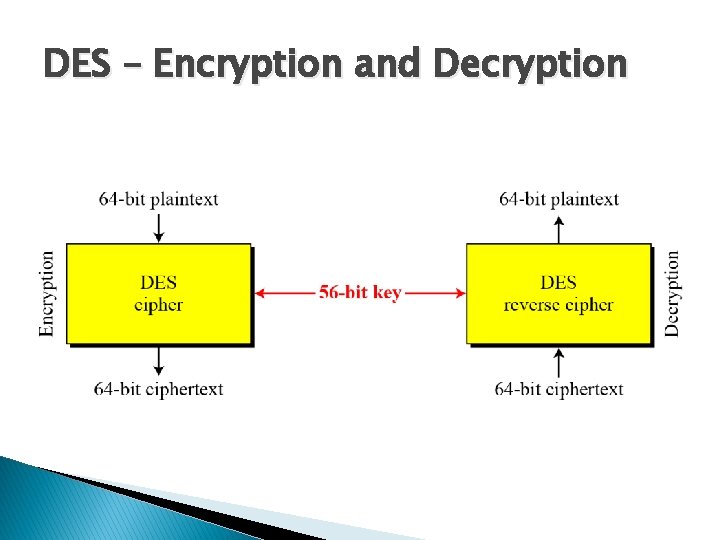
DES – Encryption and Decryption

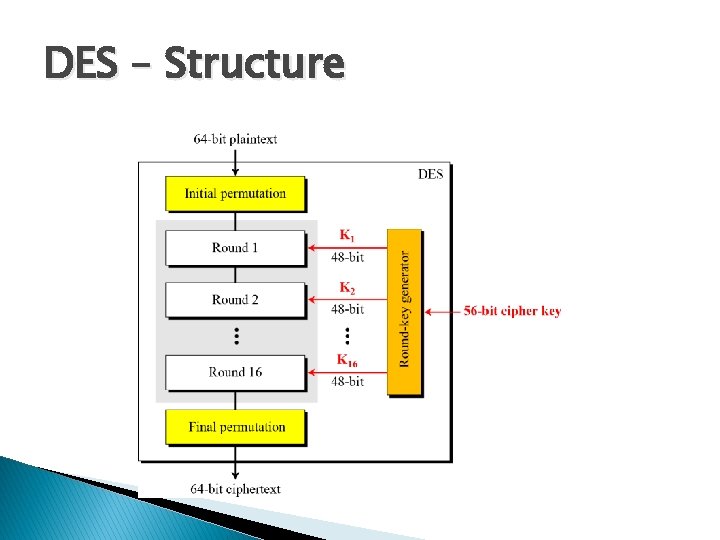
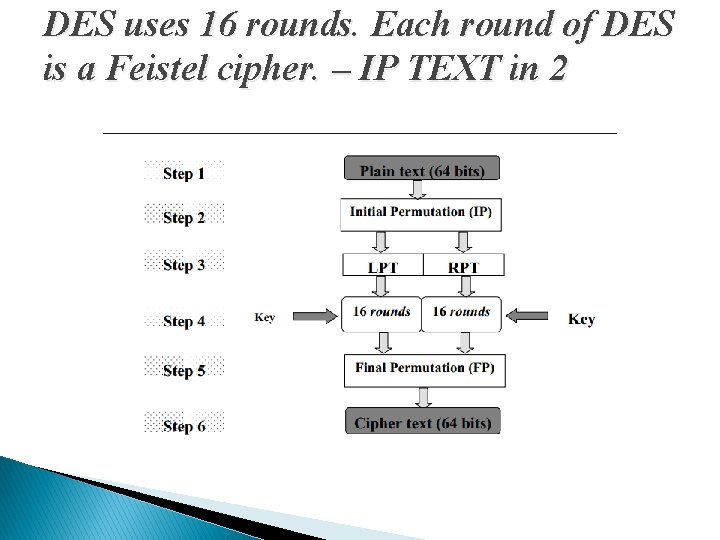
DES Structure �Des is based on Confusion and Diffusion �The encryption process is made of two permutations (P-boxes), which we call initial and final permutations, and sixteen Feistel rounds. �Every 8 th bit is discarded from 64 bit key which results in 56 bit key.

DES – Structure

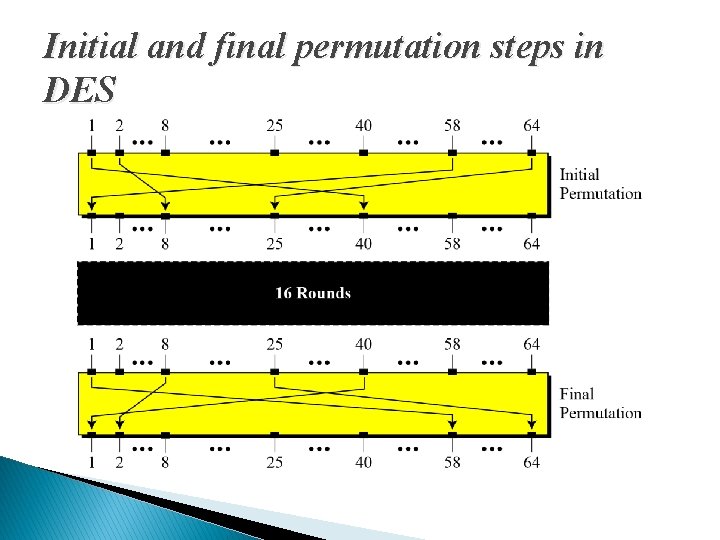
Initial and final permutation steps in DES

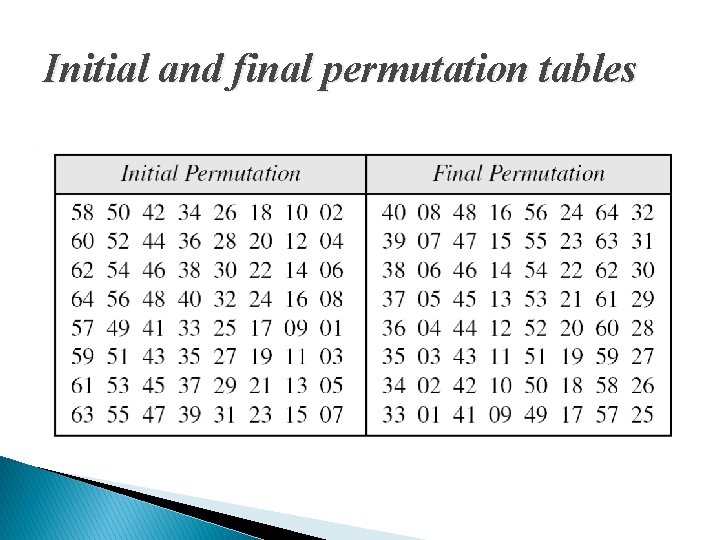
Initial and final permutation tables

NOTE** � The initial and final permutations are straight P-boxes that are inverses of each other. � They have no cryptography significance in DES.

DES uses 16 rounds. Each round of DES is a Feistel cipher. – IP TEXT in 2

What happen in each round

Ke. Y Transformation � 48 bit sub key is generated in each round from 56 bit key which we have by process KEY TRANSFORMATION � 56 bit key divided in two halves : 28 each � These halves are circularly shifted by one two positions depending on rounds � After shifting 48 bit key from two halves are selected from 56 bit key set � Compression permutation

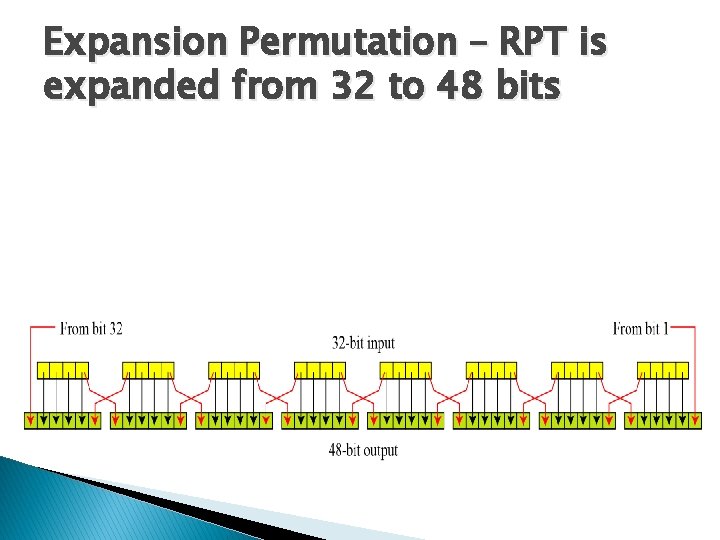
Expansion Permutation – RPT is expanded from 32 to 48 bits

Before going in S – BOX � The 48 bit RPT out obtained in “ XOR” with 48 bit subkey generated from 56 bit key

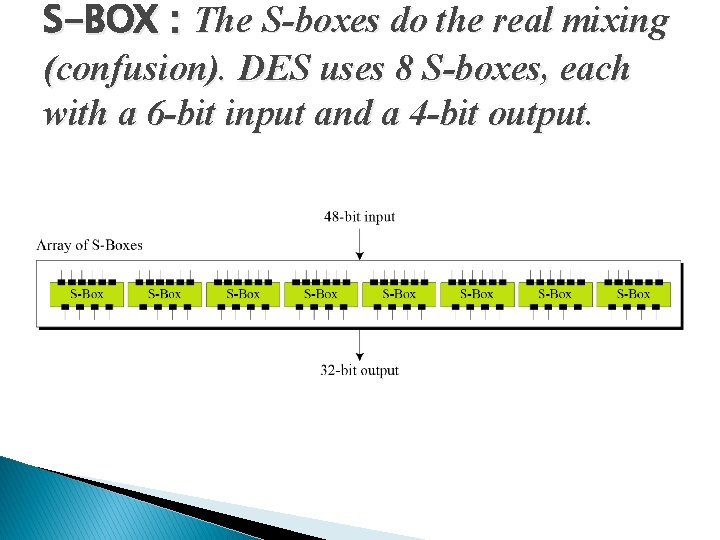
S-BOX : The S-boxes do the real mixing (confusion). DES uses 8 S-boxes, each with a 6 -bit input and a 4 -bit output.

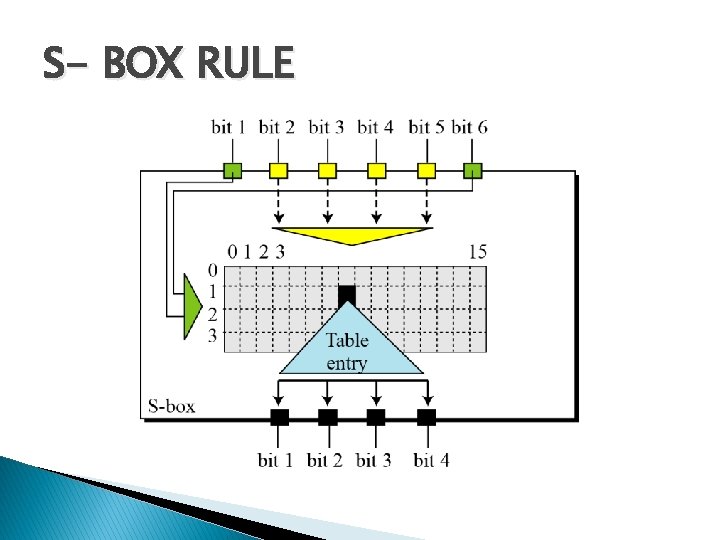
S- BOX RULE

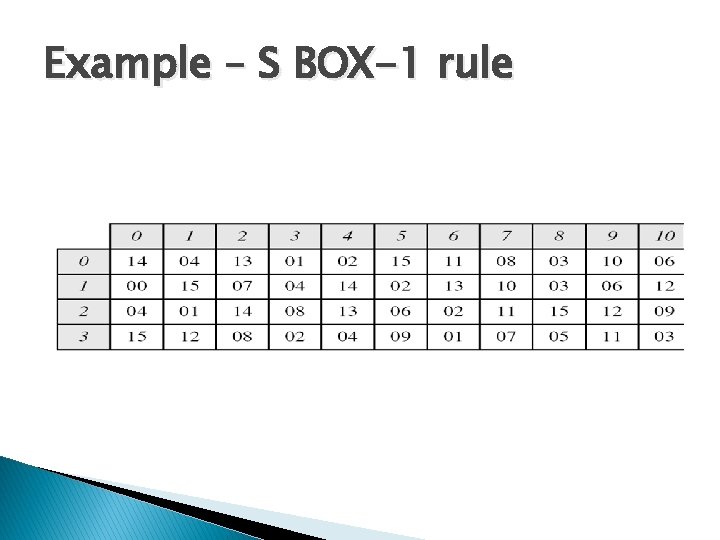
Example – S BOX-1 rule

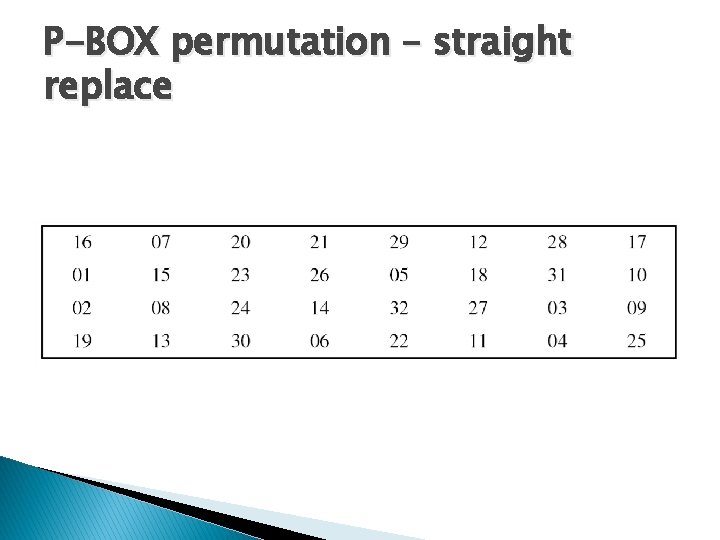
P-BOX permutation – straight replace

XOR and SWAP � LPT was untouched in whole process � RESULT LPT “XOR” RPT (After 1 round process) � For NEXT ROUND � Old RPT becomes now LPT � And RESULT becomes RPT

After 16 such rounds Final Permutation � Refer from Text book � 4 rows 16 coulmns

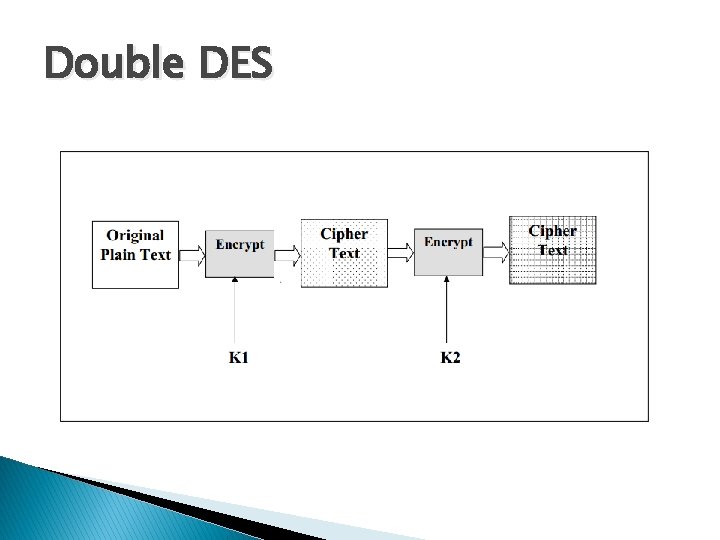
Double DES

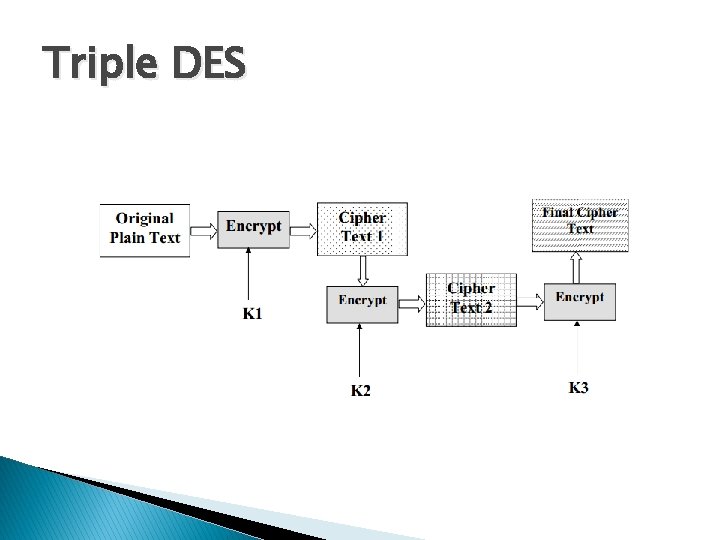
Triple DES

Strength of DES �S box design took years for IBM � 56 -bit keys have 256 = 7. 2 x 1016 values ◦ Brute force search looks hard. ◦ A machine performing one DES encryption per microsecond would take more than a thousand year to break the cipher. � Recent advances have shown is possible ◦ in 1997 on Internet in a few months ◦ in 1998 on dedicated h/w in a few days ◦ in 1999 above combined in 22 hrs!

Meet in the MIDDLE ATTACK � …. .