Cryptanalysis on Clock Controlled Stream Ciphers Shinsaku Kiyomoto







- Slides: 26

Cryptanalysis on Clock Controlled Stream Ciphers Shinsaku Kiyomoto KDDI R&D Laboratories Inc. 2005. 2. 22 This is a joint work with Kyushu University (Prof. Kouichi Sakurai) ©KDDI R&D Laboratories Inc. ALL Rights Reserved.

Information about Myself • Shinsaku Kiyomoto (age 29) – B. E. and M. E. from Tsukuba Univ. (1998 and 2000) – Researcher of Security Lab. in KDDI R&D Labs. Inc. (from April, 2000) – Current Interests: Stream Cipher, Security protocols, and Mobile Security ©KDDI R&D Laboratories Inc. ALL Rights Reserved.

KDDI R&D Laboratories Inc. http: //www. kddilabs. jp ● Incorporated April 1, 2003 (Merged KDI in April 1, 2001) ● Capital 2. 28 billion Yen ● Shareholders KDDI , Kyocera corporation, Toyota motor corporation ● President Tohru ASAMI ● Staff 197(April 1, 2004) ● Office Kamifukuoka, Saitama, Japan ● Research Area Photonic NW, Wireless NW, IP, Multimedia, Ubiquitous NW, and Information Security ©KDDI R&D Laboratories Inc. ALL Rights Reserved.

Security Laboratory • Current Research Topics – – – – – Secret and Public Key Cryptosystems Cryptographic Protocols Mobile Security PKI (Public Key Infrastructure) Software Security Secure Overlay Networks P. P. (Privacy Protection) DRM (Digital Rights Management) Intrusion Detection System Virus Protection ©KDDI R&D Laboratories Inc. ALL Rights Reserved.

Cryptanalysis on Clock Controlled Stream Ciphers Shinsaku Kiyomoto KDDI R&D Laboratories Inc. 2005. 2. 22 This is a joint work with Kyushu University (Prof. Kouichi Sakurai) ©KDDI R&D Laboratories Inc. ALL Rights Reserved.

Introduction: History of Stream Cipher Hardware based random generator LFSR based Stream Cipher Berlekamp-Massey Algorithm A 5 RC 4 Time-Memory Trade off Attack Correlation Attack Re-synchronization Attack From Bit-Oriented to Word-Oriented NESSIE Project (SNOW, BGML, SOBER, LILI etc. ) Guess-and-Determine Attack Distinguishing Attack XL, XSL ©KDDI R&D Laboratories Inc. ALL Rights Reserved.

Clock Controlled Stream Cipher • Using irregular clocking as a non-linear function. • Example – A 5: Stop-and-Go Clocking according to tap bits from 3 LFSRs. – LILI-128: 1 -2 -3 -4 Clocking by a clock controller and special LFSR ©KDDI R&D Laboratories Inc. ALL Rights Reserved.

Analysis of Irregular Clocking • Motivation – Is the irregular clocking more effective than other non-linear functions ? – Drawback of irregular clocking • Reduce efficiency of generating keystreams • Shorten a period of keystreams – How to construct or choose an algorithm of generating irregular clocking ©KDDI R&D Laboratories Inc. ALL Rights Reserved.

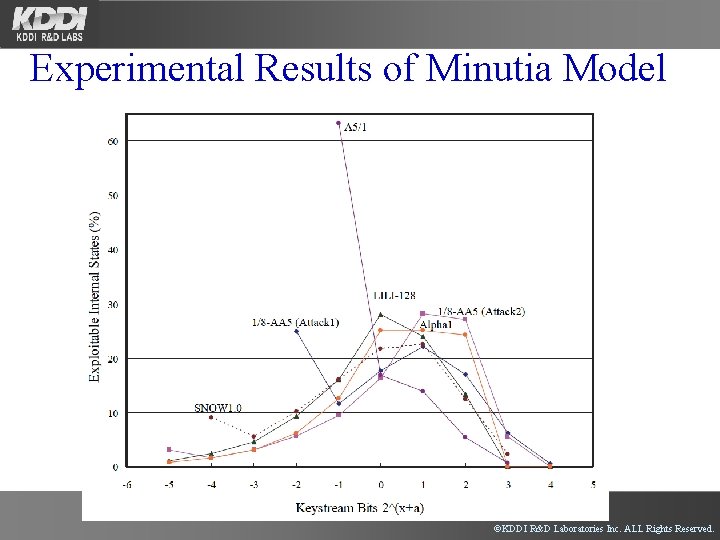
Theoretical and Experimental Analysis • Theoretical Analysis – Analysis on an ideal environment. • Experiments (Minutia Model Approach) – Constructing a minutia model of evaluating stream cipher. – How to make a minutia model • Shorten the lengths of LFSRs (in case of bit-oriented stream ciphers) • Shrink the sizes of registers in LFSRs (in case of word-oriented stream ciphers) • Modifying non-linear parts ©KDDI R&D Laboratories Inc. ALL Rights Reserved.

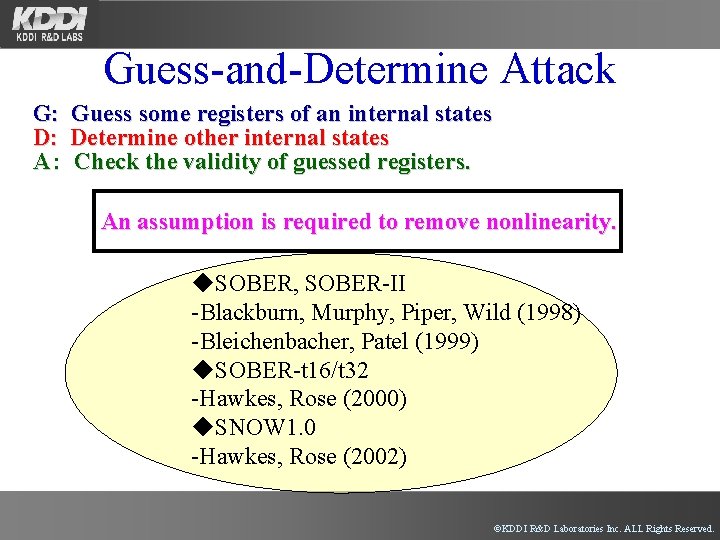
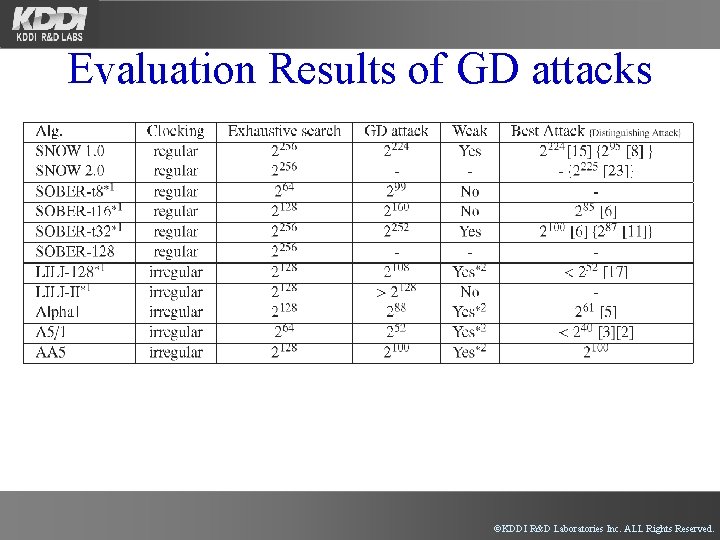
Guess-and-Determine Attack G: Guess some registers of an internal states D: Determine other internal states A: Check the validity of guessed registers. An assumption is required to remove nonlinearity. ◆SOBER, SOBER-II -Blackburn, Murphy, Piper, Wild (1998) -Bleichenbacher, Patel (1999) ◆SOBER-t 16/t 32 -Hawkes, Rose (2000) ◆SNOW 1. 0 -Hawkes, Rose (2002) ©KDDI R&D Laboratories Inc. ALL Rights Reserved.

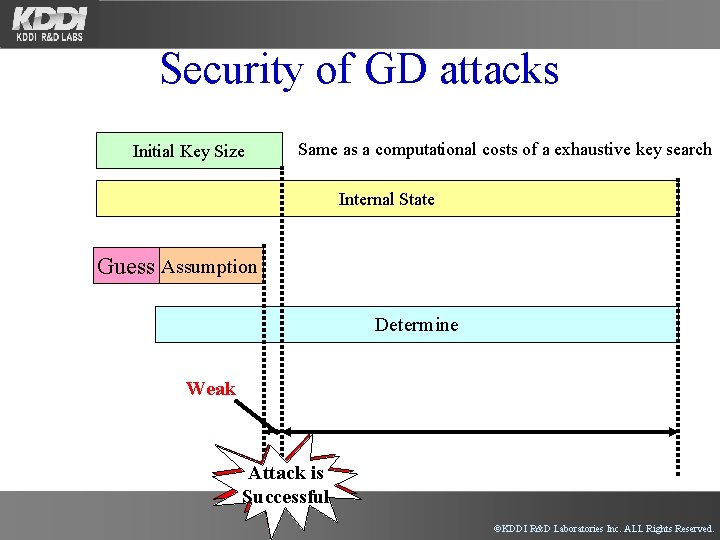
Security of GD attacks Initial Key Size Same as a computational costs of a exhaustive key search Internal State Guess Assumption Determine Weak Attack is Successful ©KDDI R&D Laboratories Inc. ALL Rights Reserved.

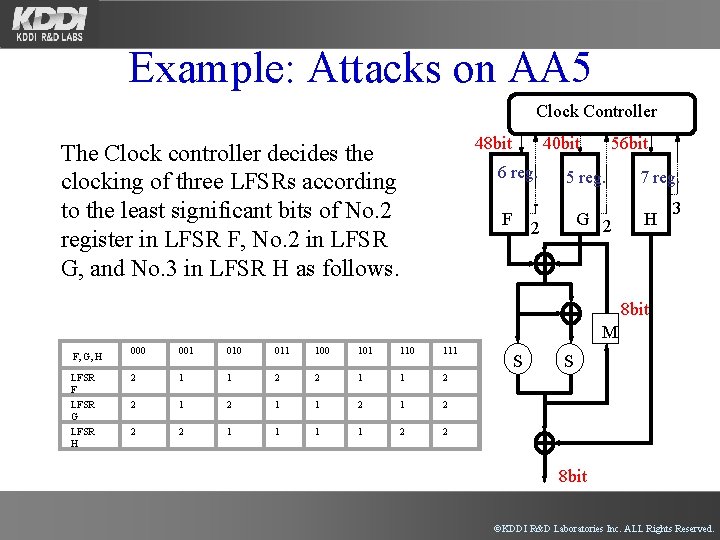
Example: Attacks on AA 5 Clock Controller 48 bit The Clock controller decides the clocking of three LFSRs according to the least significant bits of No. 2 register in LFSR F, No. 2 in LFSR G, and No. 3 in LFSR H as follows. 40 bit 6 reg. F 56 bit 5 reg. G 2 2 7 reg. H 3 8 bit M F, G, H LFSR F LFSR G LFSR H 000 001 010 011 100 101 110 111 2 1 1 2 2 2 1 1 2 2 S S 8 bit ©KDDI R&D Laboratories Inc. ALL Rights Reserved.

Strategy of proposed GD attacks • We determine LFSR H (the longest) to guess LFSR F, and G. • If we guess LFSR F, G, and internal memory M, then we can ignore influence of S-boxes. • How to remove irregularity by the clock controller. →We use assumptions that the target LFSR clocks regularly. Irregular Clocking Assumption Regular Clocking ©KDDI R&D Laboratories Inc. ALL Rights Reserved.

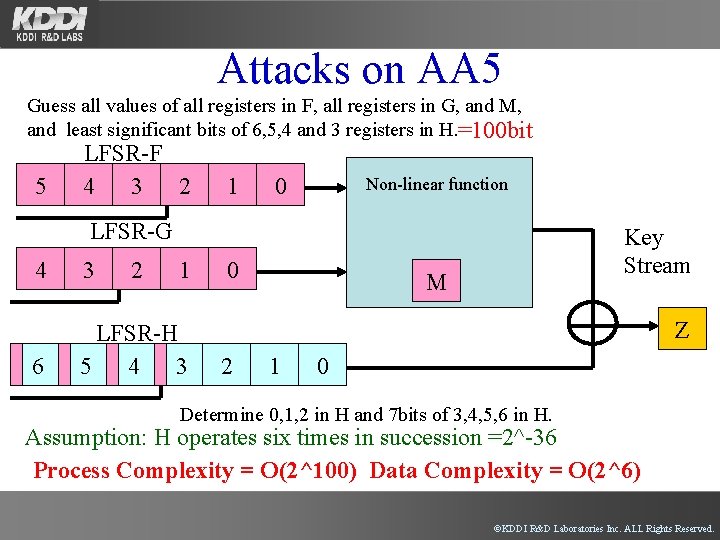
Attacks on AA 5 Guess all values of all registers in F, all registers in G, and M, and least significant bits of 6, 5, 4 and 3 registers in H. =100 bit 5 LFSR-F 4 3 2 1 0 Non-linear function LFSR-G 4 3 2 1 6 LFSR-H 5 4 3 0 Key Stream M Z 2 1 0 Determine 0, 1, 2 in H and 7 bits of 3, 4, 5, 6 in H. Assumption: H operates six times in succession =2^-36 Process Complexity = O(2^100) Data Complexity = O(2^6) ©KDDI R&D Laboratories Inc. ALL Rights Reserved.

Evaluation Results of GD attacks ©KDDI R&D Laboratories Inc. ALL Rights Reserved.

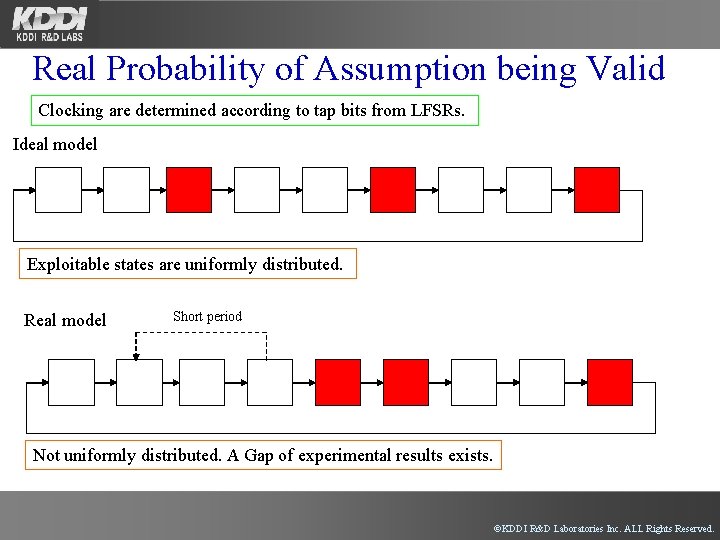
Real Probability of Assumption being Valid Clocking are determined according to tap bits from LFSRs. Ideal model Exploitable states are uniformly distributed. Real model Short period Not uniformly distributed. A Gap of experimental results exists. ©KDDI R&D Laboratories Inc. ALL Rights Reserved.

Experimental Results of Minutia Model ©KDDI R&D Laboratories Inc. ALL Rights Reserved.

Distinguishing Attack • Distinguish keystreams from stream ciphers and truly random strings. – Powerful attack on Stream Ciphers • • SNOW 1. 0 (by Coppersmith, 2000) SNOW 2. 0 (by Watanabe, 2003) SOBER-Family (by Ekdahl, 2002) SCREAM (by Johansson, 2003) ©KDDI R&D Laboratories Inc. ALL Rights Reserved.

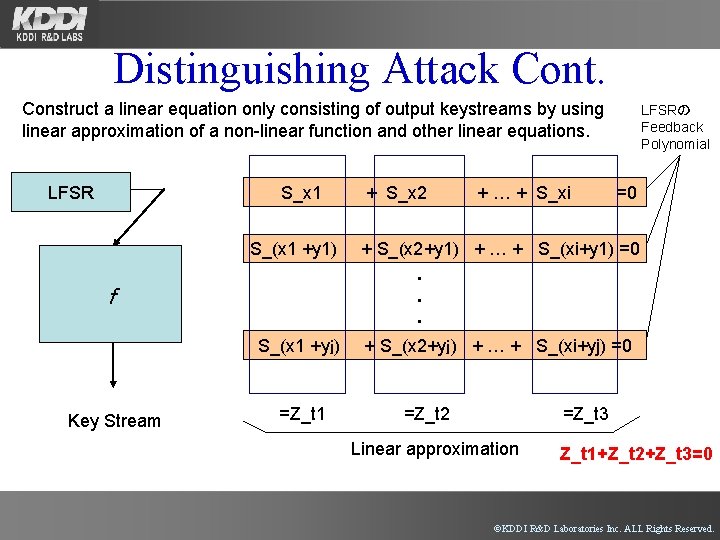
Distinguishing Attack Cont. Construct a linear equation only consisting of output keystreams by using linear approximation of a non-linear function and other linear equations. S_x 1 LFSR + S_x 2 + … + S_xi LFSRの Feedback Polynomial =0 S_(x 1 +y 1) + S_(x 2+y 1) + … + S_(xi+y 1) =0 f Key Stream ・ ・ ・ S_(x 1 +yj) + S_(x 2+yj) + … + S_(xi+yj) =0 =Z_t 1 =Z_t 2 =Z_t 3 Linear approximation Z_t 1+Z_t 2+Z_t 3=0 ©KDDI R&D Laboratories Inc. ALL Rights Reserved.

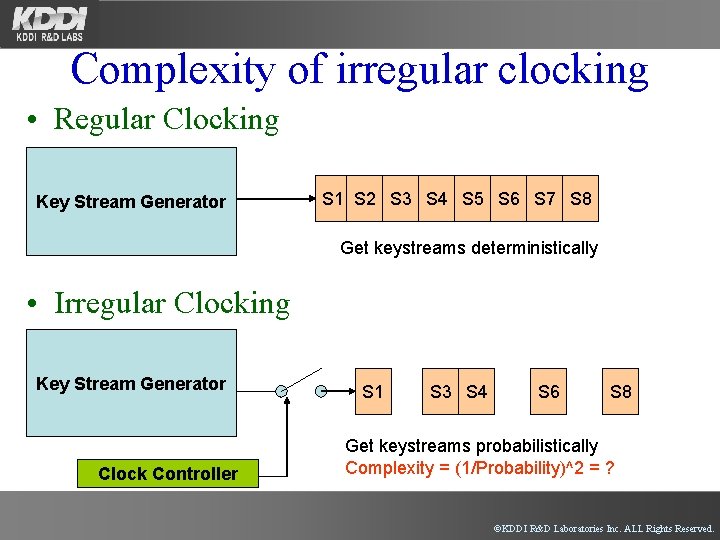
Complexity of irregular clocking • Regular Clocking Key Stream Generator S 1 S 2 S 3 S 4 S 5 S 6 S 7 S 8 Get keystreams deterministically • Irregular Clocking Key Stream Generator Clock Controller S 1 S 3 S 4 S 6 S 8 Get keystreams probabilistically Complexity = (1/Probability)^2 = ? ©KDDI R&D Laboratories Inc. ALL Rights Reserved.

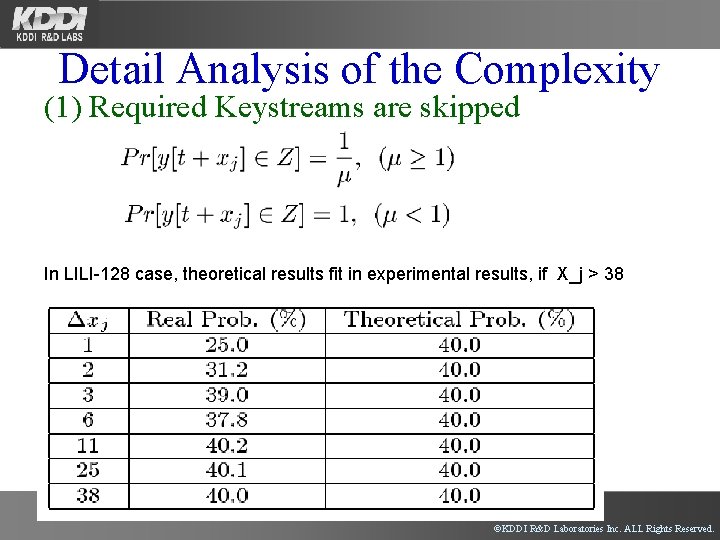
Detail Analysis of the Complexity (1) Required Keystreams are skipped In LILI-128 case, theoretical results fit in experimental results, if X_j > 38 ©KDDI R&D Laboratories Inc. ALL Rights Reserved.

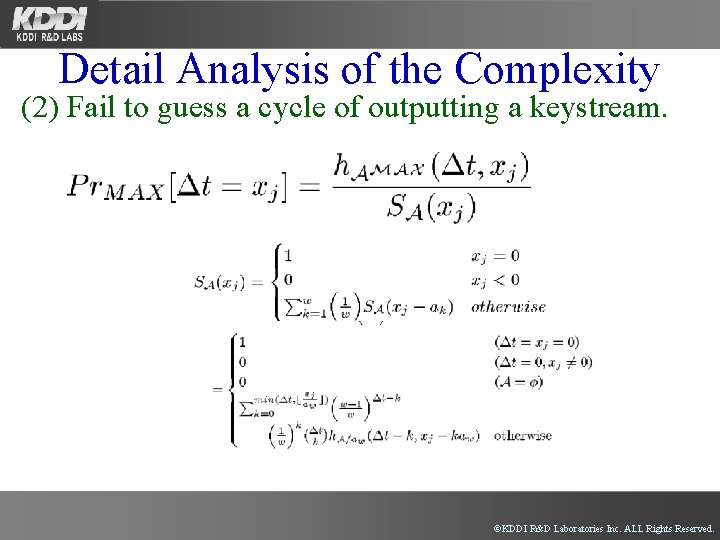
Detail Analysis of the Complexity (2) Fail to guess a cycle of outputting a keystream. ©KDDI R&D Laboratories Inc. ALL Rights Reserved.

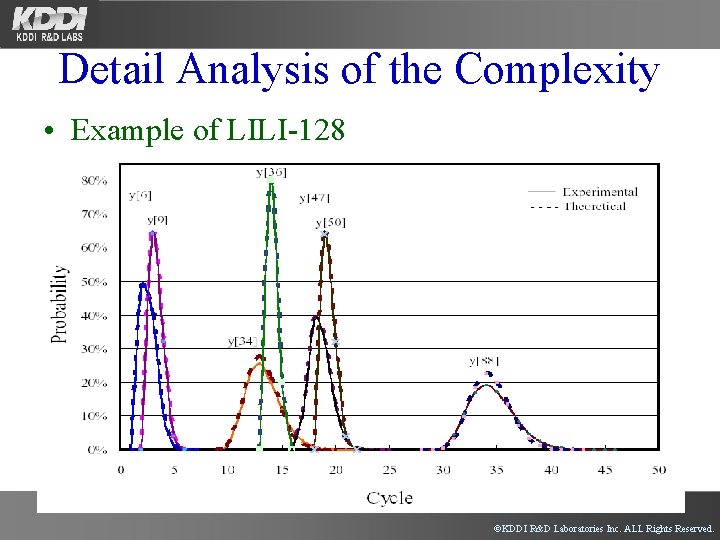
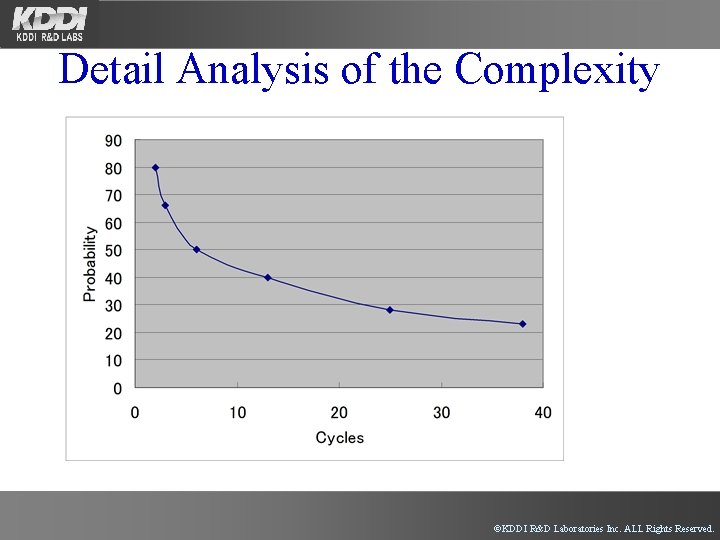
Detail Analysis of the Complexity • Example of LILI-128 ©KDDI R&D Laboratories Inc. ALL Rights Reserved.

Detail Analysis of the Complexity ©KDDI R&D Laboratories Inc. ALL Rights Reserved.

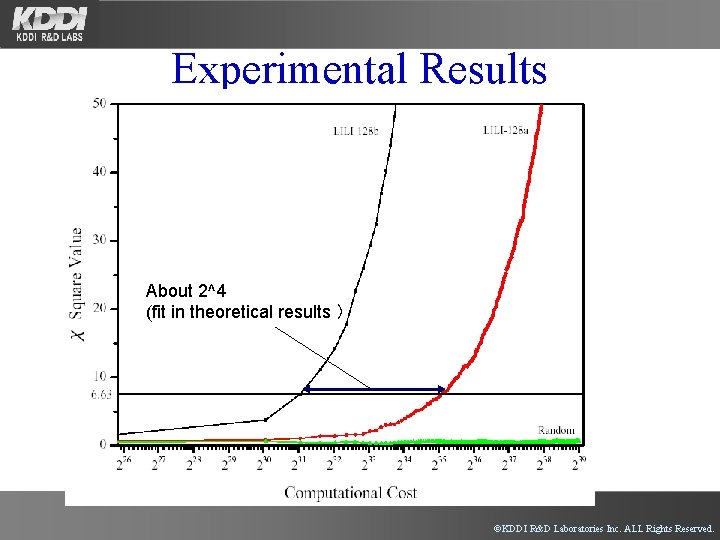
Experimental Results About 2^4 (fit in theoretical results ) ©KDDI R&D Laboratories Inc. ALL Rights Reserved.

Conclusion • Irregular clocking is effective for several attacks. However, the algorithm should be carefully designed. • Especially, large clocking is effective for protecting distinguishing attacks, even though a trade-off exists between the effect and efficiency of generating keystreams. ©KDDI R&D Laboratories Inc. ALL Rights Reserved.