Stream Ciphers 1 Stream Ciphers Generalization of onetime




















- Slides: 35

Stream Ciphers 1

Stream Ciphers Generalization of one-time pad q Trade provable security for practicality q Stream cipher is initialized with short key q Key is “stretched” into long keystream q Keystream is used like a one-time pad q o XOR to encrypt or decrypt Stream cipher is a keystream generator q Usually, keystream is bits, sometimes bytes q Stream Ciphers 2

Stream Cipher q Generic Stream Ciphers view of stream cipher 3

Stream Cipher q We consider 3 real stream ciphers o ORYX — weak cipher, uses shift registers, generates 1 byte/step o RC 4 — strong cipher, widely used but used poorly in WEP, generates 1 byte/step o PKZIP — intermediate strength, unusual mathematical design, generates 1 byte/step q But first, we discuss shift registers Stream Ciphers 4

Shift Registers q Traditionally, stream ciphers were based on shift registers o Today, a wider variety of designs q Shift register includes o A series of stages each holding one bit o A feedback function q A linear feedback shift register (LFSR) has a linear feedback function Stream Ciphers 5

Shift Register q Example (nonlinear) feedback function f(xi, xi+1, xi+2) = 1 xi+2 xi+1 xi+2 q Example q First Stream Ciphers (nonlinear) shift register 3 bits are initial fill: (x 0, x 1, x 2) 6

LFSR q Example of LFSR Then xi+5 = xi xi+2 for all i q If initial fill is (x 0, x 1, x 2, x 3, x 4) = 01110 then (x 0, x 1, …, x 15, …) = 0111010100001001… q Stream Ciphers 7

LFSR q For LFSR We have xi+5 = xi xi+2 for all i q Linear feedback functions often written in polynomial form: x 5 + x 2 + 1 q Connection polynomial of the LFSR q Stream Ciphers 8

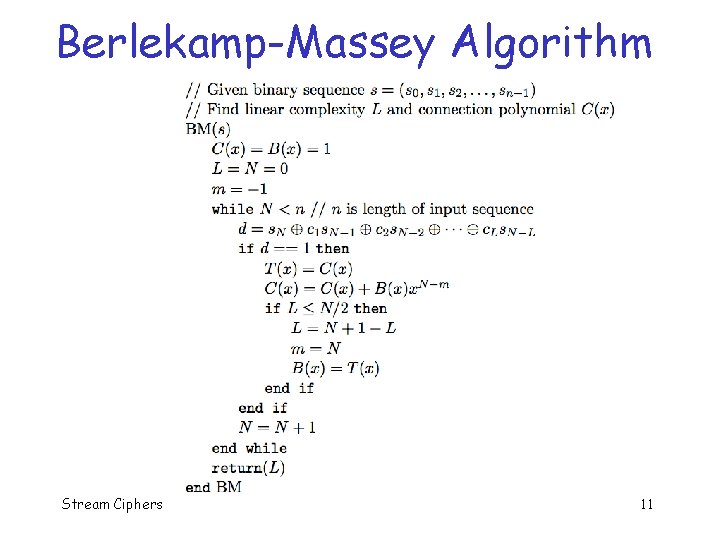
Berlekamp-Massey Algorithm q Given (part of) a (periodic) sequence, can find shortest LFSR that could generate the sequence q Berlekamp-Massey algorithm o Order N 2, where N is length of LFSR o Iterative algorithm o Only 2 N consecutive bits required Stream Ciphers 9

Berlekamp-Massey Algorithm Binary sequence: s = (s 0, s 1, s 2, …, sn-1) q Linear complexity of s is the length of shortest LFSR that can generate s q Let L be linear complexity of s q Then connection polynomial of s is of form C(x) = c 0 + c 1 x + c 2 x 2 + … + c. Lx. L q Berlekamp-Massey finds L and C(x) q o Algorithm on next slide (where d is known as the discrepancy) Stream Ciphers 10

Berlekamp-Massey Algorithm Stream Ciphers 11

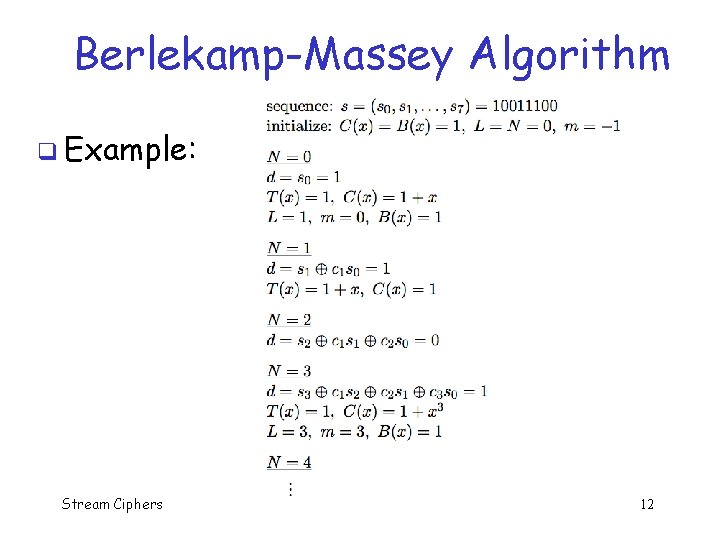
Berlekamp-Massey Algorithm q Example: Stream Ciphers 12

Berlekamp-Massey Algorithm Berlekamp-Massey is efficient way to determine minimal LFSR for sequence q With known plaintext, keystream bits of stream cipher are exposed q With enough keystream bits, can use Berlekamp-Massey to find entire keystream q o 2 L bits is enough, where L is linear complexity of the keystream q Keystream must have large linear complexity Stream Ciphers 13

Cryptographically Strong Sequences q A sequence is cryptographically strong if it is a “good” keystream o “Good” relative to some specified criteria q Crypto strong sequence must be unpredictable o Known plaintext exposes part of keystream o Trudy must not be able to determine more of the keystream from a short segment q Small linear complexity implies predictable o Due to Berlekamp-Massey algorithm Stream Ciphers 14

Crypto Strong Sequences Necessary for a cryptographically strong keystream to have a high linear complexity q But not sufficient! q Why? Consider s = (s 0, s 1, …, sn-1) = 00… 01 q Then s has linear complexity n q o Smallest shift register for s requires n stages o Largest possible for sequence of period n o But s is not cryptographically strong q Linear complexity “concentrated” in last bit Stream Ciphers 15

Linear Complexity Profile Linear complexity profile is a better measure of cryptographic strength q Plot linear complexity as function of bits processed in Berlekamp-Massey algorithm q o Should follow n/2 line “closely but irregularly” q Plot of sequence s = (s 0, s 1, …, sn-1) = 00… 01 would be 0 until last bit, then jumps to n o Does not follow n/2 line “closely but irregularly” o Not a strong sequence (by this definition) Stream Ciphers 16

Linear Complexity Profile q A “good” linear complexity profile Stream Ciphers 17

k-error Linear Complexity Profile Alternative way to measure cryptographically strong sequences q Consider again s = (s 0, s 1, …, sn-1) = 00… 01 q This s has max linear complexity, but it is only 1 bit away from having min linear complexity q k-error linear complexity is min complexity of any sequence that is “distance” k from s q 1 -error linear complexity of s = 00… 01 is 0 q o Linear complexity of this sequence is “unstable” Stream Ciphers 18

k-error Linear Complexity Profile q k-error linear complexity profile o k-error linear complexity as function of k q Example: o Not a strong s o Good profile should follow diagonal “closely” Stream Ciphers 19

Crypto Strong Sequences q Linear complexity must be “large” q Linear complexity profile must n/2 line “closely but irregularly” q k-error linear complexity profile must follow diagonal line “closely” q All of this is necessary but not sufficient for crypto strength! Stream Ciphers 20

Shift Register-Based Stream Ciphers q Two approaches to LFSR-based stream ciphers o One LFSR with nonlinear combining function o Multiple LFSRs combined via nonlinear func q In either case o Key is initial fill of LFSRs o Keystream is output of nonlinear combining function Stream Ciphers 21

Shift Register-Based Stream Ciphers q LFSR-based stream cipher o 1 LFSR with nonlinear function f(x 0, x 1, …, xn-1) q Keystream: Stream Ciphers k 0, k 1, k 2, … 22

Shift Register-Based Stream Ciphers q LFSR-based stream cipher o Multiple LFSRs with nonlinear function q Keystream: Stream Ciphers k 0, k 1, k 2, … 23

Shift Register-Based Stream Ciphers q Single LFSR example is special case of multiple LFSR example q To convert single LFSR case to multiple o Let LFSR 0, …LFSRn-1 be same as LFSR o Initial fill of LFSR 0 is initial fill of LFSR o Initial fill of LFSR 1 is initial fill of LFSR stepped once o And so on… Stream Ciphers 24

Correlation Attack q Trudy obtains some segment of keystream from LFSR stream cipher o Of the type considered on previous slides q Can assume stream cipher is the multiple shift register case o If not, convert it to this case By Kerckhoffs Principle, we assume shift registers and combining function known q Only unknown is the key q o The key consists of LFSR initial fills Stream Ciphers 25

Correlation Attack q Trudy wants to recover LFSR initial fills o She knows all connection polynomials and nonlinear combining function o She also knows N keystream bits, k 0, k 1, …, k. N-1 q Sometimes possible to determine initial fills of the LFSRs independently o By correlating each LFSR output to keystream o A classic divide and conquer attack Stream Ciphers 26

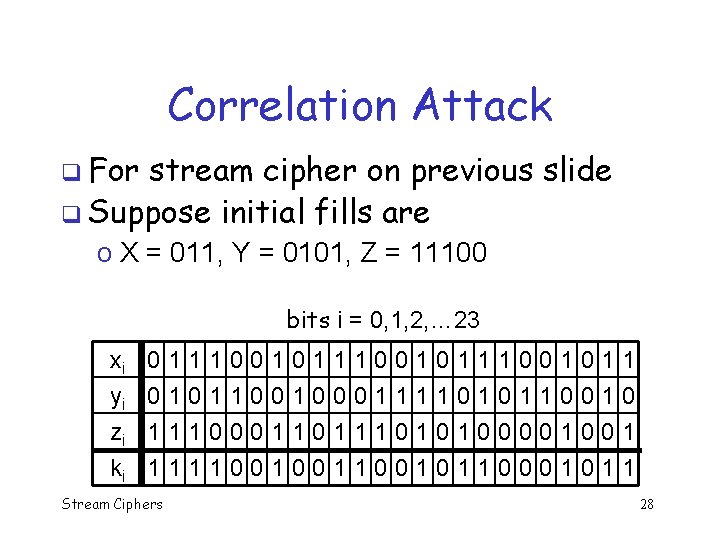
Correlation Attack q For example, suppose keystream generator is of the form: And f(x, y, z) = xy yz z q Note that key is 12 bits, initial fills q Stream Ciphers 27

Correlation Attack q For stream cipher on previous slide q Suppose initial fills are o X = 011, Y = 0101, Z = 11100 bits i = 0, 1, 2, … 23 xi yi zi ki 0 0 1 1 Stream Ciphers 1 1 1 0 1 0 0 0 1 0 1 1 0 0 0 1 1 1 0 0 1 1 0 1 1 0 0 0 1 0 1 1 0 1 1 28

Correlation Attack q Consider truth table for combining function: f(x, y, z) = xy yz z q Easy to show that f(x, y, z) = x with probability 3/4 f(x, y, z) = z with probability 3/4 q Trudy can use this to recover initial fills from known keystream Stream Ciphers 29

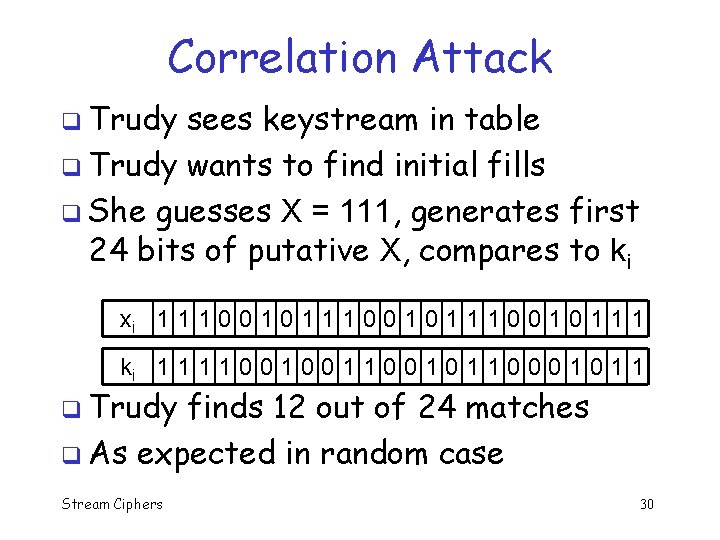
Correlation Attack q Trudy sees keystream in table q Trudy wants to find initial fills q She guesses X = 111, generates first 24 bits of putative X, compares to ki xi 1 1 1 0 0 1 0 1 1 1 0 0 1 1 1 ki 1 1 0 0 1 1 0 0 0 1 1 q Trudy finds 12 out of 24 matches q As expected in random case Stream Ciphers 30

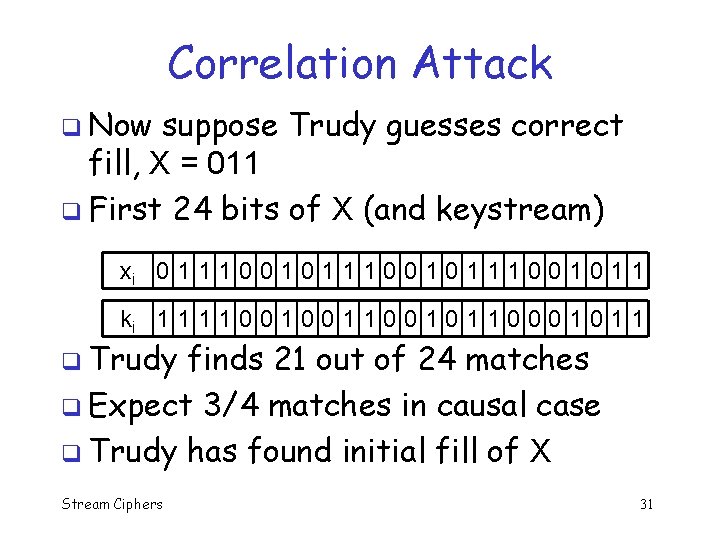
Correlation Attack q Now suppose Trudy guesses correct fill, X = 011 q First 24 bits of X (and keystream) xi 0 1 1 1 0 0 1 1 ki 1 1 0 0 1 1 0 0 0 1 1 q Trudy finds 21 out of 24 matches q Expect 3/4 matches in causal case q Trudy has found initial fill of X Stream Ciphers 31

Correlation Attack q How much work is this attack? o The X, Y, Z fills are 3, 4, 5 bits, respectively We need to try about half of the initial fills before we find X q Then we try about half of the fills for Y q Then about half of Z fills q Work is 22 + 23 + 24 < 25 q Exhaustive key search work is 211 q Stream Ciphers 32

Correlation Attack q Work factor in general… q Suppose n LFSRs o Of lengths N 0, N 1, …, Nn-1 q Correlation q Work Stream Ciphers attack work is for exhaustive key search is 33

Conclusions q Keystreams must be cryptographically strong o Crucial property: unpredictable q Lots of theory available for LFSRs o Berlekamp-Massey algorithm o Nice mathematical theory exists q LFSRs can be used to make stream ciphers o LFSR-based stream ciphers must be correlation immune o Depends on properties of function f Stream Ciphers 34

Coming Attractions q Consider attacks on 3 stream ciphers o ORYX — weak cipher, uses shift registers, generates 1 byte/step o RC 4 — strong, widely used but used poorly in WEP, generates 1 byte/step o PKZIP — medium strength, unusual design, generates 1 byte/step Stream Ciphers 35