CROSS X The Cross Platform Explorer Susheel Chandar



- Slides: 15

CROSS - X The Cross Platform Explorer Susheel Chandar Elango Guna Sekaran Mohan

Introduction o Objective n o Existing Systems n n o To develop a tool that is capable of accessing file systems of Heterogeneous Platforms in a network All existing systems are used to access or share files between particularly any two platforms For Example, SAMBA SERVICE, is used to share the files of a Linux System in a windows system Proposed System n The proposed system is intended to break this drawback of sharing between any two specific platforms and gives a solution that gives access to any file system from any platform

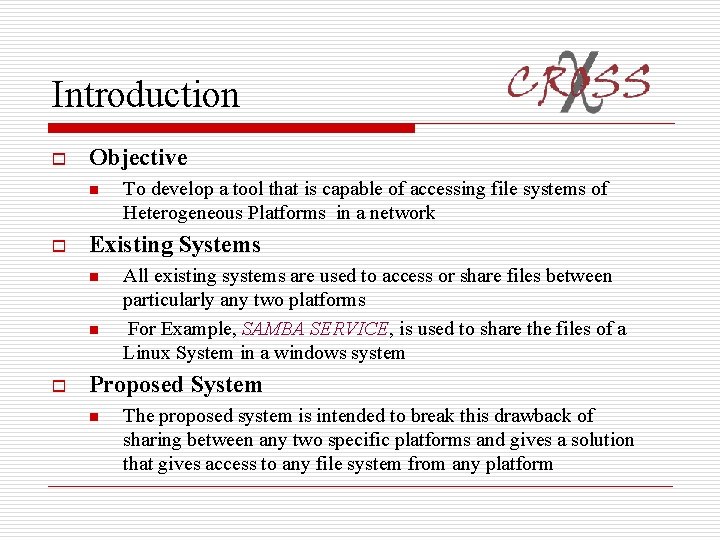
System Data Flow Model Client 1 Windows RMI Reg @ 2020 Client 2 Linux RMI Reg @ 2020 Client 4 Mac SERVER RMI Reg @ 3030 Client 3 Solaris RMI Reg @ 2020

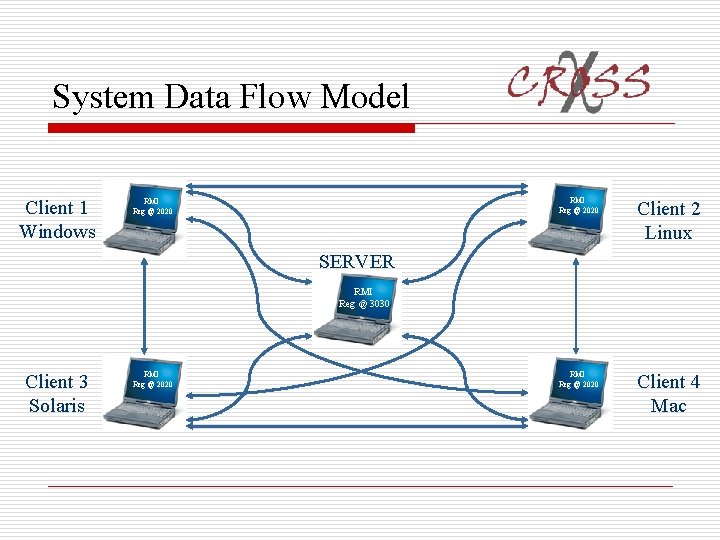
System Architecture o Three Tier Architecture GUI TIER BUSINESS TIER FORM OBJECTS VALUE OBJECTS FORM ACTIONS BUSINESS DELEGATE FACTORY BUSINESS DELEGATE OBJECT INTEGRATION TIER REMOTE INTERFACE UNICAST OBJECTS DAO FACTORY

Modules o SERVER MANAGEMENT MODULE o AUTHENTICATION MODULE o EVENT MODULE o HAND OVER MODULE

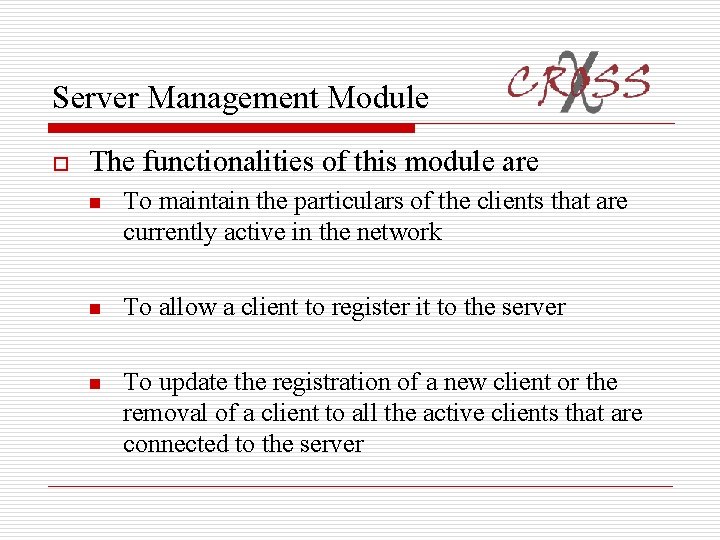
Server Management Module o The functionalities of this module are n To maintain the particulars of the clients that are currently active in the network n To allow a client to register it to the server n To update the registration of a new client or the removal of a client to all the active clients that are connected to the server

Authentication Module o The functionalities of this module are n To create new users on the installed clients n To do remote system authentication before entering into the other machine based on the user list maintained in the server n To delete or do other operations on the users list maintained on the server

Event Module o The functionalities of this module are n To Contact the client systems and place a request for the access of the files when an call event occurs in the local machine n To perform Copy, Cut, Delete, Rename, and other operations on the remote or local files n To map a file to its appropriate application

Hand Over Module o The functionalities of this module are n To transfer the information of the files requested by another client system in the format of XML Data n The Hand Over module in the client system gets the XML data from the remote system and parses it using the SAX (Simple API for XML) Parser to get the appropriate file information

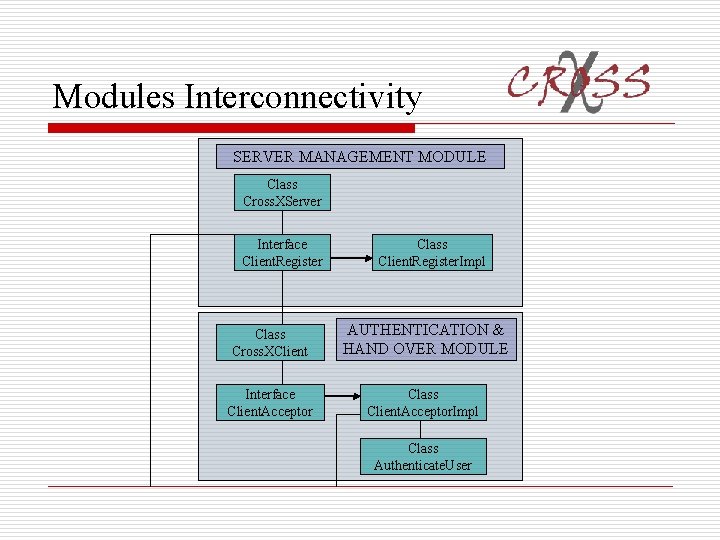
Modules Interconnectivity SERVER MANAGEMENT MODULE Class Cross. XServer Interface Client. Register Class Client. Register. Impl Class Cross. XClient AUTHENTICATION & HAND OVER MODULE Interface Client. Acceptor Class Client. Acceptor. Impl Class Authenticate. User

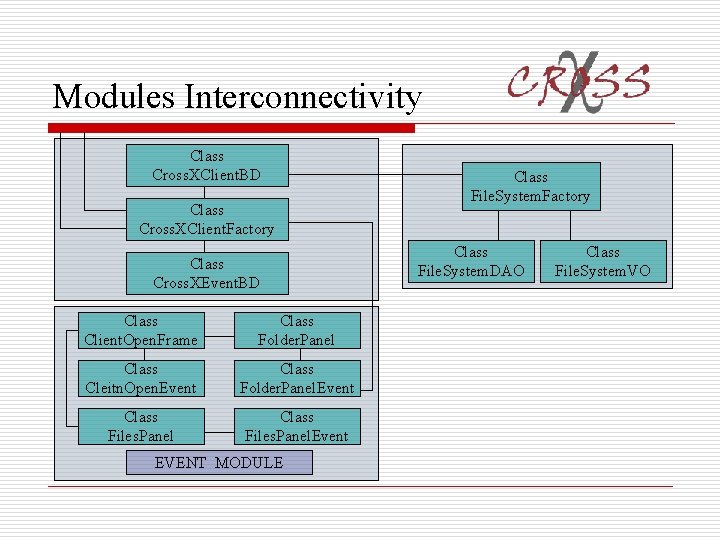
Modules Interconnectivity Class Cross. XClient. BD Class Cross. XClient. Factory Class Cross. XEvent. BD Class Client. Open. Frame Class Folder. Panel Class Cleitn. Open. Event Class Folder. Panel. Event Class Files. Panel. Event EVENT MODULE Class File. System. Factory Class File. System. DAO Class File. System. VO

Snap Shots

Snap Shots

Future Enhancements o To authenticate the users based on the system users list which is maintained by the operating system o To restrict the usage of all files by the users based on their privileges on the system

Thanks You