CMPE 252 A Computer Networks Chen Qian UCSC









- Slides: 31

CMPE 252 A : Computer Networks Chen Qian UCSC Baskin Engineering Lecture 18 Some slides from Brent Waters and Saiyu Qi 1

Scalable Data Access Control in RFID-Enabled Supply Chain Saiyu Qi 1, 2, Yuanqing Zheng 2, Mo Li 2, Yunhao Liu 3 , Jinli Qiu 4 HKUST 1 NANYANG TECHNOLOGICAL UNIVERSITY 2 TSINGHUA UNIVERSITY 3 XI’AN JIAOTONG UNIVERSITY 4 2

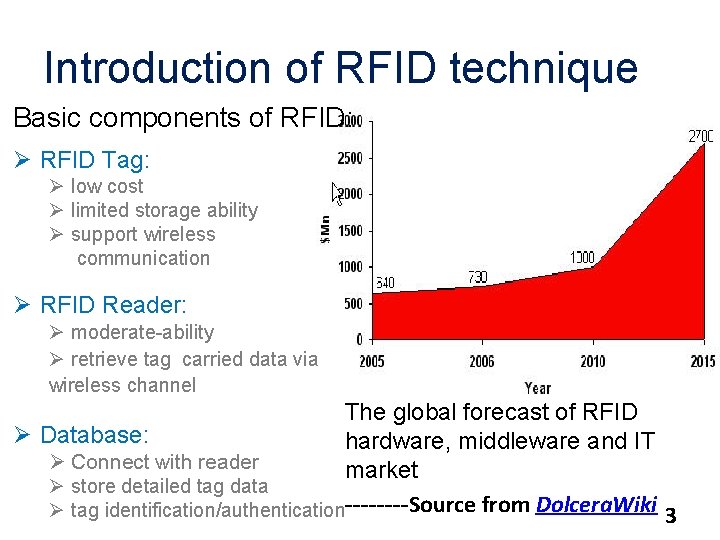
Introduction of RFID technique Basic components of RFID: Ø RFID Tag: Ø low cost Ø limited storage ability Ø support wireless communication Ø RFID Reader: Ø moderate-ability Ø retrieve tag carried data via wireless channel The global forecast of RFID Ø Database: hardware, middleware and IT Ø Connect with reader market Ø store detailed tag data Ø tag identification/authentication----Source from Dolcera. Wiki 3

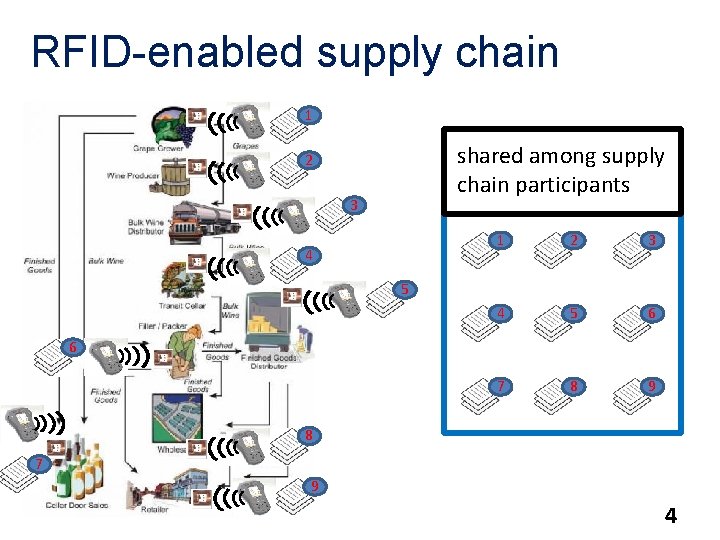
RFID-enabled supply chain 1 shared among supply chain participants 2 3 4 1 2 3 4 5 6 7 8 9 5 6 8 7 9 4

Motivation Ø The product data derived by RFID tags is usually sensitive Ø An instance: pedigree of drugs Ø created for each tagged drug in a pharmaceutical supply chain Ø be useful to verify if a drug is fake Ø often contains counterfeit certificate , time of delivery and manufactures suffer malicious accesses by drug counterfeiters and competitive manufacturers 5

The goal of this paper Ø Secure sharing of RFID-derived product data Ø A scalable data access control system for RFID- Enabled Supply Chain Ø an item-level data access control mechanism Ø an item-level privilege revocation mechanism Ø Advantages: Ø data access control in item-level Ø scalable to large amount of tagged products 6

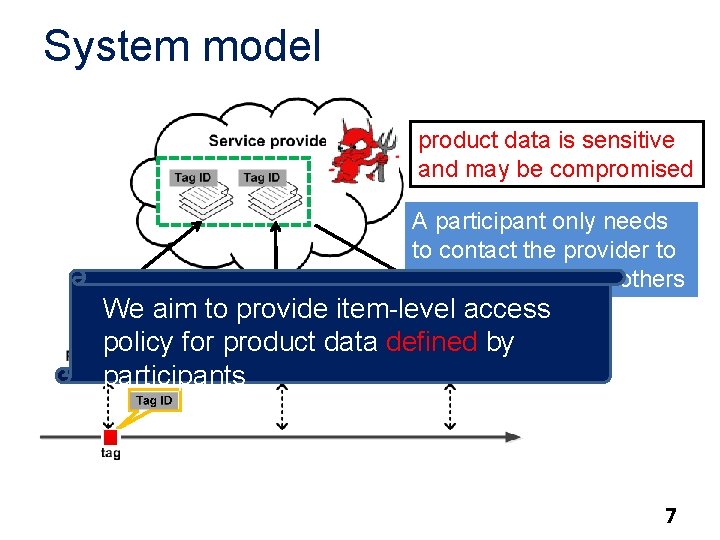
System model product data is sensitive and may be compromised A participant only needs to contact the provider to retrieve the data of others We aim to provide item-level access idxi, <Enc(wit, Ki)>sig policy for product data defined by participants 7

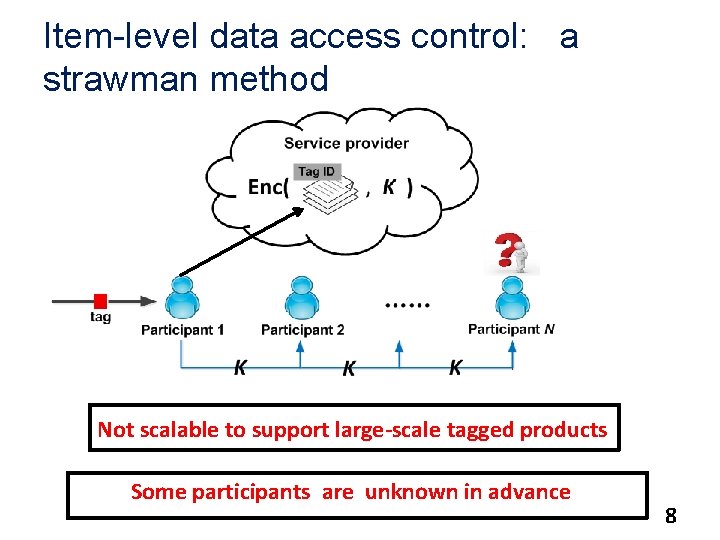
Item-level data access control: a strawman method Not scalable to support large-scale tagged products Some participants are unknown in advance 8

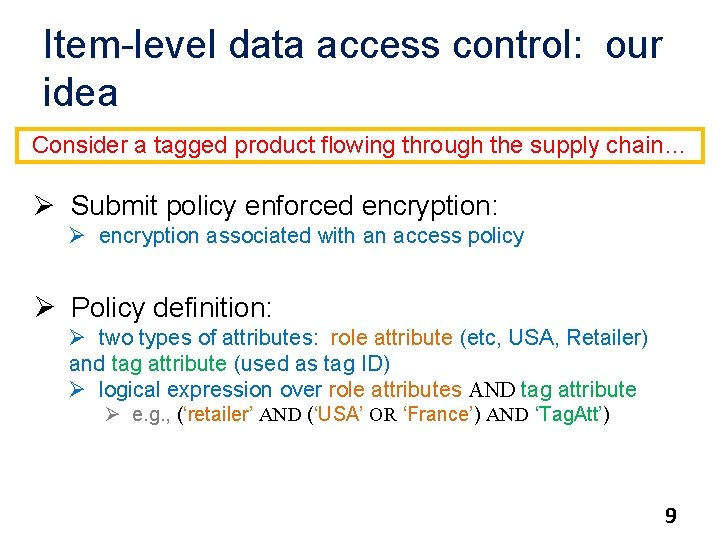
Item-level data access control: our idea Consider a tagged product flowing through the supply chain… Ø Submit policy enforced encryption: Ø encryption associated with an access policy Ø Policy definition: Ø two types of attributes: role attribute (etc, USA, Retailer) and tag attribute (used as tag ID) Ø logical expression over role attributes AND tag attribute Ø e. g. , (‘retailer’ AND (‘USA’ OR ‘France’) AND ‘Tag. Att’) 9

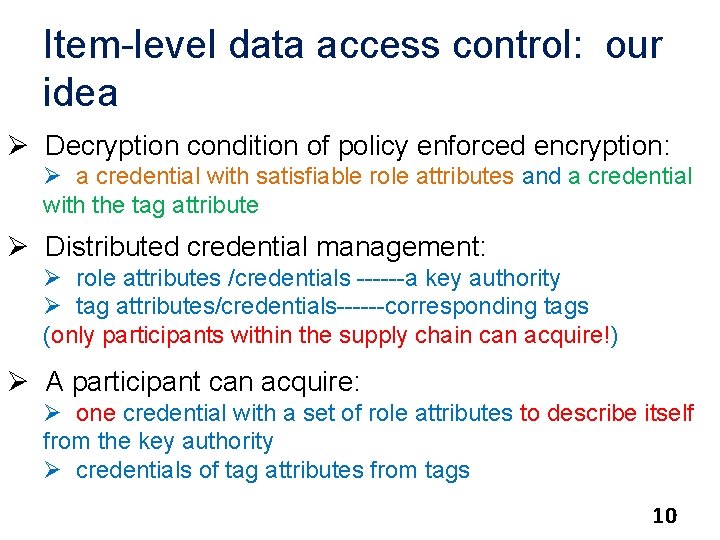
Item-level data access control: our idea Ø Decryption condition of policy enforced encryption: Ø a credential with satisfiable role attributes and a credential with the tag attribute Ø Distributed credential management: Ø role attributes /credentials ------a key authority Ø tag attributes/credentials------corresponding tags (only participants within the supply chain can acquire!) Ø A participant can acquire: Ø one credential with a set of role attributes to describe itself from the key authority Ø credentials of tag attributes from tags 10

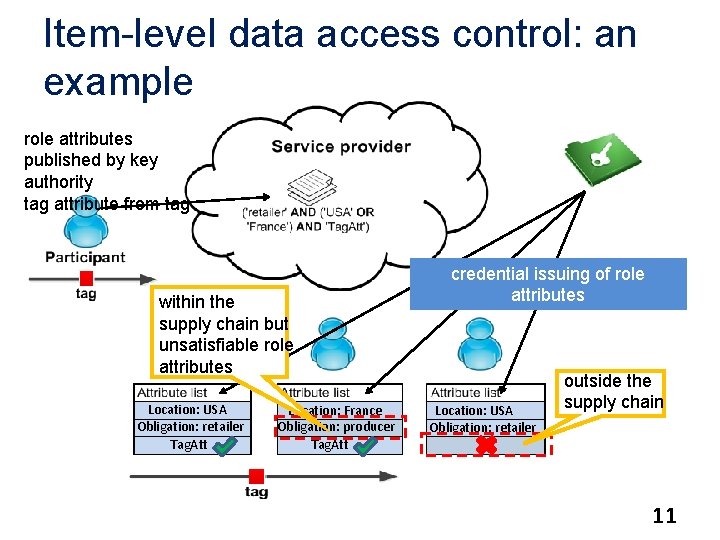
Item-level data access control: an example role attributes published by key authority tag attribute from tag within the supply chain but unsatisfiable role attributes Location: USA Obligation: retailer Tag. Att Location: France Obligation: producer Tag. Att credential issuing of role attributes Location: USA Obligation: retailer outside the supply chain 11

Item-level data access control: advantage Ø Advantages: Ø define an access policy with role attributes (acquired from the key authority) and tag attributes (acquired from tags)---do not need knowing other participants in advance Ø participants acquire credentials from key authority and tags --- item-level key issuing is avoided 12

Item-level data access control: implementation Ø Policy enforced encryption: Ø Double encryption pattern: Ciphertext Policy-Attribute Based Encryption (CP-ABE) [Bethencourt, et al. , SP '07] and Updatable Encryption (UE) scheme ABE encrypt the data Symmetric encrypt the ABE encryption Precisely enforce our desired policy: ABE to enforce role attribute part Updatable encryption to enforce tag attribute part Product data ABE encryption Policy enforced encryption Ø Two types of credentials: ØCredentials with role attributes: ABE private keys ØCredentials with tag attributes: UE private keys 13

Ciphertext-Policy, Attribute-Based Encryption John Bethencourt CMU Amit Sahai UCLA Brent Waters SRI International

Remote File Storage: Interesting Challenges o Scalability o Reliability o … But we also want security 15

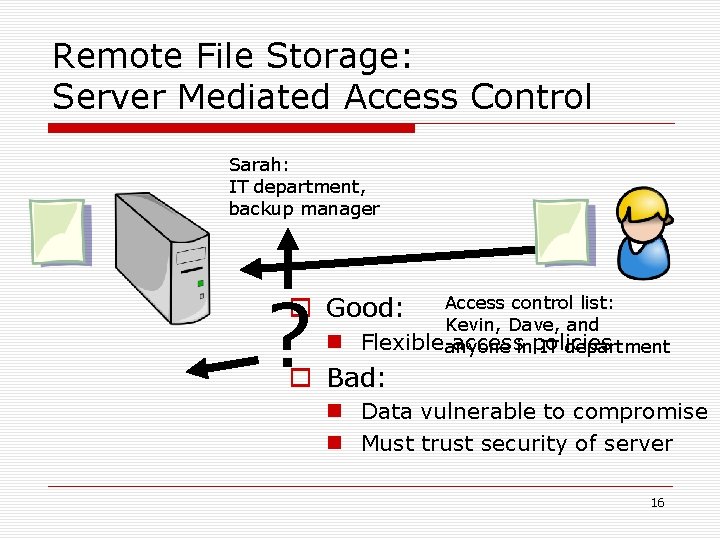
Remote File Storage: Server Mediated Access Control Sarah: IT department, backup manager ? o Good: n Access control list: Kevin, Dave, and Flexible anyone accessinpolicies IT department o Bad: n Data vulnerable to compromise n Must trust security of server 16

Remote File Storage: Encrypting the Files o More secure, but loss of flexibility o New key for each file: n Must be online to distribute keys o Many files with same key: n Fine grained access control not possible 17

Remote File Storage: We Want It All o Wishlist: n Encrypted files for untrusted storage n Setting up keys is offline n No online, trusted party mediating access to files or keys n Highly expressive, fine grained access policies o Ciphertext-policy attribute-based encryption does this! n User private keys given list of “attributes” n Files can encrypted under “policy” over those attributes n Can only decrypt if attributes satisfy policy 18

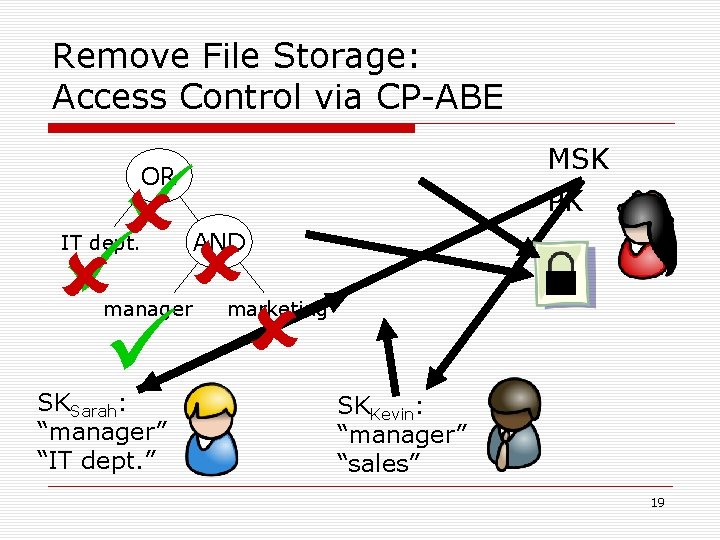
Remove File Storage: Access Control via CP-ABE MSK PK OR IT dept. manager SKSarah: “manager” “IT dept. ” AND marketing SKKevin: “manager” “sales” 19

Collusion Attacks: The Key Threat o Important potential attack o Users should not be able to combine keys AND o Essential, almost defining property of ABE A B o Main technical trick of our scheme: preventing collusion SKSarah: “A”, “C” ? SKKevin: “B”, “D” 20

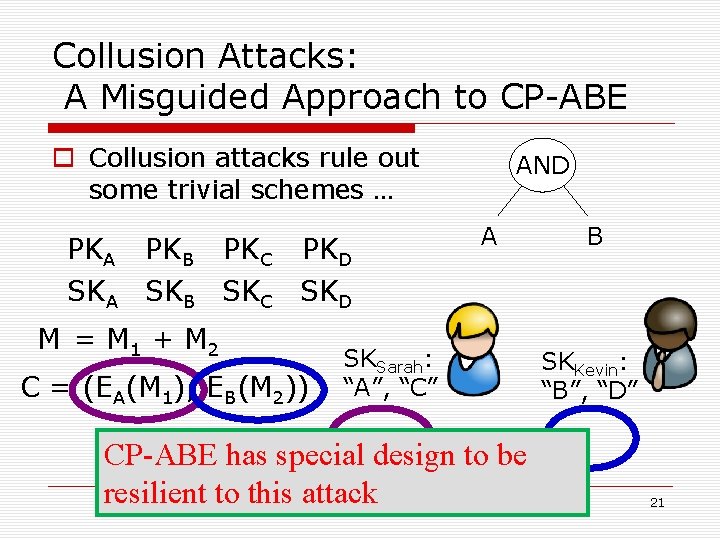
Collusion Attacks: A Misguided Approach to CP-ABE o Collusion attacks rule out some trivial schemes … PKA PKB PKC PKD SKA SKB SKC SKD M = M 1 + M 2 C = (EA(M 1), EB(M 2)) AND A SKSarah: “A”, “C” CP-ABE has special design to be resilient to this attack B SKKevin: “B”, “D” 21

Item-level data access control: CP-ABE master key ABE private key: USA retailer} {USA, ENC(M, ‘USA’ OR ‘CHINA’) ABE private key: {France, manufacturer} Logic expression over role attributes 22

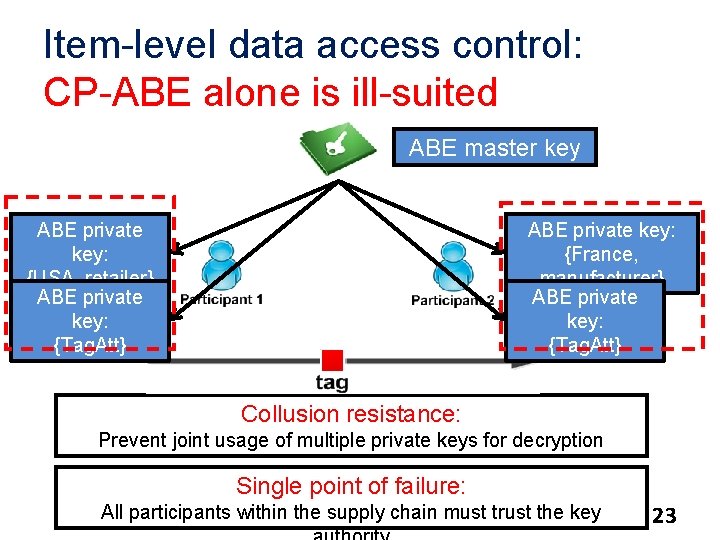
Item-level data access control: CP-ABE alone is ill-suited ABE master key ABE private key: {USA, retailer} ABE private key: {Tag. Att} ABE private key: {France, manufacturer} ABE private key: {Tag. Att} Collusion resistance: Prevent joint usage of multiple private keys for decryption Single point of failure: All participants within the supply chain must trust the key 23

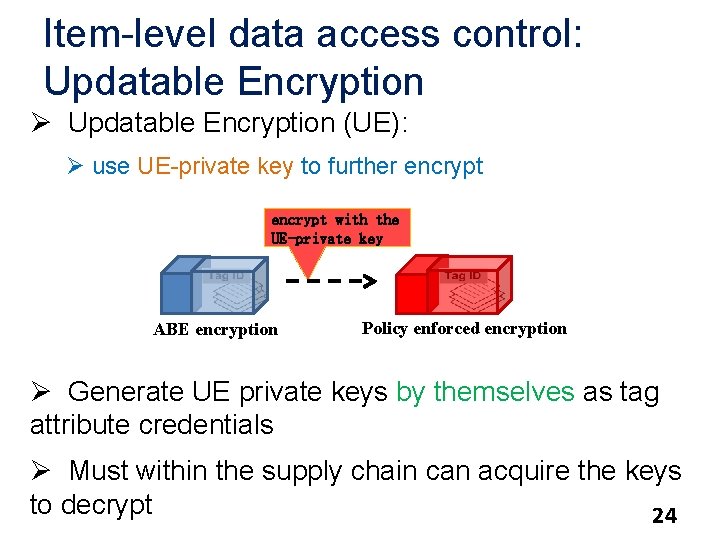
Item-level data access control: Updatable Encryption Ø Updatable Encryption (UE): Ø use UE-private key to further encrypt with the UE-private key ABE encryption Policy enforced encryption Ø Generate UE private keys by themselves as tag attribute credentials Ø Must within the supply chain can acquire the keys to decrypt 24

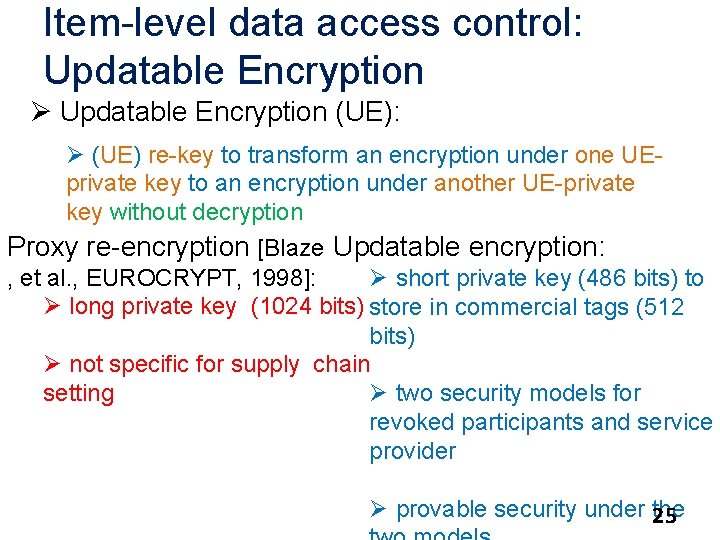
Item-level data access control: Updatable Encryption Ø Updatable Encryption (UE): Ø (UE) re-key to transform an encryption under one UEprivate key to an encryption under another UE-private key without decryption Proxy re-encryption [Blaze Updatable encryption: , et al. , EUROCRYPT, 1998]: Ø short private key (486 bits) to Ø long private key (1024 bits) store in commercial tags (512 bits) Ø not specific for supply chain setting Ø two security models for revoked participants and service provider Ø provable security under the 25

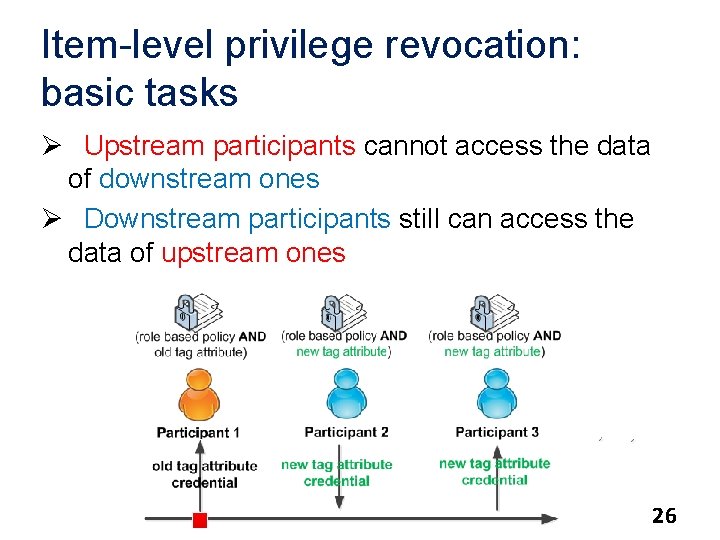
Item-level privilege revocation: basic tasks Ø Upstream participants cannot access the data of downstream ones Ø Downstream participants still can access the data of upstream ones 26

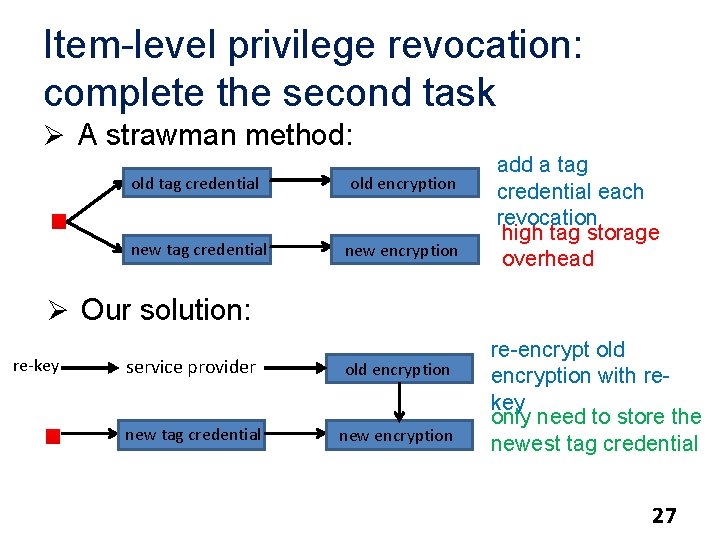
Item-level privilege revocation: complete the second task Ø A strawman method: old tag credential old encryption new tag credential new encryption add a tag credential each revocation high tag storage overhead Ø Our solution: re-key service provider old encryption new tag credential new encryption re-encrypt old encryption with rekey only need to store the newest tag credential 27

Evaluation: environment Ø PC configuration: 16 -core AMD Opteron Processor 6320 and 16 GB RAM running on Ubuntu 13. 10 OS Ø Two platforms: Ø Single PC Ø Cluster of three PCs with hadoop Ø Product data is randomly generated following normal distribution 28

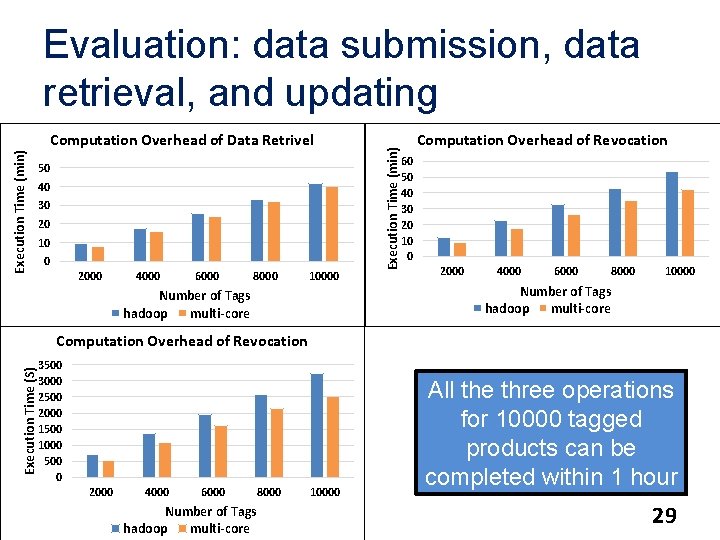
Execution Time (min) Computation Overhead of Data Retrivel 50 40 30 20 10 0 2000 4000 6000 8000 10000 Number of Tags hadoop multi-core Execution Time (min) Evaluation: data submission, data retrieval, and updating Computation Overhead of Revocation 60 50 40 30 20 10 0 2000 4000 6000 8000 10000 Number of Tags hadoop multi-core Execution Time (S) Computation Overhead of Revocation 3500 3000 2500 2000 1500 1000 500 0 2000 4000 6000 Number of Tags hadoop multi-core 8000 10000 All the three operations for 10000 tagged products can be completed within 1 hour 29

Summary Ø Policy enforced encryption with role attributes and tag attribute Ø Preclude participants outside supply chain and with unsatisfiable characters Ø separately manage credentials of role attributes and tag attributes Ø Enforce item-level access control without item-level key issuing Ø Enable servicer provider to transform old encryptions to new encryptions by re-key without decryption Ø Tag only needs to store the newest tag credential 30

End 11/24/2020 31