Cloud Computing Concepts Source Cloud Computing Architecture IT














- Slides: 56

Cloud Computing: Concepts Source: Cloud Computing Architecture, IT Security, & Operational - NASA

What is Cloud Computing?

What is Cloud Computing? Cloud Computing – NIST Definition: “A model for enabling convenient, on -demand network access to a shared pool of configurable computing resources (e. g. , networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction”

Shared / pooled resources Broad network access On-demand self-service Scalable and elastic Metered by use Five Key Cloud Attributes

What is Cloud Computing? Shared / Pooled Resources: • Resources are drawn from a common pool • Common resources build economies of scale • Common infrastructure runs at high efficiency

What is Cloud Computing? Broad Network Access: • Open standards and APIs • Almost always IP, HTTP, and REST • Available from anywhere with an internet connection

What is Cloud Computing? On-Demand Self-Service: • • Completely automated Users abstracted from the implementation Near real-time delivery (seconds or minutes) Services accessed through a self-serve web interface

What is Cloud Computing? Scalable and Elastic: • Resources dynamically-allocated between users • Additional resources dynamically-released when needed • Fully automated

What is Cloud Computing? Metered by Use: • Services are metered, like a utility • Users pay only for services used • Services can be cancelled at any time

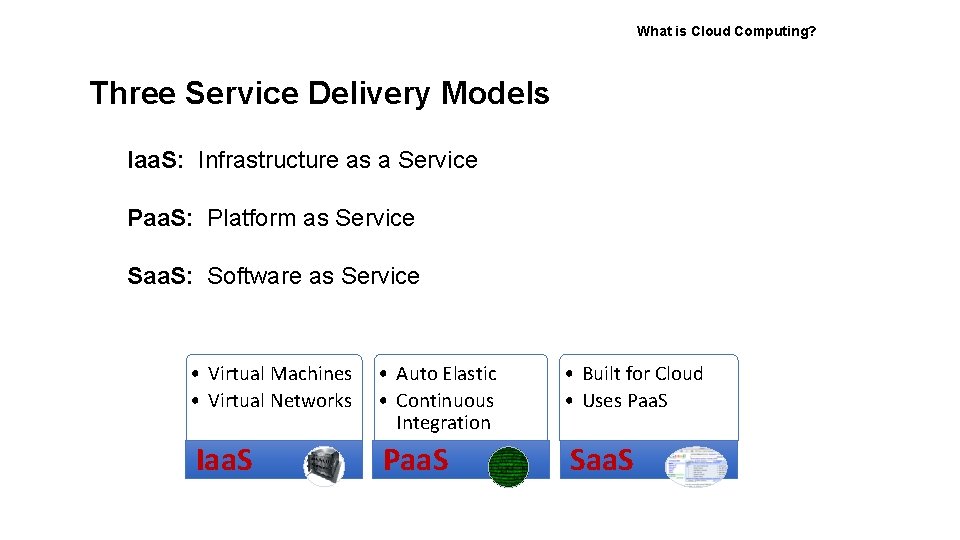
What is Cloud Computing? Three Service Delivery Models Iaa. S: Infrastructure as a Service Paa. S: Platform as Service Saa. S: Software as Service • Virtual Machines • Virtual Networks • Auto Elastic • Continuous Integration Iaa. S Paa. S • Built for Cloud • Uses Paa. S Saa. S

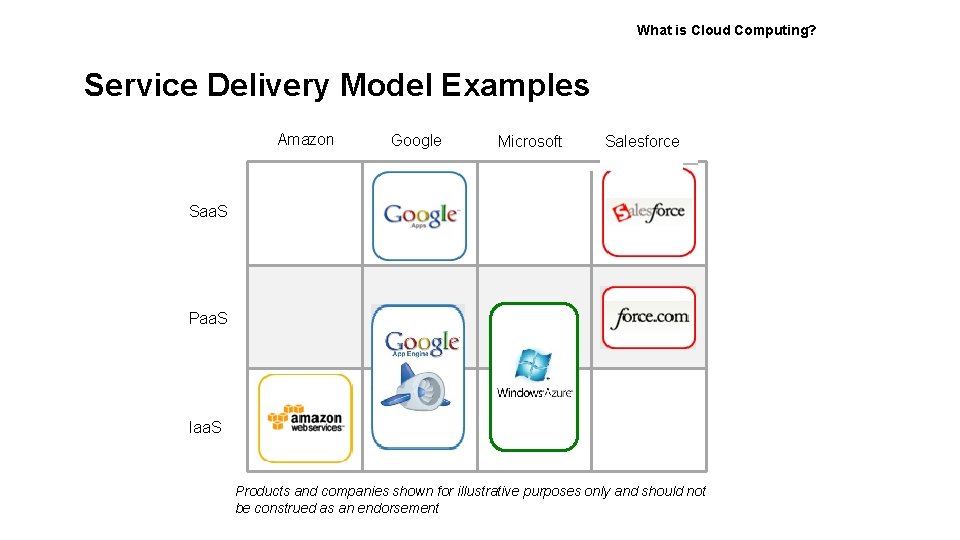
What is Cloud Computing? Service Delivery Model Examples Amazon Google Microsoft Salesforce Saa. S Paa. S Iaa. S Products and companies shown for illustrative purposes only and should not be construed as an endorsement

Deployment Models • Public Clouds • Private Clouds • Hybrid Clouds

Network Functions Virtualization Source: utfi. co. in/file. php/1/SDNNFVTalk. pptx www. cs. cmu. edu/~srini/15 -744/S 15/lectures/12 -middlebox. ppt

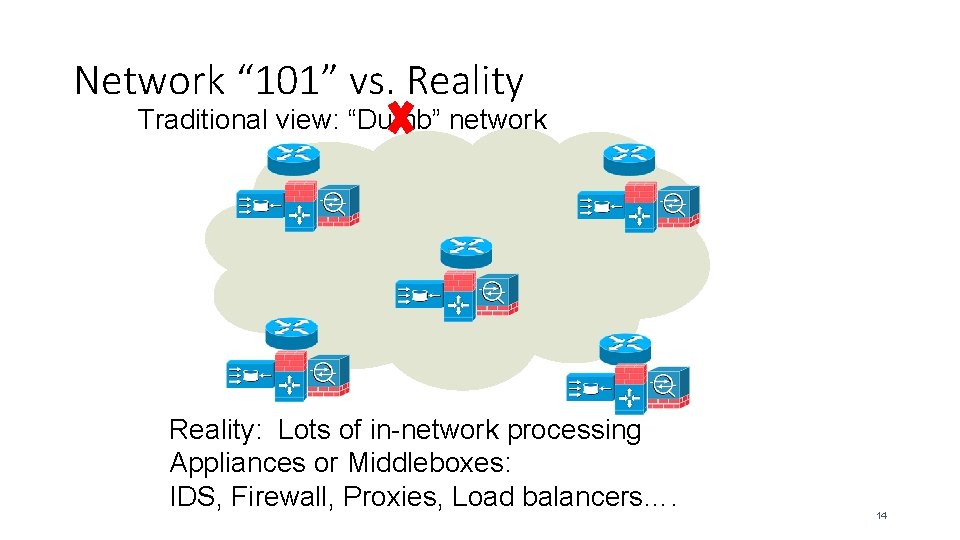
Network “ 101” vs. Reality Traditional view: “Dumb” network Reality: Lots of in-network processing Appliances or Middleboxes: IDS, Firewall, Proxies, Load balancers…. 14

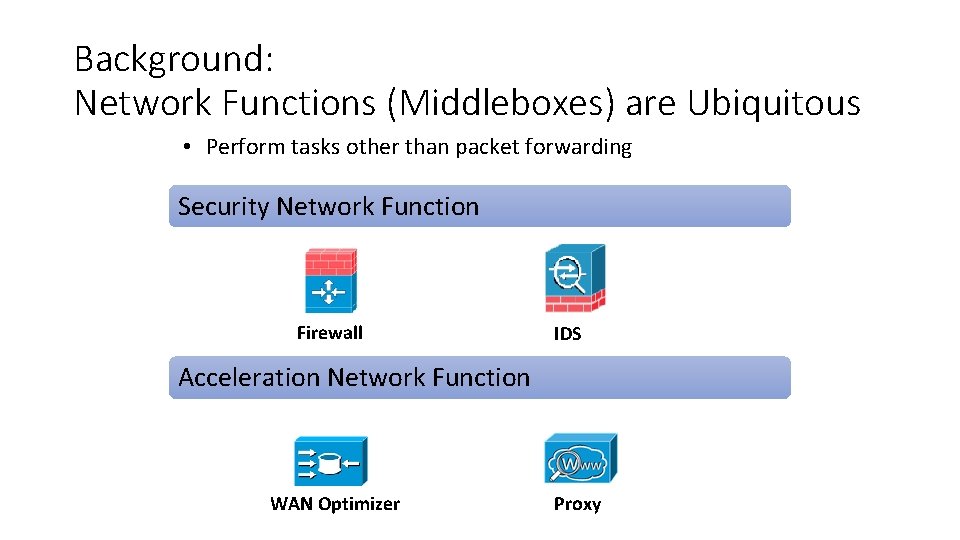
Background: Network Functions (Middleboxes) are Ubiquitous • Perform tasks other than packet forwarding Security Network Function Firewall IDS Acceleration Network Function WAN Optimizer Proxy

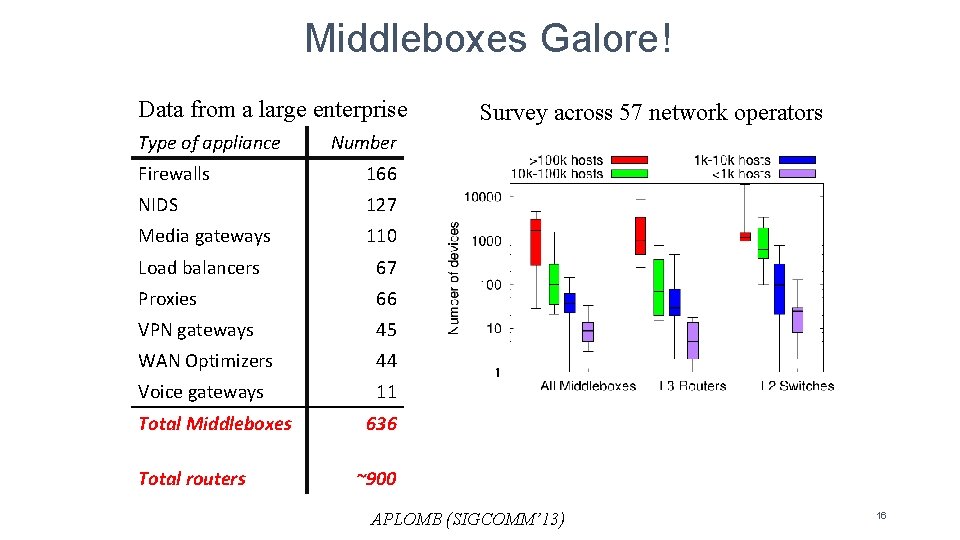
Middleboxes Galore! Data from a large enterprise Type of appliance Number Firewalls 166 NIDS 127 Media gateways 110 Load balancers 67 Proxies 66 VPN gateways 45 WAN Optimizers 44 Voice gateways 11 Total Middleboxes Total routers Survey across 57 network operators 636 ~900 APLOMB (SIGCOMM’ 13) 16

Traditional Network Functions: hardware IDS WAN Optimizer Proxy

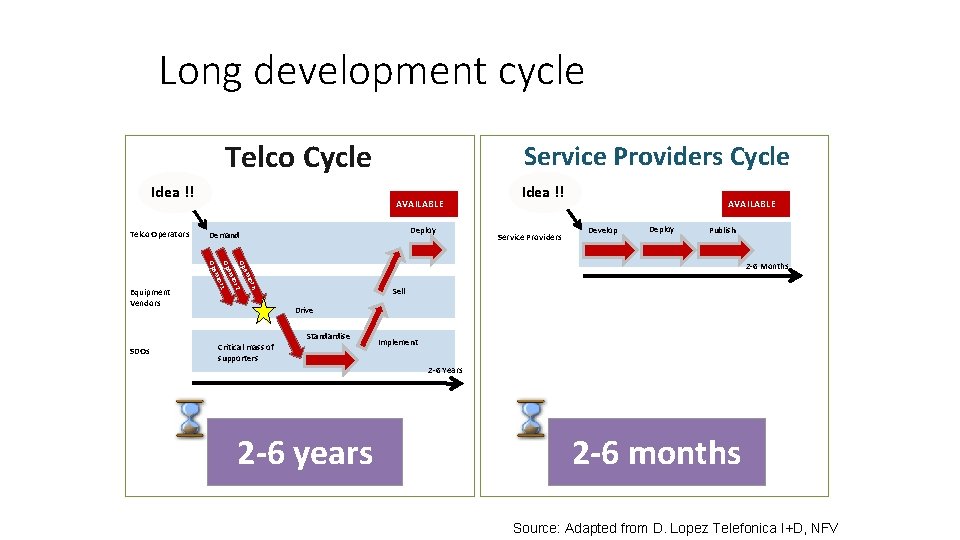
Long development cycle Telco Cycle Idea !! Telco Operators AVAILABLE Deploy Demand Service Providers AVAILABLE Develop Deploy Publish 2 1 n tor era 2 -6 Months Sell Drive Standardise SDOs Idea !! Op Op Op Equipment Vendors Service Providers Cycle Critical mass of supporters Implement 2 -6 Years 2 -6 years 2 -6 months Source: Adapted from D. Lopez Telefonica I+D, NFV

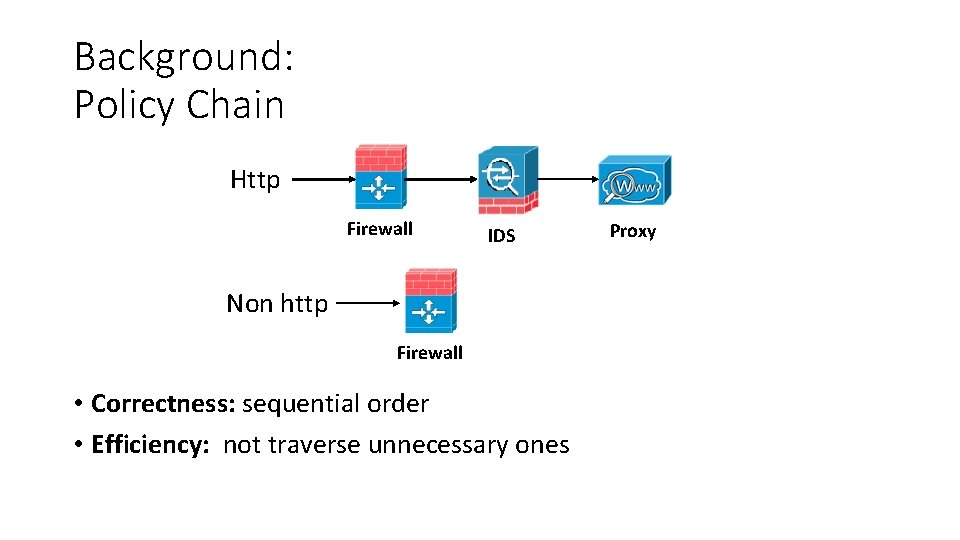
Background: Policy Chain Http Firewall IDS Non http Firewall • Correctness: sequential order • Efficiency: not traverse unnecessary ones Proxy

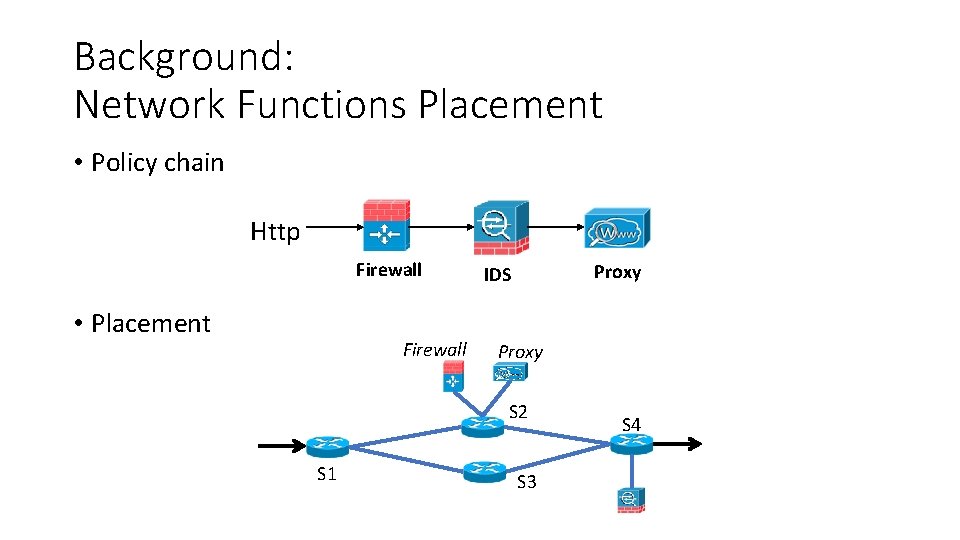
Background: Network Functions Placement • Policy chain Http Firewall • Placement Firewall Proxy IDS Proxy S 2 S 1 S 3 S 4

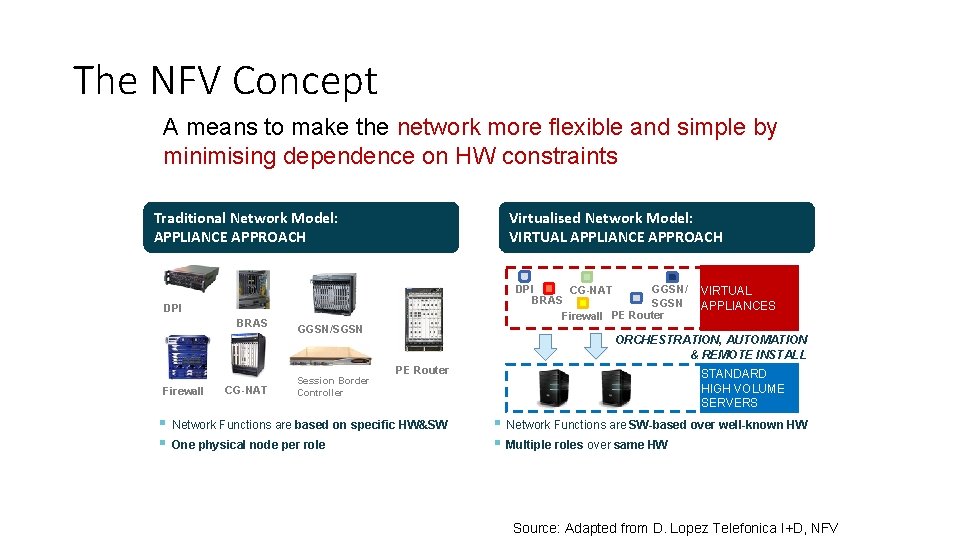
The NFV Concept A means to make the network more flexible and simple by minimising dependence on HW constraints Traditional Network Model: APPLIANCE APPROACH Virtualised Network Model: VIRTUAL APPLIANCE APPROACH v v DPI GGSN/ CG-NAT BRAS SGSN Firewall PE Router DPI BRAS Firewall CG-NAT GGSN/SGSN Session Border Controller VIRTUAL APPLIANCES ORCHESTRATION, AUTOMATION & REMOTE INSTALL PE Router § Network Functions are based on specific HW&SW § One physical node per role STANDARD HIGH VOLUME SERVERS § Network Functions are SW-based over well-known HW § Multiple roles over same HW Source: Adapted from D. Lopez Telefonica I+D, NFV

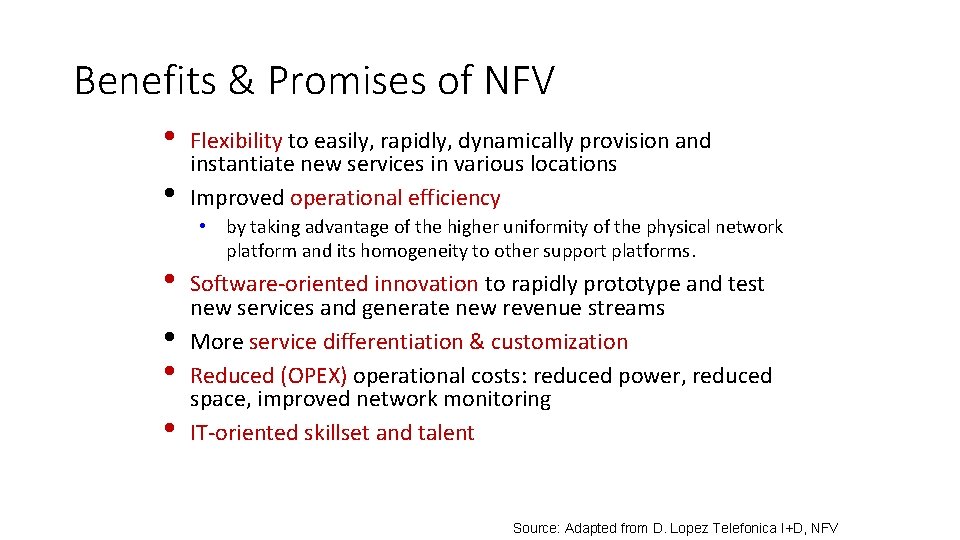
Benefits & Promises of NFV • Reduced equipment costs (CAPEX) • through consolidating equipment and economies of scale of IT industry. • Increased speed of time to market • by minimising the typical network operator cycle of innovation. • Availability of network appliance multi-version and multi-tenancy, • allows a single platform for different applications, users and tenants. • Enables a variety of eco-systems and encourages openness. • Encouraging innovation to bring new services and generate new revenue streams. Source: NFV

Benefits & Promises of NFV • • • Flexibility to easily, rapidly, dynamically provision and instantiate new services in various locations Improved operational efficiency • by taking advantage of the higher uniformity of the physical network platform and its homogeneity to other support platforms. Software-oriented innovation to rapidly prototype and test new services and generate new revenue streams More service differentiation & customization Reduced (OPEX) operational costs: reduced power, reduced space, improved network monitoring IT-oriented skillset and talent Source: Adapted from D. Lopez Telefonica I+D, NFV

NFV and SDN • NFV and SDN are highly complementary • Both topics are mutually beneficial but not dependent on each other Source: NFV

First: A Few Challenges • Achieving high performance virtualised network appliances • • • – portable between different HW vendors, and with different hypervisors. Co-existence with bespoke HW based network platforms – enabling efficient migration paths to fully virtualised network platforms. Management and orchestration of virtual network appliances – ensuring security from attack and misconfiguration. NFV will only scale if all of the functions can be automated. Appropriate level of resilience to HW and SW failures. Integrating multiple virtual appliances from different vendors. – Network operators need to be able to “mix & match” HW, – hypervisors and virtual appliances from different vendors, – without incurring significant integration costs and avoiding lock-in. NFV and SDN

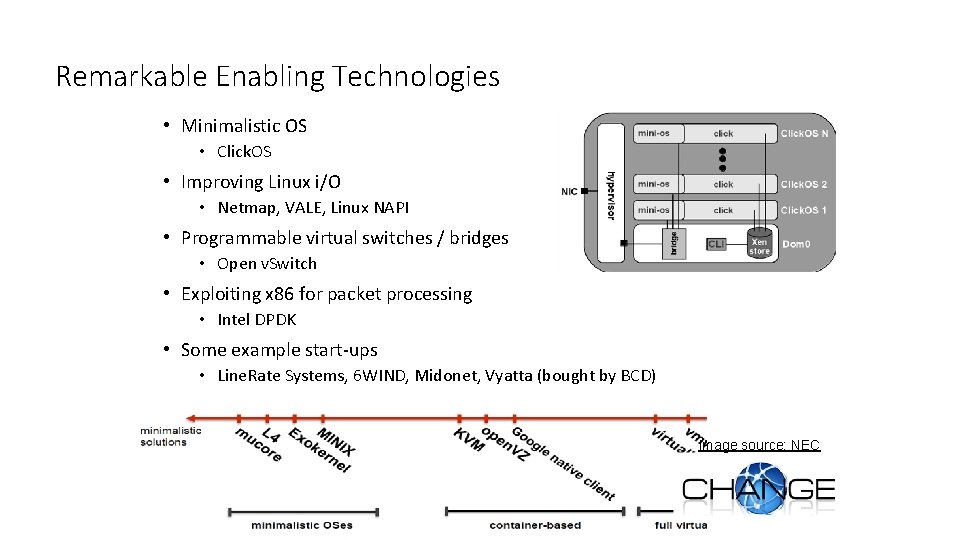
Remarkable Enabling Technologies • Minimalistic OS • Click. OS • Improving Linux i/O • Netmap, VALE, Linux NAPI • Programmable virtual switches / bridges • Open v. Switch • Exploiting x 86 for packet processing • Intel DPDK • Some example start-ups • Line. Rate Systems, 6 WIND, Midonet, Vyatta (bought by BCD) Image source: NEC

Improving the Scalability of Data Center Networks with Traffic-aware Virtual Machine Placement Source: https: //webcourse. cs. technion. ac. il/236635/Winter 2010 -2011/ho/WCFiles/9. pdf

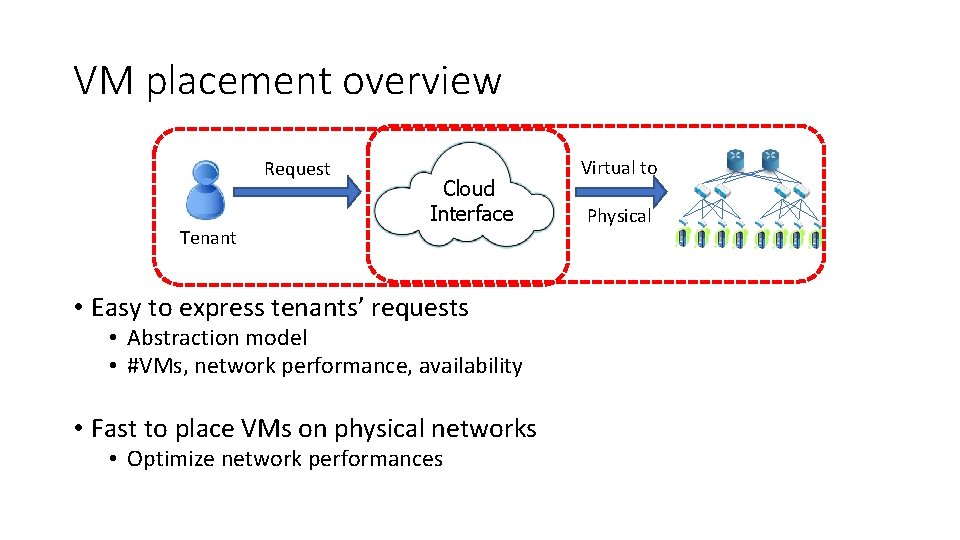
VM placement overview Request Tenant Cloud Interface • Easy to express tenants’ requests • Abstraction model • #VMs, network performance, availability • Fast to place VMs on physical networks • Optimize network performances Virtual to Physical




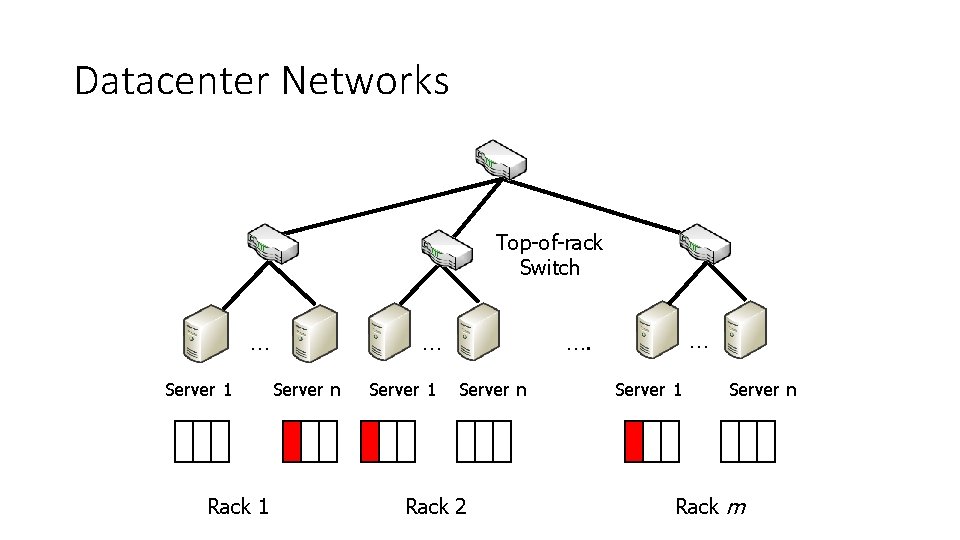
Datacenter Networks Top-of-rack Switch … … Server 1 Rack 1 Server n Server 1 … …. Server n Rack 2 Server 1 Server n Rack m

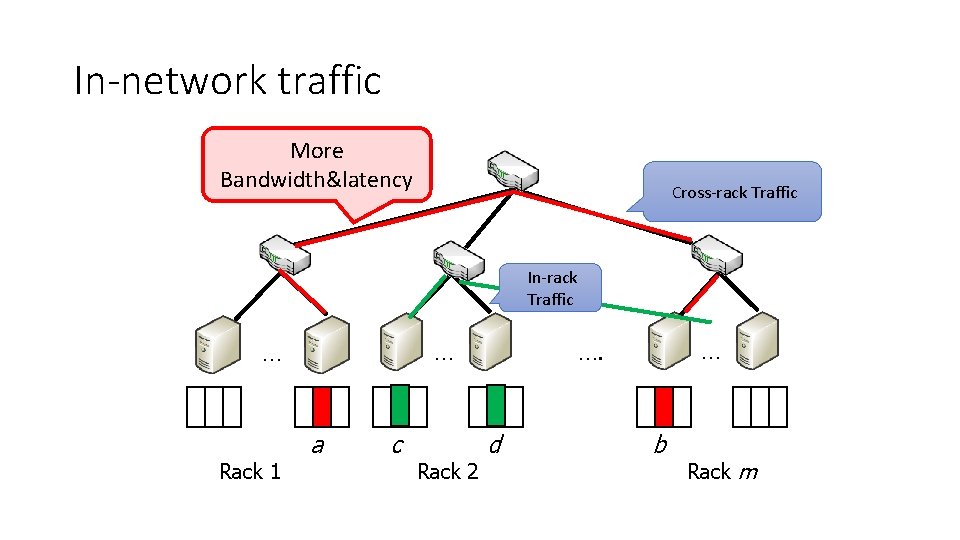
In-network traffic More Bandwidth&latency Cross-rack Traffic In-rack Traffic … … Rack 1 a c Rack 2 … …. d b Rack m

Reducing cross-rack traffic • In-rack traffic is more preferred than cross-rack traffic • Switch can forward in-rack packets at line-rate between different ports • Oversubscription is common in current DCNs • Cross-rack traffic is a level of oversubscription. Packet-drop will occur for high cross-rack traffics

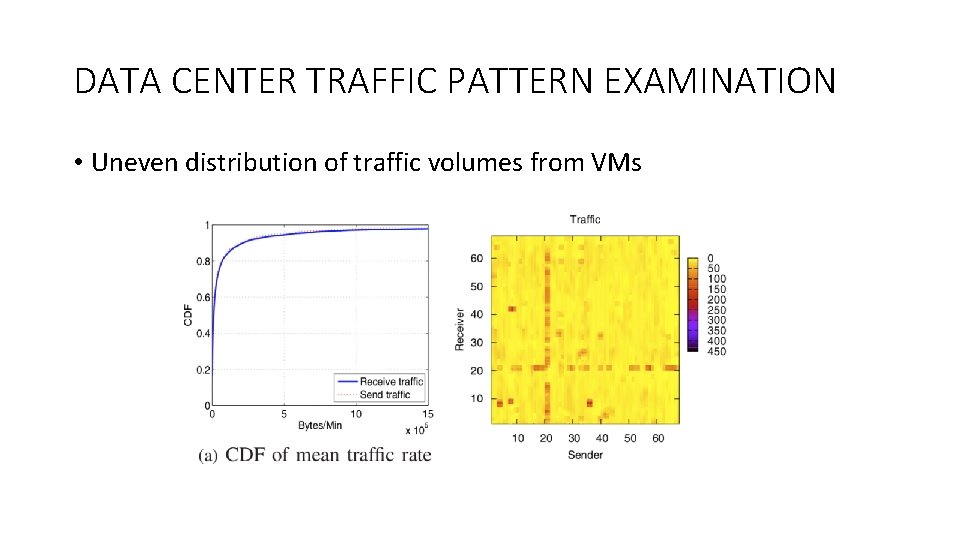
DATA CENTER TRAFFIC PATTERN EXAMINATION • Uneven distribution of traffic volumes from VMs

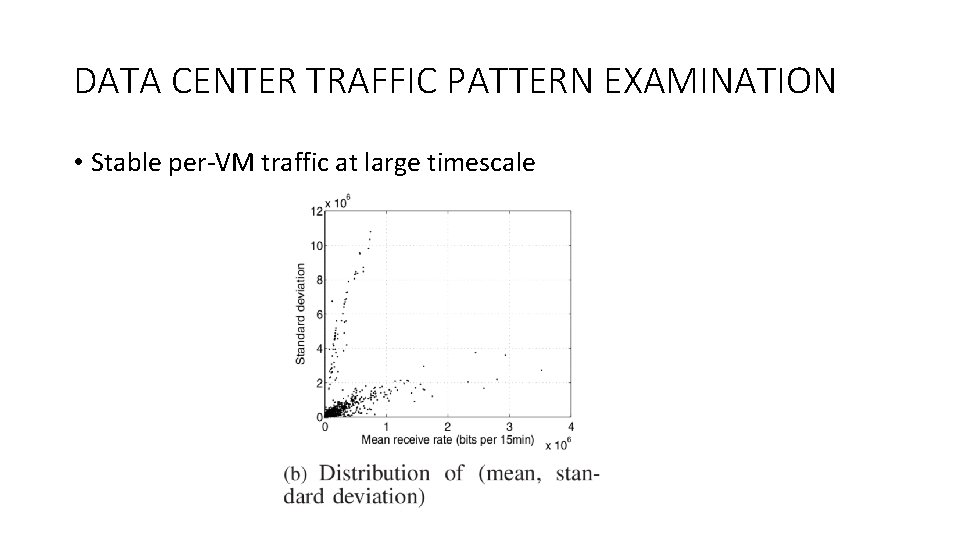
DATA CENTER TRAFFIC PATTERN EXAMINATION • Stable per-VM traffic at large timescale

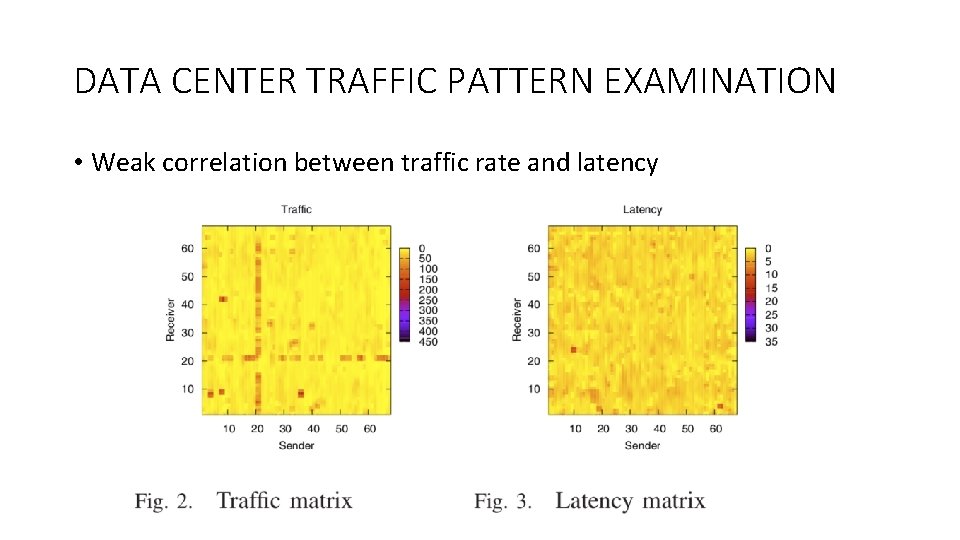
DATA CENTER TRAFFIC PATTERN EXAMINATION • Weak correlation between traffic rate and latency

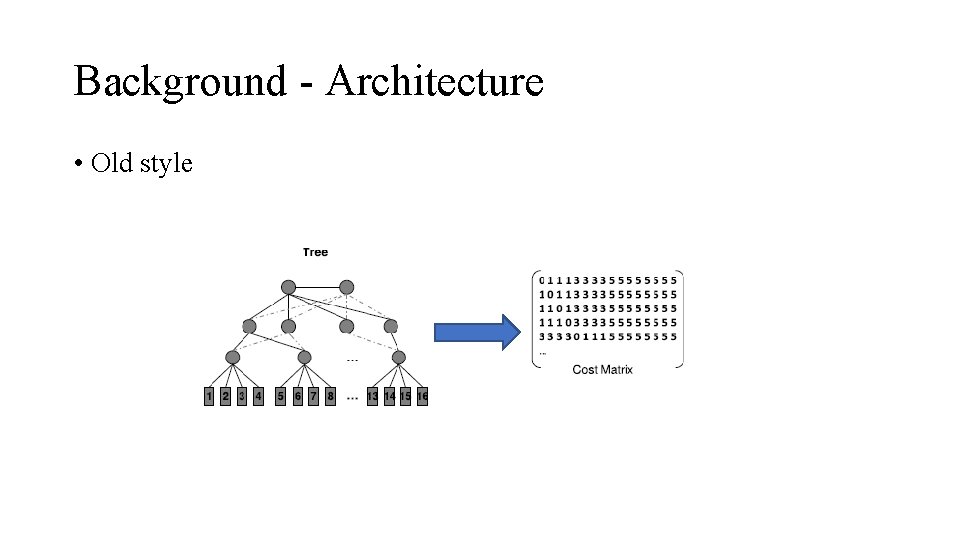
Background - Architecture • Old style

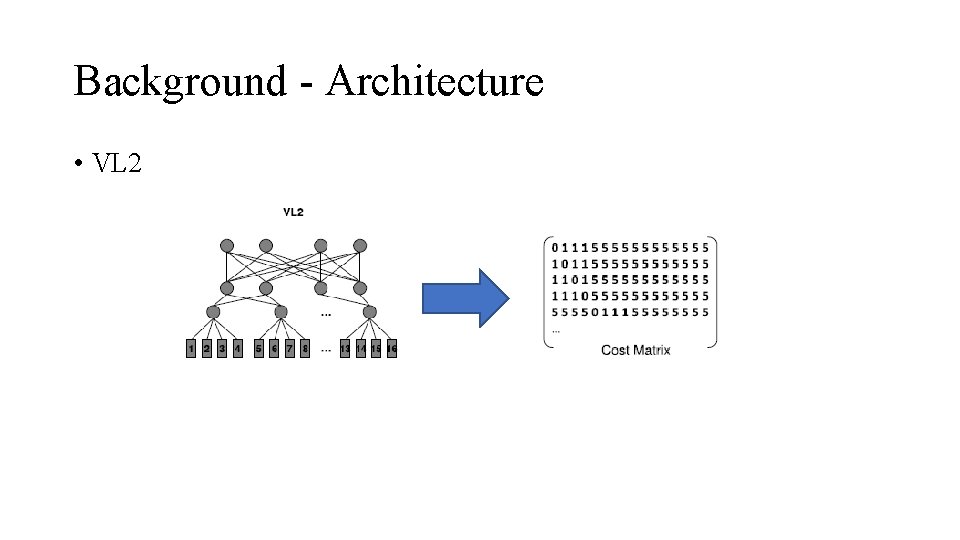
Background - Architecture • VL 2

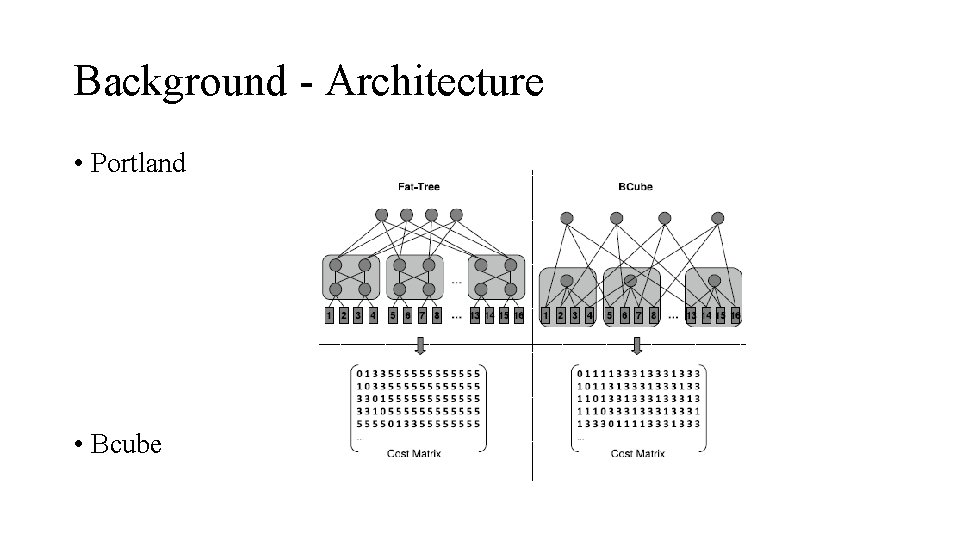
Background - Architecture • Portland • Bcube

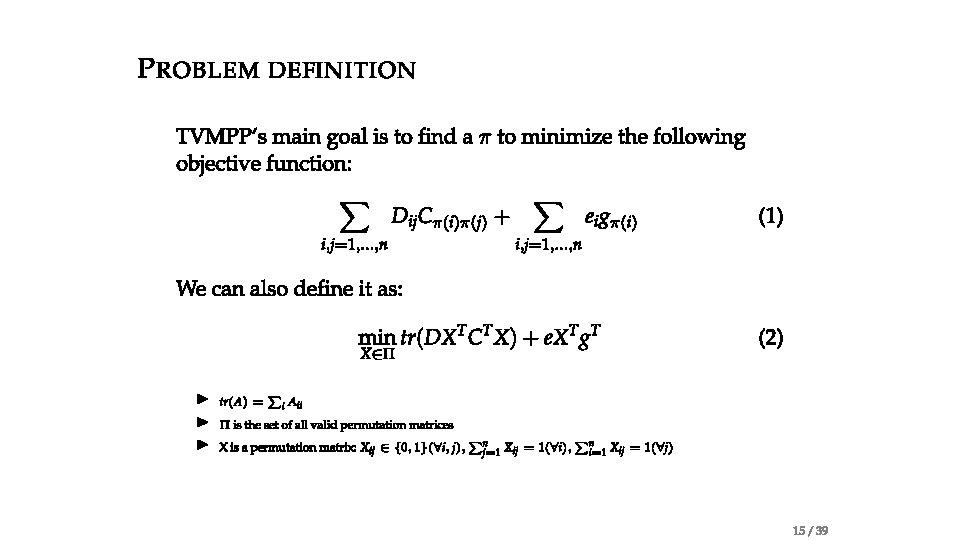
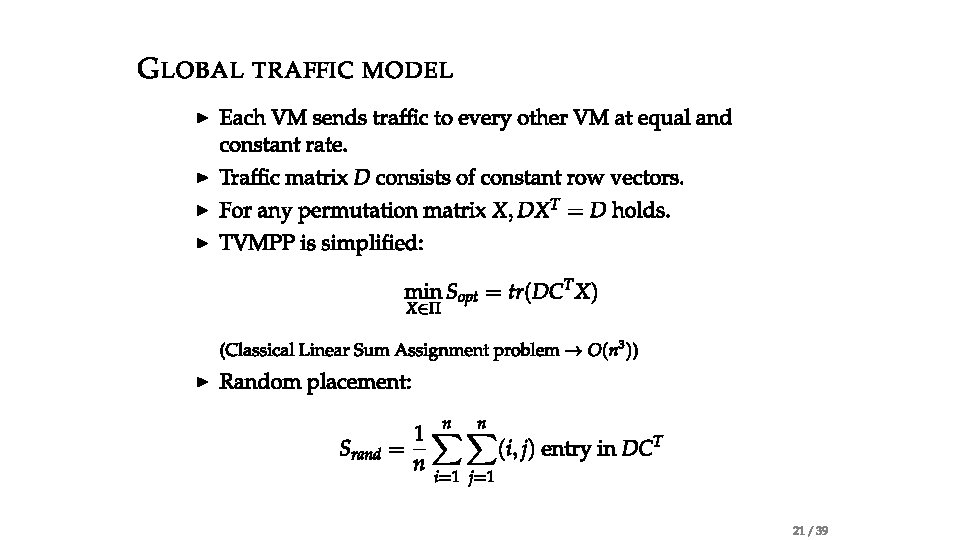
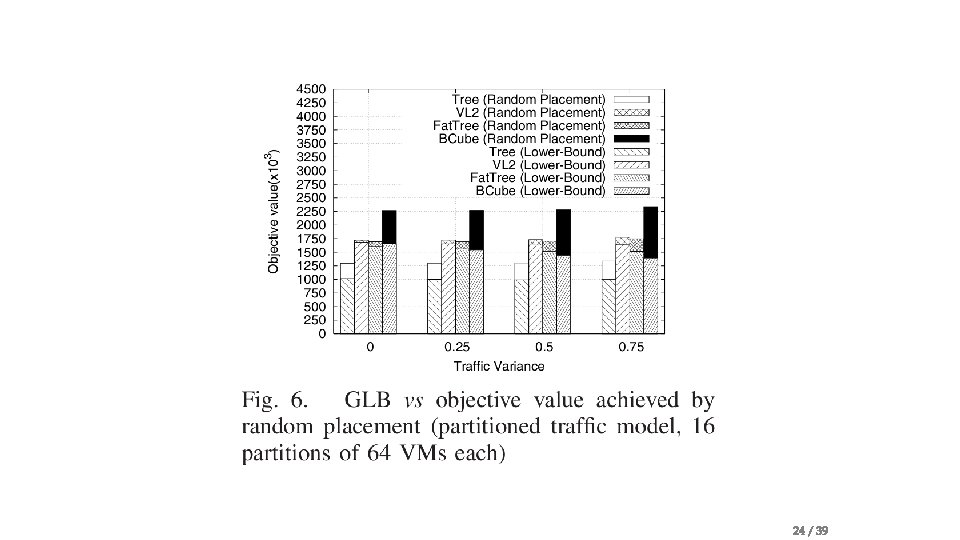
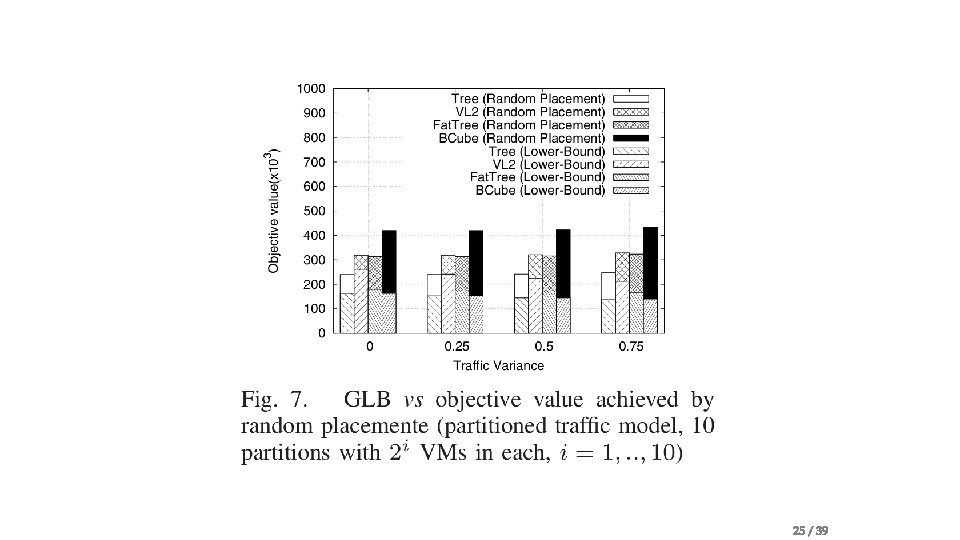
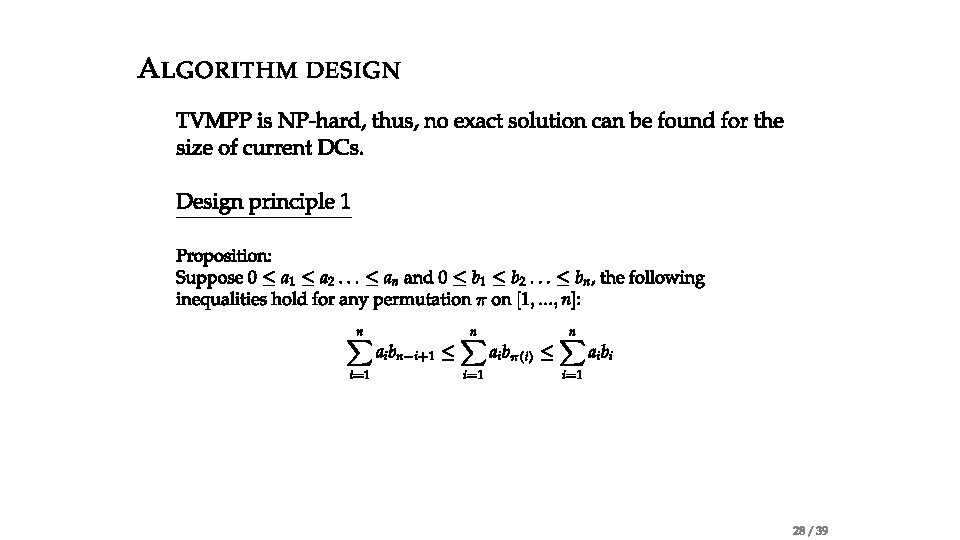
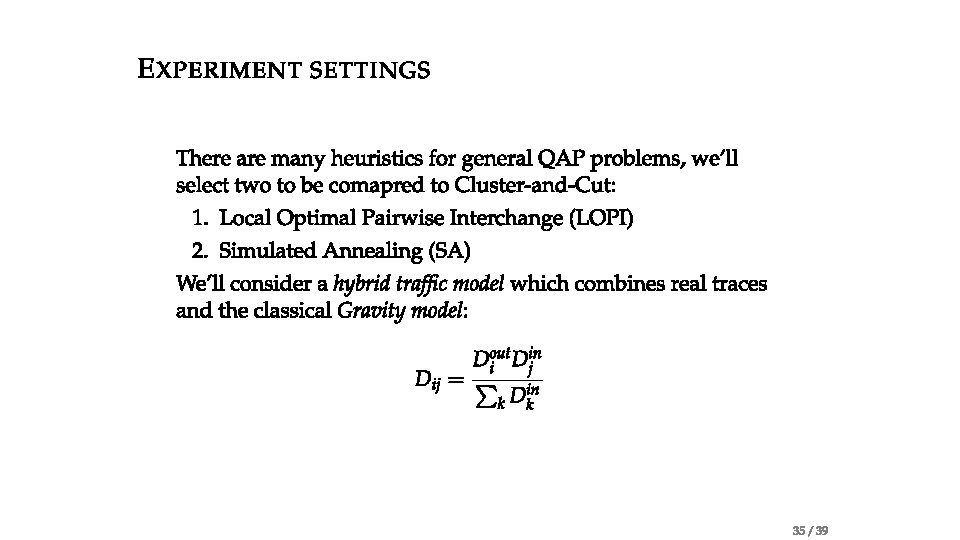
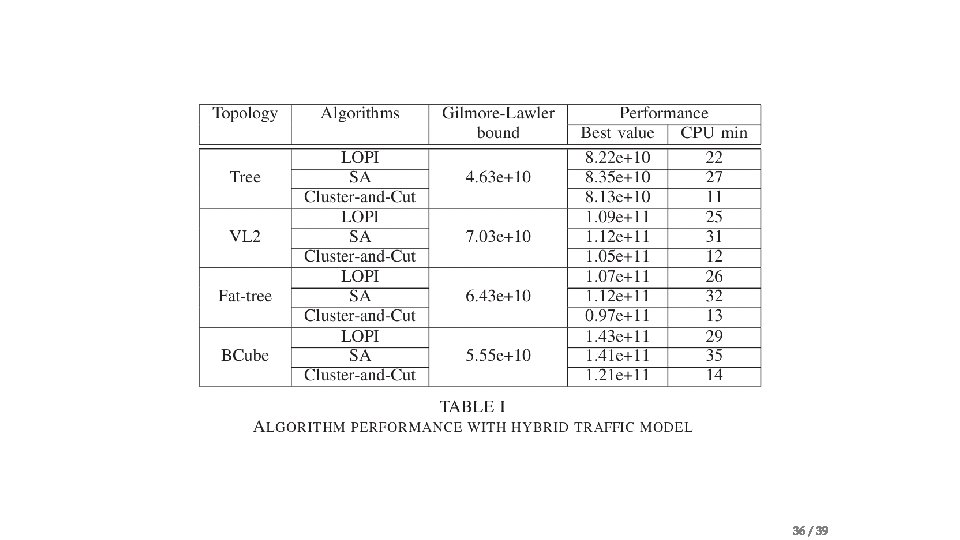
Problem statement • Traffic-aware VM Placement Problem (TVMPP) • given: traffic matrix , cost matrix • Goal: minimize cost














