CIT 412 INFORMATION TECHNOLOGY CENTRE MANAGEMENT Dr Lala






















- Slides: 26

CIT 412: INFORMATION TECHNOLOGY CENTRE MANAGEMENT Dr. Lala O. G

IT MANAGEMENT v IT management is the discipline whereby all of the information technology resources of a firm are managed in accordance with its needs and priorities. These resources may include tangible investments like computer hardware, software, data, networks and data centre facilities, as well as the staff who are hired to maintain them. v Managing this responsibility within a company entails many of the basic management functions, like budgeting, staffing, change management, and organizing and controlling, along with other aspects that are unique to technology, like software design, network planning, tech support

IT MANAGEMENT v The central aim of IT management is to generate value through the use of technology. To achieve this, business strategies and technology must be aligned. v IT Management is different from management information systems. The latter refers to management methods tied to the automation or support of human decision making. IT Management refers to IT related management activities in organizations. MIS is focused mainly on the business aspect, with strong input into the technology phase of the business/organization.

IT MANAGEMENT v A primary focus of IT management is the value creation made possible by technology. This requires the alignment of technology and business strategies. While the value creation for an organization involves a network of relationships between internal and external environments, technology plays an important role in improving the overall value chain of an organization. However, this increase requires business and technology management to work as a creative, synergistic, and collaborative team instead of a purely mechanistic span of control.

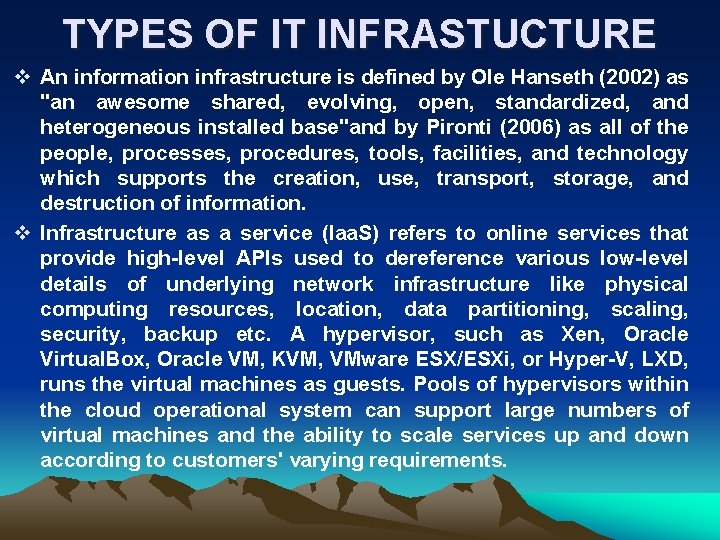
IT INFRASTUCTURE v Information technology infrastructure is defined broadly as a set of information technology (IT) components that are the foundation of an IT service; typically physical components (computer and networking hardware and facilities), but also various software and network components. v The fields of IT management and IT service management rely on IT infrastructure, and the ITIL framework was developed as a set of best practices with regard to IT infrastructure. v Enterprise IT infrastructure typically refers to components required for the existence, operation and management of an enterprise IT environment. It can be internal to an organization and deployed within owned facilities, or deployed within a cloud computing system, or a combination thereof

TYPES OF IT INFRASTUCTURE v Converged infrastructure operates by grouping multiple information technology (IT) components into a single, optimized computing package. Components of a converged infrastructure may include servers, data storage devices, networking equipment and software for IT infrastructure management, automation and orchestration. v Dynamic Infrastructure is an information technology paradigm concerning the design of data centers so that the underlying hardware and software can respond dynamically to changing levels of demand in more fundamental and efficient ways than before. v Hyper-converged infrastructure (HCI) is a software-defined IT infrastructure that virtualizes all of the elements of conventional "hardware-defined" systems. HCI includes, at a minimum, virtualized computing (a hypervisor), a virtualized SAN (softwaredefined storage) and virtualized networking (software-defined networking). HCI typically runs on commercial off-the-shelf (COTS) servers.

TYPES OF IT INFRASTUCTURE v An information infrastructure is defined by Ole Hanseth (2002) as "an awesome shared, evolving, open, standardized, and heterogeneous installed base"and by Pironti (2006) as all of the people, processes, procedures, tools, facilities, and technology which supports the creation, use, transport, storage, and destruction of information. v Infrastructure as a service (Iaa. S) refers to online services that provide high-level APIs used to dereference various low-level details of underlying network infrastructure like physical computing resources, location, data partitioning, scaling, security, backup etc. A hypervisor, such as Xen, Oracle Virtual. Box, Oracle VM, KVM, VMware ESX/ESXi, or Hyper-V, LXD, runs the virtual machines as guests. Pools of hypervisors within the cloud operational system can support large numbers of virtual machines and the ability to scale services up and down according to customers' varying requirements.

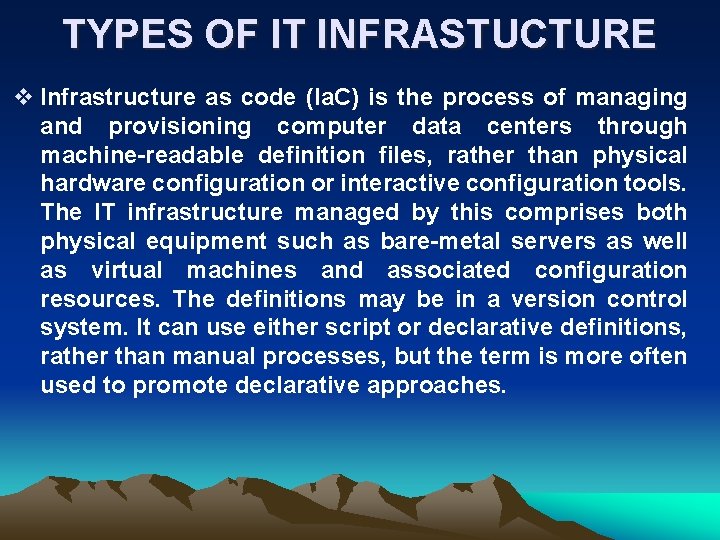
TYPES OF IT INFRASTUCTURE v Infrastructure as code (Ia. C) is the process of managing and provisioning computer data centers through machine-readable definition files, rather than physical hardware configuration or interactive configuration tools. The IT infrastructure managed by this comprises both physical equipment such as bare-metal servers as well as virtual machines and associated configuration resources. The definitions may be in a version control system. It can use either script or declarative definitions, rather than manual processes, but the term is more often used to promote declarative approaches.

IT MANAGEMENT DISCIPLINES The below concepts are commonly listed or investigated under the broad term IT Management: Business/IT alignment v Business-IT alignment is a dynamic state in which a business organization is able to use information technology (IT) to achieve business objectives - typically improved financial performance or marketplace competitiveness. Some definitions focus more on outcomes (the ability of IT to produce business value) than means (the harmony between IT and business decision-makers within the organizations).

IT MANAGEMENT DISCIPLINES IT governance v Information and technology (IT) governance is a subset discipline of corporate governance, focused on information and technology (IT) and its performance and risk management. The interest in IT governance is due to the ongoing need within organizations to focus value creation efforts on an organization's strategic objectives and to better manage the performance of those responsible for creating this value in the best interest of all stakeholders. IT financial management v Financial Management for IT Services is a Service Strategy element of the ITIL best practice framework. The aim of this ITIL process area is to give accurate and cost effective stewardship of IT assets and resources used in providing IT Services. It is used to plan, control and recover costs expended in providing the IT Services negotiated and agreed to in a service-level agreement (SLA).

IT MANAGEMENT DISCIPLINES IT service management v IT service management (ITSM) refers to the entirety of activities – directed by policies, organized and structured in processes and supporting procedures – that are performed by an organization to design, plan, deliver, operate and control information technology (IT) services offered to customers. It is thus concerned with the implementation of IT services that meet customers' needs, and it is performed by the IT service provider through an appropriate mix of people, process and information technology. Sourcing v Corporate sourcing refers to a system where divisions of companies coordinate the procurement and distribution of materials, parts, equipment, and supplies for the organization. This is a supply chain, purchasing/procurement, and inventory function. This enables bulk discounting, auditing, and Sarbanes-Oxley compliance.

DUTIES OF A CORPORATE SOURCING AGENT INCLUDE v Coordinating all activities related to procurement of a commodity beginning with intent to purchase through delivery v Analyzing the requirements of the commodity, including preliminary specifications, preferred supplier, and date commodity is needed v Soliciting and evaluating proposals for the requested commodity. Investigating and/or interviewing potential suppliers to determine if they meet the specified requirements

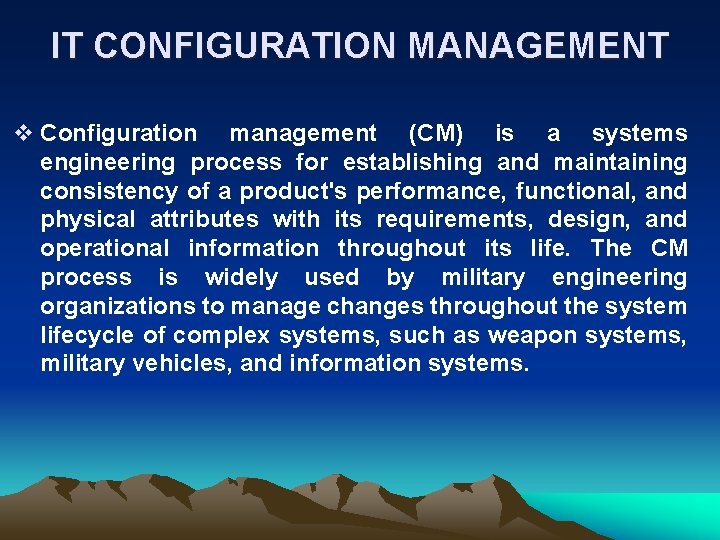
IT CONFIGURATION MANAGEMENT v Configuration management (CM) is a systems engineering process for establishing and maintaining consistency of a product's performance, functional, and physical attributes with its requirements, design, and operational information throughout its life. The CM process is widely used by military engineering organizations to manage changes throughout the system lifecycle of complex systems, such as weapon systems, military vehicles, and information systems.

IT MANAGERS v IT managers have a lot in common with project managers but their main difference is one of focus: an IT manager is responsible and accountable for an ongoing program of IT services while the project manager's responsibility and accountability are both limited to a project with a clear start and end date.

DISADVANTAGES OF IT MANAGEMENT TECHNOLOGY IMPROVES EVERYDAY TASKS v Technology improves everyday tasks that used to be performed by human employees and is now carried out by computer systems. Telephone answering systems replacing live receptionists is one example of such substitution. It is, however, important to understand that often these changes can lead to issues as well as benefits. Losing personal communication with clients, security issues, etc. may have a heavy impact in company value. Such aspects must be considered before, during and after all decisions and implementations for IT management to be successful.

OFFICE PROCEDURE v It is the responsibility of all employees in an organization to protect sensitive data against loss or theft. Awareness, education and practice of the following procedures can assist in this matter. These procedures are in place to help protect employees, customers, contractors and the organization from damages related to the loss or misuse of sensitive information.

STAFF TRAINING Employee awareness and education is an integral part of securing sensitive data for an organization. The following procedures should be enforced to ensure proper training: v a) Upon hire, the Secure Office Procedure and Setting Strong Password documents are emailed to the new employee v b) Secure Office Procedure and Setting Strong Password documents are sent annually to all employees via email v c) Internal training, specific to each area, will be provided to employees who have access to sensitive data

STAFF TRAINING v d) Information Technology will provide Best Practices information at IT seminars and offer to attend annual departmental meetings to cover the below topics: i. Awareness of Social Engineering schemes ii. Secure Office Procedures iii. Strong Password creation iv. Data storage v. Data encryption vi. Backups vii. Anti-virus and Anti-spyware tools viii. Non-secure technologies

GENERAL OFFICE SECURITY PRACTICES The following procedures should be followed within office suites, individual offices or workrooms and mobile locations where data may be referenced: v Upon hire, the Secure Office Procedure and Setting Strong Password documents are emailed to the new employee v Keys or keycards used for access to sensitive data should not be left unattended v Passwords should not be shared or written down and left in accessible locations v If you have a student that will regularly be using your machine, contact the helpdesk and request a staff account for that student. (Do NOT give out your password)

GENERAL OFFICE SECURITY PRACTICES v When you leave your workstation, lock your computer screen v Lock up laptops, USB drives, external drives, etc. when unsupervised v Contact the IT Helpdesk when a computer is to be passed to a new user. IT will clean the computer, removing previous data and place a clean image on the machine. v Printouts containing sensitive data should be removed from networked printers immediately and filed appropriately in secure cabinets

GENERAL OFFICE SECURITY PRACTICES v Dispose of sensitive data on hard copy by shredding immediately v Departmental front desk staff should confirm identity of all visitors (staff/student workers or non-employees) who are entering their area(s) v Employees should feel comfortable requesting what unit someone is from and the purpose of their visit v Employees should feel comfortable confirming meeting prior to allowing staff member/student employee to proceed within their departmental areas v Confirm with the organizational employee they are scheduled to meet v Non-employees must be escorted to/from meeting area/work area

GENERAL OFFICE SECURITY PRACTICES v Request ID if necessary v Provide front office staff the ability to view your calendar or print a schedule of your meetings in advance so they will expect attendees v All staff should be responsible to watch for or listen to any unusual activity and to be cognizant of their surroundings.

SENSITIVE INFORMATION Sensitive data can be distributed via hard copy or electronic means within an office. When given the choice, store data electronically versus printing a hard copy. Consider scanning a document to store it electronically versus hard copy. v “Sensitive information” includes but is not limited to the following items, whether stored in electronic or printed format: v All organization protected data v Credit card number (in part or in whole) v Credit card expiration date v Cardholder name v Cardholder address

SENSITIVE INFORMATION v Social Security Number v Business Identification Number v Employer Identification Number v Paychecks v Paystubs v Benefit information v Giving information/history v Health information v Content of external grants or contracts

SECURING HARD COPY SENSITIVE DATA v Lock cabinets containing sensitive data when not in use or when away for extended periods of time v Storage rooms containing sensitive data should be locked at the end of the day or when unsupervised v Desks, workstations, common work areas, printers, and fax machines should be cleared of all sensitive data when not in use v Whiteboards, dry erase boards, writing tablets, etc. should be erased, removed or shredded when not in use v Documents to be shredded should be done so immediately or locked up until shredding can occur v At the end of the day, all sensitive data should be in a locked drawer or cabinet

SECURING ELECTRONIC SENSITIVE DATA v Refrain, when possible from storing sensitive data on your personal computer hard drive or any external personal devices. Instead use the network drive space. v If storing sensitive data is required on your personal computer hard drive or an external device, encryption and password protection should be applied v Engage the screensaver when workspace is unoccupied v Computer workstations should be shut down completely at end of work day v Lock laptop or external devices containing sensitive data when not in use v Make certain data and/or PC work station screens are not visible to the public (e. g. - near windows, entry/exit doors, etc. ) v If email is used to share sensitive data, encryption and/or password protection should be used. The following statement should accompany the body of the email: