CIT 140 Introduction to IT Networking CIT 140








![Dig: DNS Lookup dig [options] Purpose Interact with name servers specified in /etc/resolv. conf Dig: DNS Lookup dig [options] Purpose Interact with name servers specified in /etc/resolv. conf](https://slidetodoc.com/presentation_image/9b5a5891cf299f784ce104dc8938080b/image-28.jpg)



![Testing a Network Connection ping [options] hostname Purpose: Send packet to hostname. If hostname Testing a Network Connection ping [options] hostname Purpose: Send packet to hostname. If hostname](https://slidetodoc.com/presentation_image/9b5a5891cf299f784ce104dc8938080b/image-35.jpg)
![Displaying User Information finger [options] [user_list] Purpose: Display information about the users in the Displaying User Information finger [options] [user_list] Purpose: Display information about the users in the](https://slidetodoc.com/presentation_image/9b5a5891cf299f784ce104dc8938080b/image-38.jpg)
![Remote Login: telnet (Obsolete) telnet host [port] Purpose: Obsolete, insecure protocol for logging into Remote Login: telnet (Obsolete) telnet host [port] Purpose: Obsolete, insecure protocol for logging into](https://slidetodoc.com/presentation_image/9b5a5891cf299f784ce104dc8938080b/image-40.jpg)
![Remote Login: ssh [options] host [command] ssh [options] user@host [command] Purpose: Secure login to Remote Login: ssh [options] host [command] ssh [options] user@host [command] Purpose: Secure login to](https://slidetodoc.com/presentation_image/9b5a5891cf299f784ce104dc8938080b/image-42.jpg)

![File Transfer ftp [options] [host] Purpose: To transfer files from or to a remote File Transfer ftp [options] [host] Purpose: To transfer files from or to a remote](https://slidetodoc.com/presentation_image/9b5a5891cf299f784ce104dc8938080b/image-46.jpg)

- Slides: 50

CIT 140: Introduction to IT Networking CIT 140: Introduction to IT 1

Topics 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. What are Networks? Why do we want Networks? Social Issues Sizes and Types of Networks Circuit vs Packet Switching Network Structures: Peer-to-peer and Client-server Performance Issues Network Protocols and Models TCP/IP History of Networks UNIX Network Commands CIT 140: Introduction to IT 2

What is a Computer Network? When two or more computer hardware resources are connected they form a computer network. CIT 140: Introduction to IT 3

Why Networks? Resource Sharing Physical resources: printers, scanners, faxes Information: files, databases, web pages Communication E-mail Collaborative work E-commerce Instant messaging CIT 140: Introduction to IT 4

Social Issues Controversial topics Politics, religion, sex Employers vs employees Monitoring Censorship Government vs citizens FBI Carnivore System National Security Letters CIT 140: Introduction to IT 5

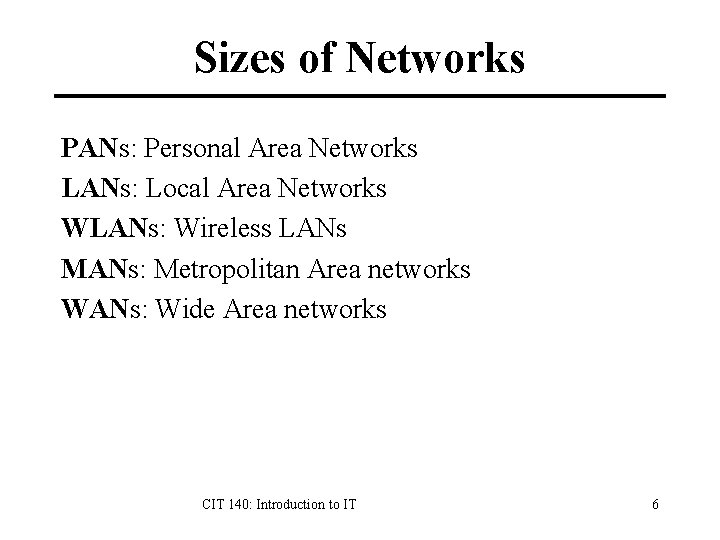
Sizes of Networks PANs: Personal Area Networks LANs: Local Area Networks WLANs: Wireless LANs MANs: Metropolitan Area networks WANs: Wide Area networks CIT 140: Introduction to IT 6

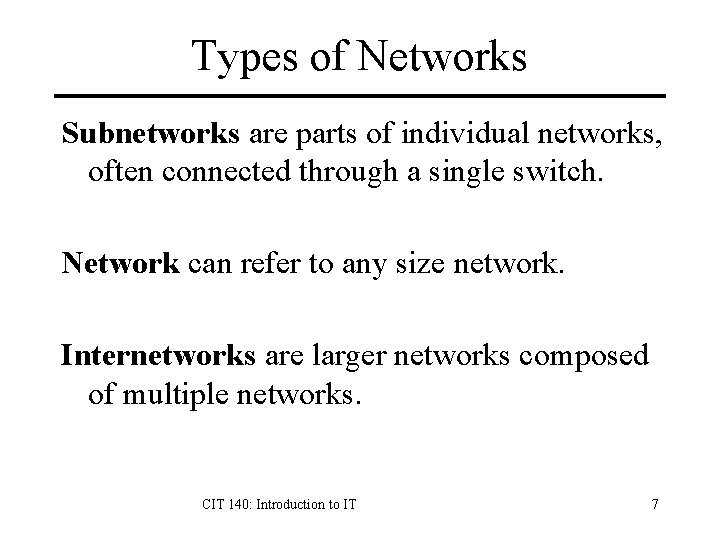
Types of Networks Subnetworks are parts of individual networks, often connected through a single switch. Network can refer to any size network. Internetworks are larger networks composed of multiple networks. CIT 140: Introduction to IT 7

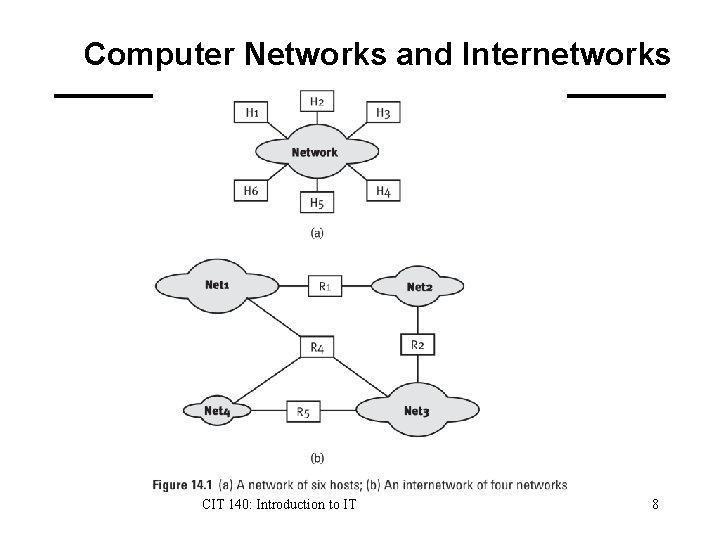
Computer Networks and Internetworks CIT 140: Introduction to IT 8

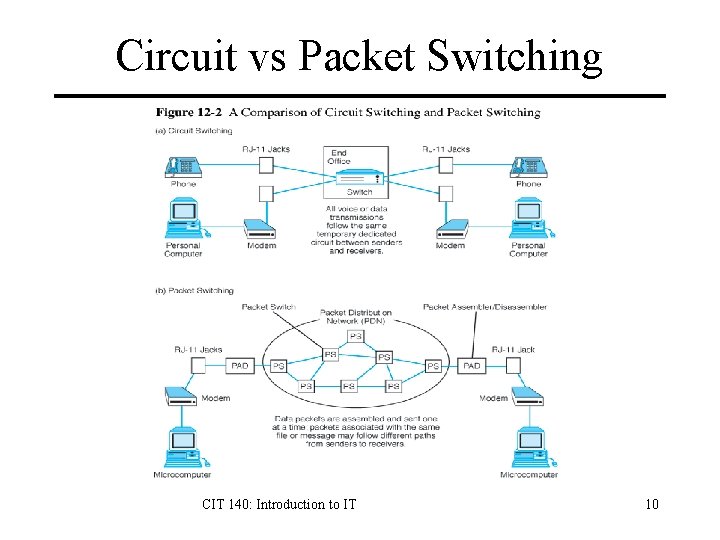
Circuit vs Packet Switching Circuit-switched: A connection called a circuit is set up between two devices and used for the whole communication. Packet-switched: Data is chopped up into small pieces called packets and sent over the network. Each packet may follow a different path between the communicating parties. CIT 140: Introduction to IT 9

Circuit vs Packet Switching CIT 140: Introduction to IT 10

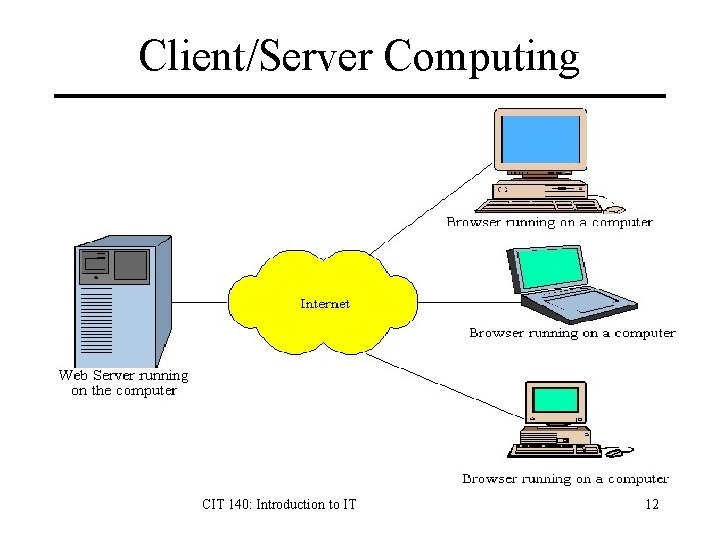
Network Structure Peer-to-Peer: Every computer is an equal peer, running similar software with no special roles. Requests can be from any computer to any other computer. Client-Server: A small number of computers are designed as central servers to provide services to a larger number of user machines called clients. CIT 140: Introduction to IT 11

Client/Server Computing CIT 140: Introduction to IT 12

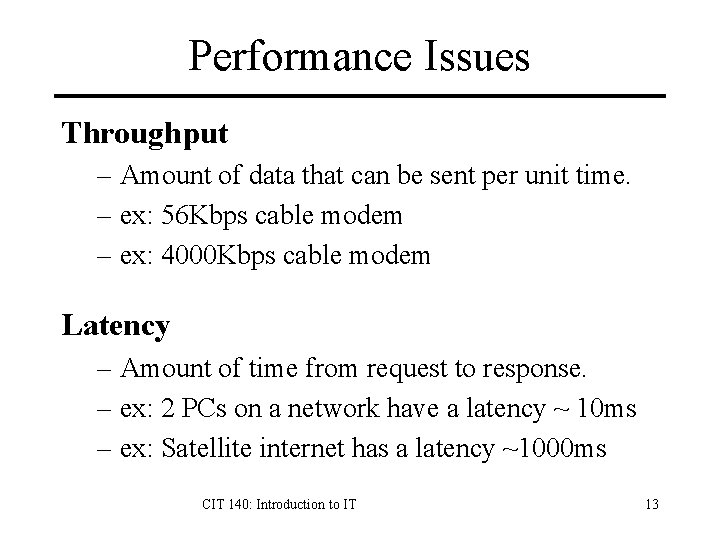
Performance Issues Throughput – Amount of data that can be sent per unit time. – ex: 56 Kbps cable modem – ex: 4000 Kbps cable modem Latency – Amount of time from request to response. – ex: 2 PCs on a network have a latency ~ 10 ms – ex: Satellite internet has a latency ~1000 ms CIT 140: Introduction to IT 13

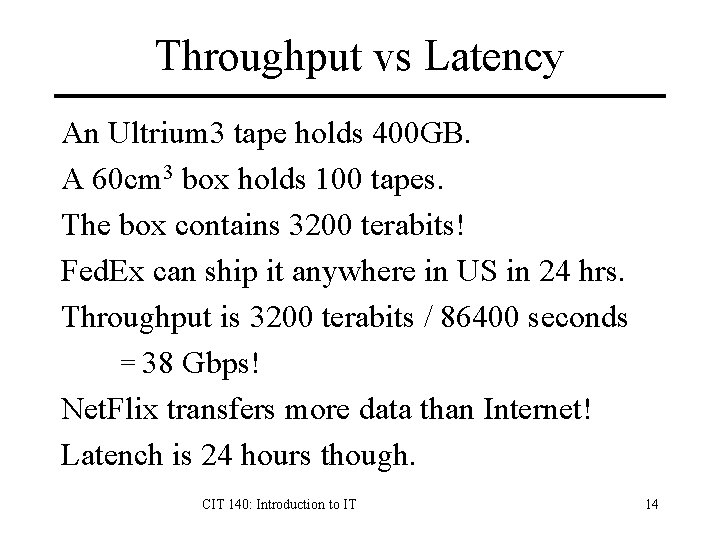
Throughput vs Latency An Ultrium 3 tape holds 400 GB. A 60 cm 3 box holds 100 tapes. The box contains 3200 terabits! Fed. Ex can ship it anywhere in US in 24 hrs. Throughput is 3200 terabits / 86400 seconds = 38 Gbps! Net. Flix transfers more data than Internet! Latench is 24 hours though. CIT 140: Introduction to IT 14

Network Protocols A protocol is an agreement between communicating parties on how communication is to proceed. CIT 140: Introduction to IT 15

Protocol Example: HTTP > telnet www. google. com 80 Trying 72. 14. 203. 99. . . Connected to www. l. google. com. Escape character is '^]'. GET / HTTP/1. 1 200 OK Cache-Control: private Content-Type: text/html Set-Cookie: PREF=ID=e 812 e 6 c 7 ead 517 fe: TM=1131846389: LM=1131846389: S=r. D 8 WNplszt 1 Ko 8 A; expires=Sun, 17 -Jan-2038 19: 14: 07 GMT; path=/; domain=. google. com Server: GWS/2. 1 Transfer-Encoding: chunked Date: Sun, 13 Nov 2005 01: 46: 29 GMT a 46 <html><head><meta http-equiv="content-type" content="text/html; charset=ISO-88591"><title>Google</title><style> CIT 140: Introduction to IT 16

Protocol Example: HTTP > telnet www. google. com 80 Trying 72. 14. 203. 99. . . Connected to www. l. google. com. Escape character is '^]'. GET /foo HTTP/1. 1 404 Not Found Content-Type: text/html Server: GWS/2. 1 Content-Length: 1244 Date: Sun, 13 Nov 2005 01: 47 GMT CIT 140: Introduction to IT 17

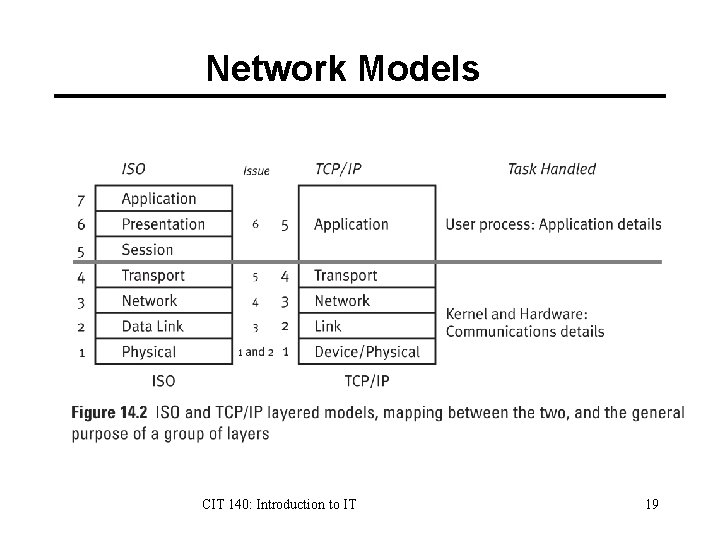
Protocol Stacks Protocols are stacked together in layers High level protocols are application protocols. Medium level ones perform tasks like routing packets through the network. Low level protocols deal with cabling and electrical signaling. CIT 140: Introduction to IT 18

Network Models CIT 140: Introduction to IT 19

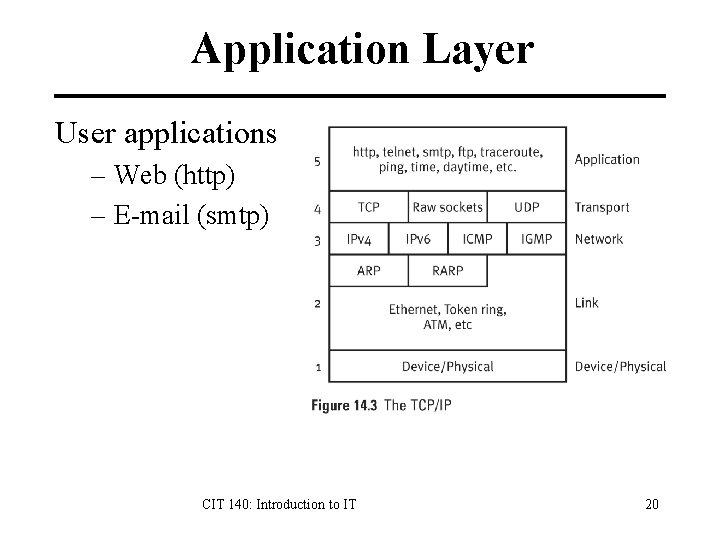
Application Layer User applications – Web (http) – E-mail (smtp) CIT 140: Introduction to IT 20

Transport Layer The transport layer is an end-to-end protocol that transports application data from your machine to a remote machine and vice versa. User Datagram Protocol (UDP) offers the best effort delivery service. Transmission Control Protocol (TCP) offers the completely reliable, in-sequence delivery. It provides a virtual circuit for the communication. CIT 140: Introduction to IT 21

Network Layer IP protocol routes packets from source to destination. Uses IP addresses for source and destination. ex: 10. 11. 32. 10 Does not guarantee delivery. Responsibility of transport or application layer. Uses special purpose computers called routers. CIT 140: Introduction to IT 22

IP Routing CIT 140: Introduction to IT 23

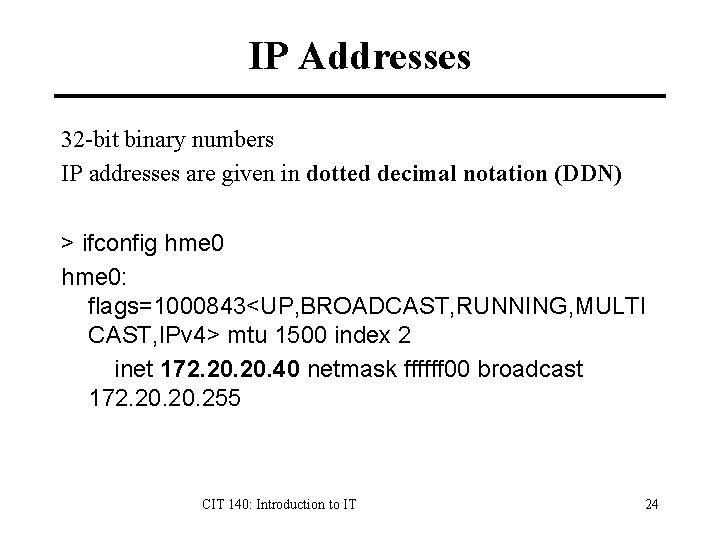
IP Addresses 32 -bit binary numbers IP addresses are given in dotted decimal notation (DDN) > ifconfig hme 0: flags=1000843<UP, BROADCAST, RUNNING, MULTI CAST, IPv 4> mtu 1500 index 2 inet 172. 20. 40 netmask ffffff 00 broadcast 172. 20. 255 CIT 140: Introduction to IT 24

DNS Names Symbolic names are easier to remember Remain same even if the numeric address changes Must be unique for a host on the Internet Format: hostname. domain_name Example: www. nku. edu mail. nku. edu cs. nku. edu CIT 140: Introduction to IT 25

The Domain Name System (DNS) translates DNS names from application layer to IP addresses for network layer. DNS implements a distributed database of name-toaddress mappings. A set of dedicated hosts run name servers that take requests from the application software and work together to map domain names to the corresponding IP addresses CIT 140: Introduction to IT 26

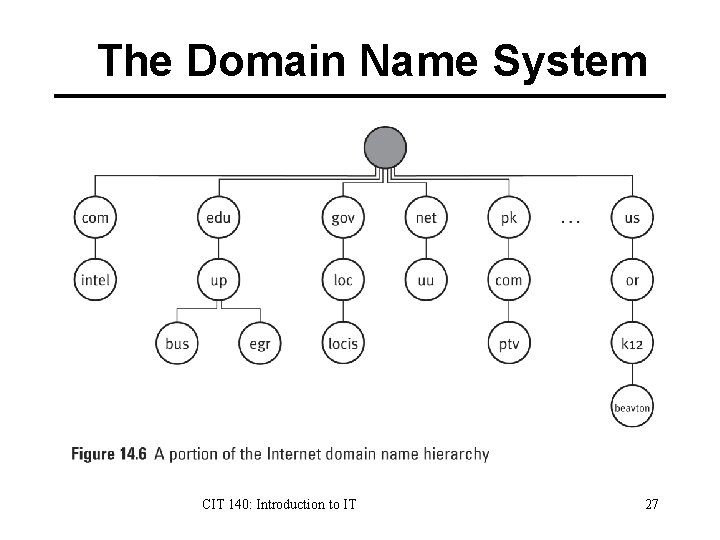
The Domain Name System CIT 140: Introduction to IT 27
![Dig DNS Lookup dig options Purpose Interact with name servers specified in etcresolv conf Dig: DNS Lookup dig [options] Purpose Interact with name servers specified in /etc/resolv. conf](https://slidetodoc.com/presentation_image/9b5a5891cf299f784ce104dc8938080b/image-28.jpg)
Dig: DNS Lookup dig [options] Purpose Interact with name servers specified in /etc/resolv. conf and display their responses Output Responses of name servers for queries sent to them Commonly used option/features: -f file For batch operation , take domain names (or IP addresses) from ‘file -p port Interact with a name server at ‘port’ instead of the default port 53 CIT 140: Introduction to IT 28

Dig Example > dig www. google. com ; <<>> Di. G 8. 3 <<>> www. google. com ; ; res options: init recurs defnam dnsrch ; ; got answer: ; ; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 2 ; ; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 5, ADDITIONAL: 0 ; ; QUERY SECTION: ; ; www. google. com, type = A, class = IN ; ; ANSWER SECTION: www. google. com. 14 m 40 s IN CNAME www. l. google. com. 4 m 40 s IN A 72. 14. 203. 104 www. l. google. com. 4 m 40 s IN A 72. 14. 203. 99 CIT 140: Introduction to IT 29

Data Link Layer Break up transmission into small enough packets (often called frames) and send them sequentially. Traffic regulation: ensure fast transmitter doesn’t overwhelm slow receiver. CIT 140: Introduction to IT 30

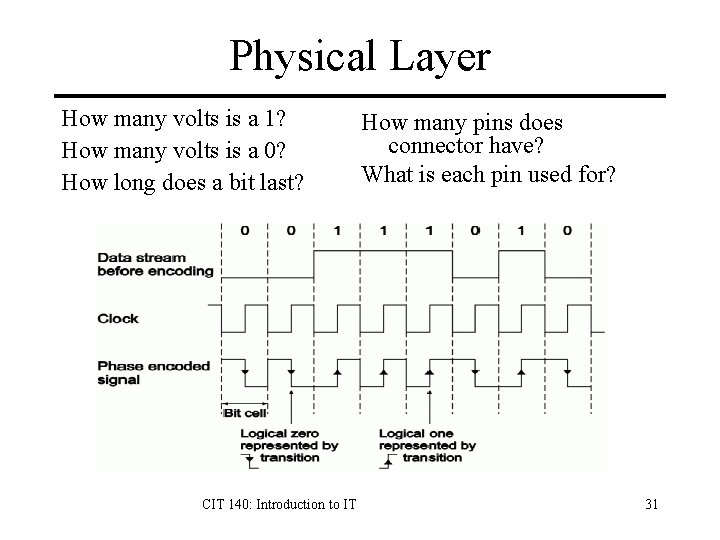
Physical Layer How many volts is a 1? How many volts is a 0? How long does a bit last? CIT 140: Introduction to IT How many pins does connector have? What is each pin used for? 31

Internet Standards IETF (Internet Engineering Task Force) – Open group responsible for Internet standards. RFC (Request for Comments) – Internet standard documents. – IETF archives RFCs at www. ietf. org. IANA (Internet Assigned Numbers Authority) – Coordinates unique network numbers. – IP addresses, protocol numbers, etc. ICANN (Inet. Corp. for Assigned Names & Numbers) – Manages DNS top level domains (TLDs) like. com, . gov – Gives domain registrars responsibilities over domains. CIT 140: Introduction to IT 32

History of Internet 1969 ARPAnet created (4 hosts) 1984 DNS deployed 1986 Cleveland Freenet offers free Internet access 1987 Number of hosts reaches 10, 000 1988 Morris Worm 1989 Number of hosts reaches 100, 000 1990 First commercial dialup ISP 1991 WWW released at CERN 1992 Number of hosts reaches 1, 000 1993 Mosaic, graphical web browser, released 1994 First banner ads appear on the web 1995 AOL offers Internet access 1996 Telcos try to ban Internet telephones 1996 Number of hosts reaches 10, 000 2000 Number of hosts reaches 100, 000 CIT 140: Introduction to IT 33

Displaying the Hostname > hostname zappa > uname -n zappa > uname -a Sun. OS zappa 5. 9 Generic_112233 -07 sun 4 u sparc SUNW, Ultra-250 CIT 140: Introduction to IT 34
![Testing a Network Connection ping options hostname Purpose Send packet to hostname If hostname Testing a Network Connection ping [options] hostname Purpose: Send packet to hostname. If hostname](https://slidetodoc.com/presentation_image/9b5a5891cf299f784ce104dc8938080b/image-35.jpg)
Testing a Network Connection ping [options] hostname Purpose: Send packet to hostname. If hostname is up, packet is echo’ed back and ping records that host is alive. Commonly used options/features: -s Send one packet/second and record latency statistics. CIT 140: Introduction to IT 35

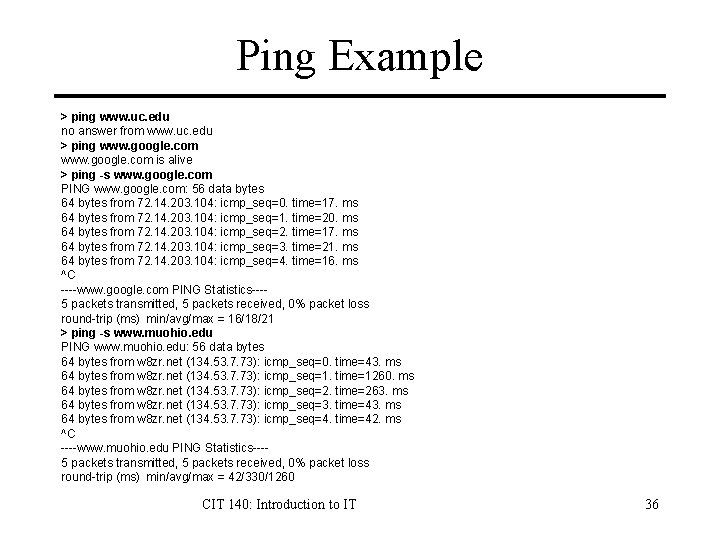
Ping Example > ping www. uc. edu no answer from www. uc. edu > ping www. google. com is alive > ping -s www. google. com PING www. google. com: 56 data bytes 64 bytes from 72. 14. 203. 104: icmp_seq=0. time=17. ms 64 bytes from 72. 14. 203. 104: icmp_seq=1. time=20. ms 64 bytes from 72. 14. 203. 104: icmp_seq=2. time=17. ms 64 bytes from 72. 14. 203. 104: icmp_seq=3. time=21. ms 64 bytes from 72. 14. 203. 104: icmp_seq=4. time=16. ms ^C ----www. google. com PING Statistics---5 packets transmitted, 5 packets received, 0% packet loss round-trip (ms) min/avg/max = 16/18/21 > ping -s www. muohio. edu PING www. muohio. edu: 56 data bytes 64 bytes from w 8 zr. net (134. 53. 7. 73): icmp_seq=0. time=43. ms 64 bytes from w 8 zr. net (134. 53. 7. 73): icmp_seq=1. time=1260. ms 64 bytes from w 8 zr. net (134. 53. 7. 73): icmp_seq=2. time=263. ms 64 bytes from w 8 zr. net (134. 53. 7. 73): icmp_seq=3. time=43. ms 64 bytes from w 8 zr. net (134. 53. 7. 73): icmp_seq=4. time=42. ms ^C ----www. muohio. edu PING Statistics---5 packets transmitted, 5 packets received, 0% packet loss round-trip (ms) min/avg/max = 42/330/1260 CIT 140: Introduction to IT 36

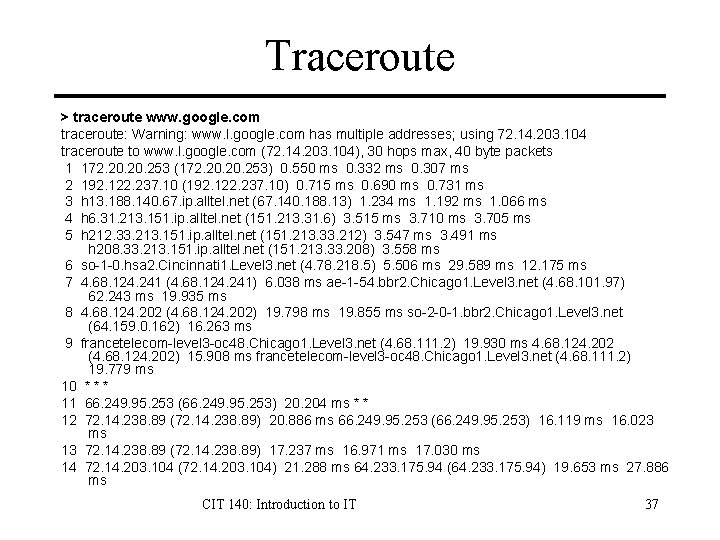
Traceroute > traceroute www. google. com traceroute: Warning: www. l. google. com has multiple addresses; using 72. 14. 203. 104 traceroute to www. l. google. com (72. 14. 203. 104), 30 hops max, 40 byte packets 1 172. 20. 253 (172. 20. 253) 0. 550 ms 0. 332 ms 0. 307 ms 2 192. 122. 237. 10 (192. 122. 237. 10) 0. 715 ms 0. 690 ms 0. 731 ms 3 h 13. 188. 140. 67. ip. alltel. net (67. 140. 188. 13) 1. 234 ms 1. 192 ms 1. 066 ms 4 h 6. 31. 213. 151. ip. alltel. net (151. 213. 31. 6) 3. 515 ms 3. 710 ms 3. 705 ms 5 h 212. 33. 213. 151. ip. alltel. net (151. 213. 33. 212) 3. 547 ms 3. 491 ms h 208. 33. 213. 151. ip. alltel. net (151. 213. 33. 208) 3. 558 ms 6 so-1 -0. hsa 2. Cincinnati 1. Level 3. net (4. 78. 218. 5) 5. 506 ms 29. 589 ms 12. 175 ms 7 4. 68. 124. 241 (4. 68. 124. 241) 6. 038 ms ae-1 -54. bbr 2. Chicago 1. Level 3. net (4. 68. 101. 97) 62. 243 ms 19. 935 ms 8 4. 68. 124. 202 (4. 68. 124. 202) 19. 798 ms 19. 855 ms so-2 -0 -1. bbr 2. Chicago 1. Level 3. net (64. 159. 0. 162) 16. 263 ms 9 francetelecom-level 3 -oc 48. Chicago 1. Level 3. net (4. 68. 111. 2) 19. 930 ms 4. 68. 124. 202 (4. 68. 124. 202) 15. 908 ms francetelecom-level 3 -oc 48. Chicago 1. Level 3. net (4. 68. 111. 2) 19. 779 ms 10 * * * 11 66. 249. 95. 253 (66. 249. 95. 253) 20. 204 ms * * 12 72. 14. 238. 89 (72. 14. 238. 89) 20. 886 ms 66. 249. 95. 253 (66. 249. 95. 253) 16. 119 ms 16. 023 ms 13 72. 14. 238. 89 (72. 14. 238. 89) 17. 237 ms 16. 971 ms 17. 030 ms 14 72. 14. 203. 104 (72. 14. 203. 104) 21. 288 ms 64. 233. 175. 94 (64. 233. 175. 94) 19. 653 ms 27. 886 ms CIT 140: Introduction to IT 37
![Displaying User Information finger options userlist Purpose Display information about the users in the Displaying User Information finger [options] [user_list] Purpose: Display information about the users in the](https://slidetodoc.com/presentation_image/9b5a5891cf299f784ce104dc8938080b/image-38.jpg)
Displaying User Information finger [options] [user_list] Purpose: Display information about the users in the ‘user_list’; without a ‘user_list’, the command displays a short status report about all the users currently logged on to the specified hosts Output: User information extracted from the ~/. project and ~/. plan files Commonly used options/features: -m Match ‘user_list’ to login names only -s Display output in a short format. CIT 140: Introduction to IT 38

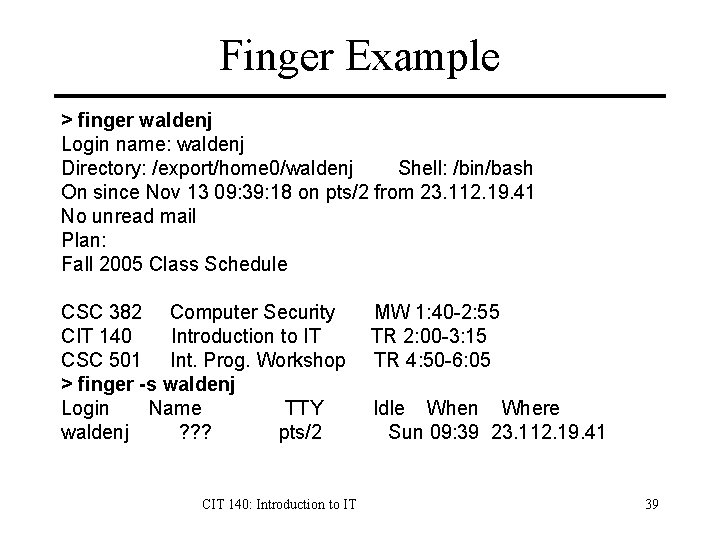
Finger Example > finger waldenj Login name: waldenj Directory: /export/home 0/waldenj Shell: /bin/bash On since Nov 13 09: 39: 18 on pts/2 from 23. 112. 19. 41 No unread mail Plan: Fall 2005 Class Schedule CSC 382 Computer Security CIT 140 Introduction to IT CSC 501 Int. Prog. Workshop > finger -s waldenj Login Name TTY waldenj ? ? ? pts/2 CIT 140: Introduction to IT MW 1: 40 -2: 55 TR 2: 00 -3: 15 TR 4: 50 -6: 05 Idle When Where Sun 09: 39 23. 112. 19. 41 39
![Remote Login telnet Obsolete telnet host port Purpose Obsolete insecure protocol for logging into Remote Login: telnet (Obsolete) telnet host [port] Purpose: Obsolete, insecure protocol for logging into](https://slidetodoc.com/presentation_image/9b5a5891cf299f784ce104dc8938080b/image-40.jpg)
Remote Login: telnet (Obsolete) telnet host [port] Purpose: Obsolete, insecure protocol for logging into a remote system. Superseded by ssh. Currently used to demonstrate network protocols by connecting to their ports, as we did for HTTP earlier. Ports for common protocols are listed in the file /etc/services. CIT 140: Introduction to IT 40

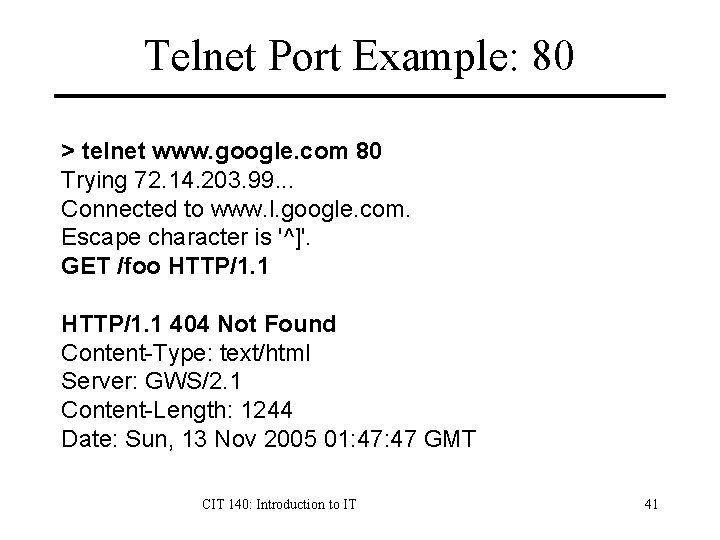
Telnet Port Example: 80 > telnet www. google. com 80 Trying 72. 14. 203. 99. . . Connected to www. l. google. com. Escape character is '^]'. GET /foo HTTP/1. 1 404 Not Found Content-Type: text/html Server: GWS/2. 1 Content-Length: 1244 Date: Sun, 13 Nov 2005 01: 47 GMT CIT 140: Introduction to IT 41
![Remote Login ssh options host command ssh options userhost command Purpose Secure login to Remote Login: ssh [options] host [command] ssh [options] user@host [command] Purpose: Secure login to](https://slidetodoc.com/presentation_image/9b5a5891cf299f784ce104dc8938080b/image-42.jpg)
Remote Login: ssh [options] host [command] ssh [options] user@host [command] Purpose: Secure login to remote host. Commonly used options/features: -l user Login as specified username. -p port Specifies remote port to connect to -v Verbose output CIT 140: Introduction to IT 42

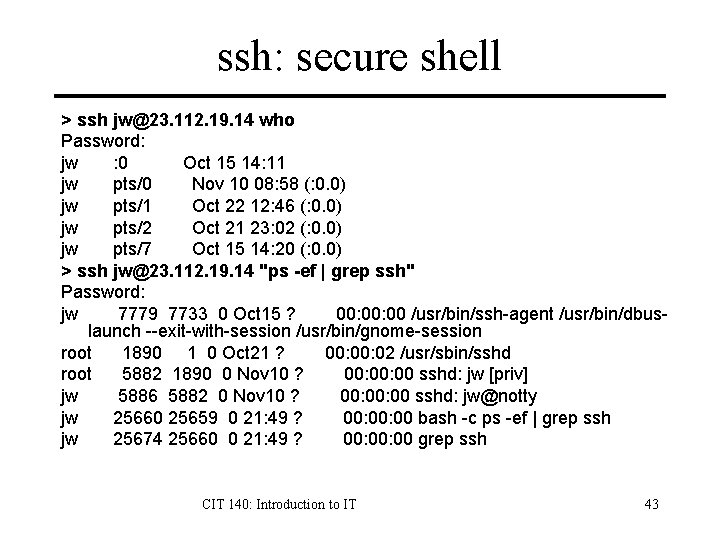
ssh: secure shell > ssh jw@23. 112. 19. 14 who Password: jw : 0 Oct 15 14: 11 jw pts/0 Nov 10 08: 58 (: 0. 0) jw pts/1 Oct 22 12: 46 (: 0. 0) jw pts/2 Oct 21 23: 02 (: 0. 0) jw pts/7 Oct 15 14: 20 (: 0. 0) > ssh jw@23. 112. 19. 14 "ps -ef | grep ssh" Password: jw 7779 7733 0 Oct 15 ? 00: 00 /usr/bin/ssh-agent /usr/bin/dbuslaunch --exit-with-session /usr/bin/gnome-session root 1890 1 0 Oct 21 ? 00: 02 /usr/sbin/sshd root 5882 1890 0 Nov 10 ? 00: 00 sshd: jw [priv] jw 5886 5882 0 Nov 10 ? 00: 00 sshd: jw@notty jw 25660 25659 0 21: 49 ? 00: 00 bash -c ps -ef | grep ssh jw 25674 25660 0 21: 49 ? 00: 00 grep ssh CIT 140: Introduction to IT 43

The scp Command Securely copy files from machine to machine across the network > scp prog. c zappa. nku. edu: ~/classes/cit 140/programs/ Password: > scp -r zappa. nku. edu: classeses. Password: CIT 140: Introduction to IT 44

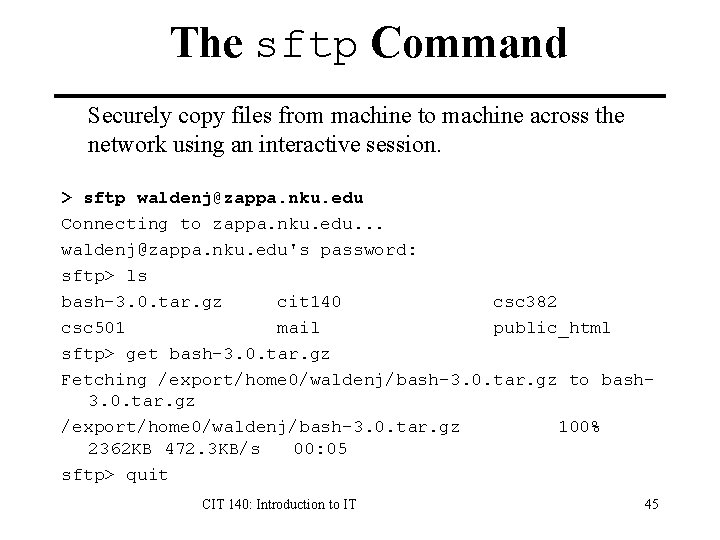
The sftp Command Securely copy files from machine to machine across the network using an interactive session. > sftp waldenj@zappa. nku. edu Connecting to zappa. nku. edu. . . waldenj@zappa. nku. edu's password: sftp> ls bash-3. 0. tar. gz cit 140 csc 382 csc 501 mail public_html sftp> get bash-3. 0. tar. gz Fetching /export/home 0/waldenj/bash-3. 0. tar. gz to bash 3. 0. tar. gz /export/home 0/waldenj/bash-3. 0. tar. gz 100% 2362 KB 472. 3 KB/s 00: 05 sftp> quit CIT 140: Introduction to IT 45
![File Transfer ftp options host Purpose To transfer files from or to a remote File Transfer ftp [options] [host] Purpose: To transfer files from or to a remote](https://slidetodoc.com/presentation_image/9b5a5891cf299f784ce104dc8938080b/image-46.jpg)
File Transfer ftp [options] [host] Purpose: To transfer files from or to a remote machine. Commonly used options/features -d Enable debugging -i Disable prompting during transfers of multiple files -v Show all remote responses CIT 140: Introduction to IT 46

FTP Example > ftp. gnu. org Connected to ftp. gnu. org. 220 GNU FTP server ready. Name (ftp. gnu. org: waldenj): ftp 230 -Due to U. S. Export Regulations, all cryptographic software on this 230 -site is subject to the following legal notice: 230 Login successful. Remote system type is UNIX. Using binary mode to transfer files. ftp> cd gnu/bash 250 Directory successfully changed. ftp> dir bash-3. 0* 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. drwxr-xr-x 2 1003 4096 Feb 14 2005 bash-3. 0 -patches -rw-r--r-- 1 1003 65534 2418293 Aug 03 2004 bash-3. 0. tar. gz -rw-r--r-- 1 1003 65534 65 Aug 03 2004 bash-3. 0. tar. gz. sig 226 Directory send OK. remote: bash-3. 0* 224 bytes received in 0. 0074 seconds (29. 39 Kbytes/s) CIT 140: Introduction to IT 47

Automating Ftp > wget ftp: //ftp. gnu. org/gnu/bash-3. 0. tar. gz --21: 42: 24 -- ftp: //ftp. gnu. org/gnu/bash-3. 0. tar. gz => `bash-3. 0. tar. gz' Resolving ftp. gnu. org. . . done. Connecting to ftp. gnu. org[199. 232. 41. 7]: 21. . . connected. Logging in as anonymous. . . Logged in! ==> SYST. . . done. ==> PWD. . . done. ==> TYPE I. . . done. ==> CWD /gnu/bash. . . done. ==> PORT. . . done. ==> RETR bash-3. 0. tar. gz. . . done. Length: 2, 418, 293 (unauthoritative) 100%[==================>] 2, 418, 293 579. 54 K/s ETA 00: 00 21: 42: 29 (579. 54 KB/s) - `bash-3. 0. tar. gz' saved [2418293] CIT 140: Introduction to IT 48

Automating Web Transfers > wget http: //greenend. org. uk/~sgtatham/putty/latest/x 86/putty. exe --21: 44: 51 --http: //greenend. org. uk/~sgtatham/putty/latest/x 86/putty. exe => `putty. exe' Location: http: //the. earth. li/~sgtatham/putty/0. 58/x 86/putty. exe [following] --21: 44: 52 -- http: //the. earth. li/%7 Esgtatham/putty/0. 58/x 86/putty. exe => `putty. exe' Connecting to the. earth. li[193. 201. 200. 66]: 80. . . connected. HTTP request sent, awaiting response. . . 200 OK Length: 421, 888 [application/x-msdos-program] 100%[==================>] 421, 888 307. 46 K/s ETA 00: 00 21: 44: 54 (307. 46 KB/s) - `putty. exe' saved [421888/421888] CIT 140: Introduction to IT 49

Interactive Chat talk user Purpose: to initiate interactive chat with user who is logged in on a specific terminal > talk bob [Waiting for your party to respond] Message from Talk_Daemon@upibm 7. egr. up. edu at 13: 36. . . talk: connection requested by sarwar@upibm 7. egr. up. edu. talk: respond with: talk sarwar@upibm 7. egr. up. edu > talk sarwar@upibm 7 CIT 140: Introduction to IT 50