Chapter 14 LAN Systems Ethernet and Fast Ethernet














- Slides: 47

Chapter 14. LAN Systems • Ethernet and Fast Ethernet (CSMA/CD) • Token Ring and FDDI • 100 VG-Any. LAN • ATM LANs • Wireless LANs 1

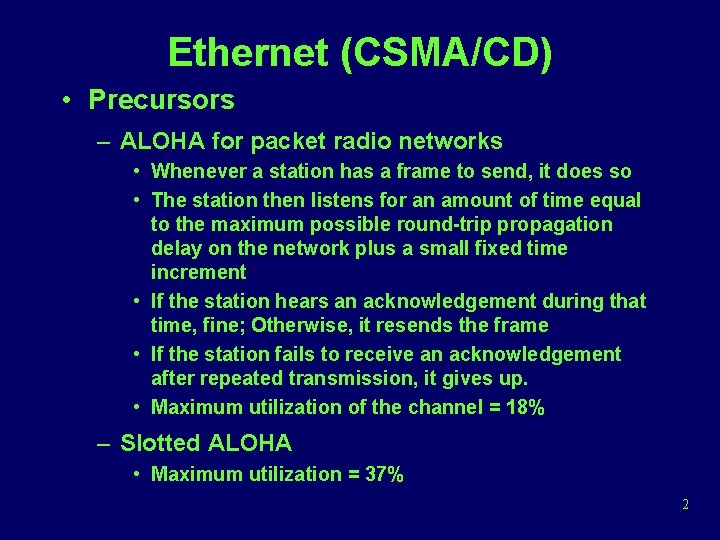
Ethernet (CSMA/CD) • Precursors – ALOHA for packet radio networks • Whenever a station has a frame to send, it does so • The station then listens for an amount of time equal to the maximum possible round-trip propagation delay on the network plus a small fixed time increment • If the station hears an acknowledgement during that time, fine; Otherwise, it resends the frame • If the station fails to receive an acknowledgement after repeated transmission, it gives up. • Maximum utilization of the channel = 18% – Slotted ALOHA • Maximum utilization = 37% 2

CSMA • If a station wishing to transmit – first listens to the medium to determine if another transmission is in progress (carrier sense) – If the medium is in use, the station must wait – If the medium is idle, the station may transmit – If two or more stations attempt to transmit at about the same time, there will be a collision – To account for the collision, a station waits a reasonable amount of time, after transmitting, for an acknowledgement. If no ack. , wait a random amount of time, then retransmit 3

CSMA (cont) • 1 -persistent – used in IEEE 802. 3 – A station wishing to transmit listens to the medium – If the medium is idle, transmit – If the medium is busy, continue to listen until the channel is sensed idle; then transmit immediately 4

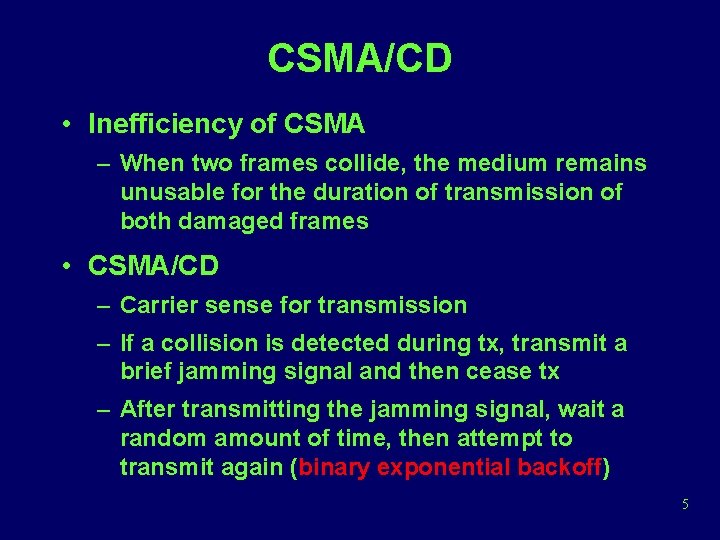
CSMA/CD • Inefficiency of CSMA – When two frames collide, the medium remains unusable for the duration of transmission of both damaged frames • CSMA/CD – Carrier sense for transmission – If a collision is detected during tx, transmit a brief jamming signal and then cease tx – After transmitting the jamming signal, wait a random amount of time, then attempt to transmit again (binary exponential backoff) 5

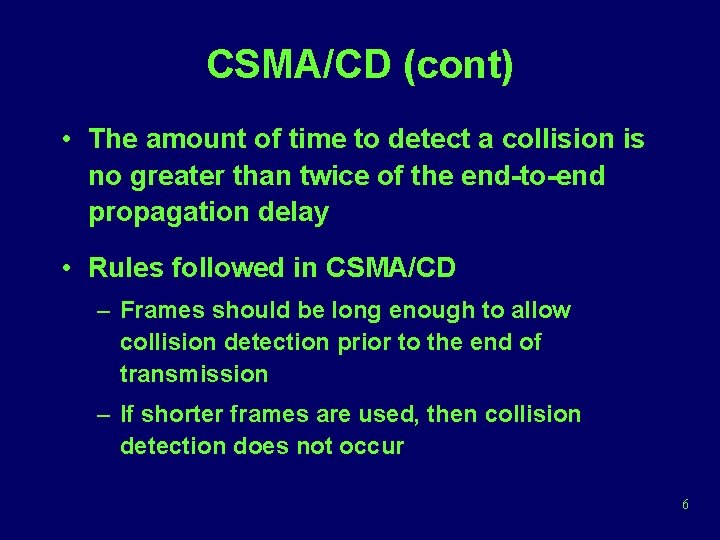
CSMA/CD (cont) • The amount of time to detect a collision is no greater than twice of the end-to-end propagation delay • Rules followed in CSMA/CD – Frames should be long enough to allow collision detection prior to the end of transmission – If shorter frames are used, then collision detection does not occur 6

CSMA/CD (ref. ) • Minimal frame size for 10 BASE 5, 10 Mbps – Typical electromagnetic wave’s speed in coaxial cable = 2. 5 x 108 m/s (table 4. 1 in textbook) – Maximum segment length = 500 m, a maximum of four repeaters length of medium = 2500 m – Minimal Ethernet frame size = 7

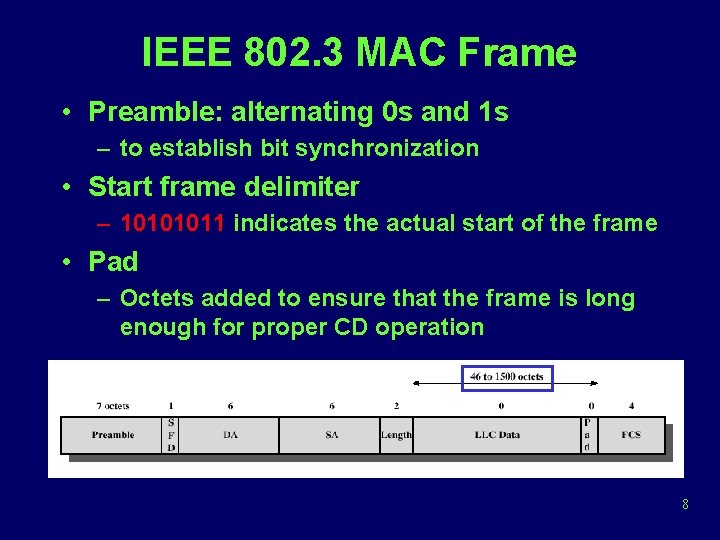
IEEE 802. 3 MAC Frame • Preamble: alternating 0 s and 1 s – to establish bit synchronization • Start frame delimiter – 10101011 indicates the actual start of the frame • Pad – Octets added to ensure that the frame is long enough for proper CD operation 8

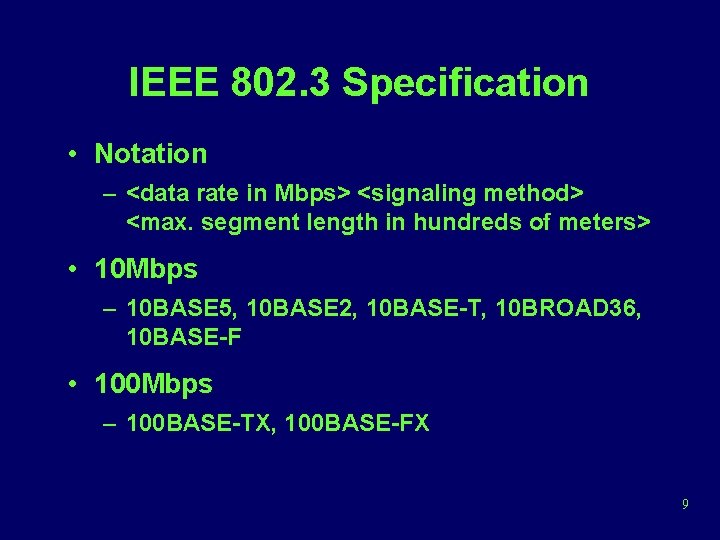
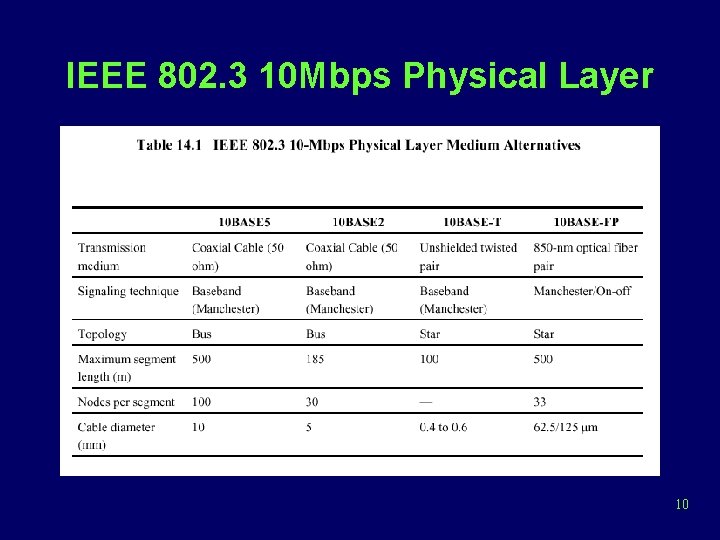
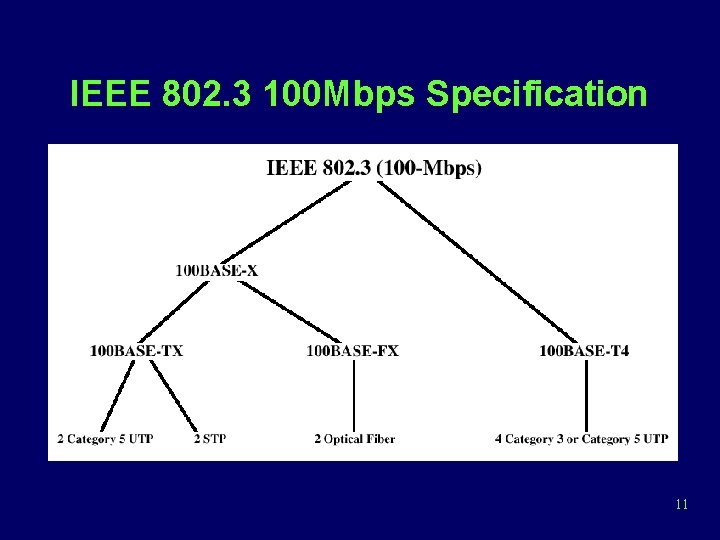
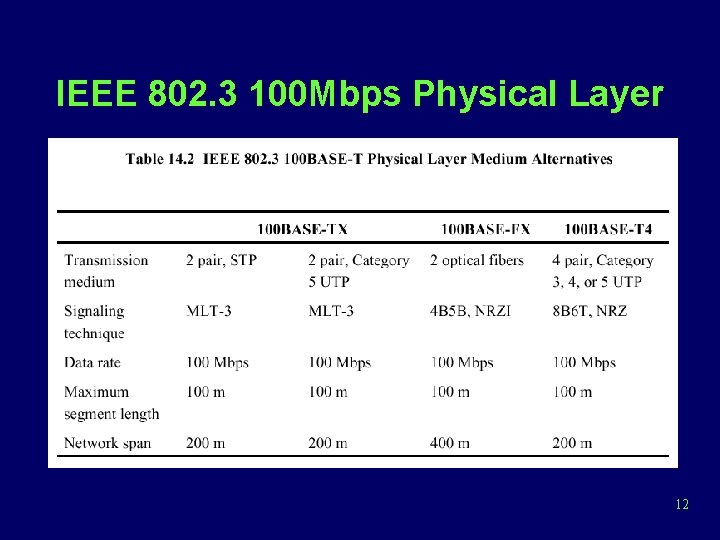
IEEE 802. 3 Specification • Notation – <data rate in Mbps> <signaling method> <max. segment length in hundreds of meters> • 10 Mbps – 10 BASE 5, 10 BASE 2, 10 BASE-T, 10 BROAD 36, 10 BASE-F • 100 Mbps – 100 BASE-TX, 100 BASE-FX 9

IEEE 802. 3 10 Mbps Physical Layer 10

IEEE 802. 3 100 Mbps Specification 11

IEEE 802. 3 100 Mbps Physical Layer 12

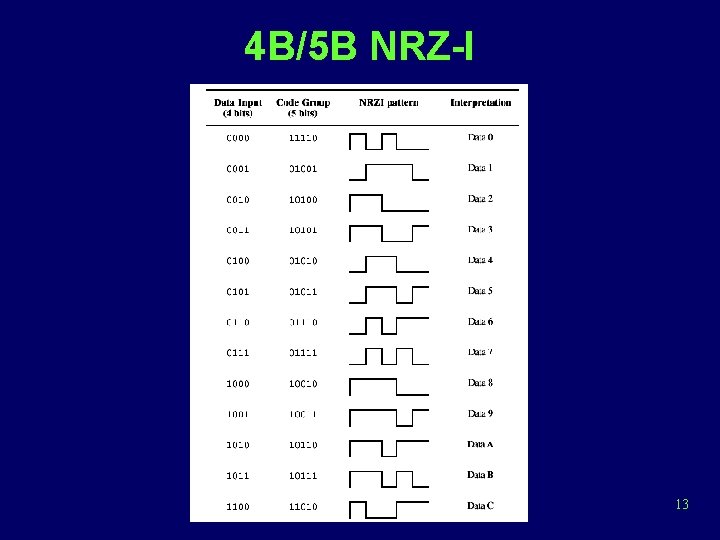
4 B/5 B NRZ-I 13

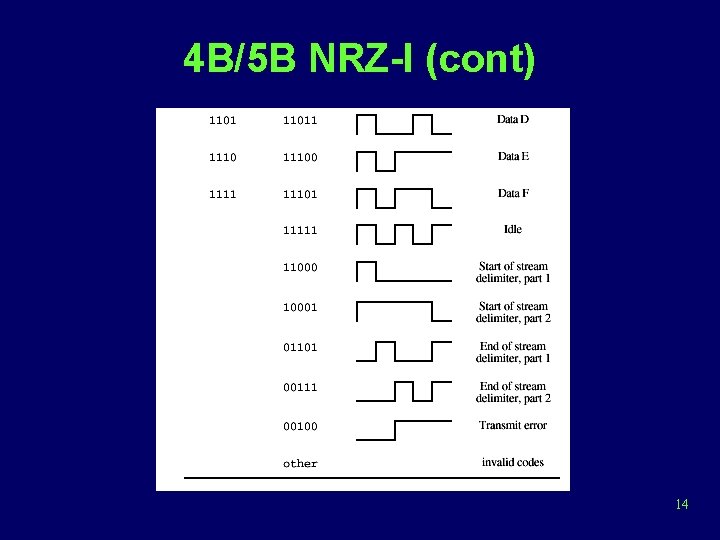
4 B/5 B NRZ-I (cont) 14

Gigabit Ethernet • Media Access Layer – Two enhancements to CSMA/CD – 1. Carrier extension • The minimum 512 bit-times (64 octets) for 10/100 Mbps 4096 bit-times (512 octets) – 2. Frame bursting • Allows for multiple short frames to be transmitted consecutively • Physical Layer – 1000 BASE-SX, -LX, -CX, -T – Signal encoding scheme: 8 B/10 B 15

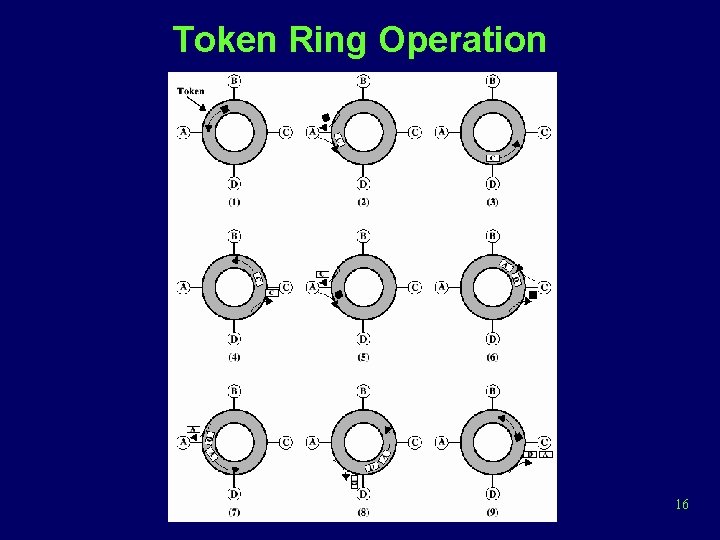
Token Ring Operation 16

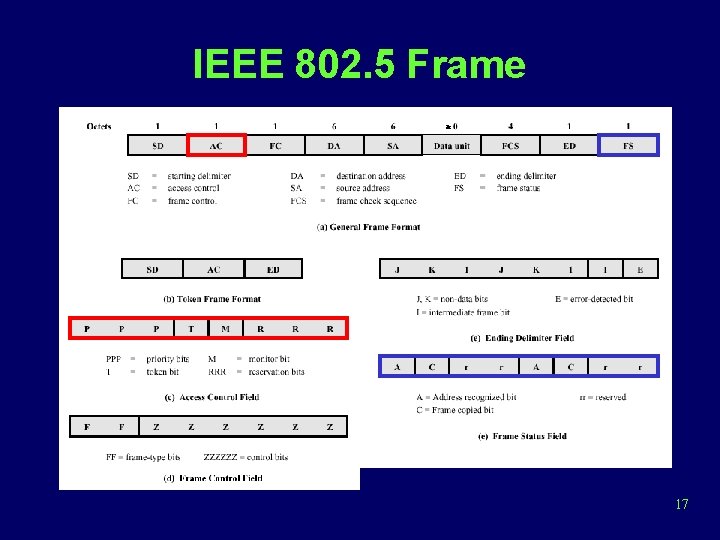
IEEE 802. 5 Frame 17

IEEE 802. 5 Frame (cont) • Ending delimiter field – E bit: each station checks passing frames for errors and set the E bit to 1 • Frame status field – Destination nonexistent or not active: A=0, C=0 – Destination exists but frame not copied: A=1, C=0 – Frame received: A=1, C=1 18

A D D Token Ring Priority Scheme B A B E E C • A is sending to B • D makes a Higher priority level reservation C • A generates a higher priority token and remembers preempting lower priority 19

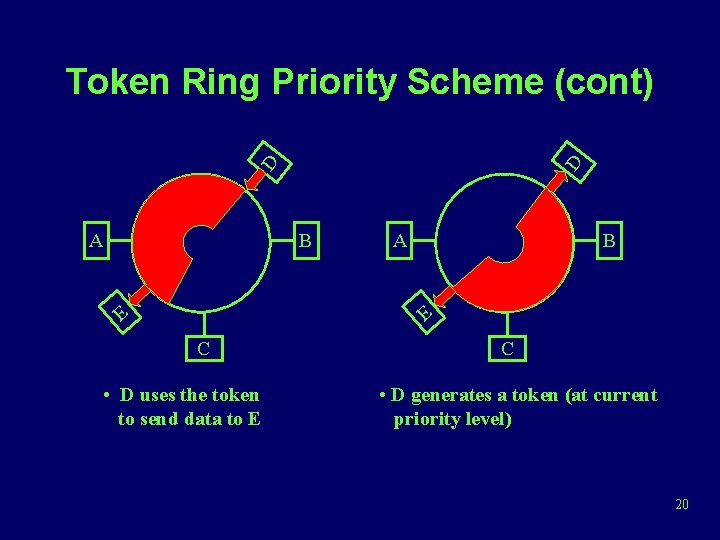
A D D Token Ring Priority Scheme (cont) B A B E E C • D uses the token to send data to E C • D generates a token (at current priority level) 20

Hi-pri free token A D D Token Ring Priority Scheme (cont) B A B E E C • A sees the high priority token C • A generates a token at the preempted priority level 21

Updates to Token Ring • Early Token Release (ETR) – Origin: The transmitting station must wait until the leading edge of the frame returns before issuing a token – ETR: Allows a transmitting station to release a token as soon as it completes frame transmission • Dedicated Token Ring (DTR) Token Ring switch – Define the use of stations and concentrators in the switched mode – Each link from concentrator to station is a dedicated link with immediate access possible; token passing is not used 22

IEEE 802. 5 Physical Layer 23

Disadvantage of Token Ring • Requirement for token maintenance – Loss of the token prevents further utilization of the ring – Duplication of the token can disrupt ring operation – One station must be selected as a monitor to ensure that exactly one token is on the ring and to ensure that a free token is reinserted, if necessary 24

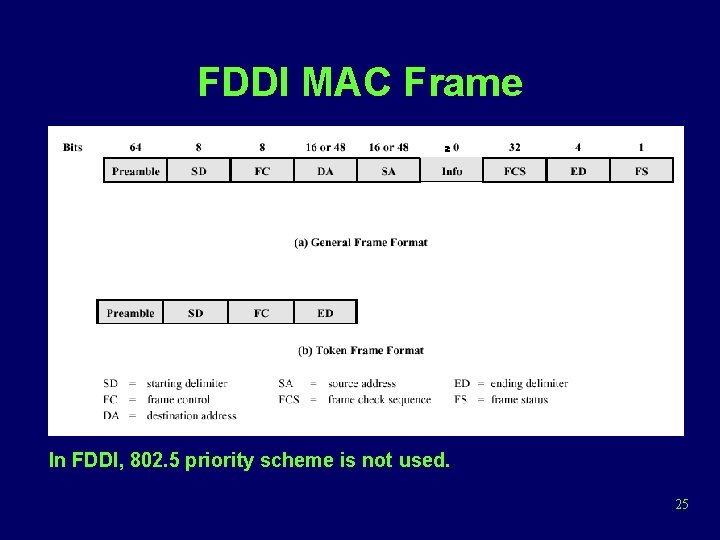
FDDI MAC Frame In FDDI, 802. 5 priority scheme is not used. 25

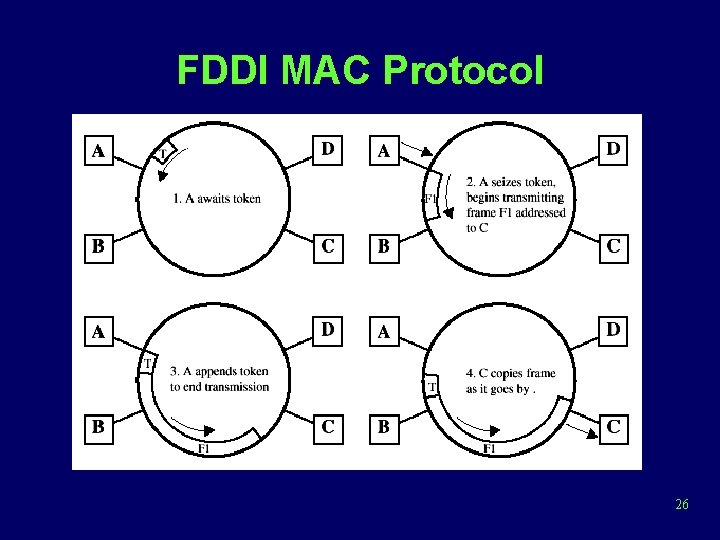
FDDI MAC Protocol 26

FDDI MAC Protocol (cont) 27

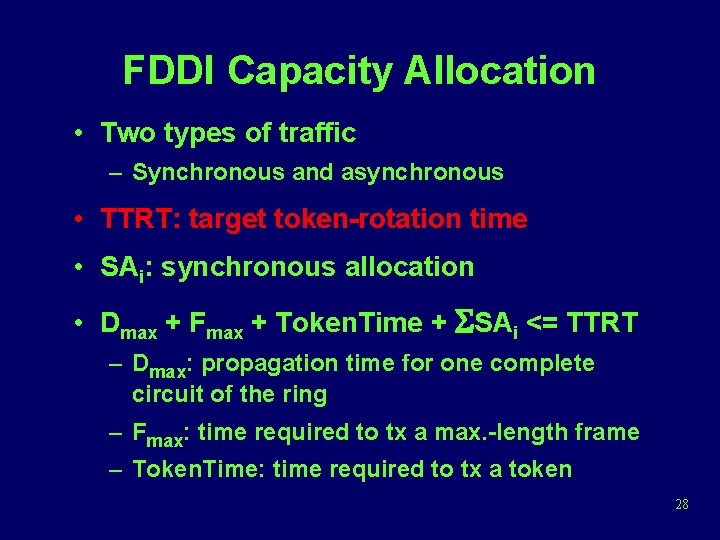
FDDI Capacity Allocation • Two types of traffic – Synchronous and asynchronous • TTRT: target token-rotation time • SAi: synchronous allocation • Dmax + Fmax + Token. Time + SSAi <= TTRT – Dmax: propagation time for one complete circuit of the ring – Fmax: time required to tx a max. -length frame – Token. Time: time required to tx a token 28

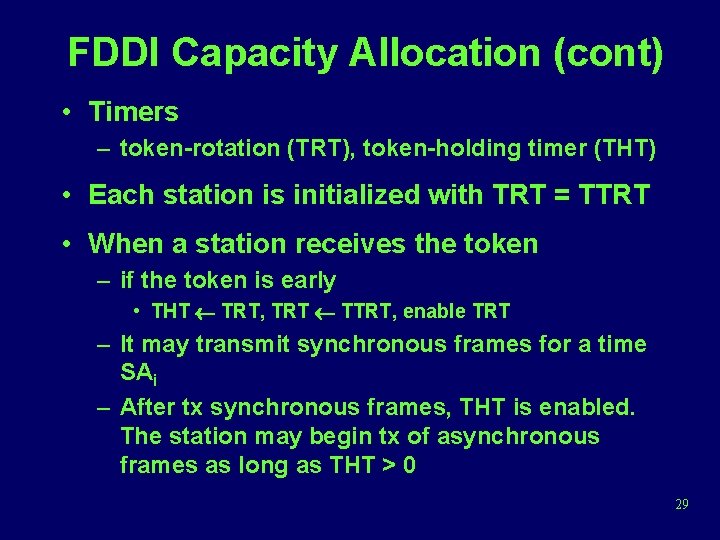
FDDI Capacity Allocation (cont) • Timers – token-rotation (TRT), token-holding timer (THT) • Each station is initialized with TRT = TTRT • When a station receives the token – if the token is early • THT TRT, TRT TTRT, enable TRT – It may transmit synchronous frames for a time SAi – After tx synchronous frames, THT is enabled. The station may begin tx of asynchronous frames as long as THT > 0 29

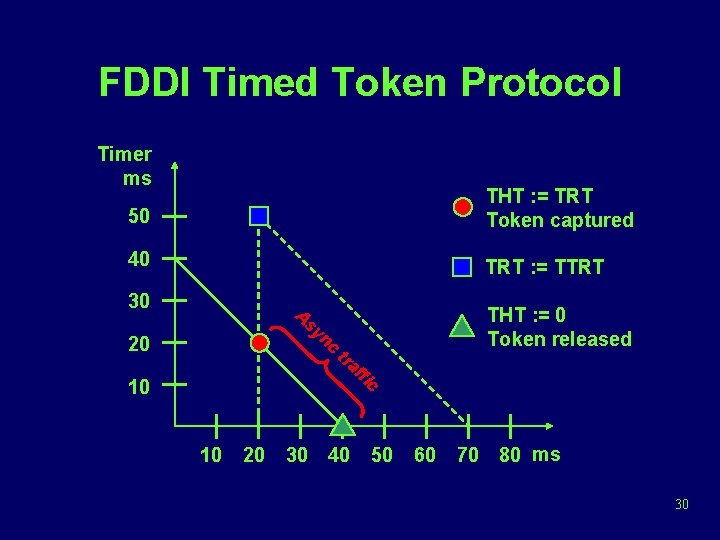
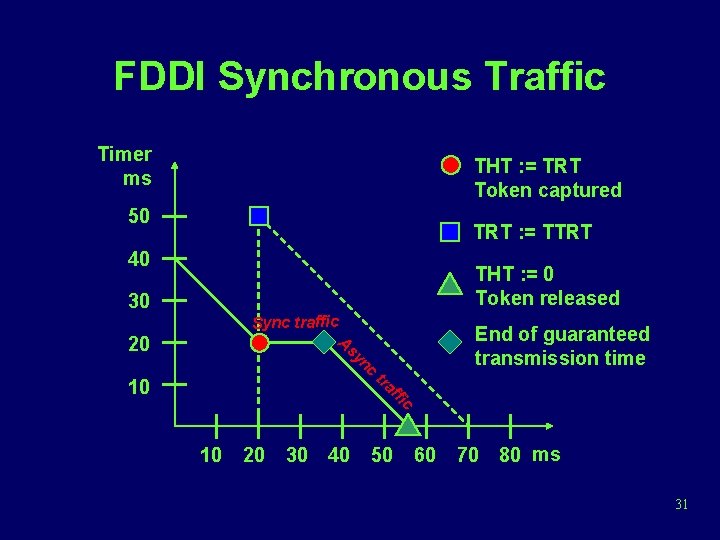
FDDI Timed Token Protocol Timer ms 50 THT : = TRT Token captured 40 TRT : = TTRT 30 A nc 20 THT : = 0 Token released sy tr a ffi 10 10 20 30 40 c 50 60 70 80 ms 30

FDDI Synchronous Traffic Timer ms THT : = TRT Token captured 50 TRT : = TTRT 40 THT : = 0 Token released 30 Sync traffic A 20 End of guaranteed transmission time sy nc 10 10 20 30 40 tr af 50 fic 60 70 80 ms 31

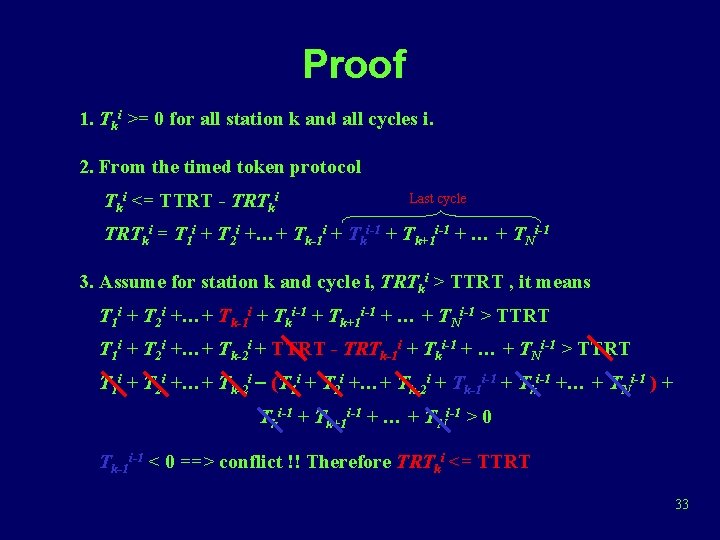
Property of Timed Token Protocol • Each station will get access at least once within the pre-configured TTRT (no SA) Assume Tki : Tx time of station k for ith captured token TRTki : ith observed token rotation time for station k Prove that TRTki <= TTRT for all stations k 1 2 N Station k 32

Proof 1. Tki >= 0 for all station k and all cycles i. 2. From the timed token protocol Tki <= TTRT - TRTki Last cycle TRTki = T 1 i + T 2 i +…+ Tk-1 i + Tki-1 + Tk+1 i-1 + … + TNi-1 3. Assume for station k and cycle i, TRTki > TTRT , it means T 1 i + T 2 i +…+ Tk-1 i + Tki-1 + Tk+1 i-1 + … + TNi-1 > TTRT T 1 i + T 2 i +…+ Tk-2 i + TTRT - TRTk-1 i + Tki-1 + … + TNi-1 > TTRT T 1 i + T 2 i +…+ Tk-2 i - (T 1 i + T 2 i +…+ Tk-2 i + Tk-1 i-1 + Tki-1 +… + TNi-1 ) + Tki-1 + Tk+1 i-1 + … + TNi-1 > 0 Tk-1 i-1 < 0 ==> conflict !! Therefore TRTki <= TTRT 33

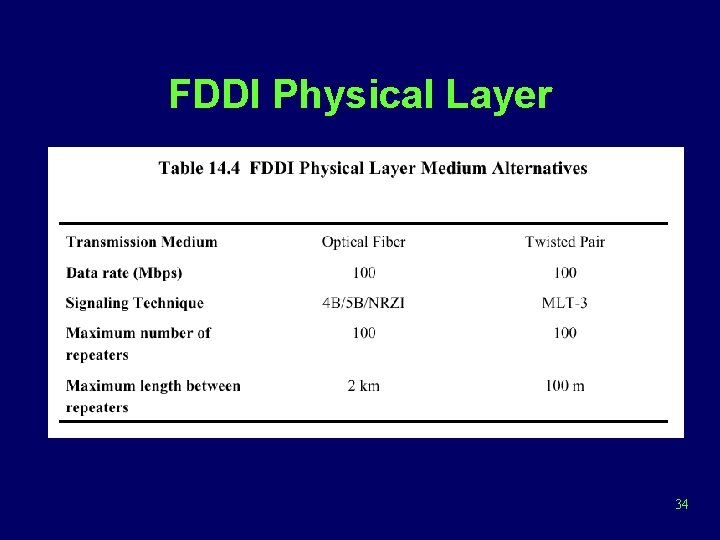
FDDI Physical Layer 34

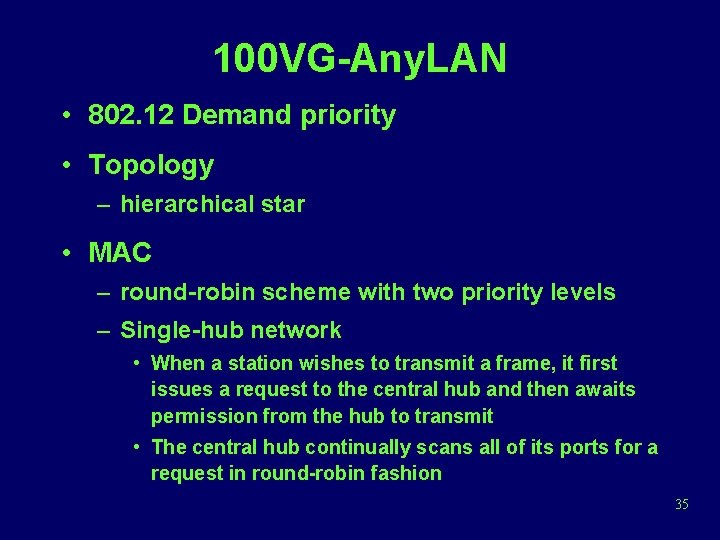
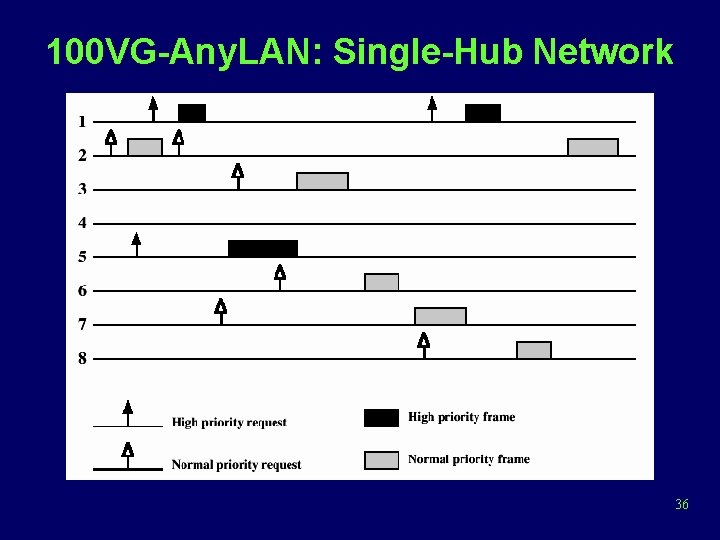
100 VG-Any. LAN • 802. 12 Demand priority • Topology – hierarchical star • MAC – round-robin scheme with two priority levels – Single-hub network • When a station wishes to transmit a frame, it first issues a request to the central hub and then awaits permission from the hub to transmit • The central hub continually scans all of its ports for a request in round-robin fashion 35

100 VG-Any. LAN: Single-Hub Network 36

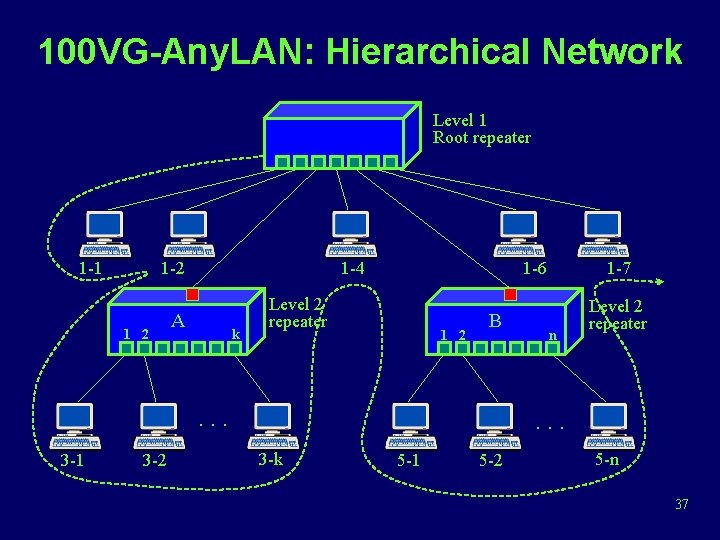
100 VG-Any. LAN: Hierarchical Network Level 1 Root repeater 1 -1 1 -2 1 2 1 -4 A k 1 -6 Level 2 repeater 1 2 B . . . 3 -1 3 -2 1 -7 n Level 2 repeater . . . 3 -k 5 -1 5 -2 5 -n 37

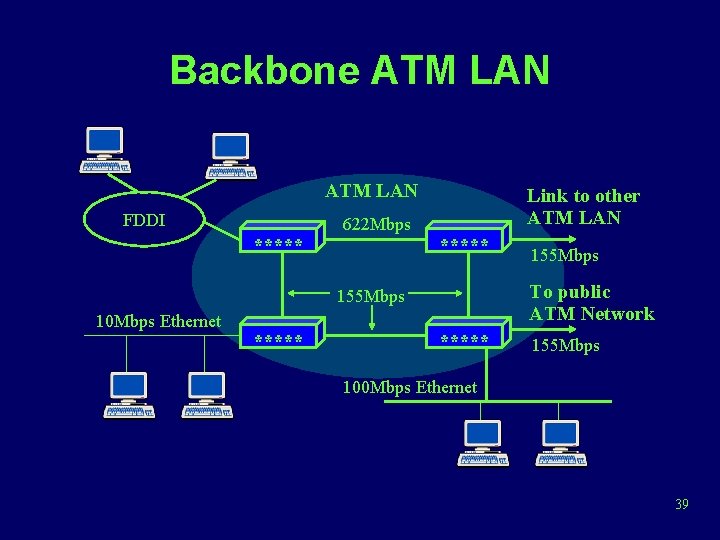
ATM LANs • Gateway to ATM WAN – An ATM switch acts as a router and traffic concentrator for linking a premises network complex to an ATM WAN • Backbone ATM switch – ATM switches interconnect other LANs • Workgroup ATM – End systems connect directly to an ATM switch 38

Backbone ATM LAN FDDI ***** 622 Mbps Link to other ATM LAN ***** To public ATM Network 155 Mbps 10 Mbps Ethernet ***** 155 Mbps 100 Mbps Ethernet 39

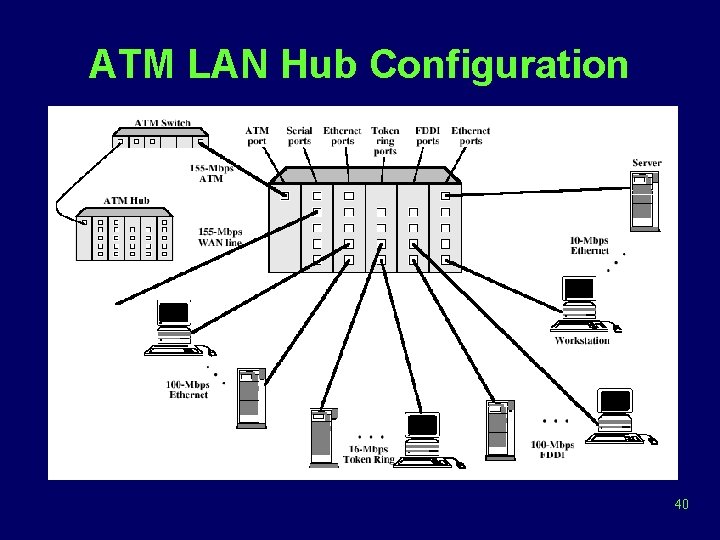
ATM LAN Hub Configuration 40

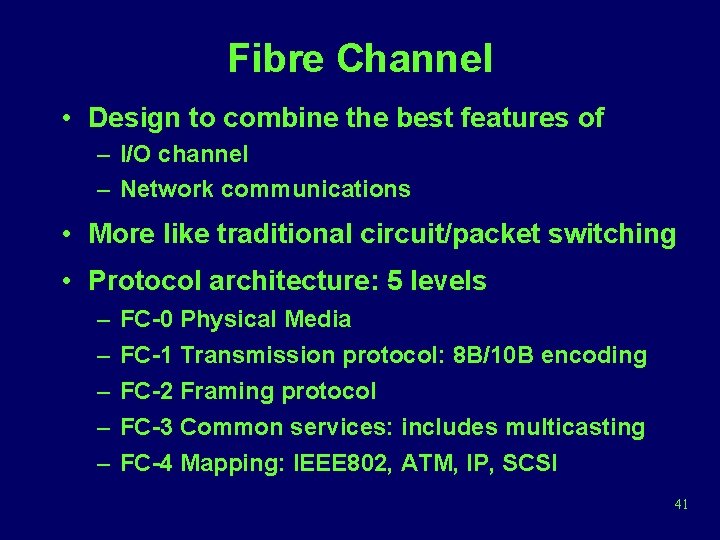
Fibre Channel • Design to combine the best features of – I/O channel – Network communications • More like traditional circuit/packet switching • Protocol architecture: 5 levels – – – FC-0 Physical Media FC-1 Transmission protocol: 8 B/10 B encoding FC-2 Framing protocol FC-3 Common services: includes multicasting FC-4 Mapping: IEEE 802, ATM, IP, SCSI 41

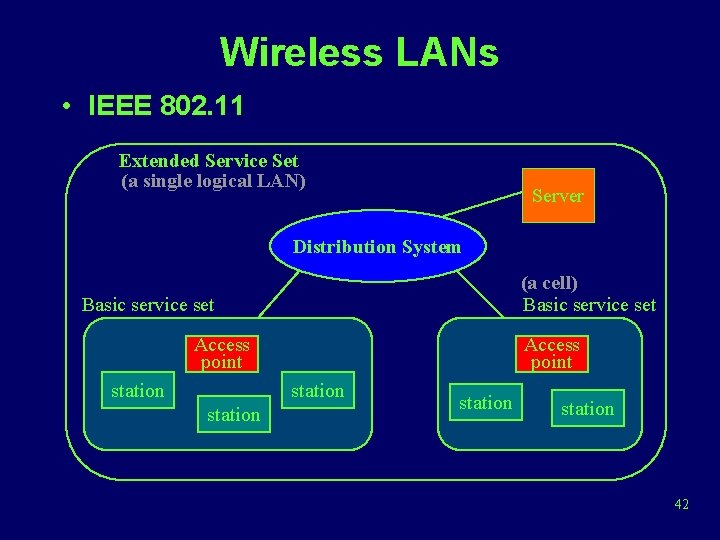
Wireless LANs • IEEE 802. 11 Extended Service Set (a single logical LAN) Server Distribution System (a cell) Basic service set Access point station station 42

Wireless LANs (cont) • Three types of stations – No transition – BSS-transition – ESS-transition • MAC – DFWMAC (distributed foundation wireless MAC) Contention-free service Contention service Point coordination function (PCF) Distributed coordination function (DCF) CSMA-CA Physical Layer 43

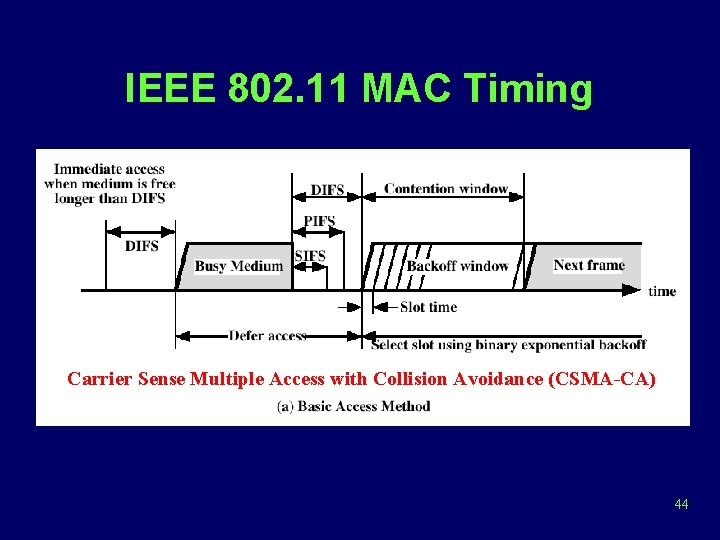
IEEE 802. 11 MAC Timing Carrier Sense Multiple Access with Collision Avoidance (CSMA-CA) 44

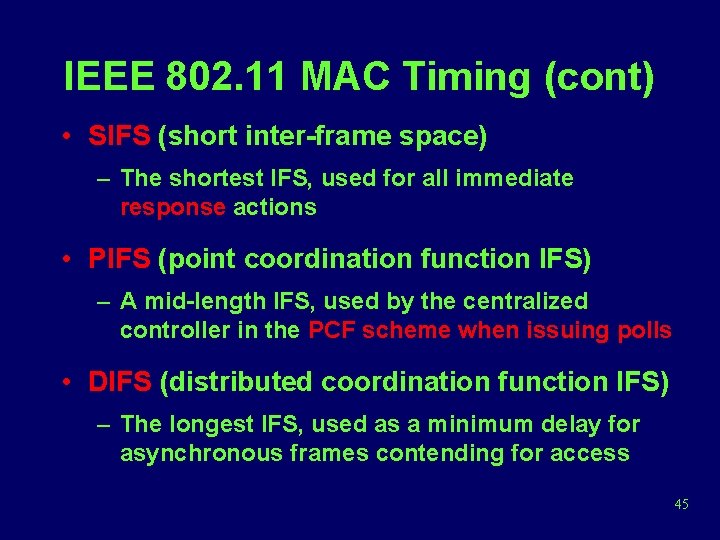
IEEE 802. 11 MAC Timing (cont) • SIFS (short inter-frame space) – The shortest IFS, used for all immediate response actions • PIFS (point coordination function IFS) – A mid-length IFS, used by the centralized controller in the PCF scheme when issuing polls • DIFS (distributed coordination function IFS) – The longest IFS, used as a minimum delay for asynchronous frames contending for access 45

IEEE 802. 11 MAC Timing (cont) • SIFS is used for – Acknowledgment (ACK) • MAC-level ACK provides for efficient collision recovery – Clear to send (CTS) • Sender sends Request to Send (RTS) frame • If receiver is ready to receive, responds with a CTS frame • All other stations defer using the medium until they see a corresponding CTS, or timeout – Poll response • For PCF 46

IEEE 802. 11 MAC Timing (cont) 47