CASE STUDY Addressing NERC CIP Using an Identity








- Slides: 21

CASE STUDY: Addressing NERC CIP Using an Identity and Access Management (IAM) Strategy Slide 1

Your Speakers… g Pete Johnson § Director of Information Assurance, PPL g Frank Villavicencio § Executive Vice President, Identropy Slide 2

What Will be Covered Today… 1. Overview of PPL’s IAM Initiative 2. Creating an IAM Strategy to Address the NERC CIP Standards 3. Lessons Learned 4. Q&A Slide 3

PPL’s Business Drivers Compliance for Logical Access • Driven by multiple regulations: SOX, FERC, and NERC CIP was the latest and most rigorous Slide 4

PPL’s Drivers Relating to NERC CIP standards submitted to FERC in 2006 by NERC, with stiff penalties (up to US $1 M+) per-violation-per-day for non-compliance since 2009 • Compliant by 12/31/2009 • Auditably Compliant by 12/31/2010 We didn’t want to address compliance as a Project, but rather as a Program to address risk Since NERC CIP is a new standard, the evidence auditors require may evolve • We need a solution in place to automate/standardize our ongoing response to any requests to demonstrate compliance Slide 5

We Identified our NERC CIP Critical Cyber Assets, Now What? What we knew: • NERC CIP Critical Cyber Assets • IAM Technologies can help us comply • Business/Tech Owners of Assets • We would achieve compliance, even with manual processes and existing tools • General Direction What we needed help on: • Laying a cohesive IAM strategy for enhanced automation to maintain NERC CIP compliance • Establishing a roadmap for implementation • Identify which IAM technologies are truly needed now • How we can leverage technology we already owned and build upon existing processes • Explore existing corporate policies and update where necessary to match compliance requirements and processes Slide 6

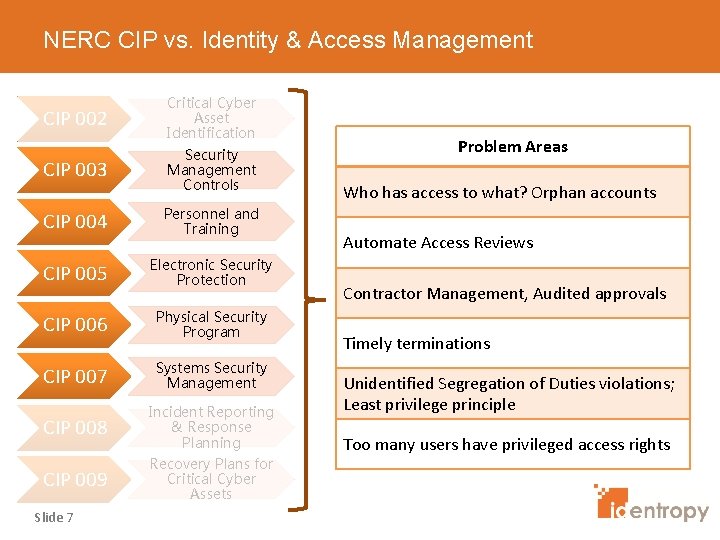
NERC CIP vs. Identity & Access Management CIP 002 Critical Cyber Asset Identification CIP 003 Security Management Controls CIP 004 Personnel and Training CIP 005 Electronic Security Protection CIP 006 Physical Security Program CIP 007 Systems Security Management CIP 008 Incident Reporting & Response Planning CIP 009 Recovery Plans for Critical Cyber Assets Slide 7 Problem Areas Who has access to what? Orphan accounts Automate Access Reviews Contractor Management, Audited approvals Timely terminations Unidentified Segregation of Duties violations; Least privilege principle Too many users have privileged access rights

Polling Question #1 How is your organization achieving NERC CIP compliance today? 1. My organization is not subject to NERC CIP 2. I am unaware of how we are achieving compliance 3. We have a NERC CIP program in place but it is largely manual 4. We are leveraging automation to comply with NERC CIP Slide 8

Identropy at a Glance Advisory Services We provide managed identity enabled solutions to our customers that help them achieve compliance, business development, cost containment and operational reliability, leveraging a unique, proven engagement model. § Strategic Planning § Roadmap Development Implementation Services §Agile-Based Deployment Methodology g Exclusive Focus on Identity & Access Management (IAM) g 3 Lines of Business: Advisory Services, Implementation, Managed Services g IAM Experts with hands-on experience in over 80 successful implementations in the last 4 years. g Full Range of Services to Support Full Solution Lifecycle Slide 9 Managed Services § Co-Sourced Post. Deployment Maintenance and Support

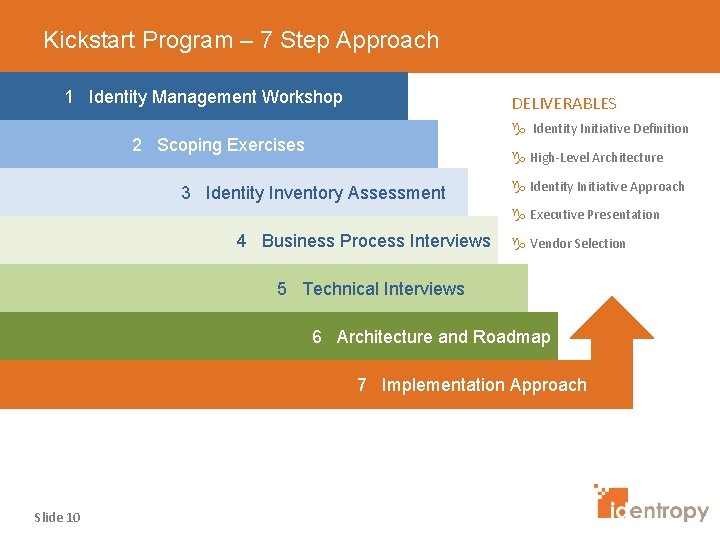
Kickstart Program – 7 Step Approach 1 Identity Management Workshop DELIVERABLES g Identity Initiative Definition 2 Scoping Exercises g High-Level Architecture 3 Identity Inventory Assessment g Identity Initiative Approach g Executive Presentation 4 Business Process Interviews g Vendor Selection 5 Technical Interviews 6 Architecture and Roadmap 7 Implementation Approach Slide 10

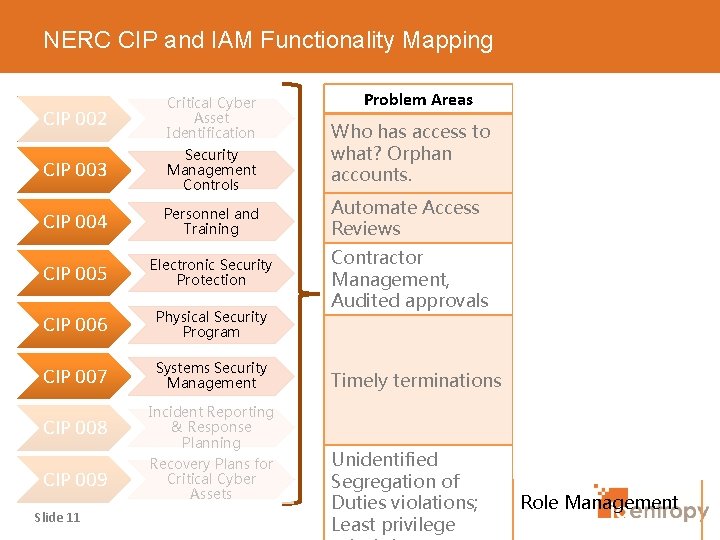
NERC CIP and IAM Functionality Mapping CIP 002 Critical Cyber Asset Identification CIP 003 Security Management Controls CIP 004 Personnel and Training CIP 005 Electronic Security Protection CIP 006 Physical Security Program CIP 007 Systems Security Management CIP 008 Incident Reporting & Response Planning CIP 009 Recovery Plans for Critical Cyber Assets Slide 11 Problem Areas IAM Functionality Who has access to what? Orphan accounts. Identity Data Mapping Automate Access Reviews Access Recertification Contractor Management, Audited approvals Workflow Engine Reporting Engine Provisioning Engine Timely terminations Access Management Identity Activity Monitoring Unidentified Segregation of Duties violations; Least privilege Role Management

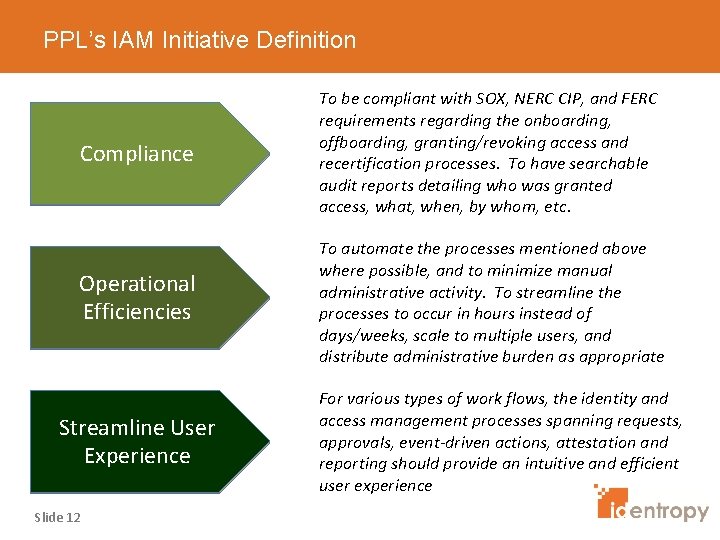
PPL’s IAM Initiative Definition Compliance To be compliant with SOX, NERC CIP, and FERC requirements regarding the onboarding, offboarding, granting/revoking access and recertification processes. To have searchable audit reports detailing who was granted access, what, when, by whom, etc. Operational Efficiencies To automate the processes mentioned above where possible, and to minimize manual administrative activity. To streamline the processes to occur in hours instead of days/weeks, scale to multiple users, and distribute administrative burden as appropriate Streamline User Experience Slide 12 For various types of work flows, the identity and access management processes spanning requests, approvals, event-driven actions, attestation and reporting should provide an intuitive and efficient user experience

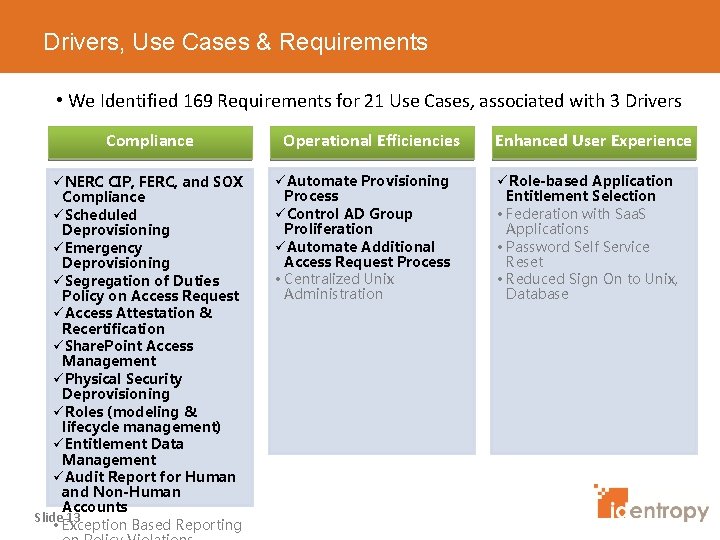
Drivers, Use Cases & Requirements • We Identified 169 Requirements for 21 Use Cases, associated with 3 Drivers Compliance üNERC CIP, FERC, and SOX Compliance üScheduled Deprovisioning üEmergency Deprovisioning üSegregation of Duties Policy on Access Request üAccess Attestation & Recertification üShare. Point Access Management üPhysical Security Deprovisioning üRoles (modeling & lifecycle management) üEntitlement Data Management üAudit Report for Human and Non-Human Accounts Slide 13 • Exception Based Reporting Operational Efficiencies üAutomate Provisioning Process üControl AD Group Proliferation üAutomate Additional Access Request Process • Centralized Unix Administration Enhanced User Experience üRole-based Application Entitlement Selection • Federation with Saa. S Applications • Password Self Service Reset • Reduced Sign On to Unix, Database

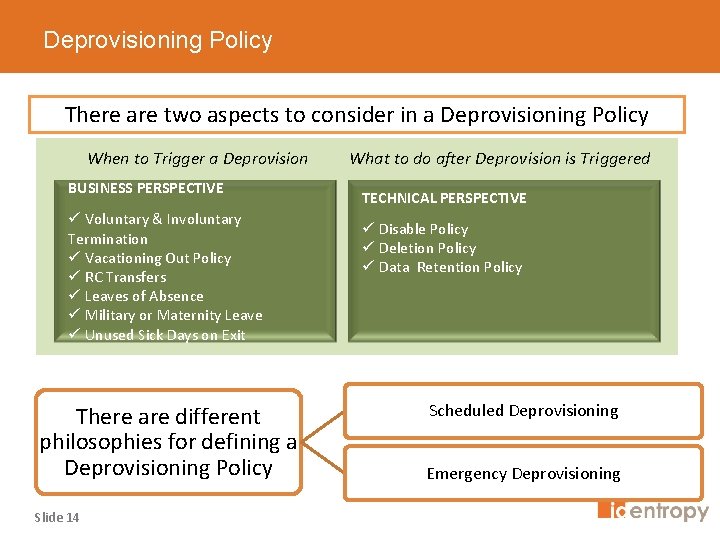
Deprovisioning Policy There are two aspects to consider in a Deprovisioning Policy When to Trigger a Deprovision BUSINESS PERSPECTIVE ü Voluntary & Involuntary Termination ü Vacationing Out Policy ü RC Transfers ü Leaves of Absence ü Military or Maternity Leave ü Unused Sick Days on Exit There are different philosophies for defining a Deprovisioning Policy Slide 14 What to do after Deprovision is Triggered TECHNICAL PERSPECTIVE ü Disable Policy ü Deletion Policy ü Data Retention Policy Scheduled Deprovisioning Emergency Deprovisioning

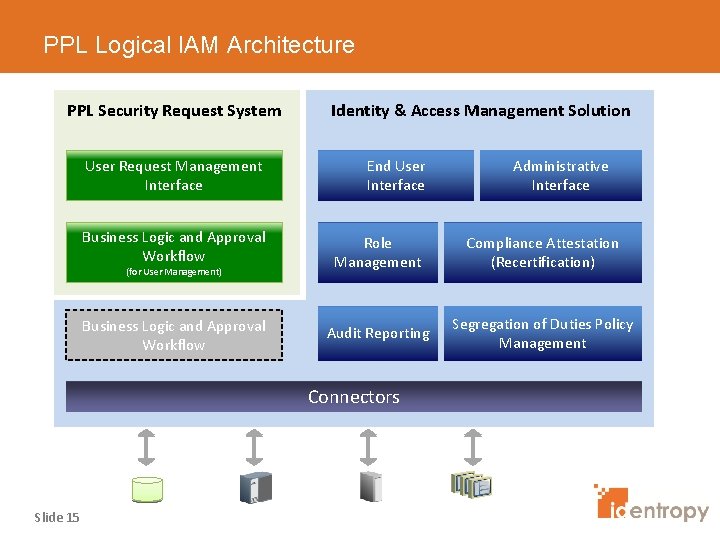
PPL Logical IAM Architecture PPL Security Request System Identity & Access Management Solution User Request Management Interface End User Interface Business Logic and Approval Workflow Role Management Compliance Attestation (Recertification) Business Logic and Approval Workflow Audit Reporting Segregation of Duties Policy Management (for User Management) Connectors Slide 15 Administrative Interface

Polling Question #2 How is your organization managing deprovisioning today? (check all that apply) 1. We do not have a deprovisioning process defined 2. We have defined Deprovisioning Policies 3. We have automated most if not all of our deprovisioning process 4. We haven’t automated much of our deprovisioning process 5. We have implemented a closed-loop deprovisioning process Slide 16

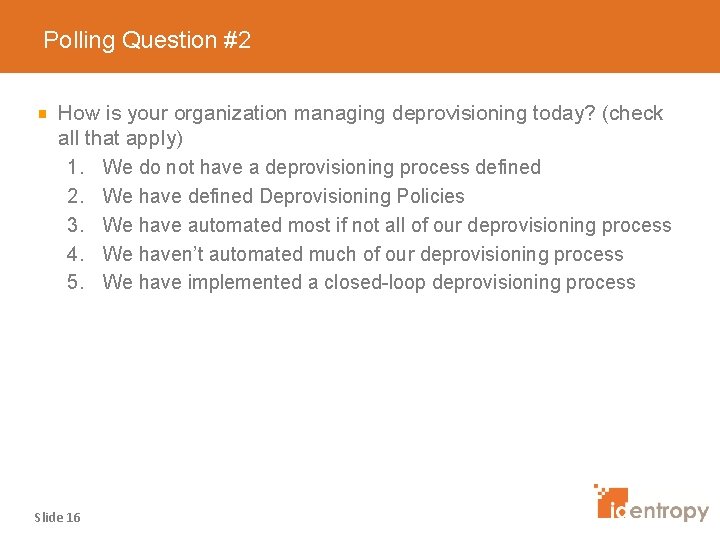
Q & A: Where did PPL decide to begin and why? Slide 17

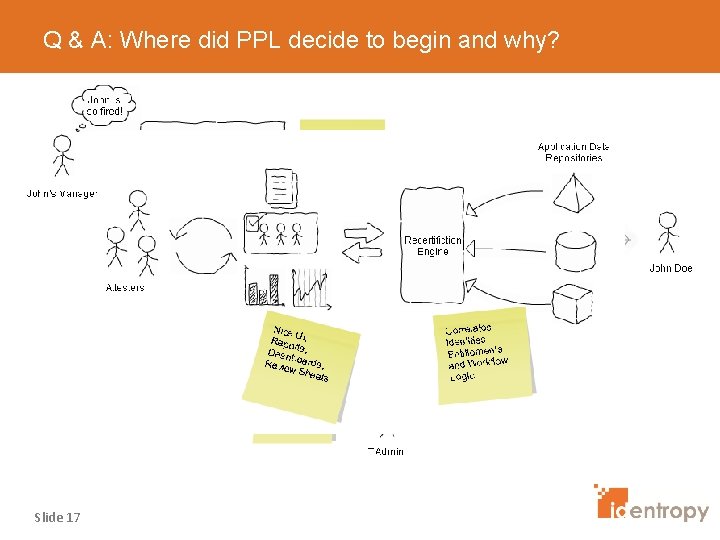
Q&A: How will PPL handle compliance for legacy apps? Slide 18

Q&A: Were there “aha” moments in this process? A target system, from an access recertification perspective, is often more than just an application • Ex: Windows/AD is one target in our inventory, but has a multitude of components to recertify (user accounts, groups, GPOs, etc. ) The fact that we had a database of all NERC CIP apps, and owners in place beforehand, really helped with the strategy • A good application inventory is key Don’t underestimate the complexity of bringing legacy apps under governance. And don’t be afraid of considering unorthodox methods • We learned that identity activity monitoring could help us expedite compliance within legacy apps Slide 19

Any Questions? If you prefer to ask questions offline, email us at info@identropy. com Slide 20

Thank You… Visit us www. identropy. com …email us info@identropy. com …or visit our blog www. identropy. com/blog Slide 21