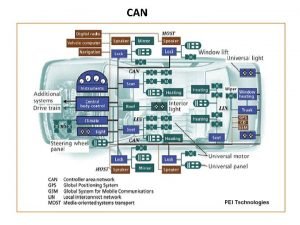
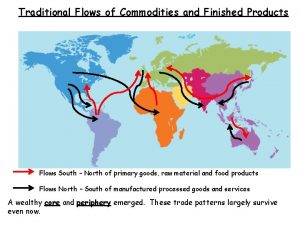
Can Sec Westcore 05 Network Flows and Security






- Slides: 29

Can. Sec. West/core 05 Network Flows and Security v 1. 02 Nicolas FISCHBACH Senior Manager, Network Engineering Security, COLT Telecom nico@securite. org - http: //www. securite. org/nico/

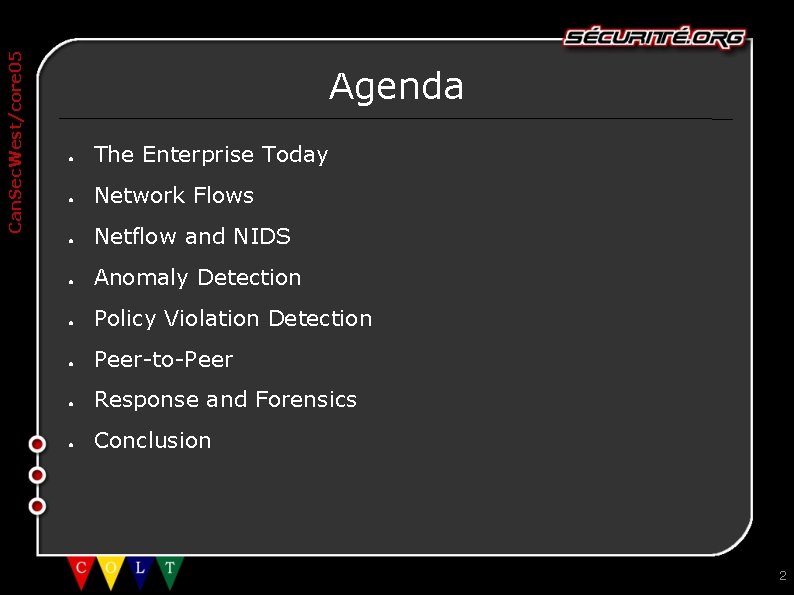
Can. Sec. West/core 05 Agenda ● The Enterprise Today ● Network Flows ● Netflow and NIDS ● Anomaly Detection ● Policy Violation Detection ● Peer-to-Peer ● Response and Forensics ● Conclusion 2

Can. Sec. West/core 05 The Enterprise Today ● Where’s my border ? ● WLANs, 3 G devices, etc. ● Remote VPN/maintenance access: employees, partners, vendors and customers ● Client-side attacks ● Malware/spyware relying on covert channels ● ● Usually one “flat” undocumented network: no internal filtering, no dedicated clients/servers LANs, etc. More and more (wannabe) power users 3

Can. Sec. West/core 05 The Enterprise Today ● Undocumented systems and applications ● Have you ever sniffed on a core switch’s SPAN port ? ● Do you really need (expensive) NIDS to detect worms ? ● More and more communications are encrypted: SSH, SSL, IPsec, etc (even internally) 4

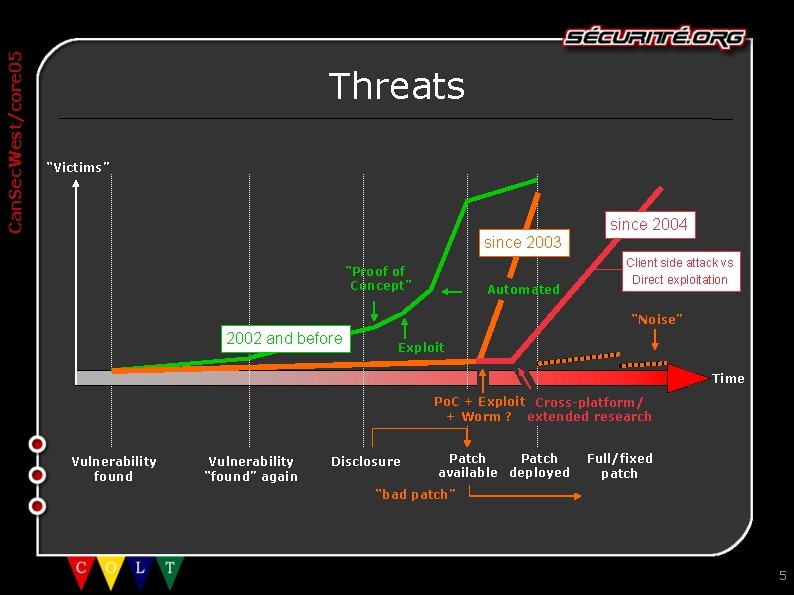
Can. Sec. West/core 05 Threats “Victims” since 2004 since 2003 “Proof of Concept” Automated Client side attack vs Direct exploitation “Noise” 2002 and before Exploit Time Po. C + Exploit Cross-platform/ + Worm ? extended research Vulnerability found Vulnerability “found” again Disclosure Patch available deployed Full/fixed patch “bad patch” 5

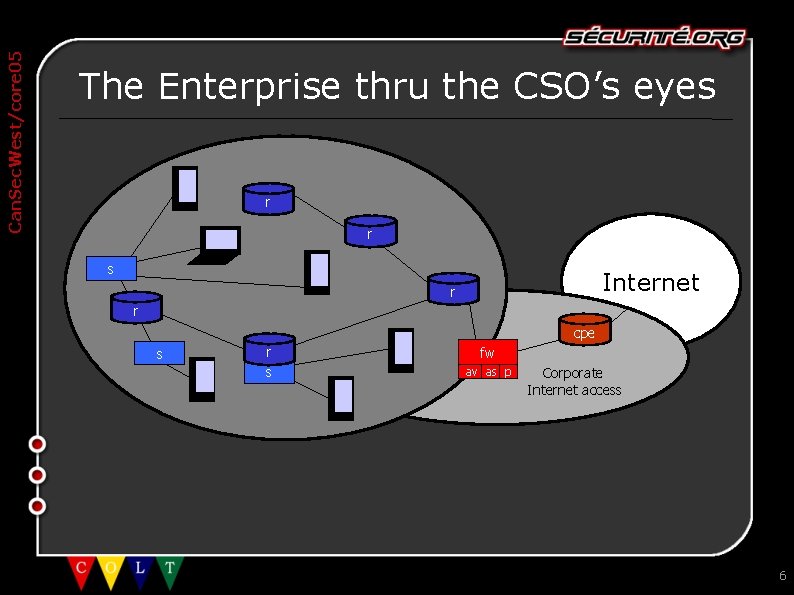
Can. Sec. West/core 05 The Enterprise thru the CSO’s eyes r r s Internet r r cpe s r s fw av as p Corporate Internet access 6

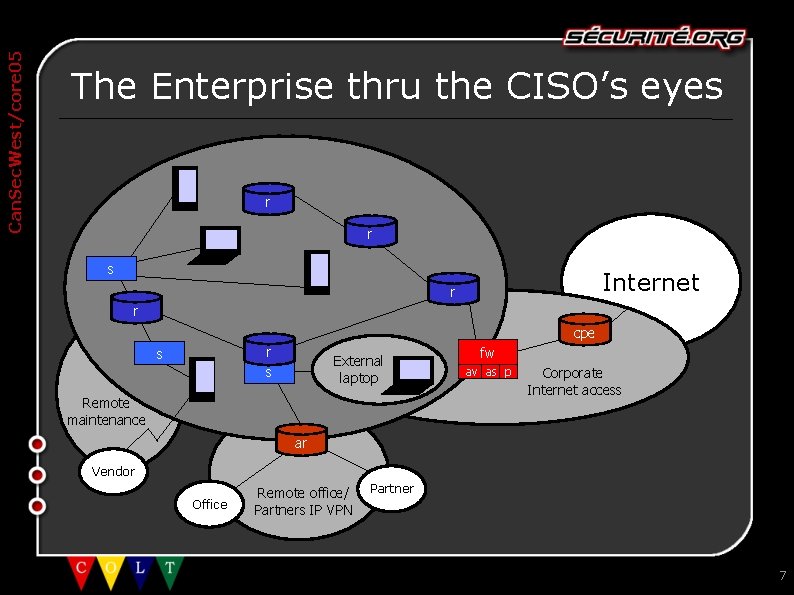
Can. Sec. West/core 05 The Enterprise thru the CISO’s eyes r r s Internet r r cpe r s s External laptop Remote maintenance fw av as p Corporate Internet access ar Vendor Office Remote office/ Partners IP VPN Partner 7

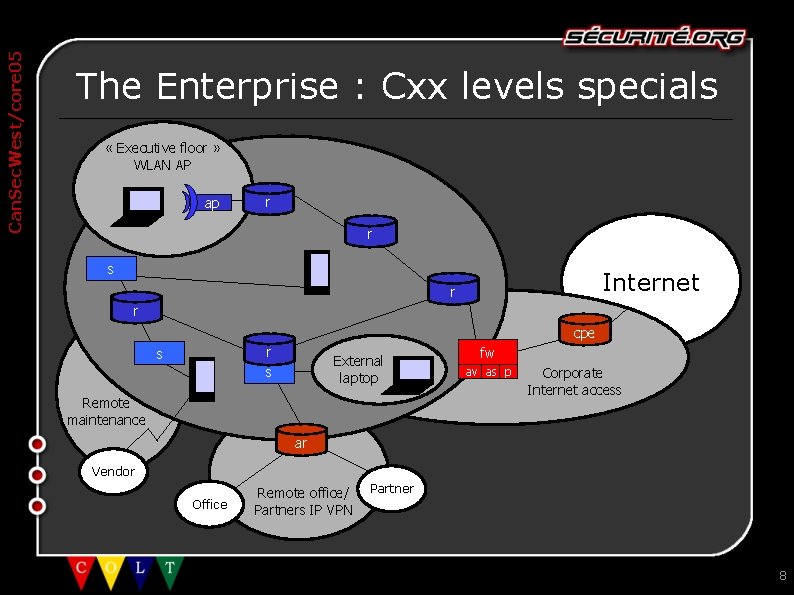
Can. Sec. West/core 05 The Enterprise : Cxx levels specials « Executive floor » WLAN AP ap r r s Internet r r cpe r s s External laptop Remote maintenance fw av as p Corporate Internet access ar Vendor Office Remote office/ Partners IP VPN Partner 8

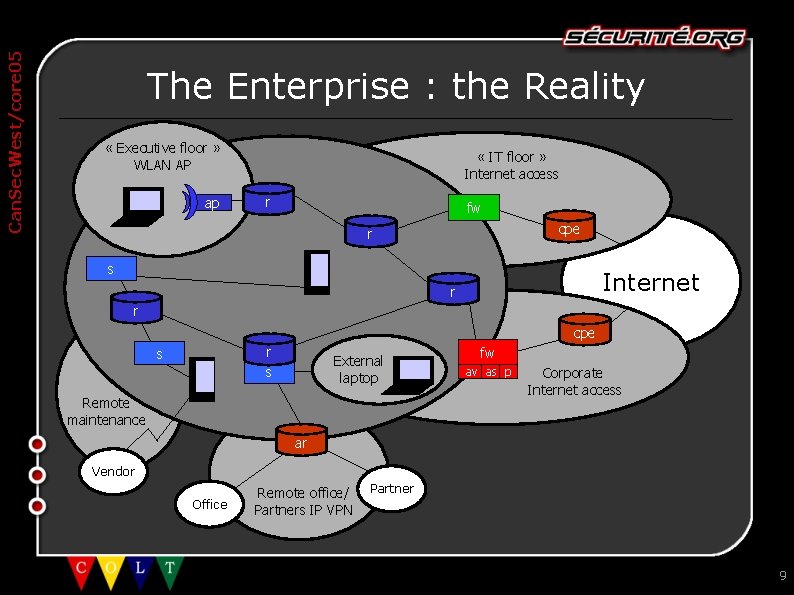
Can. Sec. West/core 05 The Enterprise : the Reality « Executive floor » WLAN AP ap « IT floor » Internet access r fw cpe r s Internet r r cpe r s s External laptop Remote maintenance fw av as p Corporate Internet access ar Vendor Office Remote office/ Partners IP VPN Partner 9

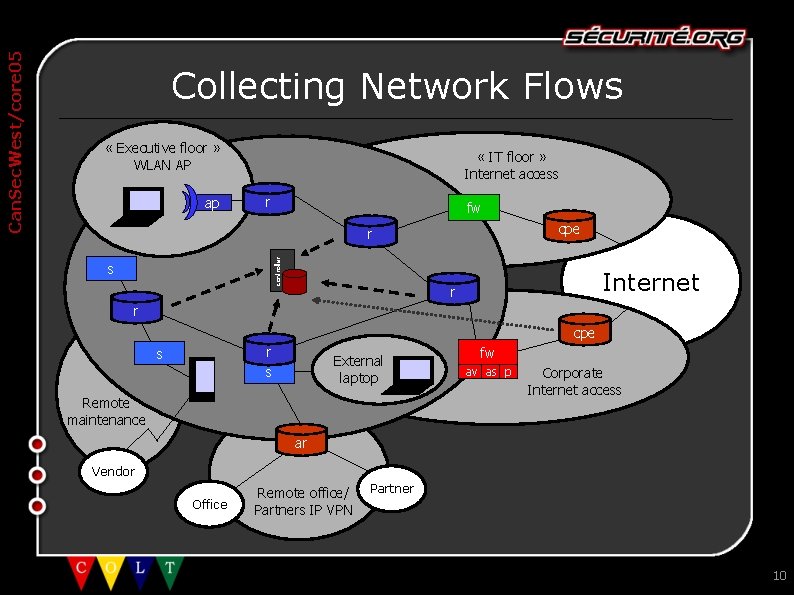
« Executive floor » WLAN AP ap « IT floor » Internet access r fw cpe r controller Can. Sec. West/core 05 Collecting Network Flows s Internet r r cpe r s s External laptop Remote maintenance fw av as p Corporate Internet access ar Vendor Office Remote office/ Partners IP VPN Partner 10

Can. Sec. West/core 05 Network Flows ● ● What are network flows and why are they so interesting? Netflow (Cisco terminology) used to be a routing technology which became a traffic accounting solution Used since years by Service Providers to detect and traceback DDo. S attacks and more recently for traffic engineering purposes In the enterprise network: – Network and application profiling, forensics, anomaly detection, policy violation, etc. – Netflow/NIDS: and/or ? Mix of macroscopic and microscopic views in high speed environments 11

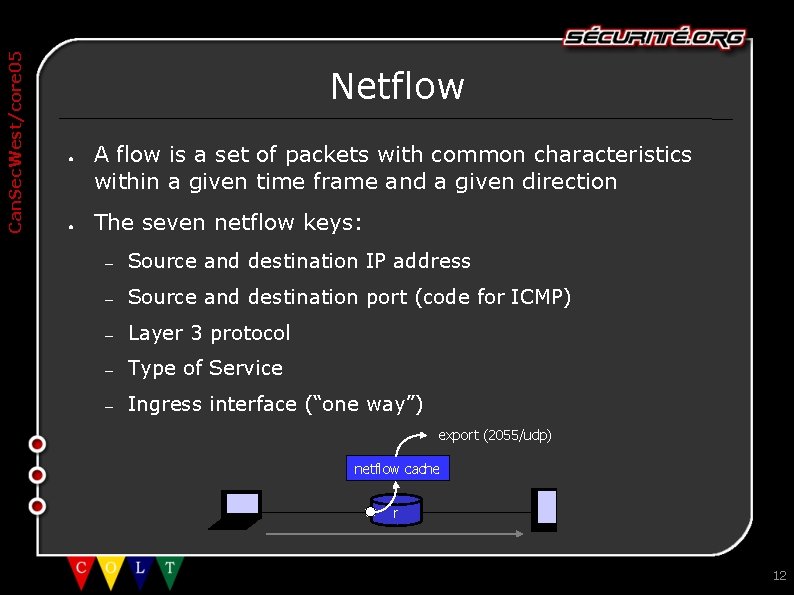
Can. Sec. West/core 05 Netflow ● ● A flow is a set of packets with common characteristics within a given time frame and a given direction The seven netflow keys: – Source and destination IP address – Source and destination port (code for ICMP) – Layer 3 protocol – Type of Service – Ingress interface (“one way”) export (2055/udp) netflow cache r 12

Can. Sec. West/core 05 Netflow ● ● The following data are exported (Netflow v 5) – The 7 key fields – Bytes and packets count – Start and end time – Egress interface and next-hop – TCP flags (except on some HW/SW combination on multilayer switches) And you may also see the AS number and other fields depending on version and configuration ● IPFIX is based on Netflow v 9 ● Egress Netflow and per class sampling in recent IOSes 13

Can. Sec. West/core 05 Netflow ● The cache contains 64 k entries (default) ● A flow expires: ● ● – After 15 seconds of inactivity (default) – After 30 minutes of activity (default) – When the RST or FIN flag is set – If the cache is full Counting issues: aggregation and duplicates (a flow may be counted by multiple routers and long lasting flows may be “duplicated” in the database) Security issues: clear text, no checksum, can be spoofed (UDP) and possible Do. S (48 bytes per flow for a 32 bytes packet) 14

Can. Sec. West/core 05 Netflow ● ● Sampling – By default, no sampling: each flow entry is exported – Sampled: percentage of flows only (deterministic) – Random Sampled: like sampled, but randomized (statistically better) “Full netflow” is supported on/by most of the HW/SW, sampled and random sampled only on a subset Sampling reduces load and export size but “losses” data: – OK: DDo. S detection – NOK: Policy violation detection Avoid router-based aggregation 15

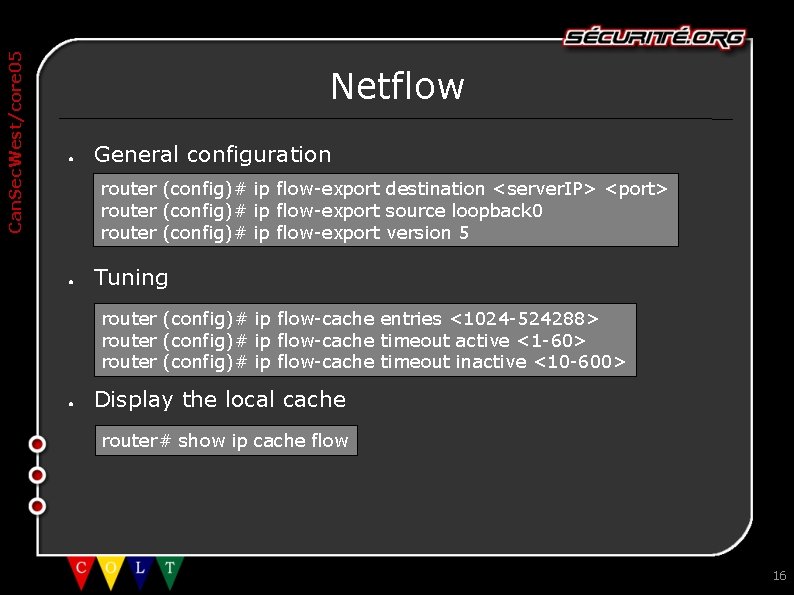
Can. Sec. West/core 05 Netflow ● General configuration router (config)# ip flow-export destination <server. IP> <port> router (config)# ip flow-export source loopback 0 router (config)# ip flow-export version 5 ● Tuning router (config)# ip flow-cache entries <1024 -524288> router (config)# ip flow-cache timeout active <1 -60> router (config)# ip flow-cache timeout inactive <10 -600> ● Display the local cache router# show ip cache flow 16

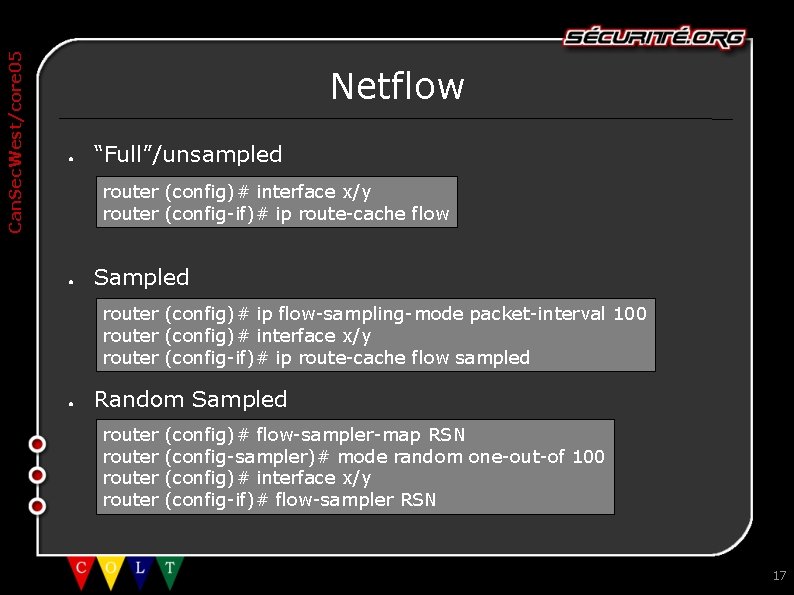
Can. Sec. West/core 05 Netflow ● “Full”/unsampled router (config)# interface x/y router (config-if)# ip route-cache flow ● Sampled router (config)# ip flow-sampling-mode packet-interval 100 router (config)# interface x/y router (config-if)# ip route-cache flow sampled ● Random Sampled router (config)# flow-sampler-map RSN (config-sampler)# mode random one-out-of 100 (config)# interface x/y (config-if)# flow-sampler RSN 17

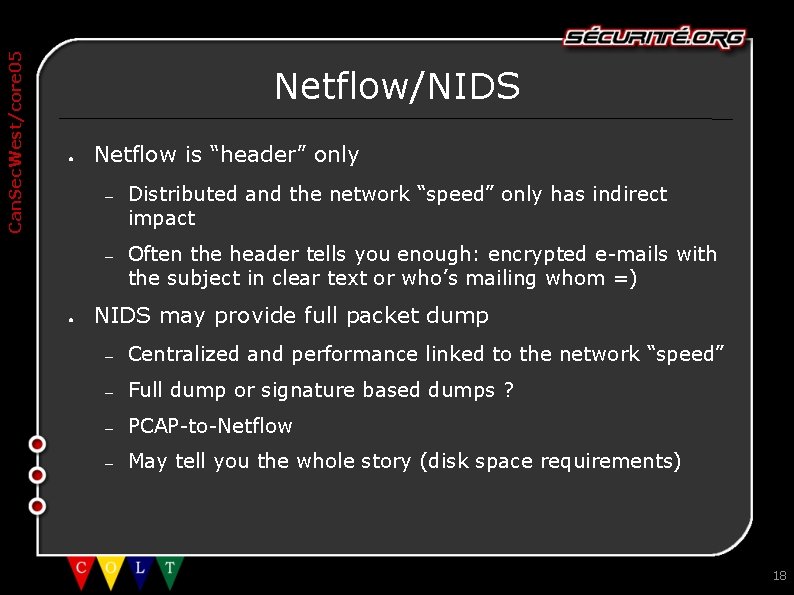
Can. Sec. West/core 05 Netflow/NIDS ● ● Netflow is “header” only – Distributed and the network “speed” only has indirect impact – Often the header tells you enough: encrypted e-mails with the subject in clear text or who’s mailing whom =) NIDS may provide full packet dump – Centralized and performance linked to the network “speed” – Full dump or signature based dumps ? – PCAP-to-Netflow – May tell you the whole story (disk space requirements) 18

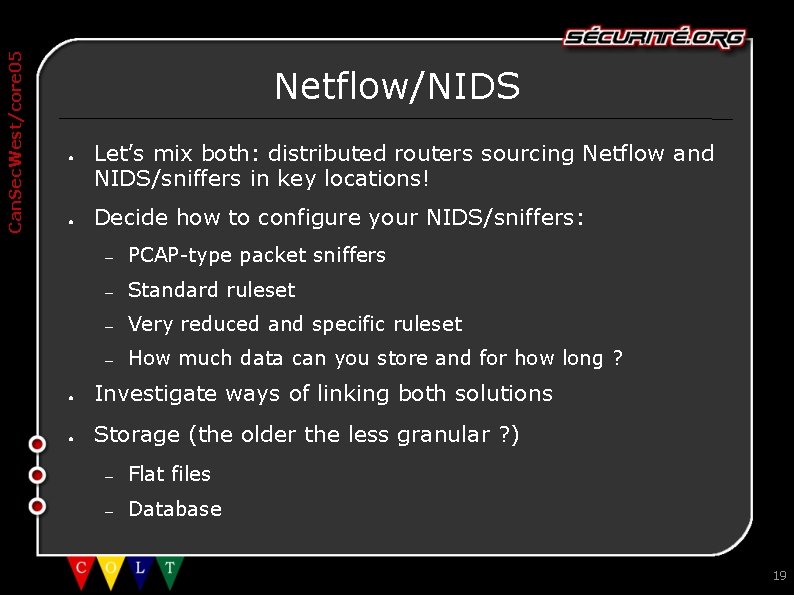
Can. Sec. West/core 05 Netflow/NIDS ● ● Let’s mix both: distributed routers sourcing Netflow and NIDS/sniffers in key locations! Decide how to configure your NIDS/sniffers: – PCAP-type packet sniffers – Standard ruleset – Very reduced and specific ruleset – How much data can you store and for how long ? ● Investigate ways of linking both solutions ● Storage (the older the less granular ? ) – Flat files – Database 19

Can. Sec. West/core 05 Anomaly Detection ● Discover your network – Enabling netflow will give you some insight on what your network actually carries : ) – After the shock and the first clean up round: – ● Sniff traffic in specific locations ● Introduce security driven network segmentation ● Build a complete baseline Update your network diagram 20

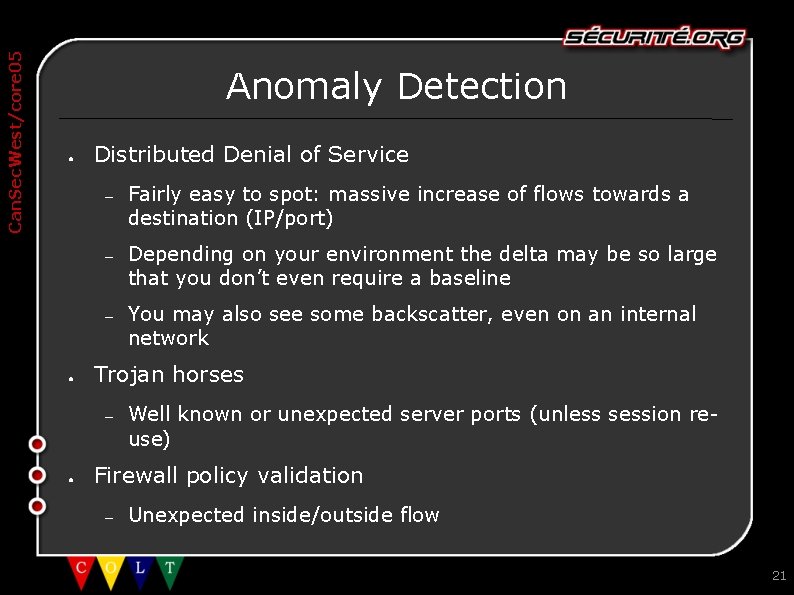
Can. Sec. West/core 05 Anomaly Detection ● ● Distributed Denial of Service – Fairly easy to spot: massive increase of flows towards a destination (IP/port) – Depending on your environment the delta may be so large that you don’t even require a baseline – You may also see some backscatter, even on an internal network Trojan horses – ● Well known or unexpected server ports (unless session reuse) Firewall policy validation – Unexpected inside/outside flow 21

Can. Sec. West/core 05 Anomaly Detection ● Worms – Old ones are easy to spot: they wildly scan the same /8, /16 or /24 or easy to code discovery pattern – New ones are looking for specific ports – Each variant may have a specific payload size – May scan BOGON space – The payload may be downloaded from specific, AV identified, websites – The source address is spoofed (but that’s less and less the case) 22

Can. Sec. West/core 05 Anomaly Detection ● ● Covert channels / Tunnels – Long flows while short ones are expected (lookups) – Symmetric vs asymmetric traffic (web surfing) – Large payloads instead of small ones – Think ICMP, DNS, HTTP(s) Scans – Slow: single flows (bottom. N) – Issue with bottom. N: long tail – Normal/Fast: large sum of small flows from and/or to an IP – Return packets (RST for TCP and ICMP Port Unreachable for UDP) 23

Can. Sec. West/core 05 Policy Violation Detection ● Workstation / server behaviour – Usually very “static” client/server communications – Who initiates the communication and to which destination ? – Office hours – New source/destination IPs/ports showing up – Tracking using DHCP logs, MAC address, physical switch port (SNMP) – Identify the “early” flows (auto-update and spyware) – ● After DHCP allocation or after login ● Flows after the initial communication Recurring flows (keyloggers) or flows towards the same destination but using various protocols (firewall piercing) 24

Can. Sec. West/core 05 Peer to Peer (P 2 P) ● ● ● Legacy P 2 P protocols often use fixed ports or ranges Sometimes (like with FTP) the data port is the control port +/-1 Recent P 2 P protocols have the session details in the payload: they can’t be tracked using netflow but the flow size may give you a hint 25

Can. Sec. West/core 05 Response ● ● Locate the source host – Requires the “netflow source” information (which router saw that flow) – Layer 3 and Layer 2 trace: identify the last layer 3 hop and then layer 2 trace or use previously SNMP polled MAC/port address Block the host – Port shutdown – ACLs – Blackhole route injection 26

Can. Sec. West/core 05 Forensics ● Netflow and dumps storage need to resolved first ● Clear post-mortem process ● ● Usual approach is to look for the flows and once identified extract the relevant dumps/logs In some environment only a couple of minutes/hours may be stored Legal/privacy issues Out-of-band network to push data and avoid multiaccounting 27

Can. Sec. West/core 05 Tools ● Lolo’s early proof-of-concept: Ye. FLOW http: //yeflow. rstack. org/ ● argus (http: //www. qosient. com/argus/) ● flow-tools (http: //www. splintered. net/sw/flow-tools/) ● nfdump (http: //nfdump. sourceforge. net) ● ● ● graphviz (http: //www. graphviz. org/): human eye is good at catching things, but the graphs become really complex Comprehensive list: tant/floma/software. html http: //www. switch. ch/tf- Commercial products 28

Can. Sec. West/core 05 Conclusion ● Netflow: macroscopic view ● NIDS/sniffer: microscopic view ● Network switches: layer 0/1 view (MAC address/port) ● Mix them while controlling – CAPEX/OPEX – Storage – Search/detection capabilities – Avoid impact on the network ● Active response ● Q&A (quarantine/active defense) ? 29
 Wireless security in cryptography and network security
Wireless security in cryptography and network security Private securit
Private securit Osi security architecture in hindi
Osi security architecture in hindi Security guide to network security fundamentals
Security guide to network security fundamentals Electronic mail security in network security
Electronic mail security in network security Security guide to network security fundamentals
Security guide to network security fundamentals Security guide to network security fundamentals
Security guide to network security fundamentals Minimum cost flow
Minimum cost flow E commerce security policy
E commerce security policy 5g americas
5g americas Network design and implementation
Network design and implementation Module 3: information and network security
Module 3: information and network security Modulo table
Modulo table криптографический модуль
криптографический модуль Number theory in cyber security
Number theory in cyber security Firewall in cryptography and network security
Firewall in cryptography and network security Authentication in cryptography and network security
Authentication in cryptography and network security Intruders in cryptography and network security
Intruders in cryptography and network security Primitive root
Primitive root Cryptography and network security 6th edition pdf
Cryptography and network security 6th edition pdf Cryptography and network security pearson
Cryptography and network security pearson Source
Source Cryptography and network security 4th edition
Cryptography and network security 4th edition Fermat's theorem in cryptography and network security
Fermat's theorem in cryptography and network security Finite fields in cryptography and network security
Finite fields in cryptography and network security Digital signature in cryptography and network security
Digital signature in cryptography and network security Modular arithmetic in cryptography and network security
Modular arithmetic in cryptography and network security Pgp in cryptography and network security
Pgp in cryptography and network security Top down network design
Top down network design It network and security greensboro
It network and security greensboro