Azure Identity Premier Fast Start Optional Module Active












- Slides: 32

Azure Identity Premier Fast Start Optional Module

Active Directory Federation Services

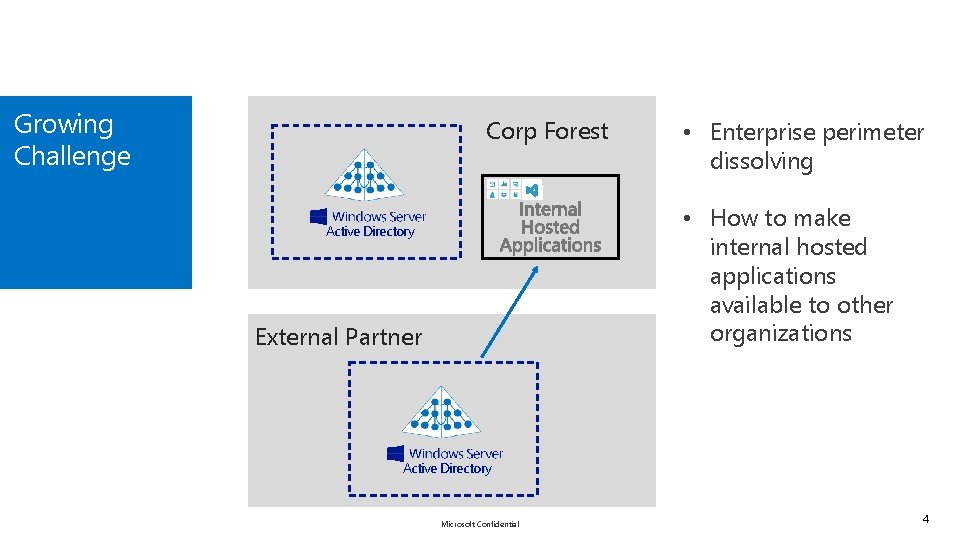
Growing Challenge Corp Forest • Enterprise perimeter dissolving • How to make internal hosted applications available to other organizations Active Directory External Partner Active Directory Microsoft Confidential 4

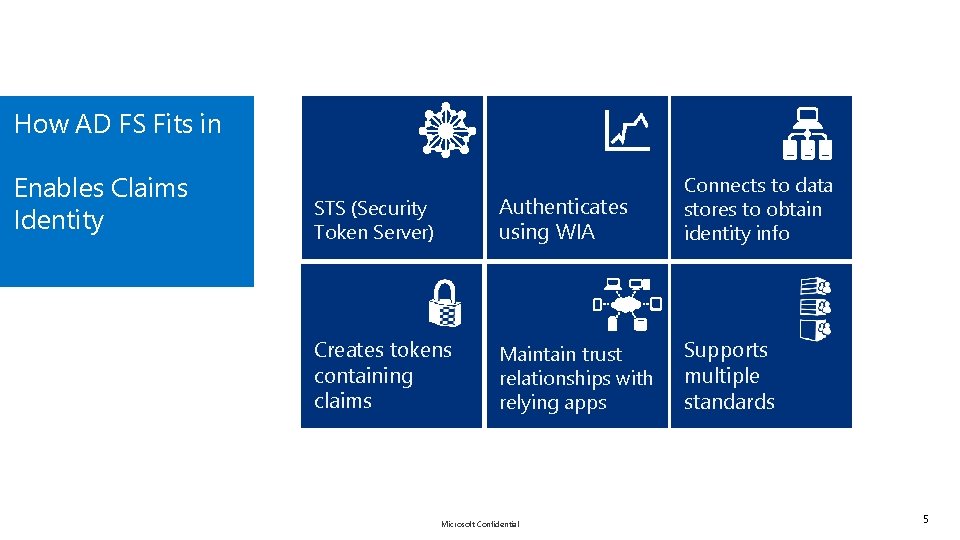
How AD FS Fits in Enables Claims Identity STS (Security Token Server) Authenticates using WIA Connects to data stores to obtain identity info Creates tokens containing claims Maintain trust relationships with relying apps Supports multiple standards Microsoft Confidential 5

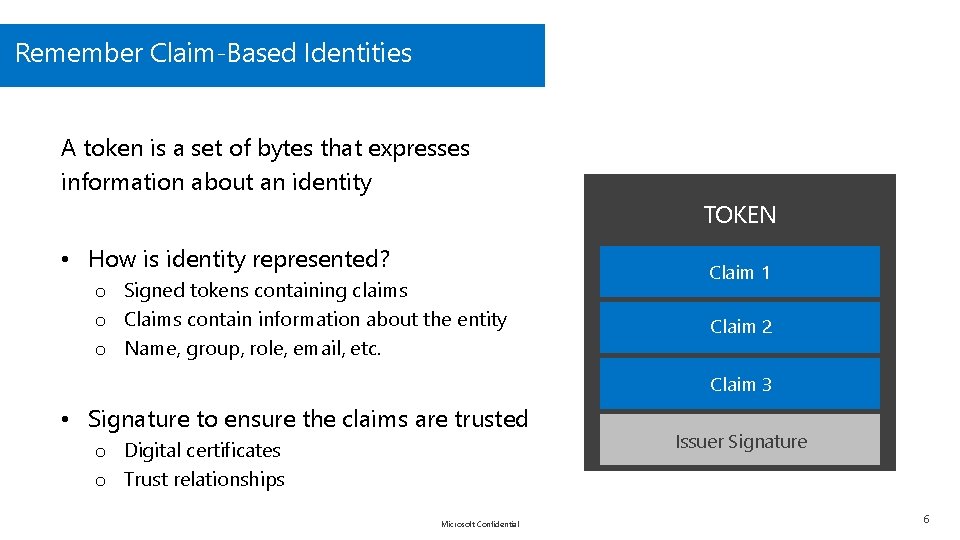
Remember Claim-Based Identities A token is a set of bytes that expresses information about an identity TOKEN • How is identity represented? o Signed tokens containing claims o Claims contain information about the entity o Name, group, role, email, etc. Claim 1 Claim 2 Claim 3 • Signature to ensure the claims are trusted o Digital certificates o Trust relationships Microsoft Confidential Issuer Signature 6

Scenarios for Using AD FS Company that want their users to authenticate only once to access onpremises or off-premises claims aware apps A company has an application that they want a partner to gain access to External partner organization has an application that a company want their users have access to Need for internal users to gain access to an application in the perimeter network forest without doing the forest trust Microsoft Confidential 7

Scenarios for Using AD FS (Continued) Federation needs for Microsoft Share. Point Need to access web services from mobile device applications Need to move on-premises services to public clouds Companies merging need users in both forests to access claims aware apps without a need for a forest trust Microsoft Confidential 8

AD FS Versions • • • Active Directory Federation Services 2. 0 o Released to Web o Can be installed on Windows 2008 SP 2 or Windows 2008 R 2 Active Directory Federation Services 1. 1 (not covered in workshop) o Available in Windows 2008 R 2 and Windows 2008 o Installed as a role from server manager Active Directory Federation Services 1. 0 (not covered in workshop) o Only available in Windows 2003 R 2 o Part of the operating system AD FS in Windows Server 2012 R 2 o Available in Windows 2012 R 2 o Installed as a role from server manager AD FS in Windows Server 2012 o Available in Windows 2012 o Installed as a role from server manager Microsoft Confidential 9

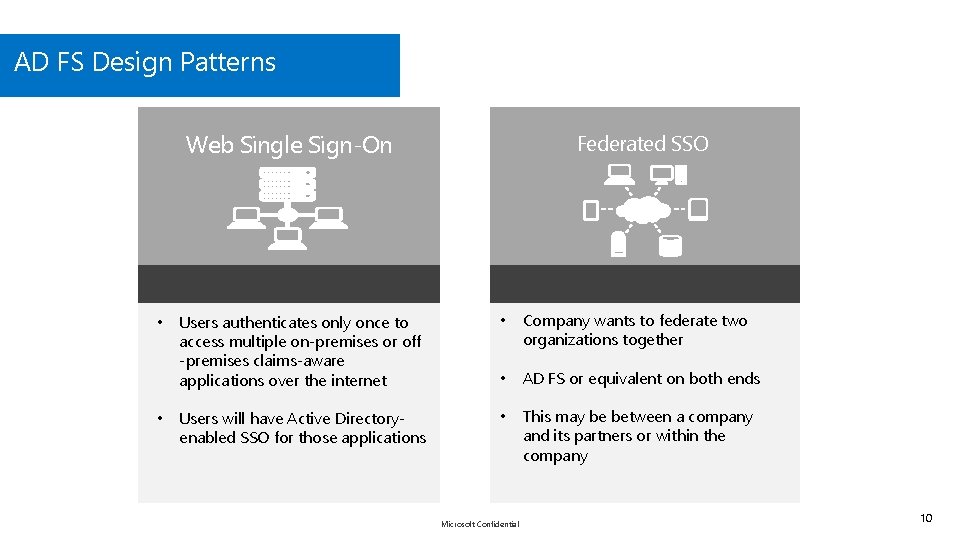
AD FS Design Patterns Web Single Sign-On • • Federated SSO Users authenticates only once to access multiple on-premises or off -premises claims-aware applications over the internet • Company wants to federate two organizations together • AD FS or equivalent on both ends Users will have Active Directoryenabled SSO for those applications • This may be between a company and its partners or within the company Microsoft Confidential 10

Web SSO • One to many applications • Typically, within one organization • Allows SSO between multiple apps Microsoft Confidential 11

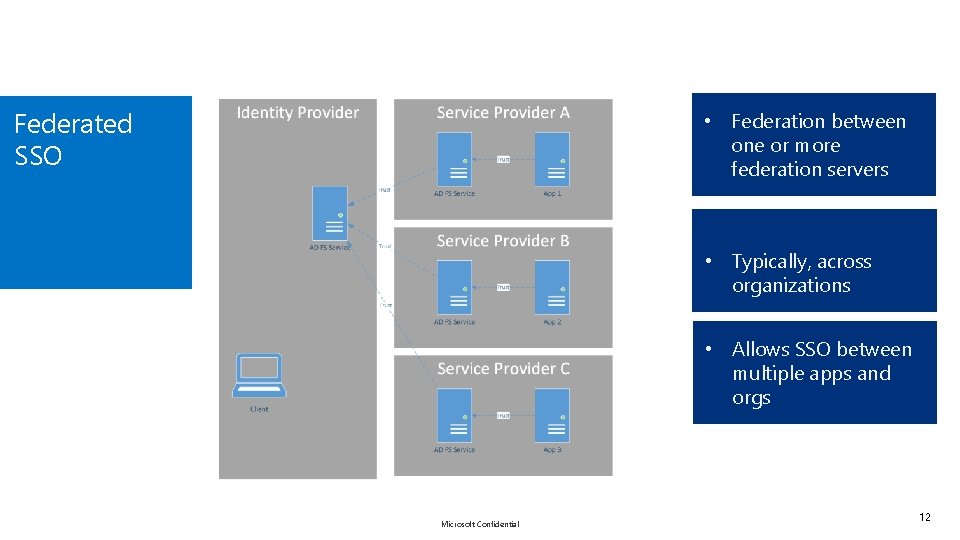
Federated SSO • Federation between one or more federation servers • Typically, across organizations • Allows SSO between multiple apps and orgs Microsoft Confidential 12

Supported Standards AD FS 1. x AD FS 2. x AD FS 3. x • • WS-Federation Passive Requestor Profile (browser) SAML 1. 0 TOKENS • • WS-Federation PRP WS-Federation Active Requestor Profile SAML 1. 1/2. 0 TOKENS SAML 2. 0 Operational Modes o Id. P Lite/SP Lite/e. Gov 1. 5 • Same as AD FS 2 x and: o Oauth o JSON Web Tokens (JWT) Microsoft Confidential 13

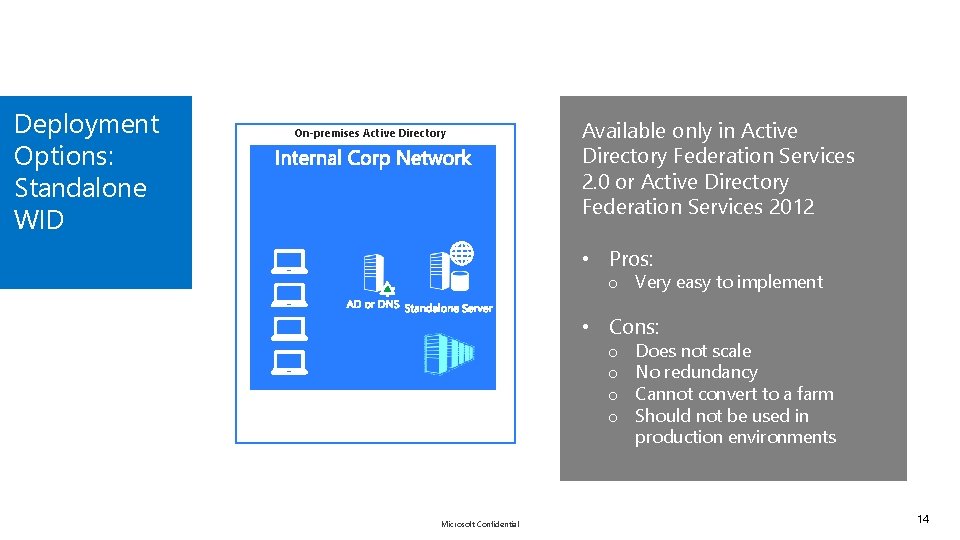
Deployment Options: Standalone WID On-premises Active Directory Available only in Active Directory Federation Services 2. 0 or Active Directory Federation Services 2012 • Pros: o Very easy to implement • Cons: o o Microsoft Confidential Does not scale No redundancy Cannot convert to a farm Should not be used in production environments 14

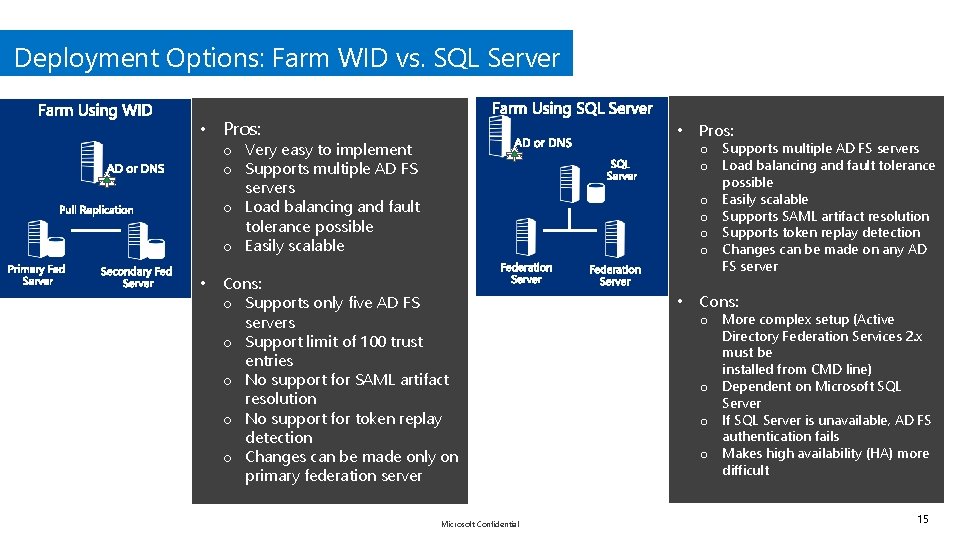
Deployment Options: Farm WID vs. SQL Server • Pros: o Very easy to implement o Supports multiple AD FS servers o Load balancing and fault tolerance possible o Easily scalable • Cons: o Supports only five AD FS servers o Support limit of 100 trust entries o No support for SAML artifact resolution o No support for token replay detection o Changes can be made only on primary federation server Microsoft Confidential • Pros: • Cons: o Supports multiple AD FS servers o Load balancing and fault tolerance possible o Easily scalable o Supports SAML artifact resolution o Supports token replay detection o Changes can be made on any AD FS server o More complex setup (Active Directory Federation Services 2. x must be installed from CMD line) o Dependent on Microsoft SQL Server o If SQL Server is unavailable, AD FS authentication fails o Makes high availability (HA) more difficult 15

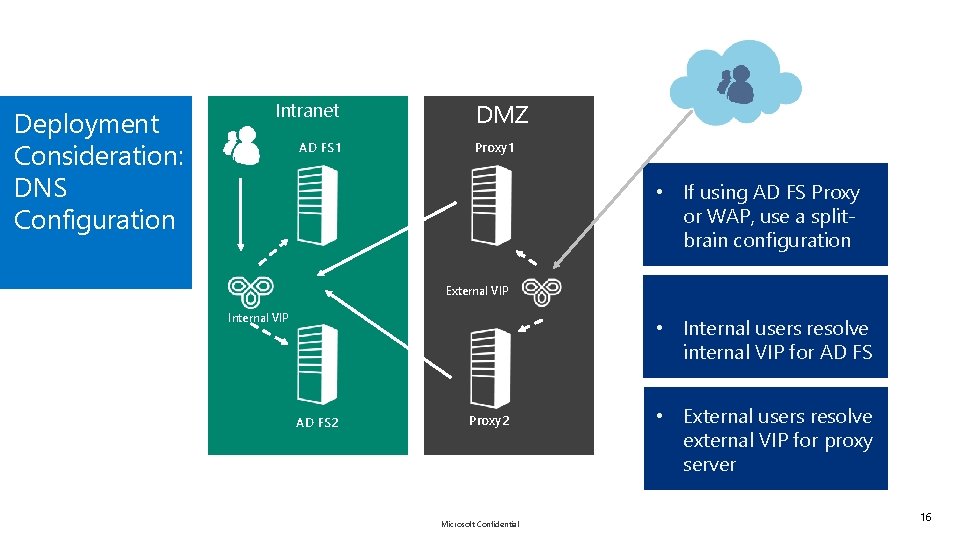
Deployment Consideration: DNS Configuration Intranet AD FS 1 DMZ Proxy 1 • If using AD FS Proxy or WAP, use a splitbrain configuration External VIP Internal VIP • Internal users resolve internal VIP for AD FS 2 Proxy 2 Microsoft Confidential • External users resolve external VIP for proxy server 16

AD FS Certificate Requirements • AD FS 2. 0 federation servers use certificates for: o • • • Establishing the SSL connection between users and the federation server Establishing the SSL connection between users and the Proxy federation server Token Decryption o o o • Service Communications Used when AD FS is not the Identity Provider Id. P encrypts the token with the relying party’s AD FS server’s public key Relying Party AD FS uses the private key to decrypt the token Token Signing o o o Tokens are signed with the private key in the token signing certificate Applications verify the signature using the federation server’s public key Every AD FS server in a farm must use the same token signing certificate with the same public or private key pair Microsoft Confidential 17

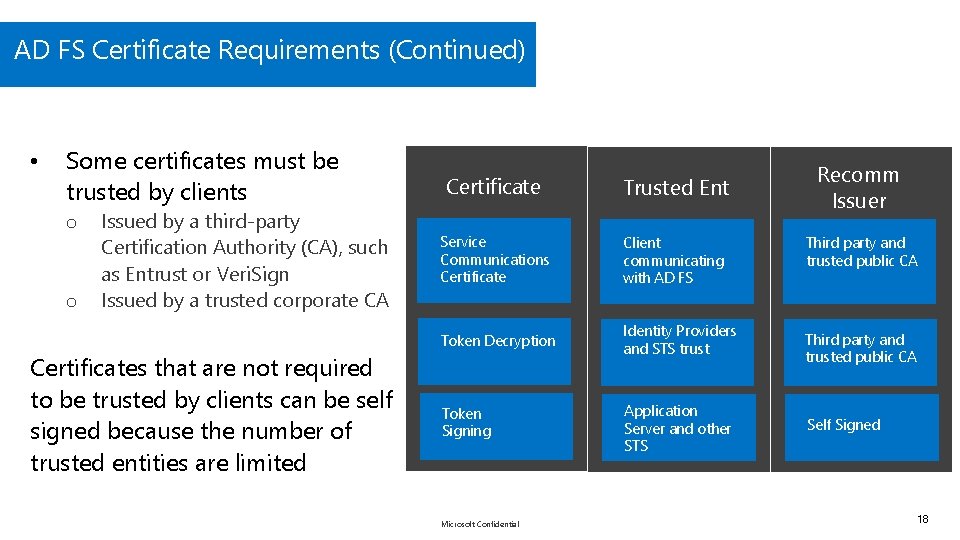
AD FS Certificate Requirements (Continued) • Some certificates must be trusted by clients o o Issued by a third-party Certification Authority (CA), such as Entrust or Veri. Sign Issued by a trusted corporate CA Certificates that are not required to be trusted by clients can be self signed because the number of trusted entities are limited Certificate Trusted Ent Service Communications Certificate Client communicating with AD FS Token Decryption Identity Providers and STS trust Token Signing Application Server and other STS Microsoft Confidential Recomm Issuer Third party and trusted public CA Self Signed 18

Why to Install AD FS 3. 0? Device Registration Service Flexible Authentication and Conditional Access Work Folders Extranet Password Change Improved Signin pages Support for Robust SQL Server HA Simplified Deployment Experiences Soft Account Lockout Customizations Options HRD Discovery Optimization Microsoft Confidential 19

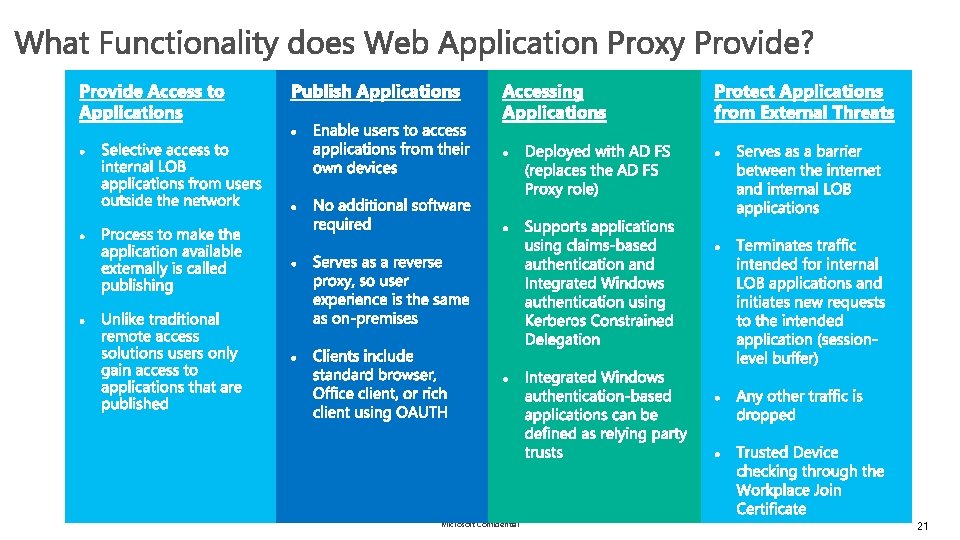
What Is Web Application Proxy? Web Application Proxy is a new Remote Access role service in Windows Server 2012 R 2. Web Application Proxy provides reverse proxy functionality for Web Applications inside your corporate network to allow users on virtually any device to access them from outside the corporate network and functions as an AD FS proxy Microsoft Confidential 20

Microsoft Confidential 21

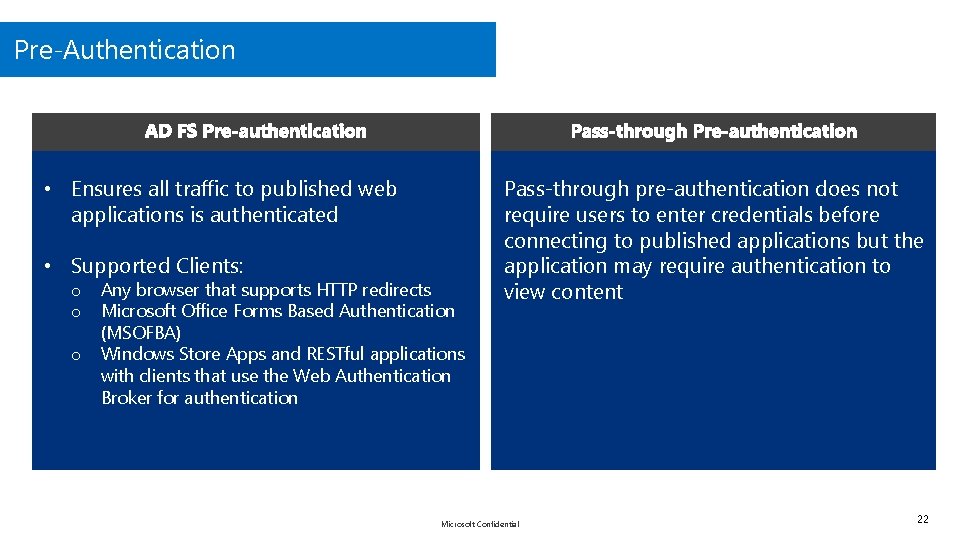
Pre-Authentication • Ensures all traffic to published web applications is authenticated • Supported Clients: o o o Any browser that supports HTTP redirects Microsoft Office Forms Based Authentication (MSOFBA) Windows Store Apps and RESTful applications with clients that use the Web Authentication Broker for authentication Pass-through pre-authentication does not require users to enter credentials before connecting to published applications but the application may require authentication to view content Microsoft Confidential 22

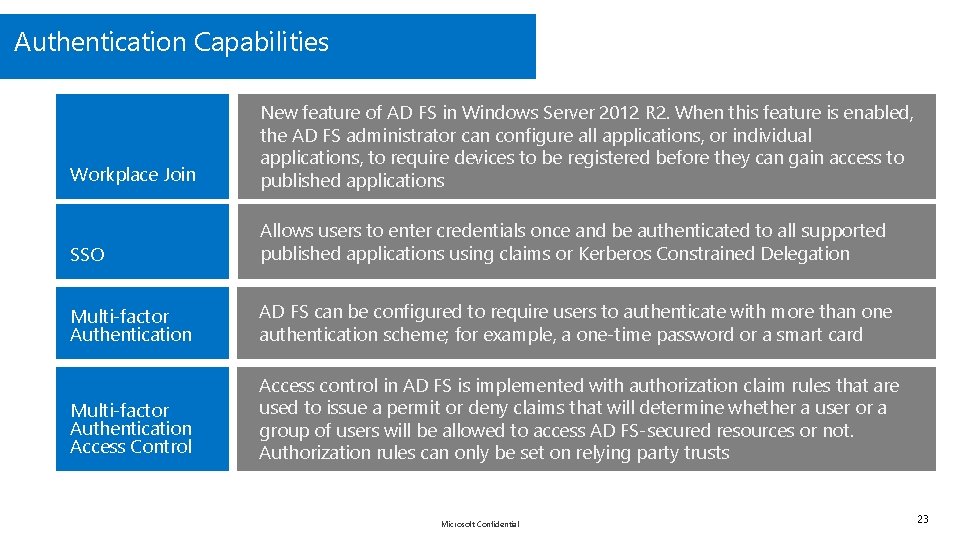
Authentication Capabilities Workplace Join New feature of AD FS in Windows Server 2012 R 2. When this feature is enabled, the AD FS administrator can configure all applications, or individual applications, to require devices to be registered before they can gain access to published applications SSO Allows users to enter credentials once and be authenticated to all supported published applications using claims or Kerberos Constrained Delegation Multi-factor Authentication AD FS can be configured to require users to authenticate with more than one authentication scheme; for example, a one-time password or a smart card Multi-factor Authentication Access Control Access control in AD FS is implemented with authorization claim rules that are used to issue a permit or deny claims that will determine whether a user or a group of users will be allowed to access AD FS-secured resources or not. Authorization rules can only be set on relying party trusts Microsoft Confidential 23

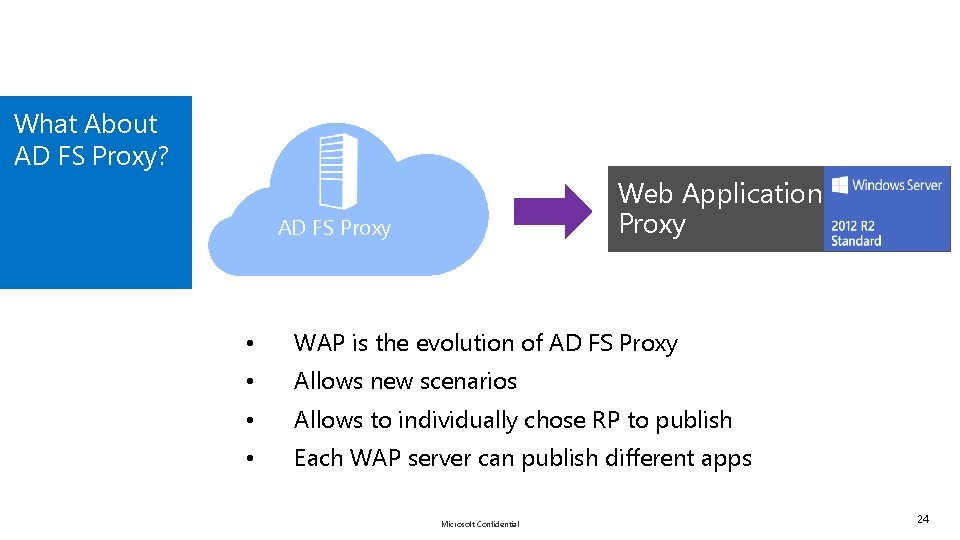
What About AD FS Proxy? Web Application Proxy AD FS Proxy • WAP is the evolution of AD FS Proxy • Allows new scenarios • Allows to individually chose RP to publish • Each WAP server can publish different apps Microsoft Confidential 24

Claims-Based Applications • To publish an application that uses claims for authentication, you must add a relying party trust for the application to the Federation Service • When publishing claims-based applications and accessing the application from a browser, the general authentication flow is as follows: 1. The client attempts to access a claims-based application using a web browser; for example, https: //appserver. contoso. com/claimapp/ 2. The web browser sends an HTTPS request to the Web Application Proxy server which redirects the request to the AD FS server 3. The AD FS server authenticates the user and the device and redirects the request back to Web Application Proxy. The request now contains the edge token. The AD FS server adds a single sign-on (SSO) cookie to the request because the user has already performed authentication against the AD FS server 4. Web Application Proxy validates the token, adds its own cookie, and forwards the request to the backend server 5. The backend server redirects the request to the AD FS server to get the application security token 6. The request is redirected to the backend server by the AD FS server. The request now contains the application token and the SSO cookie. The user is granted access to the application and is not required to enter a user name or password Microsoft Confidential 25

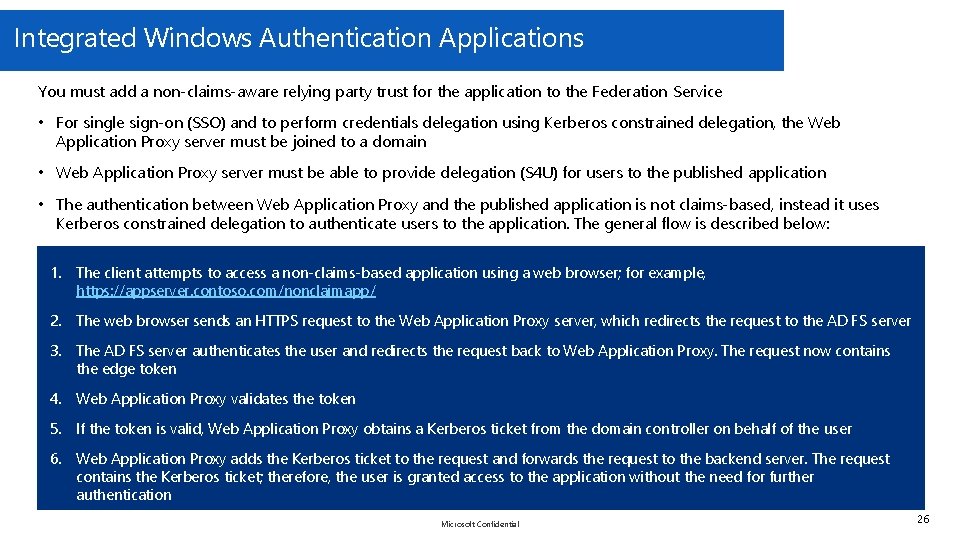
Integrated Windows Authentication Applications You must add a non-claims-aware relying party trust for the application to the Federation Service • For single sign-on (SSO) and to perform credentials delegation using Kerberos constrained delegation, the Web Application Proxy server must be joined to a domain • Web Application Proxy server must be able to provide delegation (S 4 U) for users to the published application • The authentication between Web Application Proxy and the published application is not claims-based, instead it uses Kerberos constrained delegation to authenticate users to the application. The general flow is described below: 1. The client attempts to access a non-claims-based application using a web browser; for example, https: //appserver. contoso. com/nonclaimapp/ 2. The web browser sends an HTTPS request to the Web Application Proxy server, which redirects the request to the AD FS server 3. The AD FS server authenticates the user and redirects the request back to Web Application Proxy. The request now contains the edge token 4. Web Application Proxy validates the token 5. If the token is valid, Web Application Proxy obtains a Kerberos ticket from the domain controller on behalf of the user 6. Web Application Proxy adds the Kerberos ticket to the request and forwards the request to the backend server. The request contains the Kerberos ticket; therefore, the user is granted access to the application without the need for further authentication Microsoft Confidential 26

AD FS in Azure (Requirements) • Active Microsoft Azure account in good standing • Virtual Private Network (VPN) or Microsoft EXPRESSROUTE networking to Azure • Domain controller deployed in Azure (Infrastructure as a service (Iaa. S)) • Not required for all scenarios but strongly recommended • The latest version of Azure Power. Shell Microsoft Confidential 27

Azure Net 1 AD FS and Proxy in Azure Filtered Azure? WAP DMZ AD FS 3 44 DC VPN CORP Web App 44 3 Client Microsoft Confidential DC 28

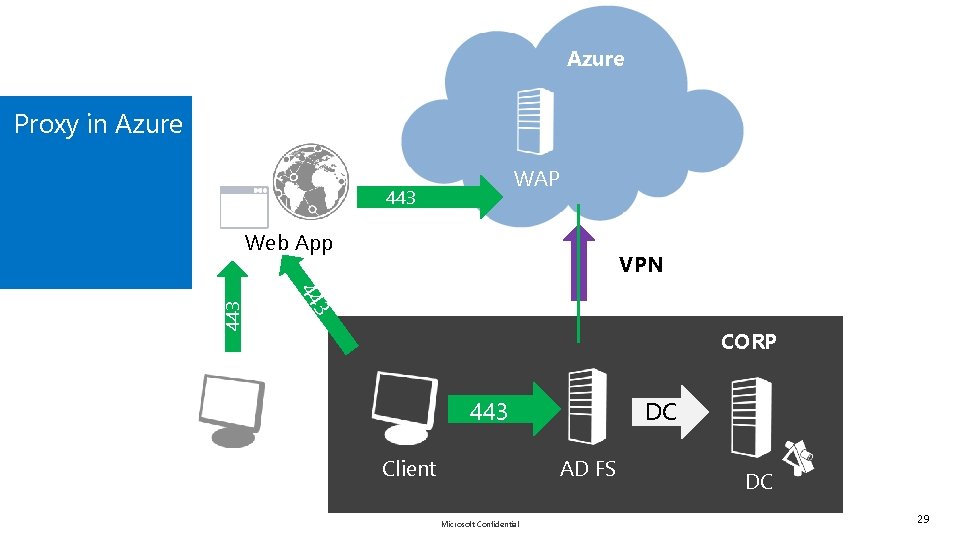
Azure Proxy in Azure WAP VPN 44 3 443 Azure ? 443 DMZ Web App CORP 443 Client DC AD FS Microsoft Confidential DC 29

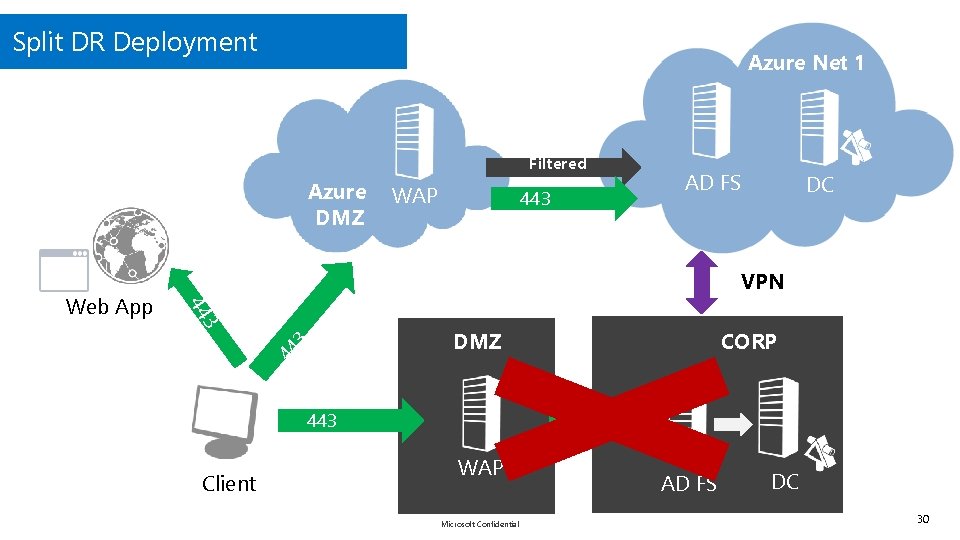
Split DR Deployment Azure Net 1 Filtered Azure DMZ 443 AD FS DC VPN 3 44 3 DMZ 44 Web App WAP 443 Client CORP 443 WAP Microsoft Confidential AD FS DC 30

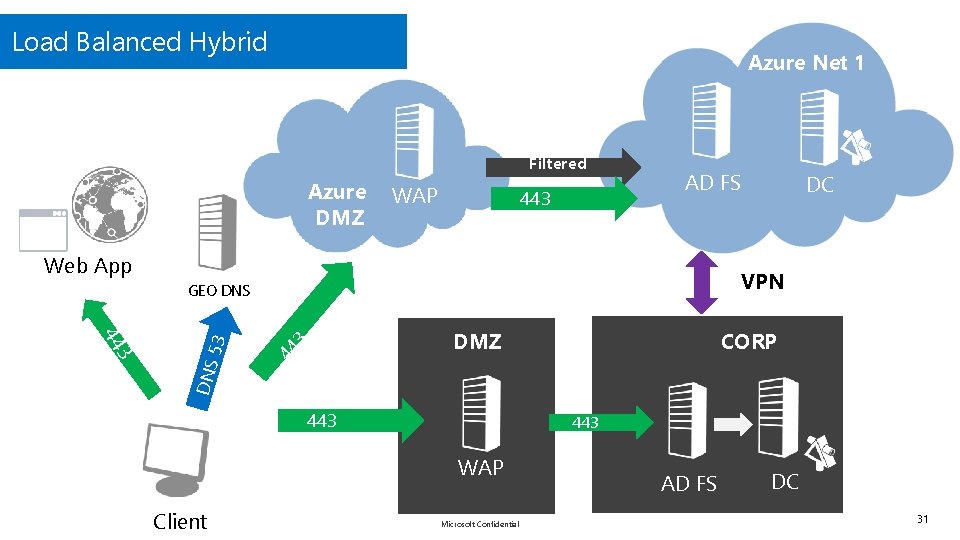
Load Balanced Hybrid Azure Net 1 Filtered Azure DMZ WAP 443 AD FS Web App VPN GEO DNS 3 44 3 DMZ CORP DNS 44 53 DC 443 WAP Client Microsoft Confidential AD FS DC 31

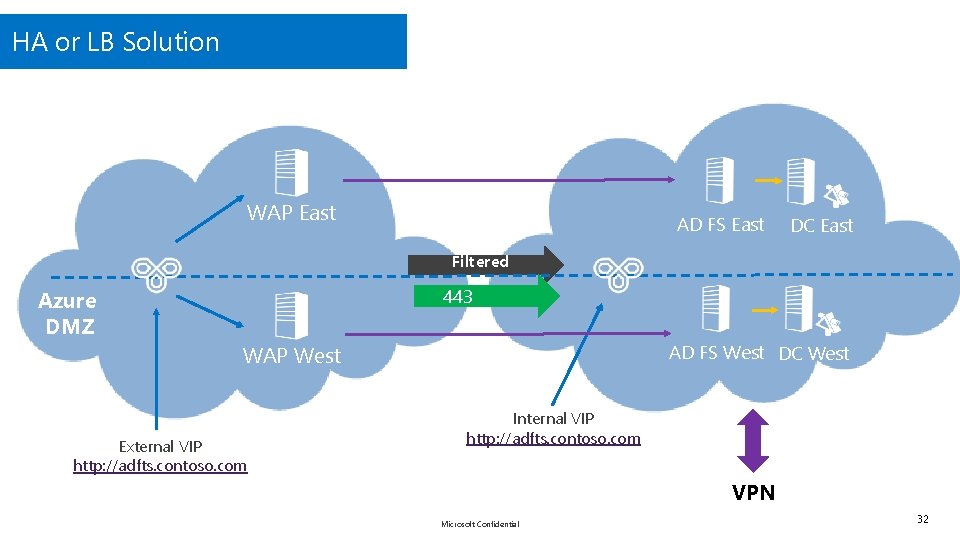
HA or LB Solution Azure Net 1 WAP East AD FS East DC East Filtered 443 Azure DMZ AD FS West DC West WAP West External VIP http: //adfts. contoso. com Internal VIP http: //adfts. contoso. com VPN Microsoft Confidential 32
