Authors Muhammad Rizwan Asghar Gyrgy Dn Daniele Miorandi








- Slides: 22

Authors: Muhammad Rizwan Asghar, György Dán, Daniele Miorandi, Imrich Chlamtac Source: IEEE Communications Surveys & Tutorials, Vol. 19, pp. 2820 -2835, 27 Jun 2017 Speaker: Kai. Fan Chien Date: 3/16/2019

§ Introduction § Smart Meter Data and Privacy § Requirements of Privacy and Security § Privacy Protection for Smart Meter Data under the Trusted Operator Model § Service-Specific Privacy Protection Under the Non-Trusted Operator Model § Conclusions 2

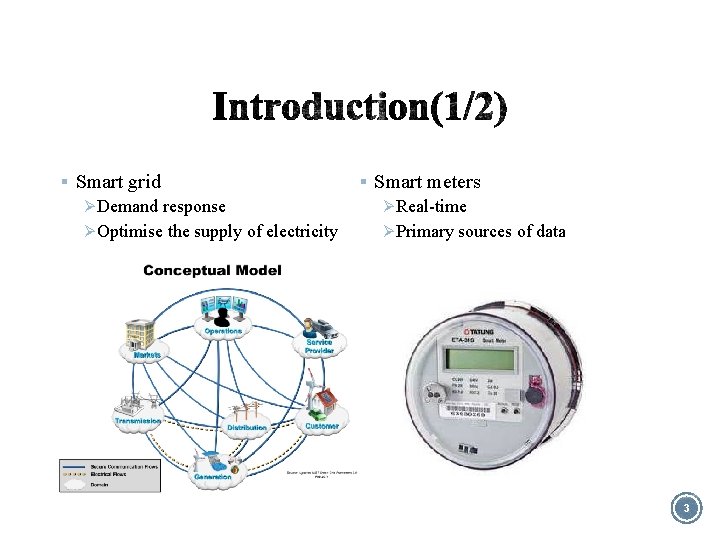
§ Smart grid Ø Demand response Ø Optimise the supply of electricity § Smart meters Ø Real-time Ø Primary sources of data 3

§ Data collected by smart meters may also serve for invading consumers’ privacy. § In this survey Ø Regulatory and policy context Ø Overview of state-of-the-art solutions Ø Provide recommendations 1. 2. 3. Billing Operations Alue-added services 4

§ Automated meters and smart meters Ø Consumption of electric energy with a variable time granularity Ø Meter Data Management System (MDMS) Ø Receive pricing information and load control commands Ø Exchange information with smart home appliances § Intervals of 15 minutes 5

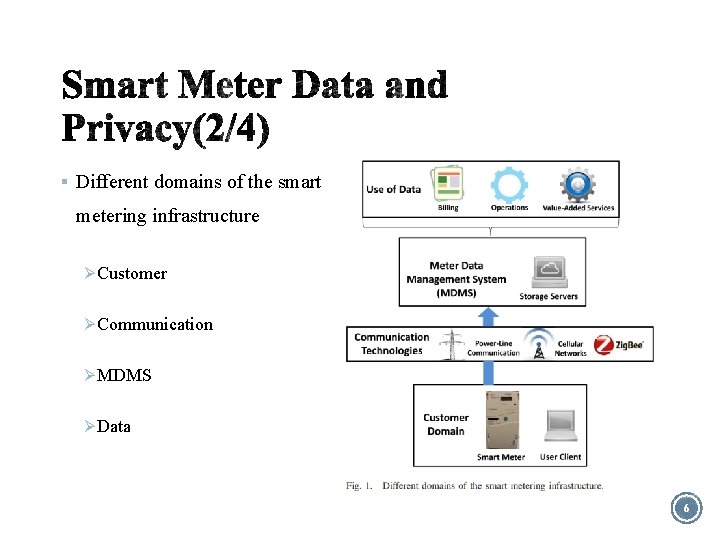
§ Different domains of the smart metering infrastructure Ø Customer Ø Communication Ø MDMS Ø Data 6

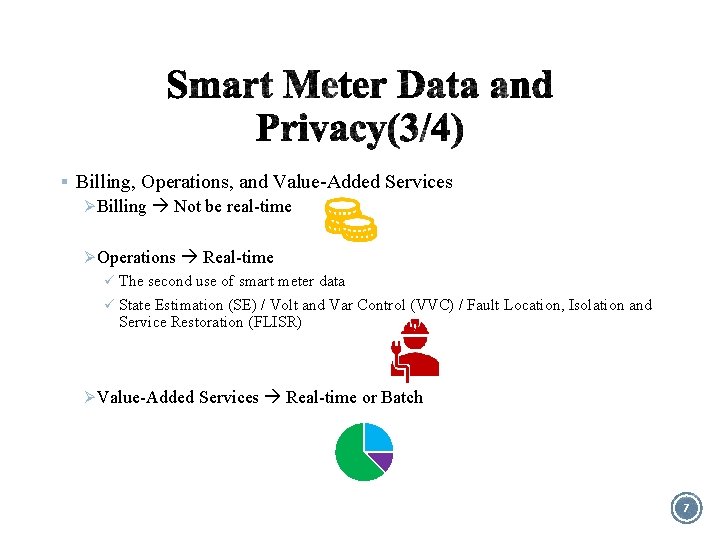
§ Billing, Operations, and Value-Added Services Ø Billing Not be real-time Ø Operations Real-time ü The second use of smart meter data ü State Estimation (SE) / Volt and Var Control (VVC) / Fault Location, Isolation and Service Restoration (FLISR) Ø Value-Added Services Real-time or Batch 7

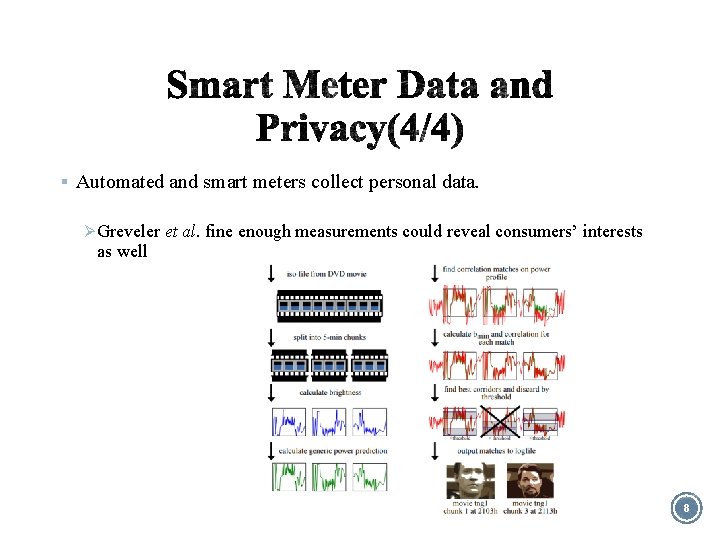
§ Automated and smart meters collect personal data. Ø Greveler et al. fine enough measurements could reveal consumers’ interests as well 8

§ Privacy legislation for smart meter data Ø EU ü Data are necessary ü Cannot be used for a different purpose Ø NIST 9

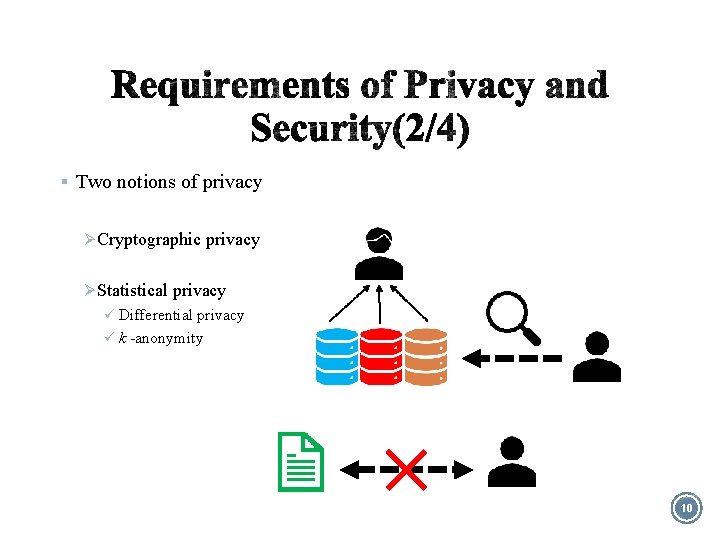
§ Two notions of privacy Ø Cryptographic privacy Ø Statistical privacy ü Differential privacy ü k -anonymity 10

§ Requirements for privacy-preserving protocols for smart meter data management Ø Confidentiality Ø Integrity Ø Authenticity Ø Non-Repudiation Ø Auditability 11

§ Preserving privacy depends significantly on the attacker model Ø Honest-but-curious, also called semi-honest Ø Malicious attacker 12

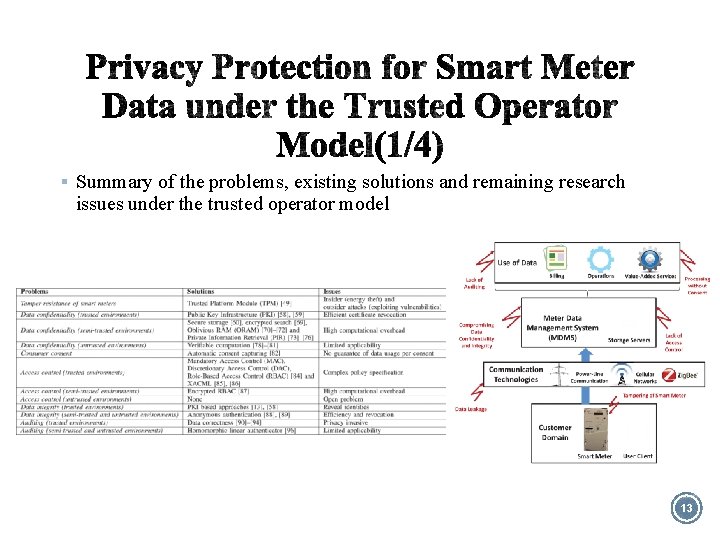
§ Summary of the problems, existing solutions and remaining research issues under the trusted operator model 13

§ Tamper-resistance of smart meters Ø Trusted Platform Module (TPM) § Electricity theft Ø Mc. Laughlin, Podkuiko and Mc. Daniel describe methods, including password extraction and storage tampering Ø Automated meters for electricity and for gas were recently found tampered within the U. K 14

§ Data confidentiality and trust models Ø Public Key Infrastructure (PKI) Ø Baumeister investigated what PKI architecture would be most suitable to meet the requirements Ø Main issue with the PKI is efficient certificate revocation Ø By adding random noise to the data ? ? ? 15

§ Consent and Access Control Ø Mandatory Access Control (MAC). Ø Discretionary Access Control (DAC). Ø Role-Based Access Control (RBAC). Ø e. Xtensible Access Control Markup Language (XACML) § Data Integrity and Auditing 16

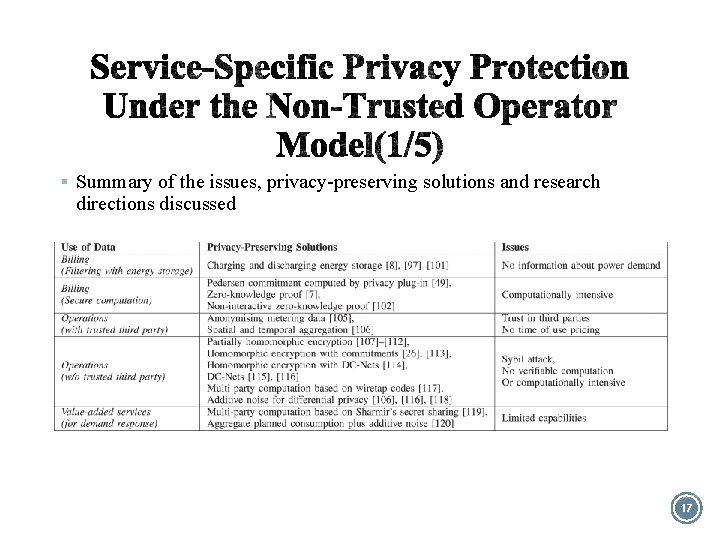
§ Summary of the issues, privacy-preserving solutions and research directions discussed 17

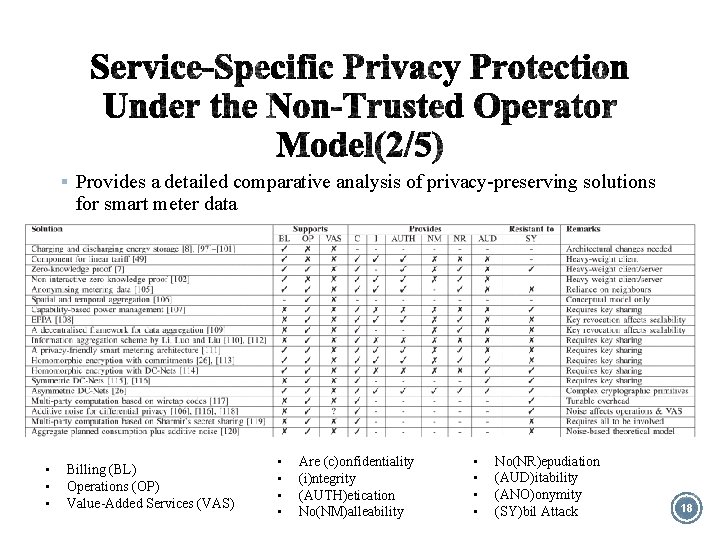
§ Provides a detailed comparative analysis of privacy-preserving solutions for smart meter data • • • Billing (BL) Operations (OP) Value-Added Services (VAS) • • Are (c)onfidentiality (i)ntegrity (AUTH)etication No(NM)alleability • • No(NR)epudiation (AUD)itability (ANO)onymity (SY)bil Attack 18

§ Privacy-Preserving Billing Ø Filtering With Energy Storage for Statistical Privacy ü The energy storage protects customers’ privacy by hiding the use of individual appliances Ø Secure Computation for Cryptographic Privacy ü Jawurek et al. propose a scheme based on Pedersen commitments ü Non-Interactive Zero-Knowledge proof (NIZK) ü Anonymous credential system 19

§ Privacy-preserving operations Ø With a trusted third party ü Aggregation algorithms for cryptographic privacy Ø Without a trusted third party ü Homomorphic encryption ü Providing Statistical Privacy ü Privacy Economics 20

§ Value-Added Services Ø Demand-response Ø Identifying appliance level anomalies Ø Optimise the electricity consumption of a household 21

§ Privacy-preserving meter data delivery and management § Meter data collection for the three application areas Ø Billing Ø Operations Ø Alue-added services § Trusted Operator Model and non-Trusted Operator Model 22
 Gyrgy
Gyrgy Gyrgy
Gyrgy Faiza asghar
Faiza asghar Dr faiza asghar death
Dr faiza asghar death Hyperparathyroidism causes
Hyperparathyroidism causes Nadeem asghar
Nadeem asghar Dr raja rizwan
Dr raja rizwan Saddle type pontic
Saddle type pontic Dr raja rizwan
Dr raja rizwan Rizwan qamar
Rizwan qamar Bait rizwan
Bait rizwan Dua e sabah
Dua e sabah Allahumma salli ala muhammad
Allahumma salli ala muhammad Renina
Renina Daniele durante
Daniele durante Contact slide 2
Contact slide 2 Corneglio 3e
Corneglio 3e Daniele brotto
Daniele brotto Daniele gualdi
Daniele gualdi Pamela zullino
Pamela zullino Rocce di fiume per acquario
Rocce di fiume per acquario Daniele novara conflitti
Daniele novara conflitti Anna e daniele giocano con due dadi
Anna e daniele giocano con due dadi