A New ForwardSecure Digital Signature Scheme Source Advances






- Slides: 20

A New Forward-Secure Digital Signature Scheme Source : Advances in Cryptology - Asiacrypt 2000, Lecture Notes in Computer Science, p. 116 -129 Authors : Michel Abdalla, Leonid Reyzin Date : 2001/8/16 Speaker : Ya-Ping Pan 1

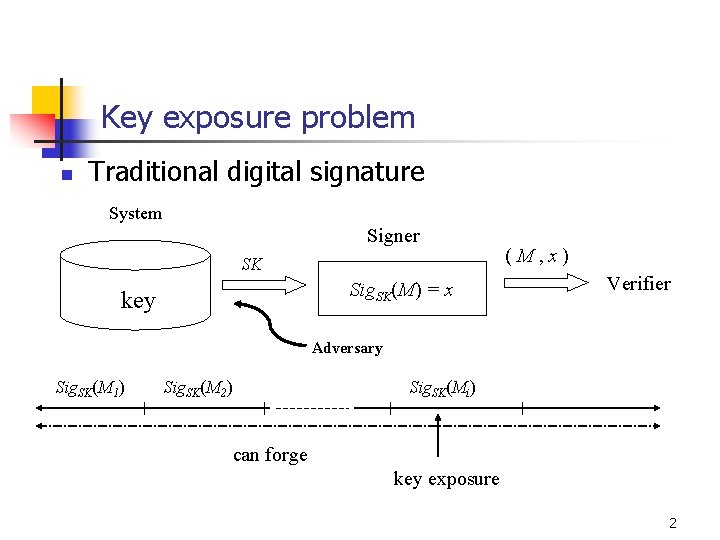
Key exposure problem n Traditional digital signature System Signer SK Sig. SK(M) = x key (M, x) Verifier Adversary Sig. SK(M 1) Sig. SK(M 2) Sig. SK(Mi) can forge key exposure 2

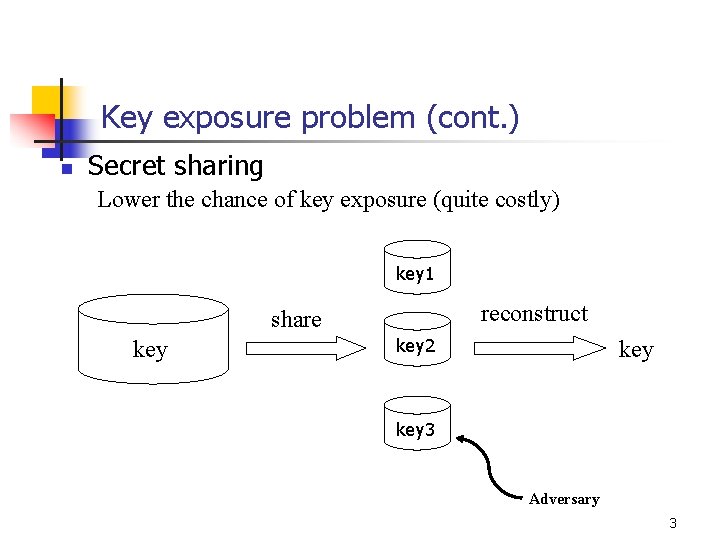
Key exposure problem (cont. ) n Secret sharing Lower the chance of key exposure (quite costly) key 1 reconstruct share key 2 key 3 Adversary 3

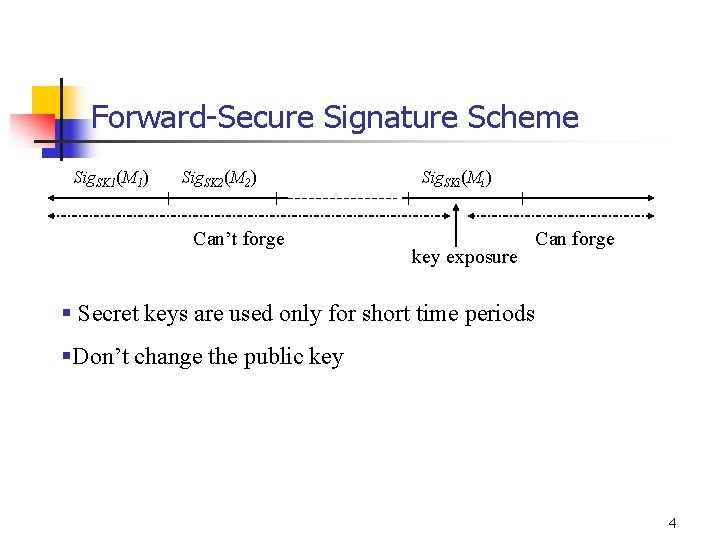
Forward-Secure Signature Scheme Sig. SK 1(M 1) Sig. SK 2(M 2) Can’t forge Sig. SKi(Mi) key exposure Can forge § Secret keys are used only for short time periods §Don’t change the public key 4

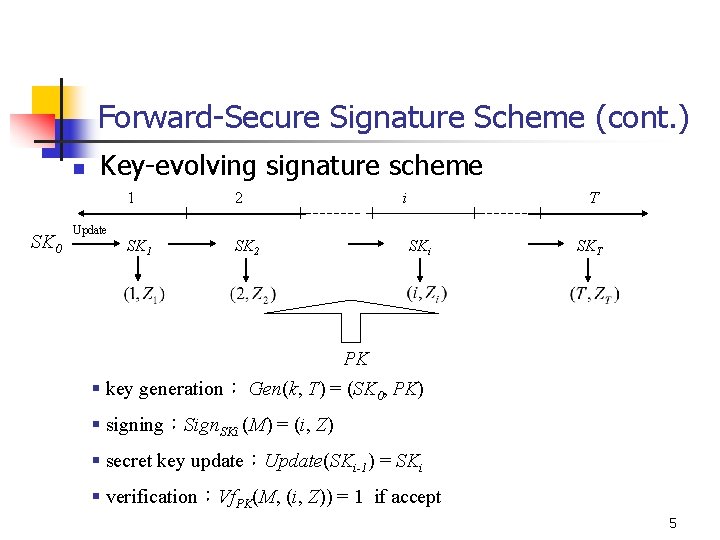
Forward-Secure Signature Scheme (cont. ) n SK 0 Key-evolving signature scheme 1 2 SK 1 SK 2 i T Update SKi SKT PK § key generation: Gen(k, T) = (SK 0, PK) § signing:Sign. SKi (M) = (i, Z) § secret key update:Update(SKi-1) = SKi § verification:Vf. PK(M, (i, Z)) = 1 if accept 5

Forward-Secure Signature Scheme (cont. ) § Anderson (ACM 1997) n n the size of secret key grows linearly with T Bellare and Miner (Crypto 99) n key size is very large 6

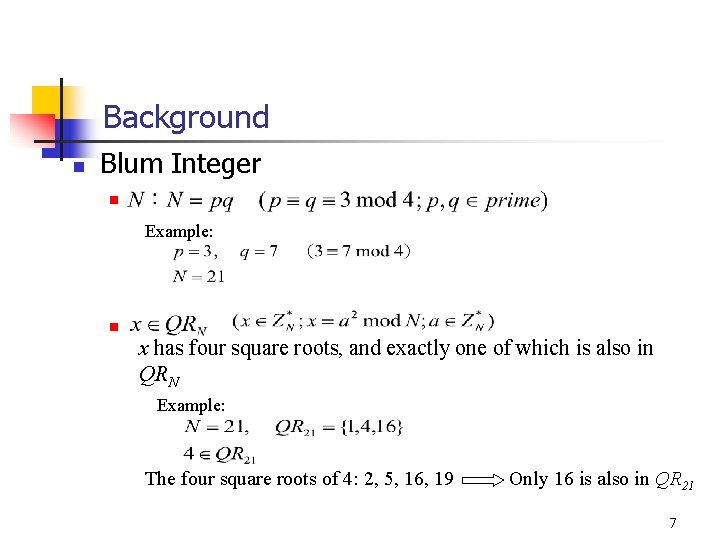
Background n Blum Integer n Example: n x has four square roots, and exactly one of which is also in QRN Example: The four square roots of 4: 2, 5, 16, 19 Only 16 is also in QR 21 7

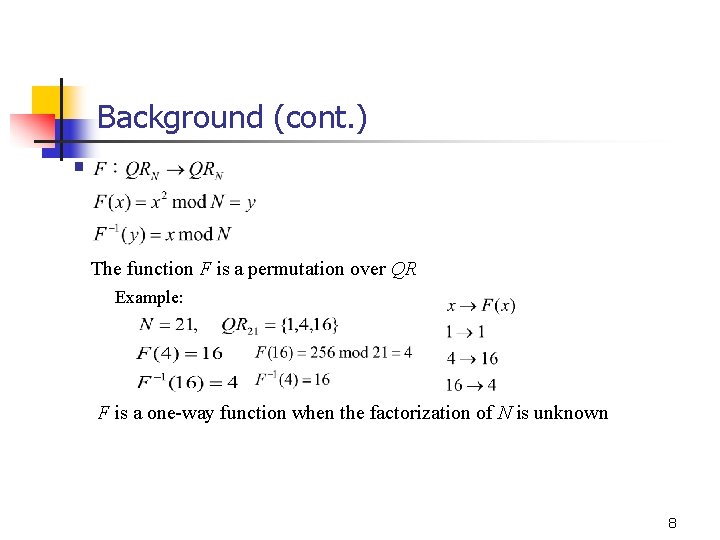
Background (cont. ) § The function F is a permutation over QR Example: F is a one-way function when the factorization of N is unknown 8

Background (cont. ) § Example: § Compute and : 9

Background (cont. ) § , l-bit binary string Example: 10

Background (cont. ) § Know N and U : (knowing p and q, it can be efficiently computed) Example: 11

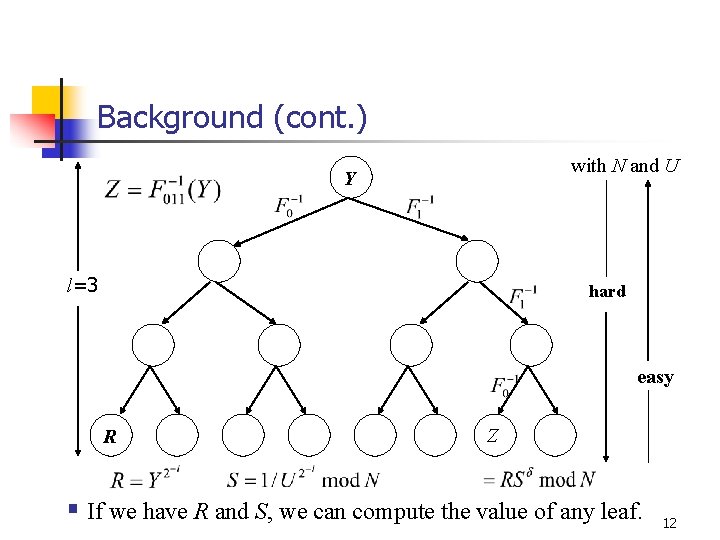
Background (cont. ) with N and U Y l=3 hard easy R Z § If we have R and S, we can compute the value of any leaf. 12

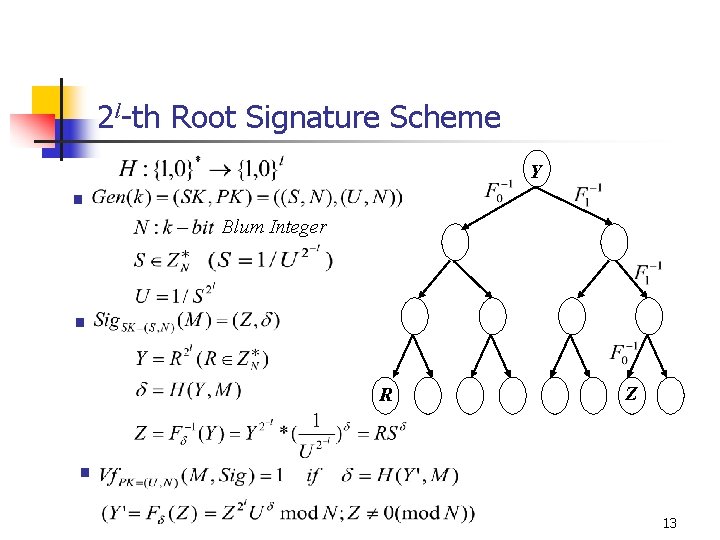
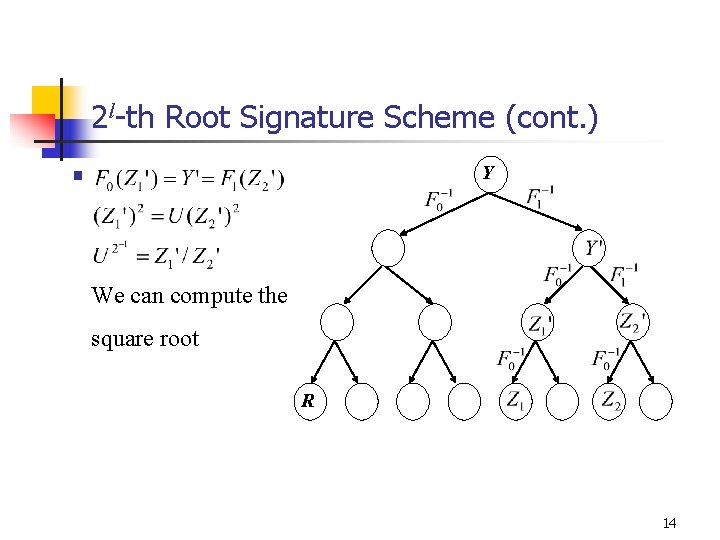
2 l-th Root Signature Scheme Y § Blum Integer § R Z § 13

2 l-th Root Signature Scheme (cont. ) § Y We can compute the square root R 14

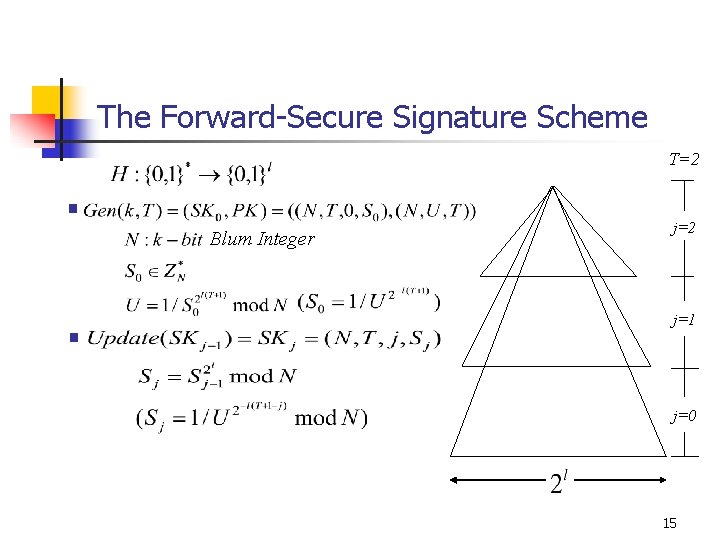
The Forward-Secure Signature Scheme T=2 § Blum Integer § j=2 j=1 j=0 15

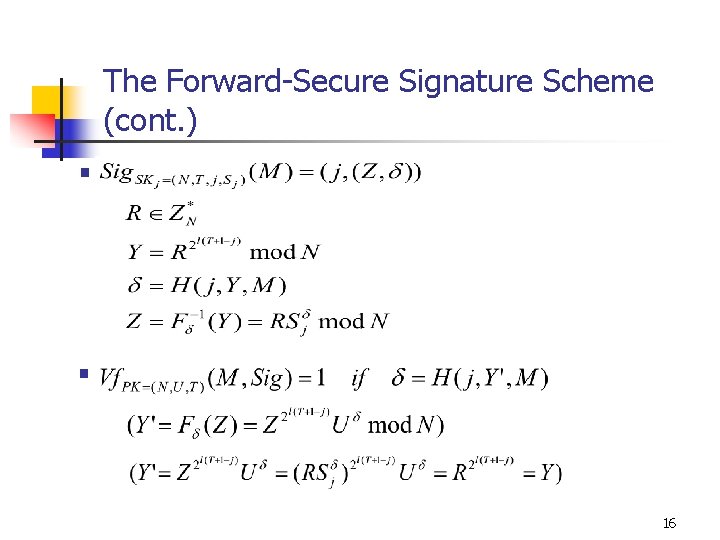
The Forward-Secure Signature Scheme (cont. ) § § 16

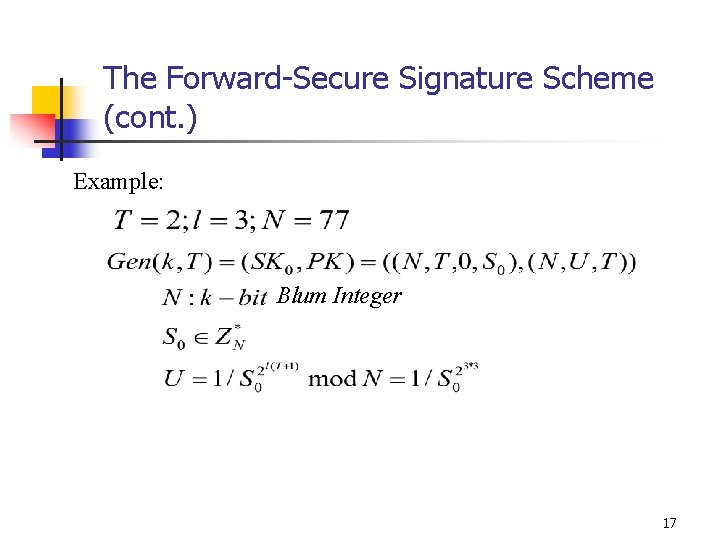
The Forward-Secure Signature Scheme (cont. ) Example: Blum Integer 17

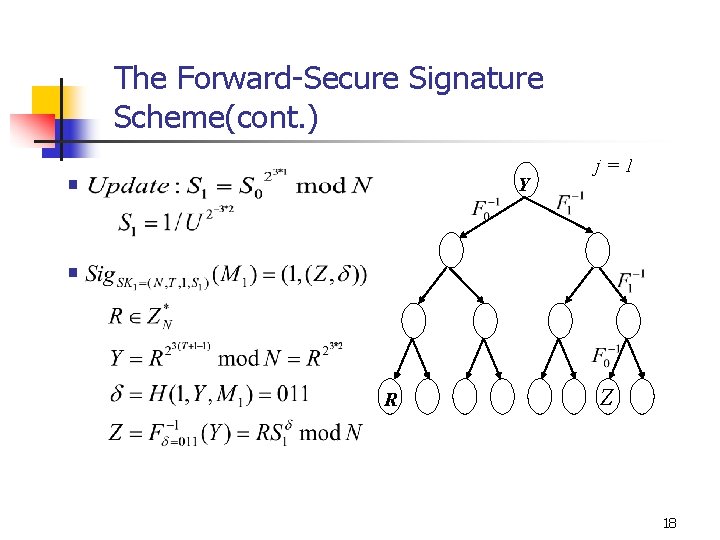
The Forward-Secure Signature Scheme(cont. ) § Y j=1 § R Z 18

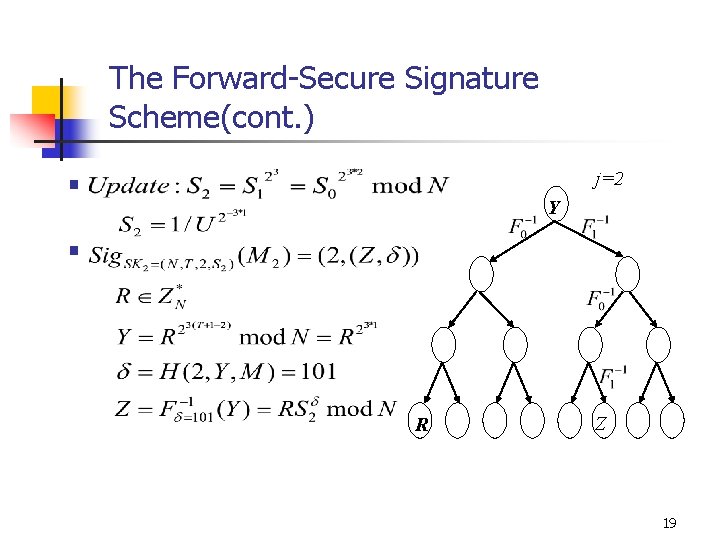
The Forward-Secure Signature Scheme(cont. ) j=2 § Y § R Z 19

Conclusions n n The scheme is based on the hardness of factoring forge successfully compute square root factor the Blum Integer N When k is large enough, the insecurity of the scheme is low slightly better security, shorter keys 20