2014 FIDO Alliance Who What Why 142 growing

















- Slides: 30

© 2014 FIDO Alliance

Who… What… Why…


142+ & growing…

142+ & growing…

To Change Authentication Online by: (a) Developing unencumbered Specifications that define interoperable mechanisms that supplant reliance on passwords (b) Operating programs to help ensure industry adoption (c) Submitting mature Specifications formal standardization

FIDO Alliance’s Role… • • • “Paper” Specifications Interoperability and Conformance testing Trademark licensing against criteria Thought leadership, nurture ecosystem The Alliance does not ship products! Implementations left to commercial vendors

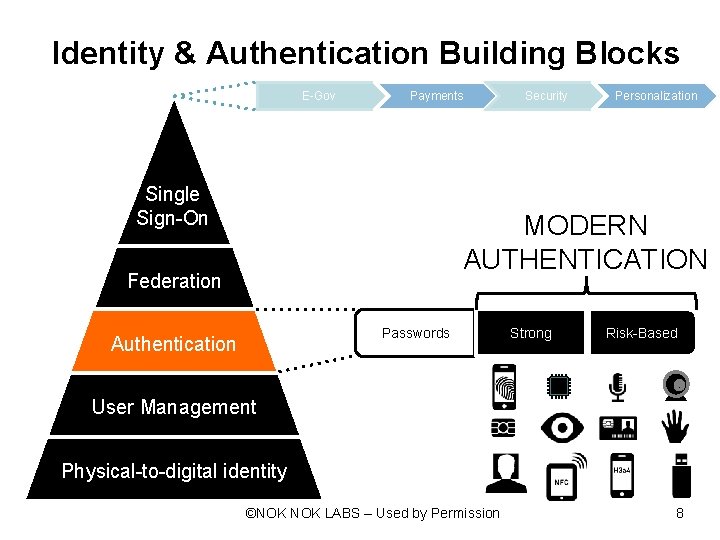
Identity & Authentication Building Blocks E-Gov Payments Single Sign-On Security Personalization MODERN AUTHENTICATION Federation Passwords Authentication Strong Risk-Based User Management Physical-to-digital identity ©NOK LABS – Used by Permission 8

Why Authentication is Cybersecurity Priority #1 Poor authentication mechanisms are a commonly exploited vector of attack by adversaries; the 2013 Data Breach Investigations Report (conducted by Verizon in concert with the U. S. Department of Homeland Security) noted that 76% of 2012 network intrusions exploited weak or stolen credentials. -- NIST Roadmap for Improving Critical Infrastructure Cybersecurity, 12 -Feb-2014

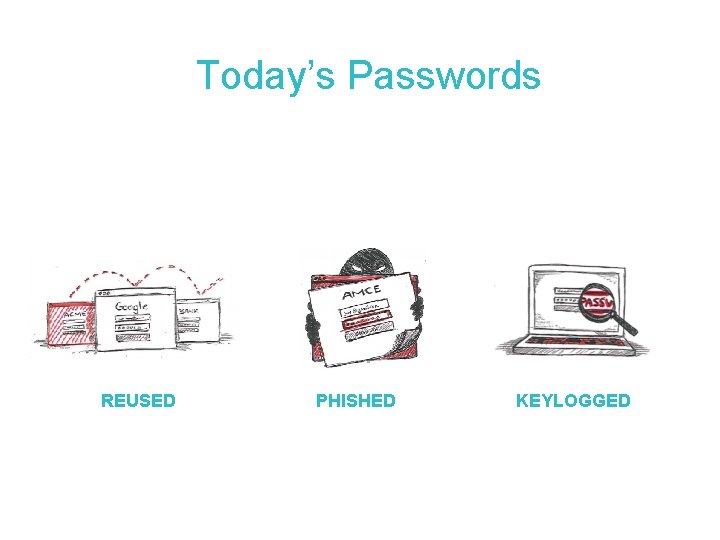
Today’s Passwords REUSED PHISHED KEYLOGGED

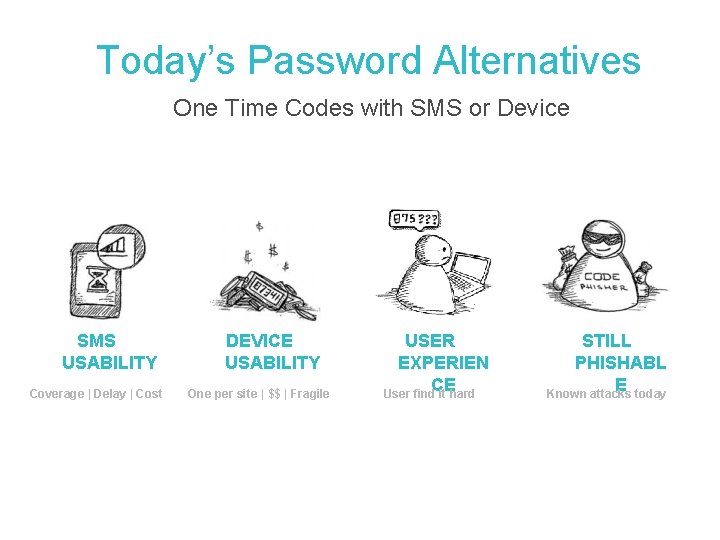
Today’s Password Alternatives One Time Codes with SMS or Device SMS USABILITY Coverage | Delay | Cost DEVICE USABILITY One per site | $$ | Fragile USER EXPERIEN CE User find it hard STILL PHISHABL E Known attacks today

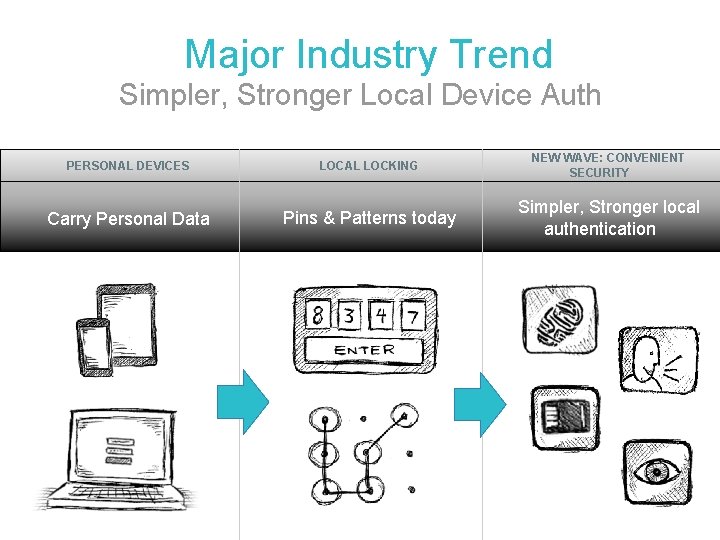
Major Industry Trend Simpler, Stronger Local Device Auth PERSONAL DEVICES LOCAL LOCKING NEW WAVE: CONVENIENT SECURITY Carry Personal Data Pins & Patterns today Simpler, Stronger local authentication

Putting It Together The problem: Simpler, Stronger online The trend: Simpler, Stronger local device auth Why not: Use local device auth for online auth? This is the core idea behind FIDO standards!

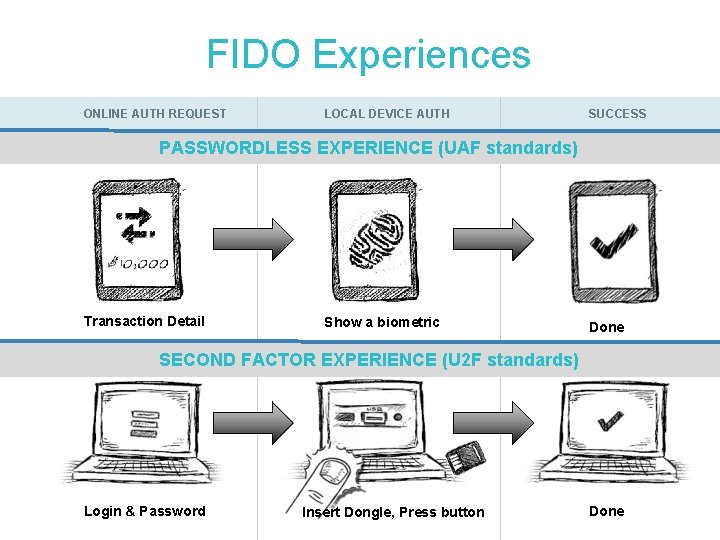
FIDO Experiences ONLINE AUTH REQUEST LOCAL DEVICE AUTH SUCCESS PASSWORDLESS EXPERIENCE (UAF standards) Transaction Detail Show a biometric Done SECOND FACTOR EXPERIENCE (U 2 F standards) Login & Password Insert Dongle, Press button Done

State of Market Adoption

Version 1. 0 is in Public Review

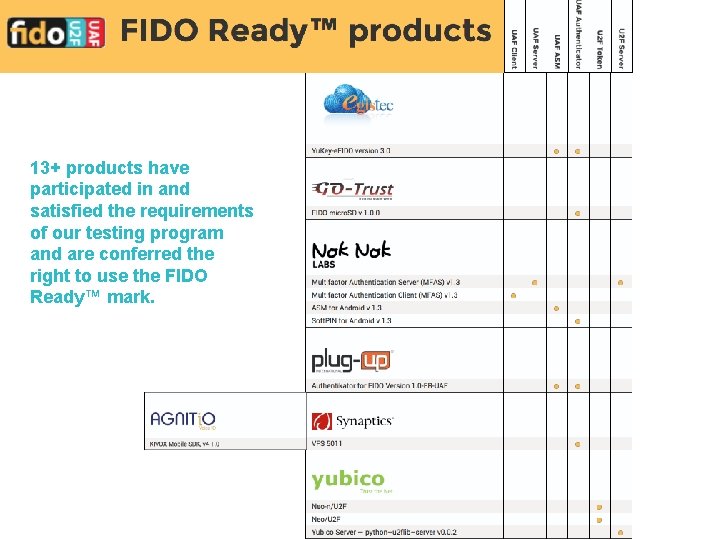
13+ products have participated in and satisfied the requirements of our testing program and are conferred the right to use the FIDO Ready™ mark.

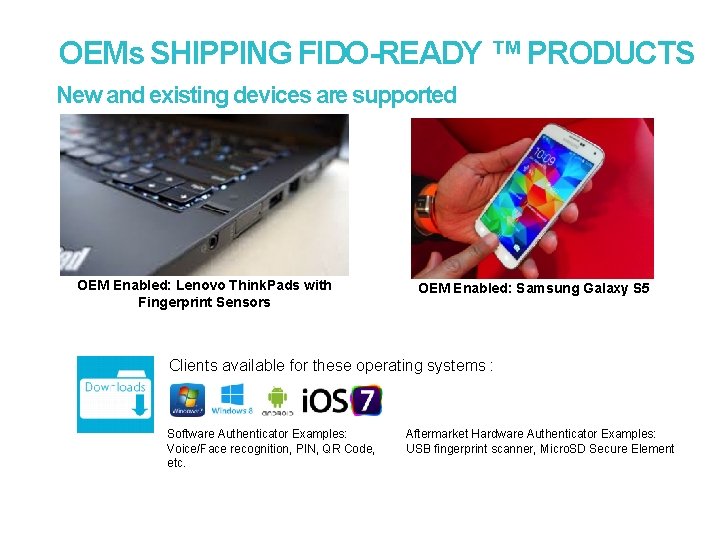
OEMs SHIPPING FIDO-READY ™ PRODUCTS New and existing devices are supported OEM Enabled: Lenovo Think. Pads with Fingerprint Sensors OEM Enabled: Samsung Galaxy S 5 Clients available for these operating systems : Software Authenticator Examples: Voice/Face recognition, PIN, QR Code, etc. Aftermarket Hardware Authenticator Examples: USB fingerprint scanner, Micro. SD Secure Element

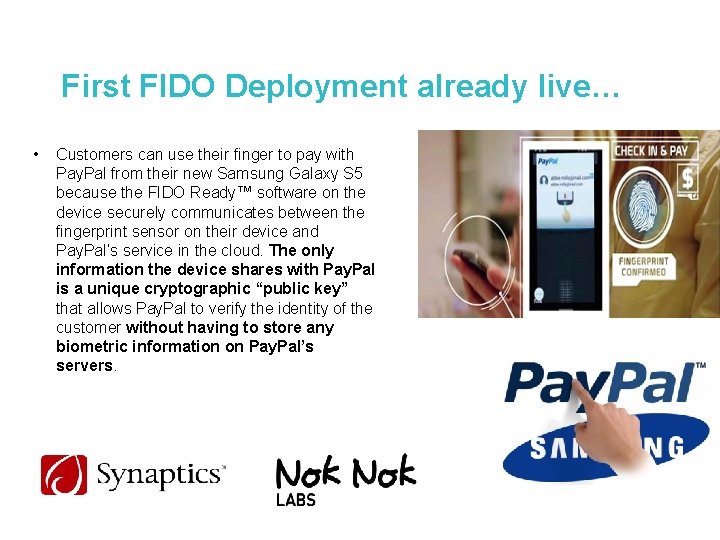
First FIDO Deployment already live… • Customers can use their finger to pay with Pay. Pal from their new Samsung Galaxy S 5 because the FIDO Ready™ software on the device securely communicates between the fingerprint sensor on their device and Pay. Pal’s service in the cloud. The only information the device shares with Pay. Pal is a unique cryptographic “public key” that allows Pay. Pal to verify the identity of the customer without having to store any biometric information on Pay. Pal’s servers.

From July 2014… • • • Alipay – formerly a part of Alibaba Group in China Processed $519 Billion in transactions in 2013 Launched FIDO-based payments using Galaxy S 5

How it works

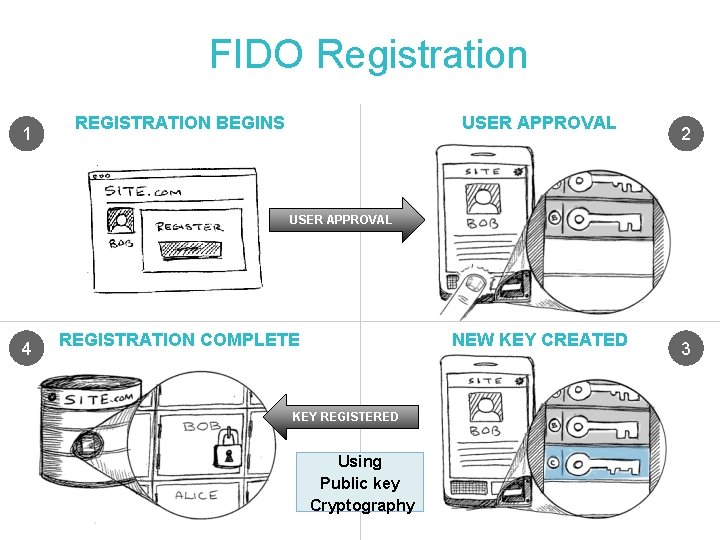
FIDO Registration 1 REGISTRATION BEGINS USER APPROVAL 2 USER APPROVAL 4 REGISTRATION COMPLETE NEW KEY CREATED KEY REGISTERED Using Public key Cryptography 3

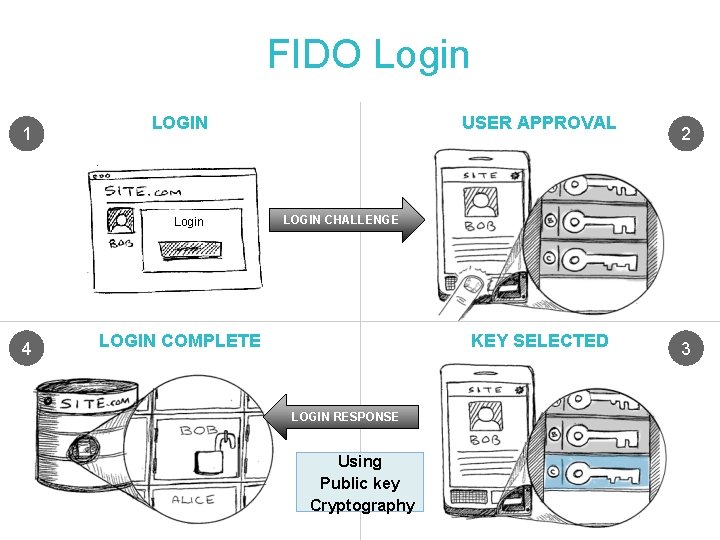
FIDO Login 1 LOGIN Login 4 USER APPROVAL 2 LOGIN CHALLENGE LOGIN COMPLETE KEY SELECTED LOGIN RESPONSE Using Public key Cryptography 3

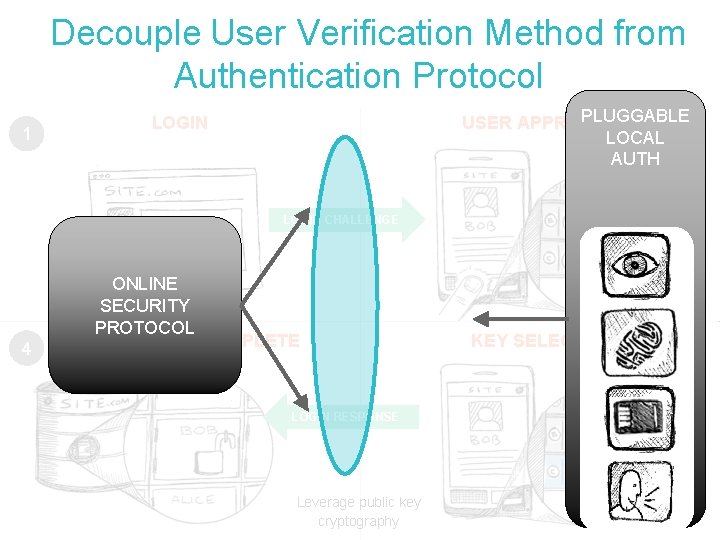
Decouple User Verification Method from Authentication Protocol 1 PLUGGABLE USER APPROVAL LOCAL 2 AUTH LOGIN CHALLENGE 4 ONLINE SECURITY PROTOCOL REGISTRATION COMPLETE LOGIN RESPONSE Leverage public key cryptography KEY SELECTED 3

No 3 rd Party in the Protocol

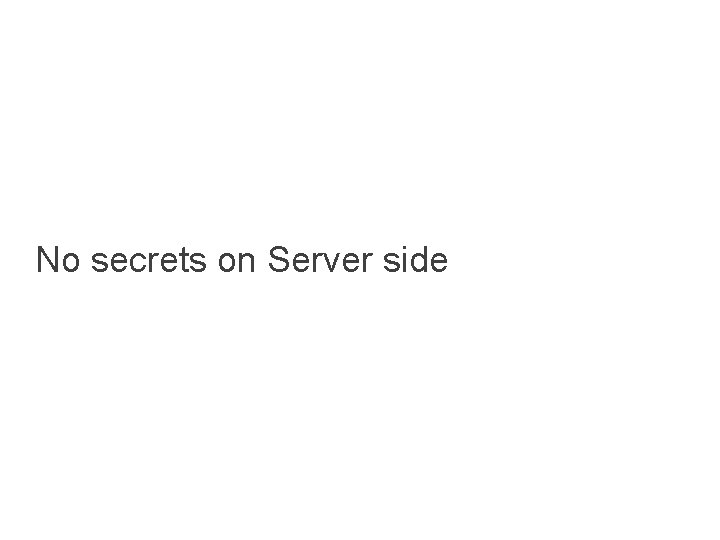
No secrets on Server side

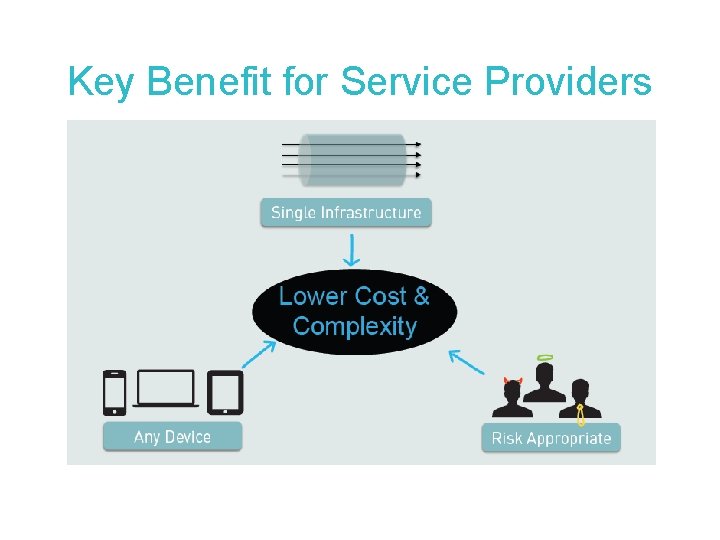
Key Benefit for Service Providers

FIDO’s Focus on User Privacy • Biometric data (if used) never leaves device • No link-ability between Services • No link-ability between Accounts

Call to Action • FIDO is ready for use o launch a Proof-of-Concept & Pilot • Get involved: o Adapt your strategy & roadmap to include FIDO o Join the Alliance – we are non-profit & volunteer § Contact Brett Mc. Dowell – brett@fidoalliance. org

THANK YOU
 Andreas carlsson bye bye bye
Andreas carlsson bye bye bye Fido metadata service
Fido metadata service Fido.jbv
Fido.jbv Informazioni post-fido
Informazioni post-fido Istruttoria di fido fasi
Istruttoria di fido fasi Pratica elettronica di fido
Pratica elettronica di fido Fido bancario
Fido bancario Sistema creditizio
Sistema creditizio Why do cells divide? *
Why do cells divide? * Why do cells divide, instead of simply growing larger?
Why do cells divide, instead of simply growing larger? Why do cells divide instead of growing larger
Why do cells divide instead of growing larger Dont ask why why why
Dont ask why why why Prime number 101
Prime number 101 Pl94-142
Pl94-142 Pl 94-142
Pl 94-142 18 numero romano
18 numero romano Stanford cs 142
Stanford cs 142 Psalms 142 meaning
Psalms 142 meaning Asu mat 142
Asu mat 142 770 000 in scientific notation
770 000 in scientific notation Dimercaperol
Dimercaperol Java critter strategy
Java critter strategy Læ 145
Læ 145 Stanford cs 142
Stanford cs 142 Convenio 142 oit
Convenio 142 oit Sfas 142
Sfas 142 Fasb 142
Fasb 142 Physics 142
Physics 142 Dicom supplement 142
Dicom supplement 142 Phys 142
Phys 142 12 742 km in miles
12 742 km in miles