The FIDO Approach to Privacy Hannes Tschofenig ARM






- Slides: 18

The FIDO Approach to Privacy Hannes Tschofenig, ARM Limited 1

Privacy by Design History • Ann Cavoukian, the former Information and Privacy Commissioner of Ontario/Canada, coined the term “Privacy by Design” back in the late 90’s. • Idea was to take privacy into account already early in the design process. • Cavoukian went a step further and developed 7 principles. • It took years to investigate the idea further and to become familiar with privacy as an engineering concept. 2

Privacy Principles https: //fidoalliance. org/wp-content/uploads/2014/12/FIDO_Alliance_Whitepaper_Privacy_Principles. pdf 3

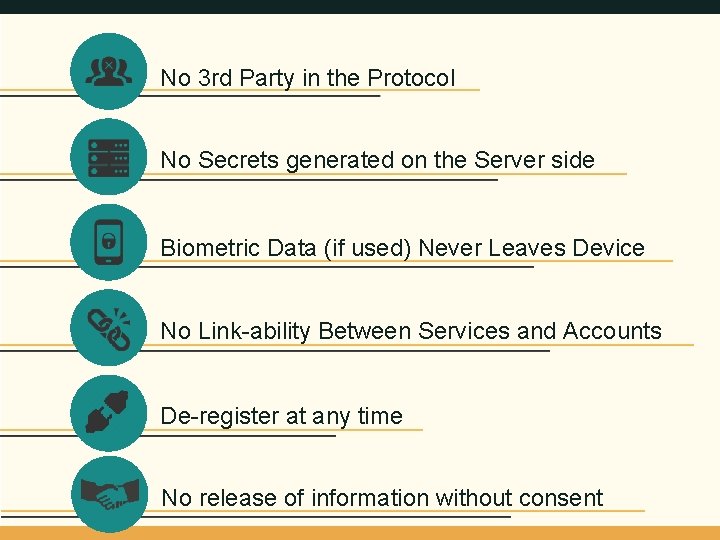
No 3 rd Party in the Protocol No Secrets generated on the Server side Biometric Data (if used) Never Leaves Device No Link-ability Between Services and Accounts De-register at any time No release of information without consent 4

FIDO & Privacy USER VERIFICATION FIDO AUTHENTICATION AUTHENTICATOR 5

FIDO REGISTRATION STEP 1 FIDO Authenticator Web App 0 6 Prepare FIDO Server

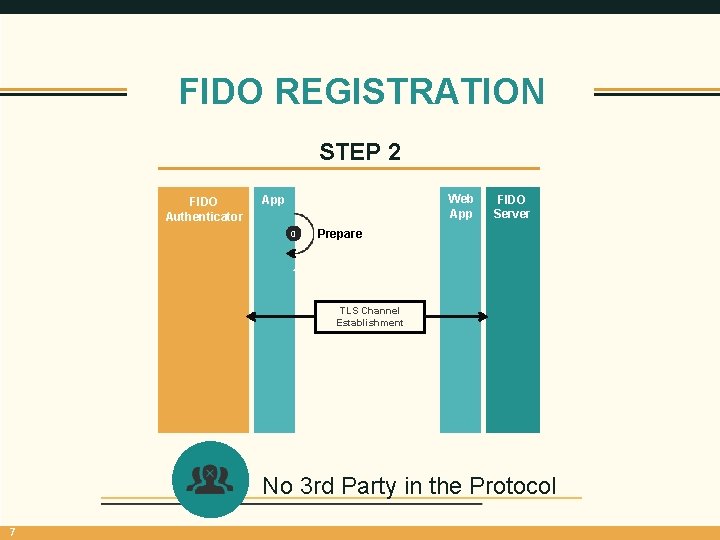
FIDO REGISTRATION STEP 2 FIDO Authenticator Web App 0 FIDO Server Prepare 1 TLS Channel Establishment No 3 rd Party in the Protocol 7

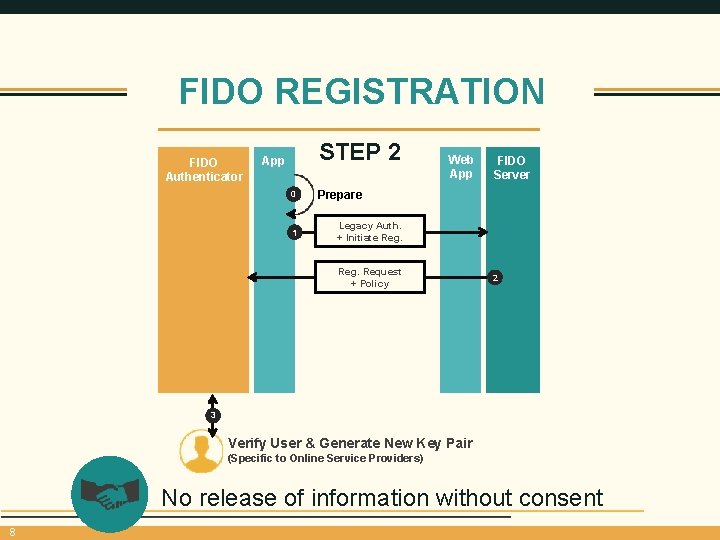
FIDO REGISTRATION FIDO Authenticator STEP 2 App 0 1 Web App FIDO Server Prepare Legacy Auth. + Initiate Reg. Request + Policy 2 3 Verify User & Generate New Key Pair (Specific to Online Service Providers) No release of information without consent 8

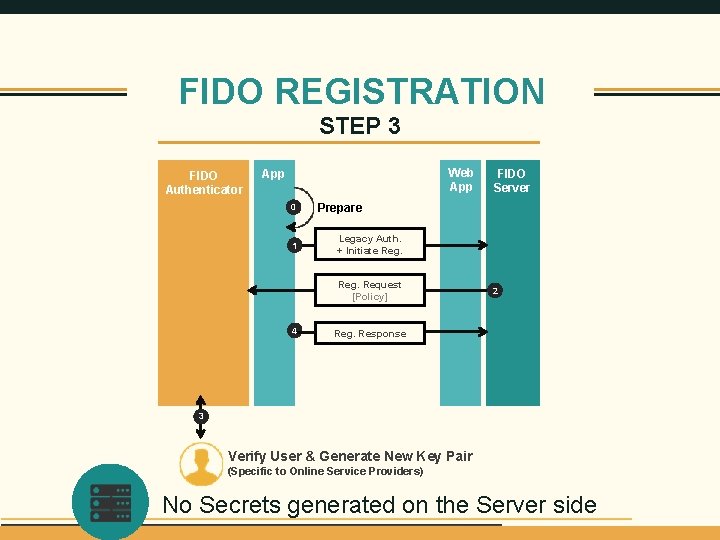
FIDO REGISTRATION STEP 3 FIDO Authenticator Web App 0 1 Prepare Legacy Auth. + Initiate Reg. Request [Policy] 4 FIDO Server 2 Reg. Response 3 Verify User & Generate New Key Pair 9 (Specific to Online Service Providers) No Secrets generated on the Server side

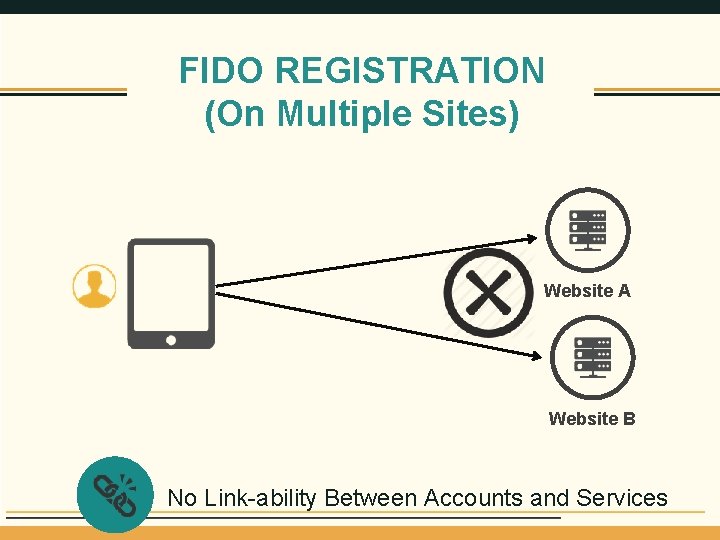
FIDO REGISTRATION (On Multiple Sites) Website A Website B No Link-ability Between Accounts and Services 10

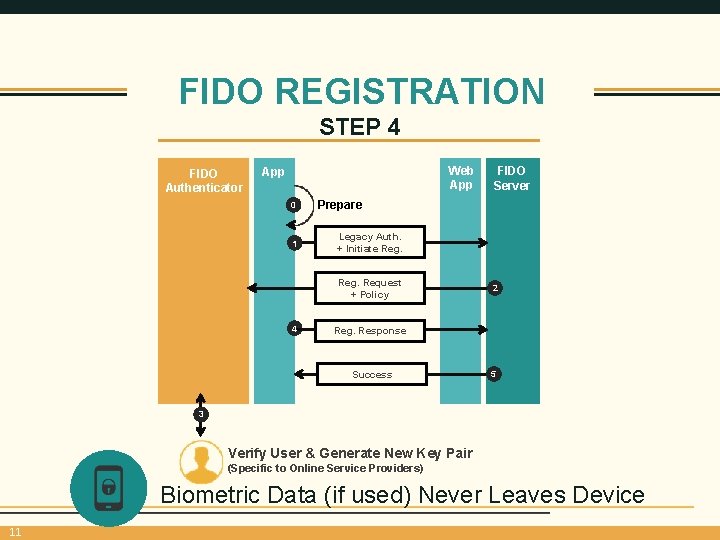
FIDO REGISTRATION STEP 4 FIDO Authenticator Web App 0 1 Prepare Legacy Auth. + Initiate Reg. Request + Policy 4 FIDO Server 2 Reg. Response Success 5 3 Verify User & Generate New Key Pair (Specific to Online Service Providers) Biometric Data (if used) Never Leaves Device 11

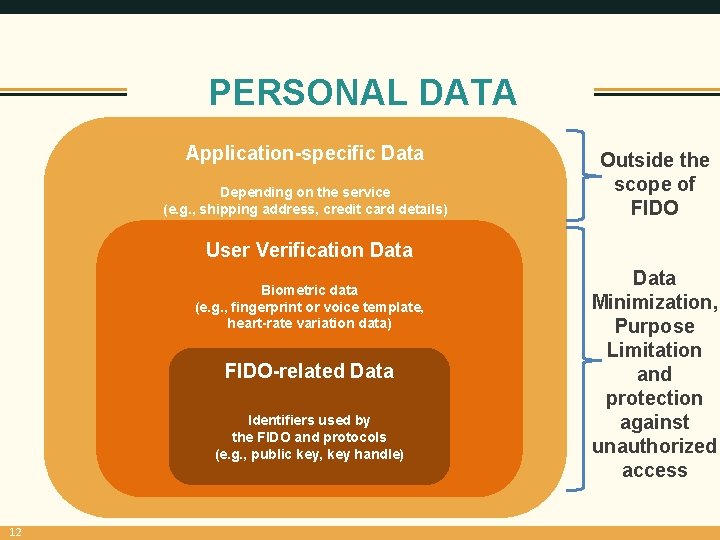
PERSONAL DATA Application-specific Data Depending on the service (e. g. , shipping address, credit card details) Outside the scope of FIDO User Verification Data Biometric data (e. g. , fingerprint or voice template, heart-rate variation data) FIDO-related Data Identifiers used by the FIDO and protocols (e. g. , public key, key handle) 12 Data Minimization, Purpose Limitation and protection against unauthorized access

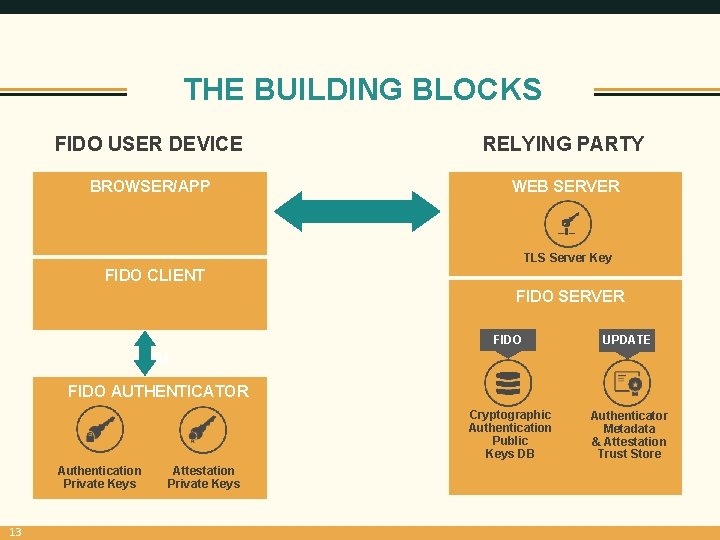
THE BUILDING BLOCKS FIDO USER DEVICE RELYING PARTY BROWSER/APP WEB SERVER TLS Server Key FIDO CLIENT FIDO SERVER FIDO UPDATE Cryptographic Authentication Public Keys DB Authenticator Metadata & Attestation Trust Store ASM FIDO AUTHENTICATOR Authentication Private Keys 13 Attestation Private Keys

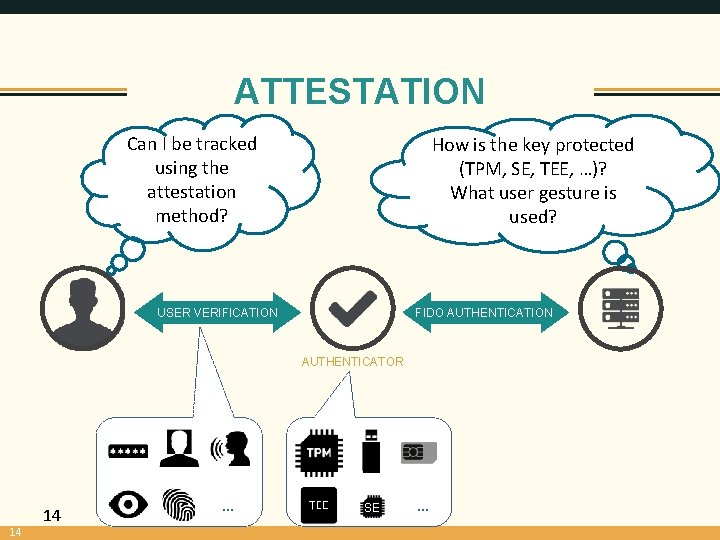
ATTESTATION Can I be tracked using the attestation method? How is the key protected (TPM, SE, TEE, …)? What user gesture is used? USER VERIFICATION FIDO AUTHENTICATION AUTHENTICATOR 14 14 … SE …

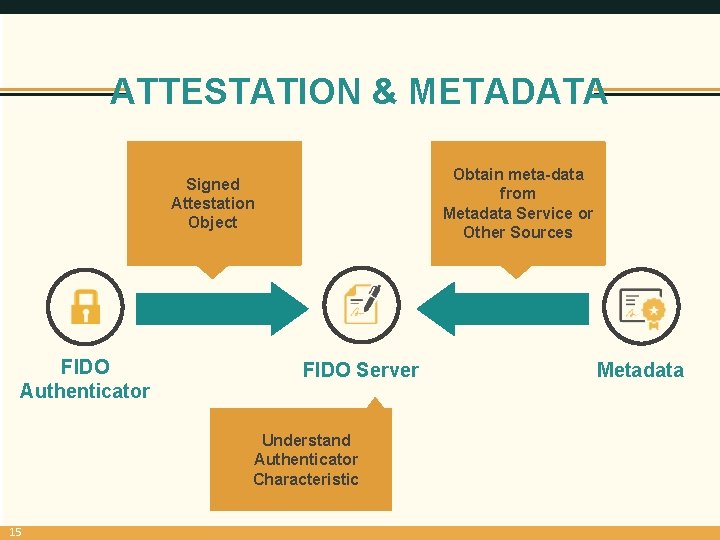
ATTESTATION & METADATA Obtain meta-data from Metadata Service or Other Sources Signed Attestation Object FIDO Authenticator FIDO Server Understand Authenticator Characteristic 15 Metadata

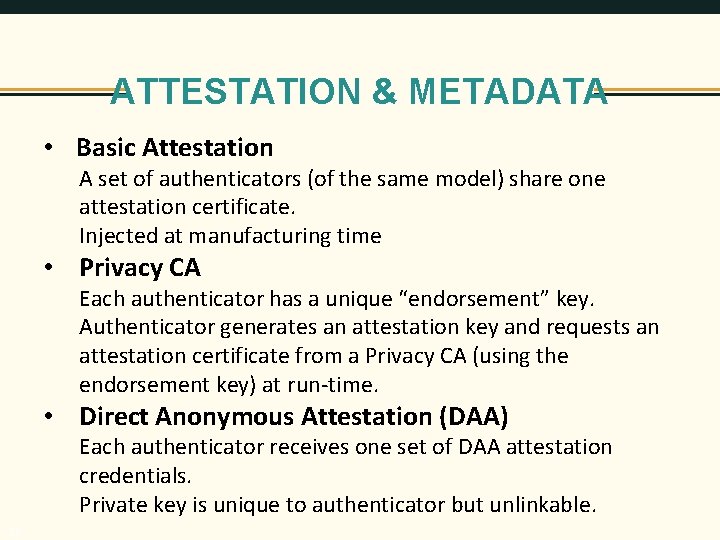
ATTESTATION & METADATA • Basic Attestation A set of authenticators (of the same model) share one attestation certificate. Injected at manufacturing time • Privacy CA Each authenticator has a unique “endorsement” key. Authenticator generates an attestation key and requests an attestation certificate from a Privacy CA (using the endorsement key) at run-time. • Direct Anonymous Attestation (DAA) Each authenticator receives one set of DAA attestation credentials. Private key is unique to authenticator but unlinkable. 16

Mapping to Regulatory Requirements • FIDO privacy principles guided the work inside the FIDO Alliance on technical specifications. • Interoperability tests and certification programs verify implementations. • Regulation impacts those who deploy services. • Intentionally, the FIDO principles are more detailed versions of already existing regulatory requirements. • Upcoming whitepaper explains the regulatory requirements to FIDO-offered functionality. • Offers mapping based on the European Data Protection Directive (95/46/EC) and the Identity Ecosystem Steering Group (IDESG) privacy principles. 17

Summary • With the work in FIDO we have been trying to exercise the privacy by design philosophy. • Whitepaper explains the privacy principles. Those principles have been taken into account during the work on the technical specifications. • Unique privacy characteristics: • User verification happens locally at the Authenticator • No centrally created or managed credentials. • Reduced tracking capability. 18
 Cvs privacy awareness and hipaa training answers
Cvs privacy awareness and hipaa training answers Advantages and disadvantages of second class levers
Advantages and disadvantages of second class levers Disadvantages of second class levers
Disadvantages of second class levers Linker arm left arm
Linker arm left arm Approach arm of bar clasp
Approach arm of bar clasp Intracoronal direct retainer
Intracoronal direct retainer How do machines make work easier
How do machines make work easier Fido metadata service
Fido metadata service Pratica elettronica di fido
Pratica elettronica di fido Fido.jbv
Fido.jbv Fido bancario
Fido bancario Informazioni post-fido
Informazioni post-fido Sconfinamento fido segnalazione
Sconfinamento fido segnalazione Istruttoria di fido
Istruttoria di fido Hannes verlis
Hannes verlis Hannes pretorius
Hannes pretorius Hannes wagner
Hannes wagner Hannes death
Hannes death Natura toetus
Natura toetus



































