Zero Trust CARTA CSF CJIS RMF OMG how












- Slides: 39

Zero Trust, CARTA, CSF, CJIS, RMF - OMG, how can I address all of these? A Cybersecurity Best Practices Approach Government IT Symposium Peter Romness Cybersecurity Solutions Lead – US Public Sector CTO Office December 2019

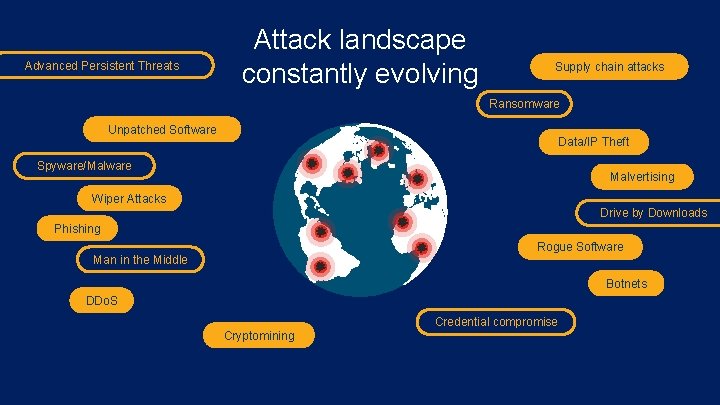
Advanced Persistent Threats Attack landscape constantly evolving Supply chain attacks Ransomware Unpatched Software Data/IP Theft Spyware/Malware Malvertising Wiper Attacks Drive by Downloads Phishing Rogue Software Man in the Middle Botnets DDo. S Cryptomining © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential Credential compromise

Impossibly complex © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential

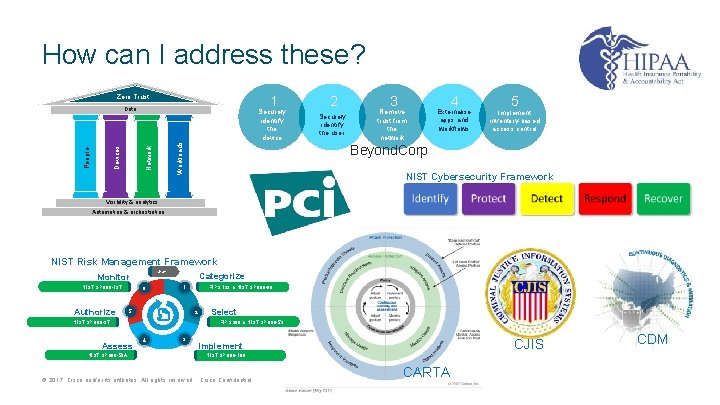
Approaches and Frameworks Zero Trust Workloads Securely identify the device Network Devices People 2 1 Data • • Visibility & analytics • NIST Risk Management Framework NIST SP 800 -137 Start Authorize 6 Categorize 2 NIST SP 800 -53 A 4 Externalise apps and workflows 5 Implement inventory-based access control Why are we hearing about them? NIST Cybersecurity Framework How can I address them? Select FIPS 200 & NIST SP 800 -53 NIST SP 800 -37 Assess FIPS 199 & NIST SP 800 -60 1 5 Remove trust from the network Beyond. Corp Automation & orchestration Monitor 3 What are these? Securely identify the user 4 3 CJIS Implement NIST SP 800 -160 © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential CARTA CDM

Let’s go from Overwhelmed to Empowered © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential If you have a scalable, open and automated foundation, you can address all Approaches and Frameworks

The NIST Risk Management Framework (RMF) NIST RMF is a process flow and more detailed reference then CSF ▶ What: A more prescriptive Risk Management Process. ▶ Goal: Describes more detailed “Outcomes” then CSF. It is a great reference ▶ Process: Uses NIST 800 series Special Publications for each part of the risk management cycle ▶ Business drivers: Still flexible, still recommendations – but more detail to drive decisions ▶ Adaptable to: All environments Start Monitor NIST SP 800 -137 It’s still FLEXIBLE… But is kind of a Checklist Authorize 6 2 Select FIPS 200 & NIST SP 800 -53 NIST SP 800 -37 NIST SP 800 -53 A FIPS 199 & NIST SP 800 -60 1 5 Assess © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential Categorize 4 3 Implement NIST SP 800 -160

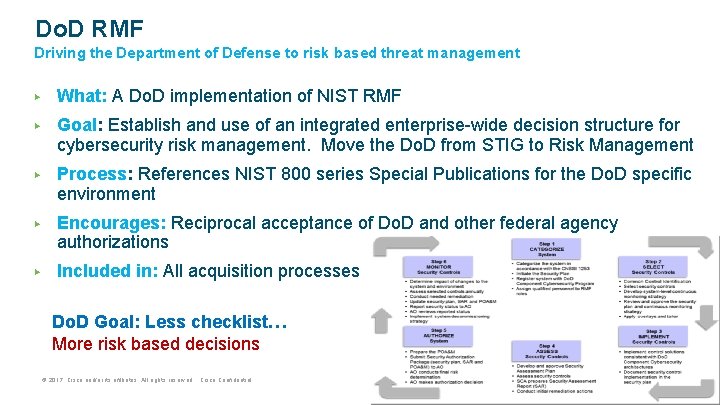
Do. D RMF Driving the Department of Defense to risk based threat management ▶ What: A Do. D implementation of NIST RMF ▶ Goal: Establish and use of an integrated enterprise-wide decision structure for cybersecurity risk management. Move the Do. D from STIG to Risk Management ▶ Process: References NIST 800 series Special Publications for the Do. D specific environment ▶ Encourages: Reciprocal acceptance of Do. D and other federal agency authorizations ▶ Included in: All acquisition processes Do. D Goal: Less checklist… More risk based decisions © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential

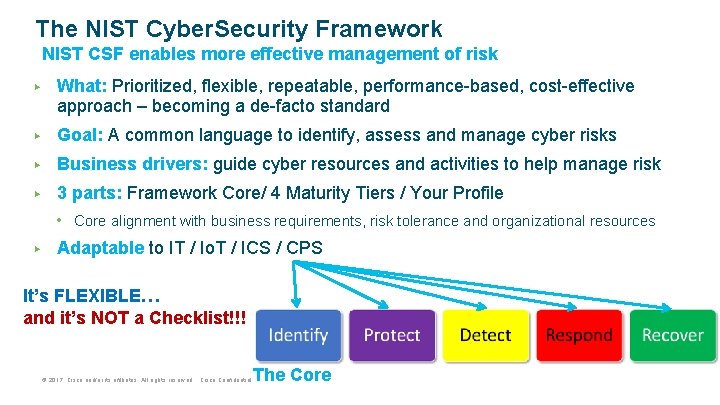
The NIST Cyber. Security Framework NIST CSF enables more effective management of risk ▶ What: Prioritized, flexible, repeatable, performance-based, cost-effective approach – becoming a de-facto standard ▶ Goal: A common language to identify, assess and manage cyber risks ▶ Business drivers: guide cyber resources and activities to help manage risk ▶ 3 parts: Framework Core/ 4 Maturity Tiers / Your Profile • Core alignment with business requirements, risk tolerance and organizational resources ▶ Adaptable to IT / Io. T / ICS / CPS It’s FLEXIBLE… and it’s NOT a Checklist!!! © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential The Core

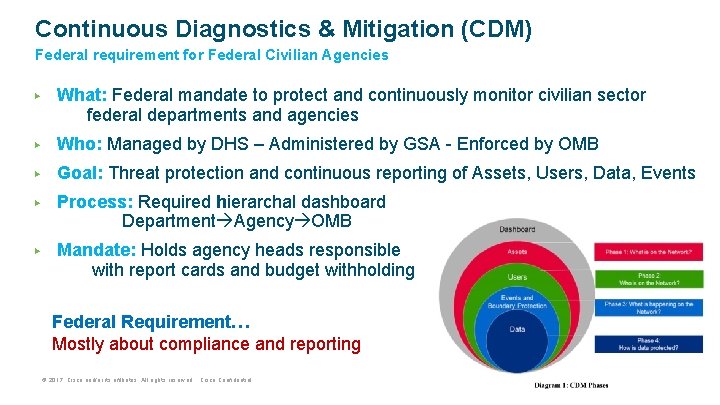
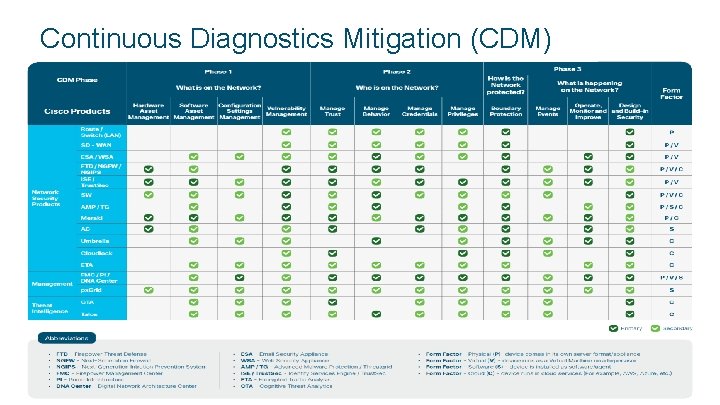
Continuous Diagnostics & Mitigation (CDM) Federal requirement for Federal Civilian Agencies ▶ What: Federal mandate to protect and continuously monitor civilian sector federal departments and agencies ▶ Who: Managed by DHS – Administered by GSA - Enforced by OMB ▶ Goal: Threat protection and continuous reporting of Assets, Users, Data, Events ▶ Process: Required hierarchal dashboard Department Agency OMB ▶ Mandate: Holds agency heads responsible with report cards and budget withholding compliance Federal Requirement… Mostly about compliance and reporting © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential

Criminal Justice Information System (CJIS) FBI Requirement to connect to the CJIS database ▶ What: Requires compliance to access CJIS Data ▶ Who: Every law enforcement agency in the nation who uses FBI criminal justice information to reduce and stop crime ▶ Audits: Audits occur every three years, and non-compliance has serious ramifications – including potential loss of access to FBI CJIS systems ▶ Based on: NIST RMF particularly NIST SP 800 -53 compliance FBI Requirement… Completely about compliance © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential

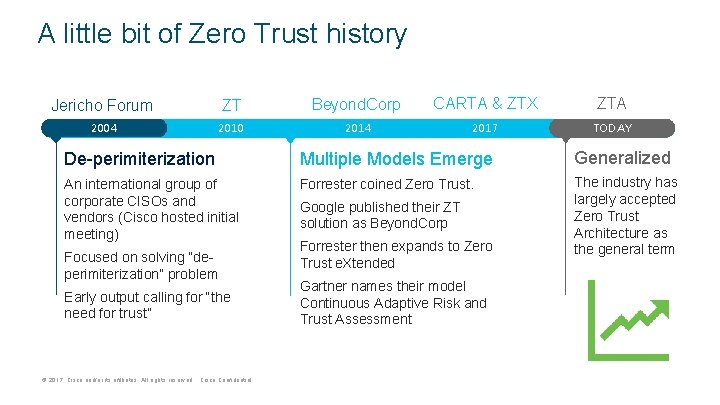
A little bit of Zero Trust history Jericho Forum ZT Beyond. Corp CARTA & ZTX ZTA 2004 2010 2014 2017 Today TODAY De-perimiterization Multiple Models Emerge Generalized An international group of corporate CISOs and vendors (Cisco hosted initial meeting) Forrester coined Zero Trust. The industry has largely accepted Zero Trust Architecture as the general term Focused on solving “deperimiterization” problem Early output calling for “the need for trust” © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential Google published their ZT solution as Beyond. Corp Forrester then expands to Zero Trust e. Xtended Gartner names their model Continuous Adaptive Risk and Trust Assessment

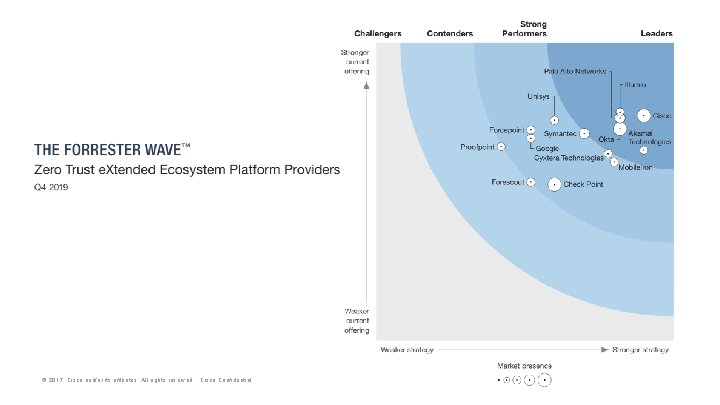
Zero Trust Popularized by Forrester - ZT and ZTX ▶ What: A security strategy based on “least-privilege” to address the modern “perimeter-less” IT environment ▶ Intent: Assumes all environments are hostile - no access until proven trusted ▶ Tenants: All users, devices, applications, data, and network flows encrypted, authenticated and authorized ▶ Enablement: Visibility and automation systems are what allow a zero trust network to be built and operated ▶ Adaptable to: All environments ▶ Missing: Threats © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential Visibility & analytics Data Automation & orchestration Mission Focus Analytics Automation Workloads Network Devices Data People Zero Trust is a strategy and design approach - not a checklist or a thing you buy Zero Trust

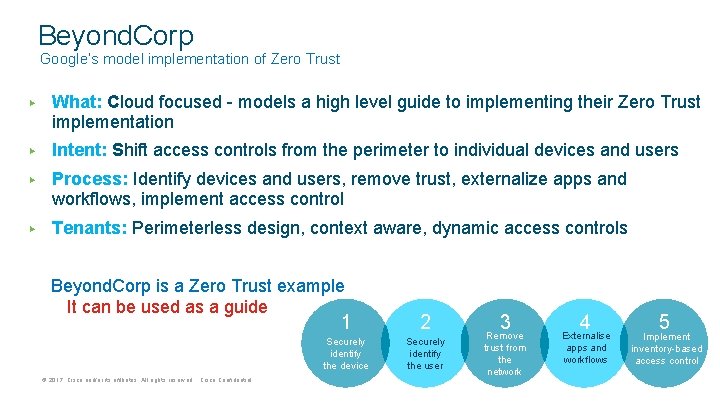
Beyond. Corp Google’s model implementation of Zero Trust ▶ What: Cloud focused - models a high level guide to implementing their Zero Trust implementation ▶ Intent: Shift access controls from the perimeter to individual devices and users ▶ Process: Identify devices and users, remove trust, externalize apps and workflows, implement access control ▶ Tenants: Perimeterless design, context aware, dynamic access controls Beyond. Corp is a Zero Trust example - It can be used as a guide © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential 1 2 Securely identify the device Securely identify the user 3 Remove trust from the network 4 Externalise apps and workflows 5 Implement inventory-based access control

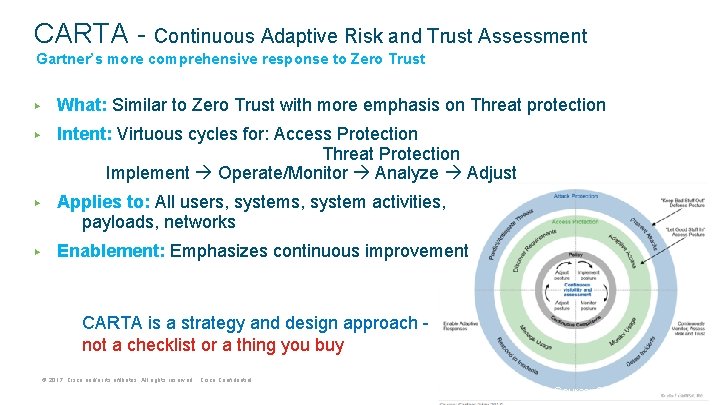
CARTA - Continuous Adaptive Risk and Trust Assessment Gartner’s more comprehensive response to Zero Trust ▶ What: Similar to Zero Trust with more emphasis on Threat protection ▶ Intent: Virtuous cycles for: Access Protection Threat Protection Implement Operate/Monitor Analyze Adjust ▶ Applies to: All users, system activities, payloads, networks ▶ Enablement: Emphasizes continuous improvement CARTA is a strategy and design approach not a checklist or a thing you buy © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential Source: Gartner (May 2017)

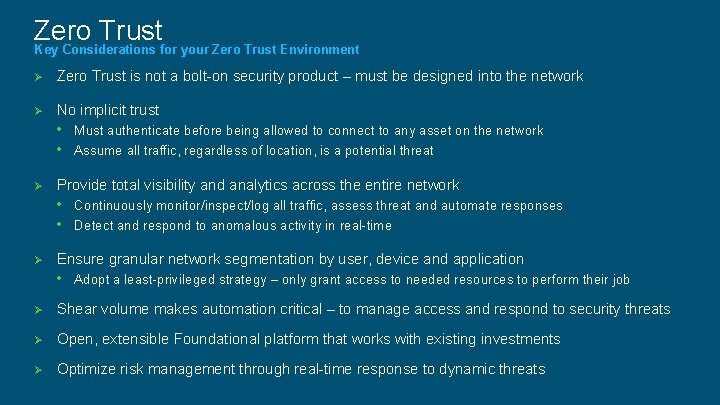
Zero Trust Key Considerations for your Zero Trust Environment Ø Zero Trust is not a bolt-on security product – must be designed into the network Ø No implicit trust • Must authenticate before being allowed to connect to any asset on the network • Assume all traffic, regardless of location, is a potential threat Ø Provide total visibility and analytics across the entire network • Continuously monitor/inspect/log all traffic, assess threat and automate responses • Detect and respond to anomalous activity in real-time Ø Ensure granular network segmentation by user, device and application • Adopt a least-privileged strategy – only grant access to needed resources to perform their job Ø Shear volume makes automation critical – to manage access and respond to security threats Ø Open, extensible Foundational platform that works with existing investments Ø Optimize risk management through real-time response to dynamic threats

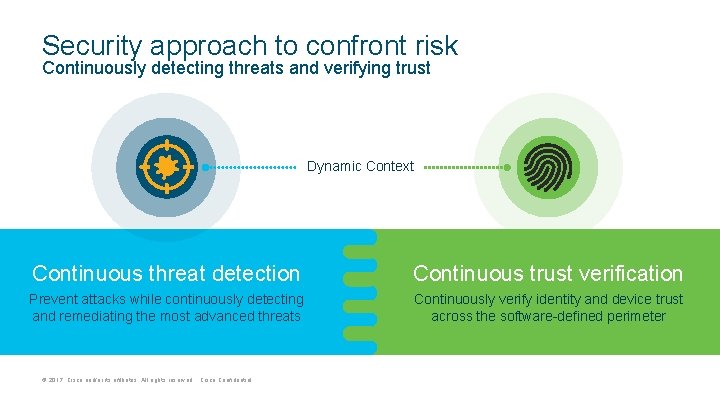
Security approach to confront risk Continuously detecting threats and verifying trust Dynamic Context Continuous threat detection Continuous trust verification Prevent attacks while continuously detecting and remediating the most advanced threats Continuously verify identity and device trust across the software-defined perimeter © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential

NIST Zero Trust Logical Components From NIST SP 800 -207 Draft Identity Services Engine (ISE) SD Access (Network) © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential Tetration (Data Center)

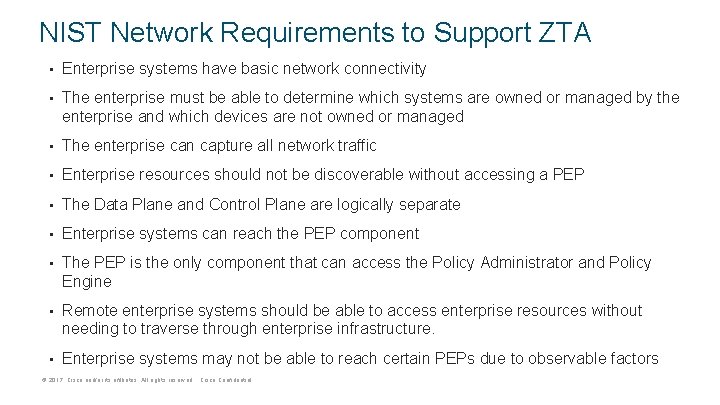
NIST Network Requirements to Support ZTA • Enterprise systems have basic network connectivity • The enterprise must be able to determine which systems are owned or managed by the enterprise and which devices are not owned or managed • The enterprise can capture all network traffic • Enterprise resources should not be discoverable without accessing a PEP • The Data Plane and Control Plane are logically separate • Enterprise systems can reach the PEP component • The PEP is the only component that can access the Policy Administrator and Policy Engine • Remote enterprise systems should be able to access enterprise resources without needing to traverse through enterprise infrastructure. • Enterprise systems may not be able to reach certain PEPs due to observable factors © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential

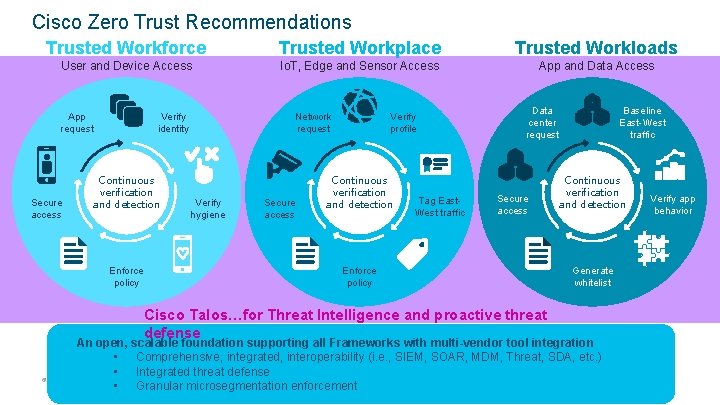
Cisco Zero Trust Recommendations Trusted Workforce Trusted Workplace Trusted Workloads User and Device Access Io. T, Edge and Sensor Access App and Data Access App request Secure access Verify identity Continuous verification and detection Enforce policy Network request Verify hygiene Secure access Verify profile Continuous verification and detection Tag East. West traffic Data center request Secure access Enforce policy Cisco Talos…for Threat Intelligence and proactive threat defense © 2017 Baseline East-West traffic Continuous verification and detection Generate whitelist An open, scalable foundation supporting all Frameworks with multi-vendor tool integration • Comprehensive, integrated, interoperability (i. e. , SIEM, SOAR, MDM, Threat, SDA, etc. ) • Integrated threat defense Cisco and/or its affiliates. All rights reserved. Cisco Confidential • Granular microsegmentation enforcement Verify app behavior

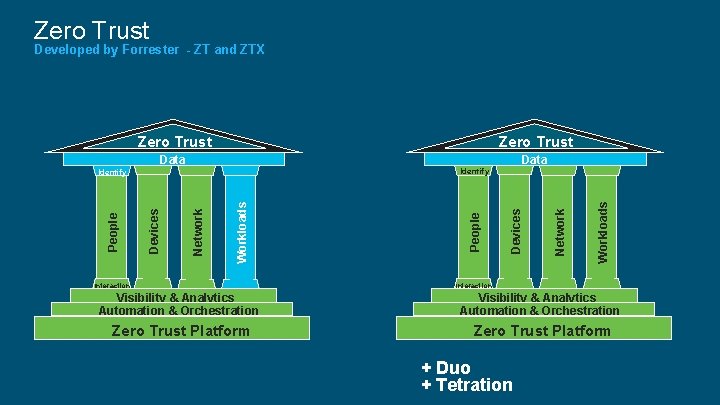
Zero Trust Developed by Forrester - ZT and ZTX Zero Trust Data Workloads Network Devices People Interaction People Identify Interaction Visibility & Analytics Automation & Orchestration Zero Trust Platform + Duo + Tetration

© 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential

How can I address these? Zero Trust 1 Workloads Securely identify the device Network People Devices Data 2 Securely identify the user 3 Remove trust from the network 4 Externalise apps and workflows 5 Implement inventory-based access control Beyond. Corp NIST Cybersecurity Framework Visibility & analytics Automation & orchestration NIST Risk Management Framework Start Monitor NIST SP 800 -137 Authorize 6 Categorize 5 2 NIST SP 800 -53 A Select FIPS 200 & NIST SP 800 -53 NIST SP 800 -37 Assess FIPS 199 & NIST SP 800 -60 1 4 3 CJIS Implement NIST SP 800 -160 © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential CARTA CDM

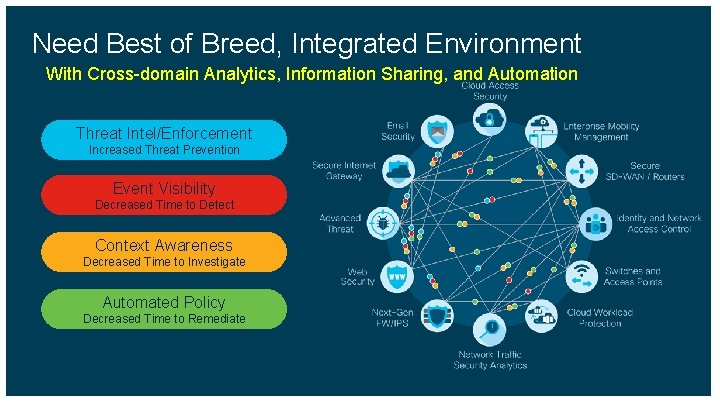
Need Best of Breed, Integrated Environment With Cross-domain Analytics, Information Sharing, and Automation Threat Intel/Enforcement Increased Threat Prevention Event Visibility Decreased Time to Detect Context Awareness Decreased Time to Investigate Automated Policy Decreased Time to Remediate © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential

Modern Security Architecture Open APIs · Developer Environment · Services Management · Response Deploy Policy Detect Continuous Trust Verification Users, devices, applications, and more Investigate Remediate Technology Partners and threat feeds Enforcement Everywhere Network Endpoint Application Comprehensive Threat Intelligence Known Threats © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential Cloud Unknown/Zero-day

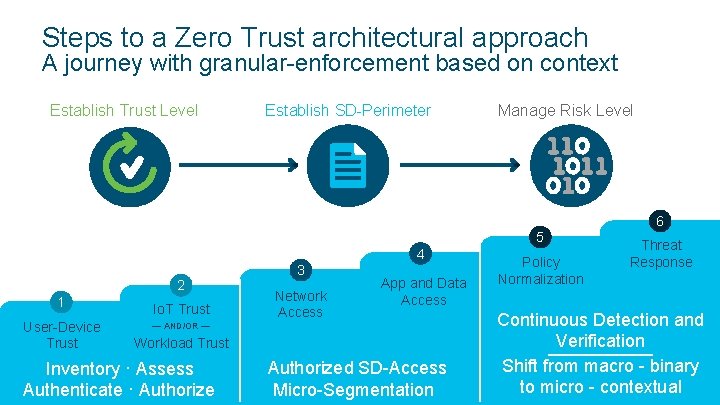
Steps to a Zero Trust architectural approach A journey with granular-enforcement based on context Establish Trust Level Establish SD-Perimeter Manage Risk Level 6 5 4 2 1 User-Device Trust Io. T Trust 3 Network Access App and Data Access — AND/OR — Workload Trust Inventory · Assess Authenticate · Authorize © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential Authorized SD-Access Micro-Segmentation Policy Normalization Threat Response Continuous Detection and Verification Shift from macro - binary to micro - contextual

The Path to an Integrated Security Platform A resilient Cybersecurity posture builds on the foundation of all cyber communications – the Network. The journey to comprehensive protection requires an adaptive architecture that can respond to evolving threats and enable automated response. © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential

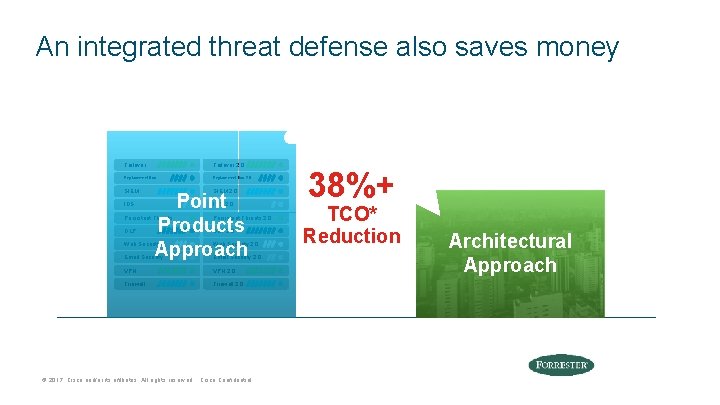
An integrated threat defense also saves money Failover 2. 0 Replacement Box 2. 0 SIEM 2. 0 IDS Point Products Approach IDS 2. 0 Persistent Threats 2. 0 DLP 2. 0 Web Security 2. 0 Email Security 2. 0 VPN 2. 0 Firewall 2. 0 38%+ TCO* Reduction Architectural Approach * Final Results © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential

If you have a scalable, open and automated foundation, you can address all Approaches and Frameworks © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential

From Overwhelmed to Empowered With an integrated approach to security © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential

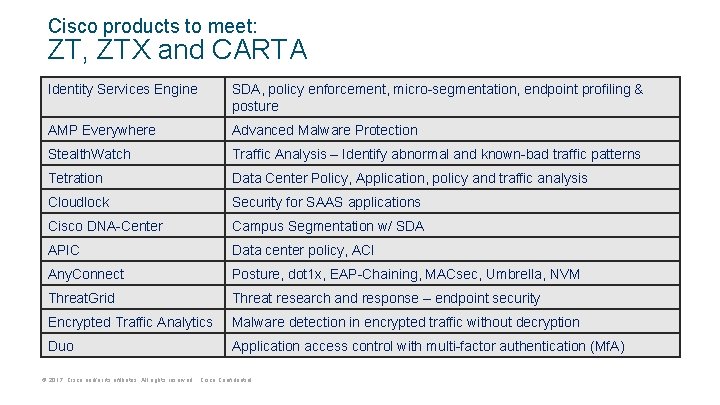
Cisco products to meet: ZT, ZTX and CARTA Identity Services Engine SDA, policy enforcement, micro-segmentation, endpoint profiling & posture AMP Everywhere Advanced Malware Protection Stealth. Watch Traffic Analysis – Identify abnormal and known-bad traffic patterns Tetration Data Center Policy, Application, policy and traffic analysis Cloudlock Security for SAAS applications Cisco DNA-Center Campus Segmentation w/ SDA APIC Data center policy, ACI Any. Connect Posture, dot 1 x, EAP-Chaining, MACsec, Umbrella, NVM Threat. Grid Threat research and response – endpoint security Encrypted Traffic Analytics Malware detection in encrypted traffic without decryption Duo Application access control with multi-factor authentication (Mf. A) © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential

Continuous Diagnostics Mitigation (CDM) © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential

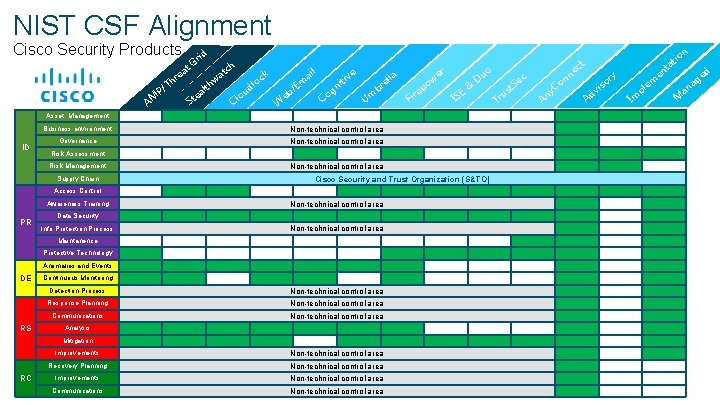
NIST CSF Alignment Cisco Security Products P/ AM rid G at e r Th t al e St ch at hw ck lo ud o Cl W eb m /E l ai ve g ti ni Co lla re b Um Fi re w po o er E IS & Du Asset Management ID Business environment Non-technical control area Governance Non-technical control area Risk Assessment Risk Management Supply Chain Non-technical control area Cisco Security and Trust Organization (S&TO) Access Control Awareness Training PR Non-technical control area Data Security Info Protection Process Non-technical control area Maintanence Protective Technology Anomalies and Events DE RS Continuous Monitoring Detection Process Non-technical control area Response Planning Non-technical control area Communications Non-technical control area Analysis Mitigation RC Improvements Non-technical control area Recovery Planning Non-technical control area Improvements © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential Communications Non-technical control area t us r T c Se n An y n Co n tio t ec e y Ad r so vi Im em pl a nt ed M a g na

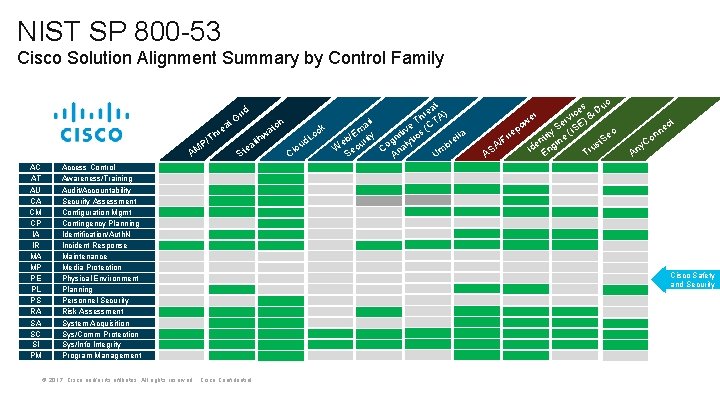
NIST SP 800 -53 Cisco Solution Alignment Summary by Control Family at re A) h l T CT ai ch at m at ck ive s ( re t i E o h w y / c lla t T gn lyti d. L lth re eb curi P/ o u a b a o e W e C n AM Cl St S Um A id Gr AC AT AU CA CM CP IA IR MA MP PE PL PS RA SA SC SI PM Access Control Awareness/Training Audit/Accountability Security Assessment Configuration Mgmt Contingency Planning Identification/Auth. N Incident Response Maintenance Media Protection Physical Environment Planning Personnel Security Risk Assessment System Acquisition Sys/Comm Protection Sys/Info Integrity Program Management © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential o es Du c i rv ) & ow Se (ISE p c y re it Se Fi nt ine t / e s A u Id Eng Tr AS er ct ne n o y. C An Cisco Safety and Security

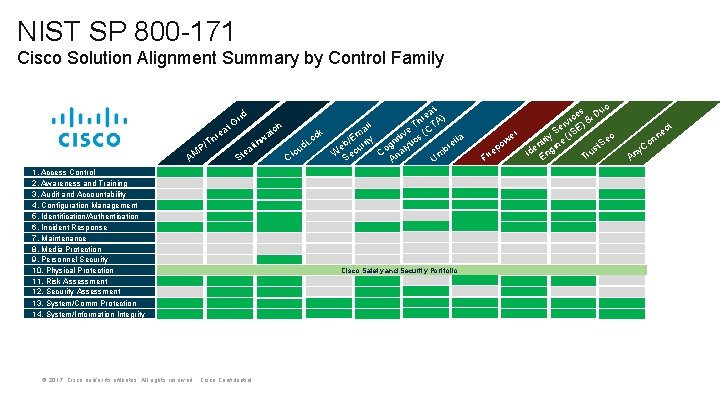
NIST SP 800 -171 Cisco Solution Alignment Summary by Control Family at re A) h l T CT ai ch at m at ck ive s ( re t i E o h w y / c lla t T gn lyti d. L lth re eb curi P/ o u a b a o e W e C n AM Cl St S Um A id Gr 1. Access Control 2. Awareness and Training 3. Audit and Accountability 4. Configuration Management 5. Identification/Authentication 6. Incident Response 7. Maintenance 8. Media Protection 9. Personnel Security 10. Physical Protection 11. Risk Assessment 12. Security Assessment 13. System/Comm Protection 14. System/Information Integrity © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential Cisco Safety and Security Portfolio o es Du c i & v er E) S r S I e ( ec ity S ow nt ine t p e us re Id Eng Tr Fi y. C An ct ne n o

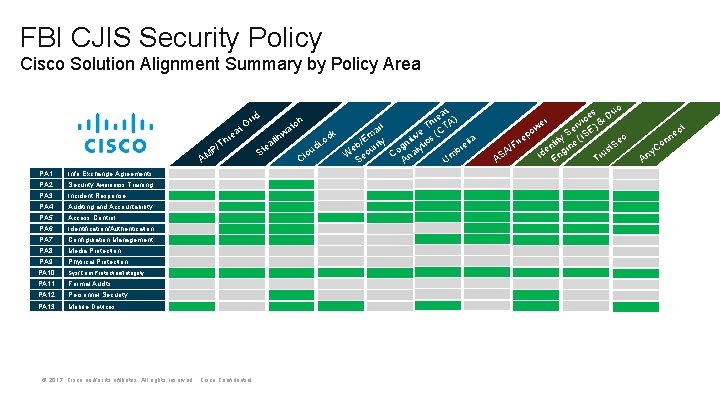
FBI CJIS Security Policy Cisco Solution Alignment Summary by Policy Area at e hr /T P AM PA 1 Info Exchange Agreements PA 2 Security Awareness Training PA 3 Incident Response PA 4 Auditing and Accountability PA 5 Access Control PA 6 Identification/Authentication PA 7 Configuration Management PA 8 Media Protection PA 9 Physical Protection PA 10 Sys/Com Protection/Integrity PA 11 Formal Audits PA 12 Personnel Security PA 13 Mobile Devices at re A) h h c T T at ail ve s (C m ck i hw t t i E o l c lla b/ urity gn lyti d. L ea re e t o u b S o W ec C na Cl S Um A id Gr © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential ire F A/ AS o es Du c i & v er E) S S I ( ec ity nt ine t. S e s g u Id En Tr r we o p y. C An ct ne n o

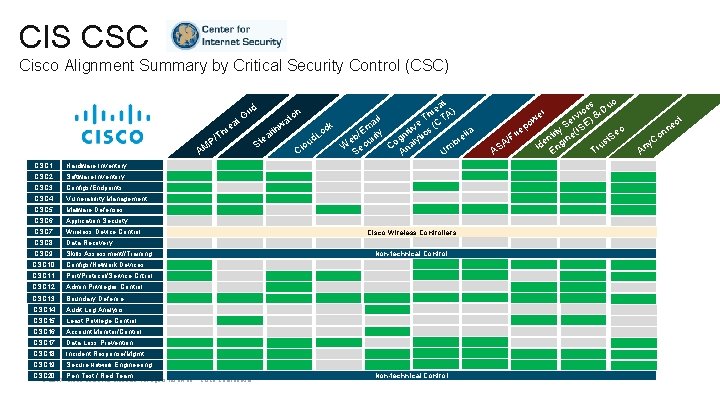
CIS CSC Cisco Alignment Summary by Critical Security Control (CSC) hr /T ea t P AM CSC 1 Hardware Inventory CSC 2 Software Inventory CSC 3 Configs/Endpoints CSC 4 Vulnerability Management CSC 5 Malware Defenses CSC 6 Application Security CSC 7 Wireless Device Control CSC 8 Data Recovery CSC 9 Skills Assessment//Training CSC 10 Configs/Network Devices CSC 11 Port/Protocol/Service Cntrol CSC 12 Admin Privileges Control CSC 13 Boundary Defense CSC 14 Audit Log Analysis CSC 15 Least Privilege Control CSC 16 Account Monitor/Control CSC 17 Data Loss Prevention CSC 18 Incident Response/Mgmt CSC 19 Secure Network Engineering at re A) h T T a ail ve s (C m ck i hw t t i E o l c lla b/ urity gn lyti d. L ea re e t o u b S o W ec C na Cl S Um A id Gr CSC 20 Pen Test / Red Team © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential tch Cisco Wireless Controllers Non-technical Control s uo ice & D v r ) Se ISE po y t ( ri e ec i nt ine t. S /F e s A g u Id En Tr AS r we y. C An ct ne n o

Thank You

Fundamental Transformative Drivers are Here! Cybersecurity threat / potential adverse impact have never been greater Increasing threat capabilities and sophistication: • • • Increased availability and number of attack surfaces and attack vectors (devices / cloud / Io. T / edge) Availability of automated and compromised tools, vulnerabilities & knowledge Rapidly evolving, dynamic nature of the threat Creates the need for: • • Real-time visibility across the entire network and support infrastructure • And the data and applications that ride across them Real-time enforcement of network policies for security and performance Ability to dynamically change network – especially in response to anomalous behavior Going beyond Zero Trust Security – continuous, threat-aware visibility © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential

The Way We Work is Evolving Data Center Io. T / IIo. T / OT / Edge V M Campus & Branch Users V M V M SDWAN V M Private Cloud Iaa. S Users Everywhere Saa. S / Paa. S Multi-domain World with Applications / Workloads / Data © 2017 Cisco and/or its affiliates. All rights reserved. Cisco Confidential