Yossef Oren Dvir Schirman and Avishai Wool Tel














- Slides: 25

Yossef Oren, Dvir Schirman, and Avishai Wool: Tel Aviv University Range Extension Attacks on Contactless Smartcards ESORICS 2013

Agenda �Introduction Contactless smartcards Attack motivation �System design �Experimental results �Attack scenarios �Conclusions

Contactless smartcards

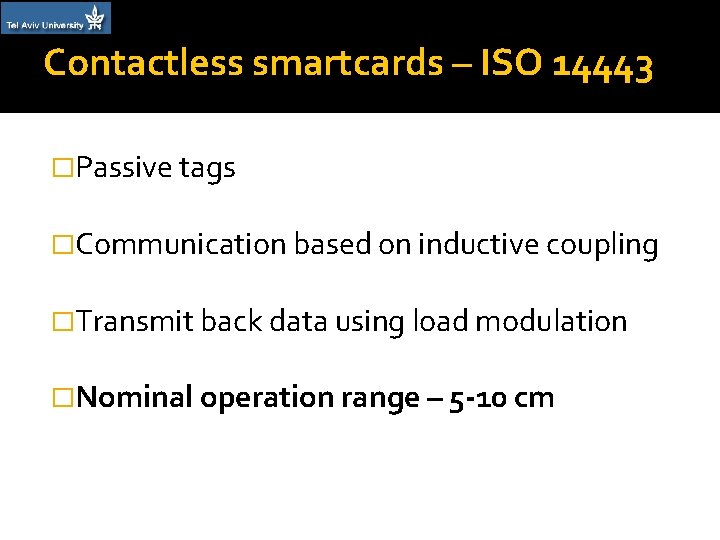
Contactless smartcards – ISO 14443 �Passive tags �Communication based on inductive coupling �Transmit back data using load modulation �Nominal operation range – 5 -10 cm

Attack Motivation �Contactless smartcards are being used in a variety of security oriented applications: Access control Payment E-voting Smart ID card Passports �All of them assume the tag is in proximity of the reader

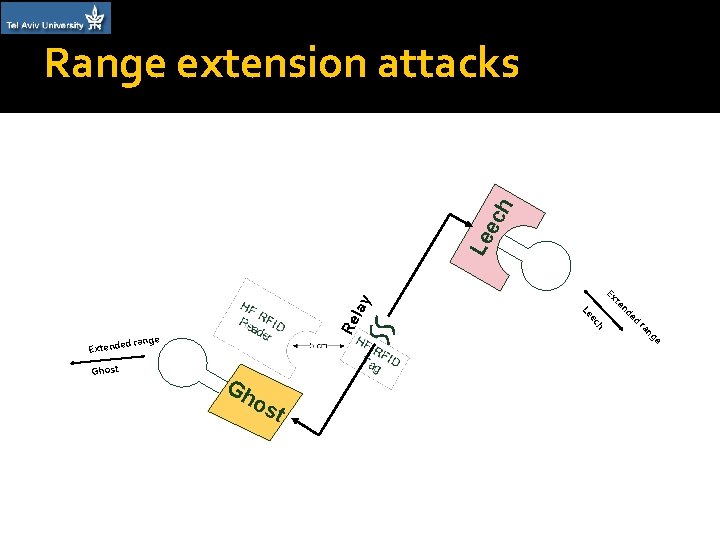
Motivation �If a communication between the reader and the tag could be established from a longer range – the proximity assumption would be broken �Our goal – build a device (a. k. a “Ghost”) which allow a standard tag to communicate with a standard reader from a distance of more than 1 m

Re Gh os t h Ghost range te ec d Extende Ex Le lay Le e ch Range extension attacks nd ed ra n ge

Related work �Relay attack – extending the nominal communication range between a reader and a tag using a relay channel between two custom made devices (“Ghost” & “Leech”) [KW 05, Han 05, FHMM 11, SC 13] �Extended range Leech – a device that allows to read a standard tag from a distance of 30 cm [KW 06]

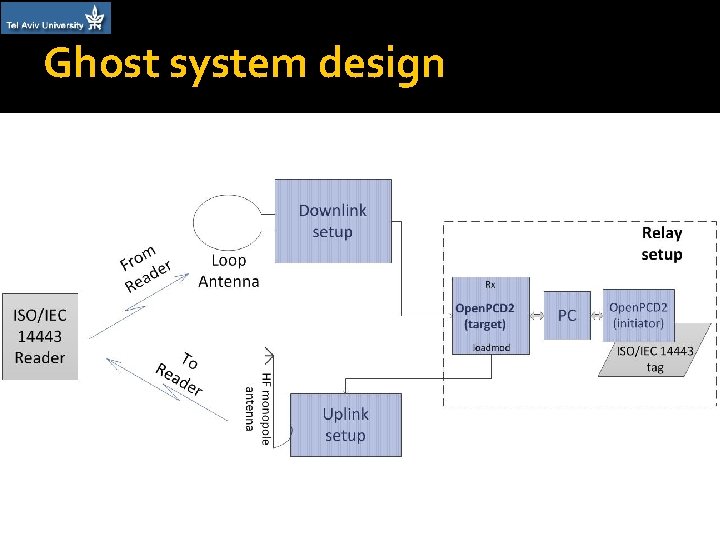
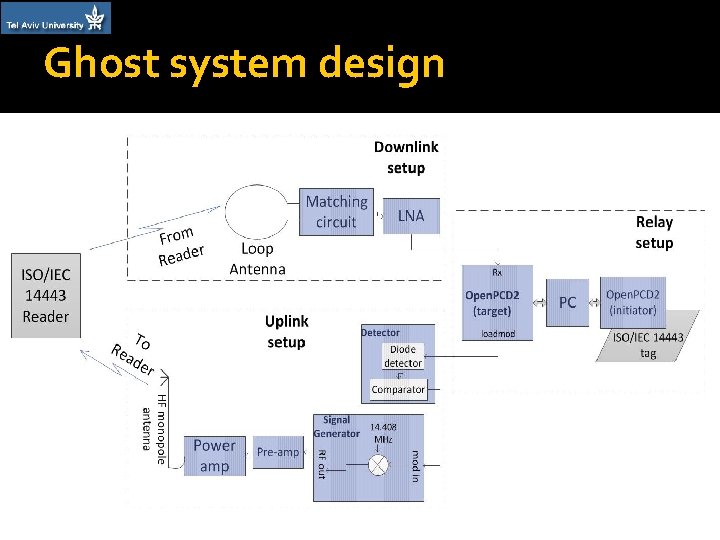
Ghost system design �Design principles: Two separate antennas: ▪ A large loop antenna for downlink ▪ A mobile monopole HF antenna for uplink Active load modulation for uplink transmission PC based relay

Open. PCD 2 �An open source & open hardware evaluation board for ISO 14443 �Can emulate a tag or a reader �Based on NXP PN 532 �www. openpcd. org

Ghost system design

Ghost system design – Relay & Leech �A relay & a Leech were not part of this research, but necessary for the whole system �Relay channel between two Open. PCD 2 boards was implemented inside a single PC Using libnfc’s nfc-relay-picc – designed to overcome relay timing limitations �Leech was based on an unmodified Open. PCD 2

Ghost system design – Downlink �Receiving antenna: a 39 cm loop antenna designed for prior Leech project �Matching circuit: Based on NXP’s app note �LNA: Mini-Circuits’ ZFL-500 LN

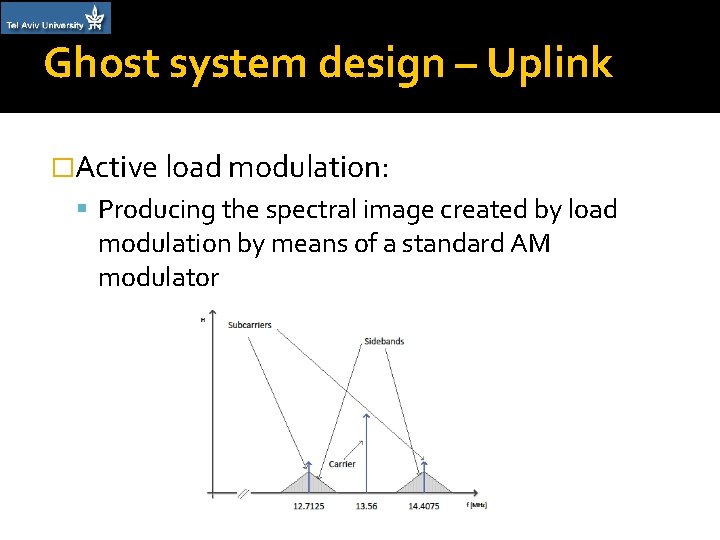
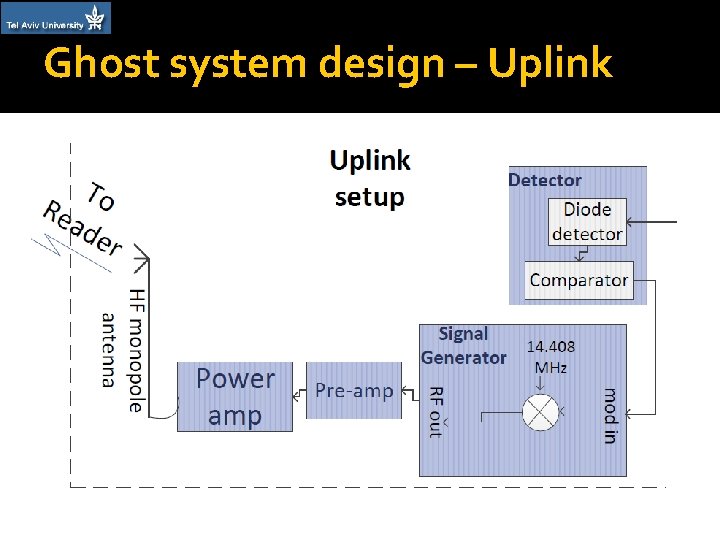
Ghost system design – Uplink �Active load modulation: Producing the spectral image created by load modulation by means of a standard AM modulator

Ghost system design – Uplink �Ghost Open. PCD 2 modification: LOADMOD pin was enabled – outputs modulated subcarrier (847. 5 k. Hz) �The above signal was connected to a detector, in order to extract coded bitstream �The bitstream was pulse modulated on a 14. 4075 MHz carrier signal �The HF signal was pre-amplified (Mini. Circuits’ ZHL-32 A) & power amplified (RMItaly KL 400)

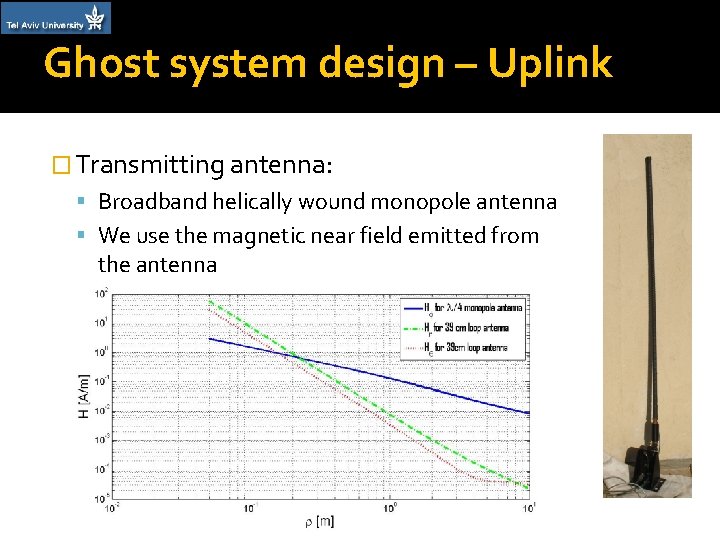
Ghost system design – Uplink � Transmitting antenna: Broadband helically wound monopole antenna We use the magnetic near field emitted from the antenna

Ghost system design

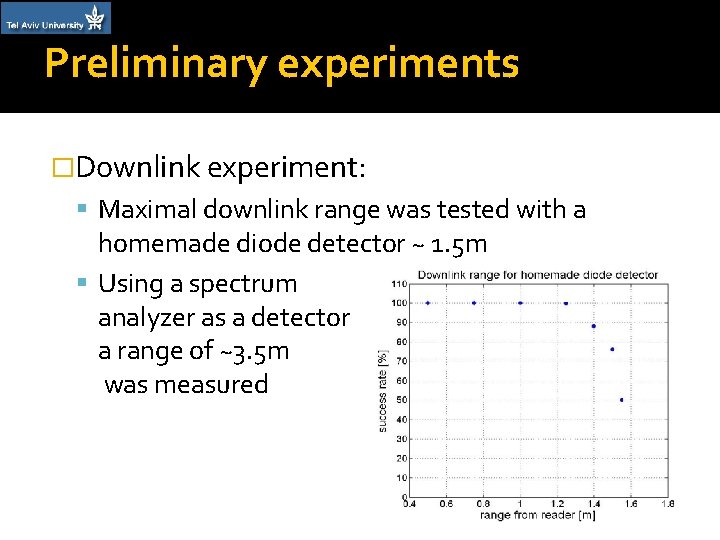
Preliminary experiments �Downlink experiment: Maximal downlink range was tested with a homemade diode detector ~ 1. 5 m Using a spectrum analyzer as a detector a range of ~3. 5 m was measured

Preliminary experiments �Jamming By transmitting a continuous signal on 14. 4075 MHz the reader can be jammed Since we couldn’t measure uplink range independently from downlink system, maximal Jamming range was measured in order to evaluate the performance of the uplink system By transmitting a 29 d. Bm signal, a jamming range of 2 m was achieved

Range extension experiment – Setup

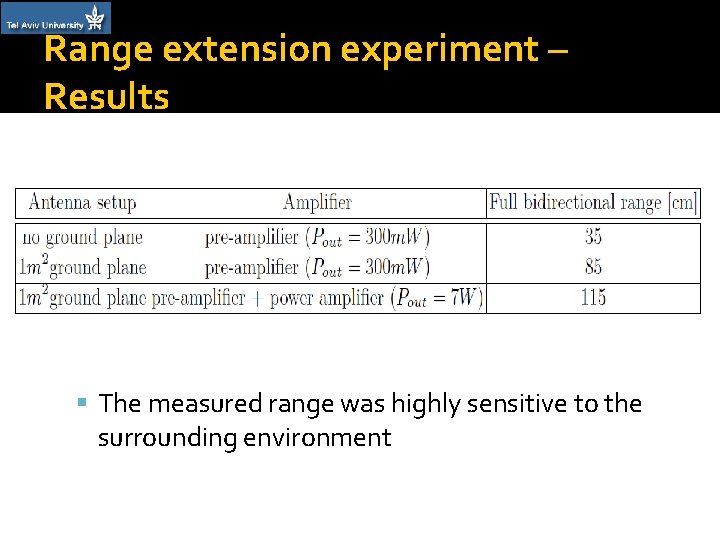
Range extension experiment – Results The measured range was highly sensitive to the surrounding environment

Attack Scenarios �E-voting Using a range extended Ghost and a relay attack, an adversary can mount several attacks on Israel’s proposed e-voting system Allows the attacker complete control over previously cast votes �Access control By using a range extended Ghost and a relay setup the attacker can open a secured door without being detected by a guard / security camera

Conclusions �We offer a car mounted range extension setup for ISO 14443 RFID systems �We successfully built a prototype working from 1. 15 m (more than 10 times the nominal range)

Conclusions �Extending the nominal communication range of contactless smartcards form a severe threat on the system’s security �Combining with a relay attack the presented device can allow adversary to mount his attack without being detected

Thank you
 Avishai wool
Avishai wool Yossef av-gay
Yossef av-gay Dvir rules
Dvir rules Zeev dvir
Zeev dvir Ndvir
Ndvir Arik dvir
Arik dvir Danny dvir
Danny dvir Woollen textile industry in india
Woollen textile industry in india Battery and steel wool
Battery and steel wool Torrance-sparrow model
Torrance-sparrow model Melody randford
Melody randford 14 necesidades de dorothea orem
14 necesidades de dorothea orem Dorothea orem teoria
Dorothea orem teoria Oren freifeld
Oren freifeld Oren freifeld
Oren freifeld Oren shriki
Oren shriki Sifat kimia asid
Sifat kimia asid Joel oren
Joel oren Shmuel oren
Shmuel oren Yossi oren
Yossi oren Suffix array java
Suffix array java Oren weimann
Oren weimann Shmuel oren
Shmuel oren Meryem merve ören
Meryem merve ören Wool act of 1699
Wool act of 1699 Coral clasps and amber studs meaning
Coral clasps and amber studs meaning