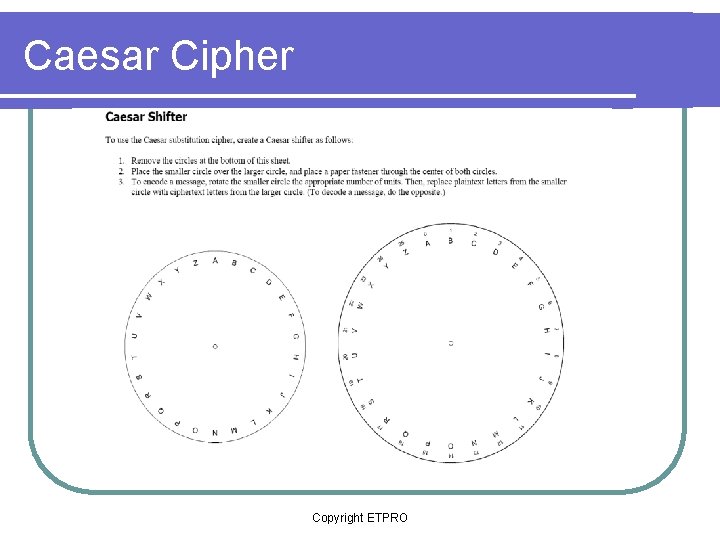
What is Cryptography Copyright ETPRO What is Cryptography



















- Slides: 36

What is Cryptography? Copyright ETPRO

What is Cryptography/ Cryptology? The art of protecting information by transforming it (encrypting it) into an unreadable format, called cipher text. l Only those who possess a secret key can decipher (or decrypt) the message into plain text. l Encrypted messages can sometimes be broken by cryptanalysis, also called codebreaking, although modern cryptography techniques are virtually unbreakable. l Copyright ETPRO

What is Cryptography? l As the Internet and other forms of electronic communication become more prevalent, electronic security is becoming increasingly important. l Cryptography is used to protect e-mail messages, credit card information, and corporate data. Copyright ETPRO

Break this code 20 -15 -4 -1 -25 25 -15 -21 23 -9 -12 -12 12 -5 -1 -18 -14 1 -2 -15 -21 -20 3 -15 -4 -519 Copyright ETPRO

Cipher Text l Text that has been transformed into an unreadable format. l Code l In cryptology, code means substituting a meaningful word or phrase with another word or phrase to change or hide meaning Copyright ETPRO 2010 20 -15 -4 -1 -25 25 -15 -21 23 -9 -12 -12 12 -5 -1 -18 -14 1 -2 -15 -21 -20 3 -15 -4 -5 -19 l Cipher text

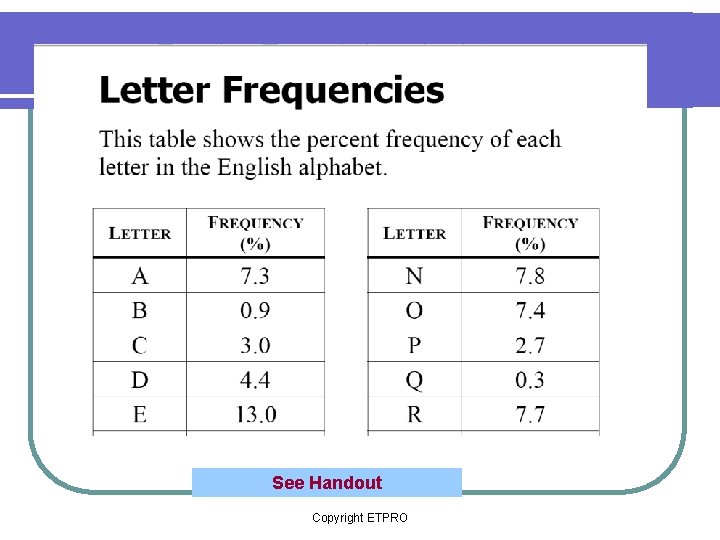
What numbers occur most frequently in the ciphertext? l Frequency analysis is the process by which the frequency of a letter in an encoded messages is compared with the frequency of letters in English words. Copyright ETPRO

What numbers occur most frequently in the ciphertext? l For instance, the letter E occurs most often in English words, so if the letter W occurs most often in ciphertext, then it is likely that E has been replaced by W. Copyright ETPRO

See Handout Copyright ETPRO

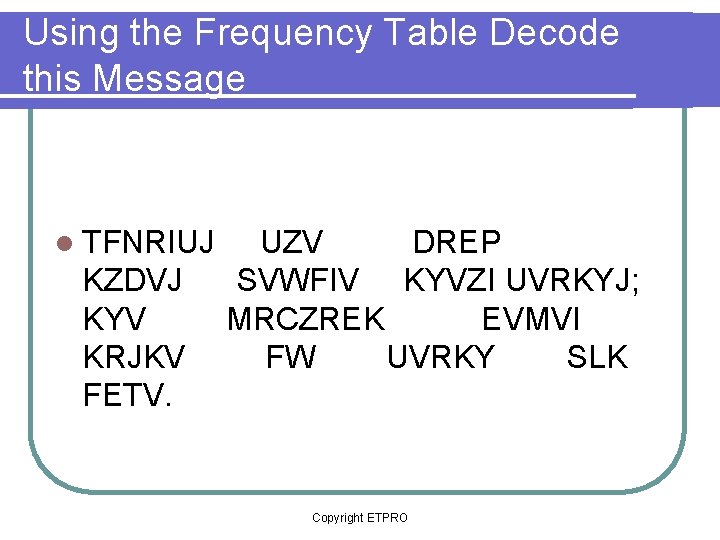
Using the Frequency Table Decode this Message l TFNRIUJ UZV DREP KZDVJ SVWFIV KYVZI UVRKYJ; KYV MRCZREK EVMVI KRJKV FW UVRKY SLK FETV. Copyright ETPRO

Caesar cipher A Caesar cipher is a coding system in which letters are replaced by letters a certain distance ahead in the alphabet. l Julius Caesar is thought to have used this method to communicate with officers in the Roman army. l When sending a message, Caesar would inform his generals what the shift was, so they would be the only ones who could read the encrypted message. l Copyright ETPRO

Caesar Cipher Copyright ETPRO

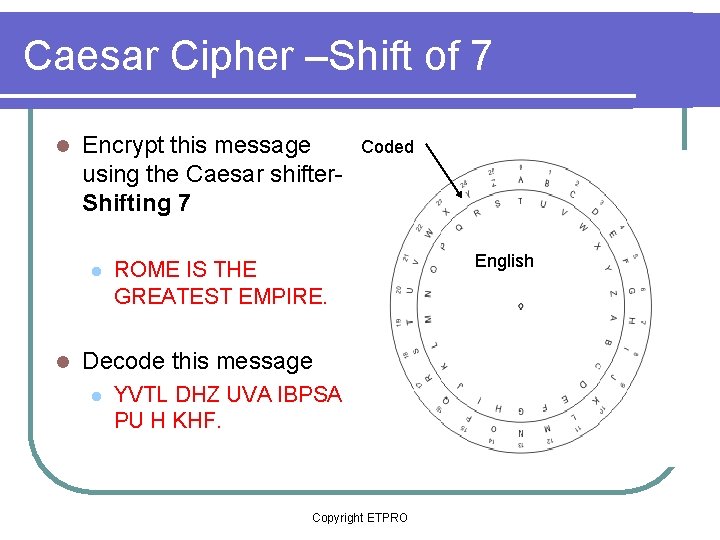
Caesar Cipher –Shift of 7 l Encrypt this message using the Caesar shifter. Shifting 7 l l Coded ROME IS THE GREATEST EMPIRE. Decode this message l YVTL DHZ UVA IBPSA PU H KHF. Copyright ETPRO English

You may have also used logic when decoding the message. l Some may have noticed the one-letter word h that appears near the end of the message. l Since this letter must represent either a or I (these are the only two single-letter English words), students can determine the possible shifts and see which one works for the remainder of the message. l Copyright ETPRO

Answers l Correct Code =YVTL PZ AOL NYLHALZA LTWPYL. l Decoded message = Rome was not built in a day. Copyright ETPRO

To Check… l Go To: http: //illuminations. nctm. org/Activity. Detail. a spx? id=5 Copyright ETPRO

To Check the Cipher l Crypto. Club l http: //cryptoclub. math. uic. edu/shiftcipher/shi ftcipher. htm Copyright ETPRO

Caesar Cipher named after Julius Caesar l Who was he? Where was he from? And when did he live? l Julius Caesar was the Emperor of Rome. He lived from 100 -44 B. C. Copyright ETPRO

l The Caesar Cipher is based on shifting the letters in the alphabet a certain number of spaces. How many shifts are possible? l The Caesar cipher has 25 possible shifts. A shift of 26 or more will simply repeat one of the shifts of 1 -25. Copyright ETPRO

l Why do you think this method was used by Julius Caesar? During his time, how effective do you think it was to send secret messages? l This was probably sufficient during Caesar’s time, but it is insufficient today because of advanced code breaking methods. Copyright ETPRO

l Would this method provide adequate security today or would a code using this method be easily broken? l No, this would be insufficient today because of advanced code breaking methods. Copyright ETPRO

l Explain why the number of total shifts (from the second question) is the weak point of the Caesar Cipher. l Because there are only 25 possible shifts, a person could test each possible shift to determine if an encoded message uses the Caesar cipher. Copyright ETPRO

Try one on your own l Encode a “common” message using the Caesar Cipher and any shift you choose and exchange the ciphertext with a classmate. l The student receiving the ciphertext should decode the message and be able to tell what shift was used. Copyright ETPRO

Go back to … http: //illuminations. nctm. org/Activity. Detail. a spx? id=5 l Walk through the Instructions l Try Explorations l Crack the Code lxwpajcdujcrxwb Make sure you type in only lower case—type in encoded message box and click decode Copyright ETPRO

In Excel l Secret Messages l Plot the Secret Location See Handouts for Directions Answers: Secret messages Plot the location Copyright ETPRO

Copyright ETPRO

Methods of Cryptography l Substitution l Transposition l l l Hiding a message (example: invisible inks, Herodotus tattooed messages on a shaved slave’s head and waited for the hair to re-grow to hide his messages) Mathematical l l Rearranging the order of letters of the words of a message. (example: “the letters in each word get moved around = eth ttseelr ni ceah drow etg veodm uarndo”) Steganography l Uses advanced formulas to encrypt text Computer or Mechanically Assisted l Copyright ETPRO 2010 l Replacing each letter with a different letter or symbol (a=@, b=J, c=2 so that “a cat” = “@ 2 J@”) Using complex algorithms and any single or combination of the mathematical, transposition, substitution and steganography to Copyright ETPRO encrypt plain text.

The Enigma Machine l The most famous mechanical encryption Copyright ETPRO 2010 device in history. l INSERT PICUTRE OF MACHINE HERE WITH LINK TO YOU TUBE VIDEO

Cryptanalyst: Job Description text into unreadable information (cipher text), or for decoding encrypted information Copyright ETPRO 2010 l Creates algorithms for transforming plain

Cryptanalyst: AKA l l l l AKA Cryptographer Chronologic Technician Chronologic Linguist Symbolist Decipherer Copyright ETPRO l l Copyright ETPRO 2010 l l Information Security Expert Intelligence Agent Intelligence Officer Information Security Engineer

Cryptanalyst: Salary l $55, 000 - $130, 000. 00 + Copyright ETPRO

Cryptanalyst: Education l Entry Level: Undergraduate: l l l l Math Computer Science Foreign Languages Engineering Telecommunications Computer Programming Languages Political Science Mid and High Level: Masters + l l Math Computer Science Engineering Information Assurance / Information Security Source: http: //careersthatdonotsuck. com/2007/02/24/careers-profile. Copyright ETPRO cryptologist/

The Need l Copyright Protection Personal Email l Businesses l Government l Military l l Credit Card Processing l Password Protection l RSA tokens: for business and games (like Warcraft) Copyright ETPRO 2010 l Security of communications for

Legal Problems l Digital Millennium Copyright Act (1998) l l Copyright ETPRO 2010 l Intended to provide law enforcement with a tool to go after piracy and file sharing (media like music, movies, and software) Made it illegal to use cryptanalytic techniques to get around the copyright protection methods (called Digital Rights Management) Unintended result was to limit research and research sharing in the Cryptanalyst field for fear that their work might violate this law. l l Cryptanalyst argue that the algorithms should be published so that they can be improved and used. Only the keys should remain a secret. The first arrest was Dmitry Sklyarov, whose dissertation work and subsequent work with a Russian book reader company identified weaknesses in the protection of PDF files. Copyright ETPRO

Your are the Cryptanalyst! l Create your own algorithm for encrypting a message! Substitution l l Transposition l l Hiding a message (example: invisible inks, Herodotus tattooed messages on a shaved slave’s head and waited for the hair to re-grow to hide his messages) Mathematical l l Rearranging the order of letters of the words of a message. (example: “the letters in each word get moved around = eth ttseelr ni ceah drow etg veodm uarndo”) Steganography l l Replacing each letter with a different letter or symbol (a=@, b=J, c=2 so that “a cat” = “@ 2 J@”) Uses advanced formulas to encrypt text Computer or Mechanically Assisted l Using complex algorithms and any single or combination of the mathematical, transposition, substitution and steganography to encrypt plain text. Copyright ETPRO 2010 l

Number Theory Applet 11. Letter Frequency Analysis Calculator l http: //www. wiley. com/college/mat/gilbert 139343/jav a/java 11_s. html l Black Chamber l http: //www. simonsingh. net/The_Black_Chamber/fre quencyanalysis. html l Code Breaking Software & simulations l http: //www. richkni. co. uk/php/crypta/freq. php l Copyright ETPRO

Remainder of Time Visit America's Crypto Kids (K-12) National Security Agency (NSA) http: //www. nsa. gov/kids/ l CIA Kids’ Page (K-12) Central Intelligence Agency (CIA) https: //www. cia. gov/kids-page/index. html FBI Kids’ Page Federal Bureau of Investigation (FBI) http: //www. fbi. gov/fbikids. htm l Future State U. S. Department of States http: //www. future. state. gov/ l Ready Kids Department of Homeland Security http: //www. ready. gov/kids/home. html l Copyright ETPRO