Weekly Meeting 2018 May 09 Security Working Group












- Slides: 47

Weekly Meeting 2018 May 09 Security Working Group edgexfoundry. org | @edgexfoundry

2018 May 09 Security Working Group Meeting Agenda Week May 09 Meeting Focus • Review Apr 14 Meeting Notes • Riaz will provide a Messy Update ; ) • Rodney Hess will provide results of research on what cert format should used to store in vault • What’s Next for Delhi Discussion • See next slide edgexfoundry. org | @edgexfoundry

Review Last Meeting Notes (May 14, 2018) • Rodney Hess will provide results of research on what cert format should used to store in vault • Having issues with Go and will move on without the GO implementation • Looking at using PKCS#12 format and Java • Walked through Delhi discussion points. The team will work on generating a backlog list for Delhi that we will go through next week. • Next Week • Riaz Messy Update • Rodney Hess will provide results of research on what cert format should used to store in vault • Tingyu to propose CA ideas for Delhi • Create Prioritized Backlog for Delhi and beyond edgexfoundry. org | @edgexfoundry

Messy Update ; ) • Riaz to provide an update on discussion and actions • Other to provide their update edgexfoundry. org | @edgexfoundry

Rodney Hess To Present Results of research on what cert format should used to store in vault edgexfoundry. org | @edgexfoundry

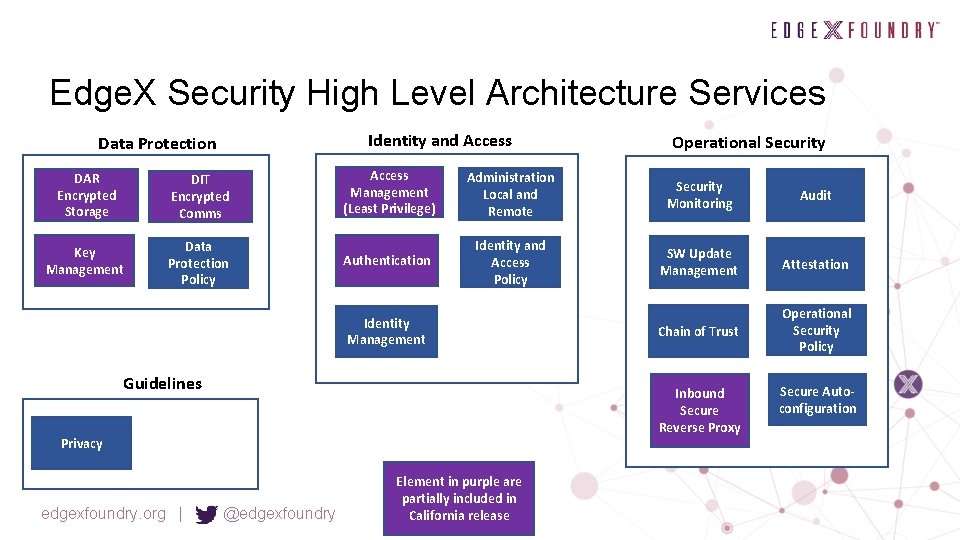
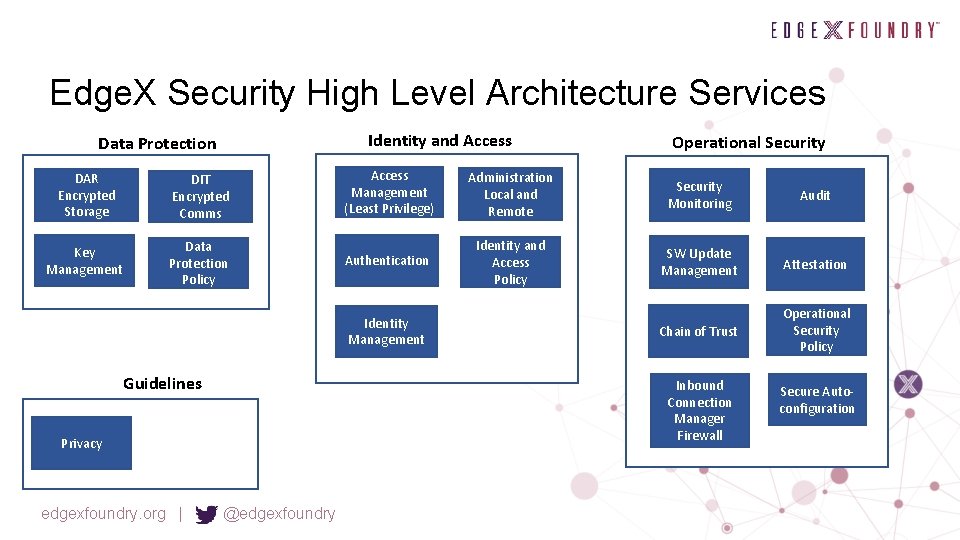
Edge. X Security High Level Architecture Services Identity and Access Data Protection DAR Encrypted Storage DIT Encrypted Comms Key Management Data Protection Policy Access Management (Least Privilege) Administration Local and Remote Security Monitoring Audit Authentication Identity and Access Policy SW Update Management Attestation Chain of Trust Operational Security Policy Identity Management Guidelines Inbound Secure Reverse Proxy Privacy edgexfoundry. org | Operational Security @edgexfoundry Element in purple are partially included in California release Secure Autoconfiguration

Delhi Discussion • What’s Next for Delhi Discussion Points • What do we need to start to test and how? Do we need to consider frameworks/tools for pen testing, etc. ? • Riaz and Jim running a sub-group within the security working group • When/how do we start to address the threat model/evaluation again? • What other functions do we need to start on coming from the security roadmap below? For that matter, is this roadmap still valid or do we need to think about some adjustments or making it more fine grain in certain areas? • Do we need a south bound reverse proxy? Initial thoughts are no. Security WG only needs to provide certificate API access to other south bound servers (like MQTTS) edgexfoundry. org | @edgexfoundry

Meeting Notes (May 09, 2018) • IIC Security Level Discussion • • Gateway should allow a hardware root of trust Gateway should meet Security Level Basic Prepared for support of Security Level Enhance and Security Level Critical via API. Vendors would add their products to Edge. X to achieve SLE and SLC • Rodney discussed Cert Format • • Using a key value pair Will be using PKCS#12 format • Tingyu discussed high level ideas around CA • • Discussed using Vault interface or using Vault CA Target local CA for Delhi • Discussed Delhi backlog • • • Reverse proxy does not need to change to allow MQTTS for Delhi. North bound interface will only support HTTP and HTTPS. Every micro service needs to have an identity – may be a cert or other. Edge. X gateway will support multi-tenancy in the future and we need to take that into account. • Next week. • • • Rodney to present integration between Kong and Vault for certificate handling Tingyu to present CA ideas for Delhi Continue Delhi backlog discussion edgexfoundry. org | @edgexfoundry

Meeting Attendees (May 09, 2018) edgexfoundry. org | @edgexfoundry

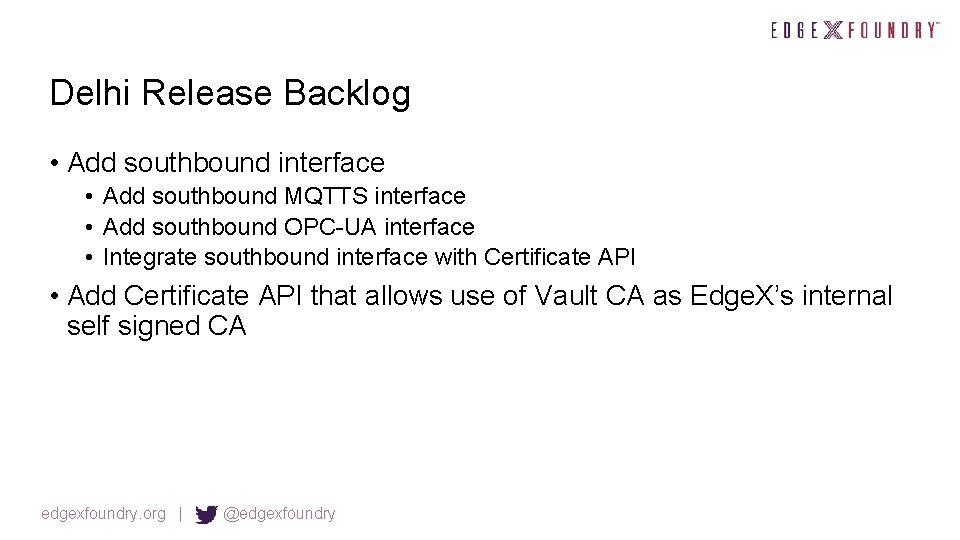
Delhi Release Backlog • Add southbound interface • Add southbound MQTTS interface • Add southbound OPC-UA interface • Integrate southbound interface with Certificate API • Add Certificate API that allows use of Vault CA as Edge. X’s internal self signed CA edgexfoundry. org | @edgexfoundry

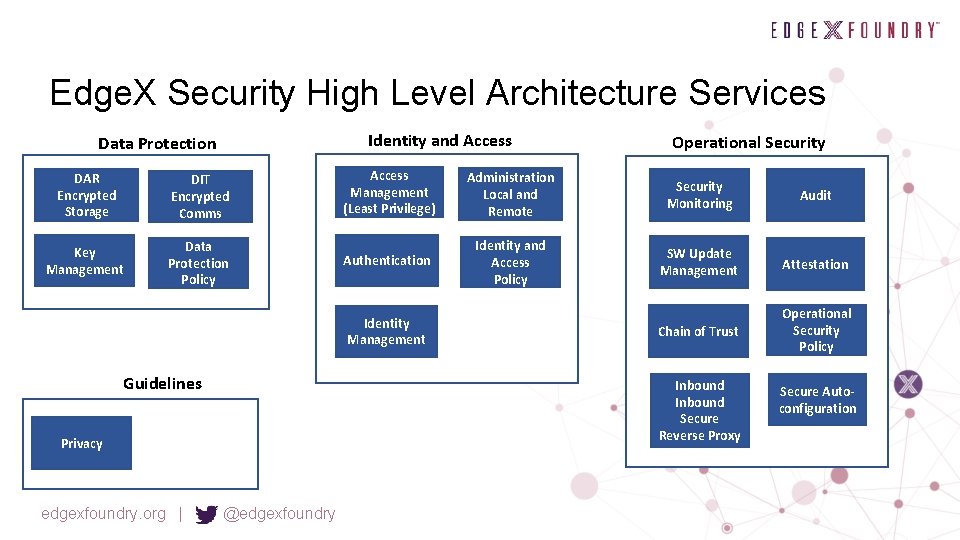
Edge. X Security High Level Architecture Services Identity and Access Data Protection DAR Encrypted Storage DIT Encrypted Comms Key Management Data Protection Policy Access Management (Least Privilege) Administration Local and Remote Security Monitoring Audit Authentication Identity and Access Policy SW Update Management Attestation Chain of Trust Operational Security Policy Identity Management Guidelines Inbound Secure Reverse Proxy Privacy edgexfoundry. org | Operational Security @edgexfoundry Secure Autoconfiguration

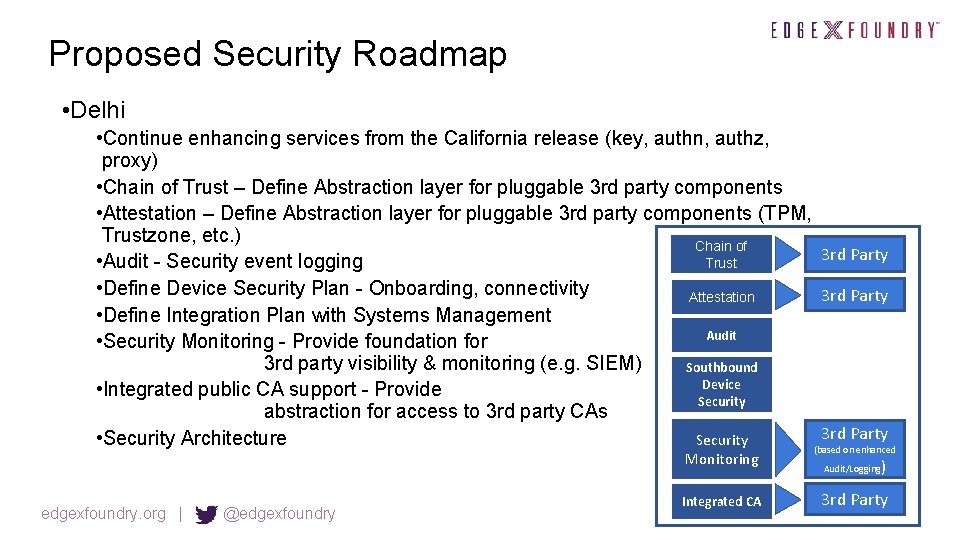
Proposed Security Roadmap • Delhi • Continue enhancing services from the California release (key, authn, authz, proxy) • Chain of Trust – Define Abstraction layer for pluggable 3 rd party components • Attestation – Define Abstraction layer for pluggable 3 rd party components (TPM, Trustzone, etc. ) Chain of 3 rd Party Trust • Audit - Security event logging • Define Device Security Plan - Onboarding, connectivity 3 rd Party Attestation • Define Integration Plan with Systems Management Audit • Security Monitoring - Provide foundation for 3 rd party visibility & monitoring (e. g. SIEM) Southbound Device • Integrated public CA support - Provide Security abstraction for access to 3 rd party CAs 3 rd Party • Security Architecture Security (based on enhanced Monitoring edgexfoundry. org | @edgexfoundry Integrated CA Audit/Logging ) 3 rd Party

Inbound Connection Manager Firewall (Priority #1) Discussion topics Technical Lead: David Ferriera (Forgerock)

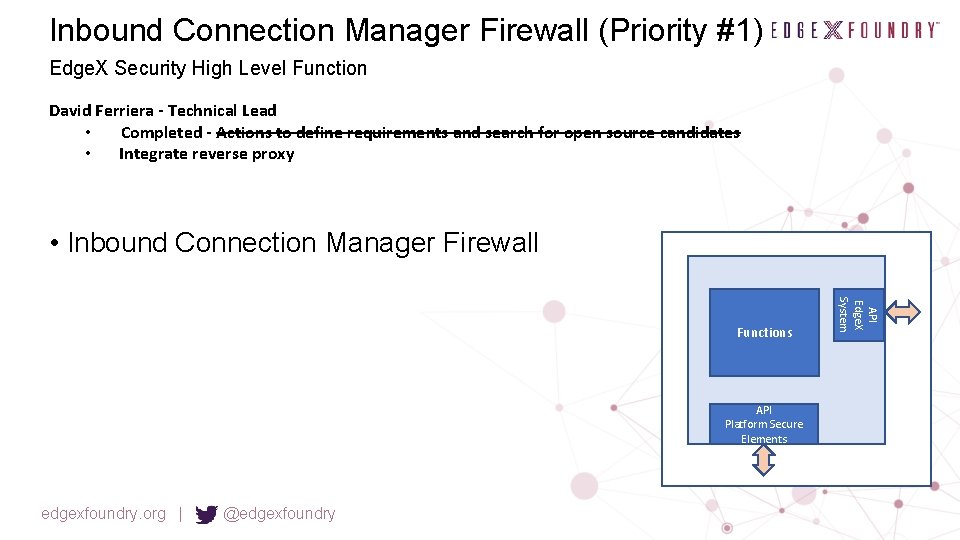
Inbound Connection Manager Firewall (Priority #1) Edge. X Security High Level Function David Ferriera - Technical Lead • Completed - Actions to define requirements and search for open source candidates • Integrate reverse proxy • Inbound Connection Manager Firewall API Platform Secure Elements edgexfoundry. org | @edgexfoundry API Edge. X System Functions

Internal Microservice Security Protocol (Priority #3) Edge. X Security High Level Function On Hold • Internal Micro service Security Protocol • ? ? API Platform Secure Elements edgexfoundry. org | @edgexfoundry API Edge. X System Functions

Other Priority Items Volunteer Please!! edgexfoundry. org | @edgexfoundry

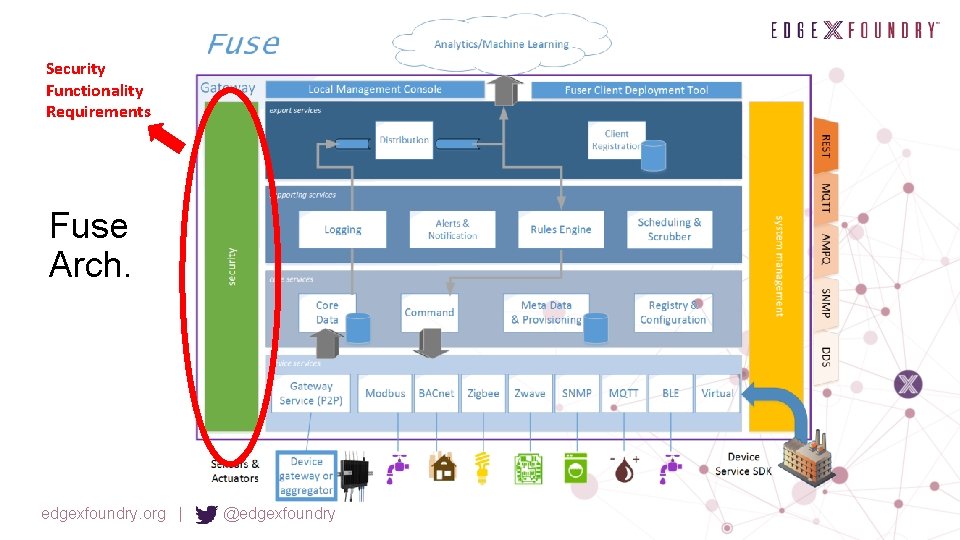
Security Functionality Requirements Fuse Arch. edgexfoundry. org | @edgexfoundry

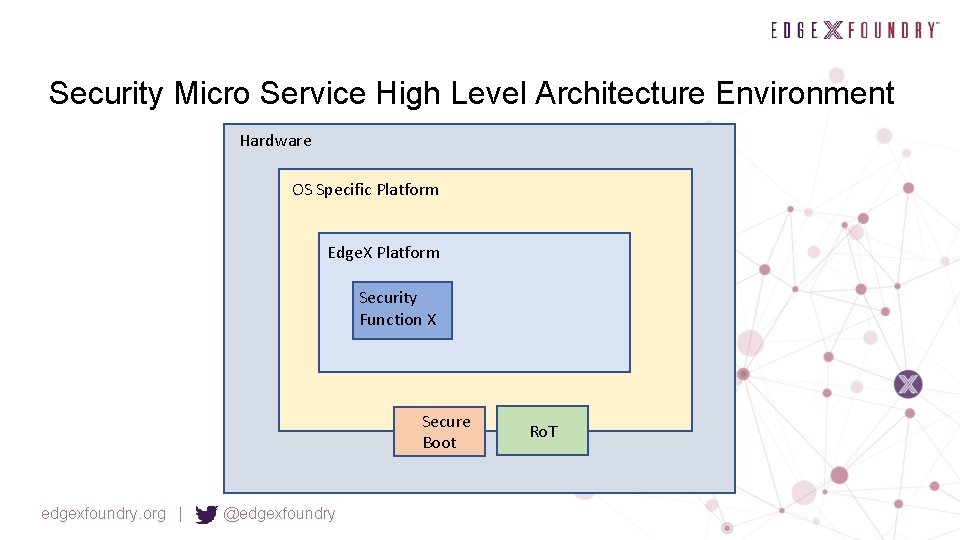
Security Micro Service High Level Architecture Environment Hardware OS Specific Platform Edge. X Platform Security Function X Secure Boot edgexfoundry. org | @edgexfoundry Ro. T

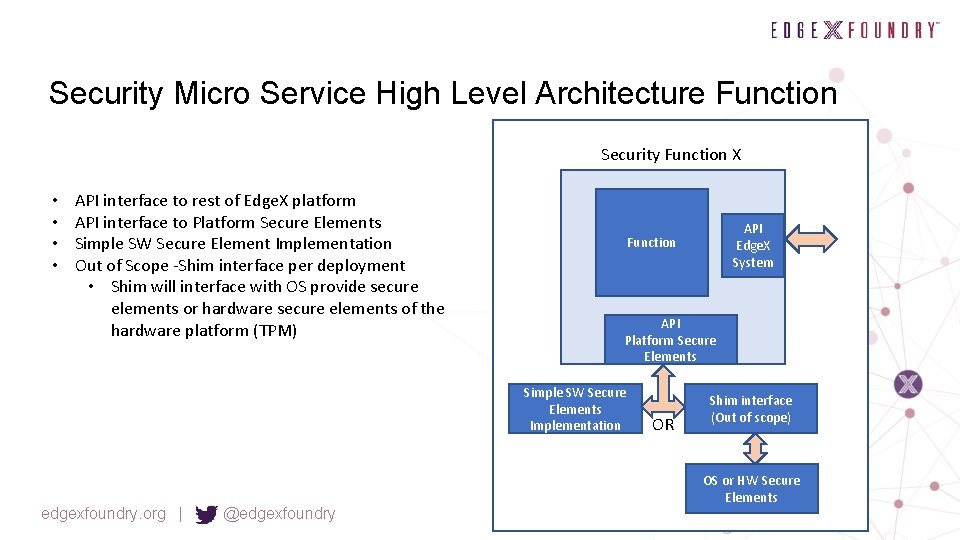
Security Micro Service High Level Architecture Function Security Function X • • API interface to rest of Edge. X platform API interface to Platform Secure Elements Simple SW Secure Element Implementation Out of Scope -Shim interface per deployment • Shim will interface with OS provide secure elements or hardware secure elements of the hardware platform (TPM) API Platform Secure Elements Simple SW Secure Elements Implementation edgexfoundry. org | @edgexfoundry API Edge. X System Function OR Shim interface (Out of scope) OS or HW Secure Elements

Edge. X Security High Level Architecture Services Identity and Access Data Protection DAR Encrypted Storage DIT Encrypted Comms Key Management Data Protection Policy Access Management (Least Privilege) Administration Local and Remote Security Monitoring Audit Authentication Identity and Access Policy SW Update Management Attestation Chain of Trust Operational Security Policy Identity Management Guidelines Inbound Connection Manager Firewall Privacy edgexfoundry. org | Operational Security @edgexfoundry Secure Autoconfiguration

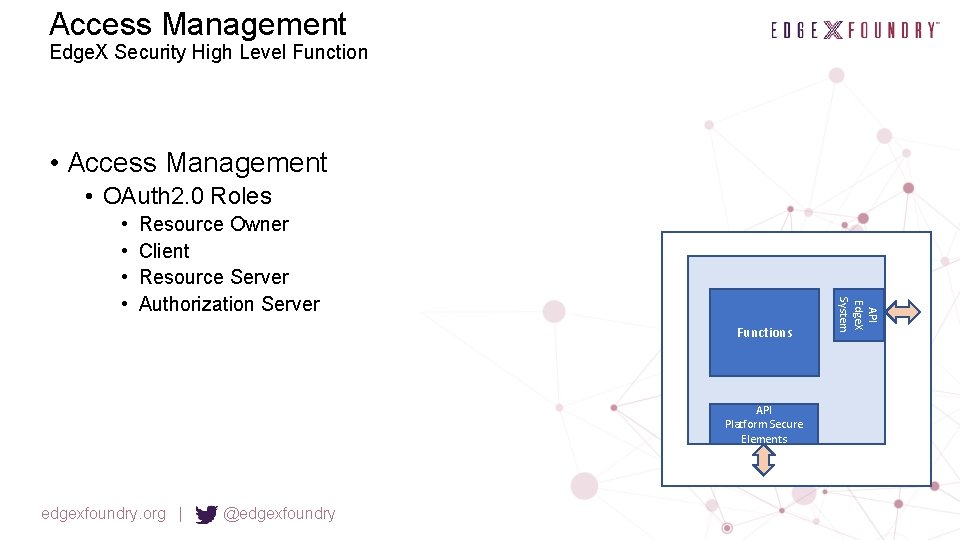
Access Management Edge. X Security High Level Function • Access Management • OAuth 2. 0 Roles Resource Owner Client Resource Server Authorization Server Functions API Platform Secure Elements edgexfoundry. org | @edgexfoundry API Edge. X System • •

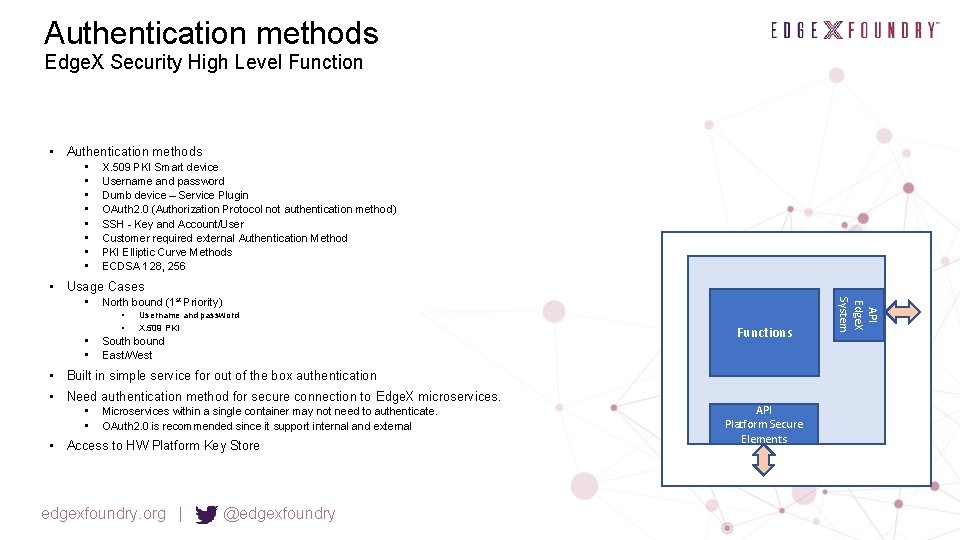
Authentication methods Edge. X Security High Level Function • Authentication methods • • X. 509 PKI Smart device Username and password Dumb device – Service Plugin OAuth 2. 0 (Authorization Protocol not authentication method) SSH - Key and Account/User Customer required external Authentication Method PKI Elliptic Curve Methods ECDSA 128, 256 • Usage Cases North bound (1 st Priority) • • Username and password X. 509 PKI South bound East/West Functions • Built in simple service for out of the box authentication • Need authentication method for secure connection to Edge. X microservices. • • Microservices within a single container may not need to authenticate. OAuth 2. 0 is recommended since it support internal and external • Access to HW Platform Key Store edgexfoundry. org | @edgexfoundry API Platform Secure Elements API Edge. X System •

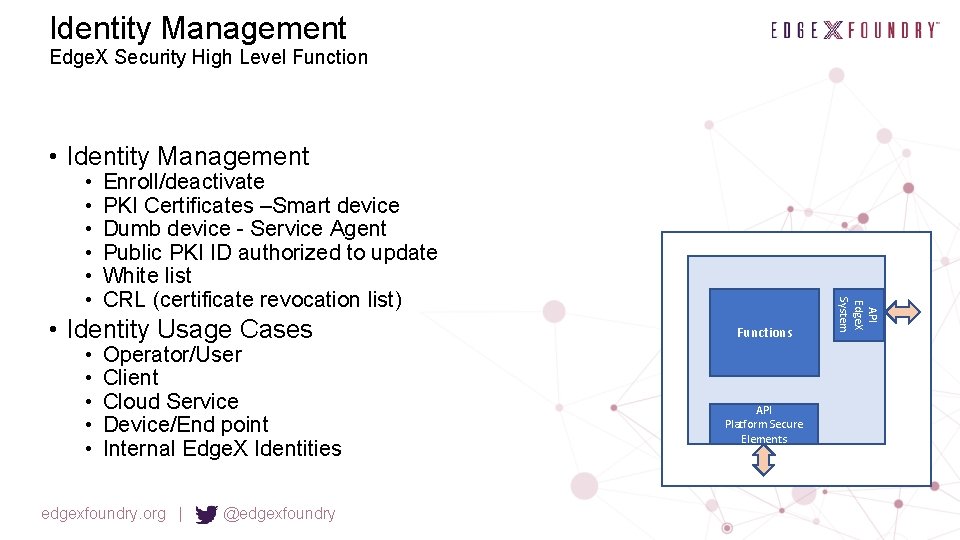
Identity Management Edge. X Security High Level Function • Identity Management Enroll/deactivate PKI Certificates –Smart device Dumb device - Service Agent Public PKI ID authorized to update White list CRL (certificate revocation list) • Identity Usage Cases • • • Operator/User Client Cloud Service Device/End point Internal Edge. X Identities edgexfoundry. org | @edgexfoundry Functions API Platform Secure Elements API Edge. X System • • •

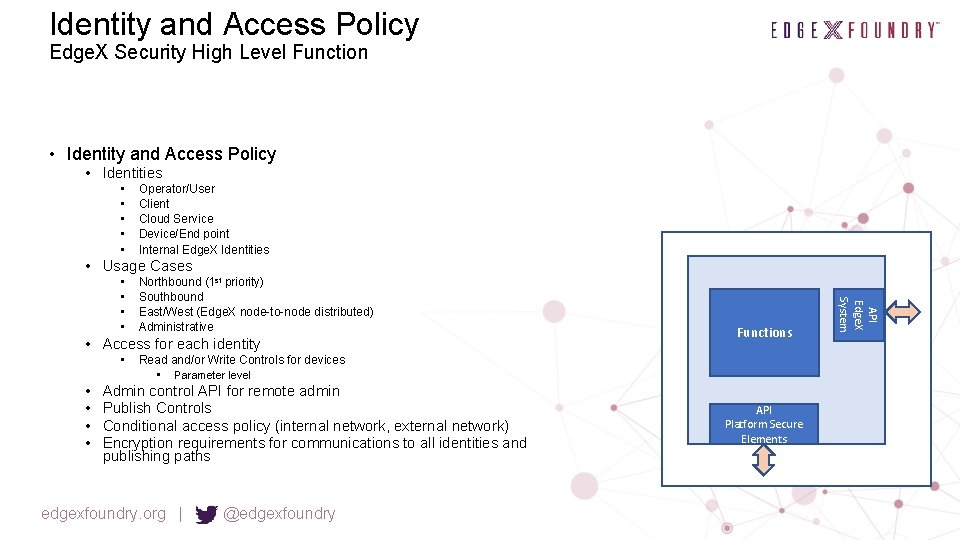
Identity and Access Policy Edge. X Security High Level Function • Identity and Access Policy • Identities • • • Operator/User Client Cloud Service Device/End point Internal Edge. X Identities • Usage Cases Northbound (1 st priority) Southbound East/West (Edge. X node-to-node distributed) Administrative • Access for each identity • • • Functions Read and/or Write Controls for devices • Parameter level Admin control API for remote admin Publish Controls Conditional access policy (internal network, external network) Encryption requirements for communications to all identities and publishing paths edgexfoundry. org | @edgexfoundry API Platform Secure Elements API Edge. X System • •

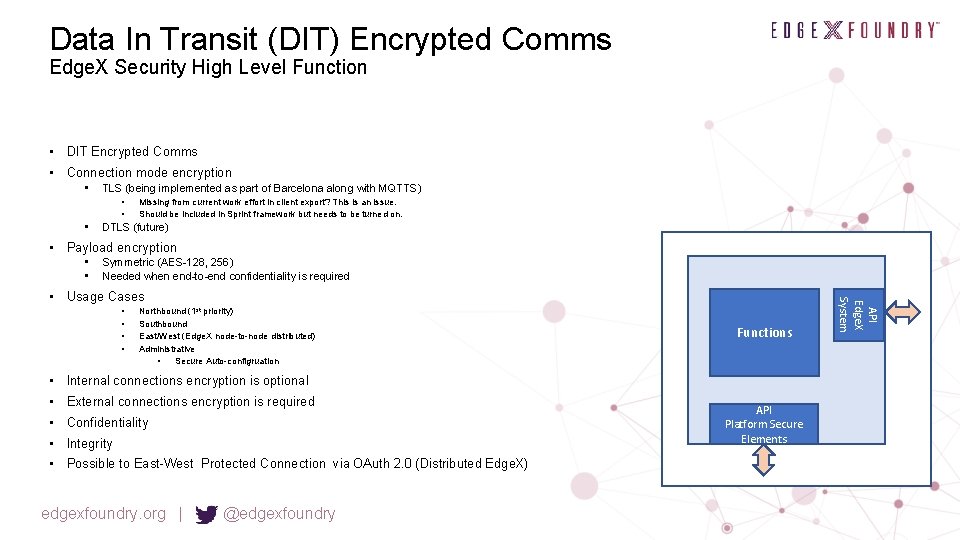
Data In Transit (DIT) Encrypted Comms Edge. X Security High Level Function • DIT Encrypted Comms • Connection mode encryption • TLS (being implemented as part of Barcelona along with MQTTS) • • • Missing from current work effort in client export? This is an issue. Should be included in Sprint framework but needs to be turned on. DTLS (future) • Payload encryption • • Symmetric (AES-128, 256) Needed when end-to-end confidentiality is required • • Northbound (1 st priority) Southbound East/West (Edge. X node-to-node distributed) Administrative • Secure Auto-configruation Functions • Internal connections encryption is optional • External connections encryption is required • Confidentiality • Integrity • Possible to East-West Protected Connection via OAuth 2. 0 (Distributed Edge. X) edgexfoundry. org | @edgexfoundry API Platform Secure Elements API Edge. X System • Usage Cases

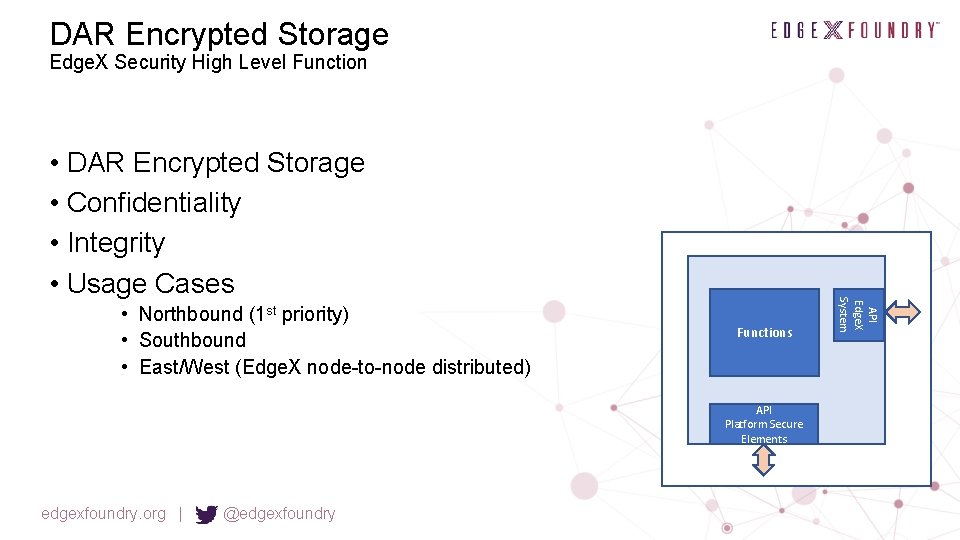
DAR Encrypted Storage Edge. X Security High Level Function • Northbound (1 st priority) • Southbound • East/West (Edge. X node-to-node distributed) Functions API Platform Secure Elements edgexfoundry. org | @edgexfoundry API Edge. X System • DAR Encrypted Storage • Confidentiality • Integrity • Usage Cases

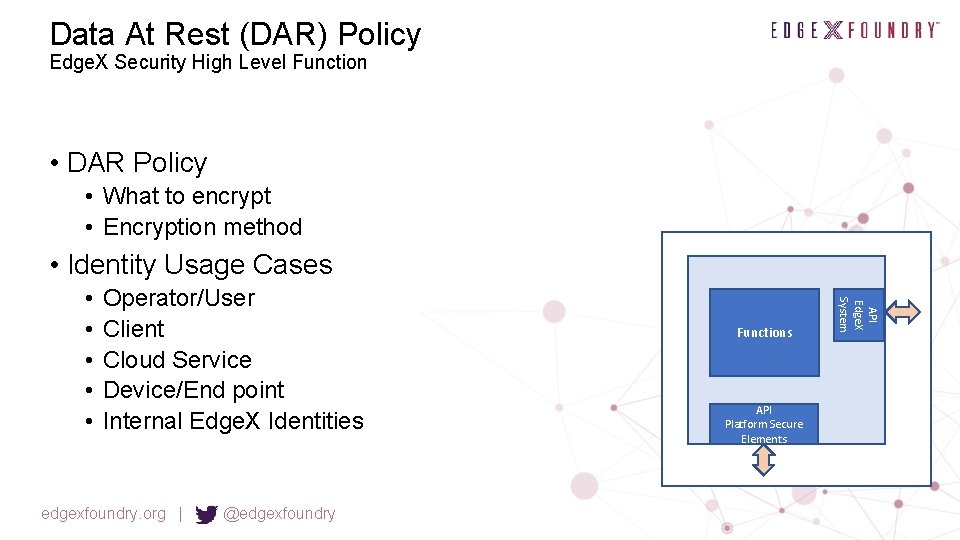
Data At Rest (DAR) Policy Edge. X Security High Level Function • DAR Policy • What to encrypt • Encryption method • Identity Usage Cases Operator/User Client Cloud Service Device/End point Internal Edge. X Identities edgexfoundry. org | @edgexfoundry Functions API Platform Secure Elements API Edge. X System • • •

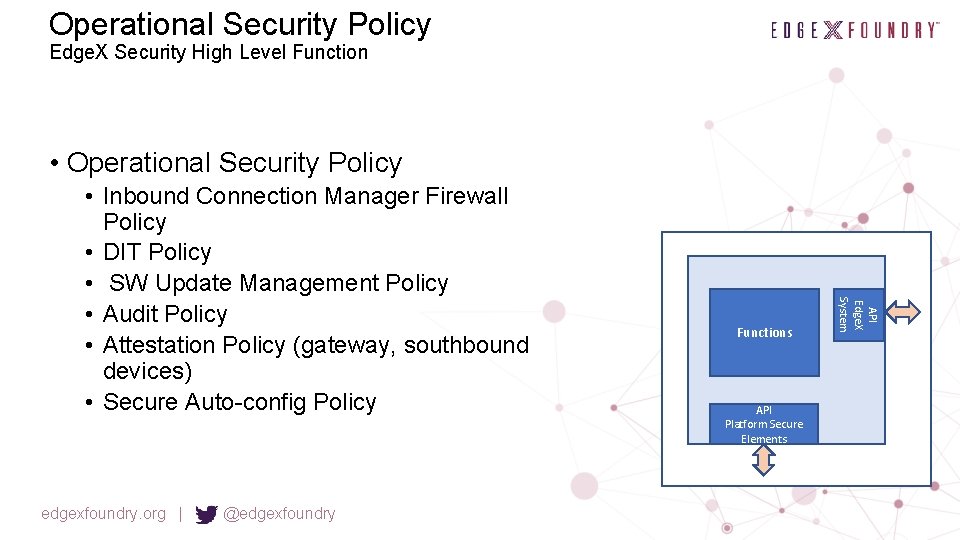
Operational Security Policy Edge. X Security High Level Function • Operational Security Policy edgexfoundry. org | @edgexfoundry Functions API Platform Secure Elements API Edge. X System • Inbound Connection Manager Firewall Policy • DIT Policy • SW Update Management Policy • Audit Policy • Attestation Policy (gateway, southbound devices) • Secure Auto-config Policy

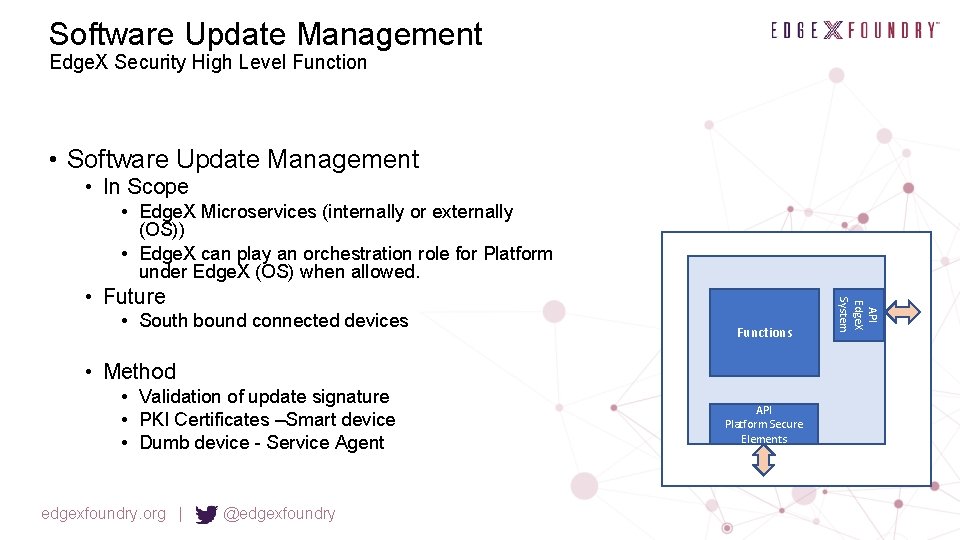
Software Update Management Edge. X Security High Level Function • Software Update Management • In Scope • Edge. X Microservices (internally or externally (OS)) • Edge. X can play an orchestration role for Platform under Edge. X (OS) when allowed. • South bound connected devices Functions • Method • Validation of update signature • PKI Certificates –Smart device • Dumb device - Service Agent edgexfoundry. org | @edgexfoundry API Platform Secure Elements API Edge. X System • Future

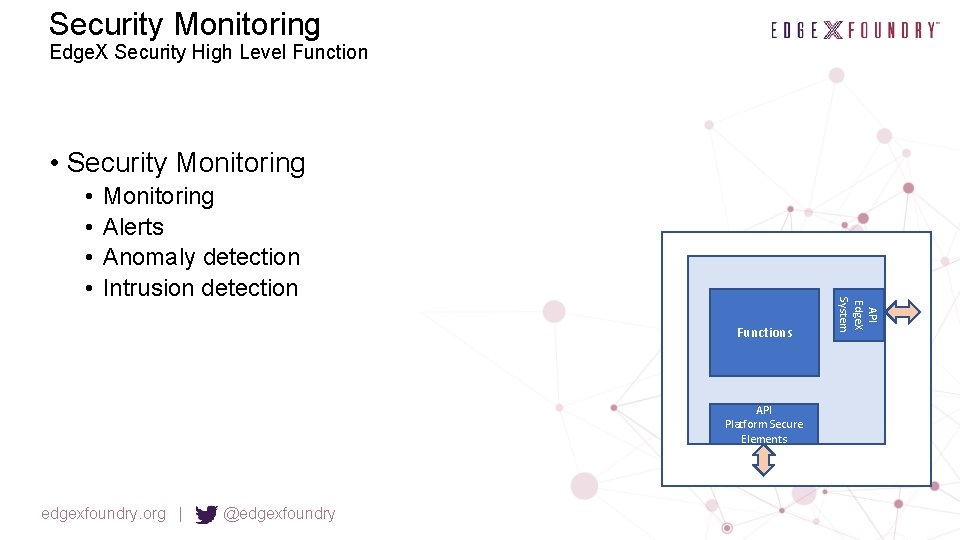
Security Monitoring Edge. X Security High Level Function • Security Monitoring Alerts Anomaly detection Intrusion detection Functions API Platform Secure Elements edgexfoundry. org | @edgexfoundry API Edge. X System • •

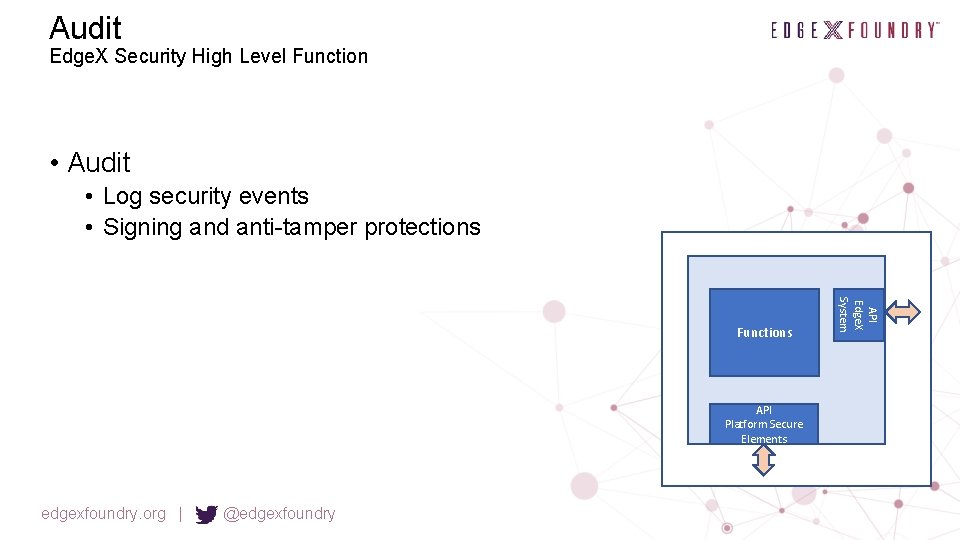
Audit Edge. X Security High Level Function • Audit • Log security events • Signing and anti-tamper protections API Platform Secure Elements edgexfoundry. org | @edgexfoundry API Edge. X System Functions

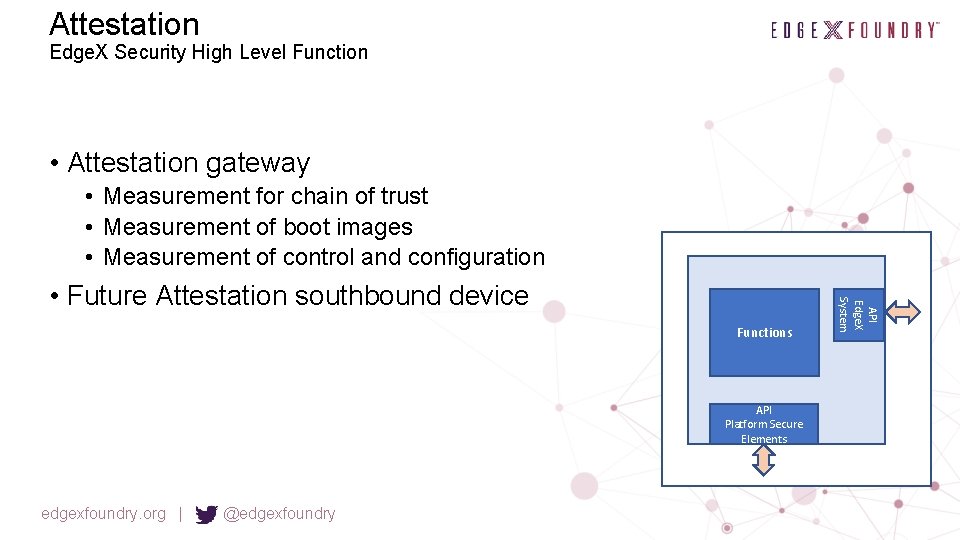
Attestation Edge. X Security High Level Function • Attestation gateway • Measurement for chain of trust • Measurement of boot images • Measurement of control and configuration Functions API Platform Secure Elements edgexfoundry. org | @edgexfoundry API Edge. X System • Future Attestation southbound device

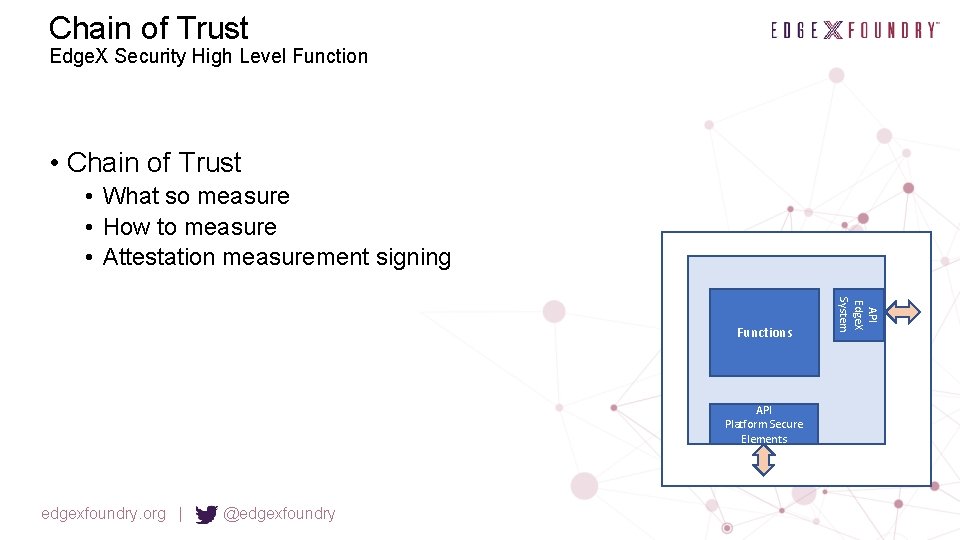
Chain of Trust Edge. X Security High Level Function • Chain of Trust • What so measure • How to measure • Attestation measurement signing API Platform Secure Elements edgexfoundry. org | @edgexfoundry API Edge. X System Functions

Privacy Edge. X Security High Level Function • Privacy • Needs to be taken into consideration • Consumer • Health Care (HIPA) • EU Requirements API Platform Secure Elements edgexfoundry. org | @edgexfoundry API Edge. X System Functions

Hardware Platform Required Security Functionality Edge. X Security High Level Architecture HW TEE Secure Update Key Store Digital Signature Algorithm TRNG Attestation/Tru sted Boot Secure Boot edgexfoundry. org | @edgexfoundry

HW TEE (Trusted Execution Environment) Edge. X Security High Level Function • HW TEE (Trusted Execution Environment) • Required in platform to protect and isolate security sensitive values API Platform Secure Elements edgexfoundry. org | @edgexfoundry API Edge. X System Functions

Key Store Edge. X Security High Level Function • Key Store • Required in platform to protect stored keys API Platform Secure Elements edgexfoundry. org | @edgexfoundry API Edge. X System Functions

RNG (Random Number Generator) Edge. X Security High Level Function • RNG (Random Number Generator) • TRNG (True Random Number Generator) • DRNG (Deterministic RNG) API Platform Secure Elements edgexfoundry. org | @edgexfoundry API Edge. X System Functions

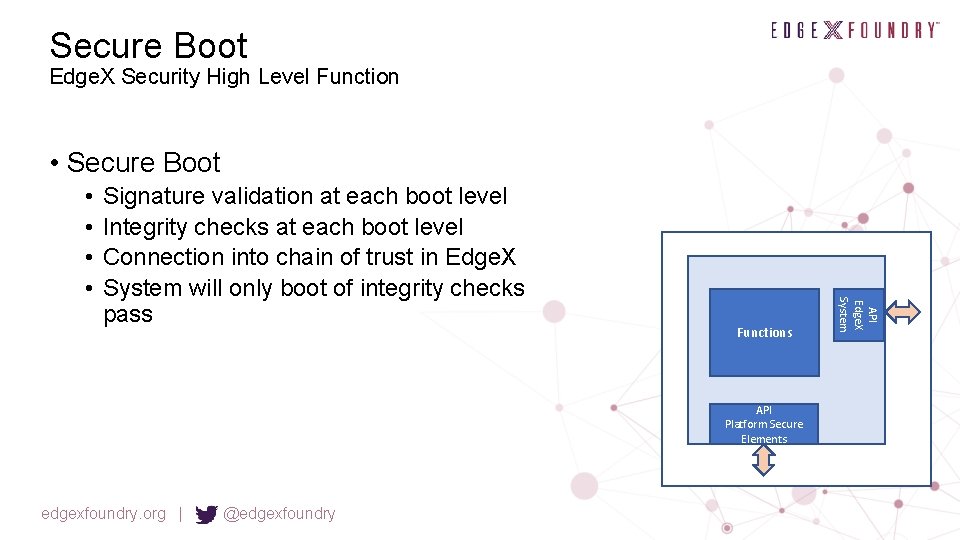
Secure Boot Edge. X Security High Level Function • Secure Boot Signature validation at each boot level Integrity checks at each boot level Connection into chain of trust in Edge. X System will only boot of integrity checks pass Functions API Platform Secure Elements edgexfoundry. org | @edgexfoundry API Edge. X System • •

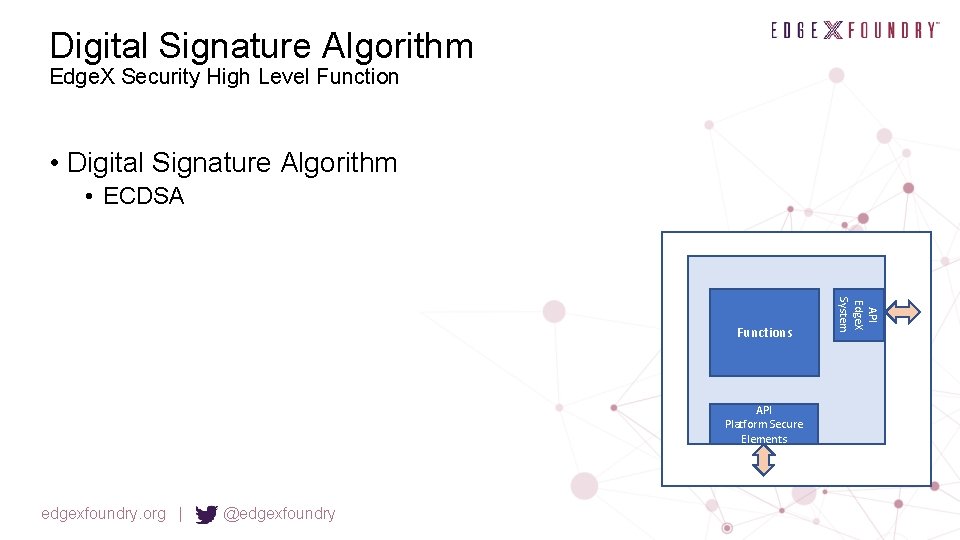
Digital Signature Algorithm Edge. X Security High Level Function • Digital Signature Algorithm • ECDSA API Platform Secure Elements edgexfoundry. org | @edgexfoundry API Edge. X System Functions

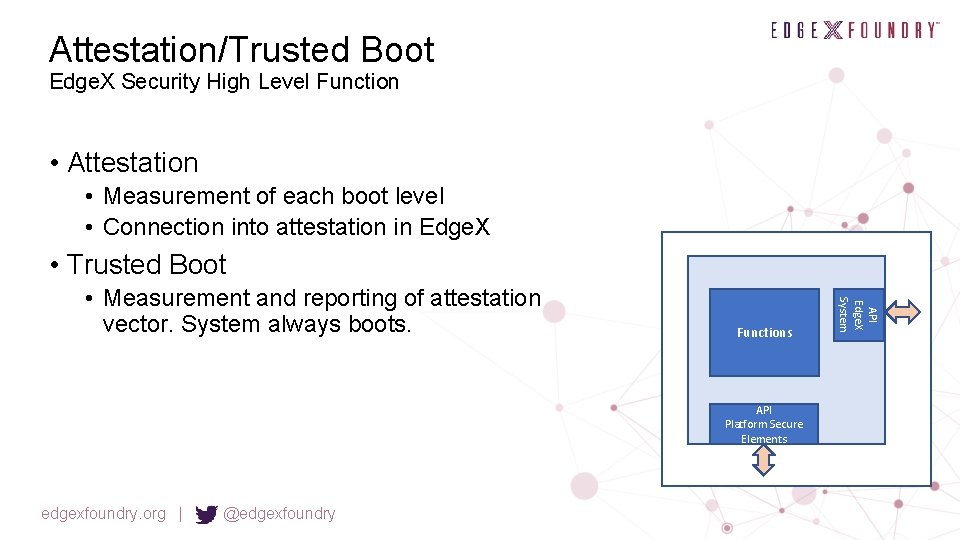
Attestation/Trusted Boot Edge. X Security High Level Function • Attestation • Measurement of each boot level • Connection into attestation in Edge. X • Trusted Boot Functions API Platform Secure Elements edgexfoundry. org | @edgexfoundry API Edge. X System • Measurement and reporting of attestation vector. System always boots.

Edge. X Security High Level Architecture Open Questions • Out of Scope - Provide guidance on how security features can/should be tested edgexfoundry. org | @edgexfoundry

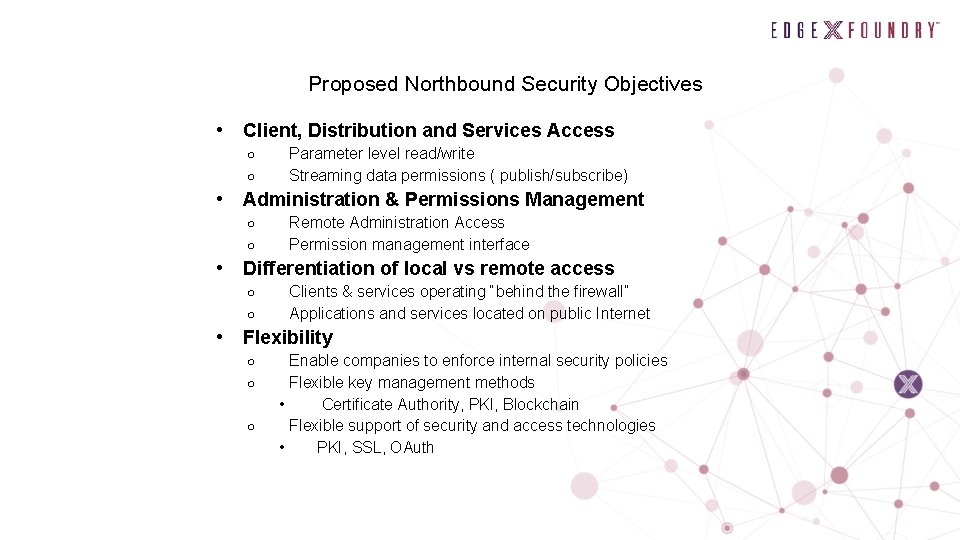
Proposed Northbound Security Objectives • Client, Distribution and Services Access ○ ○ • Administration & Permissions Management ○ ○ • Remote Administration Access Permission management interface Differentiation of local vs remote access ○ ○ • Parameter level read/write Streaming data permissions ( publish/subscribe) Clients & services operating “behind the firewall” Applications and services located on public Internet Flexibility ○ ○ ○ Enable companies to enforce internal security policies Flexible key management methods • Certificate Authority, PKI, Blockchain Flexible support of security and access technologies • PKI, SSL, OAuth

Edge. X Northbound Connection Example Use Case • • Edge. X Gateway Connection is initiated from Edge. X to Cloud Set up a mutually authenticated TLS connection using x. 509 methods Certificate Handling • Provisioning, renewal, • Use OS certificate store and services • Required to use export service to obtain a connection • Policy service • Who can talk to who, read, write, connection type • Initial settings of Edge. X to configure Cloud connection edgexfoundry. org | @edgexfoundry

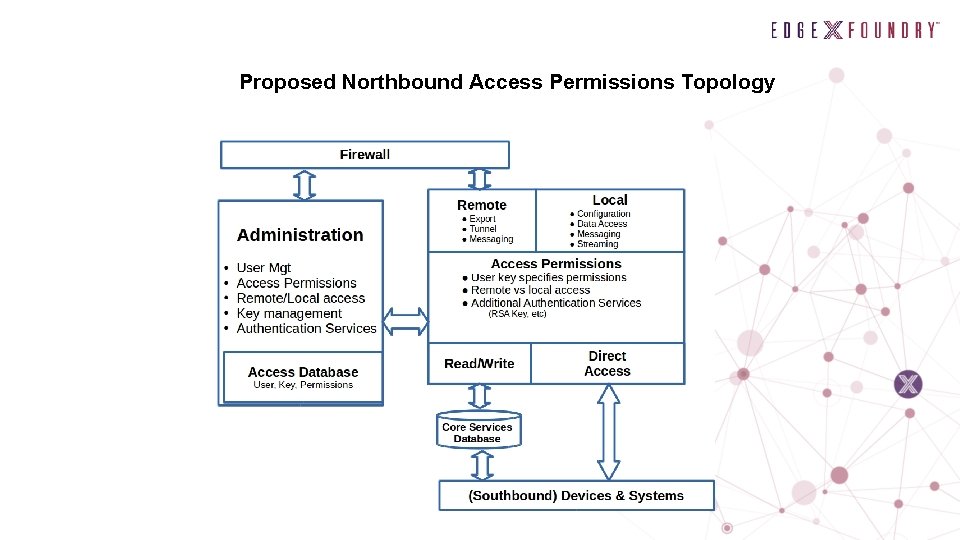
Proposed Northbound Access Permissions Topology

Past Security Agreements 1. 2. 3. 4. 5. 6. 7. 8. “Fuse microservices to enforce access control, authentication, and authorization (AAA). ” – Also needs to support smart end points to cloud (AAA) Needs to support tunneled and encrypted sensor data to the cloud – Gateway in pass through mode only. Specifies Gateway administrator provisions devices. Should also allow for smart devices to connect to cloud in pass through mode. “Rely on installation-unique credentials for protecting access to any of the Fuse repositories. ” – Add support for Smart end points support (certificate, authentication, integrity, optional encryption) “Documentation provided with Fuse should strongly recommend that implementers expose HTTPS only. ” – Needs to require TLS 2. 0 or higher, down grade to unsecure modes should be flagged as insecure by Edge. X. “For those subscribers of MQTT data, there is no ability to protect sensitive data in transit” – This statement is in error. Typical protection is provided by a TLS layer that MQTT is tunneled through. Mangement Use Cases “Edge. X Administrator updates software” – This is only the Edge. X software upgrade and not end devices. Needs to support upgrade of devices from cloud to device in pass through mode to support various vendor methods. Control Use Cases “Edge. X published all data” – Need to change to allow for smart devices to publishing data directly to cloud. edgexfoundry. org | @edgexfoundry

Back Up – High Level Architecture edgexfoundry. org | @edgexfoundry