Vulnerabilities of Passive Internet Threat Monitors Yoichi Shinoda

Vulnerabilities of Passive Internet Threat Monitors Yoichi Shinoda Japan Advanced Institute of Science and Technology Ko Ikai National Police Agency, Japan Motomu Itoh JPCERT/CC

Passive Internet Threat Monitors l Passive Internet monitoring measures and characterizes interesting network activity – l e. g. worms, distributed Do. S attacks, etc. The operation of Internet threat monitors assumes that sensors are observing only non -biased background traffic.
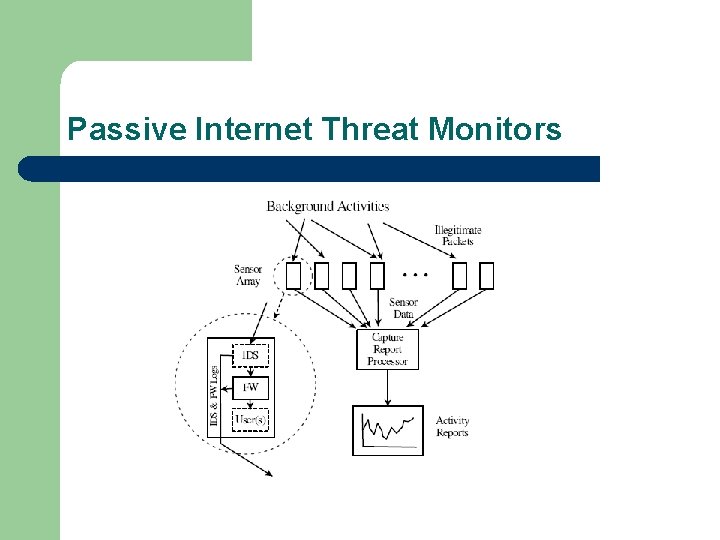
Passive Internet Threat Monitors
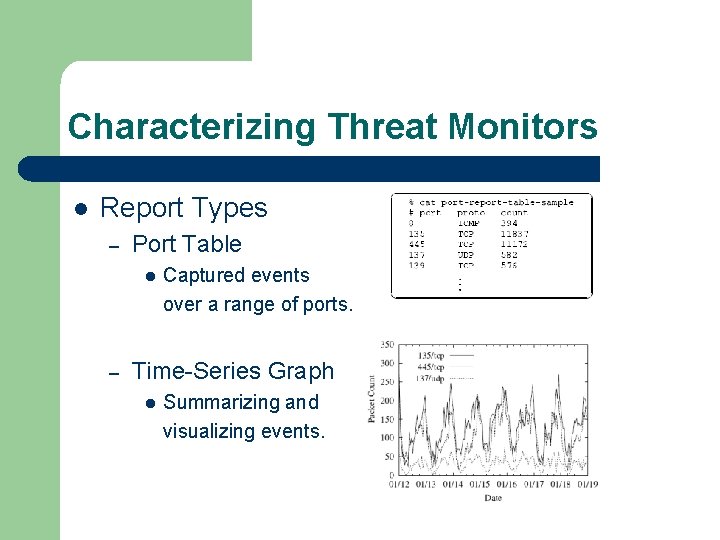
Characterizing Threat Monitors l Report Types – Port Table l – Captured events over a range of ports. Time-Series Graph l Summarizing and visualizing events.
The Problem l The addresses of real network monitor sensors can be identified. – – – l Sensors may be fed with arbitrary packets. Sensors may become Do. S victims. Sensors may be evaded. Sensor attackers or evaders do not require a complete list of sensor addresses.
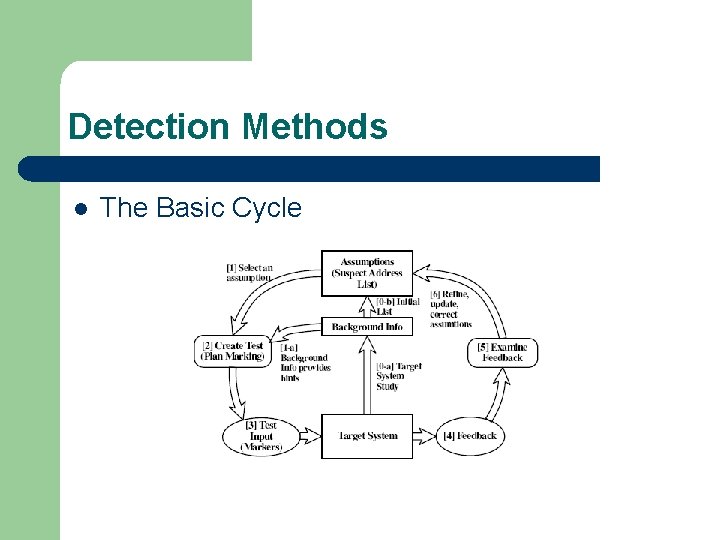
Detection Methods l The Basic Cycle
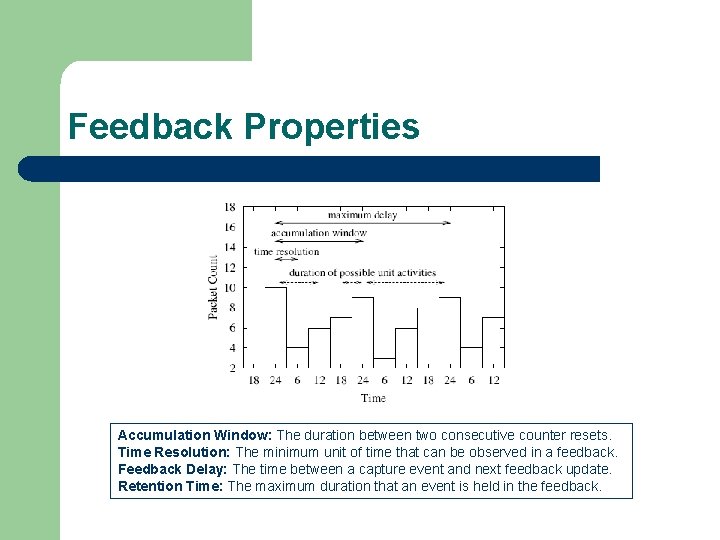
Feedback Properties Accumulation Window: The duration between two consecutive counter resets. Time Resolution: The minimum unit of time that can be observed in a feedback. Feedback Delay: The time between a capture event and next feedback update. Retention Time: The maximum duration that an event is held in the feedback.
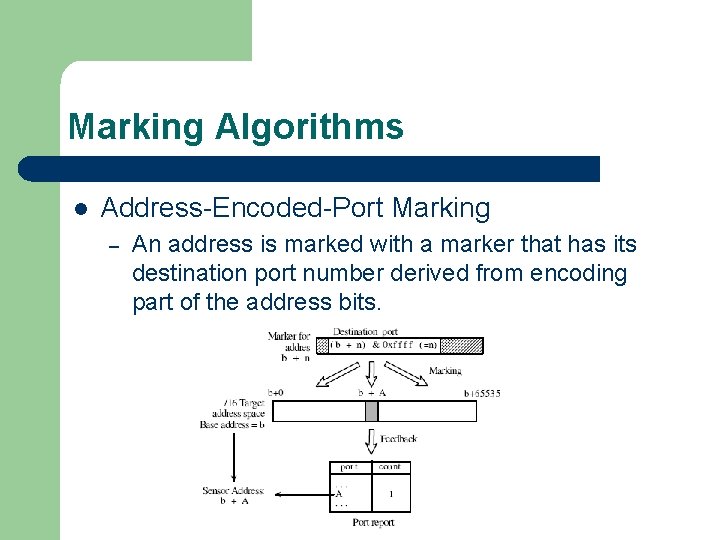
Marking Algorithms l Address-Encoded-Port Marking – An address is marked with a marker that has its destination port number derived from encoding part of the address bits.

Marking Algorithms l Time Series Marking – Each sub-block is marked within the time resolution window of the feedback so that results from marking can be reverse back to the corresponding sub-block.
Marking Algorithms l Uniform Intensity Marking (1/2) – – – All addresses are marked with the same intensity. Address blocks are divided into smaller subblocks. Each sub-block is marked using time-series marking, each address with a single marker.
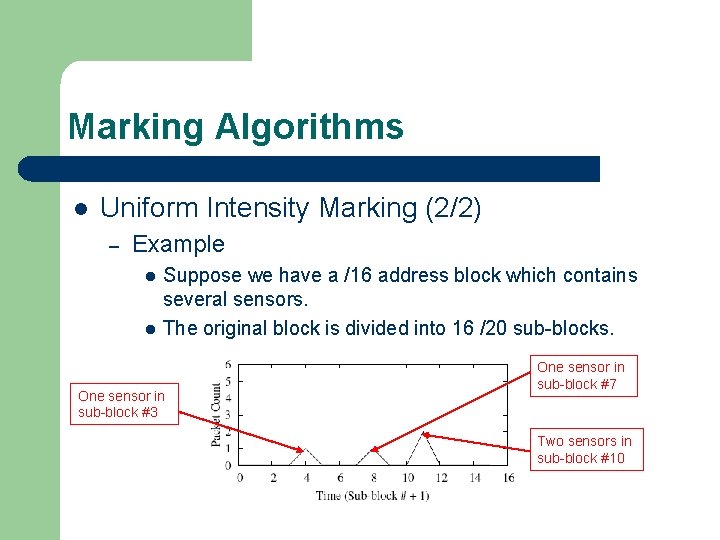
Marking Algorithms l Uniform Intensity Marking (2/2) – Example l l Suppose we have a /16 address block which contains several sensors. The original block is divided into 16 /20 sub-blocks. One sensor in sub-block #3 One sensor in sub-block #7 Two sensors in sub-block #10
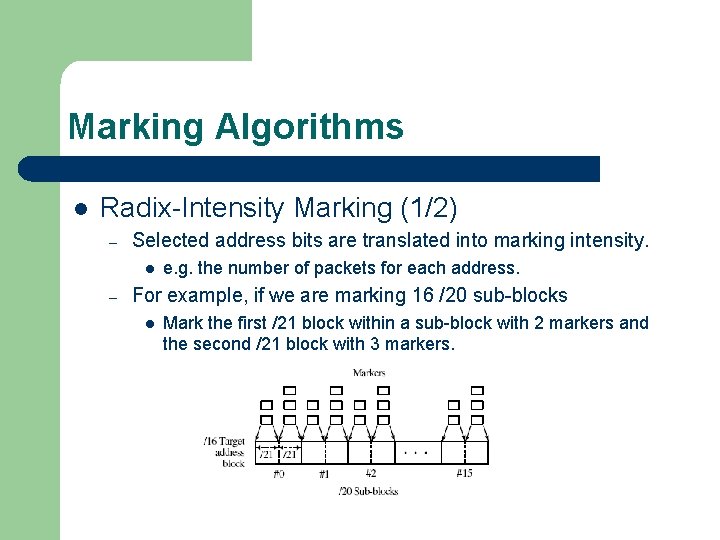
Marking Algorithms l Radix-Intensity Marking (1/2) – Selected address bits are translated into marking intensity. l – e. g. the number of packets for each address. For example, if we are marking 16 /20 sub-blocks l Mark the first /21 block within a sub-block with 2 markers and the second /21 block with 3 markers.
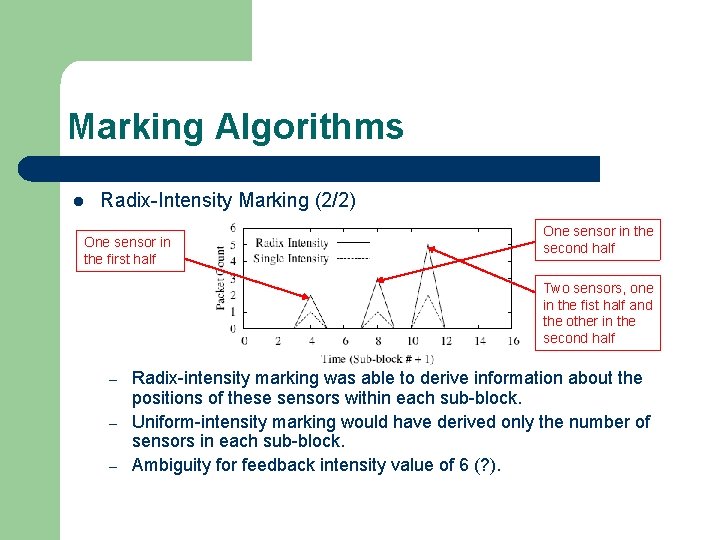
Marking Algorithms l Radix-Intensity Marking (2/2) One sensor in the first half One sensor in the second half Two sensors, one in the fist half and the other in the second half – – – Radix-intensity marking was able to derive information about the positions of these sensors within each sub-block. Uniform-intensity marking would have derived only the number of sensors in each sub-block. Ambiguity for feedback intensity value of 6 (? ).

Designing a Marking Activity l Target Range – l Decide on the range of addresses that we want to mark. Marking Algorithm – Determined by the properties of the feedback. Ø Ø l Table form Address-Encoded-Port marking Graph form Time-Series marking Marker Design – – – Marker type: proto, source and destination port. Source address. Payload.

Designing a Marking Activity l Intensity – l Bandwidth – l The speed with which marker packets can be generated. Address Range Subdivision – l Limiting factor. Velocity – l Number of markers sent to a single address. Calculated from the velocity and the intensity. Marking Order – Scramble the order in which we send the markers.
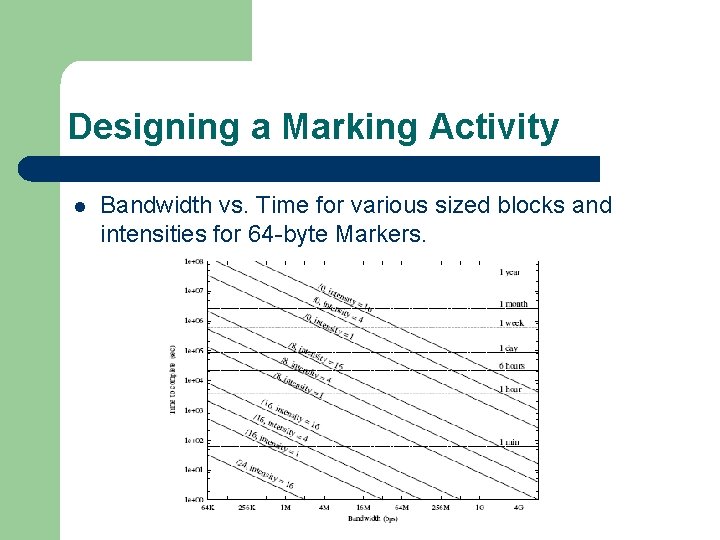
Designing a Marking Activity l Bandwidth vs. Time for various sized blocks and intensities for 64 -byte Markers.

Protecting Threat Monitors l Provide Less Information – Decrease the amount of information the system is giving out. l l E. g. longer accumulation window, less sensitivity, etc. Throttle the Information – Apply some standard remediation techniques that are being used to provide privacy in data mining.

Protecting Threat Monitors l Introducing Explicit Noise – – l Introduce explicit variance into level sensitivity into sensors. Inter-monitor collaboration. Disturbing Mark-Examine-Update Cycle – Degree of mobility required to disturb the cycle and how it affects monitor results must be studied.

Protecting Threat Monitors l Marking Detection – l Sensor Scale and Placement – l Events generated by marking activities are basically local and transient by nature. Increasing number of sensors that are carefully placed provide a certain level of protection. Small Cautions – – Prevent ICMP-based fingerprinting introduce TTL mangling
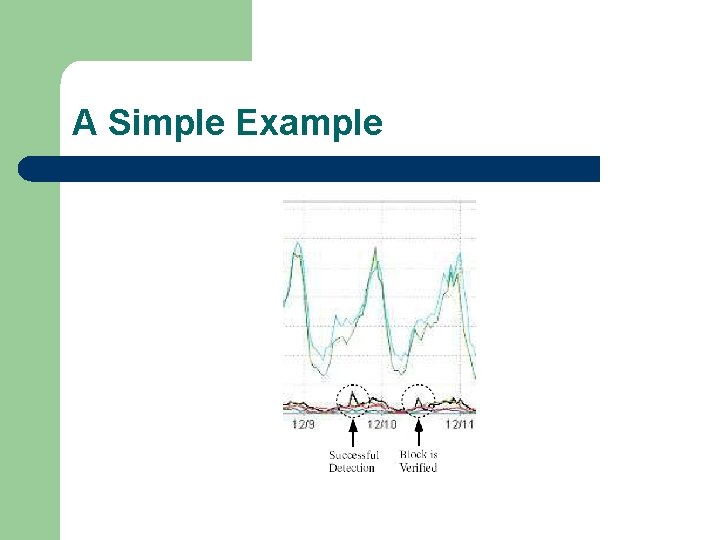
A Simple Example
- Slides: 20