CYBER THREAT INTELLIGENCE What is Threat Intelligence Threat

CYBER THREAT INTELLIGENCE

What is Threat Intelligence Threat intelligence is evidence-based knowledge, including context, mechanisms, indicators, implications and actionable advice, about an existing or emerging menace or hazard to assets that can be used to inform decisions regarding the subject’s response to that menace or hazard. ZERO | DAY | LIVE 2
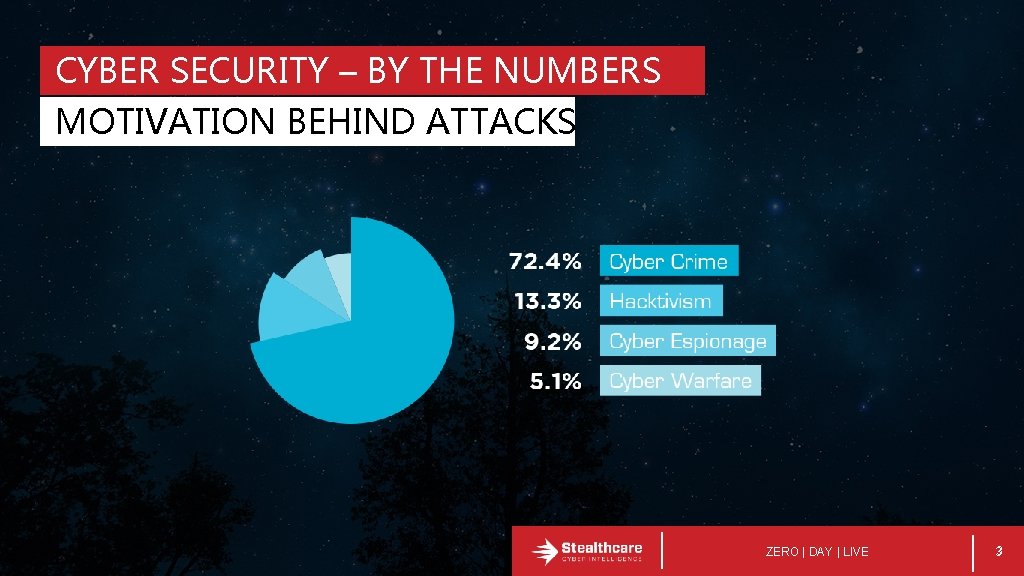
CYBER SECURITY – BY THE NUMBERS MOTIVATION BEHIND ATTACKS ZERO | DAY | LIVE 3
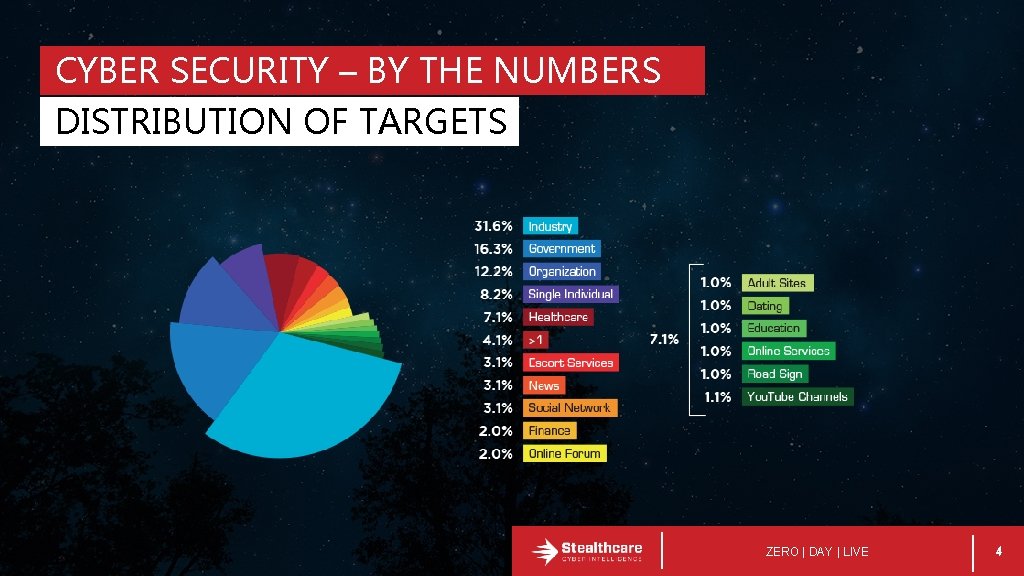
CYBER SECURITY – BY THE NUMBERS DISTRIBUTION OF TARGETS ZERO | DAY | LIVE 4
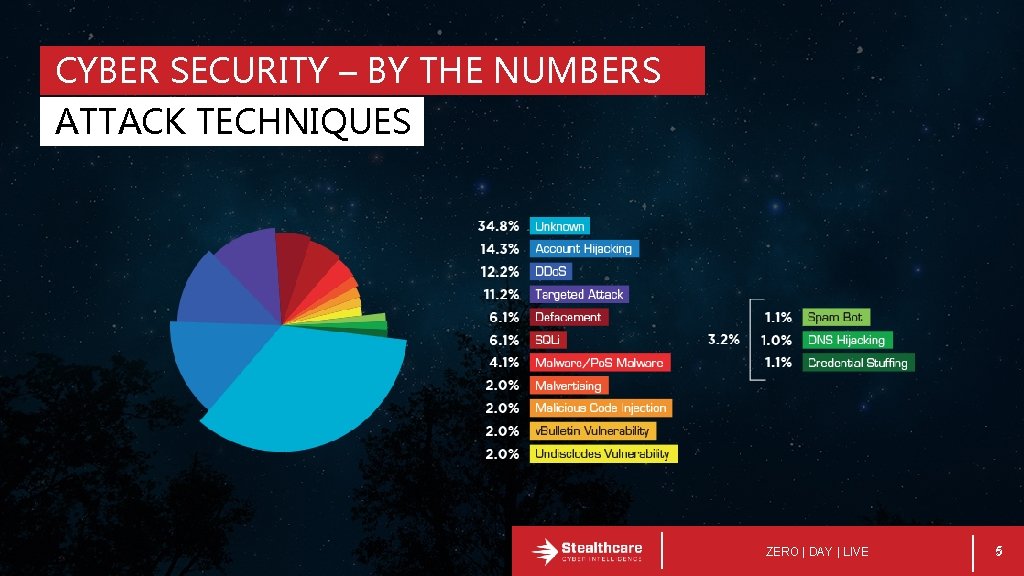
CYBER SECURITY – BY THE NUMBERS ATTACK TECHNIQUES ZERO | DAY | LIVE 5

THE DARK HACKING COMMUNITY EXPLAINED ZERO | DAY | LIVE 6

THE PROBLEM: • Over 80% say threats have doubled last year • 97% of security technology is signature based • Threats today are polymorphic • 98% of security technologies are reactive • 66% of SOCs falling behind in addressing threats ZERO | DAY | LIVE 7

THE PROBLEM: • Security spending is based on failure, rather than need. • The more secure that you feel, the less you spend. This is an inherently dangerous approach to cyber risk management. • Instead of looking to spend significantly more in their enterprise, Boards should be looking at greater efficiencies with their existing technologies (they exist). ZERO | DAY | LIVE 8

THE PROBLEM: • Staying ahead in today’s new, fast-evolving security environment calls for placing threat intelligence at the center of security. • Threat Intelligence will be the top enterprise security priority from 2017 through 2020. • Focusing on threat intelligence is one of the smartest ways to protect employees, along with critical IP and business data. ZERO | DAY | LIVE 9

THE PROBLEM: • Advanced behavior and sophisticated techniques used to evade conventional security products • As high as 46% of cyber attacks are unknown • 0 days are killing us • No one looking beyond the horizon where threats are born ZERO | DAY | LIVE 10

THE PROBLEM: • Companies do NOT know what Threat Intelligence is • Intelligence is generally used to learn about a particular threat and used to make a plan to defend against said threat. • Actionable Intelligence does not always equal preventative actions/measures. ZERO | DAY | LIVE 11

THE PROBLEM: • Companies do NOT know what Threat Intelligence is • SIEM does not EQUAL Threat Intelligence • Insider Threat is NOT Threat Intelligence • Saying ‘bad’ things on Social Media is NOT Threat Intelligence ZERO | DAY | LIVE 12

THE PROBLEM: • Too many EXTERNAL feeds • How do you choose what is relevant • Are you looking inside the organization for Intelligence? – What patterns do you see? – During the last incident, what did you learn? ZERO | DAY | LIVE 13

THE PROBLEM: • WHO owns Threat Intelligence? • Currently not a lot of dedicated teams – Growing trend of the numbers increasing • Threat Intelligence is NOT easy • Too much data can become overwhelming • Digesting Threat Intelligence in to environment can be PAINFUL! • Threat Intelligence expertise is slowly growing ZERO | DAY | LIVE 14

THE PROBLEM: • Security Practitioners are Educating our Foes • We all attend conferences, write opinions, appear on TV • You. Tube is a great source for bad actors to learn our capabilities • Security Hardware Companies freely distribute Data Sheets, Videos, How-To’s ZERO | DAY | LIVE 15

THE SOLUTION: • Close the gap between threat Prediction and Pro. Active Defense • The acquisition and analysis of information to identify, track, and predict cyber capabilities, intentions, and activities to offer course of action that enhance decision making ~Carnegie Melon Software Engineering Institute ZERO | DAY | LIVE 16

THE SOLUTION: • The DNA has to be in research • Identifying the real threat – the unknowns • Deliver productive intelligence on what matters • Contextual learning and cognitive computing • Correlation analysis, connecting the dots ZERO | DAY | LIVE 17

THE SOLUTION: • In depth analysis of unknown threats, 0 days, etc. • Differentiate the signal from the noise • Answer the “why” and “how” not just the “what” • Customized intelligence built around your Organization ZERO | DAY | LIVE 18
THE VALUE: • Deep analytical insight into cyber threats • Industry analysis on security and technology companies • Customized global threat dashboard • Direct access to Threat Analysts • Customized reports on threats, industry and trends • Visibility into Bad. IPs, Bad. URLs and Phishing sites ZERO | DAY | LIVE 19
THE VALUE: • Threat Intelligence can cut in half the time to detect a threat and improve an investigation by 42% • Increase readiness, Indicators of Compromise analysis, archived data, and Tools, Techniques, and Procedures • Better prepared for the future threat on the horizon • Threat Intelligence needs to do the heavy lifting; deliver important, productive intelligence ZERO | DAY | LIVE 20
Intelligence Categorized As Tactical, Raw and Finished • Depending on an organization’s operational maturity, determines at what stage they use this intelligence. • Tactical intelligence is defined as your indicators of compromise: bad IP’s, file hashes, domain names. Analysts must understand the context of this intelligence to put it into use within their organization. • Raw intelligence has been collected and processed but not analyzed. Usually collected via API’s or alerts are triggered on key words or phrases. Examples include: malware analysis, and compromised account data. • Finished intelligence is ready to be used and is raw intelligence put into context. Examples include: fraud intelligence, brand protection, threat actor data and third party risk information. ZERO | DAY | LIVE 21
Why Build a Threat Intelligence Practice Tactical: Enforce and improve the ability for your security team (NOC/SOC) and all IT personnel to anticipate, prevent and mitigate cyber attacks. Operational: Improve the ability for high levels across your organization (CISO, CIO, CTO, CEO) to transform the use of threat intelligence for both protection and response. Strategic: Improve the board’s decisions to allocate budget for solutions that integrate and operationalize threat intelligence. ZERO | DAY | LIVE 22

Use External Threat Intelligence To Understand Prevent Threats • The hardest patterns for threat actors to change are their TTP’s or Tactics, Techniques and Procedures – how they actually implement a threat. • How does TI help you prevent and detect threats? • Preempt attempts to defraud customers with impersonating domain registrations. • Track exploit kits to prioritize patching. • Detect breaches by monitoring dark net marketplaces for stolen data. ZERO | DAY | LIVE 23

THE BENEFIT OF THREAT INTELLIGENCE: • Increase Security Posture within your Organization • Timely and Prioritize threats to assign Risk • Create a Program with a Dedicated Team Intelligence is the ability to adapt to Change ~ Stephan Hawking ZERO | DAY | LIVE 24
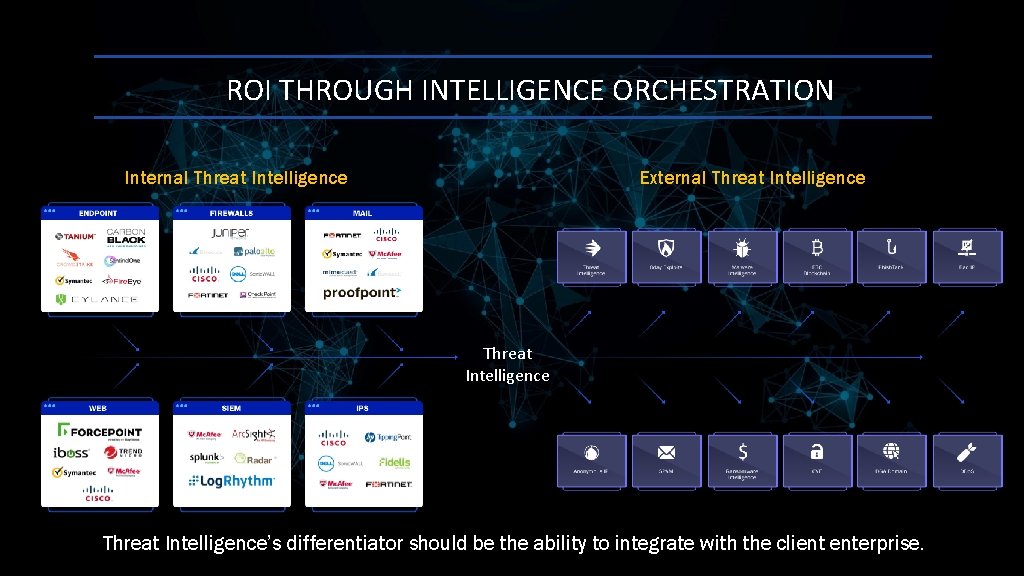
ROI THROUGH INTELLIGENCE ORCHESTRATION Internal Threat Intelligence External Threat Intelligence’s differentiator should be the ability to integrate with the client enterprise.

THE BENEFIT OF THREAT INTELLIGENCE: • Understand your Assets • Need to understand how threats will affect your organization • Understand your Controls and Capabilities • What does your firewall stop? • Endpoint Detection and Response? • Orchestration and Mitigation • Automation is the future ZERO | DAY | LIVE 26

THE SUMMARY: • Threat Intelligence will change the game in cybersecurity • A competitive differentiator in the market place • Invest in cyber resilience • Create a watchtower with productive intelligence and research that drives your business • Create a smarter workforce with a Threat Intelligence platform ZERO | DAY | LIVE 27

THE SUMMARY: Intelligence is like underwear, it is important that you have it but not necessary that you show it off! ZERO | DAY | LIVE 28

THANK YOU jeremy@stealthcare. com jason@stealthcare. com Stealthcare. com 440. 477. 1144 216. 849. 1192
- Slides: 29