Using CLIPS to Detect Network Intrusions CLIPNIDS Phase











- Slides: 19

Using CLIPS to Detect Network Intrusions (CLIPNIDS) Phase I MSE Project Sripriya Marry Committee Members Dr. David Gustafson (Major Professor) Dr. Rodney Howell Dr. Mitchell Nielsen

Overview § Problem Statement § Purpose and Motivation § Background § Project phases § Project Requirements § User Interface § Cost Estimation § Effort Distribution

Problem Statement Objective To update Clipnids with the signatures of latest network attacks so as to detect and notify network administrators about any unauthorized access to the network resources by intruders

Purpose and Motivation § To excel in the Linux, C and GNU Programming. § Inspired by SNORT.

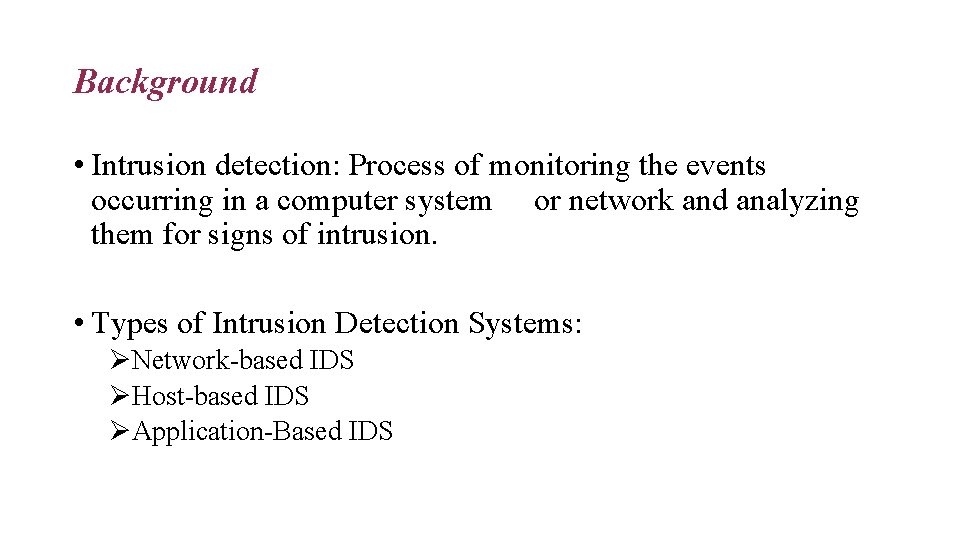
Background • Intrusion detection: Process of monitoring the events occurring in a computer system or network and analyzing them for signs of intrusion. • Types of Intrusion Detection Systems: ØNetwork-based IDS ØHost-based IDS ØApplication-Based IDS

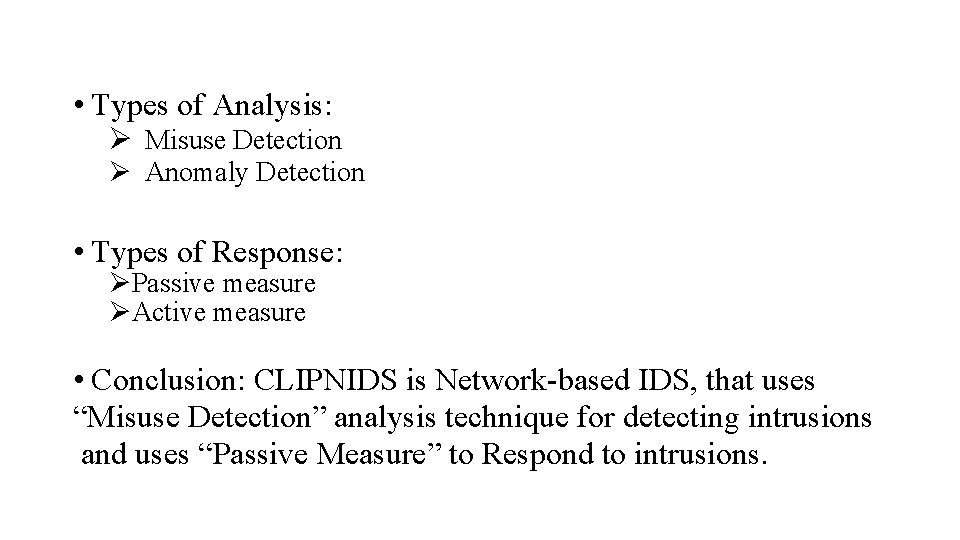
• Types of Analysis: Ø Misuse Detection Ø Anomaly Detection • Types of Response: ØPassive measure ØActive measure • Conclusion: CLIPNIDS is Network-based IDS, that uses “Misuse Detection” analysis technique for detecting intrusions and uses “Passive Measure” to Respond to intrusions.

Project phases § Inception Phase. § Elaboration Phase. • Production Phase

Inception Phase § Vision Document 1. 0 § Project Plan 1. 0 § Software Quality Assurance Plan § Prototype

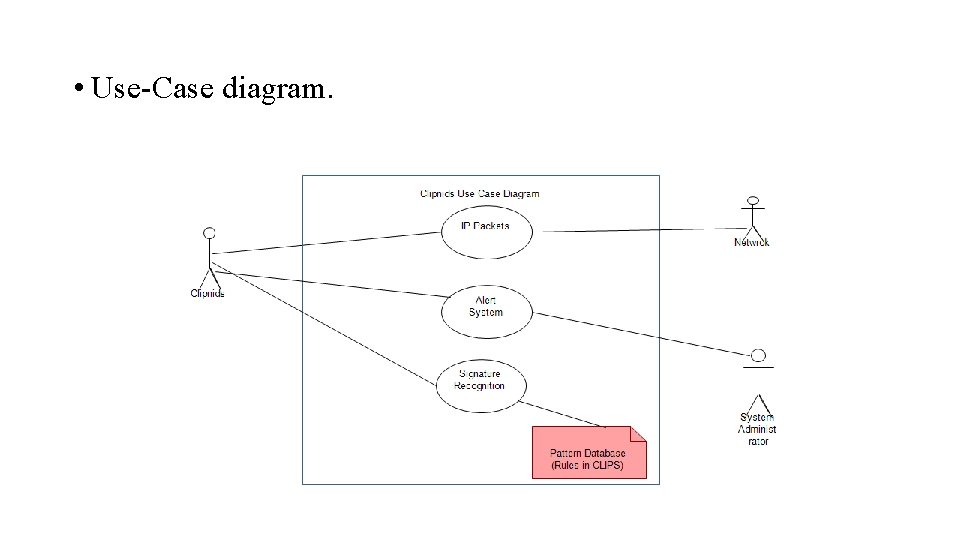
Project Requirements • Actors identified for Clipnids. • Use-Case diagram. • Tasks required to achieve the objective of the project.

• Actors identified for Clipnids. Ø Network Ø Clipnids Ø System Administrator

• Use-Case diagram.

• Tasks required to achieve the objective of the project. ØStrong knowledge of Linux, C, GNU Programming and Bash scripting language. ØStrong knowledge of GDB tool for debugging. ØMigration of source code of CLIPNIDS from PCAP to DAQ to capture packets.

ØIntegrating of latest versions of decoders and pre-processors from SNORT into CLIPNIDS § Identifying the version of SNORT using which CLIPNIDS decoder and pre -processors were built. § Possessing the latest version of SNORT. § Good understanding of working of expert-system CLIPS. § Good understanding of working of CLIPNIDS and its architecture. § Good understanding of working of SNORT and its architecture.

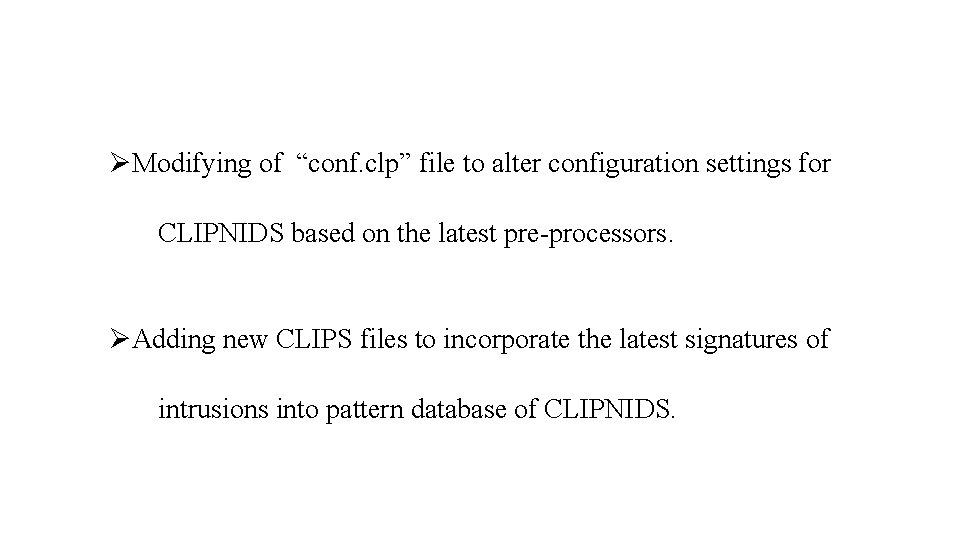
ØModifying of “conf. clp” file to alter configuration settings for CLIPNIDS based on the latest pre-processors. ØAdding new CLIPS files to incorporate the latest signatures of intrusions into pattern database of CLIPNIDS.

User Interface


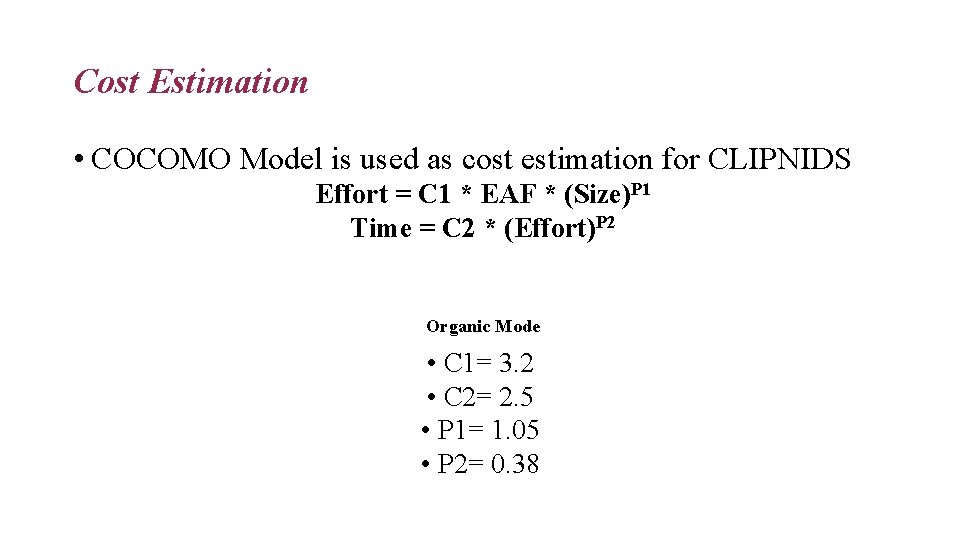
Cost Estimation • COCOMO Model is used as cost estimation for CLIPNIDS Effort = C 1 * EAF * (Size)P 1 Time = C 2 * (Effort)P 2 Organic Mode • C 1= 3. 2 • C 2= 2. 5 • P 1= 1. 05 • P 2= 0. 38

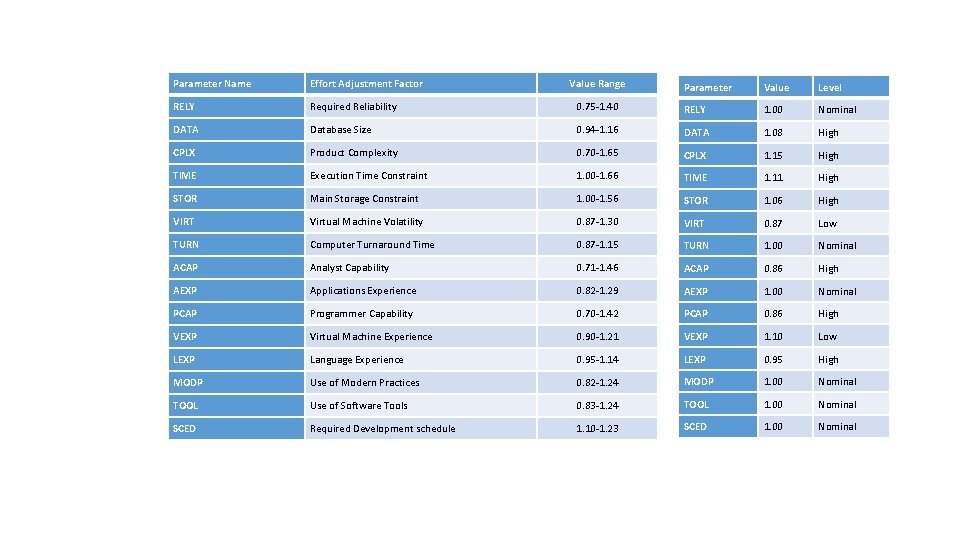
Parameter Name Effort Adjustment Factor RELY Required Reliability DATA Value Range Parameter Value Level 0. 75 -1. 40 RELY 1. 00 Nominal Database Size 0. 94 -1. 16 DATA 1. 08 High CPLX Product Complexity 0. 70 -1. 65 CPLX 1. 15 High TIME Execution Time Constraint 1. 00 -1. 66 TIME 1. 11 High STOR Main Storage Constraint 1. 00 -1. 56 STOR 1. 06 High VIRT Virtual Machine Volatility 0. 87 -1. 30 VIRT 0. 87 Low TURN Computer Turnaround Time 0. 87 -1. 15 TURN 1. 00 Nominal ACAP Analyst Capability 0. 71 -1. 46 ACAP 0. 86 High AEXP Applications Experience 0. 82 -1. 29 AEXP 1. 00 Nominal PCAP Programmer Capability 0. 70 -1. 42 PCAP 0. 86 High VEXP Virtual Machine Experience 0. 90 -1. 21 VEXP 1. 10 Low LEXP Language Experience 0. 95 -1. 14 LEXP 0. 95 High MODP Use of Modern Practices 0. 82 -1. 24 MODP 1. 00 Nominal TOOL Use of Software Tools 0. 83 -1. 24 TOOL 1. 00 Nominal SCED Required Development schedule 1. 10 -1. 23 SCED 1. 00 Nominal

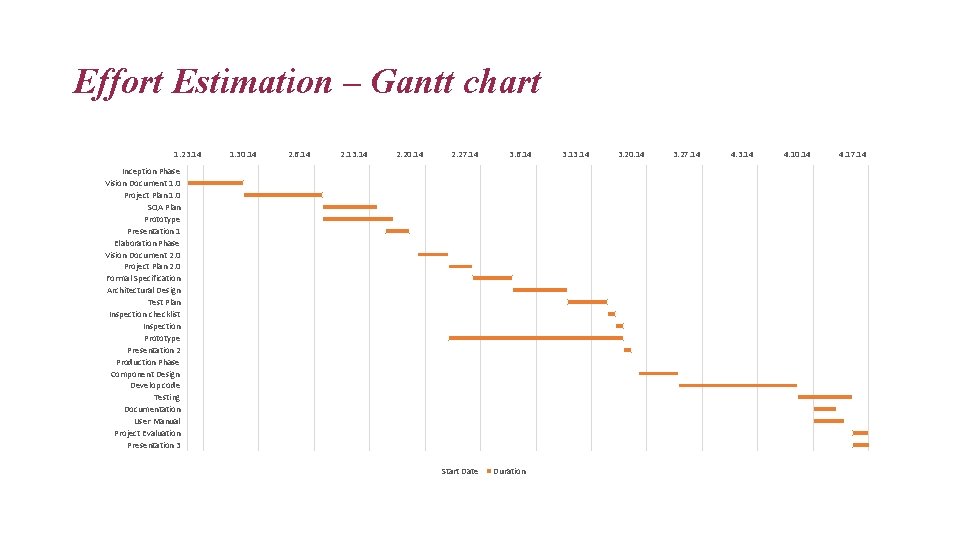
Effort Estimation – Gantt chart 1. 23. 14 1. 30. 14 2. 6. 14 2. 13. 14 2. 20. 14 2. 27. 14 3. 6. 14 Inception Phase Vision Document 1. 0 Project Plan 1. 0 SQA Plan Prototype Presentation 1 Elaboration Phase Vision Document 2. 0 Project Plan 2. 0 Formal Specification Architectural Design Test Plan Inspection checklist Inspection Prototype Presentation 2 Production Phase Component Design Develop code Testing Documentation User Manual Project Evaluation Presentation 3 Start Date Duration 3. 14 3. 20. 14 3. 27. 14 4. 3. 14 4. 10. 14 4. 17. 14