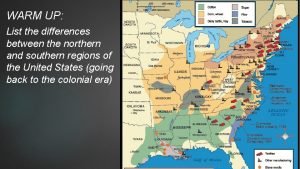
United States Air Force Integrity Service Excellence The

















- Slides: 30

United States Air Force Integrity - Service - Excellence The Vocabulary Driven Value Chain Do. D Co. I Forum July 31, 2007

Agenda n Introduction: n n Our Current State n n n How we are sharing now Current Challenges Our Future State n n The Vocabulary of this briefing Why Are We sharing? What We Need To Succeed Target Capability The Vocabulary-Driven Triple Threat Where do Co. Is fit in? Getting There: n n n What Is the Vocabulary Driven Value Chain? What is the Co. Is’ role? What is the EVT’s role? Six Major Milestones Keys To Success Integrity - Service - Excellence 2

The Vocabulary of This Briefing n Semantic: n Context: The meaning of some “symbol”. Semantics relate symbols (e. g. terms) to the concepts that they represent n Example: What does the term tank mean? Terms surrounding a term or passage that clarify its meaning n Example: gas tank vs. armored tank n Ontology: n Service Oriented Architecture (SOA): An information map that specifies the contextual semantics of information technology that enables information exchange without reengineering legacy systems Integrity - Service - Excellence 3

Why Are We Sharing? n Air Force Information Strategy, SECAF & CSAF, August 2002 n n Do. D Net-Centric Data Strategy Memorandum, ASD/NII, May 2003 n n https: //afkm. wpafb. af. mil/ASPs/Doc. Man/DOCDisplay. asp? Filter=OO-EA-AFSP&Doc. ID=285404 Air Force Information and Data Management Strategy Policy, SECAF & CSAF, 3 March 2004 n n https: //afkm. wpafb. af. mil/ASPs/Doc. Man/DOCDisplay. asp? Filter=OO-AQ-IDEW&Doc. ID=29679 https: //afkm. wpafb. af. mil/ASPs/Doc. Man/DOCDisplay. asp? Filter=OO-SC-AF 04&Doc. ID=115325 Do. D Directive 8320. 2, Data Sharing in a Net-Centric Environment, 2 December 2004 n https: //afkm. wpafb. af. mil/ASPs/Doc. Man/DOCDisplay. asp? Filter=OO-SC-AN 11&Doc. ID=229248 It is “NOT” just about data sharing, this is only the means to an end… It “IS” about providing FIRST TO ACTION CAPABILITY n Transforming enterprise data into ACTIONABLE INFORMATION n Being the first to action depends on being FIRST TO KNOW Integrity - Service - Excellence 4

What We Need to Succeed “What we don’t know can hurt us, but what we think we know, but don’t can be fatal to an organization” -Data quality expert, Larry English What will it take to achieve first to “know” capability? n “Share” what we know: Information that is… n n n “Understand” what we share: Information that is… n n n relevant accessible easy to find available on demand delivered in a usable form delivered in context expressed in a known “vocabulary” organized for mission support “Trust” what we understand: Information that is… n n current complete authoritative reliable Integrity - Service - Excellence 5

Agenda n Introduction: n n Our Current State n n n How we are sharing now Current Challenges Our Future State n n The Vocabulary of this briefing Why Are We sharing? What We Need To Succeed Target Capability The Vocabulary-Driven Triple Threat Where do Co. Is fit in? Getting There: n n n What Is the Vocabulary Driven Value Chain? What is the Co. Is’ role? What is the EVT’s role? Six Major Milestones Keys To Success Integrity - Service - Excellence 6

How are we sharing now? n Point to point sharing n n Centralize everything n n Not scalable, unnecessary rework, not authoritative costly, time consuming, brittle, does not accommodate change Standard data exchange models n Limited sharing value, imposes a common structure, inflexible, does not accommodate change Integrity - Service - Excellence 7

Current Challenges n “Share” what we know n n n Relevant: fragmented, redundant, buried in irrelevant information Accessible: scattered among disconnected systems with different access rules Findable: must know in advance which pieces of information are in which systems Available: information that we are authorized to use is trapped in systems that we don’t know about or can not access. “Understand” what we share n Usable: must evaluate, filter, and restructure information before we can use it. n Delivered in context: Must guess about the semantics because there is no way to preserve intended context. n Known “vocabulary”: Must learn the vocabulary of every system that we use and how to translate between vocabularies n Organized for mission support: Reconfiguring information for a different context requires building new or modifying existing systems. n “Trust” what we understand n Current: don’t know if there is more current information available elsewhere n Complete: don’t know if there are pieces of information missing n Authoritative: don’t know the authoritative source of the information, e. g. who created, modified or reused it. Integrity - Service - Excellence 8

Agenda n Introduction: n n Our Current State n n n The Vocabulary of this briefing Why Are We sharing? What We Need To Succeed How we are sharing now Current Challenges Our Future State n n Target Capability The Vocabulary-Driven Triple Threat n n Ontologies Governance SOA Getting There: n n n What Is the Vocabulary Driven Value Chain? What is the Co. Is’ role? What is the EVT’s role? Six Major Milestones Keys To Success Integrity - Service - Excellence 9

Target Capability n “Share” what we know n Relevant: direct users to a single source of authoritative information n Accessible: authorized users, must have a central point of access for authoritative information n Findable: locating the information that we need with no system specific knowledge n Available: information must be available on-demand, enterprise wide to authorized applications and users regardless of where the “pieces” are stored n “Understand” what we share n Usable: deliver in a form that enables users to concentrate on making use of, rather than making sense of information n Delivered in context: the intended context information must be preserved for the entire information life cycle. n Known “vocabulary”: Must be able to retrieve information using known vocabulary, regardless of the vocabulary of the source systems. n Organized for mission support: semantics must be abstracted from source systems so that information can be repurposed without requiring manual reconfiguration or source system modification. n “Trust” what we understand n Current: ensure currency by directing the user to a single authoritative source. n Complete: What we need to know can be quickly packaged from modular pieces of information. n Authoritative: Authority of information is predefined by the Co. I and its history is traceable. Integrity - Service - Excellence 10

The Vocabulary Driven Triple Threat Making information actionable, is more about business processes and governance than technology n Vocabularies n organized to support AF business processes n provide the semantics for building ontologies n Governance and Support n Transparency Integrated Product Team (TIPT): ensures consistent implementation of AF Net-Centric Compliance n Sub-IPTS: TIPT subteams organized by functional area n Co. I Coordination Panel: Manages Co. I activities n EVT provides technical support to Co. I Coordination Panel and its Co. Is n Service Oriented Enterprise Migration n n Loose coupling Lower Cost Less Rework Rapid Development cycles Optimizes reuse Integrity - Service - Excellence 11

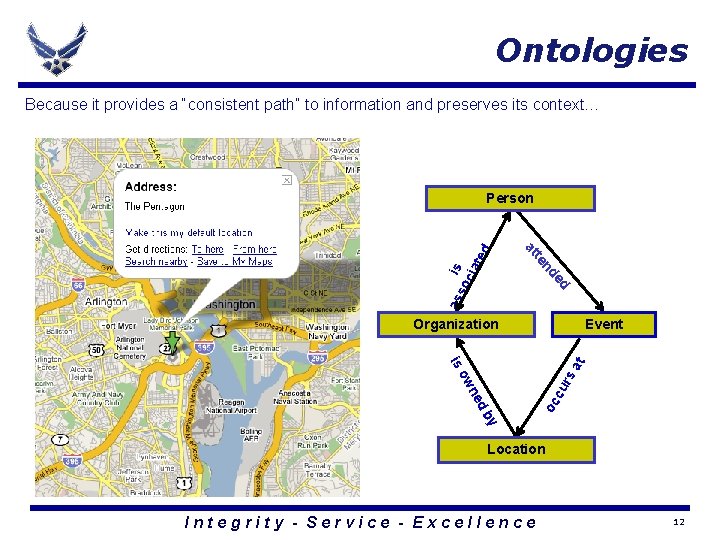
Ontologies Because it provides a “consistent path” to information and preserves its context… so is cia t as ed nd te at ed Person Organization Event oc c y db e wn ur s at o is Location Integrity - Service - Excellence 12

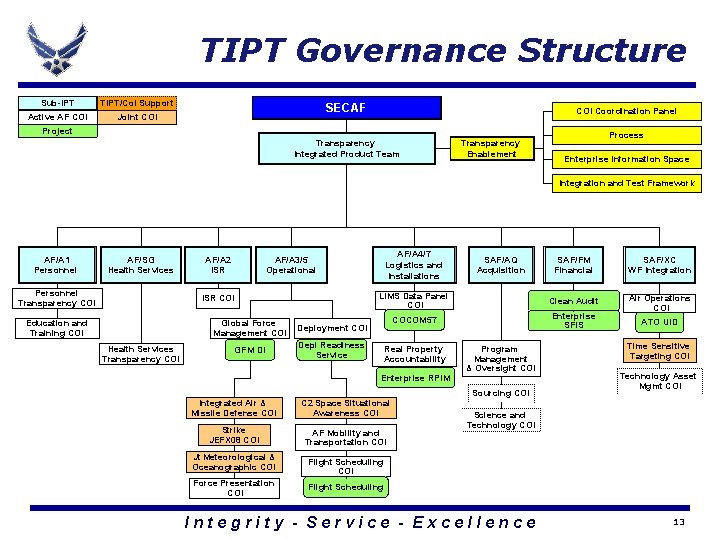
TIPT Governance Structure Sub-IPT TIPT/Co. I Support Active AF COI Joint COI SECAF COI Coordination Panel Project Transparency Integrated Product Team Transparency Enablement Process Enterprise Information Space Integration and Test Framework AF/A 1 Personnel AF/SG Health Services Personnel Transparency COI AF/A 2 ISR COI Education and Training COI Health Services Transparency COI AF/A 4/7 Logistics and Installations AF/A 3/5 Operational Global Force Management COI Deployment COI GFM DI Depl Readiness Service SAF/FM Financial SAF/XC WF Integration LIMS Data Panel COI Clean Audit COCOM 57 Enterprise SFIS Air Operations COI Real Property Accountability Enterprise RPIM Integrated Air & Missile Defense COI C 2 Space Situational Awareness COI Strike JEFX 08 COI AF Mobility and Transportation COI Jt Meteorological & Oceanographic COI Force Presentation COI SAF/AQ Acquisition Program Management & Oversight COI Sourcing COI ATO UID Time Sensitive Targeting COI Technology Asset Mgmt COI Science and Technology COI Flight Scheduling Integrity - Service - Excellence 13

SOA Rapid delivery of capability due to re-use of existing n “Services” n “Standard Interfaces” n “ Co. I Vocabularies” n Cost to deploy and sustain capability slashed n Short development cycles and re-use n Standard interfaces mitigates need to continually rewrite interfaces to associated systems (80% of software sustainment) n Delivers information now! n Desktop access to all exposed data in the format required n Negates the requirement to build large client server systems or huge data storage warehouses n Integrity - Service - Excellence 14

Agenda n Introduction: n n Our Current State n n n The Vocabulary of this briefing Why Are We sharing? What We Need To Succeed How we are sharing now Current Challenges Our Future State n n Target Capability The Vocabulary-Driven Triple Threat n n Ontologies Governance SOA Getting There: n n n What Is the Vocabulary Driven Value Chain? What is the Co. Is’ role? What is the EVT’s role? Six Major Milestones Keys To Success Integrity - Service - Excellence 15

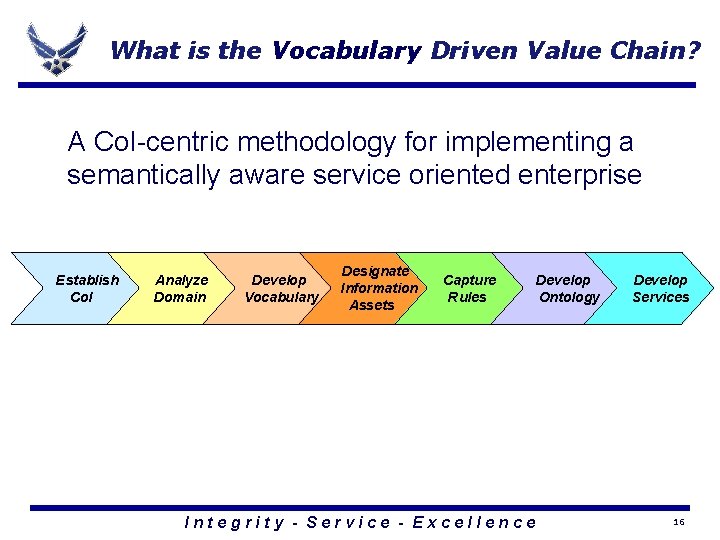
What is the Vocabulary Driven Value Chain? A Co. I-centric methodology for implementing a semantically aware service oriented enterprise Establish Co. I Analyze Domain Develop Vocabulary Designate Information Assets Capture Rules Integrity - Service - Excellence Develop Ontology Develop Services 16

What Is the Co. I’s Role? Primary role is to manage the “value chain” for your mission area n n n Serve as subject matter experts throughout the process Develop a vocabulary that represents your subject area (AKA Standard information structure (SIS)) Identify single source for authoritative pieces of information (AKA information assets) and their source systems. Ensure that the SOA implementation supports business processes and semantics Collaborate with other Co. Is to promote cross Co. I vocabulary sharing and reuse Integrity - Service - Excellence 17

What is the EVT’s Role? AF Enterprise Vocabulary Team n Mission: To provide guidance and support for AF Co. I goals and the vocabulary development process n Provide expertise on managing the “value chain” n Training n Vocabulary Development n Time and task management n SAF/XC – Co. I Liaison Integrity - Service - Excellence 18

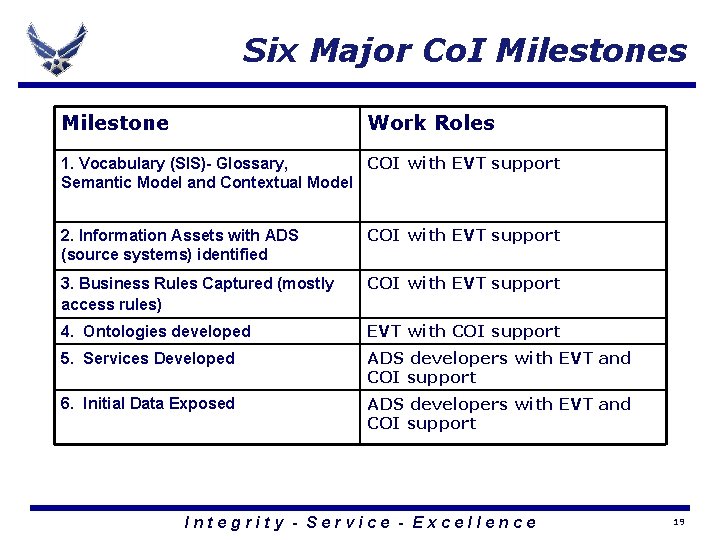
Six Major Co. I Milestones Milestone Work Roles 1. Vocabulary (SIS)- Glossary, COI with EVT support Semantic Model and Contextual Model 2. Information Assets with ADS (source systems) identified COI with EVT support 3. Business Rules Captured (mostly access rules) COI with EVT support 4. Ontologies developed EVT with COI support 5. Services Developed ADS developers with EVT and COI support 6. Initial Data Exposed ADS developers with EVT and COI support Integrity - Service - Excellence 19

Keys to Success n Data Discipline TIPT for governance n COIs for execution n n Process Discipline Policy Directives, AFIs, TTPs, etc. n AFOS 21: continuous process improvement and new technology exploitation n n IT Discipline and Mission Assurance Centralized management of federated environment n Applied at all levels – from the communications pipes through the delivery of information n Integrity - Service - Excellence 20

Questions? Contact Information: Mary Parmelee AF EVT Team Lead MITRE supporting Warfighting Integration and CIO (SAF/XC) 1101 Wilson Boulevard, Suite 1020 Arlington, Virginia 22209 mary. parmelee. ctr@pentagon. af. mil Mobile: 571 -334 -5935 Learn More: n AF Information & Data Management Strategy - Implementation Co. P: https: //wwwd. my. af. mil/afknprod/ASPs/Co. P/Open. Co. P. asp? Filter=OO-SC-AF-DM Integrity - Service - Excellence 21

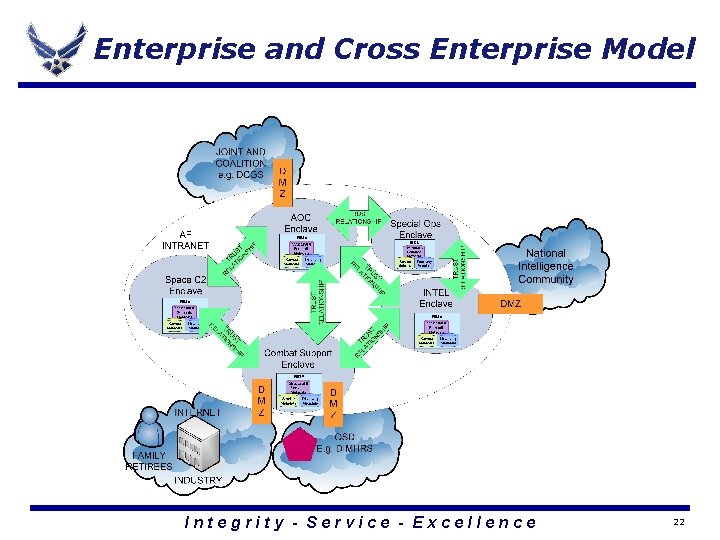
Enterprise and Cross Enterprise Model Integrity - Service - Excellence 22

Back Up Slides Integrity - Service - Excellence 23

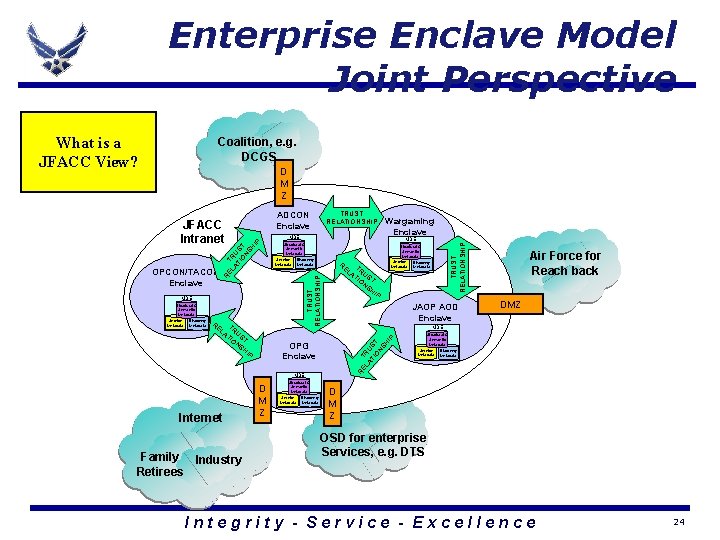
Enterprise Enclave Model Joint Perspective What is a JFACC View? Coalition, e. g. DCGS D M Z T LA RU TI ST ON SH IP JAOP AOD Enclave OPG Enclave IP MDE Internet Family Industry Retirees D M Z Structural & Semantic Metadata Service Discovery Metadata Air Force for Reach back DMZ MDE RE T LA RU TI S O T NS HI P RE Structural & Semantic Metadata Service Discovery Metadata RE TRUST RELATIONSHIP MDE Structural & Semantic Metadata Service Discovery Metadata RE LA TRU TI S O T NS HI P MDE Wargaming Enclave TRUST RELATIONSHIP JFACC Intranet OPCON/TACON Enclave TRUST RELATIONSHIP ADCON Enclave Structural & Semantic Metadata Service Discovery Metadata D M Z OSD for enterprise Services, e. g. DTS Integrity - Service - Excellence 24

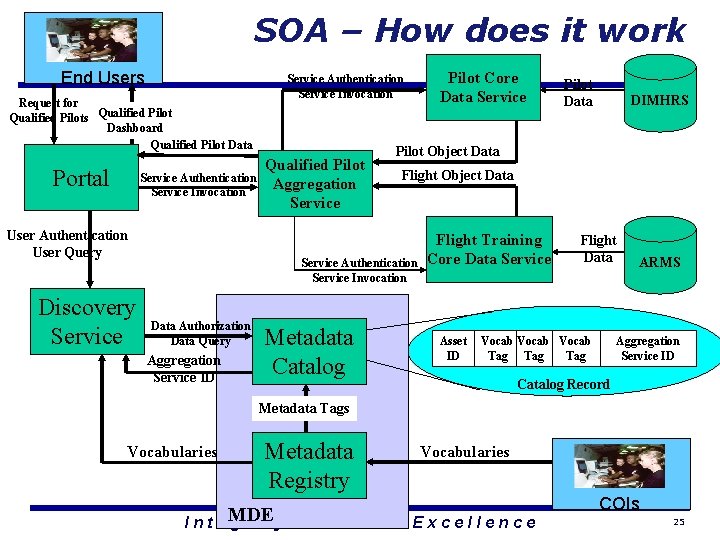
SOA – How does it work End Users Service Authentication Service Invocation Request for Qualified Pilots Qualified Pilot Dashboard Qualified Pilot Data Portal Service Authentication Service Invocation Qualified Pilot Aggregation Service User Authentication User Query Discovery Service Aggregation Service ID Metadata Catalog Pilot Data DIMHRS Pilot Object Data Flight Object Data Service Authentication Service Invocation Data Authorization Data Query Pilot Core Data Service Flight Training Core Data Service Asset ID Flight Data Vocab Tag Tag ARMS Aggregation Service ID Catalog Record Metadata Tags Vocabularies Metadata Registry I n t e MDE grity Vocabularies - Service - Excellence COIs 25

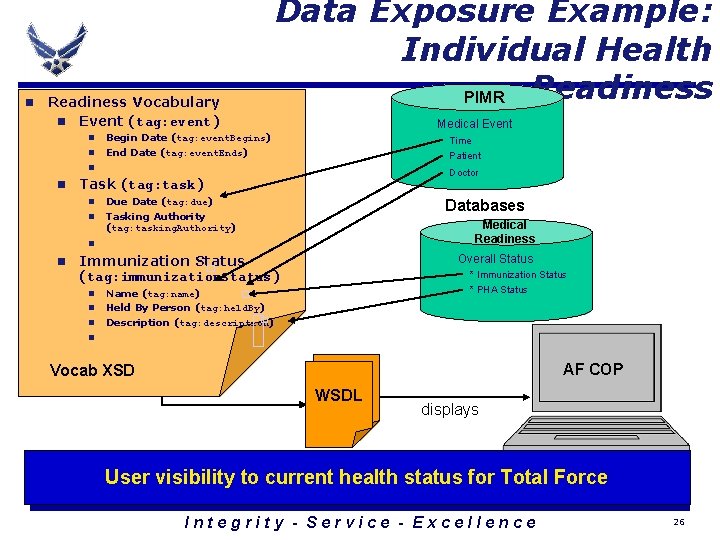
n Readiness Vocabulary n Event (tag: event) n n Data Exposure Example: Individual Health Readiness PIMR Medical Event Begin Date (tag: event. Begins) End Date (tag: event. Ends) Time Patient n n Doctor Task (tag: task) n Due Date (tag: due) n Tasking Authority (tag: tasking. Authority) Databases Medical Readiness n n Overall Status Immunization Status (tag: immunization. Status) n n n * Immunization Status * PHA Status Name (tag: name) Held By Person (tag: held. By) Description (tag: description) n Vocab XSD AF COP WSDL displays User visibility to current health status for Total Force Integrity - Service - Excellence 26

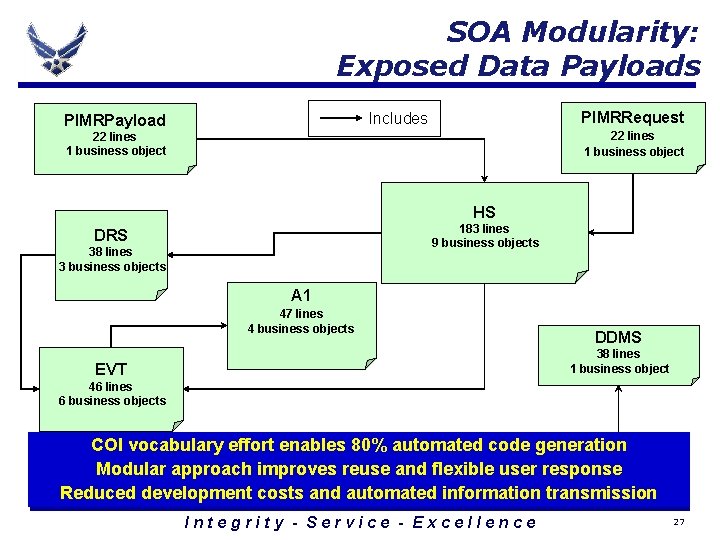
SOA Modularity: Exposed Data Payloads PIMRRequest Includes PIMRPayload 22 lines 1 business object HS 183 lines 9 business objects DRS 38 lines 3 business objects A 1 47 lines 4 business objects DDMS 38 lines 1 business object EVT 46 lines 6 business objects COI vocabulary effort enables 80% automated code generation Modular approach improves reuse and flexible user response Reduced development costs and automated information transmission Integrity - Service - Excellence 27

Barriers to SOA Implementation n Acquisition Force Transformation Shift our technical development paradigm from systems to SOA n Educate our SPOs/PMOs on the process n Acquire SOA skills from small, agile contractors n n Agile Service Delivery Big Ugly – Re-engineer AF Acquisition Processes n Dynamic Testing – Re-engineer AF Testing Processes n n Initial Investment Subject Matter Experts for upfront vocabulary work n Support to functionals to expose their data Integrity - Service - Excellence n 28

AF COI Coordination Panel Activities n Alignment/Enterprise CM of COI vocabularies n Vocabulary Training for COIs n Coordination with DOD, Joint, Service COI activities n Guidance on COI activities n Technical Support – Enterprise Vocabulary Team (EVT) n Core Team n Road Team Integrity - Service - Excellence n Expanding to charter C 2 Data 29

Key SOA Principles n n n Communities of Interest (COIs) n Identify and define information to expose n Select Authoritative Data Sources (ADS) ADS Owner n Resource and implement services to expose data Limited and controlled implementation of data warehouses, data marts, and persistent data stores Limited build of new systems and applications n Reuse of services from across AF and DOD enterprises No new point to point interfaces shall be built Scalability will be achieved through the creation of capability-based enclaves Integrity - Service - Excellence 30
 Integrity service excellence
Integrity service excellence Integrity service excellence
Integrity service excellence Integrity service excellence
Integrity service excellence Mhu-141 munitions trailer
Mhu-141 munitions trailer Air force integrity
Air force integrity Afi36-807
Afi36-807 Respect integrity communication and excellence
Respect integrity communication and excellence Ethics and integrity at the united nations
Ethics and integrity at the united nations Pt tanah air sentosa
Pt tanah air sentosa Enterprise it as a service air force
Enterprise it as a service air force Another name for customer
Another name for customer Four pillars of service excellence
Four pillars of service excellence Was the united states on the axis powers or allied powers?
Was the united states on the axis powers or allied powers? Unit 2: the united states and canada worksheet answers
Unit 2: the united states and canada worksheet answers 36 30 line
36 30 line Usa pro soccer
Usa pro soccer Marshall case
Marshall case United states student association
United states student association The united states ought to provide a universal basic income
The united states ought to provide a universal basic income Us constitution preamble
Us constitution preamble The united states in the caribbean 1776 to 1985
The united states in the caribbean 1776 to 1985 Southeast region physical features
Southeast region physical features Expansion of the united states of america 1607 to 1853 map
Expansion of the united states of america 1607 to 1853 map Why did truman believe greece needed aid
Why did truman believe greece needed aid Previous owner of louisiana purchase
Previous owner of louisiana purchase Awake united states author
Awake united states author Heart of atlanta motel v. united states
Heart of atlanta motel v. united states We have pacified some thousands of the islanders
We have pacified some thousands of the islanders Chapter 6 lesson 2
Chapter 6 lesson 2 Midwestern region of the united states
Midwestern region of the united states 7 regions of the united states
7 regions of the united states