T110 5140 Network Application Frameworks and XML Routing


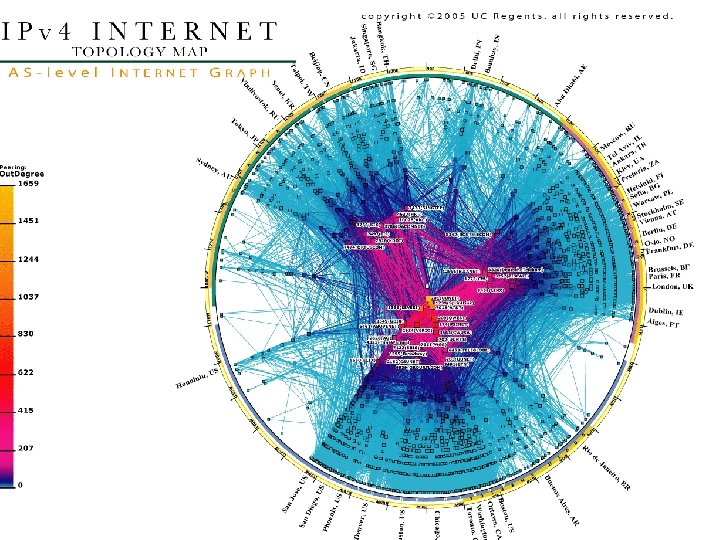
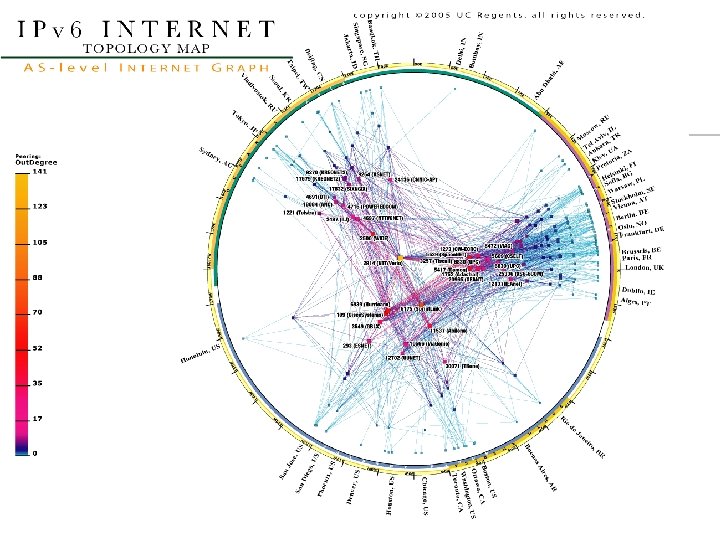
- Slides: 44

T-110. 5140 Network Application Frameworks and XML Routing and mobility 12. 2. 2008 Sasu Tarkoma Based on slides by Pekka Nikander

Contents n n Background IP routing and scalability Mobility Multi-layer mobility

Background n n What is network architecture? Layered architecture The original requirements for IP Later requirements for IP

Network architecture n A set of principles and basic mechanisms that guide network engineering u u Physical links Communication protocols F F F n Format of messages The way in messages are exchanged Protocol stack Where is the state?

Protocol Stack n Layers are part of a network architecture u u n Multiple layers are needed in order to reduce complexity u u u n Provide services for layers above Hiding the complexity of the current layer Separation of network functions distribution of complexity OSI, TCP/IP Protocols are building blocks of a network design u Can exist independently of layering

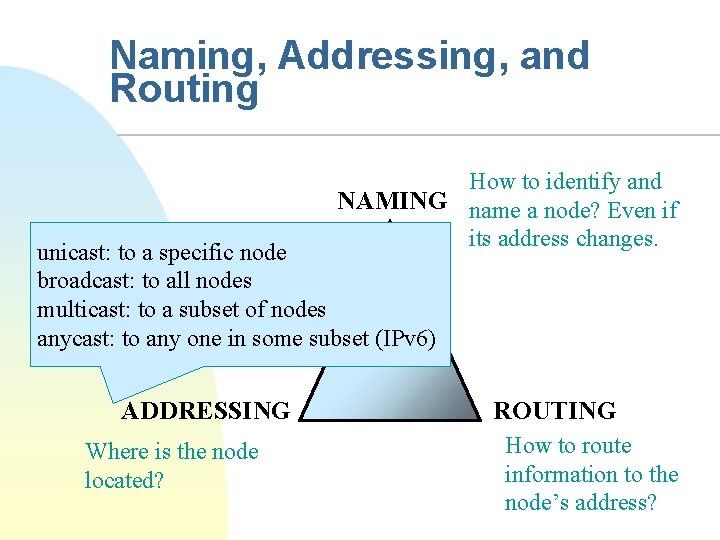
Naming, Addressing, and Routing How to identify and NAMING name a node? Even if its address changes. unicast: to a specific node broadcast: to all nodes multicast: to a subset of nodes anycast: to any one in some subset (IPv 6) ADDRESSING Where is the node located? ROUTING How to route information to the node’s address?

TCP/IP Network Stack Application Layer Transport Layer (TCP/UDP) Networking Layer (IP) Underlying network (link layer, physical)

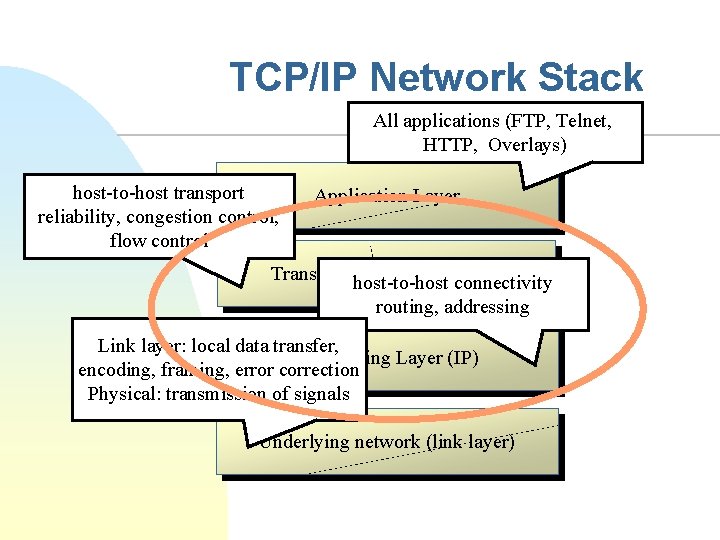
TCP/IP Network Stack All applications (FTP, Telnet, HTTP, Overlays) host-to-host transport reliability, congestion control, flow control Application Layer Transport host-to-host Layer (TCP/UDP) connectivity routing, addressing Link layer: local data transfer, Networking Layer (IP) encoding, framing, error correction Physical: transmission of signals Underlying network (link layer)

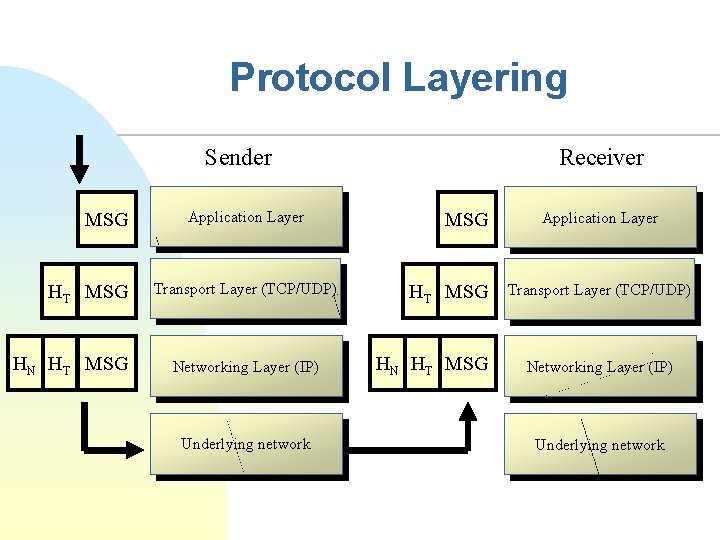
Protocol Layering Sender MSG HT MSG HN HT MSG Application Layer Transport Layer (TCP/UDP) Networking Layer (IP) Underlying network Receiver MSG HT MSG HN HT MSG Application Layer Transport Layer (TCP/UDP) Networking Layer (IP) Underlying network

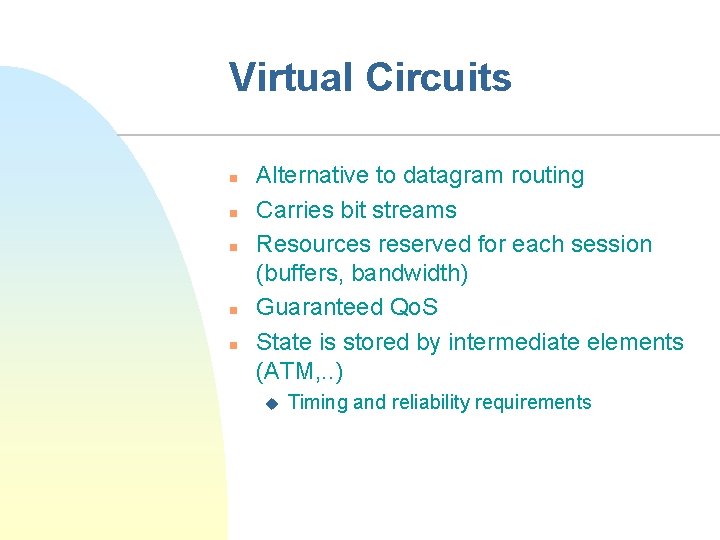
Virtual Circuits n n n Alternative to datagram routing Carries bit streams Resources reserved for each session (buffers, bandwidth) Guaranteed Qo. S State is stored by intermediate elements (ATM, . . ) u Timing and reliability requirements

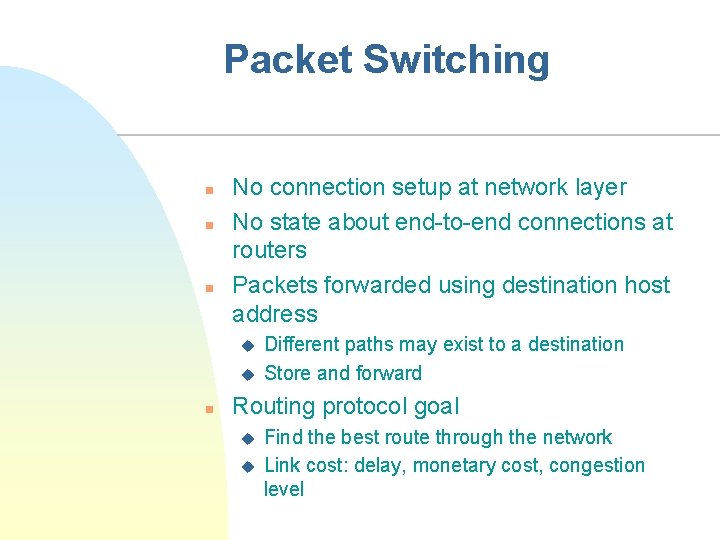
Packet Switching n n n No connection setup at network layer No state about end-to-end connections at routers Packets forwarded using destination host address u u n Different paths may exist to a destination Store and forward Routing protocol goal u u Find the best route through the network Link cost: delay, monetary cost, congestion level

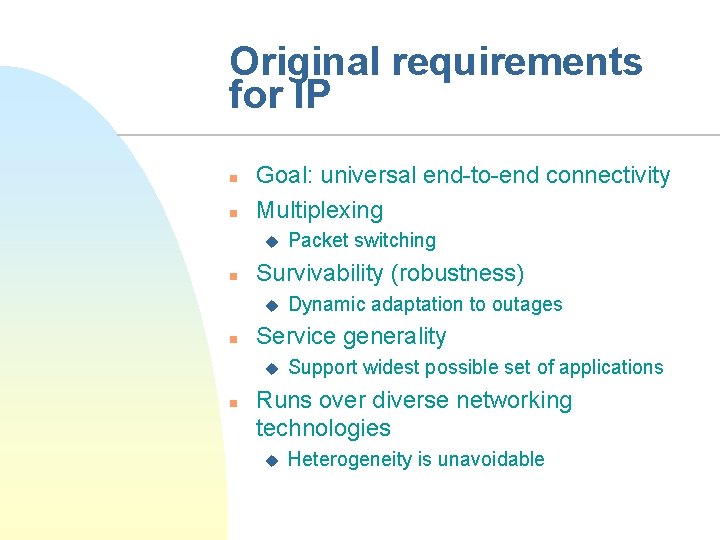
Original requirements for IP n n Goal: universal end-to-end connectivity Multiplexing u n Survivability (robustness) u n Dynamic adaptation to outages Service generality u n Packet switching Support widest possible set of applications Runs over diverse networking technologies u Heterogeneity is unavoidable

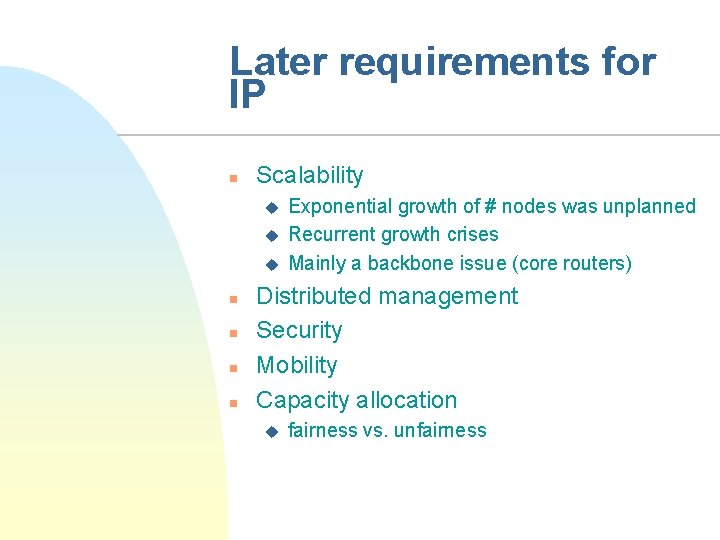
Later requirements for IP n Scalability u u u n n Exponential growth of # nodes was unplanned Recurrent growth crises Mainly a backbone issue (core routers) Distributed management Security Mobility Capacity allocation u fairness vs. unfairness

What has changed? n Permanent IP address u n End-to-end communication u n NAT, firewalls Trusted end hosts u n Middleboxes, proxies, NATs, . . Globally and uniquely routable u n Time-varying: DHCP, NAT, mobility Hackers, spammers, … Four layers u Layer splits, cross-layer interactions

Problems with four layers n Layer violations u n Middleboxes, NATs Relation to OSI 7 layers u What about presentation layer for Internet? F u XML What about session layer? F F Separate session management from data delivery For example: SIP

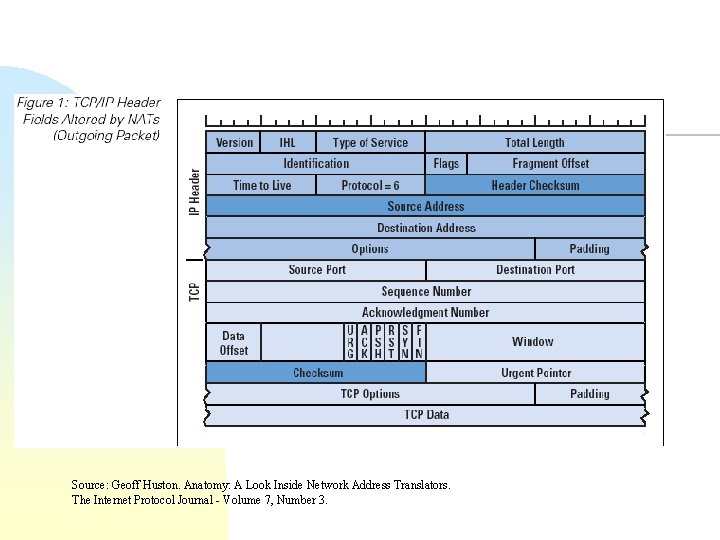
Source: Geoff Huston. Anatomy: A Look Inside Network Address Translators. The Internet Protocol Journal - Volume 7, Number 3.

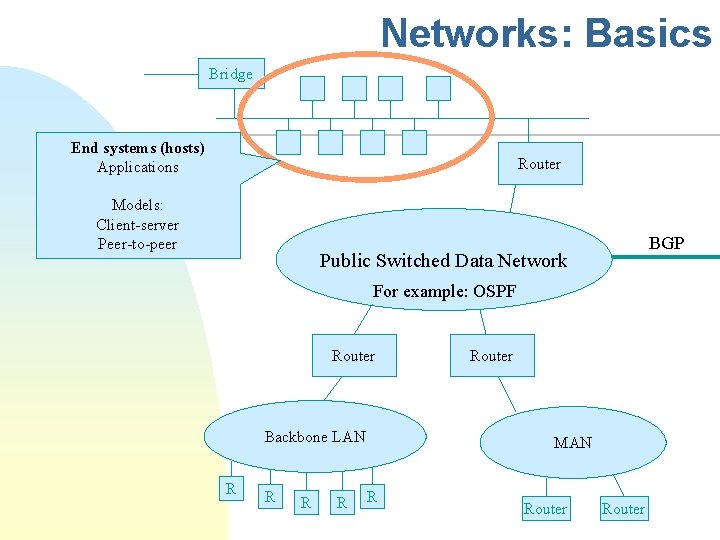
Networks: Basics Bridge End systems (hosts) Applications Router Models: Client-server Peer-to-peer BGP Public Switched Data Network For example: OSPF Router Backbone LAN R R Router MAN R Router

Networks: Wireless MH AP NAT GPRS/UMTS Access network BS MH NAT Public Switched Data Network Router BS Ad hoc MH Backbone LAN R R Router MAN R Router

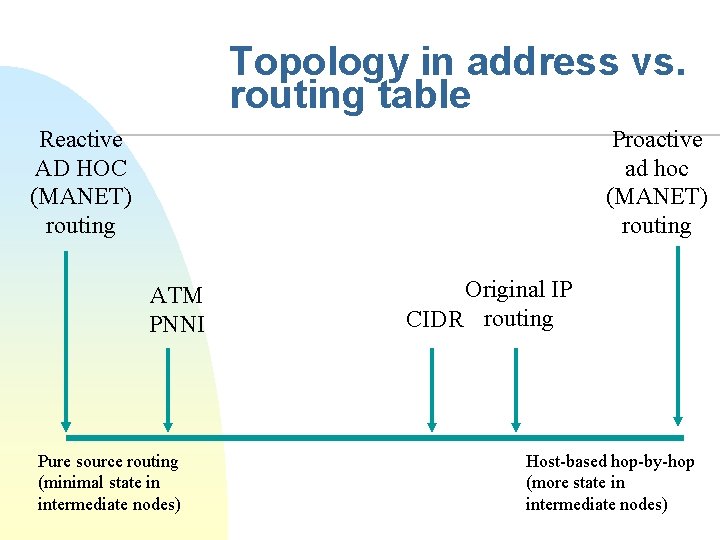
What is routing? n Selecting the right path towards an address n Addresses, names of locations or locators Routing table used for path selection Path selection algorithm n How to represent topology information? n n u In address vs. in the routing table

IP routing and scalability n What is routing? u n Addresses, routing tables, path selection, . . Different types of routing F F n Evolution of IP routing u n Source routing vs. hop-by-hop routing Source routing used by traceroute Strict source routing is never used Loose source routing used for diagnostics / performance Class-based systems to classless routing Difficult issues u State, directories, security, Qo. S

IP addresses n n Topological structure is reflected by splitting IP addresses into a host and network part Benefits of hierarchical addressing u n reduced number of routing table entries and efficient allocation of addresses. Subnetting u A subnet takes responsibility for delivering datagrams to a certain range of IP addresses. u The network part is now extended to include some bits from the host part.

Subnetting n n A subnet mask is a 32 -bit value that identifies which bits in an address represent network bits and which represent host bits. Note: Subnet-masks affect only internal structure and behaviour of a network!

Routing Tables n There are four basic items of information u A destination IP address. u A gateway IP address. This will be the same as the destination IP address for directly connected destinations. u Various flags F Usually displayed as U, G, H. U means the route is up. G means the route is via a gateway. H means the destination address is a host address as distinct from a network address. u The physical interface identification. u Additional info F Metrics, protocols

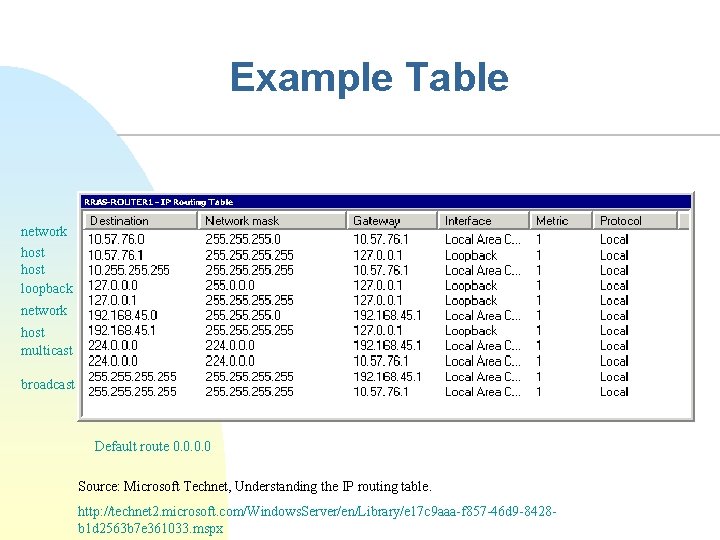
Example Table network host loopback network host multicast broadcast Default route 0. 0 Source: Microsoft Technet, Understanding the IP routing table. http: //technet 2. microsoft. com/Windows. Server/en/Library/e 17 c 9 aaa-f 857 -46 d 9 -8428 b 1 d 2563 b 7 e 361033. mspx

Host vs. router n n Host u First look for the destination address as a host address in the routing table u If it is not found then look for the destination net address in the routing table u If that is not found then use one of the default addresses (there may be several). Router u Very large routing table F u Especially in the backbone Routing protocols F Interior Gateway Protocols (OSPF) F Exterior Gateway Protocols (BGP). . .

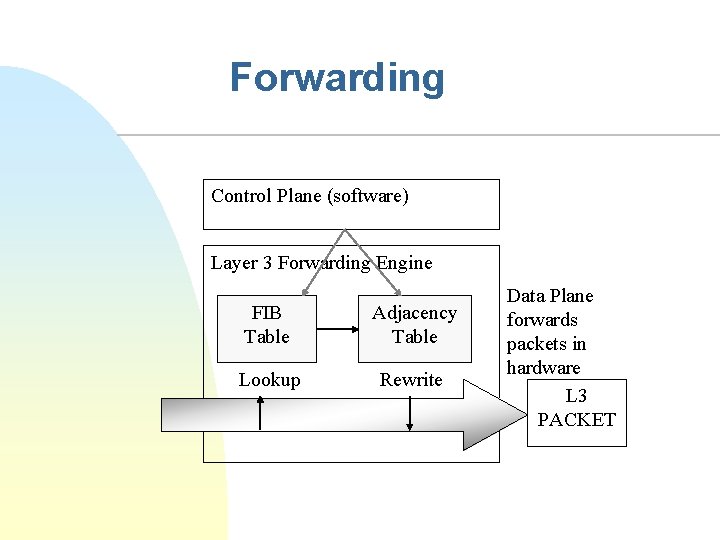
Forwarding Control Plane (software) Layer 3 Forwarding Engine FIB Table Adjacency Table Lookup Rewrite Data Plane forwards packets in hardware L 3 PACKET

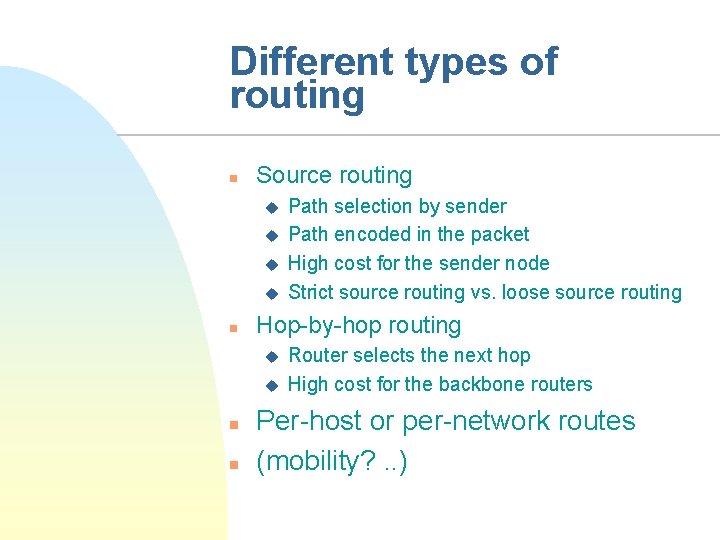
Different types of routing n Source routing u u n Hop-by-hop routing u u n n Path selection by sender Path encoded in the packet High cost for the sender node Strict source routing vs. loose source routing Router selects the next hop High cost for the backbone routers Per-host or per-network routes (mobility? . . )

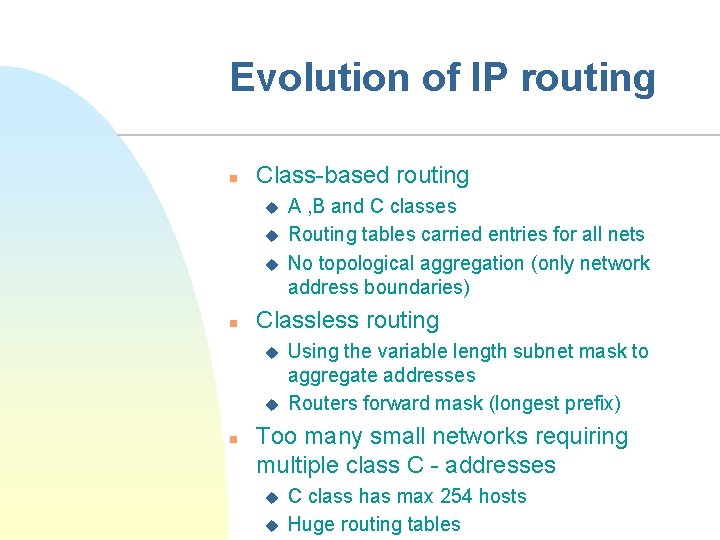
Evolution of IP routing n Class-based routing u u u n Classless routing u u n A , B and C classes Routing tables carried entries for all nets No topological aggregation (only network address boundaries) Using the variable length subnet mask to aggregate addresses Routers forward mask (longest prefix) Too many small networks requiring multiple class C - addresses u u C class has max 254 hosts Huge routing tables

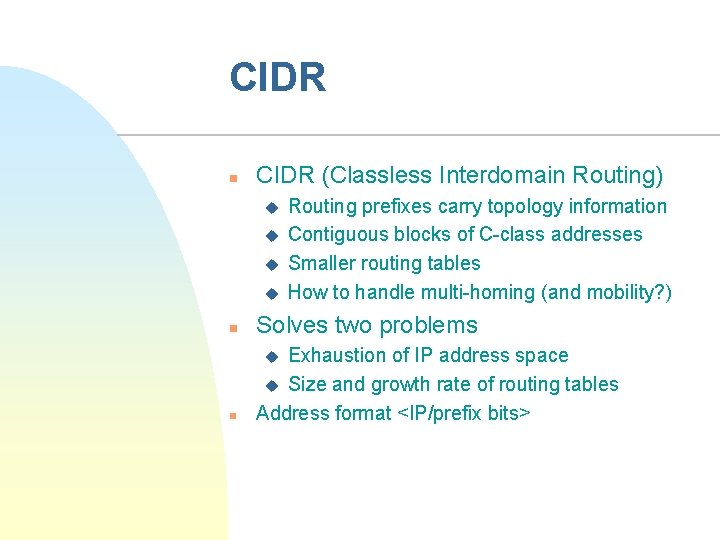
CIDR n CIDR (Classless Interdomain Routing) u u Routing prefixes carry topology information Contiguous blocks of C-class addresses Smaller routing tables How to handle multi-homing (and mobility? ) n Solves two problems n Exhaustion of IP address space u Size and growth rate of routing tables Address format <IP/prefix bits> u

CIDR and Route Summarization n The difference between CIDR and route summarization u u n Route summarization is generally done within a classful boundary CIDR combines several classful networks Examples of classless routing protocols u RIP version 2 (RIPv 2), OSPF, Intermediate System-to-Intermediate System (IS-IS), and Enhanced Interior Gateway Routing Protocol (EIGRP)

CIDR and IPv 6 n n CIDR present in IPv 6 (fully classless) 128 bit IPv 6 address has two parts: network and host u u n includes the prefix-length a decimal value indicating the number of higher-order bits in the address that belong to the network part ISP aggregates all its customers' prefixes into a single prefix and announces that single prefix to the IPv 6 Internet

BGP n n n BGP (Border Gateway Protocol) first became an Internet standard in 1989. BGP selects AS-level paths for inter-domain routing. Each AS may have multiple paths offered by neighbouring ASs. BGP-4 supports Classless Inter Domain Routing (CIDR) and is the routing protocol that is used today to route between autonomous systems. BGP uses TCP to establish a reliable connection between two BGP speakers on port 179. A path vector protocol, because it stores routing information as a combination of a destination and attributes of the path to that destination. The protocol uses a deterministic route selection process to select the best route from multiple feasible routes

BGP n n n Characteristics such as delay, link utilization or router hops are not considered in this process. BGP runs in two modes: EBGP and IBGP. EBGP (Exterior BGP) is run between different autonomous systems, and IBGP (Interior BGP) is run between BGP routers in the same autonomous system BGP only recalculates routing information relative to these updates, there is no regular process that must update all of its routing information like the SPF calculations in OSPF or IS-IS

BGP cont. n n n When the BGP router receives its neighbors' full BGP routing table (100 k routes), u Requires approx. 70 MB. u With the AS_PATH filters applied to inbound updates F 32 k routes in 28 MB. 60% decrease from optimal routing. Problems u multihomed customers forget to stop reannouncing routes from upstream A to upstream B u peer networks leak full tables to their peers u A misconfigured router leaks out all internal more specific routes (/48, /64, /128 prefixes) A network black hole is often used to improve aggregation of the BGP global routing table.

BGP Problems n n n Convergence time Limited policies Security problems

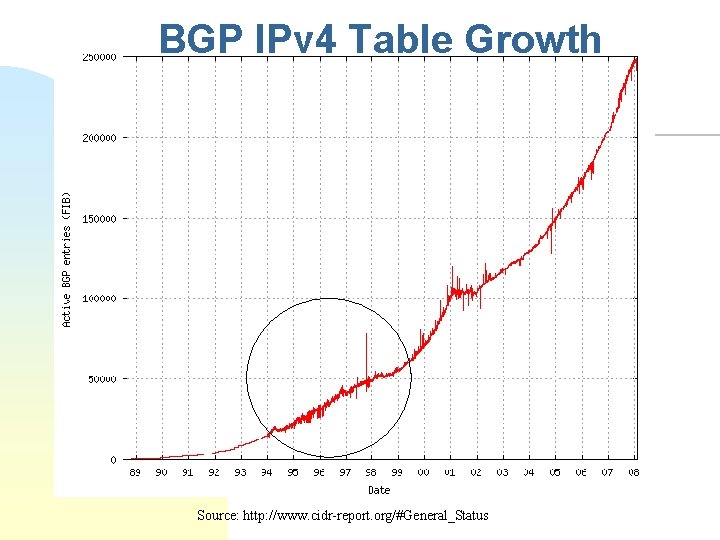
BGP IPv 4 Table Growth Source: http: //www. cidr-report. org/#General_Status

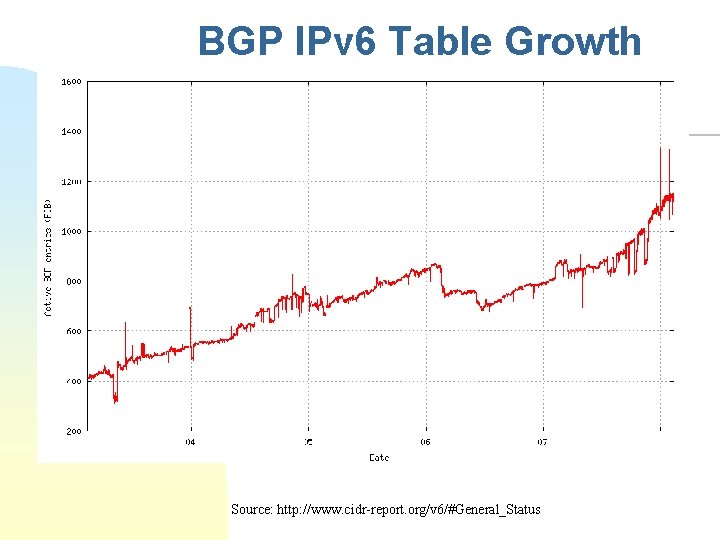
BGP IPv 6 Table Growth Source: http: //www. cidr-report. org/v 6/#General_Status

AS Numbers n n n 16 -bit AS numbers Current estimate is that limit will be reached on February 2011 IETF standards action in November 2006 u IANA extended the AS number field to 32 bits F F 65536 to 4, 294, 967, 296 values From Jan, 2007 32 bit values have been available from the Regional Internet Number Registries (RIR)



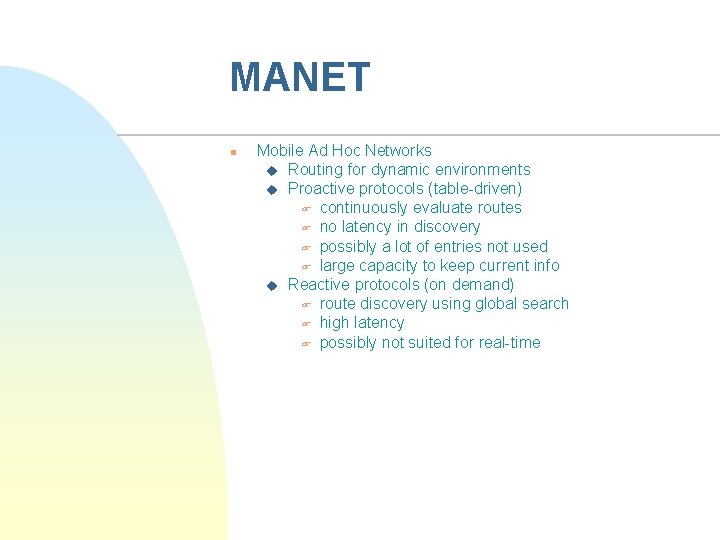
MANET n Mobile Ad Hoc Networks u Routing for dynamic environments u Proactive protocols (table-driven) F continuously evaluate routes F no latency in discovery F possibly a lot of entries not used F large capacity to keep current info u Reactive protocols (on demand) F route discovery using global search F high latency F possibly not suited for real-time

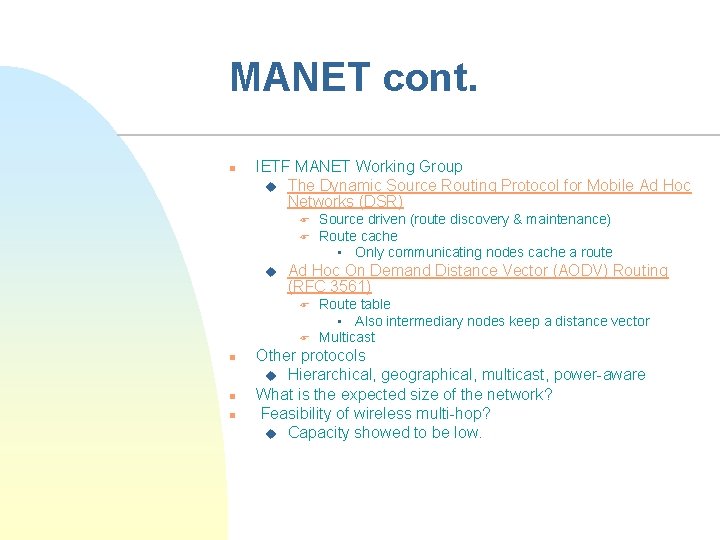
MANET cont. n IETF MANET Working Group u The Dynamic Source Routing Protocol for Mobile Ad Hoc Networks (DSR) F F u Ad Hoc On Demand Distance Vector (AODV) Routing (RFC 3561) F F n n n Source driven (route discovery & maintenance) Route cache • Only communicating nodes cache a route Route table • Also intermediary nodes keep a distance vector Multicast Other protocols u Hierarchical, geographical, multicast, power-aware What is the expected size of the network? Feasibility of wireless multi-hop? u Capacity showed to be low.

Topology in address vs. routing table Reactive AD HOC (MANET) routing Proactive ad hoc (MANET) routing ATM PNNI Pure source routing (minimal state in intermediate nodes) Original IP CIDR routing Host-based hop-by-hop (more state in intermediate nodes)

Difficult Issues n n Convergence time of routing information State in the network u n n Independence of directories Security of routing information u n Per-connection state is bad? (e. g. NAT) Whom to trust? How to represent authorization? Qo. S routing