Elements of a Trust Framework A Conceptual Model



















- Slides: 33

Elements of a Trust Framework A Conceptual Model By Jeff Stollman 12 JAN 2011

A problem well-stated is a problem half solved. – Charles Kettering, inventor (1876 -1958)

TRUST AND TRUST FRAMEWORKS

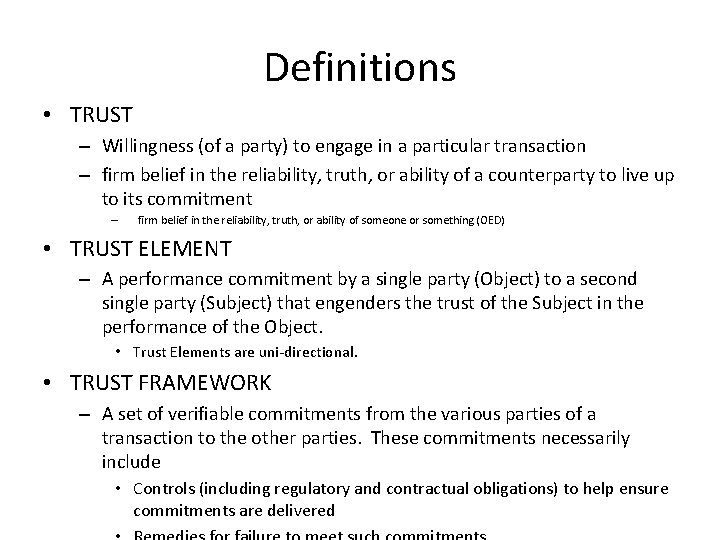
Definitions • TRUST – Willingness (of a party) to engage in a particular transaction – firm belief in the reliability, truth, or ability of a counterparty to live up to its commitment – firm belief in the reliability, truth, or ability of someone or something (OED) • TRUST ELEMENT – A performance commitment by a single party (Object) to a second single party (Subject) that engenders the trust of the Subject in the performance of the Object. • Trust Elements are uni-directional. • TRUST FRAMEWORK – A set of verifiable commitments from the various parties of a transaction to the other parties. These commitments necessarily include • Controls (including regulatory and contractual obligations) to help ensure commitments are delivered

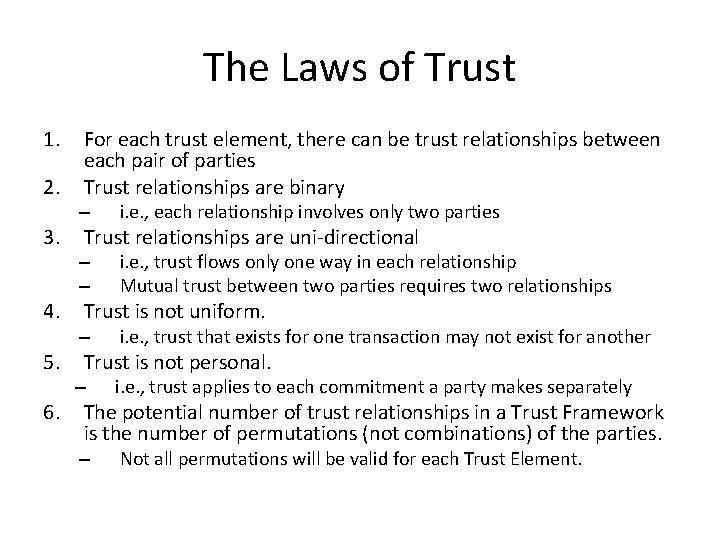
The Laws of Trust 1. 2. 3. 4. 5. 6. For each trust element, there can be trust relationships between each pair of parties Trust relationships are binary – i. e. , each relationship involves only two parties Trust relationships are uni-directional – – i. e. , trust flows only one way in each relationship Mutual trust between two parties requires two relationships Trust is not uniform. – i. e. , trust that exists for one transaction may not exist for another Trust is not personal. – i. e. , trust applies to each commitment a party makes separately The potential number of trust relationships in a Trust Framework is the number of permutations (not combinations) of the parties. – Not all permutations will be valid for each Trust Element.

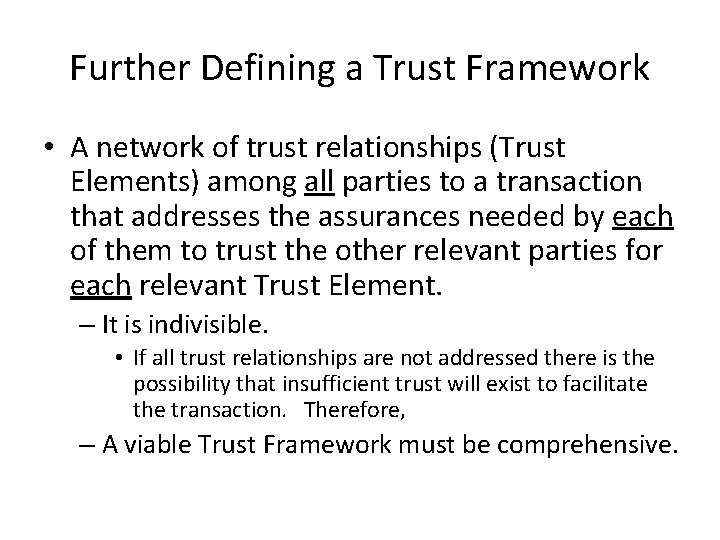
Further Defining a Trust Framework • A network of trust relationships (Trust Elements) among all parties to a transaction that addresses the assurances needed by each of them to trust the other relevant parties for each relevant Trust Element. – It is indivisible. • If all trust relationships are not addressed there is the possibility that insufficient trust will exist to facilitate the transaction. Therefore, – A viable Trust Framework must be comprehensive.

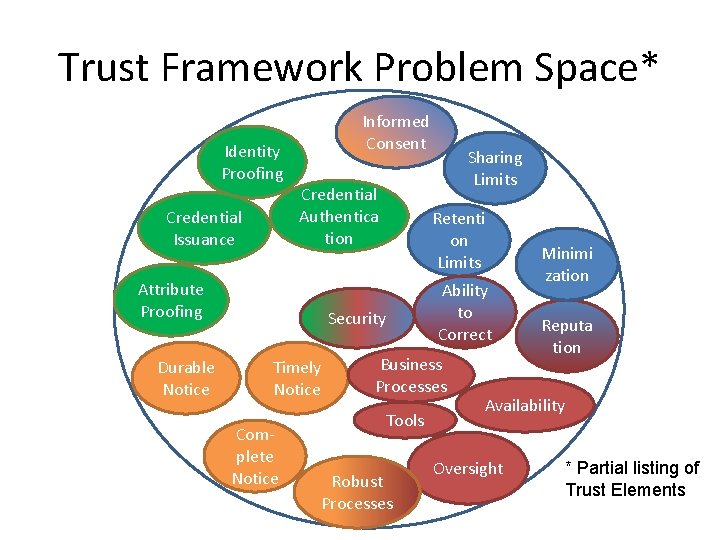
Trust Framework Problem Space* Identity Proofing Credential Issuance Informed Consent Credential Authentica tion Attribute Proofing Durable Notice Retenti on Limits Security Timely Notice Complete Notice Sharing Limits Ability to Correct Business Processes Tools Robust Processes Minimi zation Reputa tion Availability Oversight * Partial listing of Trust Elements

PRIVACY FRAMEWORKS

Defining a Privacy Framework • A Privacy Framework is a logical subset of the Trust Elements in a Trust Framework. – It is not all-inclusive of the Trust Elements in the Trust Framework. – The selection of Trust Elements to be included in the subset is not critical. • Good selection can yield more valuable benefits sooner. – It is critical that the Privacy Framework be supplemented by other subsets of the Trust Framework. – The value of the Privacy Framework is enhanced as the supplemental frameworks approach the totality of the Trust Framework.

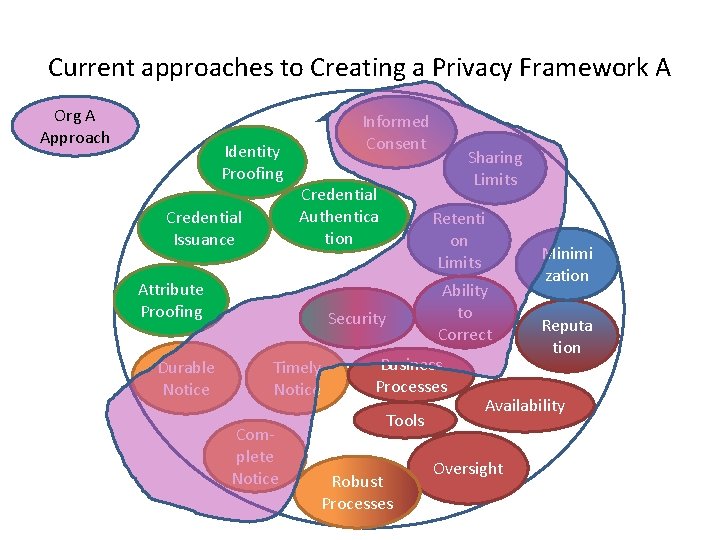
Current approaches to Creating a Privacy Framework A Org A Approach Identity Proofing Credential Issuance Informed Consent Credential Authentica tion Attribute Proofing Durable Notice Retenti on Limits Security Timely Notice Complete Notice Sharing Limits Ability to Correct Business Processes Tools Robust Processes Minimi zation Reputa tion Availability Oversight

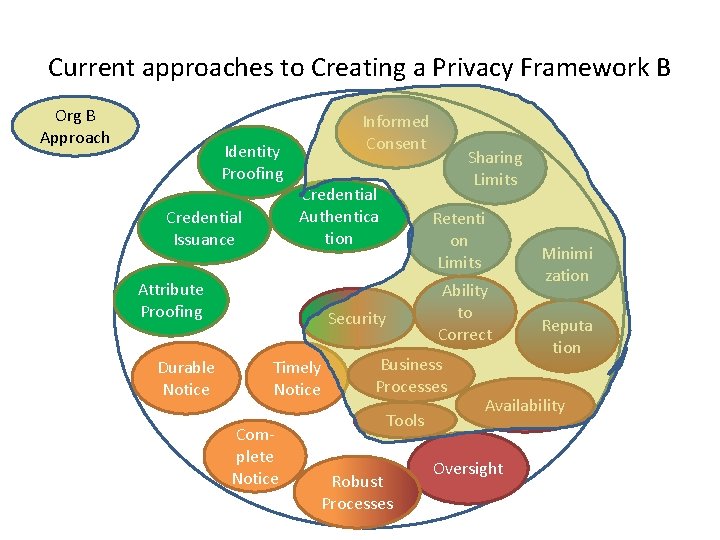
Current approaches to Creating a Privacy Framework B Org B Approach Identity Proofing Credential Issuance Informed Consent Credential Authentica tion Attribute Proofing Durable Notice Retenti on Limits Security Timely Notice Complete Notice Sharing Limits Ability to Correct Business Processes Tools Robust Processes Minimi zation Reputa tion Availability Oversight

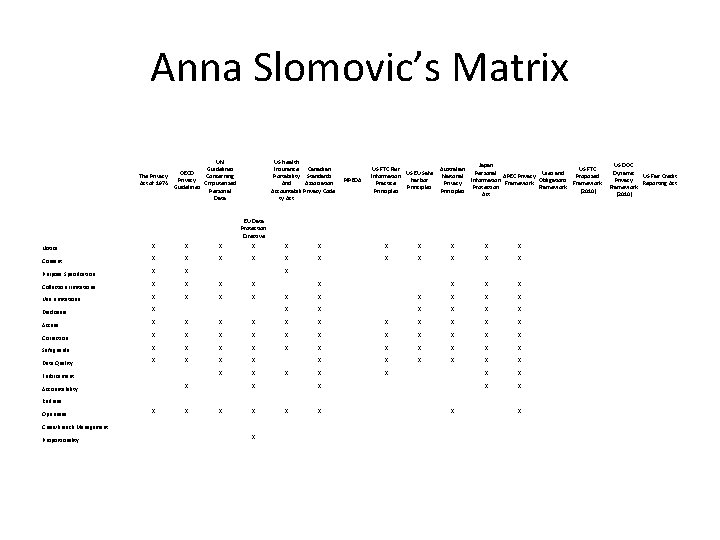
Anna Slomovic’s Matrix UN Guidelines OECD Concerning The Privacy Cmputerized Act of 1974 Guidelines Personal Data US Health Insurance Canadian Portability Standards And Association Accountabili Privacy Code ty Act PIPEDA US FTC Fair US-EU Safe Information Harbor Practice Principles Japan Australian Personal Uses and APEC Privacy Naitonal Information Obligations Privacy Framework Protection Framework Principles Act EU Data Protection Directive Notice X X X Consent X X X Purpose Specification X X Collection Limitations X X Use Limitations X X Disclosure X Access X X X Correction X X X Safeguards X X Data Quality X X Enforcement X X X X X X X X X X X X X X X Accountability X X Redress Openness X X Crisis/Breach Management Proportionality X X X US FTC Proposed Framework (2010) US DOC Dynamic US Fair Credit Privacy Reporting Act Framework (2010)

SPECIFYING THE TRUST FRAMEWORK

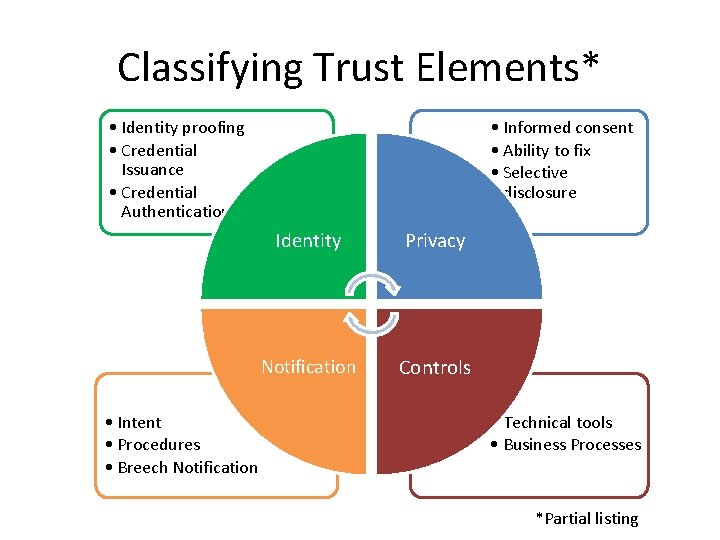
Classifying Trust Elements* • Identity proofing • Credential Issuance • Credential Authentication • Intent • Procedures • Breech Notification • Informed consent • Ability to fix • Selective disclosure Identity Privacy Notification Controls • Technical tools • Business Processes *Partial listing

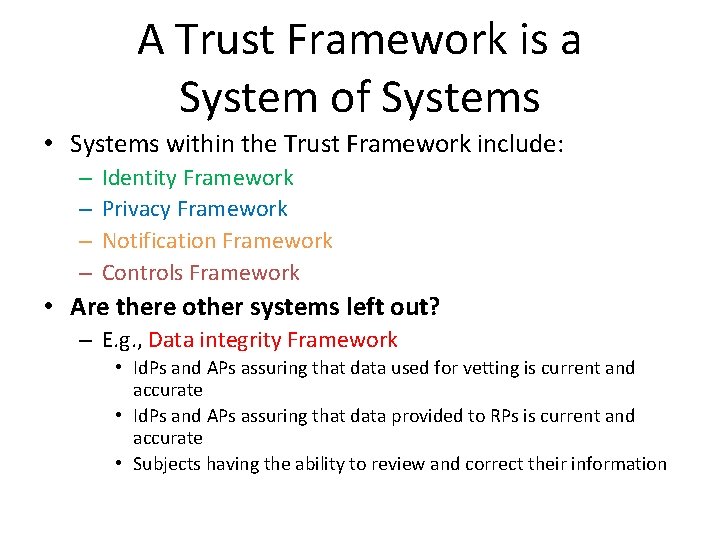
A Trust Framework is a System of Systems • Systems within the Trust Framework include: – – Identity Framework Privacy Framework Notification Framework Controls Framework • Are there other systems left out? – E. g. , Data integrity Framework • Id. Ps and APs assuring that data used for vetting is current and accurate • Id. Ps and APs assuring that data provided to RPs is current and accurate • Subjects having the ability to review and correct their information

Elements of an Identity Framework* • • • Identity proofing Attribute proofing Credential generation Credential issuance Credential lifecycle management • *Example listing

Elements of a Privacy Framework* • • Informed consent Restrictions on collection Restrictions on use Restrictions on how/to whom it is distributed Retention limits (minimum and maximum) Maintain accuracy Ability to correct Protection of data • *Example listing

Elements of a Notification Framework* • • • Timely presentation Informed Consent What is collected Why its collected How it is used How it is stored Data retention How/to whom it is distributed Remedies • *Example listing

Elements of a Controls Framework* • • • Secure network communication Secure storage Secure disposal Staff vetting Intra-organization business-process exposure Inter-organization business-process exposure Third-party verification Process monitoring Management oversight Remedies • *Example Listing

ROLES

Parties in a Trust Framework 1 • Primary roles – Those who actual conduct the transaction • • Subject Identity Provider Attribute Provider Relying Party (Service Provider)

Parties in a Trust Framework 2 • Secondary roles – Additional/alternate parties to the primary roles who may/may not be involved in a particular transaction • • • Subject Delegate Entity Agent Entity Delegate ISP – For each Party • Registration Authority • Verifier • Credential Issuer • Subscriber

Parties in a Trust Framework 3 • Tertiary roles – Those who provide enforcement of and remedies to agreements among the primary and secondary roles • • • Trust Framework Provider Federation Operator Assessor Regional legal system Referee

Roles of the Parties • The role of any party can change – even within the conduct of a single transaction. E. g. , – An Id. P may also be a Credential Provider – A Federation Operator may also act as an Assessor – An RP may be a Subject in having its identity verified by Subject, Id. P, or AP. – An RP who sells something to Subject A, may then become an AP vouching for Subject A’s conduct in the prior sale (e. g. , paid on time)

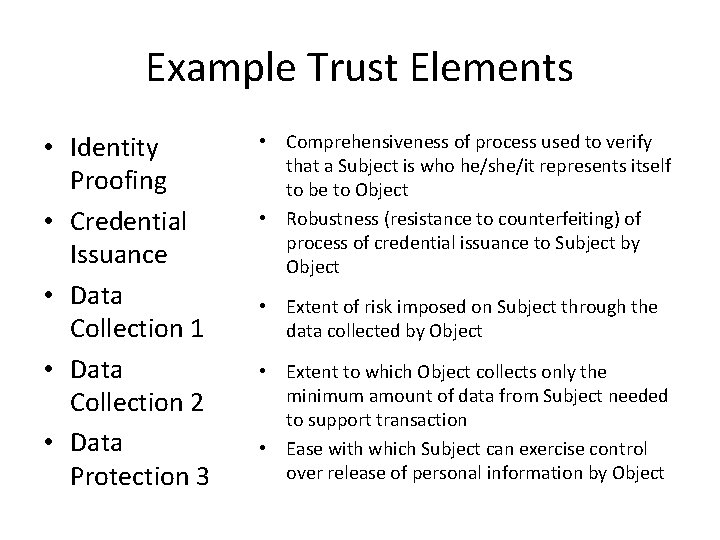
Example Trust Elements • Identity Proofing • Credential Issuance • Data Collection 1 • Data Collection 2 • Data Protection 3 • Comprehensiveness of process used to verify that a Subject is who he/she/it represents itself to be to Object • Robustness (resistance to counterfeiting) of process of credential issuance to Subject by Object • Extent of risk imposed on Subject through the data collected by Object • Extent to which Object collects only the minimum amount of data from Subject needed to support transaction • Ease with which Subject can exercise control over release of personal information by Object

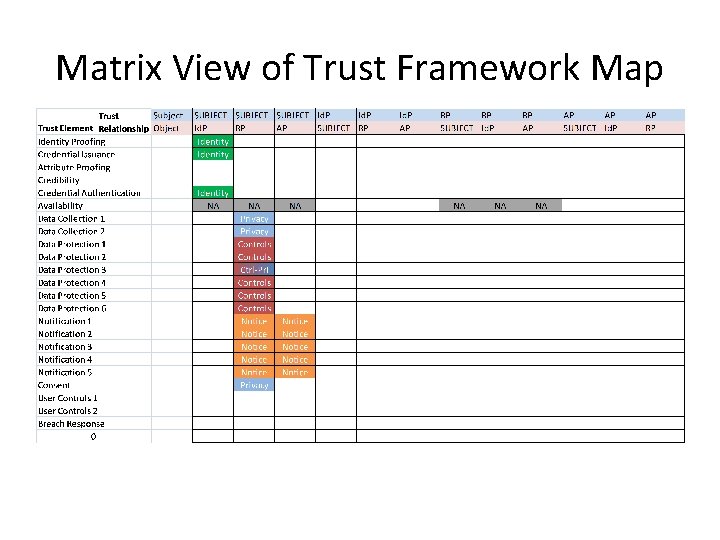
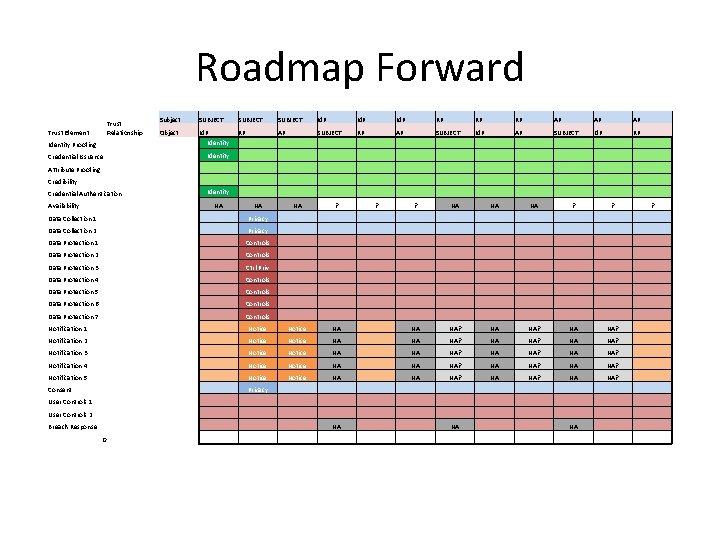
Matrix View of Trust Framework Map

Roadmap Forward Trust Relationship Trust Element Subject SUBJECT Id. P RP RP RP AP AP Object Id. P RP AP SUBJECT Id. P AP RP Identity Proofing Identity Credential Issuance Identity Attribute Proofing Credibility Credential Authentication Identity Availability NA NA NA ? ? ? Data Collection 1 Privacy Data Collection 2 Privacy Data Protection 1 Controls Data Protection 2 Controls Data Protection 3 Ctrl-Priv Data Protection 4 Controls Data Protection 5 Controls Data Protection 6 Controls Data Protection 7 Controls Notification 1 Notice NA NA NA? Notification 2 Notice NA NA NA? Notification 3 Notice NA NA NA? Notification 4 Notice NA NA NA? Notification 5 Notice NA NA NA? Consent User Controls 1 User Controls 2 Breach Response NA NA 0 Privacy

Conclusions 1. The Trust Framework problem is a System of Systems issue. 2. While in an ideal world all cells need to be complete for comprehensive trust, practical levels of trust can be obtained by specifying criteria for selective cells. 3. By attaining consensus on the map of the problem space (the trust elements and the roles), we can determine the appropriate categories for major subsystems (e. g. , Identity, Privacy, Notification, Controls).

Conclusions cont’d. 4. After attaining consensus, we can allocate the cells among the sub-systems to allow us to work in parallel to more rapidly build a coherent Trust Framework. 5. We can prioritize the order in which we address the cells to maximize our impact. 6. As long as we follow the map, we can shift cells from subsystem to subsystem and reprioritize the order without losing coherence.

Speculation • It is commonly assumed that our Service Assessment Criteria must follow existing regulatory requirements. • I suggest that this is not so. • If we devise reasonable Service Assessment Criteria that afford multiple levels of assurance/protection for each subsystem, entities can seek certification at the level needed to meet both their business and regulatory requirements. • Hopefully, the Criteria levels will afford enough parallelism with major regulations to make this achievable. • If not, perhaps the maturity of our framework will prompt regulators to have the courage to update their codes, coalescing around a better mix of economy and protection.

BACKUP SLIDES

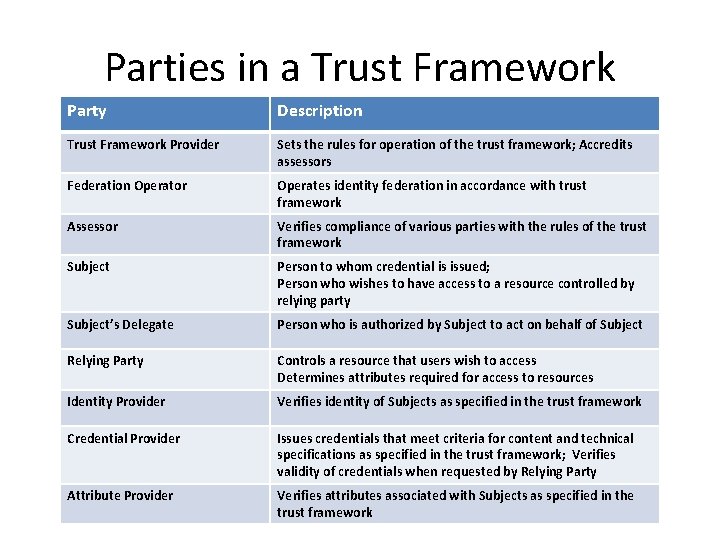
Parties in a Trust Framework Party Description Trust Framework Provider Sets the rules for operation of the trust framework; Accredits assessors Federation Operator Operates identity federation in accordance with trust framework Assessor Verifies compliance of various parties with the rules of the trust framework Subject Person to whom credential is issued; Person who wishes to have access to a resource controlled by relying party Subject’s Delegate Person who is authorized by Subject to act on behalf of Subject Relying Party Controls a resource that users wish to access Determines attributes required for access to resources Identity Provider Verifies identity of Subjects as specified in the trust framework Credential Provider Issues credentials that meet criteria for content and technical specifications as specified in the trust framework; Verifies validity of credentials when requested by Relying Party Attribute Provider Verifies attributes associated with Subjects as specified in the trust framework

Definitions 3 • IPSEITY – Your unique carbon life form • ATTRIBUTE – Everything that is not Ipseity