T110 5140 Network Application Frameworks and XML Summary












- Slides: 55

T-110. 5140 Network Application Frameworks and XML Summary and Conclusions 25. 04. 2006 Sasu Tarkoma

Topics Covered n n n Distributed systems security Multi-addressing: Mobility and multihoming Building applications with XML u u n Distributed objects Role of directory services Mobile and wireless applications XML-based presentation and RPC Scalability and performance issues

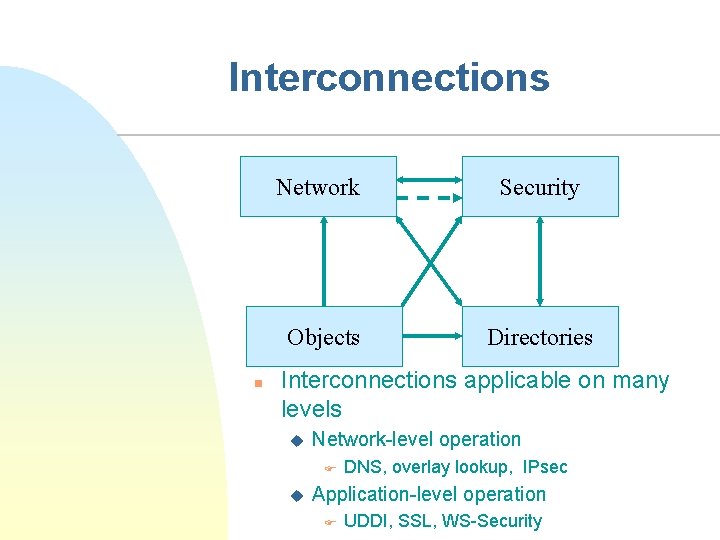
Interconnections n Network Security Objects Directories Interconnections applicable on many levels u Network-level operation F u DNS, overlay lookup, IPsec Application-level operation F UDDI, SSL, WS-Security

Mobility and Routing

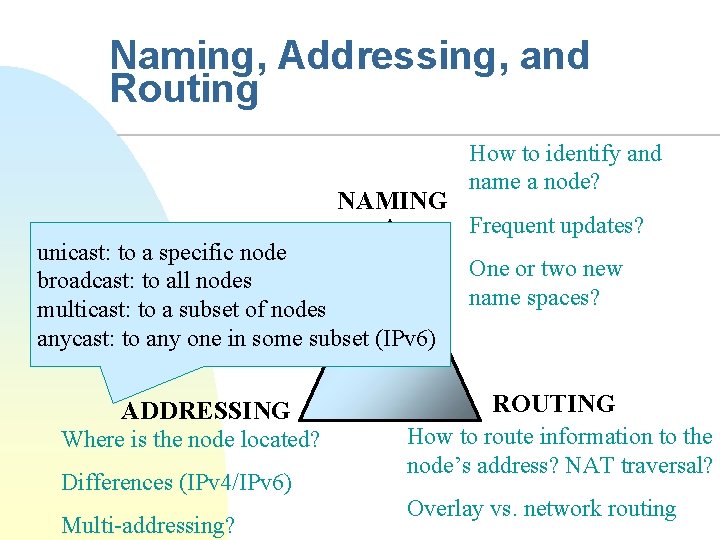
Naming, Addressing, and Routing NAMING unicast: to a specific node broadcast: to all nodes multicast: to a subset of nodes anycast: to any one in some subset (IPv 6) ADDRESSING Where is the node located? Differences (IPv 4/IPv 6) Multi-addressing? How to identify and name a node? Frequent updates? One or two new name spaces? ROUTING How to route information to the node’s address? NAT traversal? Overlay vs. network routing

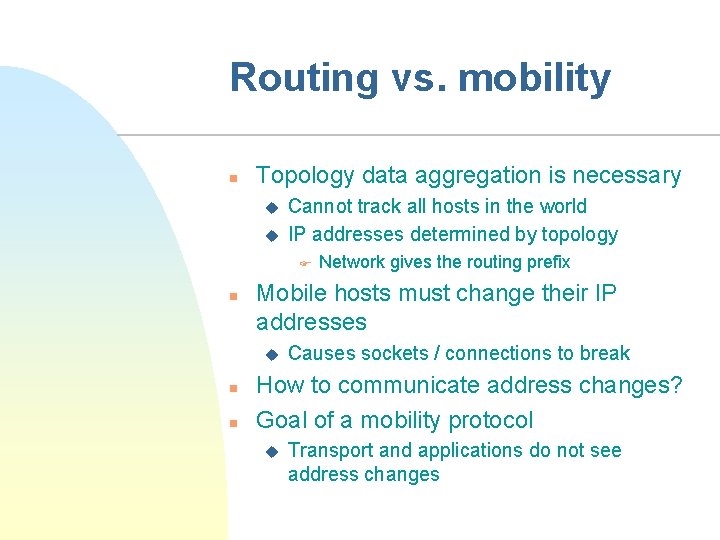
Routing vs. mobility n Topology data aggregation is necessary u u Cannot track all hosts in the world IP addresses determined by topology F n Mobile hosts must change their IP addresses u n n Network gives the routing prefix Causes sockets / connections to break How to communicate address changes? Goal of a mobility protocol u Transport and applications do not see address changes

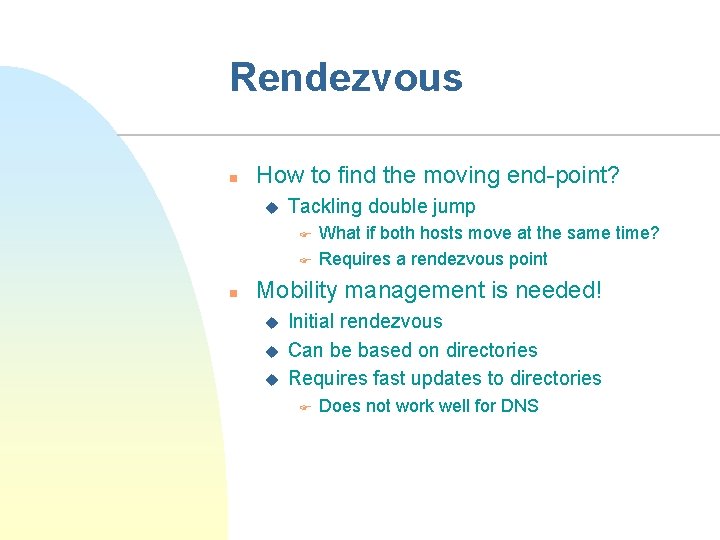
Rendezvous n How to find the moving end-point? u Tackling double jump F F n What if both hosts move at the same time? Requires a rendezvous point Mobility management is needed! u u u Initial rendezvous Can be based on directories Requires fast updates to directories F Does not work well for DNS

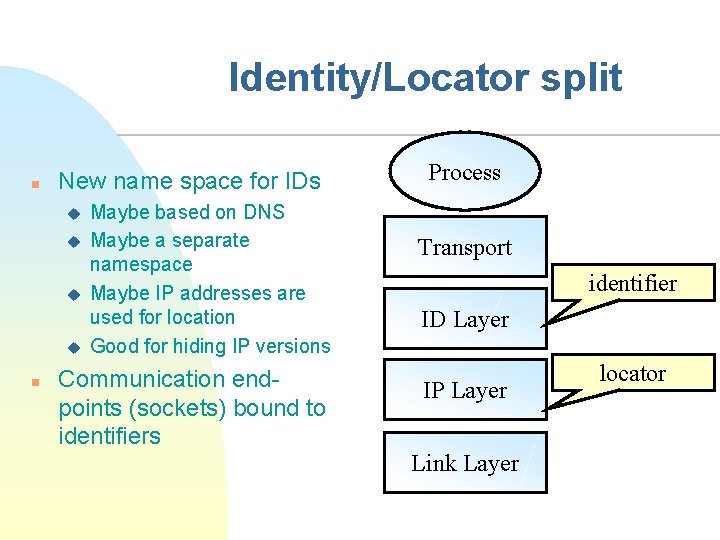
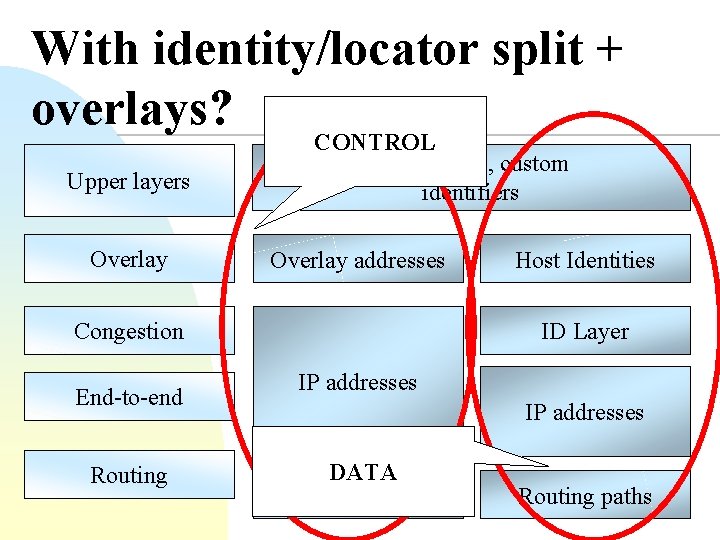
Identity/Locator split n New name space for IDs u u n Maybe based on DNS Maybe a separate namespace Maybe IP addresses are used for location Good for hiding IP versions Communication endpoints (sockets) bound to identifiers Process Transport identifier ID Layer IP Layer Link Layer locator

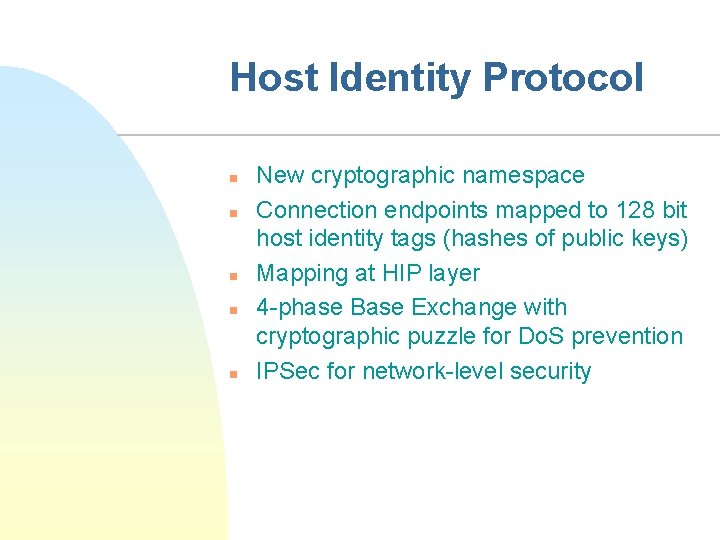
Host Identity Protocol n n n New cryptographic namespace Connection endpoints mapped to 128 bit host identity tags (hashes of public keys) Mapping at HIP layer 4 -phase Base Exchange with cryptographic puzzle for Do. S prevention IPSec for network-level security

Upper layer view n IP connectivity problematic today u u n HIP has a potential remedy u u n Broken by firewalls, NATs, mobility Two versions of IP: IPv 4 and IPv 6 Restores end-to-end connectivity (NAT traversal possible but may require changes / tunnelling) Adds opportunistic security Handles mobility and multi-homing Requires DHT based overlay (currently missing) Where is the network state? u Routers know addresses F u DHT knows HITs / SIDs F u Like today Lease based storage Middleboxes know SPIs F Soft state

Lessons to learn n Hierarchical routing likely to stay u u n Applications face changing connectivity u u n n n Addresses carry topological information Efficient and well established Qo. S varies periods of non-connectivity Identifiers and locators likely to split Mobility management is needed Probably changes in directory services u Overlays have been proposed

Summary n n Topology based routing is necessary Mobility causes address changes Address changes must be signalled endto-end Mobility management needed u u n Initial rendezvous: maybe a directory service Double jump problem: rendezvous needed Many engineering trade-offs

Distributed Hash Tables and Overlays

Overlay Networks n n n Origin in Peer-to-Peer (P 2 P) Builds upon Distributed Hash Tables (DHTs) Easy to deploy u u n No changes to routers or TCP/IP stack Typically on application layer Overlay properties u u u Resilience Fault-tolerance Scalability

Some DHT applications n n n n n File sharing Web caching Censor-resistant data storage Event notification Naming systems Query and indexing Communication primitives Backup storage Web archive

Applications for DHTs n DHTs are used as a basic building block for an application-level infrastructure u Internet Indirection Infrastructure (i 3) F u New forwarding infrastructure based on Chord DOA (Delegation Oriented Architecture) F New naming and addressing infrastructure based on overlays

Summary n Mobility and multi-homing require directories u n Overlay networks have been proposed u u u n Scalability, low-latency updates Searching, storing, routing, notification, . . Lookup (Chord, Tapestry, Pastry), coordination primitives (i 3), middlebox support (DOA) Logarithmic scalability, decentralised, … Host/identity split and overlays for directories seem good candidates for solving many of the issues with mobility and multi-homing

Middleware

Middleware n n n Widely used and popular term Fuzzy term One definition u n “A set of service elements above the operating system and the communications stack” Second definition u “Software that provides a programming model above the basic building blocks of processes and message passing” (Colouris, Dollimore, Kindberg, 2001)

Why Middleware? n Application development is complex and time-consuming u u Should every developer code their own protocols for directories, transactions, . . ? How to cope with heterogeneous environments? F n Networks, operating systems, hardware, programming languages Middleware is needed u To cut down development time F u u Rapid application development Simplify the development of applications Support heterogeneous environments and mask differences in OS/languages/hardware

Middleware cont. n Middleware services include directory, trading, brokering u remote invocation (RPC) facilities u transactions u persistent repositories u location and failure transparency u messaging u Security Network stack (transport and below) is not part of middleware u n

Transparencies n Location transparency u n transport protocol transparency u n RPC may be implemented using any transport protocol transparency of OS and hardware u u u n RPC and RMI used without knowledge of the location of the invoked procedure / object RPC/RMI uses external data representation Presentation is important XML is becoming increasingly important transparency of programming languages u language independent definition of procedures: CORBA IDL

Network Application Framework n n Network Application Framework is middleware Contains services for distributed applications Middleware as a term is fuzzier and larger In this course, we focus on network application frameworks and XML u u objects (discovery, representation) directories (overlays, . . ) network security

Examples n Middleware u u u n CORBA Message-oriented Middleware Event Systems & tuple spaces Java Message Service Java 2 Enterprise Edition (J 2 EE). NET Mobile middleware u u WAE J 2 ME Wireless CORBA FUEGO

Mobile Middleware I n Middleware is typically designed and implemented for fixed-network hosts u u u n High bandwidth, low latency, reliable communication Persistent storage and sufficient computing power No mobility Mobile environment requires new solutions u u u Existing middleware services do not scale Previous lectures: mobility is challenging Small devices / embedded systems pose totally different challenges

Mobile Middleware II n Goals for middleware: u n fault-tolerance, adaptability, heterogeneity, scalability, resource sharing Mobile middleware u u dynamically changing context decoupled F u events, tuple spaces Basic solution for wireless F Use a proxy

Summary n Middleware u u n for application development and deployment for supporting heterogeneous environments Main communication paradigms: RPC/RMI, asynchronous events (publish/subscribe) J 2 EE, CORBA, . . Mobile middleware u u u Desktop middleware not usable on small, mobile devices Special solutions are needed J 2 ME, Wireless CORBA, . .

Web Services

Standardization n W 3 C Web Services u XML Protocol Working Group F u u u Web Services Addressing Working Group Web Services Choreography Working Group Web Services Description Working Group F n WSDL OASIS u n SOAP E-business standards, UDDI WS-I (Web Service Interoperability Org. ) u Binding profiles, . .

Web Service Architecture n The three major roles in web services u Service provider F u Service Requestor F u Any consumer / client Service Registry F n Provider of the WS logically centralized directory of services A protocol stack is needed to support these roles

Web Services Protocol Stack n Message Transport u u n XML Messaging u u n Responsible for encoding messages in common XML format XML-RPC, SOAP Service Description u u n Responsible for transporting messages HTTP, BEEP Responsible for describing an interface to a specific web service WSDL Service discovery u u Responsible for service discovery and search UDDI

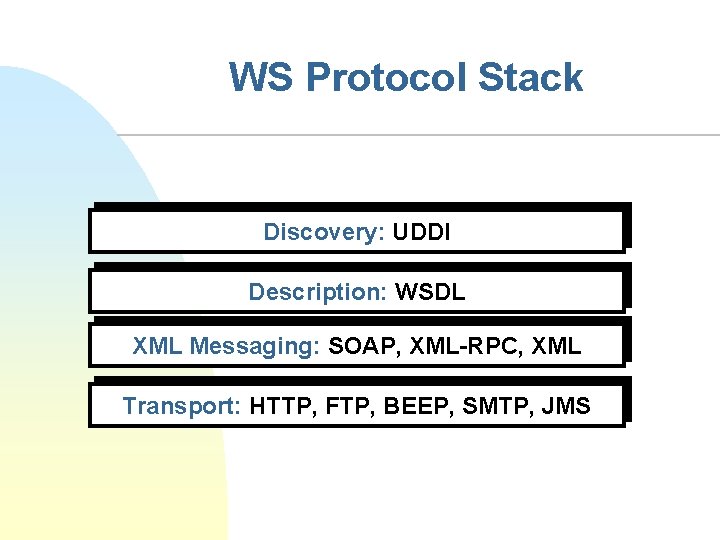
WS Protocol Stack Discovery: UDDI Description: WSDL XML Messaging: SOAP, XML-RPC, XML Transport: HTTP, FTP, BEEP, SMTP, JMS

What is WSDL? n n WSDL: Web Service Description Language An XML language used to describe and locate web services u u u n n Commonly used to describe SOAP-based services W 3 C standard (work in progress) u u u n location of web service methods that are available data type information and XML messages Initial input: WSDL 1. 1 as W 3 C Note Current version 2. 0 (last call) Some differences between 1. 1 and 2. 0 WSDL 1. 1 in WS-I Basic Profile 1. 0 and 1. 1.

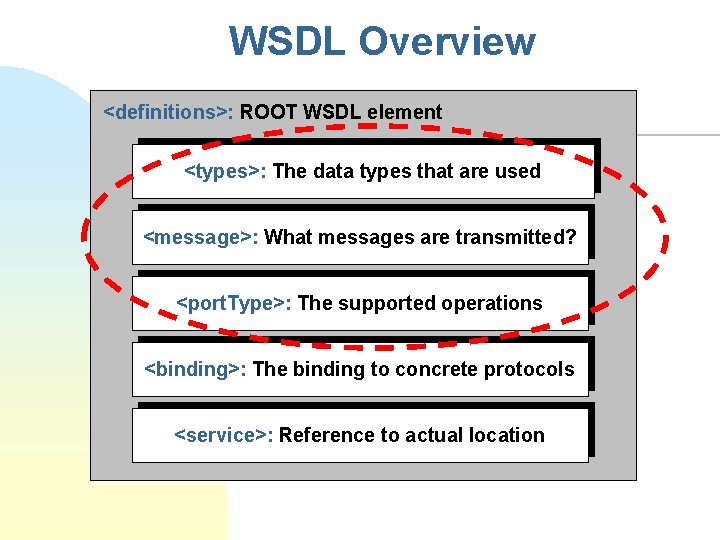
WSDL Overview <definitions>: ROOT WSDL element <types>: The data types that are used <message>: What messages are transmitted? <port. Type>: The supported operations <binding>: The binding to concrete protocols <service>: Reference to actual location

Mapping SOAP to WSDL 35

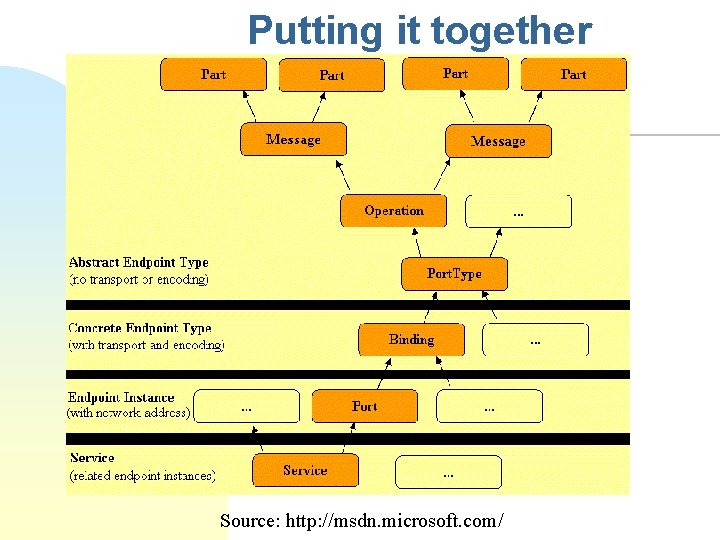
Putting it together Source: http: //msdn. microsoft. com/

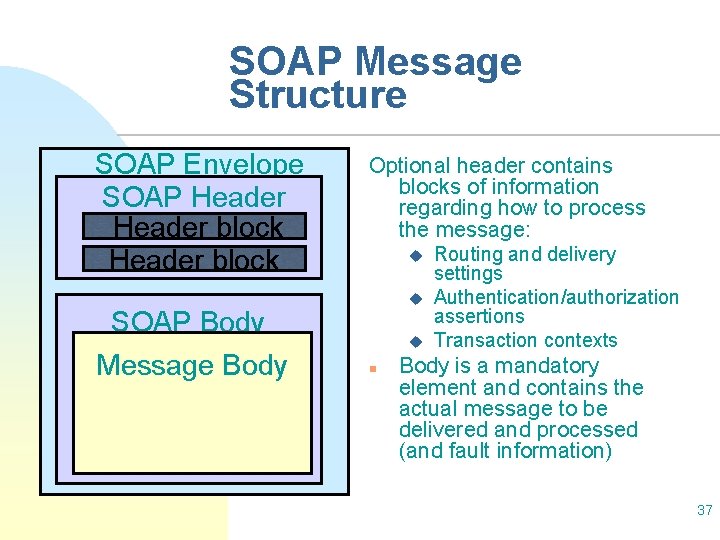
SOAP Message Structure SOAP Envelope SOAP Header block SOAP Body Message Body Optional header contains blocks of information regarding how to process the message: u u u n Routing and delivery settings Authentication/authorization assertions Transaction contexts Body is a mandatory element and contains the actual message to be delivered and processed (and fault information) 37

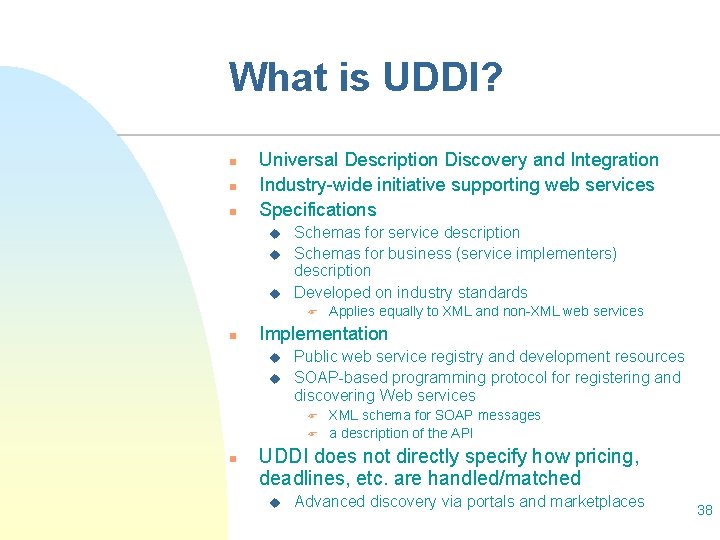
What is UDDI? n n n Universal Description Discovery and Integration Industry-wide initiative supporting web services Specifications u u u Schemas for service description Schemas for business (service implementers) description Developed on industry standards F n Implementation u u Public web service registry and development resources SOAP-based programming protocol for registering and discovering Web services F F n Applies equally to XML and non-XML web services XML schema for SOAP messages a description of the API UDDI does not directly specify how pricing, deadlines, etc. are handled/matched u Advanced discovery via portals and marketplaces 38

Web Services Security

Need for XML security n XML document can be encrypted using SSL or IPSec u u u n n this cannot handle the different parts of the documents may be routed hop-by-hop different entities must process different parts of the document SSL/TLS/IPSec provide message integrity and privacy only when the message is in transit We also need to encrypt and authenticate the document in arbitrary sequences and to involve multiple parties

High-level view to WS security n n Security is as strong as the weakest link The options for an attacker are: u Attack the Web Service directly F u u u Using ”unexpected” XML Attack the Web Services platform Attack a WS security tool Attack the underlying operating system or network connection

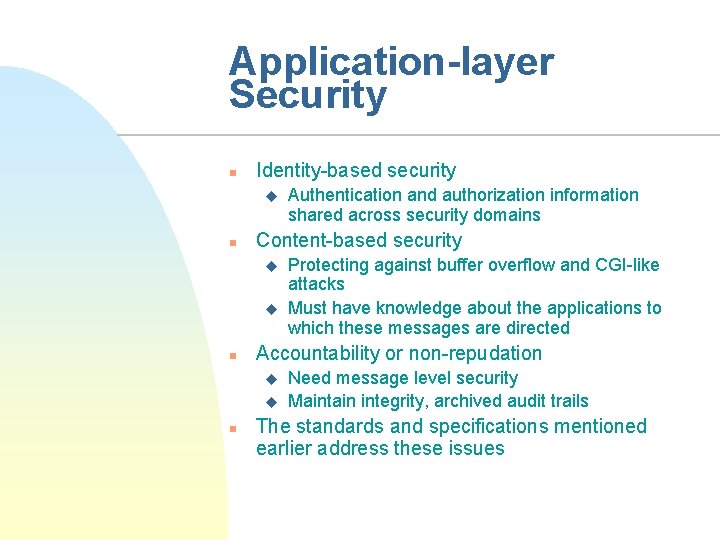
Application-layer Security n Identity-based security u n Content-based security u u n Protecting against buffer overflow and CGI-like attacks Must have knowledge about the applications to which these messages are directed Accountability or non-repudation u u n Authentication and authorization information shared across security domains Need message level security Maintain integrity, archived audit trails The standards and specifications mentioned earlier address these issues

Standardization landscape n n n Who are specifying the basic standards? Who are specifying the higher level standards? Who is implementing the standards?

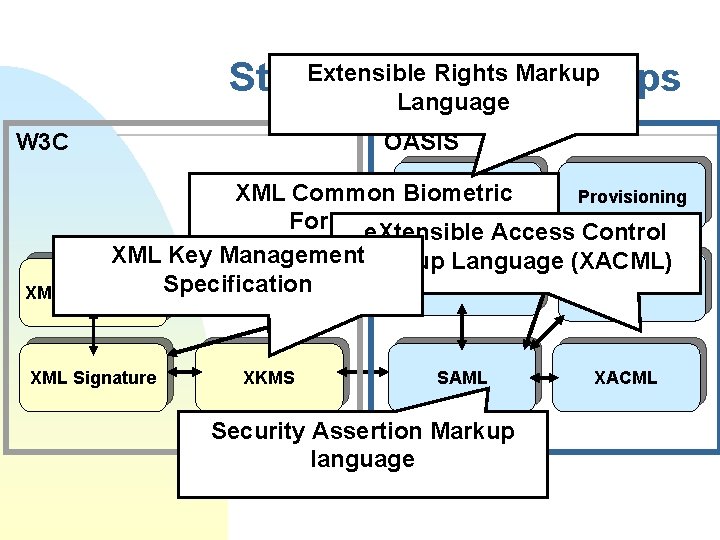
Who are specifying the standards? n Joint IETF/W 3 C u n W 3 C u u n XML Signature (www. w 3. org/Signature) XML Encryption (www. w 3. org/Encryption/2001) XML Key Management (XKMS) (www. w 3. org/2001/XKMS) OASIS u WS-Security F u u u n SOAP Message Security specification etc. SAML: Security Assertion Markup Language XACML: Extensible Access Control Markup language Electronic Business XML (eb. XML) (with UN/CEFACT) Web Services Interoperability Organization (WS-I) u Basic security

Extensible Rights Markup Standardization Groups Language W 3 C OASIS XML Common Biometric Xr. ML Provisioning Formate. Xtensible (XCBF) Access Control XML Key Management. Markup Language (XACML) WS-Security Biometrics XML Encryption Specification XML Signature XKMS SAML Security Assertion Markup language XACML

Basic XML Security n n XML Digital Signatures (XMLDSIG) XML Encryption XML Canonicalization XML Key Management

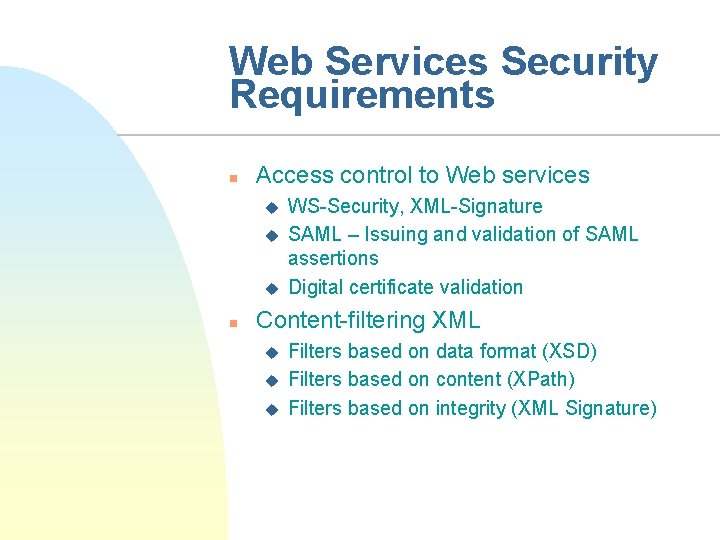
Web Services Security Requirements n Access control to Web services u u u n WS-Security, XML-Signature SAML – Issuing and validation of SAML assertions Digital certificate validation Content-filtering XML u u u Filters based on data format (XSD) Filters based on content (XPath) Filters based on integrity (XML Signature)

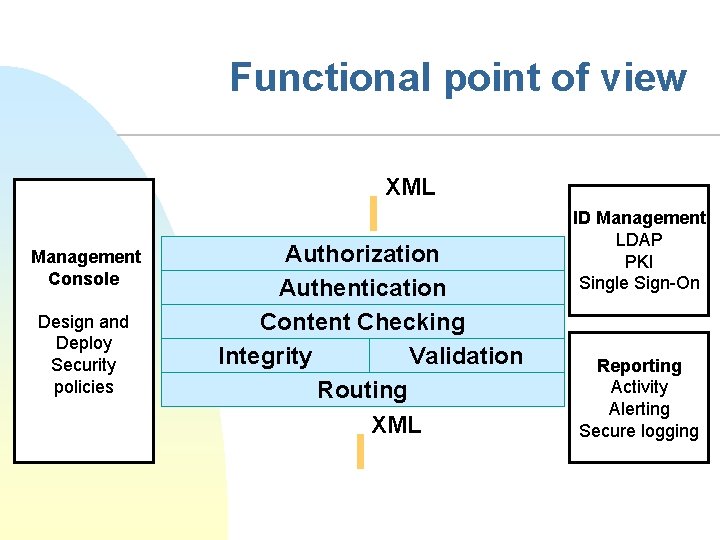
Functional point of view XML Management Console Design and Deploy Security policies Authorization Authentication Content Checking Integrity Validation Routing XML ID Management LDAP PKI Single Sign-On Reporting Activity Alerting Secure logging

Security Contexts in Web Services n Remember Web Services goals: u u n Re-use existing services Combine services from several domains Security result: Must support several security domains u u SOAP intermediaries Reusing security tokens from one message in another message

Summary n Security contexts u u n WS security standard revisited u u n SOAP header carries security information (and other info as well) Selective processing SAML u u n Security needed within and between contexts XML validation, encryption, and authentication needed between security contexts! Statements about authorization, authentication, attributes SAML & WS-Security & XACML Implementations available

Putting it together

With identity/locator split + overlays? Upper layers Overlay CONTROL DNS names, custom identifiers Overlay addresses Congestion End-to-end Routing Host Identities ID Layer IP addresses DATA Routing paths

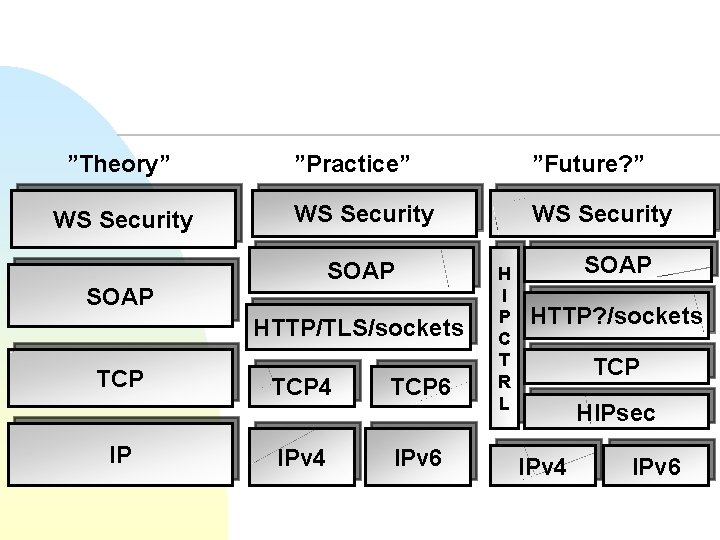
”Theory” WS Security ”Practice” ”Future? ” WS Security SOAP HTTP/TLS/sockets TCP IP TCP 4 TCP 6 IPv 4 IPv 6 H I P C T R L SOAP HTTP? /sockets TCP HIPsec IPv 4 IPv 6

Discussion

Important Dates n n Exam on Tuesday 16. 5. 9 -12 in T 1. Deadline for the second assignment 12. 5.