Stuart Aston Chief Security Advisor Microsoft UK s













- Slides: 22

Stuart Aston Chief Security Advisor Microsoft UK s tuart. aston@microsoft. com

Trustworthy Computing Memo

Threat Landscape Blended Attack National Interest Specialist Targeted Attack Personal Gain Expert Personal Fame Hacker Agenda Hacker Curiosity Hobbyist Botnets Worms Web Defacement Virus 1997 1998 2001 2004 2006 2008 Today

Top Security Drivers Summary Reduce Security Risks Improve efficiency Enable New Scenarios More Securely Prosperity Reduce intellectual property (IP) theft or system breach Save investments in existing infrastructure Loss of Sensitive Data through stolen computers, lost removable media and when decommissioning old hardware Reduce planning and deployment cost Integrity checking of early boot components Decrease number of support calls due to hardware or software incompatibilities or recovery of corporate information Secure shipping of hardware Efficient and non-intrusive protection of corporate data Control over removable storage devices Compliance with data protection regulations

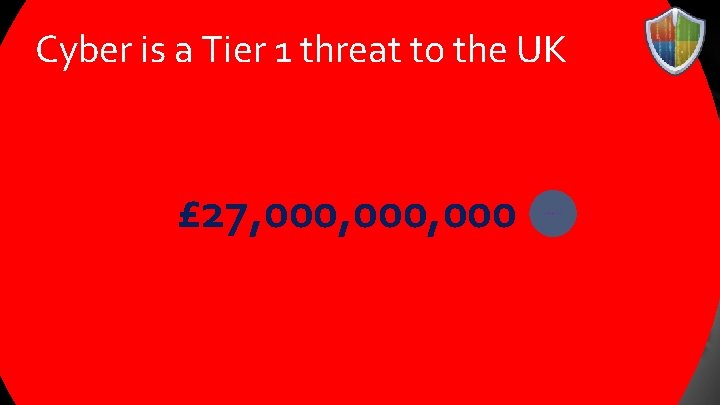
Cyber is a Tier 1 threat to the UK £ 650, 000 £ 27, 000, 000 £ 162, 500, 000

Economics of Cyber

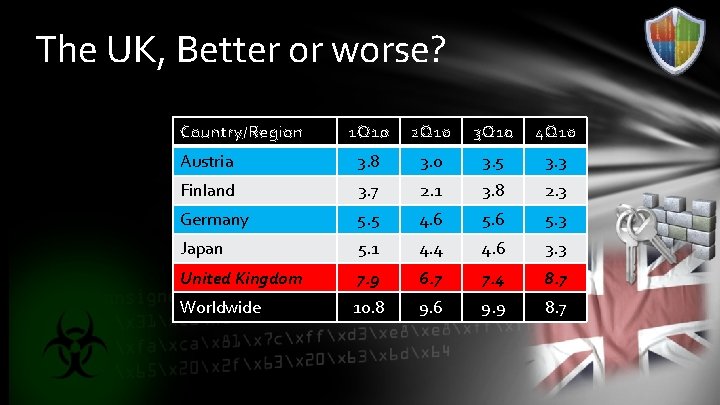
The UK, Better or worse? Country/Region 1 Q 10 2 Q 10 3 Q 10 4 Q 10 Austria 3. 8 3. 0 3. 5 3. 3 Finland 3. 7 2. 1 3. 8 2. 3 Germany 5. 5 4. 6 5. 3 Japan 5. 1 4. 4 4. 6 3. 3 United Kingdom 7. 9 6. 7 7. 4 8. 7 Worldwide 10. 8 9. 6 9. 9 8. 7

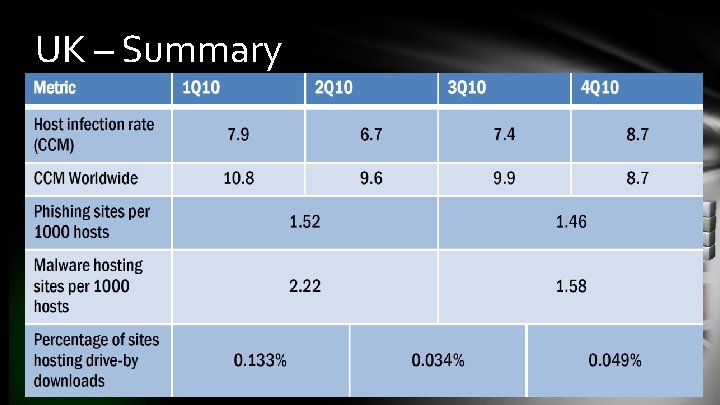
UK – Summary

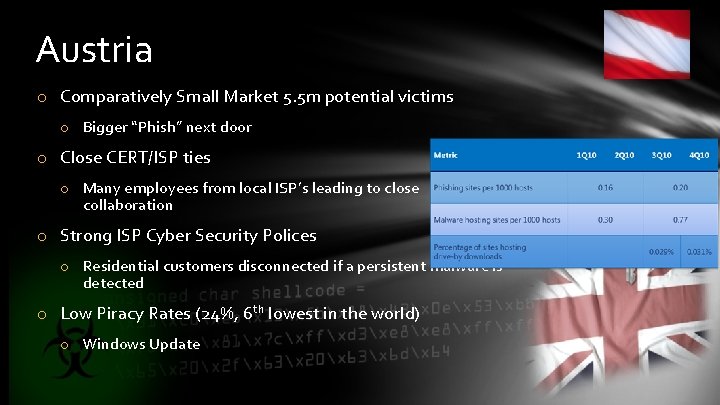
Austria o Comparatively Small Market 5. 5 m potential victims o Bigger “Phish” next door o Close CERT/ISP ties o Many employees from local ISP’s leading to close collaboration o Strong ISP Cyber Security Polices o Residential customers disconnected if a persistent malware is detected o Low Piracy Rates (24%, 6 th lowest in the world) o Windows Update

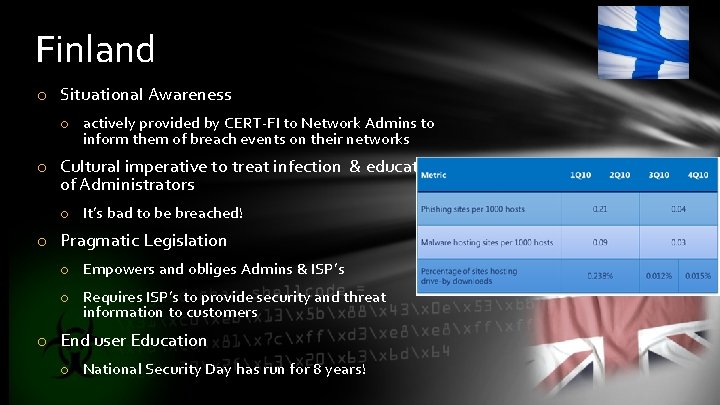
Finland o Situational Awareness o actively provided by CERT-FI to Network Admins to inform them of breach events on their networks o Cultural imperative to treat infection & education of Administrators o It’s bad to be breached! o Pragmatic Legislation o Empowers and obliges Admins & ISP’s o Requires ISP’s to provide security and threat information to customers o End user Education o National Security Day has run for 8 years!

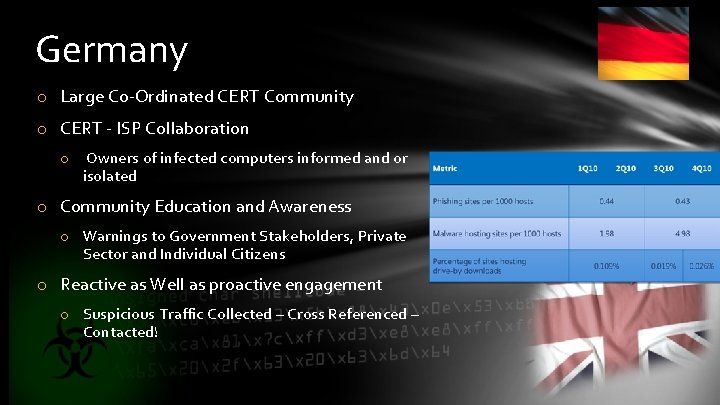
Germany o Large Co-Ordinated CERT Community o CERT - ISP Collaboration o Owners of infected computers informed and or isolated o Community Education and Awareness o Warnings to Government Stakeholders, Private Sector and Individual Citizens o Reactive as Well as proactive engagement o Suspicious Traffic Collected – Cross Referenced – Contacted!

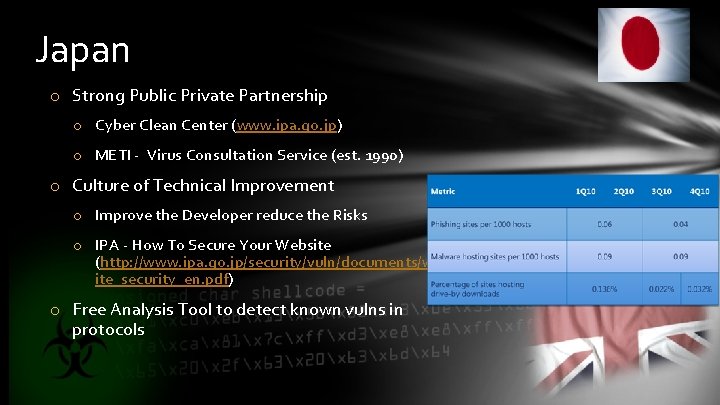
Japan o Strong Public Private Partnership o Cyber Clean Center (www. ipa. go. jp) o METI - Virus Consultation Service (est. 1990) o Culture of Technical Improvement o Improve the Developer reduce the Risks o IPA - How To Secure Your Website (http: //www. ipa. go. jp/security/vuln/documents/webs ite_security_en. pdf) o Free Analysis Tool to detect known vulns in protocols

Trends that will impact Cyber 64 -bit Computing Architectures of Safety Robust Mitigations Smart Devices Everywhere Web Modernization Cloud Computing Vulnerability Disclosure Cyber-Law “Loose” Cyber Weapons

64 -bit Computing o No SEH records on stack (breaks SEH hijack techniques) o SEHOP compensates for this on 32 -bit o Data Execute Protection (DEP) is permanently enabled o Apps must opt-in on 32 -bit o Heap “Terminate on Corruption” enabled by default for 64 -bit apps o Will see great revamping of exploit toolkits for 64 bit

Architectures of Safety o Goals o Compartmentalize a system so a compromise doesn’t result in a full system break o Increase attacker requirements (multiple vulns) o A history with Windows… o Windows NT 3. 1 introduced securable objects, DACLs, and access tokens o Windows 2000 introduced Job Objects and Restricted Tokens o Windows Vista introduced UI Privilege Isolation (UIPI) and integrity levels

Robust Mitigations o Microsoft has delivered a number of defenses since the beginning of Trustworthy Computing o Goal is to make exploits brittle Stack /GS 1. 0 /GS 1. 1 /GS 2. 0 Heap / Pool Heap 1. 0 Executable Code DEP EH 4 SEHOP Heap 2. 0 /NXCOMPAT /GS 3. 0 Heap. Term Safe Unlinking ASLR DEP+ATL DEP IE 8 DEP O 14 2003 2004 2005 2006 2007 2008 2009 17

Smart Devices Everywhere o Richer Targets o More connected o Authenticated Devices o Credentials o Location o Full featured OS o How many operating systems now? How many chips? o Do they update? o Do they use mitigation technology? o Are they ready for attacks?

Cloud Computing 19

Cyber-Law o Governments recognize: o The opportunity cyber brings to civil society (healthcare, economic prosperity, etc. ) o Need for better identity systems and trust mechanisms o The dependence of national economies on information infrastructures o The asymmetric risks of cyber threats o Approximately 50 countries pursuing legislation on: o National cyber incident reporting systems & info sharing o Critical infrastructure protection o Increasing security of government systems o Certification and training of cyber-security professionals o Increased criminal penalties

“Loose” Cyber Weapons The Internet as a unique “battlefield” Rich targets, Anonymity, Global connectivity, Lack of traceability. . Low barriers to downstream appropriation MS 08 -067 (Oct 2008) Excel (April 2009) IE Event. Obj (Jan 2010) IE #userdata (Mar 2010) XML Tags (Dec 2008) Power. Point (June 2009) Help Ctr ( July 2010) OWC AX (June 2009) Shell LNK( Aug 2010) Media Player (July 2009) Spooler ( Aug 2010) Win 32 k. sys ( Aug 2010) Task scheduler ( Aug 2010) 2008 2009 2010

How do we improve? o Stay up to date, move to x 64, stay patched o Drive genuine Public Private Partnerships – with positive measurable outcomes o IA Community actively monitor, communicate and act on threats o Cultural Change, Administrators need to be encouraged to mitigate threats o Enforcement Policies & Active Remediation of Threats o Education Campaigns and Media Focus on improving public awareness to what can be done to mitigate threats o Drive Down Low Piracy o Keep all software up to date, modernise where practical, isolate where not o EMET
