Microsofts Security Strategy Detlef Eckert Chief Security Advisor







- Slides: 17

Microsoft’s Security Strategy Detlef Eckert Chief Security Advisor Microsoft Europe, Middle East, Africa detlefe@microsoft. com Microsoft Confidential

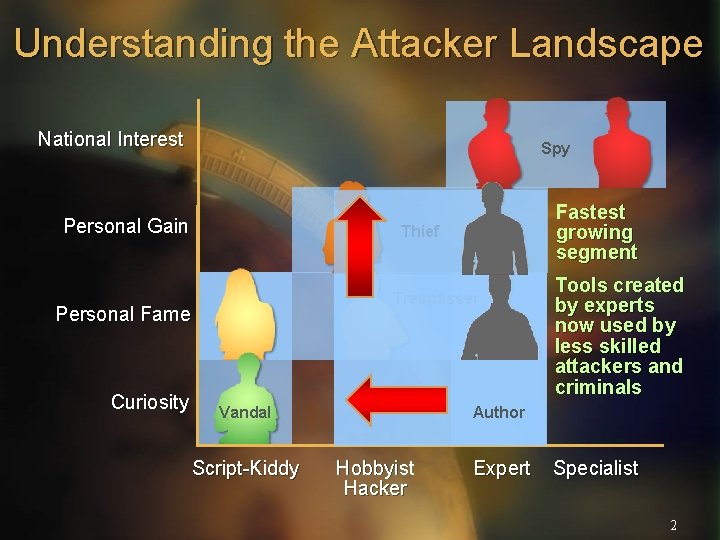
Understanding the Attacker Landscape National Interest Spy Personal Gain Thief Trespasser Personal Fame Curiosity Fastest growing segment Vandal Script-Kiddy Tools created by experts now used by less skilled attackers and criminals Author Hobbyist Hacker Expert Specialist 2

Microsoft’s security strategy in five steps Step One: Designing a more architecture Secure theresilient platform Writing code with fewer vulnerabilities Reducing the attack surface 3

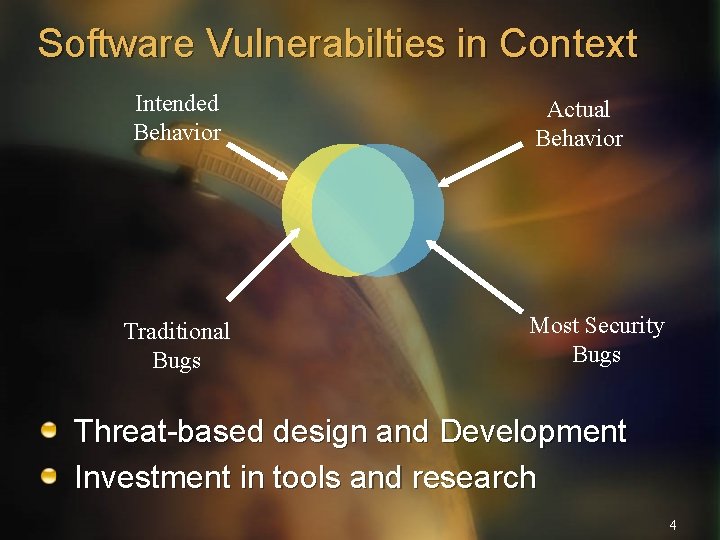
Software Vulnerabilties in Context Intended Behavior Traditional Bugs Actual Behavior Most Security Bugs Threat-based design and Development Investment in tools and research 4

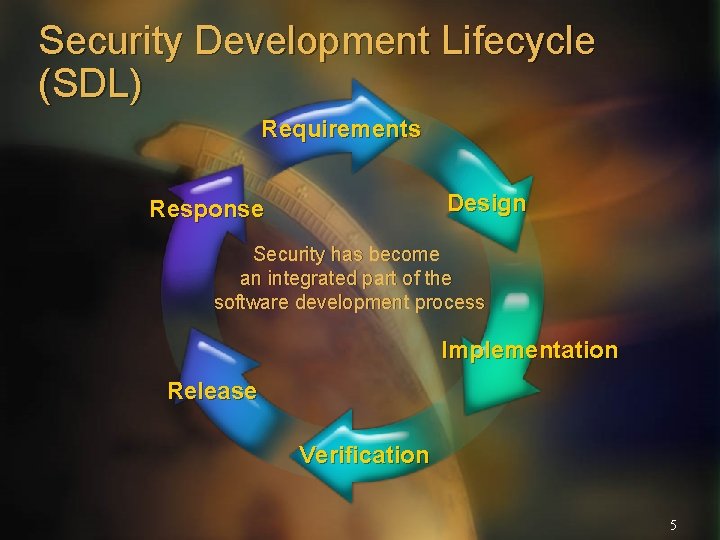
Security Development Lifecycle (SDL) Requirements Design Response Security has become an integrated part of the software development process Implementation Release Verification 5

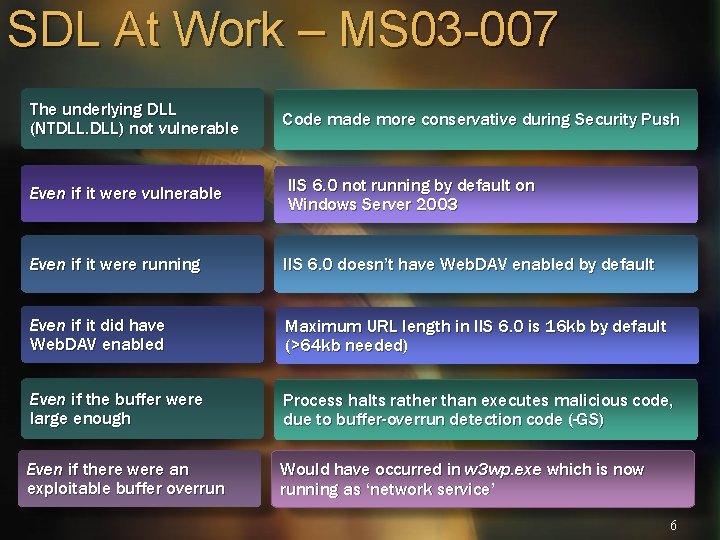
SDL At Work – MS 03 -007 The underlying DLL (NTDLL. DLL) not vulnerable Code made more conservative during Security Push Even if it were vulnerable IIS 6. 0 not running by default on Windows Server 2003 Even if it were running IIS 6. 0 doesn’t have Web. DAV enabled by default Even if it did have Web. DAV enabled Maximum URL length in IIS 6. 0 is 16 kb by default (>64 kb needed) Even if the buffer were large enough Process halts rather than executes malicious code, due to buffer-overrun detection code (-GS) Even if there were an exploitable buffer overrun Would have occurred in w 3 wp. exe which is now running as ‘network service’ 6

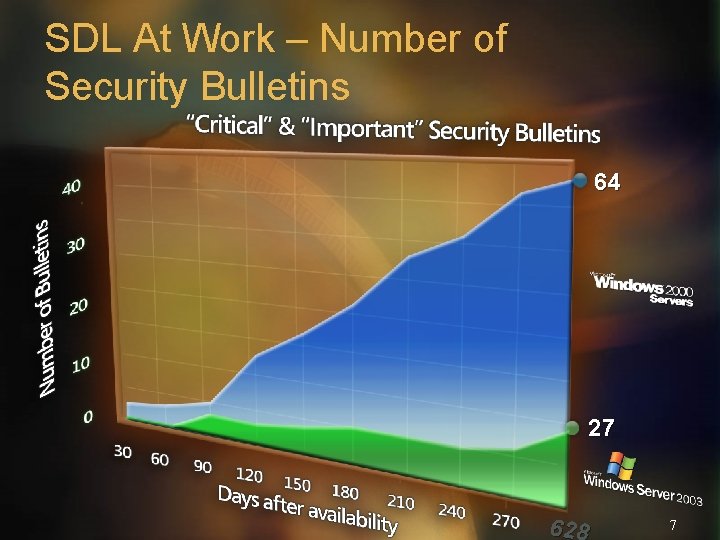
SDL At Work – Number of Security Bulletins 64 27 628 7

Microsoft’s security strategy in five steps Step Two: Improve Patch Quality Improve Unique Update Experience Rollback Facility Management Monthly Update Cycle Advanced Update Notification Security Advisory Tools and Management Software 8

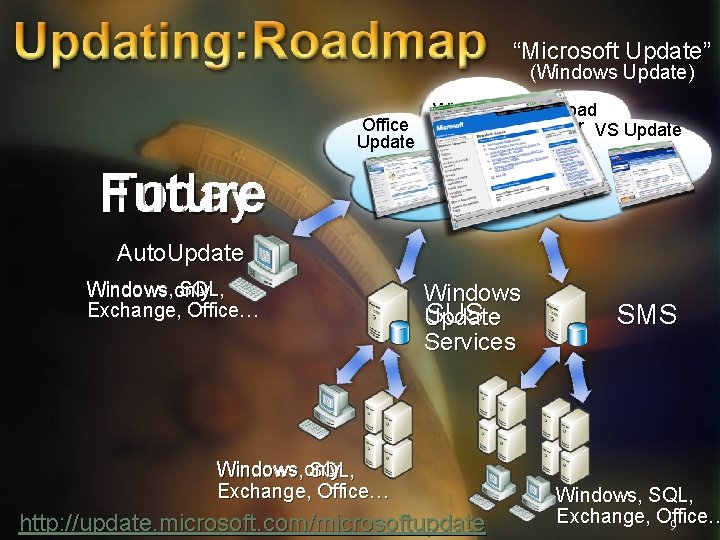
“Microsoft Update” (Windows Update) Office Update Windows Download Update Center VS Update Today Future Auto. Update Windows, only SQL, Windows Exchange, Office… Windows SUS Update Services Windows only Windows, SQL, Exchange, Office… http: //update. microsoft. com/microsoftupdate SMS Windows, SQL, Exchange, Office… 9

Microsoft’s security strategy in five steps Step Three: Windows Firewall ISA Server Protection Technology Active Anti-Virus (Ge. CAD, Sybari) Anti-Spyware More in planning (e. g. vulnerability assessment) 10

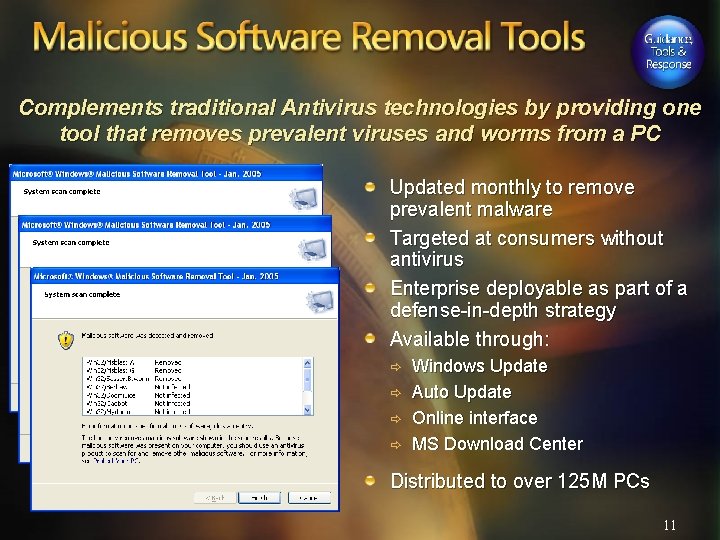
Complements traditional Antivirus technologies by providing one tool that removes prevalent viruses and worms from a PC Updated monthly to remove prevalent malware Targeted at consumers without antivirus Enterprise deployable as part of a defense-in-depth strategy Available through: ð ð Windows Update Auto Update Online interface MS Download Center Distributed to over 125 M PCs 11

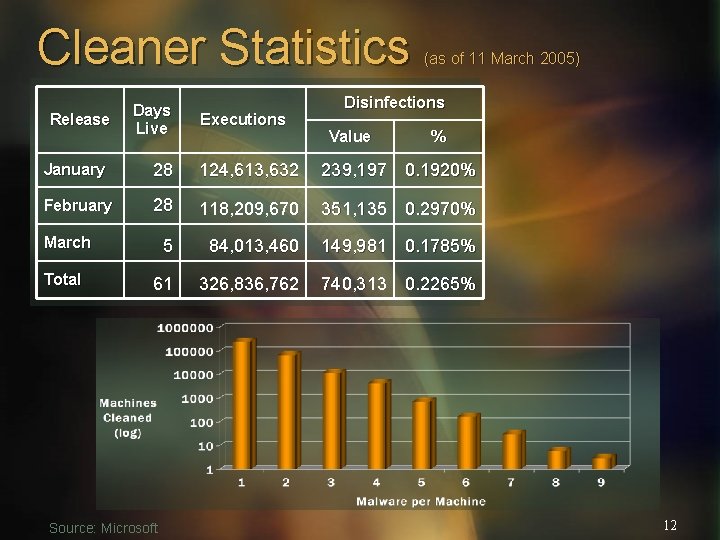
Cleaner Statistics Release Days Live Executions (as of 11 March 2005) Disinfections Value % January 28 124, 613, 632 239, 197 0. 1920% February 28 118, 209, 670 351, 135 0. 2970% 5 84, 013, 460 149, 981 0. 1785% 61 326, 836, 762 740, 313 0. 2265% March Total Source: Microsoft 12

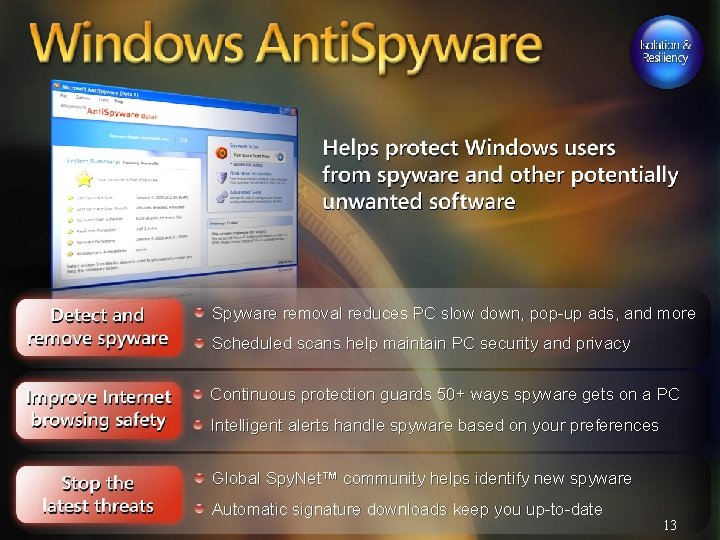
Spyware removal reduces PC slow down, pop-up ads, and more Scheduled scans help maintain PC security and privacy Continuous protection guards 50+ ways spyware gets on a PC Intelligent alerts handle spyware based on your preferences Global Spy. Net™ community helps identify new spyware Automatic signature downloads keep you up-to-date 13

Microsoft’s security strategy in five steps Step Four: Enabling Secure Designing Secure Applications (. NET, Visual Studio 2005, Guidelines & Business Scenarios Training) Secure Network Architectures Security Features of the Platform (e. g. Windows 2003 PKI, Windows Rights Management) 14

Microsoft’s security strategy in five steps Training and Education Step Five: Support for Industry Standards (e. g. Security WS Security)Eco System Partnerships (Anti. Virus Alliance) Research (Microsoft Research, Sponsorship) 15

The Longhorn Road IE 7 New levels of security building on XP SP 2 Stronger defenses against phishing, malware and spyware Least-Privilege User Administration Hardware based security: Secure start-up and Volume Encryption Network Access Protection Improved Management of Security Tokens Federated Identity: Infocards And much more …. 16

© 2004 Microsoft Corporation. All rights reserved. Microsoft Confidential This presentation is for informational purposes only. Microsoft makes no warranties, express or implied, in this summary.